- DL manuals
- Watchguard
- Network Router
- Firebox X10E
- User Manual
Watchguard Firebox X10E User Manual
Summary of Firebox X10E
Page 1
Watchguard ® firebox ® system user guide watchguard firebox system.
Page 2
Ii watchguard firebox system notice to users information in this guide is subject to change without notice. Companies, names, and data used in examples herein are fictitious unless otherwise noted. No part of this guide may be reproduced or transmitted in any form or by any means, electronic or mech...
Page 3
User guide iii 1. Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer. 2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or...
Page 4
Iv watchguard firebox system copyright remains eric young's, and as such any copyright notices in the code are not to be removed. If this package is used in a product, eric young should be given attribution as the author of the parts of the library used. This can be in the form of a textual message ...
Page 5
User guide v 2. Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/ or other materials provided with the distribution. 3. All advertising materials mentioning features or use of this software must di...
Page 6
Vi watchguard firebox system 4. The names "apache" and "apache software foundation" must not be used to endorse or promote products derived from this software without prior written permission. For written permission, please contact apache@apache.Org. 5. Products derived from this software may not be...
Page 7
User guide vii somewhere reasonably visible in your documentation and in any relevant files or online help data or similar. A reference to the ftp site for the source, that is, to: ftp://ftp.Csx.Cam.Ac.Uk/pub/software/programming/pcre/ should also be given in the documentation. However, this conditi...
Page 8
Viii watchguard firebox system product for a full refund of the price you paid. The watchguard hardware product is subject to a separate agreement and limited hardware warranty included with the watchguard hardware product packaging and/or in the associated user documentation. 1. Ownership and licen...
Page 9
User guide ix (b) use any backup or archival copy of the software product (or allow someone else to use such a copy) for any purpose other than to replace the original copy in the event it is destroyed or becomes defective; (c) sublicense, lend, lease or rent the software product; (d) transfer this ...
Page 10
X watchguard firebox system active, passive or imputed) or fault of watchguard and its licensors and any obligation, liability, right, claim or remedy for loss or damage to, or caused by or contributed to by, the software product). Limitation of liability. Watchguard's liability (whether in contract...
Page 11
User guide xi 8.Miscellaneous provisions. This agreement will be governed by and construed in accordance with the substantive laws of washington excluding the 1980 united national convention on contracts for the international sale of goods, as amended. This is the entire agreement between us relatin...
Page 12
Xii watchguard firebox system.
Page 13
User guide xiii contents chapter 1 introduction ................................................1 welcome to watchguard® ...............................................1 watchguard firebox system components .........................2 watchguard firebox ..................................................
Page 14
Xiv watchguard firebox system chapter 2 service and support .................................. 9 benefits of livesecurity® service ...................................... 9 livesecurity® broadcasts ............................................... 10 activating the livesecurity® service ..................
Page 15
User guide xv testing the connection .................................................42 entering ip addresses ...................................................43 deploying the firebox into your network ........................44 what’s next ...........................................................
Page 16
Xvi watchguard firebox system defining a firebox as a dhcp server .............................. 66 adding a new subnet .................................................. 67 modifying an existing subnet ........................................ 68 removing a subnet ......................................
Page 17
User guide xvii controlling the hostwatch display ..................................99 modifying hostwatch view properties ...........................100 chapter 7 configuring network address translation ...............................................101 dynamic nat ....................................
Page 18
Xviii watchguard firebox system chapter 9 configuring proxied services ............... 135 protocol anomaly detection ......................................... 136 customizing logging and notification for proxies .......... 137 configuring an smtp proxy service .............................. 137 con...
Page 19
User guide xix detecting man-in-the-middle attacks ............................183 blocking sites ..............................................................184 blocking a site permanently .........................................185 creating exceptions to the blocked sites list ....................
Page 20
Xx watchguard firebox system setting the log encryption key ..................................... 211 setting global logging and notification preferences ..... 211 log file size and rollover frequency .............................. 212 setting the interval for log rollover .............................
Page 21
User guide xxi deleting a report .......................................................238 viewing the reports list ...............................................238 specifying a report time span .....................................238 specifying report sections .....................................
Page 22
Xxii watchguard firebox system managing the webblocker server ................................. 262 installing multiple webblocker servers .......................... 262 automating webblocker database downloads .............. 262 installing scheduled tasks .......................................... ...
Page 23
User guide 1 chapter 1 introduction welcome to watchguard ® in the past, a connected enterprise needed a complex set of tools, systems, and personnel for access control, authentication, virtual private networking, network management, and security analysis. These costly sys- tems were difficult to in...
Page 24
Chapter 1: introduction 2 watchguard firebox system watchguard firebox system components the watchguard firebox system has all of the components needed to conduct electronic business safely. It is made up of the following: • firebox–a plug-and-play network appliance • firebox system manager–a suite ...
Page 25
Minimum requirements user guide 3 historical reports creates html reports that display session types, most active hosts, most used services, urls, and other data useful in monitoring and troubleshooting your network. Watchguard security applications in addition to basic security policy configuration...
Page 26
Chapter 1: introduction 4 watchguard firebox system windows nt requirements • microsoft windows nt 4.0 • microsoft service pack 4, service pack 5, or service pack 6a for windows nt 4.0 windows 2000 requirements • microsoft windows 2000 professional or windows 2000 server windows xp requirements • mi...
Page 27
Watchguard options user guide 5 . Watchguard options the watchguard firebox system is enhanced by optional features designed to accommodate the needs of different customer environments and security requirements. The following options are currently available for the watchguard firebox system. Vpn man...
Page 28
Chapter 1: introduction 6 watchguard firebox system headquarters, branch offices, telecommuters, and remote users. Vpn manager is bundled with the wfs software, but it is available for use only if you select the vpn manager checkbox when installing wfs and enter your license key. N ote the firebox m...
Page 29
About this guide user guide 7 allowed to enter your network unchecked, spam consumes workers’ time to read and remove. Watchguard spam- screen identifies spam as it comes through the firebox. You can choose to either block the spam at the firebox or tag it for easy identification and sorting. Spamsc...
Page 30
Chapter 1: introduction 8 watchguard firebox system must have a current subscription to the livesecurity ser- vice. The following conventions are used in this guide: • within procedures, visual elements of the user interface, such as buttons, menu items, dialog boxes, fields, and tabs, appear in bol...
Page 31
User guide 9 chapter 2 service and support no internet security solution is complete without sys- tematic updates and security intelligence. From the latest hacker techniques to the most recently discov- ered operating system bug, the daily barrage of new threats poses a perpetual challenge to any n...
Page 32
Chapter 2: service and support 10 watchguard firebox system group of network security experts, helps absorb this bur- den by monitoring the internet security landscape for you in order to identify new threats as they emerge. Threat alerts and expert advice after a new threat is identified, you’ll re...
Page 33
Livesecurity® broadcasts user guide 11 divided into channels to help you immediately recognize and process incoming information. Information alert information alerts provide timely analysis of breaking news and current issues in internet security combined with the proper system configuration recomme...
Page 34
Chapter 2: service and support 12 watchguard firebox system virus alert in cooperation with mcafee, watchguard issues weekly broadcasts that provide the latest information on new computer viruses. New from watchguard to keep you abreast of new features, product upgrades, and upcoming programs, watch...
Page 35
Livesecurity® self help tools user guide 13 3 complete the livesecurity activation form. Move through the fields on the form using either the tab key or the mouse. All of the fields are required for successful registration. The profile information helps watchguard target information and updates to y...
Page 36
Chapter 2: service and support 14 watchguard firebox system components of watchguard products. These courses are modular in design, allowing you to use them in a manner most suitable to your learning objectives. For more information, go to: www.Watchguard.Com/training/courses_online.Asp learn about ...
Page 37
Watchguard users group user guide 15 guard technical support directly by way of the web inter- face or telephone. Joining the watchguard users forum to join the watchguard users forum: 1 go to www.Watchguard.Com. Click support. Log into the livesecurity service. 2 under self-help tools, click intera...
Page 38
Chapter 2: service and support 16 watchguard firebox system firebox system software in a subdirectory of the installa- tion directory called help . In addition, a “live,” continu- ally updated version of online help is available at: http://help.Watchguard.Com/lss/70 you may need to log into the live...
Page 39
Online help user guide 17 to display a list of topics containing the word. The search feature does not support boolean searches. Copying the help system to additional platforms watchguard online help can be copied from the manage- ment station to additional workstations and platforms. When doing so,...
Page 40
Chapter 2: service and support 18 watchguard firebox system 3 to print or save the help box as a separate file, right- click the help field. A menu offering copy or print appears. 4 select the menu item you want. 5 when you are done, click anywhere outside the box to dismiss it. You can also look up...
Page 41
Assisted support user guide 19 to assist you in maintaining your enterprise security sys- tem involving our firebox, soho 6, serverlock, applock, and vpn products. Hours watchguard livesecurity technical support business hours are 4:00 am to 7:00 pm pacific time (gmt - 7), monday through friday. The...
Page 42
Chapter 2: service and support 20 watchguard firebox system — 7), and can help you with any technical issues you might have during these hours. We target a one-hour maximum response time for all new incoming cases. If a technician is not immediately available to help you, a support administrator wil...
Page 43
Training and certification user guide 21 to speed on network security issues and our award-win- ning product line, you will learn exactly what you need to do to protect valuable information assets and make the most of your watchguard products. No matter where you are located or which products you ow...
