- DL manuals
- TANDBERG
- Recording Equipment
- Border Controller
- User Manual
TANDBERG Border Controller User Manual
Summary of Border Controller
Page 1
Tandberg border controller user guide software version q6.0 d13691.08 february 2008 this document is not to be reproduced in whole or in part without permission in writing from:.
Page 2
Tandberg border controller user guide page 2 of 118 contents 1. Product information 8 1.1. Trademarks and copyright ......................................................................................................... 8 1.2. Disclaimer................................................................
Page 3
Tandberg border controller user guide page 3 of 118 4.7. Alternates..................................................................................................................................23 4.8. Call processing overview..........................................................................
Page 4
Tandberg border controller user guide page 4 of 118 11.3. Configuring dns naptr records .............................................................................................50 12. Example traversal deployments 51 12.1. Simple enterprise deployment................................................
Page 5
Tandberg border controller user guide page 5 of 118 17. Software upgrading 73 17.1. About software upgrading........................................................................................................73 17.2. Upgrading using http(s)...........................................................
Page 6
Tandberg border controller user guide page 6 of 118 18.3.11. Denylistadd......................................................................................................................................... 97 18.3.12. Denylistdelete ..................................................................
Page 7
Tandberg border controller user guide page 7 of 118 21. Appendix c: regular expression reference 112 22. Appendix d - technical data 113 22.1. Technical specifications .........................................................................................................113 22.1.1. System capacity...
Page 8
Tandberg border controller user guide page 8 of 118 1. Product information 1.1. Trademarks and copyright copyright 1993-2008 tandberg asa. All rights reserved. This document contains information that is proprietary to tandberg asa. No part of this publication may be reproduced, stored in a retrieval...
Page 9
Tandberg border controller user guide page 9 of 118 1.3.2. European environmental directives as a manufacturer of electrical and electronic equipment tandberg is responsible for compliance with the requirements in the european directives 2002/96/ec (weee) and 2002/95/ec (rohs). The primary aim of th...
Page 10
Tandberg border controller user guide page 10 of 118 1.4. Operator safety summary for your protection please read these safety instructions completely before you connect the equipment to the power source. Carefully observe all warnings, precautions and instructions both on the apparatus and in these...
Page 11
Tandberg border controller user guide page 11 of 118 1.4.7. Power connection and hazardous voltage • the product may have hazardous voltage inside. Never attempt to open this product, or any peripherals connected to the product, where this action requires a tool. • this product should always be powe...
Page 12
Tandberg border controller user guide page 12 of 118 2. Introduction this user manual is provided to help you make the best use of your tandberg border controller. A border controller is a key component of tandberg's expressway tm firewall traversal solution. Used in conjunction with a tandberg gate...
Page 13
Tandberg border controller user guide page 13 of 118 figure 1: front panel of border controller on the back of the border controller (see figure 2) there are: • a power connector • a power switch • a serial port (data 2) for connecting to a pc. Figure 2: rear panel of border controller.
Page 14
Tandberg border controller user guide page 14 of 118 3. Installation 3.1. Precautions • never install communication equipment during a lightning storm. • never install jacks for communication cables in wet locations unless the jack is specifically designed for wet locations. • never touch uninstalle...
Page 15
Tandberg border controller user guide page 15 of 118 3.3. Unpacking the tandberg border controller is delivered in a special shipping box which should contain the following components: • border controller unit • installation sheet • user manual and other documentation on cd • rack-ears and screws • ...
Page 16
Tandberg border controller user guide page 16 of 118 4. Getting started 4.1. Initial configuration the tandberg border controller requires some configuration before it can be used. This must be done using a pc connected to the serial port (data 1) or by connecting to the system's default ip address:...
Page 17
Tandberg border controller user guide page 17 of 118 9. Review other system settings. You may want to set the following: a. The name of the border controller. This is used by the tandberg management suite (tms) to identify the border controller. See the xconfiguration systemunit command (section 18....
Page 18
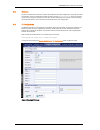
Tandberg border controller user guide page 18 of 118 you will be presented with the overview screen: note: http and https must be enabled in order to use the web interface. This is done using the following commands: xconfiguration http mode: xconfiguration https mode: note: if web access is required...
