- DL manuals
- Thecus
- Server
- N2520 series
- User Manual
Thecus N2520 series User Manual
Summary of N2520 series
Page 1
User’s manual n2520/n2560/n4520/n4560 series v 6.2.
Page 2: About This Manual
Ii copyright and trademark notice copyright and trademark notice thecus and other names of thecus products are registered trademarks of thecus technology corp. Microsoft, windows, and the windows logo are registered trademarks of microsoft corporation. Apple, itunes and apple os x are registered tra...
Page 3: Safety Warnings
Iii safety warnings safety warnings for your safety, please read and follow the following safety warnings: read this manual thoroughly before attempting to set up your thecus ip storage. ¾ your thecus ip storage is a complicated electronic device. t attempt to re thecus ip storage is a complic...
Page 4: Table of Contents
Iv table of contents table of contents copyright and trademark notice. ...............................................Ii about this manual. ......................................................................Ii limited warranty. ........................................................................
Page 5
V table of contents 3.3.13 reboot & shutdown. ................................................................................................ 20 3.3.14 file system check. .................................................................................................... 20 3.3.15 wake up n la (w...
Page 6
Vi table of contents 3.7.3 module installation. .................................................................................................... 75 3.7.4 as application. .......................................................................................................... 76 3.8 backup. ......
Page 7: Chapter 1: Introduction
1 chapter 1: introduction chapter 1: introduction § overview 1.1 thank you for choosing the thecus ip storage server. The thecus ip storage is an easy-to-use storage server that allows a dedicated approach to storing and distributing data on a network. Data reliabil- ity is ensured with raid feature...
Page 8: Front Panel
2 chapter 1: introduction front panel 1.3 n2520/n2560: • the thecus n2520/n2560’s front panel shows the device’s indicators and hard disk install slots: front panel item description 1. System status blinking white: diagnostic mode kick-in solid white: diagnostic completed 2. Hdd1 led blinking white:...
Page 9
3 chapter 1: introduction n4520/n4560: • the thecus n4520/n4560 front panel shows the device’s indicators, system information and hard disk trays: front panel item description 1. Power led solid blue: power on 2. System status blinking orange: diagnostic mode kick-in solid orange: diagnostic complet...
Page 10: Rear Panel
4 chapter 1: introduction rear panel 1.4 n2520/n2560: • the n2520/n2560 rear panel features ports and connectors. Back panel item description 1. System fan system fan that exhausts heat from the unit. 2. Hdmi for video/audio out 3. Spdif for audio out 4. Lan port lan port for connecting to an ethern...
Page 11
5 chapter 1: introduction n4520/n4560: • the n4520/n4560 rear panel features ports and connectors. Back panel item description 1. System fan system fan that exhausts heat from the unit. 2. Usb ports usb 2.0 port for compatible usb devices, such as digital cameras, usb disks, and usb printers. 3. Lan...
Page 12
6 chapter 2: hardware installation chapter 2: hardware installation § overview 221 your thecus ip storage is designed for easy installation. To help you get started, the following chapter will help you quickly get your thecus ip storage up and running. Please read it carefully to prevent damaging yo...
Page 13
7 chapter 2: hardware installation press the power button on the front panel to boot up the thecus ip storage. 3. N2520/n2560 power button s n4520/n4560 power button s.
Page 14: Overview
8 chapter 3: system administration chapter 2: system administration § overview 3.1 the thecus ip storage provides an easily accessible web administration interface. With it, you can configure and monitor the thecus ip storage anywhere on the network. Web administration interface 3.2 make sure your n...
Page 15
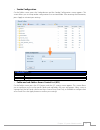
9 chapter 3: system administration my favorite 3.2.1 the user interface with “my favorite” shortcut allows the user to designate often used items and have them display on the main screen area. The figure below displays system favorite functions. Administrators can add or remove favorite functions to...