Page 44
Chapter 2: service and support 22 watchguard firebox system.
Page 45
User guide 23 chapter 3 getting started the watchguard firebox system acts as a barrier between your networks and the public internet, pro- tecting them from security threats. This chapter explains how to install the watchguard firebox sys- tem into your network. You must complete the follow- ing st...
Page 46
Chapter 3: getting started 24 watchguard firebox system before installing the watchguard firebox system, check the package contents to make sure you have the following items: • watchguard firebox security appliance • quickstart guide • user documentation • watchguard firebox system cd-rom • a serial...
Page 47
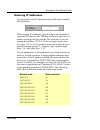
Gathering network information user guide 25 network addresses one good way to set up your network is to create two worksheets: the first worksheet represents your network now–before deploying the firebox–and the second rep- resents your network after the firebox is deployed. Fill in the ip addresses...
Page 48
Chapter 3: getting started 26 watchguard firebox system an example of a network before the firebox is installed appears in the following figure. In this example, the inter- net router performs network address translation (nat) for the internal network. The router has a public ip address of 208.15.15...
Page 49
Gathering network information user guide 27 . The following figure shows the same example network with a firebox deployed. The ip address of the internet router in the previous figure becomes the ip address of the firebox’s default gateway. This network uses drop-in con- figuration because the publi...
Page 50
Chapter 3: getting started 28 watchguard firebox system 192.168.10.1/24. This ip address then becomes the default gateway for devices on the local lan. Selecting a firewall configuration mode before installing the watchguard firebox system, you must decide how to incorporate the firebox into your ne...
Page 51
Selecting a firewall configuration mode user guide 29 trusted interface connects to the private lan or internal network that you want protected. Optional interface connects to the dmz (demilitarized zone) or mixed trust area of your network. Computers on the optional interface contain content you do...
Page 52
Chapter 3: getting started 30 watchguard firebox system characteristics of a routed configuration: • all interfaces of the firebox must be on different networks. The minimum setup involves the external and trusted interfaces. • the trusted and optional interfaces must be on separate networks and all...
Page 53
Selecting a firewall configuration mode user guide 31 address space across the firebox interfaces, you can “drop” the firebox between the router and the lan without reconfiguring any local machines. Public servers behind the firebox use public addresses, and traffic is routed through the firebox wit...
Page 54
Chapter 3: getting started 32 watchguard firebox system • all trusted computers must have their arp caches flushed. • the majority of a lan resides on the trusted interface by creating a secondary network for the lan. The benefit of a drop-in configuration is that you don’t have to reconfigure machi...
Page 55
Selecting a firewall configuration mode user guide 33 adding secondary networks to your configuration whether you have chosen routed or drop-in, your configu- ration may require that you add secondary networks to any of the three firebox interfaces. A secondary network is a separate network connecte...
Page 56
Chapter 3: getting started 34 watchguard firebox system when you add a secondary network, you map an ip address from the secondary network to the ip address of the firebox interface. This is known as creating (or adding) an ip alias to the network interface. This ip alias becomes the default gateway...
Page 57
Selecting a firewall configuration mode user guide 35 • after you have finished with the installation, you can add secondary networks to any interface using policy manager, as described in “adding secondary networks” on page 64. Dynamic ip support on the external interface if you are supporting dyna...
Page 58
Chapter 3: getting started 36 watchguard firebox system • enabling the firebox as a dvcp server • bovpn using basic dvcp (not supported on firebox 500 unless you purchase the bovpn upgrade) • muvpn • ruvpn with pptp regardless of whether the ip settings are stable, 1-to-1 nat and external aliases ar...
Page 59
Setting up the management station user guide 37 4 download the watchguard firebox system software. Download time will vary depending on your connection speed. Make sure you write down the name and path of the file as you save it to your hard drive! 5 execute the file you downloaded and follow the sc...
Page 60
Chapter 3: getting started 38 watchguard firebox system high encryption software is governed by strict export restrictions and may not be available for download. For more information, see the online support resources at: https://support.Watchguard.Com/advancedfaqs/ bovpn_ipsecgrey.Asp (you may be pr...
Page 61
Cabling the firebox user guide 39.
Page 62
Chapter 3: getting started 40 watchguard firebox system using tcp/ip refer to firebox rear panel image on the previous page. • use the red (crossover) cable to connect the firebox trusted interface to the management station ethernet port. • plug the power cord into the firebox power input and into a...
Page 63
Running the quicksetup wizard user guide 41 provide the information as prompted by the quicksetup wizard, referring to the tables and network diagrams in “gathering network information” on page 24. The quicksetup wizard takes you through the following steps: select a configuration mode specify wheth...
Page 64
Chapter 3: getting started 42 watchguard firebox system the ip address of any public servers on your network. Firebox name (dhcp or pppoe only.) specify the name used for logging and identification of a dynamic firebox. All characters are allowed except blank spaces and forward or back slashes (/ or...
Page 65
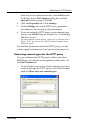
Running the quicksetup wizard user guide 43 entering ip addresses you generally enter ip addresses into fields that resemble the one below. When typing ip addresses, type the digits and periods in sequence. Do not use the tab key, arrow key, spacebar, or mouse to jump past the periods. For example, ...
Page 66
Chapter 3: getting started 44 watchguard firebox system deploying the firebox into your network congratulations! You have completed the installation of your firebox. The firebox can now be used as a basic fire- wall with the following properties: • all outgoing traffic is allowed. • all incoming tra...
Page 67
What’s next user guide 45 services, in addition to the basic ones described in the pre- vious section, that expand what you allow in and out of your firewall. Every service brings trade-offs between network security and accessibility. When selecting services, balance the needs of your organization w...
Page 68
Chapter 3: getting started 46 watchguard firebox system.
Page 69
User guide 47 chapter 4 firebox basics this chapter describes the basic tasks you perform to set up and maintain a firebox: • opening a configuration file • saving a configuration file to a local computer or the firebox • resetting firebox passphrases • setting the firebox time zone • setting a fire...
Page 70
Chapter 4: firebox basics 48 watchguard firebox system n ote there are no user-serviceable parts within the firebox. If a user opens a firebox case, it voids the limited hardware warranty. The most common and effective location for a firebox is directly behind the internet router, as pictured below:...
Page 71
Opening a configuration file user guide 49 trusted network the network behind the firewall that must be protected from the security challenge. External network the network presenting the security challenge, typically the internet. Optional network a network protected by the firewall but still access...
Page 72
Chapter 4: firebox basics 50 watchguard firebox system 4 from the firebox manager, click the policy manager icon (shown at right). You can now either open a configuration from the firebox or from the local hard disk, as explained in the next two sections. Opening a configuration from the firebox fro...
Page 73
Saving a configuration file user guide 51 3 from the new firebox configuration dialog box, select the model of firebox you are connected to. The new configuration file contains defaults for the model of firebox specified. Saving a configuration file after making changes to a configuration file, you ...
Page 74
Chapter 4: firebox basics 52 watchguard firebox system 4 if you entered the ip address of a different firebox, you are asked to confirm your choice. Click yes. The firebox flash disk dialog box, as shown in the following figure, appears. 5 select the checkbox marked save to firebox. If you want to m...
Page 75
Resetting firebox passphrases user guide 53 enter the encryption key for the firebox. In the confirm field, reenter it to confirm. 7 if you are making a backup, in the backup image field, enter the path where you want to save the backup of the current flash image. Click continue. Instead of entering...
Page 76
Chapter 4: firebox basics 54 watchguard firebox system 3 use the firebox drop-down list to select a firebox or enter the firebox ip address. Enter the configuration passphrase. Click ok . The firebox flash disk dialog box appears. 4 select the checkbox marked save to firebox and the radio button mar...
Page 77
Setting the time zone user guide 55 2 select the model of the firebox you are connecting to. The model of the firebox entered appears at the bottom of the policy manager window. Setting the time zone the firebox time zone determines the date and time stamp that appear on logs and that are displayed ...
Page 78
Chapter 4: firebox basics 56 watchguard firebox system.
Page 79
User guide 57 chapter 5 using policy manager to configure your network normally, you incorporate the firebox into your net- work when you run the quicksetup wizard, as described in “running the quicksetup wizard” on page 40. However, you can also create a basic configu- ration file from scratch usin...
Page 80
Chapter 5: using policy manager to configure your network 58 watchguard firebox system starting a new configuration file to start a new configuration file: 1 from system manager, click the policy manager button, shown at right. The policy manager appears. 2 from policy manager, select file => new. 3...
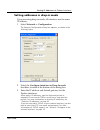
Page 81
Setting ip addresses of firebox interfaces user guide 59 setting addresses in drop-in mode if you are using drop-in mode, all interfaces use the same ip address: 1 select network => configuration. The network configuration dialog box appears, as shown in the following figure. 2 select the configure ...
Page 82
Chapter 5: using policy manager to configure your network 60 watchguard firebox system 4 select the method for obtaining an ip address: static, dhcp, or pppoe. Setting addresses in routed mode if you are using routed mode, the interfaces must use dif- ferent ip addresses. At least two interfaces mus...
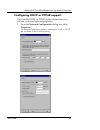
Page 83
Setting dhcp or pppoe support on the external interface user guide 61 configuring dhcp or pppoe support if you enable dhcp or pppoe on the external interface, you can set several optional properties: 1 from the network configuration dialog box, click properties. The advanced dialog box appears, show...