Page 19
Tandberg border controller user guide page 19 of 118 xconfiguration a read/write interface to set system configuration data such as ip address and subnet. Xcommand a miscellaneous group of commands for setting information or obtaining it. Xhistory provides historical information about calls and regi...
Page 20
Tandberg border controller user guide page 20 of 118 4.3. Backups you are recommended to maintain a backup of your border controller configuration. Using the command line interface, log on to the border controller as admin and type xconfiguration. Save the resulting output to a file, using cut-and-p...
Page 21
Tandberg border controller user guide page 21 of 118 4.5. Endpoint registration before an endpoint can use the border controller it must first register with it. The border controller behaves as the endpoint's gatekeeper. There are two ways an endpoint can register: • automatically • manually by spec...
Page 22
Tandberg border controller user guide page 22 of 118 4.6. Neighbor gatekeepers 4.6.1. Neighboring and dial plans as you start deploying more than one gatekeeper or border controller, it is useful to neighbor the systems together so that they can exchange information about registered endpoints. Each ...
Page 23
Tandberg border controller user guide page 23 of 118 figure 4: adding a new zone 4.6.3. Search order if a called alias matches a prefix or suffix zone a strong match is achieved. A weak match is achieved if a zone is to be queried only because it has no pattern matching configured. When an incoming ...
Page 24
Tandberg border controller user guide page 24 of 118 figure 5: alternate border controller configuration.
Page 25
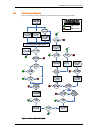
Tandberg border controller user guide page 25 of 118 4.8. Call processing overview figure 6 illustrates the process the border controller performs when receiving call requests. Figure 6: location decision flow diagram.
Page 26
Tandberg border controller user guide page 26 of 118 when an endpoint wants to call another endpoint it presents the address it wants to call to the border controller using a protocol knows as ras. The border controller applies any transforms (see section 5), tries to resolve the address, and if suc...
Page 27
Tandberg border controller user guide page 27 of 118 5. Transforming destination aliases 5.1. Alias transforms the alias transforms function takes any aliases present in arq and lrq messages and runs a set of transformations on them. The resulting aliases will then be used in the normal gatekeeper l...
Page 28
Tandberg border controller user guide page 28 of 118 5.2. Zone transforms it is possible to direct an incoming location request to a different alias by replacing either the prefix or the suffix of the alias with a new string, or by using regular expressions to specify the way in which the alias is t...
Page 29
Tandberg border controller user guide page 29 of 118 6. Unregistered endpoints although most calls are made between endpoints registered with a gatekeeper or border controller, it is sometimes necessary to place a call to or from an unregistered endpoint. 6.1. Calling from an unregistered endpoint a...
Page 30
Tandberg border controller user guide page 30 of 118 when the border controller is used with a gatekeeper for firewall traversal, you will typically set callstounknownipaddresses to indirect on the gatekeeper and direct on the border controller. This will allow endpoints registered to the gatekeeper...
Page 31
Tandberg border controller user guide page 31 of 118 7. Firewall traversal the border controller works with the tandberg gatekeeper, tandberg expressway endpoints and other endpoints which support the itu h.460.18 and h.460.19 standards to enable traversal of firewalls. 7.1. Traversal protocols and ...
Page 32
Tandberg border controller user guide page 32 of 118 7.2. Traversal zones when you use a gatekeeper to provide traversal on behalf of endpoints, you will need to create a traversal zone on the border controller. This zone may be configured to use either the assent protocol (the default) or h.460.18/...
Page 33
Tandberg border controller user guide page 33 of 118 8. Bandwidth control 8.1. About bandwidth control the tandberg border controller allows you to control endpoints' use of bandwidth on your network. Figure 9 shows a typical network deployment: a broadband lan, where high bandwidth calls are accept...
Page 34
Tandberg border controller user guide page 34 of 118 figure 10: configuring a subzone 8.2.1. Subzone bandwidths each subzone may be configured with its own bandwidth limits. Calls placed between two endpoints in the same subzone consume resource from the subzone's allocation. Subzone bandwidths are ...
Page 35
Tandberg border controller user guide page 35 of 118 figure 11: configuring a pipe pipes may be shared between one or more links. This is used to model the situation where a site communicates with several other sites over the same broadband connection to the internet. Each link may have up to two pi...
