- DL manuals
- 3Com
- Switch
- 7750 Series
- Configuration Manual
3Com 7750 Series Configuration Manual
Summary of 7750 Series
Page 1
3com ® switch 7750 family configuration guide switch 7750 switch 7754 switch 7757 switch 7758 www.3com.Com part number: 10015462 rev. Ad published: december 2007.
Page 2
3com corporation 350 campus drive marlborough, ma usa 01752-3064 copyright © 2006-2007, 3com corporation. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) without ...
Page 3: Ontents
C ontents a bout t his g uide conventions 17 related documentation 17 1 cli o verview introduction to the cli 19 command level/command view 19 cli features 29 2 l ogging into an e thernet s witch logging into an ethernet switch 33 introduction to the user interface 33 3 l ogging in through the c ons...
Page 4
4 c ontents 6 l ogging in through the w eb - based n etwork m anagement s ystem introduction 71 establishing an http connection 71 configuring the login banner 72 enabling/disabling the web server 73 7 l ogging in through nms introduction 75 connection establishment using nms 75 8 u ser c ontrol int...
Page 5
Contents 5 14 s uper vlan super vlan overview 121 super vlan configuration 121 displaying super vlan 123 super vlan configuration example 124 15 ip a ddress c onfiguration ip address overview 127 configuring an ip address for a vlan interface 129 displaying ip address configuration 130 ip address co...
Page 6
6 c ontents selective qinq configuration 165 configuring outer tag replacement 166 selective qinq configuration example 167 21 s hared vlan c onfiguration shared vlan overview 169 shared vlan configuration 170 displaying shared vlan 170 shared vlan configuration example 171 22 p ort b asic c onfigur...
Page 7
Contents 7 28 mac a ddress t able m anagement overview 225 configuring mac address table management 227 displaying and maintaining mac address configuration 230 configuration example 231 29 c entralized mac a ddress a uthentication c onfiguration centralized mac address authentication overview 233 c...
Page 8
8 c ontents troubleshooting rip configuration 300 34 ospf c onfiguration ospf overview 301 introduction to ospf configuration tasks 307 basic ospf configuration 309 ospf area attribute configuration 311 ospf network type configuration 312 ospf route control 313 ospf network adjustment and optimizati...
Page 9
Contents 9 39 802.1 x c onfiguration introduction to 802.1x 389 802.1x configuration 399 basic 802.1x configuration 399 802.1x-related parameter configuration 401 advanced 802.1x configuration 401 displaying and debugging 802.1x 403 configuration example 404 40 habp c onfiguration introduction to ha...
Page 10
10 c ontents 46 igmp c onfiguration overview 449 igmp configuration tasks 454 displaying igmp 460 47 pim c onfiguration pim overview 461 common pim configuration 469 pim-dm configuration 472 pim-sm configuration 472 displaying and debugging pim 475 pim configuration examples 476 troubleshooting pim ...
Page 11
Contents 11 52 vrrp c onfiguration vrrp overview 553 vrrp configuration 557 displaying and maintaining vrrp 559 vrrp configuration example 559 troubleshooting vrrp 565 53 ha c onfiguration ha overview 567 ha configuration 568 displaying ha 569 54 arp c onfiguration introduction to arp 571 configurin...
Page 12
12 c ontents troubleshooting dhcp relay agent 621 59 dhcp s nooping c onfiguration configuring dhcp snooping 623 dhcp snooping configuration 628 displaying and maintaining dhcp snooping 632 dhcp snooping configuration example 632 60 acl c onfiguration acl overview 637 choosing acl mode for traffic f...
Page 13
Contents 13 management device configuration 708 member device configuration 711 intra-cluster configuration 713 displaying and maintaining a cluster 713 cluster configuration example 714 64 p o e c onfiguration poe overview 719 poe configuration 721 displaying poe configuration 723 poe configuration...
Page 14
14 c ontents 70 ntp c onfiguration introduction to ntp 753 ntp implementation mode configuration 757 access control permission configuration 759 ntp authentication configuration 759 configuration of optional ntp parameters 761 displaying and debugging ntp 762 configuration example 762 71 ssh t ermin...
Page 15
Contents 15 remote software loading 846 78 b asic s ystem c onfiguration & d ebugging basic system configuration 853 displaying the system status 855 system debugging 855 79 n etwork c onnectivity t est network connectivity test 859 80 d evice m anagement introduction to device management 861 device...
Page 16
16 c ontents 85 m onitor l ink c onfiguration introduction to monitor link 931 configuring monitor link 932 displaying monitor link configuration 934 monitor link configuration example 934 86 c onfiguring h ardware -d ependent s oftware configuring boot rom upgrade with app file 937 configuring inte...
Page 17: Bout
A bout t his g uide this guide describes the 3com ® switch 7750 and how to install hardware, configure and boot software, and maintain software and hardware. This guide also provides troubleshooting and support information for your switch. This guide is intended for qualified service personnel who a...
Page 18
18 a bout t his g uide ■ switch 7750 release notes — contains the latest information about your product. If information in this guide differs from information in the release notes, use the information in the release notes. These documents are available in adobe acrobat reader portable document forma...