Page 16
10 chapter 3: system administration message bar 3.2.3 you can get quick information about your system status by moving your mouse over these icons. Message bar item status description raid information. Display the status of created raid volume. Click to go to raid information page as short cut. Disk...
Page 17: System Management
11 chapter 3: system administration language selection 3.2.6 the thecus ip storage supports multiple languages, including: english japanese traditional chinese simplified chinese french german italian korean spanish russian polish portuguese on the menu bar, click language and the selection list ap-...
Page 18
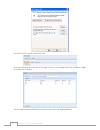
12 chapter 3: system administration system/service status 3.3.2 from the system management category,, choose the status item, system service status and hw sta- tatus item, system service status and hw sta- item, system service status and hw sta- service status and hw sta- and hw sta- hw sta- sta- tu...
Page 19
13 chapter 3: system administration warn shows only warning messages. Error shows only error messages. Download all log file export all logs to an external file. Truncate all log file clear all log files. The number of lines per page specify desired number of lines to display per page. Sort ascendin...
Page 20
14 chapter 3: system administration syslog service if server has been selected then associated syslog folder will be used to store all system logs from other nas devices which has assigned this system for syslog server as well as syslog of this server unit. It can be seen from associated syslog fold...
Page 21
15 chapter 3: system administration for the on-line users list, system monitor will display the on-line users and the share folder they have visited. System monitor item description save layout saving selected monitoring items. Layout will remain the same for future visits. Reset layout set back to ...
Page 22
16 chapter 3: system administration.
Page 23
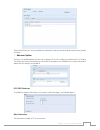
17 chapter 3: system administration time: setting system time 3.3.7 from the system management category, choose the time item and the time screen appears. Set the desired date, time, and time zone. You can also elect to synchronize the system time on thecus ip storage with an ntp (network time proto...
Page 24
18 chapter 3: system administration schedule power on/off 3.3.9 using the thecus ip storage system management, you can save energy and money by scheduling the thecus ip storage to turn itself on and off during certain times of the day. From the system management category, choose the schedule power o...
Page 25
19 chapter 3: system administration administrator password 3.3.10 from the system management category, choose the administrator password item and the change administrator password screen appears. Enter a new password in the new password box and con- firm your new password in the confirm password box...
Page 26
20 chapter 3: system administration resetting to factory defaults will not erase the data stored in the hard disks, but will revert all the settings to the factory default values reboot & shutdown 3.3.13 from the system management category, choose reboot & shutdown item, and the shutdown/re- boot sy...
Page 27
21 chapter 3: system administration once you click next, you will see the following screen: click start to begin the file system check. Click reboot to reboot the system. When the file system check is running, the system will show 20 lines of information until it is com- plete. Once complete, the re...
Page 28
22 chapter 3: system administration wake-up on lan (wol) 3.3.15 the thecus ip storage has the ability to be awoken from sleep mode via lan port. From the system management category, choose the wol item, and the wake-up on lan screen ap- pears. From here, you can enable or disable. Snmp support (n452...
Page 29
23 chapter 3: system administration networking 3.3.18 from the system management category, choose networking, and the networking configuration screen appears. This screen displays the network parameters of the global setting and available network connection. You may change any of these items and pre...
Page 30: Storage Management
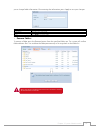
24 chapter 3: system administration most faster ethernet (10/100) switches/routers do not support jumbo frame and will not be able to connect to your thecus as after jumbo frame is turned on. Storage management 3.4 the storage menu displays the status of storage devices installed in the thecus ip s...
Page 31
25 chapter 3: system administration s2m2a2r2t2 information • on the disk information screen, select a disk then click on “smart” to list the s.M.A.R.T. Info of the associated disk. You may also perform a disk smart test; simply click “test” to start the smart test. The result is only for reference a...
Page 32
26 chapter 3: system administration current pending sector current count of unstable sectors (waiting for remapping). The raw value of this attribute indicates the total number of sectors waiting for remapping. Later, when some of these sectors are read successfully, the value is decreased. If error...