Page 36
Tandberg border controller user guide page 36 of 118 figure 12: configuring downspeeding options 8.4. Bandwidth control and firewall traversal when a border controller is being used to traverse a firewall, an additional subzone and zone(s) come into use on the border controller, as follows: • a trav...
Page 37
Tandberg border controller user guide page 37 of 118 8.5. Bandwidth control examples 8.5.1. Example without a firewall one possible configuration for the deployment in figure 9 is shown in figure 13. Each of the offices is represented as a separate subzone, with bandwidth configured according to loc...
Page 38
Tandberg border controller user guide page 38 of 118 figure 15: border controller example configuration figure 15 shows how the border controller could be configured for the deployment in figure 14. The introduction of the firewalls means that there is no longer any direct connectivity between the b...
Page 39
Tandberg border controller user guide page 39 of 118 9. Registration control the tandberg border controller can control which endpoints are allowed to register with it. Two separate mechanisms are provided: a simple registration restriction policy, and an authentication process based on user names a...
Page 40
Tandberg border controller user guide page 40 of 118 figure 17: configuring registration restrictions 9.1.3. Managing entries in the allow and deny lists when adding entries to the allow and deny lists, you can either specify an exact alias or use pattern matching to specify a group of aliases. Patt...
Page 41
Tandberg border controller user guide page 41 of 118 9.2. Authentication the tandberg border controller can use a user name and password based challenge-response scheme to permit registrations. For details of how to configure your endpoint with the appropriate information, please consult your endpoi...
Page 42
Tandberg border controller user guide page 42 of 118 that the border controller communicates with. The directory should also be configured with the h.323 aliases of endpoints that will register with the border controller. For instructions on how to configure common third party ldap servers, see appe...
Page 43
Tandberg border controller user guide page 43 of 118 configuring ldap base dn the border controller needs to be configured with the area of the directory which will be searched for the communication device information. This should be specified as the distinguished name (dn) in the directory under wh...
Page 44
Tandberg border controller user guide page 44 of 118 9.2.5. Securing the ldap connection with tls the traffic between the border controller and the ldap server can be encrypted using transport layer security (tls). To use tls, the ldap server must have a valid certificate installed so that the borde...
Page 45
Tandberg border controller user guide page 45 of 118 10.Uri dialing 10.1. About uri dialing if an alias is not located in the border controller's list of registrations, it may attempt to find an authoritative gatekeeper through the dns system. Uri dialing makes it easier for endpoints registered wit...
Page 46
Tandberg border controller user guide page 46 of 118 in addition, the dns records should be updated with the address of the border controller as the authoritative gatekeeper for the enterprise (see appendix a). This ensures that calls placed using uri dialing enter and leave the enterprise through t...
Page 47
Tandberg border controller user guide page 47 of 118 10.4. Dns records uri dialing relies on the presence of records in the dns information for the zone. For preference service (srv) records should be used. These specify the location of a server for a particular protocol and domain. Their format is ...
Page 48
Tandberg border controller user guide page 48 of 118 11.Enum dialing 11.1. About enum dialing enum provides another dns-based dialing scheme. Users dial an e.164 number - a telephone number - which is converted in to an h.323 uri by the dns system. The rules for uri dialing are then followed to plac...
Page 49
Tandberg border controller user guide page 49 of 118 figure 19: setting the enum zone.
Page 50
Tandberg border controller user guide page 50 of 118 11.3. Configuring dns naptr records enum relies on the presence of naptr records, as defined by rfc 2915 [7]. This is used to obtain an h.323 uri from the e.164 number. The record format that the border controller supports is: ;; order flag prefer...
Page 51
Tandberg border controller user guide page 51 of 118 12.Example traversal deployments 12.1. Simple enterprise deployment figure 20: simple enterprise deployment figure 20 shows a typical enterprise deployment. Endpoints 1001, 1002 and a gatekeeper are deployed on a private network, separated from th...
Page 52
Tandberg border controller user guide page 52 of 118 12.2. Enterprise gatekeepers if your enterprise has already deployed a third-party gatekeeper to manage calls within the private network, you may wish to deploy a traversal solution without having to alter the existing deployment. In order to achi...