Page 19: Cli O
1 cli o verview introduction to the cli a 3com series ethernet switch provides a command line interface (cli) and commands for you to configure and manage the ethernet switch. The cli is featured by the following: ■ commands are grouped by levels. This prevents unauthorized users from operating the ...
Page 20
20 c hapter 1: cli o verview switching between user levels a user can switch the user level from one to another by executing a related command after logging into a switch. The administrator can also set user level switching passwords as required. Setting a user level switching password table 1 lists...
Page 21
Command level/command view 21 cli views cli views are designed for different configuration tasks. They are interrelated. You will enter user view once you log into a switch successfully, where you can perform operations such as displaying operation status and statistical information. In addition, by...
Page 22
22 c hapter 1: cli o verview ■ bgp view ■ bgp ipv4 family multicast view ■ is-is view ■ es-is view ■ routing policy view ■ basic acl view ■ advanced acl view ■ layer 2 acl view ■ user-defined acl view ■ traffic-group view ■ qos view ■ qinq view ■ radius scheme view ■ hwtacacs scheme view ■ isp domai...
Page 23
Command level/command view 23 m-ethernet interface view configure m-ethernet interface parameters [sw7750-m-eth ernet0/0/0] manage ethernet port view. Execute the interface m-ethernet 0/0/0 command in system view. Execute the quit command to return to system view. Execute the return command to retur...
Page 24
24 c hapter 1: cli o verview loopback interface view configure loopback interface parameters [sw7750-loopb ack0] execute the interface loopback 0 command in system view execute the quit command to return to system view. Execute the return command to return to user view. Local user view configure loc...
Page 25
Command level/command view 25 msdp domain view configure msdp domain parameters [sw7750-msdp] execute the msdp command in system view. Execute the quit command to return to system view. Execute the return command to return to user view. Port-isolate- group view configure port-isolate-gro up paramete...
Page 26
26 c hapter 1: cli o verview ospf area view configure ospf area parameters [sw7750-ospf-1 -area-0.0.0.1] execute the area 1 command in ospf view execute the quit command to return to ospf view. Execute the return command to return to user view. Bgp view configure parameters for the (border gateway p...
Page 27
Command level/command view 27 layer 2 acl view define the sub-rules of layer 2 acls, which is numbered from 4,000 to 4,999. [sw7750-acl-lin k-4000] execute the acl number 4000 command in system view. Execute the quit command to return to system view. Execute the return command to return to user view...
Page 28
28 c hapter 1: cli o verview rprge view configure rprge logical interface attributes [sw7750-rprge 1/0/1] execute the interface rprge 1/0/1 command in system view. Execute the quit command to return to system view. Execute the return command to return to user view. Poe profile view configure poe pro...
Page 29
Cli features 29 cli features online help cli provides two types of online help: complete online help and partial online help. They assist you with your configuration. Complete online help enter a “?” character in any view on your terminal to display all the commands available in the view and their b...
Page 30
30 c hapter 1: cli o verview the string means no argument is available in the position occupied by the “?” character. You can execute the command without providing any other information. Partial online help enter a string followed directly by a “?” character on your terminal to display all the comma...
Page 31
Cli features 31 n as the up and down keys have different meanings in hyperterminal running on windows 9x, these two keys can be used to recall history commands only in terminals running windows 3.X or telnet running in windows 3.X. You can press or in windows 9x to achieve the same purpose. Error me...
Page 32
32 c hapter 1: cli o verview.
Page 33: Ogging
2 l ogging into an e thernet s witch logging into an ethernet switch you can log into a switch 7750 ethernet switch in one of the following ways: ■ logging in locally through the console port ■ telneting locally or remotely to an ethernet port ■ telneting to the console port using a modem ■ logging ...
Page 34
34 c hapter 2: l ogging into an e thernet s witch common user interface configuration c caution: ■ the auto-execute command command may cause you unable to perform common configuration in the user interface, so use it with caution. ■ before executing the auto-execute command command and save your co...
Page 35: Ogging
3 l ogging in through the c onsole p ort introduction to log in through the console port is the most common way to log into a switch. It is also the prerequisite to configure other login methods. Normally, you can log into a switch 7750 ethernet switch through its console port. To log into an ethern...
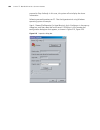
Page 36
36 c hapter 3: l ogging in through the c onsole p ort figure 2 create a connection figure 3 specify the port used to establish the connection.
Page 37
Console port login configuration 37 figure 4 set port parameters 3 turn on the switch. You will be prompted to press the enter key if the switch successfully completes post (power-on self test). The prompt (such as ) appears after you press the enter key. 4 you can then configure the switch or check...
Page 38
38 c hapter 3: l ogging in through the c onsole p ort c caution: changing of console port configuration terminates the connection to the console port. To establish the connection again, you need to modify the configuration of the termination emulation utility running on your pc accordingly. Refer to...
Page 39
Console port login configuration with authentication mode being none 39 n changes of the authentication mode of console port login will not take effect unless you quit the command-line interface and then enter it again. Console port login configuration with authentication mode being none configurati...
Page 41
Console port login configuration with authentication mode being none 41 note that the command level available to users logging into a switch through the none authentication mode depends on both the authentication-mode none command and the user privilege level level command, as listed in the followin...