Page 33
27 chapter 3: system administration raid level shows the current raid configuration. Status indicates status of the raid. Can read either healthy, degraded, or damaged. Disks used hard disks used to form the current raid volume. Total capacity total capacity of the current raid. Data capacity indica...
Page 34
28 chapter 3: system administration specify a raid id. 3. If this raid volume is meant to be the master raid volume, tick the master raid checkbox. 4. In a multiple rai configuration, one rai volume must be designated as the master rai volume. The master rai volume will store all installed modul...
Page 35
29 chapter 3: system administration once the create button has been pressed with the encryption checkbox enabled, the following message pop-up will appear for confirmation. After the raid volume has been created, you may remove the usb disk until the next time the system boots. The raid volume canno...
Page 36
30 chapter 3: system administration selected the file system you would like to have for this raid volume. . 8. Press submit to build the raid storage volume. 9. Press “yes” for raid volume creation preparation. Then click “finish” to start up with raid 10. Volume building..
Page 37
31 chapter 3: system administration building a rai volume may be time consuming, depending on the size of hard drives and rai mode. In general, if the rai volume building process is up to “rai building”, then the data volume is accessible. Creating rai destroys all data in the current rai volu...
Page 38
32 chapter 3: system administration creating rai destroys all data in the current rai volume. The data will be unrecoverable. Edit raid • on the raid information screen, press the edit button to go to the raid information screen. Using edit raid, you can select raid id and the spare disk..
Page 39
33 chapter 3: system administration remove raid • click to remove the raid volume. All user data and iscsi created in the selected raid volume will be deleted. To remove a raid volume, follow the steps below: on the raid list screen, select the raid volume by clicking on its radio button, and click ...
Page 40
34 chapter 3: system administration migrating a raid(dose not apply to the n2520/n2560) • once a raid volume has been created, you may want to move it to other physical drives or change the raid array all together. To migrate a raid 1, raid 5 or raid 6 volume, follow the steps below: from the raid c...
Page 41
35 chapter 3: system administration migrating a rai volume could take several hours to complete. • the rai migration feature is available only when it is configurable. • here is a list of limitation with raid level migration function: during raid level migration, it is not permitted to reboot or s...
Page 42
36 chapter 3: system administration nas stacking (n4520/n4560 only) 3.4.3 the thecus ip storage’s capacity can be expanded even further using the stackable function. With it, users can expand the capacity of their network storage systems up to 5 other stack target volumes which are located in differ...
Page 43
37 chapter 3: system administration next, input the target ip address of the stackable device and click the discovery button. The system will list available target volumes from the inputted ip address. Once the volume ip has been set, you may need to input a valid user name and password to validate ...
Page 44
38 chapter 3: system administration from the figure above, the stacked target name is “pmmeeting”. The figures below show the result before and after via microsoft network access when settings have been completed. The browseable setting is the same method used for setting a system share folder. It d...
Page 45
39 chapter 3: system administration the public setting will be set the same way as the setting for the system share folder associated with the acl permission is. If public is set to yes, all users will be able to access it, and acl button will be grayed out. If public is set to no, the acl button wi...
Page 46
40 chapter 3: system administration with this newly attached stack target device, you will see the information displayed and also have access to several options to choose from. In general, if the attached stack target device has been used by another thecus nas as stack target volume, then the format...
Page 47
41 chapter 3: system administration d2 stack target acl if the stack target public setting set to yes, then the acl button will be grayed out. However, if public setting is set to no, then the acl button will be available for you to setup user access permissions for the stack target. The acl setting...
Page 48
42 chapter 3: system administration iso mount (n4520/n4560 only) 3.4.4 the iso mount feature is a very useful tool from the thecus products. With it, users can mount an iso file and have the export name display all the details from the mounted iso file. From the main menu, the iso mount feature is l...