Page 53
Tandberg border controller user guide page 53 of 118 in order to achieve this: 1. On the gatekeeper, set calls to unknown ip addresses to indirect. This can be done via either: xconfiguration gatekeeper callstounknownipaddresses: indirect or gatekeeper configuration -> gatekeeper and in the configur...
Page 54
Tandberg border controller user guide page 54 of 118 uri dialing will send all queries for a particular domain to the same border controller. If you want to have uri dialing covering multiple border controllers, nominate one as the master. That system is registered in dns and is set up with all the ...
Page 55
Tandberg border controller user guide page 55 of 118 13.Third party call control 13.1. About third party call control the border controller provides a third party call control api which enables you to place calls, disconnect calls, or initiate a blind transfer of an existing call. The api is provide...
Page 56
Tandberg border controller user guide page 56 of 118 13.3.2. Enabling call transfer to enable call transfer, either: issue the command: xconfiguration services calltransfer mode: or go to border controller configuration -> services and in the call transfer section, tick the allow call transfer box (...
Page 57
Tandberg border controller user guide page 57 of 118 14.Multiway 14.1. About multiway two callers in a simple point-to-point call may sometimes wish to bring other endpoints into the call. This can be achieved seamlessly using tandberg equipment, even if the two original endpoints do not support mul...
Page 58
Tandberg border controller user guide page 58 of 118 14.4. Configuration 1. Set call routed mode to on . This can be done via either: xconfiguration gatekeeper callrouted: on or border controller configuration > gatekeeper . In the configuration section, tick the call routed box. 2. Set ad hoc confe...
Page 59
Tandberg border controller user guide page 59 of 118 15.Call policy 15.1. About call policy your tandberg border controller allows you to set up policy to control which calls are allowed and even redirect selected calls to different destinations. You specify this policy by uploading a script written...
Page 60
Tandberg border controller user guide page 60 of 118 15.2. Making decisions based on addresses 15.2.1. Address-switch the address-switch node allows the script to run different actions based on the source or destination aliases of the call. The address-switch specifies which fields to match and then...
Page 61
Tandberg border controller user guide page 61 of 118 subfield the following table gives the definition of subfields for each alias type. If a subfield is not specified for the alias type being matched then the not-present action will be taken. Address-type for all alias types the address-type subfie...
Page 62
Tandberg border controller user guide page 62 of 118 address the address construct is used within an address-switch to specify addresses to match. It supports the use of regular expressions (see appendix c for further information). Note: all address comparisons ignore upper/lower case differences so...
Page 63
Tandberg border controller user guide page 63 of 118 15.3.2. Proxy on executing a proxy node the border controller will attempt to forward the call to the locations specified in the current location set. If multiple entries are in the location set then they are treated as different aliases for the s...
Page 64
Tandberg border controller user guide page 64 of 118 15.5.2. Call screening based on domain in this example, user fred will not accept calls from anyone at annoying.Com, or from any unauthenticated users. All other users will allow any calls. 15.5.3. Call redirection this example redirects all calls...
Page 65
Tandberg border controller user guide page 65 of 118 15.5.5. Prevent external use of gateway in this example, we have an isdn gateway registered with an alias of mygateway that uses the prefixes of 0 and 9 to route outbound isdn calls. The following script shows how to prevent callers from outside y...
Page 66
Tandberg border controller user guide page 66 of 118 16.Logging 16.1. About logging the border controller provides logging for troubleshooting and auditing purposes. 16.2. Viewing the event log to view the event log, either issue the command: eventlog [n/all] where n the number of lines (from end of...
Page 67
Tandberg border controller user guide page 67 of 118 16.4. Event log format the event log is displayed in an extension of the unix syslog format: date time host_name facility_name : message_details where date the local date on which the message was logged time the local time at which the message was...
Page 68
Tandberg border controller user guide page 68 of 118 16.5. Logged events events logged at level 1 event description eventlog cleared an operator cleared the event log. Admin session start an administrator has logged onto the system. Admin session finish an administrator has logged off the system. Sy...
Page 69
Tandberg border controller user guide page 69 of 118 event description external server communication failure communication with an external server failed unexpectedly. The event detail data should differentiate between 'no response' and 'request rejected'. Servers concerned are: • dns servers • ldap...