Page 84
Chapter 5: using policy manager to configure your network 62 watchguard firebox system 2 set an initialization timeout in the dhcp initialization timeout field. 3 in the dhcp device name field, assign a name to the device. The name can be any combination of ascii numbers and letters up to 15 charact...
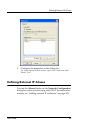
Page 85
Defining external ip aliases user guide 63 2 configure the properties in the dialog box. For a description of each control, right-click it and then select what’s this?. Defining external ip aliases you use the aliases button on the network configuration dialog box when you are using static nat. For ...
Page 86
Chapter 5: using policy manager to configure your network 64 watchguard firebox system adding secondary networks your configuration may require that you add secondary networks to any of the firebox interfaces. For more infor- mation on secondary networks, see “adding secondary networks to your confi...
Page 87
Entering wins and dns server addresses user guide 65 n ote check secondary network addresses carefully. Policy manager does not verify that you have entered the correct address. Watchguard strongly recommends that you do not enter a subnet on one interface that is part of a larger network on another...
Page 88
Chapter 5: using policy manager to configure your network 66 watchguard firebox system configuring out-of-band management you use the oob tab on the network configuration dia- log box to enable the management station to communicate with a firebox by way of a modem (not provided with the firebox) and...
Page 89
Defining a firebox as a dhcp server user guide 67 2 select the enable dhcp server checkbox. 3 enter the default lease time for the server. The default lease time is provided to clients that do not specifically request times. 4 enter the maximum lease time. The maximum lease time is the longest time ...
Page 90
Chapter 5: using policy manager to configure your network 68 watchguard firebox system 3 in the subnet box, type the subnet’s ip address; for example, 10.1.1.0/24. 4 define the address pool by entering values for start and end fields. 5 click ok. Modifying an existing subnet you can modify an existi...
Page 91
Adding basic services to policy manager user guide 69 3 click ok. Adding basic services to policy manager after you have set up ip addressing, add the following ser- vices to policy manager to give your firebox some basic functionality. N ote the watchguard service is particularly important. If you ...
Page 92
Chapter 5: using policy manager to configure your network 70 watchguard firebox system configuring routes a route is the sequence of devices that network traffic takes from its source to its destination. A router is a device within a route that determines the next point to which traf- fic should be ...
Page 93
Configuring routes user guide 71 3 click the net option. 4 enter the network ip address. 5 in the gateway text box, enter the ip address of the router. Be sure to specify an ip address that is on one of the same networks as the firebox. 6 click ok. The setup routes dialog box lists the newly configu...
Page 94
Chapter 5: using policy manager to configure your network 72 watchguard firebox system 7 click ok. The route data is written to the configuration file..
Page 95
User guide 73 chapter 6 managing and monitoring the firebox the watchguard firebox system manager combines access to watchguard firebox system applications and tools in one intuitive interface. System manager also includes a real-time monitor of traffic through the firewall, as well as a number of m...
Page 96
Chapter 6: managing and monitoring the firebox 74 watchguard firebox system explained in the quickstart guide included with your firebox. Otherwise, click continue. The connect to firebox dialog box appears. You can connect to a firebox at this point, or you can cancel the connect to firebox dialog ...
Page 97
Viewing basic firebox status user guide 75 the top part of the display just below the title bar contains several buttons for performing basic operations and launching firebox system applications: open the main menu for system manager. (this is also referred to as the main menu button.) pause the dis...
Page 98
Chapter 6: managing and monitoring the firebox 76 watchguard firebox system the lights on the display represent those found on the front panel of the firebox. The triangle shows the predominant flows of traffic among the trusted, external, and optional interfaces. A red corner of the triangle is lit...
Page 99
Viewing basic firebox status user guide 77 but the secondary firebox is not responding, the display indicates “not responding.” • the ip address of each firebox interface, and the configuration mode of the external interface. • status of the ca (root) certificate and the ipsec (client) certificate. ...
Page 100
Chapter 6: managing and monitoring the firebox 78 watchguard firebox system branch office vpn tunnels beneath firebox status is a section on bovpn tunnels, in which two categories of these types of tunnels appear: ipsec and dvcp. The figure below shows an expanded entry for a bovpn tunnel. The infor...
Page 101
Viewing basic firebox status user guide 79 • the amount of data sent and received on the tunnel in both bytes and packets. • the time at which the key expires and the tunnel is renegotiated. Expiration can be expressed as a time deadline or in bytes passed. Dvcp tunnels that have been configured for...
Page 102
Chapter 6: managing and monitoring the firebox 80 watchguard firebox system ing properly with the firebox management station. For example, a red exclamation point next to the firebox entry indicates that a firebox is not communicating with either the watchguard security event processor (wsep) or man...
Page 103
Monitoring firebox traffic user guide 81 setting the maximum number of log entries you can change the maximum number of log entries that are stored and viewable on the traffic monitor tab. After the maximum is reached, the earliest logs are removed as more come in. A high value in this field places ...
Page 104
Chapter 6: managing and monitoring the firebox 82 watchguard firebox system 6 to cancel the changes you have made in this dialog box since opening it, click reset to defaults. Copying messages to another application to copy a log message so you can paste it into another application such as email or ...
Page 105
Performing basic tasks with system manager user guide 83 • flushing the arp cache • connecting to a firebox • changing the interval at which the firebox is queried for status information • getting help on the web • opening other firebox system applications running the quicksetup wizard normally, you...
Page 106
Chapter 6: managing and monitoring the firebox 84 watchguard firebox system connecting to a firebox when launched, system manager automatically prompts you to connect to the last firebox with which it established a connection. You can connect to that firebox or you can specify a different one. From ...
Page 107
Performing basic tasks with system manager user guide 85 home page select to bring up the watchguard home page at: http://www.Watchguard.Com livesecurity service logon select to log in to the livesecurity service. For more information on this service, see chapter 2, “service and support.” training a...
Page 108
Chapter 6: managing and monitoring the firebox 86 watchguard firebox system launching logviewer the logviewer application displays a static view of a log file. You can filter by type, search for keywords and fields, and print and save log data to a separate file. For more information, see “reviewing...
Page 109
Viewing bandwidth usage user guide 87 (shown above) in the windows desktop tray. Click wsep status/configuration. For more information, see “setting up the watchguard security event processor” on page 207. If the wsep icon is not displayed in the windows desktop tray, click the main menu button. Sel...
Page 110
Chapter 6: managing and monitoring the firebox 88 watchguard firebox system viewing number of connections by service the servicewatch tab on the system manager display, shown in the following figure, graphs the number of con- nections by service, providing a service-centric view of net- work activit...
Page 112
Chapter 6: managing and monitoring the firebox 90 watchguard firebox system blocked sites list the current manually blocked sites, if any. Temporarily blocked site entries appear on the blocked sites tab. Blocked list network 10.0.0.0/8 permanent network 172.16.0.0/12 permanent network 192.168.0.0/1...
Page 113
Viewing details on firebox activity user guide 91 number of active processes per number of total processes running, and the last number is the next process id number. Load average: 0.04 0.06 0.09 2/21 6282 processes the process id, the name of the process, and the status of the process, as shown in ...
Page 114
Chapter 6: managing and monitoring the firebox 92 watchguard firebox system 74 /bin/logger s 1372 592 1:29.72 ( 0) 99 (round robin) 94 ppp-ttys2 s 804 456 0:00.74 ( 0) 0 (nice) 78 firewalld r 2076 1248 307:29.75 ( 0) 98 (round robin) 79 liedentd s 708 356 0:00.03 ( 0) 0 (nice) 80 dvcpd s 1152 576 57...
Page 115
Viewing details on firebox activity user guide 93 rx packets:3254358 errors:0 dropped:0 overruns:0 frame:0 tx packets:1662288 errors:0 dropped:0 overruns:0 carrier:0 collisions:193 interrupt:11 base address:0xf000 eth0:0 link encap:ethernet hwaddr 00:90:7f:1e:79:84 inet addr:192.168.49.5 bcast:192.1...
Page 116
Chapter 6: managing and monitoring the firebox 94 watchguard firebox system the interfaces used in this section are as follows: eth0 - external (public) interface eth1 - trusted (internal) interface eth2 - optional (dmz) interface ipsec0 - ipsec virtual interface eth0:0 - interface alias fbd0 - virt...
Page 117
Viewing details on firebox activity user guide 95 arp table a snapshot of the arp table on the running firebox. The arp table is used to map ip addresses to hardware addresses. Arp table address hwtype hwaddress flags mask iface 207.23.8.32 ether 00:20:af:b6:fa:29 c * eth1 207.23.8.52 ether 00:a0:24...
Page 118
Chapter 6: managing and monitoring the firebox 96 watchguard firebox system blocked site list the blocked site list tab lists the ip addresses (in slash notation) of any external sites that are temporarily blocked by port space probes, spoofing attempts, address space probes, or another event config...
Page 119
Hostwatch user guide 97 hostwatch hostwatch is a real-time display of active connections occurring on a firebox. It can also graphically represent the connections listed in a log file, either playing back a previ- ous file for review or displaying connections as they are logged into the current log ...
Page 120
Chapter 6: managing and monitoring the firebox 98 watchguard firebox system hostwatch display as shown in the following figure, the upper pane of the hostwatch display is split into two sides, inside and out- side. Double-click an item on either side to produce a pop- up window displaying detailed i...