Page 49
43 chapter 3: system administration to mount the new iso file, select one file from the list of files and input the desired mounting name into the “mount as:” field. Click “add” to confirm the completion of the mounting. If nothing is input in the “mount as” iso file export name field, the system wi...
Page 50
44 chapter 3: system administration iscsi (n4520/n4560 only) 3.4.5 you may specify the space allocated for iscsi. See the table below to the allowed iscsi target num- see the table below to the allowed iscsi target num- see the table below to the allowed iscsi target num- iscsi target num- num- ber ...
Page 51
45 chapter 3: system administration to allocate space for an iscsi target on the current raid volume, follow the steps below: under the iscsi target list, select iscsi target then click add. 1. The create iscsi volume screen appears. Create iscsi volume item description iscsi target volume enable or...
Page 52
46 chapter 3: system administration username enter a username. Password enter a password. Password confirm reenter the chosen password raid id id of current raid volume. Lun allocation two modes can be choose from: thin-provision: iscsi thin-provisioning shares the available physical capacity to mul...
Page 53
47 chapter 3: system administration modify your settings. Press ok to change. 2. Expand volume • the iscsi volume is now able to expand its capacity from unused space (instant allocation mode only). From the volume list, simply select the iscsi volume you like to expand and click the expand button:.
Page 54
48 chapter 3: system administration you will then see the dialog box displayed below. Drag the expand capacity bar to the size you want. Then press expand to confirm the operation. Delete volume • to delete volume on the current raid volume, follow the steps below: under the volume allocation list, ...
Page 55
49 chapter 3: system administration press yes. All data in the volume will be removed. 2. Iscsi thin-provisioning • if iscsi thin-provisioning is selected when creating an iscsi target volume, virtual memory is as- iscsi target volume, virtual memory is as- virtual memory is as- signed to the target...
Page 56
50 chapter 3: system administration from the lun acl setting screen click “add”: next, input “initiator iqn” and setup iscsi target volume access privileges from the available list. Apply by clicking the ok button. The accessible initiator will be listed as shown in the screen shot displayed below..
Page 57
51 chapter 3: system administration the listed “initiator iqn” can be modified or deleted by selecting the desired iqn and pressing modify or delete. Advance option • there are 3 available options for the user to operate thecus ip storage associated with iscsi setting. The details are listed in the ...
Page 58: File Sharing/privilege
52 chapter 3: system administration error recovery level the error recovery level (erl) is negotiated during a leading iscsi connection login in traditional iscsi (rfc 3720) and iser (rfc 5046). Erl=0: session recovery erl=0 (session recovery) is triggered when failures within a command, within a co...
Page 59
53 chapter 3: system administration item description work group / domain name specifies the smb/cifs work group / ads domain name (e.G. Mygroup). Ads support select disable to disable authentication through windows active directory server. Ads server name specifies the ads server name (e.G. Adserver...
Page 60
54 chapter 3: system administration local user configuration item description add press the add button to add a user to the list of local users. Edit press the edit button to modify a local user. Remove press the remove button to delete a selected user from the system. Add users • click on the add b...
Page 61
55 chapter 3: system administration edit users • select an existing user from the local user configuration screen. 1. Click on the edit button, and the local user setting screen appears. 2. From here, you can enter a new password and re-enter to confirm, or use the > but- 3. Tons to have this user j...
Page 62
56 chapter 3: system administration local group configuration item description add press the add button to add a user to the list of local groups. Edit press the edit button to modify a selected group from the system. Remove press the remove button to delete a selected group from the system. Add gro...
Page 63
57 chapter 3: system administration remove groups • on the local group configuration screen, select a group name from the list. 1. Press remove to delete the group from the system. 2. Batch users and groups creation 3.5.4 the thecus ip storage can also add users and groups in batch mode. This enable...
Page 64
58 chapter 3: system administration share folder 3.5.5 from the file sharing/privilege menu, choose share folders, and the shared folder screen appears. This screen allows you to create and configure folders on the thecus ip storage volume. Adding folders • on the folder screen, press the add button...