Page 70
Tandberg border controller user guide page 70 of 118 event data fields each event has associated data fields. Fields are listed below in the order in which they appear in the log message. Field description applicable events protocol specifies which protocol was used for the communication. Valid valu...
Page 71
Tandberg border controller user guide page 71 of 118 field description applicable events src-ip specifies the source ip address (the ip address of the device attempting to establish communications). The source ip is recorded in the dotted decimal format: (number).(number).(number).(number) or the ip...
Page 72
Tandberg border controller user guide page 72 of 118 field description applicable events level the level of the event as defined in section 16.3.1. All events * included if event parameter relevant or available for message concerned. In addition to the events described above, a syslog.Info event con...
Page 73
Tandberg border controller user guide page 73 of 118 17.Software upgrading 17.1. About software upgrading software upgrade can be done in one of two ways: • using a web browser (http/https). • using secure copy (scp). Note: to upgrade the border controller, a valid release key and software file is r...
Page 74
Tandberg border controller user guide page 74 of 118 3. Browse to the file containing the software and select install . You will see a page indicating that upload is in progress: when the upload is completed you will see the following: 4. Select restart . You will see a confirmation window: the syst...
Page 75
Tandberg border controller user guide page 75 of 118 to upgrade using scp or pscp: 1. Make sure the system is turned on and available on ip. 2. Upload the release key file using scp/pscp to the /tmp folder on the system e.G. Scp release-key root@10.0.0.1:/tmp/release-key or pscp release-key root@10....
Page 76
Tandberg border controller user guide page 76 of 118 18.Command reference this chapter lists the basic usage of each command. The commands also support more advanced usage, which is outside the scope of this document. 18.1. Status the status root command, xstatus, returns status information from the...
Page 77
Tandberg border controller user guide page 77 of 118 18.1.5. Externalmanager xstatus externalmanager returns information about the external manager. The external manager is the remote system, such as the tandberg management suite (tms) used to manage the endpoints and network infrastructure. Address...
Page 78
Tandberg border controller user guide page 78 of 118 18.1.9. Links xstatus links r eports call and bandwidth information for all links on the system. Xstatus links link index> reports call and bandwidth information for the specified link. Name returns the name assigned to this link calls returns a l...
Page 79
Tandberg border controller user guide page 79 of 118 18.1.14. Resourceusage xstatus resourceusage returns information about the usage of system resources. Registrations number of currently active registrations. Maxregistrations maximum number of concurrent registrations since system traversalcalls n...
Page 80
Tandberg border controller user guide page 80 of 118 18.1.17. Zones xstatus zones returns call and bandwidth information for all zones on the system. Also shows status of the zone as a whole and the status of each gatekeeper in the zone. 18.2. Configuration the configuration root command, xconfigura...
Page 81
Tandberg border controller user guide page 81 of 118 xconfiguration authentication mode: specifies whether or not to use h.235 authentication of calls and registrations. The default is off: no authentication is required. Xconfiguration authentication username: specifies the user name to be used by t...
Page 82
Tandberg border controller user guide page 82 of 118 xconfiguration gatekeeper callrouted: specifies whether the border controller should operate in call routed mode. The defaults is off..
Page 83
Tandberg border controller user guide page 83 of 118 xconfiguration gatekeeper callstounknownipaddresses: specifies whether or not the border controller will attempt to call systems which are not registered with it or one of its neighbor gatekeepers. Options are: direct allows an endpoint to make a ...
Page 84
Tandberg border controller user guide page 84 of 118 sets the local zone prefix of the system. Xconfiguration gatekeeper policy mode: determines whether or not the cpl policy engine is active. The default is on..
Page 85
Tandberg border controller user guide page 85 of 118 xconfiguration gatekeeper registration allowlist [1..1000] pattern: pattern> specifies a pattern in the list of allowed registrations. If one of an endpoint's aliases matches one of the patterns in the allow list, the registration will be allowed....
Page 86
Tandberg border controller user guide page 86 of 118 18.2.5. Http/https commands under the http and https nodes control web access to the border controller. Xconfiguration http mode: enables/disables http support. The default is on. You must restart the system for changes to take effect. Xconfigurat...