Page 121
Hostwatch user guide 99 3 enter the firebox status passphrase. Click ok. Replaying a log file in hostwatch you can replay a log file in hostwatch in order to trouble- shoot and retrace a suspected break-in. From hostwatch: 1 select file => open. Browse to locate and select the log file. By default, ...
Page 122
Chapter 6: managing and monitoring the firebox 100 watchguard firebox system modifying hostwatch view properties you can change how hostwatch displays information. For example, hostwatch can display host names rather than ip addresses. From hostwatch: 1 select view => properties. 2 use the host disp...
Page 123
User guide 101 chapter 7 configuring network address translation network address translation (nat) protects your net- work by hiding its internal structure. It also provides an effective way to conserve public ip addresses when the number of addresses is limited. At its most basic level, nat transla...
Page 124
Chapter 7: configuring network address translation 102 watchguard firebox system static nat. Typically, static nat is used for public services that do not require authentication such as web sites and email. 1-to-1 nat the firebox uses private and public ip ranges that you specify, rather than the ra...
Page 125
Using simple dynamic nat user guide 103 service-based dynamic nat each service is configured individually for outgoing dynamic nat. N ote machines making incoming requests over a vpn connection are allowed to access masqueraded hosts by their actual private addresses. Using simple dynamic nat in the...
Page 126
Chapter 7: configuring network address translation 104 watchguard firebox system adding simple dynamic nat entries using built-in host aliases, you can quickly configure the firebox to masquerade addresses from your trusted and optional networks. If trusted hosts are already covered by the default, ...
Page 127
Using simple dynamic nat user guide 105 3 use the to drop-down list to select the destination of outgoing packets. 4 to add either a host or network ip address, click the ... Button. Use the drop-down list to select the address type. Enter the ip address or range. Network addresses must be entered i...
Page 128
Chapter 7: configuring network address translation 106 watchguard firebox system networks behind the dvcp server. Under normal circumstances, you should not make dynamic nat exceptions for these networks. 6 click the button next to the from box and enter the value of the host ip address, network ip ...
Page 129
Using service-based dynamic nat user guide 107 enabling service-based dynamic nat service-based nat is not dependent on enabling simple dynamic nat. From policy manager: 1 select setup => nat. Click advanced. 2 select the checkbox marked enable service-based nat. 3 click ok to close the advanced nat...
Page 130
Chapter 7: configuring network address translation 108 watchguard firebox system configuring a service for incoming static nat for more information on static nat, see the following faqs: https://support.Watchguard.Com/advancedfaqs/ nat_whenstatic.Asp https://support.Watchguard.Com/advancedfaqs/nat_o...
Page 131
Configuring a service for incoming static nat user guide 109 vice. See the following faq before configuring static nat for a service: https://support.Watchguard.Com/advancedfaqs/nat_outin.Asp 1 double-click the service icon in the services arena. The service’s properties dialog box appears displayin...
Page 132
Chapter 7: configuring network address translation 110 watchguard firebox system using 1-to-1 nat 1-to-1 nat uses a global nat policy that rewrites and redirects packets sent to one range of addresses to a com- pletely different range of addresses. This address conver- sion works in both directions....
Page 133
Using 1-to-1 nat user guide 111 a one-to-one mapping exists between each nat address and the forwarded (real) ip address: 210.199.6.0 becomes 192.168.69.0. From policy manager: 1 select setup => nat. The nat setup dialog box appears. 2 click advanced. The advanced nat settings dialog box appears. 3 ...
Page 134
Chapter 7: configuring network address translation 112 watchguard firebox system 12 in the to box, select the appropriate interface. In most cases, you will choose the external interface. The dvcp_ choices are aliases for vpn manager and appear if your firebox is configured as a dvcp client. Dvcp_ne...
Page 135
User guide 113 chapter 8 configuring filtered services you add filtered services–in addition to proxied ser- vices–to control and monitor the flow of ip packets through the firebox. Services can be configured for outgoing and incoming traffic, and they can be active or inactive. When you configure a...
Page 136
Chapter 8: configuring filtered services 114 watchguard firebox system https://support.Watchguard.Com/advancedfaqs/svc_main.Asp selecting services for your security policy objectives the watchguard firebox system, like most commercial firewalls, discards all packets that are not explicitly allowed, ...
Page 137
Selecting services for your security policy objectives user guide 115 • services that send passwords in the clear (ftp, telnet, pop) are very risky. • services with built-in strong authentication (such as ssh) are reasonably safe. If the service does not have built-in authentication, you can mitigat...
Page 138
Chapter 8: configuring filtered services 116 watchguard firebox system as another example, passwords used for some services (ftp, telnet, pop) are sent in the clear. If the passwords are the same as those used internally, a hacker can hijack that password and use it to gain access to your network. A...
Page 139
Adding and configuring services user guide 117 right of the toolbar. The detailed view appears, as shown in the following figure. Detailed view of the services arena to return to the normal view of the services arena, select the large icons button (shown at right). Configurable parameters for servic...
Page 140
Chapter 8: configuring filtered services 118 watchguard firebox system to add a new service to your firewall policy: 1 on the policy manager toolbar, click the add servicesicon (shown at right). You can also select, from the menu bar, edit => add service. The services dialog box appears, as shown in...
Page 141
Adding and configuring services user guide 119 5 (optional) you can customize both the name and the comments that appear when the service is being configured. Click in the name or comment box and type the name or comment you want. 6 click ok. The service’s properties dialog box appears. For informat...
Page 142
Chapter 8: configuring filtered services 120 watchguard firebox system 3 click ok to bring up the service’s properties dialog box and define outgoing properties, as described in “adding service properties” on page 125. Using the previous example, you might add an alias called “staff,” which includes...
Page 143
Adding and configuring services user guide 121 3 in the name text box, type the name of the service. This name must be unique and not already listed in the services dialog box. 4 in the description text box, type a description of the service. This description appears in the details section of the ne...
Page 144
Chapter 8: configuring filtered services 122 watchguard firebox system 7 in the client port text box, select an option from the drop-down list. Note that you can select a range of port numbers. The following options are available: ignore source port can be any number (0—65565). (if you are not sure ...
Page 145
Adding and configuring services user guide 123 11 click ok. The services dialog box appears with the new service displayed under the user filters folder. You can now add the custom service to the services arena just as you would an existing service. 12 in the services dialog box, expand the user fil...
Page 146
Chapter 8: configuring filtered services 124 watchguard firebox system the dialog box that appears, select the save to firebox checkbox. Defining service properties you use the service’s properties dialog box to configure the incoming and outgoing access rules for a given service. The incoming tab d...
Page 147
Defining service properties user guide 125 enabled and allowed traffic is allowed through this service in the selected direction according to the from and to properties. Accessing a service’s properties dialog box when you add a service, the service’s properties dialog box automatically appears. You...
Page 148
Chapter 8: configuring filtered services 126 watchguard firebox system adding addresses or users to service properties both the incoming and outgoing properties include from and to address lists. Use the add address dialog box to add a network, ip address, or specific user to a given ser- vice. 1 in...
Page 149
Defining service properties user guide 127 6 click ok. The new selection appears in either the incoming or outgoing tab under the appropriate from or to box. Working with wg_icons service icons beginning with “wg_” are created automati- cally when you enable features such as pptp and authenti- catio...
Page 150
Chapter 8: configuring filtered services 128 watchguard firebox system customizing logging and notification the watchguard firebox system allows you to create cus- tom logging and notification properties for each filtered service, proxied service, and blocking option. This level of flexibility allow...
Page 151
Defining service properties user guide 129 the service or option you’ve selected. You click the event name to display and set its properties. Enter it in the log when you select this checkbox, an entry appears in the log file each time someone on the external network uses the service incorrectly. Fo...
Page 152
Chapter 8: configuring filtered services 130 watchguard firebox system custom program runs a program when the event occurs. Enter the path of the executable file in the box provided, or browse to specify a path. Launch interval and repeat count work in conjunction to control notification timing. For...
Page 153
Service precedence user guide 131 group always have higher precedence than the services of a lower precedence group, regardless of their individual settings. For example, because the “any” service is in the highest precedence group, all incidences of the “any” ser- vice will take precedence over the...
Page 154
Chapter 8: configuring filtered services 132 watchguard firebox system the following order is used: ip refers to exactly one host ip address list refers to multiple host ip addresses, a network address, or an alias any refers to the special “any” target (not “any” services) when two icons are repres...
Page 155
Service precedence user guide 133 ther down the precedence chain, including outgoing ser- vices. For more information on outgoing services, see the follow- ing faq: https://support.Watchguard.Com/advancedfaqs/ svc_outgoing.Asp.
Page 156
Chapter 8: configuring filtered services 134 watchguard firebox system.
Page 157
User guide 135 chapter 9 configuring proxied services proxy filtering goes a step beyond packet filtering by examining a packet’s content, not just the packet’s header. Consequently, the proxy determines whether a forbidden content type is hidden or embedded in the data payload. For example, an emai...
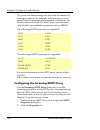
Page 158
Chapter 9: configuring proxied services 136 watchguard firebox system catch dangerous content types in ways that packet filters cannot. To add or configure a proxied service, use the procedures for filtered services in the previous chapter, “configuring filtered services.” for more information on pr...