Page 65
59 chapter 3: system administration you to change folder information. After entering the information, press apply to save your changes. Modify folder item description folder name enter the name of the folder. Public admit or deny public access to this folder. Apply press apply to create the folder. ...
Page 66
60 chapter 3: system administration nfs share (n4520/n4560 only) • to allow nfs access to the share folder, enable the nfs service, and then set up hosts with access rights by clicking add. Nfs share item description hostname enter the name or ip address of the host privilege host has either read on...
Page 67
61 chapter 3: system administration samba configuration • on the folder screen, press the samba button and the samba configuration screen appears. This screen allows you to setup samba configuration for associated folder. After entering the information, press apply to activate input settings. Samba ...
Page 68
62 chapter 3: system administration acl setting item description deny denies access to users or groups who are displayed in this column. Read only provides read only access to users or groups who are displayed in this column. Writable provides write access to users or groups who are displayed in thi...
Page 69
63 chapter 3: system administration the acl can only be set for share and sub folders level, not for files. The acl screen also allows you to search for a particular user. To do this, follow the steps below: in the blank, enter the name of the user you would like to find. 1. From the drop down selec...
Page 70
64 chapter 3: system administration user and group backup 3.5.7 the user and group backup feature allow system users and groups to be backed up to another location and be restored if needed. Please note, when restoring previous backup users and groups, the current users and groups list will be repla...
Page 71
65 chapter 3: system administration a description of each item follows: ldap support item description ldap service enable or disable ldap service. Ldap server ip input ldap server ip address. Base domain input base domain information ex. Dc=tuned, dc=com, dc=tw manager input manager’s name. Password...
Page 72: Network Service
66 chapter 3: system administration network service 3.6 use the network service menu to make network service support settings. Samba / cifs 3.6.1 there are options allow admin to enable/disable to operate thecus ip storage associated with samba / cifs protocol. With the option changed, it will need ...
Page 73
67 chapter 3: system administration simply enable the “recycle bin” function and “recycle folder display” then all of deleted files/folders will reside in the “_nas_recycle_(associated rdid volume)” share folder. For example, the system has created 2 raid volumes with id “raidpm” and ‘raid”. Then it...
Page 74
68 chapter 3: system administration afp (apple network setup) 3.6.2 from the system network menu, choose the afp item, and the afp support screen appears. This screen displays the configuration items for the apple filing protocol. You can change any of these items and press apply to confirm your set...
Page 75
69 chapter 3: system administration nfs setup (n4520/n4560 only) 3.6.3 from the system network menu, choose the nfs item, and the nfs support screen appears. The thecus ip storage can act as an nfs server, enabling users to download and upload files with their favorite nfs clients. Press apply to co...
Page 76
70 chapter 3: system administration allow anonymous ftp access upload/download: allow anonymous ftp users to upload or download files to/from public folders. Download: allow anonymous ftp users to download files from public folders. No access: block anonymous ftp user access. Auto rename if checked,...
Page 77
71 chapter 3: system administration a description of each item follows: web service item description http (webdisk) support enable or disable webdisk support. Enter the port number if this option is enabled. The port number is default 80. Https (secure webdisk) support enable or disable secure webdi...
Page 78
72 chapter 3: system administration ssh 3.6.9 the device is now ssh protocol supported. It allows user to use ssh and have console to manipulate as needed. The ssh default login user name is “root” with full privilege and password is admin’s pass- needed. The ssh default login user name is “root” wi...
Page 79
73 chapter 3: system administration a description for each item as following: ddns item description ddns service enable or disable ddns service. Register choose the service provider from the drop down list. User name input user name with ddns registry. Password input password with ddns registry. Dom...
Page 80
74 chapter 3: system administration and click “add rule” to add more port mapping from internet to access desired services or press “refresh” to get most updated list. A description for each item as following: upnp port management item description start port specific port number starts with. End por...