Page 87
Tandberg border controller user guide page 87 of 118 xconfiguration ip dns domain name: name> specifies the name to be appended to the domain name before a query to the dns server is executed, when attempting to resolve a domain name which is not fully qualified. Note: this parameter is only used wh...
Page 88
Tandberg border controller user guide page 88 of 118 controls the granularity of event logging with 1 being the least verbose, 3 the most. 18.2.10. Ntp xconfiguration ntp address: address> sets the ip address of the ntp server to be used when synchronizing system time. This can be either an ip addre...
Page 89
Tandberg border controller user guide page 89 of 118 xconfiguration services adhocconferencing prefix: specifies the prefix to be used for unencrypted conference requests. Xconfiguration services adhocconferencing encryption prefix: specifies the prefix to be used for encrypted conference requests. ...
Page 90
Tandberg border controller user guide page 90 of 118 18.2.14. Session xconfiguration session timeout: controls how long an administration session (https, telnet or ssh) may be inactive before the session is timed out. A value of 0 turns session time outs off. The default is 0. You must restart the s...
Page 91
Tandberg border controller user guide page 91 of 118 xconfiguration subzones traversalsubzone bandwidth percall limit: per-call bandwidth available on the traversal subzone. Xconfiguration subzones traversalsubzone bandwidth percall mode: whether or not the traversal subzone is enforcing per-call ba...
Page 92
Tandberg border controller user guide page 92 of 118 18.2.18. Systemunit xconfiguration systemunit name: the name of the unit. Choose a name that uniquely identifies the system. Xconfiguration systemunit password: specify the password of the unit. The password is used to login with telnet, http(s), ...
Page 93
Tandberg border controller user guide page 93 of 118 xconfiguration traversal media rtcp port: specifies the udp port to which media control information should be sent. Conventionally this will be set to rtp port + 1. The default is 2777. Xconfiguration traversal assentenabled: determines whether or...
Page 94
Tandberg border controller user guide page 94 of 118 xconfiguration zones traversalzone [1..50] match [1..5] pattern behavior: determines whether the matched part of the alias should be modified before an lrq is sent to the indicated zone. If set to leave, the alias will be unmodified. If set to str...
Page 95
Tandberg border controller user guide page 95 of 118 xconfiguration zones zone [1..100] match [1..5] pattern behavior: determines whether the matched part of the alias should be modified before an lrq is sent to the indicated zone. If set to leave, the alias will be unmodified. If set to strip, the ...
Page 96
Tandberg border controller user guide page 96 of 118 18.3. Command the command root command, xcommand, is used to execute commands on the border controller. To list all xcommands type: xcommand ? To get usage information for a specific command, type: xcommand command_name> ? 18.3.1. Adhocconference ...
Page 97
Tandberg border controller user guide page 97 of 118 node1 node2 the case-sensitive names of the nodes. Bandwidth the required bandwidth. Calltype must be one of traversal, routed or direct 18.3.7. Credentialadd xcommand credentialadd username> password> adds the given username and password to the l...
Page 98
Tandberg border controller user guide page 98 of 118 18.3.12. Denylistdelete xcommand denylistdelete removes the pattern with the specified index from the deny list. Deny list entries can be viewed using the command xconfiguration gatekeeper registration denylist ..
Page 99
Tandberg border controller user guide page 99 of 118 18.3.13. Dial xcommand dial places call halves out to the specified source and destination, joining them together. Callsrc and calldst can be specified using either an alias or ip address. Bandwidth is in kbps. 18.3.14. Disconnectcall xcommand dis...
Page 100
Tandberg border controller user guide page 100 of 118 18.3.16. Feedbackderegister xcommand feedbackderegister deregisters the specified feedback expression. All registered feedback expressions may be removed by issuing the command: xcommand feedbackderegister 0 18.3.17. Findregistration xcommand fin...
Page 101
Tandberg border controller user guide page 101 of 118 18.3.24. Pipedelete xcommand pipedelete deletes the pipe with the specified index. 18.3.25. Removeregistration xcommand removeregistration removes the specified registration. 18.3.26. Subzoneadd xcommand subzoneadd name> address> adds and configu...
Page 102
Tandberg border controller user guide page 102 of 118 18.3.29. Transformdelete xcommand transformdelete deletes the transform with the specified index. Note: a list of all current transforms can be obtained using the command: xconfiguration gatekeeper transform . 18.3.30. Traversalzoneadd xcommand t...