Page 42
42 c hapter 3: l ogging in through the c onsole p ort network diagram figure 5 network diagram for aux user interface configuration (with the authentication mode being none) configuration procedure # enter system view. System-view # enter aux user interface view. [sw7750] user-interface aux 0 # spec...
Page 43
Console port login configuration with authentication mode being password 43 enter aux user interface view user-interface aux 0 - configure to authenticate users using the local password authentication-mode password required by default, users logging into a switch through the console port are not aut...
Page 44
44 c hapter 3: l ogging in through the c onsole p ort note that the command level available to users logging into a switch through the password authentication mode depends on both the authentication-mode password and the user privilege level level command, as listed in the following table. Configura...
Page 45
Console port login configuration with authentication mode being password 45 network diagram figure 6 network diagram for aux user interface configuration (with the authentication mode being password) configuration procedure # enter system view. System-view # enter aux user interface view. [sw7750] u...
Page 46
46 c hapter 3: l ogging in through the c onsole p ort console port login configuration with authentication mode being scheme configuration procedure table 18 console port login configuration with the authentication mode being scheme operation command description enter system view system-view - confi...
Page 47
Console port login configuration with authentication mode being scheme 47 configure to authenticate users locally or remotely authentication-mode scheme [ command- authorization ] required the specified aaa scheme determines whether to authenticate users locally or remotely. Users are authenticated ...
Page 48
48 c hapter 3: l ogging in through the c onsole p ort note that the command level available to users logging into a switch through the scheme authentication mode depends on the authentication-mode scheme [ command-authentication ] command and the service-type terminal [ level level ] command, as lis...
Page 49
Console port login configuration with authentication mode being scheme 49 ■ configure to authenticate users logging in through the console port in the scheme mode. ■ the baud rate of the console port is 19,200 bps. ■ the screen can contain up to 30 lines. ■ the history command buffer can store up to...
Page 50
50 c hapter 3: l ogging in through the c onsole p ort [sw7750-ui-aux0] history-command max-size 20 # set the timeout time of the aux user interface to 6 minutes. [sw7750-ui-aux0] idle-timeout 6.
Page 51: Ogging
4 l ogging in through t elnet introduction you can manage and maintain a switch remotely by telneting to the switch. To achieve this, you need to configure both the switch and the telnet terminal accordingly. Common configuration table 21 lists the common telnet configuration. Table 20 requirements ...
Page 52
52 c hapter 4: l ogging in through t elnet telnet configurations for different authentication modes table 22 lists telnet configurations for different authentication modes. Telnet configuration with authentication mode being none configuration procedure table 22 telnet configurations for different a...
Page 53
Telnet configuration with authentication mode being none 53 note that if you configure not to authenticate the users, the command level available to users logging into a switch depends on both the authentication-mode none command and the user privilege level level command, as listed in table 24. Con...
Page 54
54 c hapter 4: l ogging in through t elnet configuration example network requirements perform the following configuration for telnet users logging into vty 0: ■ do not authenticate users logging into vty 0. ■ commands of level 2 are available to users logging into vty 0. ■ vty 0 user interface suppo...
Page 55
Telnet configuration with authentication mode being password 55 # specify commands of level 2 are available to users logging into vty 0. [sw7750-ui-vty0] user privilege level 2 # configure telnet protocol is supported. [sw7750-ui-vty0] protocol inbound telnet # set the maximum number of lines the sc...
Page 56
56 c hapter 4: l ogging in through t elnet note that if you configure to authenticate the users in the password mode, the command level available to users logging into a switch depends on both the authentication-mode password command and the user privilege level level command, as listed in table 26....
Page 57
Telnet configuration with authentication mode being password 57 ■ telnet protocol is supported. ■ the screen can contain up to 30 lines. ■ the history command buffer can contain up to 20 commands. ■ the timeout time of vty 0 is 6 minutes. Network diagram figure 9 network diagram for telnet configura...
Page 58
58 c hapter 4: l ogging in through t elnet # set the timeout time to 6 minutes. [sw7750-ui-vty0] idle-timeout 6 telnet configuration with authentication mode being scheme configuration procedure table 27 telnet configuration with the authentication mode being scheme operation command description ent...
Page 59
Telnet configuration with authentication mode being scheme 59 note that if you configure to authenticate the users in the scheme mode, the command level available to users logging into a switch depends on the authentication-mode scheme [ command-authentication ] command, the user privilege level lev...
Page 60
60 c hapter 4: l ogging in through t elnet n refer to “aaa & radius & hwtacacs configuration example” on page 537 and “ssh terminal services” on page 773. Table 28 determine the command level when users logging into switches are authenticated in the scheme mode scenario command level authentication ...
Page 61
Telnet configuration with authentication mode being scheme 61 configuration example network requirements perform the following configuration for telnet users logging into vty 0: ■ configure the name of the local user to be “guest”. ■ set the authentication password of the local user to 1234567890 (i...
Page 62
62 c hapter 4: l ogging in through t elnet [sw7750-ui-vty0] authentication-mode scheme # configure telnet protocol is supported. [sw7750-ui-vty0] protocol inbound telnet # set the maximum number of lines the screen can contain to 30. [sw7750-ui-vty0] screen-length 30 # set the maximum number of comm...
Page 63
Telneting to a switch 63 [sw7750-vlan-interface1] ip address 202.38.160.92 255.255.255.0 2 perform telnet-related configuration on the switch. Refer to “telnet configuration with authentication mode being none” on page 52, “telnet configuration with authentication mode being password” on page 55, an...