Page 81: Application Server
75 chapter 3: system administration application server 3.7 the thecus ip storage supports built-in application such as itunes server as well as add-on official or third -party applications. Itunes® server (built in) 3.7.1 with the built-in itunes server capability, thecus ip storage enables digital ...
Page 82: Backup
76 chapter 3: system administration nas application 3.7.4 click on nas application from the application server category, it will list the current system software and official application status. Backup 3.8 there are a number of ways to back up data with the thecus ip storage. Rsync target server 3.8...
Page 83
77 chapter 3: system administration enable rsync target server 1. Add a username and password (they can be different than your nas’s username and 2. Password) select apply 3. You will need this user name and password while the data is going to remotely backup to this rsync target server. Now rsync i...
Page 84
78 chapter 3: system administration then 3 different selections appear and can be chosen from: remote data backup item description full backup the “full backup” will have all shares from source backup to destination. It could also create shares automatically from destination if it is not existent. T...
Page 85
79 chapter 3: system administration full backup • click on full backup and the setup screen appear as below. Fill in the remote target ip (destination) and port (need to be changed only if this port is already in use). If encryption is required then enable it. Please make sure the associated target ...
Page 86
80 chapter 3: system administration -fill out all the necessary details and choose your parameters add rsync backup task item description task name this is how this task will appear in the task list. Backup type real time: it will backup folders/files from source to target on the fly. On the other h...
Page 87
81 chapter 3: system administration from the task list, you can now see the newly added task “fullback01”. The backup is setup as “real time”. From the status field, “processing” can be read as the back-up is performed on the fly. Custom backup • the custom backup setting is similar to the full back...
Page 88
82 chapter 3: system administration click “next” and more setting appears. These are the as the settings for “full backup” 3. Click “finish” and the data guard task will appear in the list as shown below. 4. From the task list, you can now see the newly added “customback01”. This backup is setup as ...
Page 89
83 chapter 3: system administration iscsi backup • if the source unit contains iscsi volume, it can be backed up to the target unit as a single file. The procedure is the same as for the previous “full backup” and “custom backup”, select “iscsi backup” from data guard wizard. Inputs the share folder...
Page 90
84 chapter 3: system administration 4. Click “finish” and the data guard task will appear in the list as shown below. From the task list, you can now see the newly added “iscsiback”. This backup is setup as “schedule”. The source folder name will use iscsi_+target volume name. So here it is displaye...
Page 91
85 chapter 3: system administration restore nas configuration • this is a useful feature if the system configuration needs to be restored to a brand new unit. Let’s go thru the following example to see how it works. The original source system has 3 raid volume, “raid”, ‘raid10” and “raid20”, and has...
Page 92
86 chapter 3: system administration click “next” and a screen will appear as shown below. It has the listed available system 3. Configuration backup files. Select the one you want and click next. You also have the option to download the current system configuration before restoring from the backup f...
Page 93
87 chapter 3: system administration the backup configuration has different numbers of raid volume than the current system (3 5. Vs 1). It can be kept as the raid volume mapping arranged by the system, then carry on to click “finish”. This means that all 3 raid volumes configuration such as share fol...
Page 94
88 chapter 3: system administration data guard (local backup) 3.8.3 the thecus product provides complete backup solution between thecus nas systems as well as between folders of local systems. Remote data backup item description add add a new task. Edit edit selected task. Remove remove selected tas...
Page 95
89 chapter 3: system administration local data backup item description import this is associated with external devices which are added to the system such as usb disk. You can select a folder from an external device and import it to the nas as a share folder. Copy copy folder to folder or nas folder ...
Page 96
90 chapter 3: system administration imported them to the nas under the raid60volume. Next, please select the path from the drop down list to save the log. Also, give the access permission whether these selected folders will be “public” or not after the import. Read the notes and check the “accept” b...
Page 97
91 chapter 3: system administration now, you will see in the data guard task list that you have created a task . And that the system has created 2 new share folders from the task just created. Copy: click on “copy” and this screen appears. 2. 3 different options can be selected, folder to folder, fo...
