- DL manuals
- Vasco
- Gateway
- Personal aXsGUARD
- Installation And Configuration Manual
Vasco Personal aXsGUARD Installation And Configuration Manual
Summary of Personal aXsGUARD
Page 1
Personal axsguard installation and configuration guide 7.7.1.
Page 2: Table of Contents
Personal axsguard - 7.7.1 © vasco data security 2013 ii table of contents 1. Introduction ...................................................................................................................... 1 1.1. About his document ....................................................................
Page 3
Personal axsguard - 7.7.1 © vasco data security 2013 iii 4.10.2. Automated nat ......................................................................................... 20 4.10.3. Dnat and port forwarding .......................................................................... 20 4.10.4. Snat and ...
Page 4
Personal axsguard - 7.7.1 © vasco data security 2013 iv vasco products vasco data security, inc. And/or vasco data security international gmbh are referred to in this document as ‘vasco’. Vasco products comprise hardware, software, services and documentation. This document addresses potential and ex...
Page 5: Chapter 1. Introduction
Personal axsguard - 7.7.1 © vasco data security 2013 1 chapter 1. Introduction 1.1. About his document • this document has been written for axsguard gatekeeper version 7.7.1 and is based on changes and features that have been implemented since version 7.7.0. • this document was last updated on 22 no...
Page 6
Personal axsguard - 7.7.1 chapter 1. Introduction © vasco data security 2013 2 • axsguard gatekeeper firewall • axsguard gatekeeper single sign-on • axsguard gatekeeper vpn • axsguard gatekeeper reverse proxy • axsguard gatekeeper directory services access to axsguard gatekeeper guides is provided t...
Page 7
Personal axsguard - 7.7.1 chapter 1. Introduction © vasco data security 2013 3 a new license. If a new license has not been issued after this grace period, all services on the appliance will be stopped. Only the administrator tool will remain accessible. Contact vasco support ( support@vasco.Com ) t...
Page 8: Chapter 2. Before You Begin
Personal axsguard - 7.7.1 © vasco data security 2013 4 chapter 2. Before you begin 2.1. Pax models there are two hardware models: • the ag-1296: this model is still supported, but has been discontinued. Please see prior documentation for reference. • the ag-1497: see section 2.3, “hardware and envir...
Page 9
Personal axsguard - 7.7.1 chapter 2. Before you begin © vasco data security 2013 5 hardware features dimensions (w x d x h) 9.6x6.4x1.3 in.(243x160.6x32.5mm) antenna 3 external detachable dual band antennas (rp-sma) wireless features wireless standards ieee 802.11a, ieee 802.11b, ieee 802.11g, ieee ...
Page 10
Personal axsguard - 7.7.1 © vasco data security 2013 6 chapter 3. Features and concepts 3.1. Documentation you may need the concepts mentioned in this guide, i.E. Certificates, ip address ranges, dhcp, nat, routing, dns and firewall settings, are fully explained in separate guides which can be acces...
Page 11
Personal axsguard - 7.7.1 chapter 3. Features and concepts © vasco data security 2013 7 • pax network settings, such as routing, nat and dns servers. • pax dhcp server settings. • wireless access settings, in case you are connecting to the pax from a pc equipped with a wireless network device. • fir...
Page 12
Personal axsguard - 7.7.1 chapter 3. Features and concepts © vasco data security 2013 8 should be connected to the pax. A secure option is to connect the internet interface of the pax to the user’s lan and only connect the client computers that actually need access to corporate resources to the pax ...
Page 13
Personal axsguard - 7.7.1 chapter 3. Features and concepts © vasco data security 2013 9 with the option enabled (see section 4.6, “network settings” ), hosts in the nat’d network connected to the pax’s wan interface can connect seamlessly to machines in the pax’s lan, as if they were a part of the s...
Page 14
Personal axsguard - 7.7.1 chapter 3. Features and concepts © vasco data security 2013 10 figure 3.4. Snat and masquerading 3.5. Vpn failover in computing, failover is the capability to switch over automatically to a redundant or secondary computer server, system, or a network upon the failure or abn...
Page 15
Personal axsguard - 7.7.1 chapter 3. Features and concepts © vasco data security 2013 11 will first try to establish a tcp connection with the same server, before it switches to the second server. If a connection is made to the second server, udp will be attempted first. In case a specific vpn proto...
Page 16
Personal axsguard - 7.7.1 chapter 3. Features and concepts © vasco data security 2013 12 3.8. Remote administration 3.8.1. Https the pax is administered via a web-based administration tool. Http is the default protocol, but you also have the option to switch to https. The benefit of https is that an...
Page 17
Personal axsguard - 7.7.1 © vasco data security 2013 13 chapter 4. Server-side configuration 4.1. Overview in this chapter, we explain how to configure the corporate axsguard gatekeeper vpn server, so that a pax can download its settings and establish a vpn connection. The configuration steps must b...
Page 18
Personal axsguard - 7.7.1 chapter 4. Server-side configuration © vasco data security 2013 14 4.4. Client options any pax in the field must be configured on the axsguard gatekeeper vpn server before it can be used to successfully establish a vpn connection (see section 3.2, “central management and pk...
Page 19
Personal axsguard - 7.7.1 chapter 4. Server-side configuration © vasco data security 2013 15 parameter description hardware model select the model that applies to you. Enable dhcp server check this option to enable the dhcp server on the pax unit. If enabled, the pax will assign ip addresses to its ...
Page 20
Personal axsguard - 7.7.1 chapter 4. Server-side configuration © vasco data security 2013 16 figure 4.3. Pax network settings parameter description remote lan ip – address netmask this is the lan ip address and subnet mask to be assigned to the pax. Use the cidr notation, e.G. 10.0.0.1/24 . Use the ...