Page 159
Customizing logging and notification for proxies user guide 137 customizing logging and notification for proxies for more information on logging and notification and the various fields on the logging and notification dialog box, see “customizing logging and notification” on page 128. From the proper...
Page 160
Chapter 9: configuring proxied services 138 watchguard firebox system the proxy can limit message size and limit the number of message recipients. For example, if the message exceeds preset limits for message size or number of recipients, the firebox refuses the mail. The smtp proxy also automati- c...
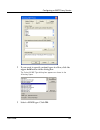
Page 161
Configuring an smtp proxy service user guide 139 3 click incoming. The incoming smtp proxy dialog box appears, displaying the general tab. 4 modify properties on the general tab according to your preferences. For a description of each control, right-click it, and then select what’s this?. You can al...
Page 162
Chapter 9: configuring proxied services 140 watchguard firebox system blocking email attachments you can use two methods to block email attachments. Either allow only save content types or deny file name pat- terns. These two methods can be used together to further protect your network from maliciou...
Page 163
Configuring an smtp proxy service user guide 141 2 if you want to specify content types to allow, click the upper add button in the dialog box. The select mime type dialog box appears as shown in the following figure. 3 select a mime type. Click ok..
Page 164
Chapter 9: configuring proxied services 142 watchguard firebox system 4 to create a new mime type, click new type. Enter the mime type and description. Click ok. The new type appears at the bottom of the content types drop- down list. Repeat this process for each content type. For a list of mime con...
Page 165
Configuring an smtp proxy service user guide 143 adding address patterns adding address patterns can be useful for reducing spam content. From the incoming smtp proxy properties dia- log box: 1 click the address patterns tab. 2 use the category drop-down list to select a category. 3 type the address...
Page 166
Chapter 9: configuring proxied services 144 watchguard firebox system list, or remove headers from the list. From the incoming smtp proxy properties dialog box: 1 click the headers tab. The headers information appears, as shown in the following figure. 2 to add a new header, type the header name in ...
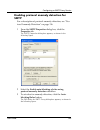
Page 167
Configuring an smtp proxy service user guide 145 enabling protocol anomaly detection for smtp for a description of protocol anomaly detection, see “pro- tocol anomaly detection” on page 136. 1 from the smtp properties dialog box, click the properties tab. The smtp properties dialog box appears, as s...
Page 168
Chapter 9: configuring proxied services 146 watchguard firebox system 4 in the upper box, select the rules to determine which packet originators are automatically added to the auto- blocked sites list. 5 the next box lists the denied content types listed on the content types tab (“allowing safe cont...
Page 169
Configuring an smtp proxy service user guide 147 configuring the outgoing smtp proxy use the outgoing smtp proxy dialog box to set the parameters for traffic going from the trusted and optional networks to the world. You must already have an smtp proxy service icon in the services arena to use this ...
Page 170
Chapter 9: configuring proxied services 148 watchguard firebox system inside.Salesdept.Bigcompany.Com, which would become the public address bigcompany.Com . 1 click the masquerading tab. The smtp masquerading information appears, as shown in the following figure. 2 enter the official domain name. T...
Page 171
Configuring an ftp proxy service user guide 149 6 select the checkbox marked masquerade mime boundary strings to specify that the firewall converts mime boundary strings in messages and attachments to a string that does not reveal internal host names or other identifying information. Configuring an ...
Page 172
Chapter 9: configuring proxied services 150 watchguard firebox system from policy manager: 1 if you have not done so already, use the add service button to add the ftp proxy service. Expand the proxies tree and double-click the ftp service icon. 2 click the properties tab. Click settings. The settin...
Page 173
Selecting an http service user guide 151 4 select the rules to determine which packet originators are automatically added to the auto-blocked sites list. Selecting an http service because of the extensive security implications of http traffic, it is important to restrict the incoming service as much...
Page 174
Chapter 9: configuring proxied services 152 watchguard firebox system a variety of custom options including specialized logging features, definition of safe content types, and webblocker. • http is a proxy service that functions very much like proxied-http, except that it controls both incoming and ...
Page 175
Selecting an http service user guide 153 from any to the optional network, click add beneath the to list. In the add address dialog box, add the optional firebox group. Click ok. 4 click the properties tab. Click settings. 5 on the settings tab, enable http proxy properties according to your securit...
Page 176
Chapter 9: configuring proxied services 154 watchguard firebox system 2 if you want to specify content types to allow, click the upper add button in the dialog box. The select mime type dialog box appears. 3 select a mime type. Click ok. 4 to create a new mime type, click new type. Enter the mime ty...
Page 177
Configuring the dns proxy service user guide 155 get www.Mydomain.Com / http/1.1 the proxy server then forwards this request to the web server mentioned in the get request. To set up an external caching proxy server: 1 configure an external proxy server, such as microsoft proxy server 2.0. 2 open po...
Page 178
Chapter 9: configuring proxied services 156 watchguard firebox system valid transaction signature but no valid key, processing steps that initialize important variables (notably the required buffer size) are skipped. Subsequent function calls make invalid assumptions about the size of the request bu...
Page 179
Configuring the dns proxy service user guide 157 3 click dns-proxy. Click add. The add service dialog box appears. You can change the name assigned to the dns proxy or change the comment associated with the proxy. 4 click ok to close the add service dialog box. The dns-proxy properties dialog box ap...
Page 180
Chapter 9: configuring proxied services 158 watchguard firebox system 4 by default, all rules are enabled. You can enable or disable the rules as you choose to determine which packet originators are automatically added to the auto- blocked sites list. To be able to select or clear several consecutiv...
Page 181
Configuring the dns proxy service user guide 159 you can work around this problem in two ways (the first method is the most secure): • avoid using dynamic nat between your clients and your dns server. • disable the outgoing portion of the dns proxied service and replace it with a filtered dns servic...
Page 182
Chapter 9: configuring proxied services 160 watchguard firebox system.
Page 183
User guide 161 chapter 10 creating aliases and implementing authentication aliases are shortcuts used to identify groups of hosts, networks, or users. The use of aliases simplifies ser- vice configuration. User authentication allows the tracking of connections based on name rather than ip address. W...
Page 184
Chapter 10: creating aliases and implementing authentication 162 watchguard firebox system n ote because usernames are bound to ip addresses, user authentication is not recommended for use in an environment with shared multiuser machines (such as unix, citrix, or nt terminal servers), because only o...
Page 185
Using aliases user guide 163 a host alias takes precedence over a windows nt or radius group with the same name. Adding an alias from policy manager: 1 select setup => aliases. The aliases dialog box appears, as shown in the following figure. 2 click add. 3 in the host alias name text box, enter the...
Page 186
Chapter 10: creating aliases and implementing authentication 164 watchguard firebox system 5 define the alias by adding members. To add an existing member, click the name in the members list. Click add. 6 to configure a new member, click add other. The add member dialog box appears. 7 use the choose...
Page 187
How user authentication works user guide 165 how user authentication works a specialized http server runs on the firebox. To authen- ticate, clients must connect to the authentication server using a java-enabled web browser pointed to: http://ip address of any firebox interface:4100/ a java applet l...
Page 188
Chapter 10: creating aliases and implementing authentication 166 watchguard firebox system 3 under the from box, click add. 4 click add under and add the ip addresses of the remote users you are allowing to authenticate externally. Authentication server types the watchguard firebox system can authen...
Page 189
Defining firebox users and groups for authentication user guide 167 2 in the authentication enabled via box, select the authentication server you want you use. 3 in logon time-out, select how many seconds are allowed for an attempted logon before the time-out shuts down the connection. 4 in session ...
Page 190
Chapter 10: creating aliases and implementing authentication 168 watchguard firebox system within groups, you define users according to factors such as the method they use to authenticate, the type of system they use, or the information they need to access. Users can be either networks or individual...
Page 191
Defining firebox users and groups for authentication user guide 169 2 to add a new group, click the add button beneath the groups list. The add firebox group dialog box appears. 3 type the name of the group. Click ok. 4 to add a new user, click the add button beneath the users list. The setup firebo...
Page 192
Chapter 10: creating aliases and implementing authentication 170 watchguard firebox system 7 when you finish adding the user to groups, click add. The user is added to the user list. The setup firebox user dialog box remains open and cleared for entry of another user. 8 to close the setup firebox us...
Page 193
Configuring radius server authentication user guide 171 3 to identify the host, enter both the host name and the ip address of the windows nt network. If you don’t know the ip address of the host, click find ip. The ip address is automatically entered. When typing ip addresses, type the digits and p...
Page 194
Chapter 10: creating aliases and implementing authentication 172 watchguard firebox system although watchguard supports both chap and pap authentication, chap is considered more secure. From policy manager: 1 select setup => authentication servers. The authentication servers dialog box appears. 2 cl...
Page 195
Configuring cryptocard server authentication user guide 173 to configure the radius server 1 add the ip address of the firebox where appropriate according to the radius server vendor. Some radius vendors may not require this. To determine if this is required for your implementation, check the radius...
Page 196
Chapter 10: creating aliases and implementing authentication 174 watchguard firebox system in the individual service’s properties dialog box, and the ip address of the firebox on the cryptocard authentication server. From policy manager: 1 select setup => authentication servers. The authentication s...
Page 197
Configuring securid authentication user guide 175 cryptocard. The aliases appear in the from and to listboxes in the individual services’ properties dialog boxes. On the cryptocard server: 1 add the ip address of the firebox where appropriate according to cryptocard’s instructions. 2 take the user o...