Page 64
64 c hapter 4: l ogging in through t elnet by default, commands of level 0 are available to telnet users authenticated by password. Refer to “command level/command view” on page 19 for information about command hierarchy. Telneting to another switch from the current switch you can telnet to another ...
Page 65: Ogging
5 l ogging in u sing m odem introduction the administrator can log into the console port of a remote switch using a modem through pstn (public switched telephone network) if the remote switch is connected to the pstn through a modem to configure and maintain the switch remotely. When a network opera...
Page 66
66 c hapter 5: l ogging in u sing m odem you can verify your configuration by executing the at&v command. N the above configuration is unnecessary to the modem on the administrator side. The configuration commands and the output of different modems may differ. Refer to the user manual of the modem w...
Page 67
Modem connection establishment 67 at&s0 ----------------------- set dsr to high level by force ateq1&w ----------------------- disable the modem from returning com mand response and the result, save the changes you can verify your configuration by executing the at&v command. N ■ the configuration co...
Page 68
68 c hapter 5: l ogging in u sing m odem figure 16 set the telephone number figure 17 call the modem 5 provide the password when prompted. If the password is correct, the prompt (such as ) appears. You can then configure or manage the switch. You can also enter the character ? At anytime for help. R...
Page 69
Modem attributes configuration 69 configuration procedure configuration example # enable modem call-in and call-out, set the answer mode to auto answer, and set the timeout time to 45 seconds. System-view [sw7750] user-interface aux 0 [sw7750-ui-aux0] modem both [sw7750-ui-aux0] modem auto-answer [s...
Page 70
70 c hapter 5: l ogging in u sing m odem.
Page 71: Ogging
6 l ogging in through the w eb - based n etwork m anagement s ystem introduction a switch 7750 has a web server built in. It enables you to log into a switch 7750 through a web browser and then manage and maintain the switch intuitively by interacting with the built-in web server. To log into a swit...
Page 72
72 c hapter 6: l ogging in through the w eb - based n etwork m anagement s ystem figure 18 establish an http connection between your pc and the switch 4 log into the switch through ie. Launch ie on the web-based network management terminal (your pc) and enter the ip address of the management vlan in...
Page 73
Enabling/disabling the web server 73 network diagram figure 20 network diagram for login banner configuration configuration procedure # enter system view. System-view # configure the banner “welcome” to be displayed when a user logs into the switch through web. [sw7750] header login %welcome% assume...
Page 74
74 c hapter 6: l ogging in through the w eb - based n etwork m anagement s ystem n to improve security and prevent attack to the unused sockets, tcp 80 port (which is for http service) is enabled/disabled after the corresponding configuration. ■ enabling the web server (by using the undo ip http shu...
Page 75: Ogging
7 l ogging in through nms introduction you can also log into a switch through an nms (network management station), and then configure and manage the switch through the agent module on the switch. ■ the agent here refers to the software running on network devices (switches) and as the server. ■ snmp ...
Page 76
76 c hapter 7: l ogging in through nms.
Page 77: Ser
8 u ser c ontrol introduction a switch provides ways to control different types of login users, as listed in table 35. Controlling telnet users prerequisites: the controlling policy against telnet users is determined, including the source and destination ip addresses to be controlled and the control...
Page 78
78 c hapter 8: u ser c ontrol controlling telnet users by source and destination ip addresses controlling telnet users by source and destination ip addresses is achieved by applying advanced acls, which are numbered from 3000 to 3999. Refer to “defining advanced acls” on page 642. Quit to system vie...
Page 79
Controlling network management users by source ip addresses 79 controlling network management users by source ip addresses you can manage a 3com series ethernet switch through network management software. Network management users can access switches through snmp. You need to perform the following tw...
Page 80
80 c hapter 8: u ser c ontrol n you can specify different acls while configuring the snmp community name, the snmp group name, and the snmp user name. As snmp community name is a feature of snmpv1 and snmpv2c, the specified acls in the command that configures snmp community names (the snmp-agent com...
Page 81
Controlling web users by source ip address 81 you need to perform the following two operations to control web users by source ip addresses. ■ defining an acl ■ applying the acl to control web users prerequisites the controlling policy against web users is determined, including the source ip addresse...
Page 82
82 c hapter 8: u ser c ontrol network diagram figure 24 network diagram for controlling web users using acls configuration procedure # define a basic acl. System-view [sw7750] acl number 2030 [sw7750-acl-basic-2030] rule 1 permit source 10.110.100.52 0 [sw7750-acl-basic-2030] quit # apply acl 2030 t...
Page 83: Onfiguration
9 c onfiguration f ile m anagement introduction to configuration file configuration file records and stores user configurations performed to a switch. It also enables users to check switch configurations easily. Upon powered on, a switch loads the configuration file known as saved-configuration file...
Page 84
84 c hapter 9: c onfiguration f ile m anagement c caution: currently, the extension of a configuration file is cfg. Configuration files are saved in the root directory of the flash. In the following conditions, it may be necessary for you to remove the configuration files from the flash: ■ the syste...