Page 98
92 chapter 3: system administration folder to folder • folder to external device • external device to folder •.
Page 99
93 chapter 3: system administration let’s take “folder to external device” as an example. In the source pane, select the desired raid volume and its associated folder list will appear; same method in the target pane for the associated external device. Select a folder from the source pane which is go...
Page 100
94 chapter 3: system administration read the notes and check the “accept” box for confirmation. Now, you will see in the data guard task list that you have created a task. Realtime backup: click on “realtime backup” and this screen will appear. 3. 2 different options can be selected from, folder to ...
Page 101
95 chapter 3: system administration next, fill in the task name and related settings..
Page 102
96 chapter 3: system administration realtime backup item description task name input the task name, length limited to 4~12 characters. Sync type select “incremental” or “synchronize”. Backup symbolic link choose to backup symbolic link which is included in the source. Filter the filter can be set to...
Page 103
97 chapter 3: system administration schedule backup: click on “schedule backup” and this screen will. 2 different choices can be 4. Selected from, folder to folder, folder to external device. Let’s use “folder to external device” backup for our example. From the nas volume raid in the source pane se...
Page 104
98 chapter 3: system administration read the notes and check the “accept” box for confirmation. Now, you will see in the data guard task list that you have created a task. Iscsi backup: click on “iscsi backup” and screen appear as below. 5. It can be backup to two different storage pool, iscsi to fo...
Page 105
99 chapter 3: system administration let’s take example to have “iscsi to folder” backup, from existed iscsi volume “iscsi_iscsiv502” to volume raid folder “andy_local”. The source pane listed “iscsi_iscsiv502” and “iscsi_iscsiv50” where are iscsi volume has existed in this system with name “iscsi_+i...
Page 106
100 chapter 3: system administration task list will have created task listed. To start the iscsi volume backup, select the task and click “start” from task bar. Once “start” click, the associated iscsi volume will not allow to i/o during backup processing. And the task status will change to ‘process...
Page 107
101 chapter 3: system administration iscsi import: click on “iscsi import” and screen appear as below. 6. It can be imported from two different storage pools, folder to iscsi or external device to iscsi. It is depend on where iscsi volume has backup to. Let’s take example to import “raid folder to i...
Page 108
102 chapter 3: system administration next, provide where the task log will store. Reading the note and check on “accept” for confirmation. Now, from the data guard task list will have created task listed. Acl backup and restore 3.8.4 the acl backup and restore feature enables the system acl (access ...
Page 109
103 chapter 3: system administration for the acl restore, it can be restored in the same system or used in another unit. For example, let’s restore the acl backup file to another unit. This unit has a raid volume “raidpm” with share folders as listed on right hand screen shot. After inputting the ac...
Page 110
104 chapter 3: system administration data burn 3.8.5 the data burn is featured to support 3 different modes of data burning for files/folders to and from image file and physical optical disk. The 3 different modes are “write files/folders to disc”, “write image to disk” and “write files/folders to i...
Page 111
105 chapter 3: system administration select from the installed usb burning devices. Please click the “detect disc” button to c. Check the status once the disc is inserted. Select the burning speed from the drop down list. D. Select whether disc data verification is required or not. E. Click “burn” t...
Page 112
106 chapter 3: system administration select the iso file. B. Select from the installed usb burning devices. Please click the “detect disc” button to c. Check the status once the disc is inserted. Select the burning speed from the drop down list. D. Select whether disc data verification is required o...
Page 113: External Devices
107 chapter 3: system administration input the path where the iso file is going to be stored, you can press the “browse” c. Button to have the share list appear. Input the iso file name for burned image file. D. Click “burn” to start the iso file burning. E. The data burn does not support rewriteabl...