Page 21
Personal axsguard - 7.7.1 chapter 4. Server-side configuration © vasco data security 2013 17 when the vpn tunnel is down, the client will use its isp’s dns server(s). 4.7. Dhcp settings in this section, we provide a table explaining the dhcp settings of the pax (the dhcp tab). Via this tab you can c...
Page 22
Personal axsguard - 7.7.1 chapter 4. Server-side configuration © vasco data security 2013 18 figure 4.5. Pax wireless settings parameter description enable check to enable the radio signal of the desired frequency. The frequency of 5 ghz is only supported by the ag-1497. Channel select the desired w...
Page 23
Personal axsguard - 7.7.1 chapter 4. Server-side configuration © vasco data security 2013 19 “security recommendations” ). Use the add policy button to select a firewall policy. The difference between regular and tunnel firewall policies is explained in the table below. Figure 4.6. Pax firewall conf...
Page 24
Personal axsguard - 7.7.1 chapter 4. Server-side configuration © vasco data security 2013 20 figure 4.7. Activating nat 4.10.2. Automated nat in this section, we explain how to enable upnp and nat-pmp (see section 3.4.2, “upnp and nat-pmp” ). These options are only available if you checked "activate...
Page 25
Personal axsguard - 7.7.1 chapter 4. Server-side configuration © vasco data security 2013 21 parameter description description a description for the new nat rule, e.G. Mail. Source ip specify the source ip address (range) to which the port forwarding rule must be applied. Use the cidr notation to sp...
Page 26
Personal axsguard - 7.7.1 chapter 4. Server-side configuration © vasco data security 2013 22 parameter description destination ip specify the destination ip address or network for which snat must be performed. Use the cidr notation to specify a network, e.G. 192.168.0.1/24. If left empty, the rule a...
Page 27
Personal axsguard - 7.7.1 © vasco data security 2013 23 chapter 5. Client-side configuration 5.1. Overview in this chapter, we explain how to configure your pax, once the server-side configuration has been completed (see chapter 4, server-side configuration ). Topics covered in this chapter include:...
Page 28
Personal axsguard - 7.7.1 chapter 5. Client-side configuration © vasco data security 2013 24 • choose a complex user password and keep it secret if you want to prevent users from rebooting the pax or controlling the vpn tunnel (see section 4.5, “general settings” ). • the default passwords (see tabl...
Page 29
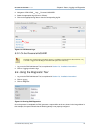
Personal axsguard - 7.7.1 chapter 5. Client-side configuration © vasco data security 2013 25 figure 5.2. Internet connection and ntp settings parameter description network time server the ip address or fqdn of an internet time server. Internet type select the appropriate method to connect to the int...
Page 30
Personal axsguard - 7.7.1 chapter 5. Client-side configuration © vasco data security 2013 26 figure 5.3. Pax status overview the vpn tunnel will start automatically after importing the pax certificate (pkcs12). Rebooting is allowed, but not required. The pax automatically checks whether a valid clie...
Page 31: Diagnostics
Personal axsguard - 7.7.1 © vasco data security 2013 27 chapter 6. Status, logging and diagnostics 6.1. Overview in this chapter, we explain how to: • check the pax connection status and logs (remotely and locally) • use the diagnostic tool for troubleshooting • initiate a remote support connection ...
Page 32
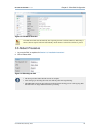
Personal axsguard - 7.7.1 chapter 6. Status, logging and diagnostics © vasco data security 2013 28 2. Navigate to vpn & ras ⇒ logs ⇒ personal axsguard. 3. Select the appropriate logs (server or clients). 4. Click on the appropriate log date to view the corresponding log file. Figure 6.2. Pax access ...
Page 33
Personal axsguard - 7.7.1 chapter 6. Status, logging and diagnostics © vasco data security 2013 29 figure 6.4. Example of a pax diagnostics result if your vpn tunnel disconnects and reconnects frequently, check the load averages in the status screen. If the load is persistently high, try rebooting t...
Page 34: Chapter 7. Troubleshooting
Personal axsguard - 7.7.1 © vasco data security 2013 30 chapter 7. Troubleshooting the pax cannot establish a vpn connection to the corporate axsguard gatekeeper. • ensure that traffic towards port 1194 is allowed on the internet interface of the corporate axsguard gatekeeper for the selected vpn pr...
Page 35: Chapter 8. Support
Personal axsguard - 7.7.1 © vasco data security 2013 31 chapter 8. Support 8.1. Overview in this section we provide instructions on what to do if you have a problem, or experience a hardware failure. 8.2. If you encounter a problem if you encounter a problem with a vasco product, follow the steps be...
Page 36
Personal axsguard - 7.7.1 © vasco data security 2013 xxxii list of figures 2.1. Ag-1296 front and back panel .......................................................................................... 4 2.2. Ag-1497 front and back panel ...................................................................
Page 37
Personal axsguard - 7.7.1 © vasco data security 2013 xxxiii list of tables 4.1. Pax client settings ........................................................................................................ 14 4.2. Client settings - general tab ............................................................
Page 38
Personal axsguard - 7.7.1 © vasco data security 2013 xxxiv list of examples 3.1. Maintenance of master in ha cluster .................................................................................. 11 3.2. Selecting udp as the vpn protocol .............................................................
Page 39: Alphabetical Index
Alphabetical index a aes, 11 axsguard gatekeeper, 2 c ca, 6 certificate authority, 6 d dhcp, 17 digital certificate, 6 documentation, 1 f failover, 10 firewall, 7 fwd-access-lan, 7, 18 l licensed appliance, 3 logging, 27 m masquerading, 21 n nat, 8, 21 nat port mapping, 8 nat-pmp, 8 network address ...