Page 198
Chapter 10: creating aliases and implementing authentication 176 watchguard firebox system 3 enter the ip address of the securid server. 4 enter or verify the port number used for securid authentication. The default is 1645. 5 enter the value of the secret shared between the firebox and the securid ...
Page 199
User guide 177 chapter 11 intrusion detection and prevention the watchguard firebox system can protect your net- work from many types of attacks. In addition to the protection provided through filtered and proxied ser- vices, the firebox also gives you the following tools to stop attacks that servic...
Page 200
Chapter 11: intrusion detection and prevention 178 watchguard firebox system default packet handling the watchguard firebox system provides default packet handling options to automatically block hosts that origi- nate probes and attacks. Logging options help you identify sites that exhibit suspiciou...
Page 201
Default packet handling user guide 179 tion. In conjunction with the false identity, the attacker may route the packet so that it appears to originate from a host that the targeted system trusts. If the destination system performs session authentication based on a connection’s ip address, the destin...
Page 202
Chapter 11: intrusion detection and prevention 180 watchguard firebox system blocking port space and address space attacks other methods that attackers use to gain access to net- works and hosts are known as probes. Port space probes are used to scan a host to find what services are running on it. A...
Page 203
Default packet handling user guide 181 network. Although there is some gain to leaving ip options enabled, the risk generally outweighs the benefit. From policy manager: 1 on the toolbar, click the default packet handling icon. You can also, from policy manager, select setup => intrusion prevention ...
Page 204
Chapter 11: intrusion detection and prevention 182 watchguard firebox system protection feature will self-activate. Once active, further connection attempts from the external side of the firebox must be verified before being allowed to reach your serv- ers. Connections that cannot be verified are no...
Page 205
Detecting man-in-the-middle attacks user guide 183 affecting your server, the setting may be too high. Consult your server’s documentation for help choosing a new value, or experiment by adjusting the setting until the problems disappear. The validation timeout controls how long the firebox “remembe...
Page 206
Chapter 11: intrusion detection and prevention 184 watchguard firebox system to detect whether a man-in-the-middle attack is in progress: 1 bring up the user interface for the certificate authority. The browser displays the fingerprint for the ca certificate. 2 verify the certificate against the one...
Page 207
Blocking sites user guide 185 • permanently blocked sites–which are listed in the configuration file and change only if you manually change them. • auto-blocked sites–which are sites the firebox adds or deletes dynamically based on default packet handling rules and service-by-service rules for denie...
Page 208
Chapter 11: intrusion detection and prevention 186 watchguard firebox system n ote the blocked sites list applies only to traffic on the external interface. Connections between the trusted and optional interfaces are not subject to the blocked sites list. From policy manager: 1 on the toolbar, click...
Page 209
Blocking sites user guide 187 using an external list of blocked sites you can create a list of blocked sites in an external file. This file must be a .Txt file. To load an external file into your blocked sites list: 1 in the blocked sites dialog box, click import. 2 browse to locate the file. Double...
Page 210
Chapter 11: intrusion detection and prevention 188 watchguard firebox system logging and notification for blocked sites from the blocked sites dialog box: 1 click logging. The logging and notification dialog box appears. 2 in the category list, click blocked sites. 3 modify the logging and notificat...
Page 211
Blocking ports user guide 189 by default, the firebox blocks several destination ports. This measure provides convenient defaults which do not normally require changing. Typically, the following ser- vices should be blocked: x window system (ports 6000-6063) the x window system (or x-windows) has se...
Page 212
Chapter 11: intrusion detection and prevention 190 watchguard firebox system would be a good idea to verify that nfs is using port 2049 on all your systems. Openwindows (port 2000) openwindows is a windowing system from sun microsystems that has similar security risks to x- windows. Rlogin, rsh, rcp...
Page 213
Blocking ports user guide 191 avoiding problems with legitimate users it is possible for legitimate users to have problems because of blocked ports. In particular, some clients might tempo- rarily fail because of blocked ports. You should be very careful about blocking port numbers between 1000 thro...
Page 214
Chapter 11: intrusion detection and prevention 192 watchguard firebox system auto-blocking sites that try to use blocked ports you can configure the firebox such that when an outside host attempts to access a blocked port, that host is tempo- rarily auto-blocked. In the blocked ports dialog box, sel...
Page 215
Integrating intrusion detection user guide 193 and monitor sites that attempt access to restricted ports on your network. Configuring a service to temporarily block sites configure the service to automatically block sites that attempt to connect using a denied service. From policy manager: 1 double-...
Page 216
Chapter 11: intrusion detection and prevention 194 watchguard firebox system the watchguard firebox system default packet handling options provide a basic intrusion detection system by blocking common and readily recognizable attacks such as ip address spoofing and linear port space probes. The intr...
Page 217
Integrating intrusion detection user guide 195 using the fbidsmate command-line utility the fbidsmate utility works from the command line. Although you can execute the commands directly against the firebox, the tool is used most frequently in the context of an ids application script. The command syn...
Page 218
Chapter 11: intrusion detection and prevention 196 watchguard firebox system return value the return value of fbidsmate is zero if the command exe- cuted successfully; otherwise it is non-zero. This value should be checked upon return if calling fbidsmate from a shell script or through some other in...
Page 219
Integrating intrusion detection user guide 197 possible. First, you must import the passphrase “secure1” to an encrypted file on the ids host: fbidsmate import_passphrase secure1 /etc/ fbidsmate.Passphrase then you could rewrite the previous examples as: fbidsmate 10.0.0.1 -f /etc/ fbidsmate.Passphr...
Page 220
Chapter 11: intrusion detection and prevention 198 watchguard firebox system.
Page 221
User guide 199 chapter 12 setting up logging and notification an event is any single activity that occurs at the fire- box, such as denying a packet from passing through the firebox. Logging is the recording of these events to a log host. A notification is a message sent to the administrator by the ...
Page 222
Chapter 12: setting up logging and notification 200 watchguard firebox system logging and notification are crucial to an effective network security policy. Together, they make it possible to monitor your network security, identify both attacks and attackers, and take action to address security threa...
Page 223
Developing logging and notification policies user guide 201 and denied packets, and not logging allowed packets. Allowed packets should not be indicative of a security threat. Furthermore, allowed traffic usually far exceeds the volume of denied traffic and would slow response times as well as causi...
Page 224
Chapter 12: setting up logging and notification 202 watchguard firebox system there many more services that require a notification policy, the high number of routes through the firebox increases the likelihood that the log host will issue frequent notifica- tions. If you set up a very accommodating ...
Page 225
Watchguard logging architecture user guide 203 host. For more information, see “setting up the watch- guard security event processor” on page 207. Watchguard logging architecture by default, policy manager and the log and notification application–the watchguard security event processor– are installe...
Page 226
Chapter 12: setting up logging and notification 204 watchguard firebox system multiple log hosts operate in failover, not redundant mode. The primary log host handles the bulk of the logging duties; others are called in as needed when the highest- ranking log host is unavailable to receive logs. Bef...
Page 227
Designating log hosts for a firebox user guide 205 5 click ok. Repeat until all primary and backup log hosts appear in the watchguard security event processors list. Enabling syslog logging note that syslog logging is not encrypted; therefore, do not set the syslog server to a host on the external i...
Page 228
Chapter 12: setting up logging and notification 206 watchguard firebox system 2 click the host name. Click edit. 3 type in the new log encryption key. Click ok. You must use the same log encryption key for both the firebox and the watchguard security event processor. To change the log encryption key...
Page 229
Setting up the watchguard security event processor user guide 207 firebox time to that of the primary log host. Therefore, you should set all log hosts’ clocks to a single source. In a local installation where all log hosts are on the same domain, set each log host to the common domain controller. F...
Page 230
Chapter 12: setting up logging and notification 208 watchguard firebox system windows service. The default method is for the wsep application to run as a windows service. By default, the wsep application is installed to run as a windows service, starting automatically every time the host computer re...
Page 231
Setting up the watchguard security event processor user guide 209 4 if the wsep application was running, restart it after saving the changes. As a service, using the command prompt if the wsep application was not installed by the watch- guard firebox system installation wizard, this must be done fro...
Page 232
Chapter 12: setting up logging and notification 210 watchguard firebox system viewing the wsep application while the watchguard security event processor is running, a firebox-and-traffic icon (shown at left) appears in the windows desktop tray. To view the wsep application, right-click the tray icon...
Page 233
Setting global logging and notification preferences user guide 211 setting the log encryption key the log connection (but not the log file) between the fire- box and a log host is encrypted for security purposes. Both the management station and the wsep application must have the same encryption key....
Page 234
Chapter 12: setting up logging and notification 212 watchguard firebox system log file size and rollover frequency you can set the maximum size of the log file by number of log entries or by time (such as daily, weekly, or monthly). When the log file reaches the maximum according to your settings, t...
Page 235
Setting global logging and notification preferences user guide 213 over by time interval, number of entries, or both. From the watchguard security event processor interface: 1 click the log files tab. The log files tab information appears, as shown in the following figure. 2 for a time interval, sel...
Page 236
Chapter 12: setting up logging and notification 214 watchguard firebox system controlling notification notification occurs when the firebox sends an email mes- sage, pops up a window on the log host, dials a pager, or executes a program to notify an administrator that the fire- box has detected a tr...