Page 85
Configuration file-related operations 85 you are recommended to adopt the fast saving mode in the conditions of stable power and adopt the safe mode in the conditions of unstable power or remote maintenance. N ■ you are recommended to use the save command to save the configuration before restarting ...
Page 86
86 c hapter 9: c onfiguration f ile m anagement.
Page 87: Vlan O
10 vlan o verview vlan overview introduction to vlan the traditional ethernet is a flat network, where all hosts are in the same broadcast domain and connected with each other through hubs or switches. The hub is a physical layer device without the switching function, so it forwards the received pac...
Page 88
88 c hapter 10: vlan o verview figure 25 a vlan implementation a vlan can span across multiple switches, or even routers. This enables hosts in a vlan to be dispersed in a looser way. That is, hosts in a vlan can belong to different physical network segment. Compared with the traditional ethernet, v...
Page 89
Port-based vlan 89 in figure 26 da refers to the destination mac address, sa refers to the source mac address, and type refers to the protocol type of the packet. Ieee 802.1q protocol defines that a 4-byte vlan tag is encapsulated after the destination mac address and source mac address to show the ...
Page 90
90 c hapter 10: vlan o verview you can configure all the three types of ports on the same device. However, note that you cannot directly switch a port between trunk and hybrid and you must set the port as access before the switching. For example, to change a trunk port to hybrid, you must first set ...
Page 91
Protocol-based vlan 91 c caution: you are recommended to set the default vlan id of the local hybrid or trunk ports to the same value as that of the hybrid or trunk ports on the peer switch. Otherwise, packet forwarding may fail on the ports. Protocol-based vlan introduction to protocol-based vlan p...
Page 92
92 c hapter 10: vlan o verview in the two figures, da and sa refer to the destination mac address and source mac address of the packet respectively. The number in the bracket indicates the field length in bits. The maximum length of an ethernet packet is 1500 bytes, that is, 5dc in hexadecimal, so t...
Page 93
Protocol-based vlan 93 the switch differentiates between 802.2 llc encapsulation and 802.3 snap encapsulation according to the values of the dsap field and the ssap field. N when the oui is 00-00-00 in 802.2 snap encapsulation, the pid field has the same meaning as the type field in ethernet ii enca...
Page 94
94 c hapter 10: vlan o verview implementation of protocol-based vlan switch 7750 ethernet switches assign the packet to the specific vlan by matching the packet with the protocol template. The protocol template is the standard to determine the protocol to which a packet belongs. Protocol templates i...
Page 95: Vlan C
11 vlan c onfiguration vlan configuration basic vlan configuration create a range of vlans you can use the following command to create a range of vlans, reducing your workload of creating vlans. C caution: as the default vlan, vlan 1 needs not to be created and cannot be removed. Configuring vlan br...
Page 96
96 c hapter 11: vlan c onfiguration a vlan only supports one broadcast storm suppression mode at one time. If you configure broadcast storm suppression modes multiple times for a vlan, the latest configuration will overwrite the previous configuration. Different modules of switch 7750s support diffe...
Page 97
Configuring a port-based vlan 97 if a vlan interface is disabled, its status is not determined by the status of its ports. Displaying vlan configuration after the configuration above, you can execute the display command in any view to display the running status after the configuration, so as to veri...
Page 98
98 c hapter 11: vlan c onfiguration configuring a hybrid-port-based vlan a hybrid port may belong to multiple vlans, and this configuration can only be performed in ethernet port view. Follow these steps to configure the hybrid-port-based vlan: n ■ to configure a trunk port into a hybrid port (or vi...
Page 99
Configuring a port-based vlan 99 ■ the default vlan ids of the trunk ports on the local and peer devices must be the same. Otherwise, packets cannot be transmitted properly. Displaying and maintaining port-based vlan configuring a port-based vlan configuration prerequisites create a vlan before conf...
Page 100
100 c hapter 11: vlan c onfiguration configuring a protocol-based vlan creating protocol template for protocol-based vlan configuration prerequisites create a vlan before configuring a protocol-based vlan. Configuration procedure when you are creating protocol templates for protocol-based vlans, the...
Page 101
Configuring a protocol-based vlan 101 ■ ip [ ip-address [ net-mask ] ] defines ipv4-based vlan. If you want to define the vlans based on ip or other encapsulation formats, use mode { ethernetii [ etype etype-id ] } and snap [ etype etype-id ], in which, etype-id is 0x0800. Associating a port with th...
Page 102
102 c hapter 11: vlan c onfiguration ■ currently, only non-type-a modules, including i/o modules and fabric, support this command. ■ if a protocol-based vlan has been associated with a module, the vlan cannot be removed. ■ if a protocol in a vlan has been associated with a module, the protocol canno...
Page 103
Configuring a protocol-based vlan 103 protocol-based vlan configuration example standard-template-protocol-based vlan configuration example 1 network requirements ■ create vlan 5 and configure it to be a protocol-based vlan, with the protocol-index being 1 and the protocol being ip. ■ associate ethe...
Page 104
104 c hapter 11: vlan c onfiguration system-view [sw7750] vlan 7 [sw7750-vlan7] # configure index 1 of vlan 7 according to the network requirement. [sw7750-vlan7] protocol-vlan 1 mode llc dsap 01 ssap ac # configure index 2 of vlan 7 according to the network requirement. [sw7750-vlan7] protocol-vlan...