Page 103
Tandberg border controller user guide page 103 of 118 18.4. History the history root command, xhistory, is used to display historical data on the border controller. To list all xhistory commands type: xhistory ? To list all history data, type: xhistory to show a specific set of history data, type: x...
Page 104
Tandberg border controller user guide page 104 of 118 18.5. Feedback the feedback root command, xfeedback, is used to control notifications of events and status changes on the border controller. A feedback expression describes an interesting event or change in status. When a feedback expression is r...
Page 105
Tandberg border controller user guide page 105 of 118 18.5.3. Register event xfeedback register event registers for all available events. Xfeedback register event/ unregistration/bandwidth/resourceusage> registers for feedback on the occurrence of the specified event. Note: registering for the resou...
Page 106
Tandberg border controller user guide page 106 of 118 18.6. Other commands 18.6.1. About about returns information about the software version installed on the system. 18.6.2. Clear clear clears the event log or history of all calls and registrations. 18.6.3. Eventlog eventlog n/all> displays the eve...
Page 107
Tandberg border controller user guide page 107 of 118 19.Appendix a: configuring dns servers in the examples below, we set up an srv record to handle h.323 uris of the form user@example.Com these are handled by the system with the fully qualified domain name of gatekeeper1.Example.Com which is liste...
Page 108
Tandberg border controller user guide page 108 of 118 20.Appendix b: configuring ldap servers 20.1. Microsoft active directory 20.1.1. Prerequisites these comprehensive step-by-step instructions assume that active directory is installed. For details on installing active directory please consult your...
Page 109
Tandberg border controller user guide page 109 of 118 20.1.3. Securing with tls to enable active directory to use tls, you must request and install a certificate on the active directory server. The certificate must meet the following requirements: • be located in the local computer's personal certif...
Page 110
Tandberg border controller user guide page 110 of 118 20.2.3. Adding h.350 objects 1. Create the organizational hierarchy create an ldif file with the following contents: # this example creates a single organizational unit to contain # the h.350 objects dn: ou=h350,dc=my-domain,dc=com objectclass: o...
Page 111
Tandberg border controller user guide page 111 of 118 20.2.4. Securing with tls the connection to the ldap server can be encrypted by enabling transport level security (tls) on the connection. To do this you must create an x.509 certificate for the ldap server to allow the border controller to verif...
Page 112
Tandberg border controller user guide page 112 of 118 21.Appendix c: regular expression reference regular expressions can be used in conjunction with a number of border controller features such as alias transformations, zone transformations, cpl policy and enum. The border controller uses posix form...
Page 113
Tandberg border controller user guide page 113 of 118 22.Appendix d - technical data 22.1. Technical specifications 22.1.1. System capacity • 500 registered traversal endpoints • 100 traversal calls at 384 kbps • 100 zones option keys may restrict the system to a lower capacity than specified above....
Page 114
Tandberg border controller user guide page 114 of 118 22.1.9. Hardware mtbf • hardware mtbf: 80,479 hours 22.1.10. Power supply • 250 watt • 90-264v full range @47- 63 hz 22.1.11. Certification • lvd 73/23/ec • emc 89/366/ecc 22.2. Approvals this product has been approved by various international ap...
Page 115
Tandberg border controller user guide page 115 of 118 23.Bibliography 1 itu specification: h.235 security and encryption for h-series (h.323 and other h.245-based) multimedia terminals http://www.Itu.Int/rec/t-rec-h.235/en 2 itu specification: h.350 directory services architecture for multimedia con...
Page 116
Tandberg border controller user guide page 116 of 118 24.Glossary alias the name an endpoint uses when registering with the border controller. Other endpoints can then use this name to call it. Arq, admission request an endpoint ras request to make or answer a call. Dns zone a subdivision of the dns...
Page 117
Tandberg border controller user guide page 117 of 118 25.Index —a— about ...........................................................................97 account administrator account ........................................19 root account .......................................................19 activ...
Page 118
Tandberg border controller user guide page 118 of 118 ldap schema............................................................100 ldap servers - configuring.......................................100 ldif 101 license .........................................................................97 links ......