Page 237
Customizing logging and notification by service or option user guide 215 customizing logging and notification by service or option the watchguard firebox system allows you to create cus- tom logging and notification properties for each service and blocking option. You can fine-tune your security pol...
Page 238
Chapter 12: setting up logging and notification 216 watchguard firebox system there may be a time lag before logs appear in the log file. All denied packets are logged by default. Send notification select this checkbox to enable notification for the event type; clear it to disable notification for t...
Page 239
Customizing logging and notification by service or option user guide 217 setting launch interval and repeat count two parameters work in conjunction with the event pro- cessor repeat interval to control notification timing: launch interval the minimum time (in minutes) between separate launches of a...
Page 240
Chapter 12: setting up logging and notification 218 watchguard firebox system the repeat count multiplied by the launch interval equals the amount of time an event must continuously happen before it is handled as a repeat notifier. Setting logging and notification for a service for each service adde...
Page 241
Customizing logging and notification by service or option user guide 219 from policy manager: 1 select setup => intrusion protection => default packet handling. The default packet handling dialog box appears. 2 click logging. 3 modify logging and notification properties according to your security po...
Page 242
Chapter 12: setting up logging and notification 220 watchguard firebox system.
Page 243
User guide 221 chapter 13 reviewing and working with log files log files are a valuable tool for monitoring your net- work, identifying potential attacks, and taking action to address security threats and challenges. This chap- ter describes the procedures you use to work with log files, including v...
Page 244
Chapter 13: reviewing and working with log files 222 watchguard firebox system log file names and locations log entries are stored on the primary and backup watch- guard security event processor (wsep). By default, log files are placed in the watchguard installation directory in a subdirectory calle...
Page 245
Viewing files with logviewer user guide 223 2 browse to select a log file. Click open. By default, logs are stored in a subdirectory of the watchguard installation directory called \logs. Logviewer opens and displays the selected log file. Setting logviewer preferences you can adjust the content and...
Page 246
Chapter 13: reviewing and working with log files 224 watchguard firebox system 4 click search. Logviewer searches the entire log file and displays the results as either marked records in the main window or a separate filter window based on your selection. Copying and exporting logviewer data you can...
Page 247
Displaying and hiding fields user guide 225 copying log data 1 select the log entries you want to copy. Use the shift key to select a block of entries. Use the ctrl key to select multiple, non-adjacent entries. 2 to copy the entries for pasting into another application, select edit => copy to clipbo...
Page 248
Chapter 13: reviewing and working with log files 226 watchguard firebox system the following describes each column and whether the default is for the field to appear (show) or not appear (hide): number the sequence number in the file. Default = hide date the date the record entered the log file. Def...
Page 249
Displaying and hiding fields user guide 227 then computed on the log host based on the firebox’s time zone setting. To change the firebox time zone, see “setting the time zone” on page 55. The rest of the columns vary according to the type of event displayed. The events of most frequency and interes...
Page 250
Chapter 13: reviewing and working with log files 228 watchguard firebox system ip header length length, in octets, of the ip header for this packet. A header length that is not equal to 20 indicates that ip options were present. Default = hide ttl (time to live) the value of the ttl field in the log...
Page 251
Working with log files user guide 229 current log files are always open, they cannot be copied, moved, or merged using traditional copy tools; you should use wsep utilities to work with active log files. Unlike other firebox system utilities, you cannot access the watchguard security event processor...
Page 252
Chapter 13: reviewing and working with log files 230 watchguard firebox system 2 click copy each file individually. 3 enter the file to copy in the files to copy box. 4 enter the destination for the file in the copy to this directory box. 5 click copy. The log file is copied to the new directory wit...
Page 253
Working with log files user guide 231 5 stop and restart the watchguard security event processor: right-click the watchguard security event processor in the windows desktop tray. Select stop service. Right-click the icon again and select start service. New log files will be created in the specified ...
Page 254
Chapter 13: reviewing and working with log files 232 watchguard firebox system 2 on the toolbar, click the add service icon (shown at right). You can also select edit => add service. The services dialog box appears. 3 expand packet filters. 4 select watchguard-logging. Click add. Click ok. 5 on the ...
Page 255
Working with log files user guide 233 appear until the remote office firebox has been properly configured..
Page 256
Chapter 13: reviewing and working with log files 234 watchguard firebox system.
Page 257
User guide 235 chapter 14 generating reports of network activity accounting for internet usage can be a challenging network administration task. One of the best ways to provide hard data for accounting and management purposes is to generate detailed reports showing how the internet connection is bei...
Page 258
Chapter 14: generating reports of network activity 236 watchguard firebox system using the advanced features of historical reports, you can define a precise time period for a report, consolidate report sections to show activity across a group of fireboxes, and set properties to display the report da...
Page 259
Creating and editing reports user guide 237 2 enter the report name. The report name will appear in historical reports, the watchguard security event processor, and the title of the output. 3 use the log directory text box to define the location of log files. The default location for log files is th...
Page 260
Chapter 14: generating reports of network activity 238 watchguard firebox system editing an existing report at any time, you can modify the properties of an existing report. From historical reports: 1 select the report to modify. Click edit. The report properties dialog box appears. 2 modify report ...
Page 261
Specifying report sections user guide 239 3 from the time span drop-down list, select the time you want the report to cover. If you chose anything but specify time filters, click ok. If you chose specify time filters, click the start and end drop- down lists and select a start time and end time, res...
Page 262
Chapter 14: generating reports of network activity 240 watchguard firebox system zontal (cumulative) view of data. To consolidate report sec- tions: 1 from the report properties dialog box, select the consolidated sections tab. The tab contains a list of report sections that can be consolidated. Bri...
Page 263
Exporting reports user guide 241 setting a firebox friendly name for reports you can give the firebox a friendly name to be used in reports. If you do not specify a name, the firebox’s ip address is used. From policy manager: 1 select setup => name. The firebox name dialog box appears. 2 enter the f...
Page 264
Chapter 14: generating reports of network activity 242 watchguard firebox system exporting a report to webtrends for firewalls and vpns historical reports can export the log file into a format that can be imported into webtrends for firewalls and vpns. Webtrends for firewalls and vpns calculates inf...
Page 265
Using report filters user guide 243 drive :\ watchguard install directory \reports exporting a report to a text file when you select text export from the setup tab on the report properties dialog box, the report output is created as a comma-delimited format file, which you can then use in other prog...
Page 266
Chapter 14: generating reports of network activity 244 watchguard firebox system user filter a report based on authenticated username. Creating a new report filter use historical reports to create a new report filter. Filters are stored in the watchguard installation directory, in the subdirectory r...
Page 267
Scheduling and running reports user guide 245 deleting a report filter to remove a filter from the list of available filters, highlight the filter. Click delete. This command removes the .Ftr file from the \ report-defs directory. Applying a report filter each report can use only one filter. To appl...
Page 268
Chapter 14: generating reports of network activity 246 watchguard firebox system 4 select a time interval. For a custom interval, select custom and then enter the interval in hours. 5 select the first date and time the report should run. The report will run automatically at the time selected and the...
Page 269
Report sections and consolidated sections user guide 247 firebox statistics a summary of statistics on one or more log files for a single firebox. Authentication detail a detailed list of authenticated users sorted by connection time. Fields include: authenticated user, host, start date of authentic...
Page 270
Chapter 14: generating reports of network activity 248 watchguard firebox system time summary – proxied traffic a table, and optionally a graph, of all accepted connections distributed along user-defined intervals and sorted by time. If you choose the entire log file or specific time parameters, the...
Page 271
Report sections and consolidated sections user guide 249 smtp summary a table, and optionally a graph, of the most popular incoming and outgoing email addresses, sorted by byte count or number of connections. Smtp detail a table of incoming and outgoing smtp proxy traffic, sorted by time stamp. The ...
Page 272
Chapter 14: generating reports of network activity 250 watchguard firebox system denied authentication detail a detailed list of failures to authenticate, sorted by time. The fields are date, time, host, and user. Consolidated sections network statistics a summary of statistics on one or more log fi...
Page 273
Report sections and consolidated sections user guide 251 time summary – proxied traffic a table, and optionally a graph, of all accepted proxied connections distributed along user-defined intervals and sorted by time. If you choose the entire log file or specific time parameters, the default time in...
Page 274
Chapter 14: generating reports of network activity 252 watchguard firebox system.
Page 275
User guide 253 chapter 15 controlling web site access webblocker is a feature of the watchguard firebox system that works in conjunction with the http proxy to provide web site filtering capabilities. It enables you to exert fine control over the web surfing in your organization. You can designate w...
Page 276
Chapter 15: controlling web site access 254 watchguard firebox system installing the webblocker server you install the webblocker server when you first run the setup program for the watchguard firebox system, as described in “setting up the management station” on page 36. By default, the setup progr...
Page 277
Getting started with webblocker user guide 255 you can run the webblocker utility at any time to: • download a new version of the database. • view the current database status • upload the database • view the current webblocker server status • install or remove the server • start or stop the server t...
Page 278
Chapter 15: controlling web site access 256 watchguard firebox system vices. If the http service allows outgoing from any to any but webblocker settings are set to “block all urls,” all web access is blocked. For information on adding an http proxy service, see “adding a proxy service for http” on p...