Page 105: Oice
12 v oice vlan c onfiguration voice vlan overview voice vlans are vlans configured specially for voice data stream. By adding the ports with voice devices attached to voice vlans, you can perform qos (quality of service)-related configuration for voice data, ensuring the transmission priority of voi...
Page 106
106 c hapter 12: v oice vlan c onfiguration vlan; voice ports cannot be added into or removed from the voice vlan through manual configurations. ■ in manual mode: you need to execute related configuration commands to add a voice port to the voice vlan or remove a voice port from the voice vlan. Tagg...
Page 107
Voice vlan overview 107 c caution: if the voice stream transmitted by an ip voice device is with vlan tag and the port which the ip voice device is attached to is enabled with 802.1x authentication and 802.1x guest vlan, assign different vlan ids for the voice vlan bound to the port, the default vla...
Page 108
108 c hapter 12: v oice vlan c onfiguration voice vlan configuration configuration prerequisites ■ create the corresponding vlan before configuring a voice vlan. ■ as the default vlan, vlan 1 cannot be bound to a port as a voice vlan. Configuring a voice vlan to operate in automatic mode n for a por...
Page 109
Voice vlan configuration 109 c caution: ■ if the link aggregation control protocol (lacp) is enabled for a port, the voice vlan feature can not be enabled for it. Enable the voice vlan function for the port voice vlan enable required by default, the voice vlan function is disabled on a port. Bind a ...
Page 110
110 c hapter 12: v oice vlan c onfiguration ■ voice vlan function can be effective only for the static vlan. Once a dynamic vlan is enabled with voice vlan function, it automatically changes to static vlan. ■ when a voice vlan operates in the security mode, the devices in it only permit packets whos...
Page 111
Voice vlan configuration example 111 system-view [sw7750] vlan 2 # configure ethernet2/0/1 port to be a trunk port, with vlan 6 as the default vlan, and permit packets of vlan 6 to pass through the port. [sw7750-vlan2] quit [sw7750] interface ethernet 2/0/1 [sw7750-ethernet2/0/1] port link-type trun...
Page 112
112 c hapter 12: v oice vlan c onfiguration voice vlan aging time: 1440 minutes current voice vlan enabled port mode: port mode status voice vlan id -------------------------------------------------------------------- ethernet2/0/3 manual enable 3 # remove ethernet2/0/3 port from the voice vlan. [sw...
Page 113: Solate
13 i solate -u ser -vlan c onfiguration isolate-user-vlan overview introduction to isolate-user-vlan isolate-user-vlan is designed for saving vlan resource by means of copying mac address entries among the mac address tables of vlans in the network, which is utilizing the feature that an hybrid port...
Page 114
114 c hapter 13: i solate -u ser -vlan c onfiguration figure 35 diagram for isolate-user-vlan application forward packets to switch a 1 when packets sent by pc reached ethernet2/0/4, the default vlan id, that is, the vlan tag of vlan 3 is automatically added to the packets. 2 switch b learns the mac...
Page 115
Isolate-user-vlan configuration 115 configuring isolate-user-vlan you can use the following commands to create an isolate-user-vlan for a switch. C caution: ■ multiple isolate-user-vlans can be configured for a switch. ■ with gvrp function enabled, a switch cannot be enabled with isolate-user-vlan f...
Page 116
116 c hapter 13: i solate -u ser -vlan c onfiguration c caution: when you use the port hybrid pvid vlan command to configure the default vlan id for a port, you need to specify the vlan-id as a secondary vlan for a downlink port and specify the vlan-id an isolate-user-vlan for an uplink port. Config...
Page 117
Isolate-user-vlan configuration example 117 network diagram figure 36 diagram for isolate-user-vlan configuration configuration procedure ■ configure switch b # configure the isolate-user-vlan system-view [switchb] vlan 5 [switchb-vlan5] isolate-user-vlan enable # configure the secondary vlan. [swit...
Page 118
118 c hapter 13: i solate -u ser -vlan c onfiguration [switchb-ethernet2/0/5] port hybrid pvid vlan 2 [switchb-ethernet2/0/5] undo port hybrid vlan 1 # add port ethernet2/0/1 to the isolate-user-vlan and the secondary vlan, and configure the port to untag the vlan packets. Remove the port from vlan ...
Page 119
Isolate-user-vlan configuration example 119 [switchc-ethernet2/0/4] quit [switchc] interface ethernet 2/0/1 [switchc-ethernet2/0/1] port link-type hybrid [switchc-ethernet2/0/1] port hybrid vlan 3 untagged [switchc-ethernet2/0/1] port hybrid vlan 4 untagged [switchc-ethernet2/0/1] port hybrid vlan 6...
Page 120
120 c hapter 13: i solate -u ser -vlan c onfiguration.
Page 121: Uper
14 s uper vlan n only the 96gbps switch fabrics support the super vlan. Super vlan overview to save ip address resources, the super vlan concept (also known as vlan aggregation) was developed. Its principle is like this: a super vlan may include multiple sub vlans, with each as a broadcast domain. L...
Page 122
122 c hapter 14: s uper vlan c caution: you can not configure a vlan which includes ethernet ports as a super vlan; and after you configure a super vlan, you cannot add any ethernet port to it. Configuring a sub vlan you can configure a sub vlan just as configuring an ordinary vlan. See “vlan config...