Page 114
108 chapter 3: system administration windows xp sp2 • to set up the printer server in windows xp sp2, follow the steps below: connect the usb printer to one of the usb ports (preferably the rear usb ports; front usb 1. Ports can be used for external hdd enclosures). Go to start > printers and faxes....
Page 115
109 chapter 3: system administration select add a network, wireless or bluetooth printer. 3. Select the printer that i want isn’t listed. 4. You can press the printer that i want isn’t listed to go into next page without waiting for searching for available printers to finish. Click select a shared p...
Page 116
110 chapter 3: system administration type http://:631/printers/usb-printer in the box, where is the ip address of thecus ip storage. Click next. Select or install a printer and then press ok. 6. Windows will attempt to connect to the printer. 7. You can choose to set this printer as the default prin...
Page 117
111 chapter 3: system administration done! Click finish. 9..
Page 118
112 chapter 3: system administration uninterrupted power source 3.9.2 from the external devices menu, choose the uninterrupted power source item and the ups setting screen appears. Make any changes you wish, and press apply to confirm changes. See the following table for a detailed description of ea...
Page 119: Appendix A: Customer Support
113 appendix a: customer support appendix a: customer support if you are still experiencing problems with your thecus ip storage, or require a return merchandise authorization (rma), feel free to contact technical support via our technical support website: http://www.Thecus.Com/sp_tech.Php customers...
Page 120: Appendix B: Raid Basics
114 appendix b: raid basics appendix b: raid basics overview • a redundant array of independent disks (raid) is an array of several hard disks that provide data security and high performance. A raid system accesses several hard disks simultaneously, which improves i/o performance over a single hard ...
Page 121
115 appendix b: raid basics raid 5 raid 5 offers data security and it is best suited for networks that perform many small i/o transactions at the same time, as well as applications that require data security such as office automation and on- line customer service. Use it also for applications with h...
Page 122
116 appendix b: raid basics listed below: raid level percentage used raid 0 100% raid 1 1/n x 100% raid 5 (n-1)/n x 100% raid 6 (n-2)/n x 100% raid 10 50% jbod 100% n: hdd number.
Page 123
117 appendix c: active directory basics appendix c: active directory basics overview • with windows 2000, microsoft introduced active directory (ads), which is a large database/ information store. Prior to active directory the windows os could not store additional information in its domain database....
Page 124
118 appendix d: licensing information appendix d: licensing information overview • this product included copyrighted third-party software licensed under the terms of gnu general public license. Please see the gnu general public license for extra terms and conditions of this license. Source code avai...
Page 125
119 appendix d: licensing information cgic license terms • basic license cgic, copyright 1996, 1997, 1998, 1999, 2000, 2001, 2002, 2003, 2004 by thomas boutell and boutell. Com, inc. Permission is granted to use cgic in any application, commercial or noncommercial, at no cost. However, this copyrigh...
Page 126
120 appendix d: licensing information the recipients all the rights that you have. You must make sure that they, too, receive or can get the source code. And you must show them these terms so they know their rights. We protect your rights with two steps: (1) copyright the software, and (2) offer you...
Page 127
121 appendix d: licensing information warranty protection in exchange for a fee. 2. You may modify your copy or copies of the program or any portion of it, thus forming a work based on the program, and copy and distribute such modifications or work under the terms of sec- tion 1 above, provided that...
Page 128
122 appendix d: licensing information ware interchange; or, b) accompany it with a written offer, valid for at least three years, to give any third party, for a charge no more than your cost of physically performing source distribution, a complete machine- readable copy of the corresponding source c...
Page 129
123 appendix d: licensing information 7. If, as a consequence of a court judgment or allegation of patent infringement or for any other reason (not limited to patent issues), conditions are imposed on you (whether by court order, agree- ment or otherwise) that contradict the conditions of this licen...
Page 130
124 appendix d: licensing information rivatives of our free software and of promoting the sharing and reuse of software generally. No warranty 11. Because the program is licensed free of charge, there is no warranty for the program, to the extent permitted by applicable law. Except when otherwise st...