Page 279
Configuring the webblocker service user guide 257 3 select the checkbox marked activate webblocker. 4 next to the webblocker servers box, click add. 5 in the dialog box that appears, type the ip address of the server in the value field. Click ok. If you want to add additional webblocker servers, see...
Page 280
Chapter 15: controlling web site access 258 watchguard firebox system attempt to open a blocked web site. The text string must be plain text and cannot contain html or the greater than (>) or less than ( are permitted: %u the full url of the denied request. %s block status, or the reason the request...
Page 281
Configuring the webblocker service user guide 259 from the proxy’s dialog box: 1 click the wb: schedule tab. The tab appears, as shown in the following figure. 2 click hour blocks to toggle from operational to non- operational. N ote the operational and non-operational hours schedule is dependent on...
Page 282
Chapter 15: controlling web site access 260 watchguard firebox system creating webblocker exceptions webblocker provides an exceptions control to override any of the webblocker settings. Exceptions take precedence over all other webblocker rules; you can add sites that you want to be allowed or deni...
Page 283
Configuring the webblocker service user guide 261 from the http proxy dialog box: 1 click the wb: exceptions tab (you might need to use the arrow keys at the right of the dialog box to see this tab). 2 in the allowed exceptions section, click add. The define exceptions dialog box appears. 3 select t...
Page 284
Chapter 15: controlling web site access 262 watchguard firebox system managing the webblocker server the webblocker server is installed as a windows service and can be started or stopped from the services application located in the windows control panel program group. Installing multiple webblocker ...
Page 285
Automating webblocker database downloads user guide 263 which appears in your watchguard directory under the wbserver folder: 1 open control panel and select scheduled tasks. (if it is not listed, see “installing scheduled tasks,” in the following section.) 2 select add scheduled task. 3 the schedul...
Page 286
Chapter 15: controlling web site access 264 watchguard firebox system 4 a list of software appears (this may take a few minutes). If you’re using internet explorer 4.0, under additional explorer enhancements, select task scheduler. If you’re using internet explorer 5.0 or later, select offline brows...
Page 287
User guide 265 chapter 16 connecting with out- of-band management the watchguard firebox system out-of-band (oob) management feature enables the management station to communicate with a firebox by way of a modem (not provided with the firebox) and telephone line. Oob is useful for remotely configuri...
Page 288
Chapter 16: connecting with out-of-band management 266 watchguard firebox system • enable the management station for dial-up networking connections. • set firebox network configuration properties. Enabling the management station for a dial-up ppp connection to work between a manage- ment station and...
Page 289
Enabling the management station user guide 267 install the modem 1 from the desktop, click start => settings => control panel => phone and modem options. 2 click the modems tab. 3 click add. The add/remove hardware wizard appears. 4 follow the wizard through, completing the information requested. Yo...
Page 290
Chapter 16: connecting with out-of-band management 268 watchguard firebox system preparing a windows xp management station for oob before configuring the management station, you must first install the modem. If the modem is already installed, go to the instructions for configuring the dial-up connec...
Page 291
Configuring the firebox for oob user guide 269 configuring the firebox for oob oob management features are configured in policy man- ager using the network configuration dialog box, oob tab. The oob tab is divided into two identical halves: the top half controls the settings of any external modem at...
Page 292
Chapter 16: connecting with out-of-band management 270 watchguard firebox system need not specify a username or password; leave these fields blank. Oob time-out disconnects the firebox starts the ppp session and waits for a valid connection from policy manager on your management sta- tion. If none i...
Page 293
User guide 271 appendix a troubleshooting firebox connectivity this chapter provides four ways of connecting to your firebox should you lose connectivity. These proce- dures assume that you have already created a configu- ration file and will be restoring the firebox with that file. If you have not ...
Page 294
Appendix a: troubleshooting firebox connectivity 272 watchguard firebox system method 1: ethernet dongle method this method involves using a single crossover cable. 1 make sure the firebox and the management station are disconnected from the network. 2 connect one end of the crossover cable to the o...
Page 295
Method 1: ethernet dongle method user guide 273 7 open policy manager from firebox system manager. Do not connect to the firebox at this time. 8 in policy manager, select file => open => configuration file. Select the configuration file you want to load onto the firebox and load it into policy manag...
Page 296
Appendix a: troubleshooting firebox connectivity 274 watchguard firebox system you should be able to ping the firebox again with the same ip address you used earlier. At this point, you should be able to connect back to the firebox through system man- ager and reinstall the firebox back into the net...
Page 297
Method 2: the flash disk management utility user guide 275 6 when prompted to enter an ip address, it is recommended that you use the address that is currently configured as the default gateway on your management station. Click ok. 7 choose the com port that is open on the management station. Click ...
Page 298
Appendix a: troubleshooting firebox connectivity 276 watchguard firebox system you should be able to ping the firebox again with the same ip address you used earlier. At this point, you should be able to connect back to the firebox through system man- ager and reinstall the firebox into the network....
Page 299
Method 4: serial dongle (firebox ii only) user guide 277 6 in policy manager, select file => save => to firebox. When you are asked for the ip address of the firebox, use 192.168.253.1 with wg as the passphrase. 7 when the firebox flash disk dialog box appears, click the button marked save configura...
Page 300
Appendix a: troubleshooting firebox connectivity 278 watchguard firebox system 2 power-cycle the firebox. The light sequence should look like this: armed light: steady sys b: steady (on some fireboxes, the sys b light may flicker.) (do not be concerned with the lights on the security triangle displa...
Page 301
User guide 279 index symbols .Cfg files 49 .Ftr files 244 .Idx files 222 .Rep files 238 .Wgl files 222 .Wts files 242 numerics 1-1 mapping dialog box 111 1-to-1 nat. See nat, 1-to-1 a active connections on firebox, viewing 97 activex applets 154 add address dialog box 109, 126, 163 add exception dia...
Page 302
280 watchguard firebox system blocked ports dialog box 191, 192 blocked ports list 191 blocked services netbios 190 novel ipx over ip 190 openwindows 190 rcp 190 rlogin 190 rpc portmapper 190 rsh 190 x font server 189 x window 189 blocked sites and firebox interfaces 185 and ids applications 194 aut...
Page 303
User guide 281 default lease time for 67 described 66 enabling 127 lease times 66 maximum lease time for 67 modifying subnets 68 not using firebox as 66 removing subnets 68 setting up firebox as 66 dhcp server dialog box 66 dhcp subnet properties dialog box 67 dhcp support on external interface 35, ...
Page 304
282 watchguard firebox system sent after triggering event 214 encryption 37, 38 encryption for vpns, viewing 79 encryption key entering 53 when saving configuration file 52 esmtp auth types 139 configuring 139 keywords supported 138 eth1, eth 2 94 ethernet dongle method for troubleshooting 272 event...
Page 305
User guide 283 viewing active connections on 97 viewing bandwidth usage 87 viewing basic status 74 viewing everyone authenticated to 95 viewing log messages generated by 80 viewing memory usage of 90 viewing uptime and version 89 flash disk management tool 274 ftp and optional network 49 and securit...
Page 306
284 watchguard firebox system intrusion detection and prevention 177–197 intrusion detection system (ids) and fbidsmate utility 194 described 193 ip addresses adding to services 126 and drop-in configuration 30 and routed configuration 30 and static nat 108 changing 60 default gateways 77 entering 4...
Page 307
User guide 285 log rollover 212 logging architecture 203 blocked port activity 192 described 199 developing policies for 200 enabling syslog 205 failover 202 for blocked ports 192 for blocked sites 188 setting rollover interval 212 specifying for smtp proxy 144 synchronizing nt log hosts 207 logging...
Page 308
286 watchguard firebox system described 101 dynamic described 101, 102 service-based dynamic configuring exceptions 107 described 103 disabling 107 enabling 107 using 106 simple dynamic adding entries 104 defining exceptions 105 described 102 enabling 103 reordering entries 105 using 103 static addi...
Page 309
User guide 287 establishing connection 269 installing modem 267, 268 preparing nt management station for 266 preparing windows 2000 management station for 266 preparing windows xp management station for 268 timeout disconnects 270 p packet filters, described 113 packet handling, default. See default...
Page 310
288 watchguard firebox system q quicksetup wizard described 40 launching 40 rerunning 40 running from system manager 83 steps 41 r radius server authentication 171 rapid response team 9, 10 rcp service 190 realnetworks, and nat 112 red exclamation point, in vpn monitor 79 repeat count, setting 217 r...
Page 311
User guide 289 and ftp 115, 149 and http 115 and pop 115 and services 114 and smtp 115 and telnet 115 customizing 44 described 44 guidelines for services 114 opening configuration file 49 security triangle display 75 select mime type dialog box 141 serial dongle method for troubleshooting 277 servic...
Page 312
290 watchguard firebox system blocking 179 described 178 static pppoe 62 steel belted radius 175 subnets adding to dhcp server 67 modifying 68 removing 68 syn flood attacks blocking 181 changing settings 182 described 181 preventing false alarms 182 syn validation timeout setting 183 syslog color 81...
Page 313
User guide 291 and wg_dvcp service 127 described 5 vpns allowing incoming services from 115 and 1-to-1 nat 110 in routed configurations 30 w watchguard certified training partners (wctps) 21 watchguard firebox system additional information on 84 described 1 documentation 18 introduction 2 online hel...
Page 314
292 watchguard firebox system wizard.Cfg 40 wsep. See watchguard security event processor x x font server 189 x window 189 z zip files 154.