Page 123
Displaying super vlan 123 ■ after establishing the mapping between the sub vlan and the super vlan, you can still add (or delete) ports to (from) the sub vlan. Configuring super vlan to support dhcp relay with dhcp relay function enabled on the vlan interface of the super vlan, the hosts of all sub ...
Page 124
124 c hapter 14: s uper vlan super vlan configuration example super vlan configuration example network requirements ■ create super vlan 10 and sub vlans vlan 2, vlan 3, vlan 5. ■ configure ports ethernet2/0/1 and ethernet2/0/2 to belong to vlan 2, ethernet2/0/3 and ethernet2/0/4 to belong to vlan 3 ...
Page 125
Super vlan configuration example 125 ■ configure the ip address of the vlan 6 as 10.1.1.1, and the sub network mask as 255.255.255.0. ■ enable the dhcp relay function on the vlan interface of vlan 6, and establish the mapping between vlan 6 and the remote dhcp server group 2 to make the hosts in vla...
Page 126
126 c hapter 14: s uper vlan.
Page 127: Ip A
15 ip a ddress c onfiguration ip address overview ip address classification and representation an ip address is a 32-bit address allocated to a device connected to the internet. It consists of two fields: net-id and host-id. To facilitate ip address management, ip addresses are divided into five cla...
Page 128
128 c hapter 15: ip a ddress c onfiguration subnet and mask the traditional ip address classification method wastes ip addresses greatly. In order to make full use of the available ip addresses, the concepts of mask and subnet were introduced. A mask is a 32-bit number corresponding to an ip address...
Page 129
Configuring an ip address for a vlan interface 129 address, and the part corresponding to the remaining “0” bits in the mask is the host address. If there is no subnet division, the subnet mask uses the default value and the length of 1s in the mask is equal to the net-id length. Therefore, for ip a...
Page 130
130 c hapter 15: ip a ddress c onfiguration displaying ip address configuration after the above configuration, you can execute the display command in any view to display the operating status and configuration on the interface to verify your configuration. Ip address configuration example network req...
Page 131: Ip P
16 ip p erformance c onfiguration ip performance overview introduction to tcp attributes ip performance configuration mainly refers to tcp attribute configuration. The tcp attributes that can be configured include: ■ synwait timer: this timer is started when tcp sends a syn packet. If no response pa...
Page 132
132 c hapter 16: ip p erformance c onfiguration configuring tcp attributes configuring to send special ip packets to cpu usually the switch sends ttl timeout packets and unreachable packets to the cpu in the process of forwarding ip packets. The cpu processes these special packets after receiving th...
Page 133
Disabling icmp error message sending 133 if you reference an acl to filter directed broadcasts, only the directed broadcasts that pass the acl filtering can be forwarded to the directly connected network. Disabling icmp error message sending sending error packets is the major function of the interne...
Page 134
134 c hapter 16: ip p erformance c onfiguration use the reset command in user view to clear the ip, tcp, and udp traffic statistics. Troubleshooting symptom: ip packets are forwarded normally, but tcp and udp cannot work normally. Solution: enable the corresponding debugging information output to vi...
Page 135
Troubleshooting 135 then the tcp packets received or sent will be displayed in the following format in real time: tcp output packet: source ip address:202.38.160.1 source port:1024 destination ip address 202.38.160.1 destination port: 4296 sequence number :4185089 ack number: 0 flag :syn packet leng...
Page 136
136 c hapter 16: ip p erformance c onfiguration.
Page 137: Ipx C
17 ipx c onfiguration ipx protocol overview the internetwork packet exchange (ipx) protocol is a network layer protocol in the netware protocol suite. Ipx’s position in the novell netware protocol is similar to ip’s in the tcp/ip protocol suite. Ipx can address, route and forward packets. Ipx is a c...
Page 138
138 c hapter 17: ipx c onfiguration directly connected to them. However, you cannot use such information directly. Instead, the information is collected by the sap agents of the switches on the networks and saved in their server information tables. Ipx configuration configuring ipx basic ipx configu...
Page 139
Ipx configuration 139 configuring an ipx route limit in ipx, you can configure in the routing table the maximum number of the dynamic routes and equivalent routes to the same destination. These two limit settings are independent. When the number of the dynamic routes to the same destination address ...
Page 140
140 c hapter 17: ipx c onfiguration after ipx rip is enabled, the switch broadcasts ipx rip update packets periodically. You can configure the update interval of ipx rip as required. Note that for the synchronization of routing tables, all the switches on the network must have the same rip update in...
Page 141
Ipx configuration 141 to forward an ipx packet. A longer delay means slower forwarding whereas a shorter delay means faster forwarding. By importing routes, different routing protocols can share their routing information. Note that ipx rip imports only active static routes; inactive static routes ar...
Page 142
142 c hapter 17: ipx c onfiguration configuring ipx gns get nearest server (gns) is a type of sap message broadcasted by sap-enabled netware clients. To the gns requests, netware servers respond with gns messages. If a netware server is available on the network segment to which the client is connect...
Page 143
Ipx configuration 143 configuring ipx service information generally, clients can only use the services that are advertised by netware servers and saved on the switch. To make a service always available to the clients, you can manually add it into the server information table as a static entry. If th...
Page 144
144 c hapter 17: ipx c onfiguration configuring ipx forwarding ipx rip and sap periodically broadcast update packets. If the periodical broadcast is not desired, you can enable triggered update on the vlan interfaces of the switch. This allows the switch to broadcast update packets only when route o...
Page 145
Displaying and debugging ipx 145 displaying and debugging ipx after the above-mentioned configuration, use the display command in any view to view the running of ipx and to verify the effect of the configuration. Use the reset command in user view to clear the ipx statistics. Ipx configuration examp...
Page 146
146 c hapter 17: ipx c onfiguration network diagram figure 40 ipx network diagram configuration procedure 1 configure switch a. # enable ipx. System-view [switch] ipx enable # assign the network number 2 to vlan interface 2 to enable ipx on the vlan interface. [switch] interface vlan-interface 2 [sw...
Page 147
Troubleshooting ipx 147 # assign the network number 3 to vlan interface 2 to enable ipx on the vlan interface. [switch] interface vlan-interface 2 [switch-vlan-interface2] ipx network 3 # set the packet encapsulation format to ethernet_snap on vlan interface 2. [switch-vlan-interface2] ipx encapsula...
Page 148
148 c hapter 17: ipx c onfiguration operations: display the mtu setting on the vlan interface with the display interface command and the rip/sap packet size with the display ipx interface command. Check whether the rip/sap packet size is smaller than the mtu setting on the vlan interface. Symptom 3:...
Page 149
Troubleshooting ipx 149 troubleshooting ipx sap symptom 1: unable to add static service information into the service information table. Solutions: ■ use the display ipx service-table inactive command to check whether the service information is in the inactive service information table. If yes, there...
Page 150
150 c hapter 17: ipx c onfiguration ■ check whether there are update packets with the debugging ipx packet and debugging ipx sap packet verbose commands. All the received/transmitted packets can be displayed through debugging information. If there are no update packets, check whether the underlying ...
Page 151
Troubleshooting ipx 151 ■ if round-robin is enabled, check whether multiple equivalent service entries are available for the service request. The service entries are considered equivalent only when they have the same rip delay, rip hop count, sap hop count and sap preference. Troubleshooting ipx rou...
Page 152
152 c hapter 17: ipx c onfiguration.
Page 153: Gvrp C
18 gvrp c onfiguration introduction to garp and gvrp introduction to garp garp (generic attribute registration protocol) offers a mechanism that is used by the members in the same switching network to distribute, propagate and register such information as vlan and multicast addresses. Garp dose not ...
Page 154
154 c hapter 18: gvrp c onfiguration n ■ the value of garp timer will be used in all the garp applications, including gvrp and gmrp, running in one switching network. ■ in one switching network, the garp timers on all the switching devices should be set to the same value. Otherwise, garp application...
Page 155
Introduction to garp and gvrp 155 distinguishes them by their destination mac addresses and delivers them to different garp application (for example, gvrp) for further processing. Gvrp packet format the gvrp packets are in the following format: figure 41 format of gvrp packets the following table de...
Page 156
156 c hapter 18: gvrp c onfiguration protocol specifications gvrp is defined in ieee 802.1q standard. Gvrp configuration the gvrp configuration tasks include configuring the garp timers, enabling gvrp, and configuring the gvrp port registration mode. Configuration prerequisite the port on which gvrp...
Page 157
Displaying and maintaining gvrp 157 the following table describes the relations between the timers: n the recommended settings of garp timers ■ garp hold timer: 100 centiseconds (1 second). ■ garp join timer: 600 centiseconds (6 seconds). ■ garp leave timer: 3000 centiseconds (30 seconds). ■ garp le...
Page 158
158 c hapter 18: gvrp c onfiguration gvrp configuration example network requirements you need to enable gvrp on the switches to enable dynamic vlan information registration and update between the switches. Network diagram figure 42 network diagram for gvrp configuration configuration procedure ■ con...
Page 159: Q C
19 q in q c onfiguration qinq overview introduction to qinq the qinq function enables packets to be transmitted across the operators’ backbone networks with vlan tags of private networks encapsulated in those of public networks. In public networks, packets of this type are transmitted by their outer...
Page 160
160 c hapter 19: q in q c onfiguration ■ saves public network vlan id resource. ■ you can have vlan ids of your own, which is independent of public network vlan ids. ■ provides simple layer 2 vpn solutions for small-sized mans or intranets. Implementation of qinq qinq can be implemented by enabling ...
Page 161
Displaying qinq 161 n the voice vlan feature is mutually exclusive with the qinq feature for a port. ■ when you use the specific command to enable the voice vlan feature for a qinq-enabled port, the switch will prompt errors. ■ if you use the copy configuration command to duplicate the configuration...
Page 162
162 c hapter 19: q in q c onfiguration network diagram figure 46 network diagram for qinq configuration configuration procedure 1 configure switch a and switch c. As the configuration performed on switch a and switch c is the same, configuration on switch c is omitted. # configure ethernet2/0/2 port...
Page 163
Qinq configuration example 163 n the following describes how a packet is forwarded from switch a to switch c. ■ as qinq is enabled on ethernet2/0/1 port of switch a, when a packet from the user’s private network reaches ethernet2/0/1 port of switch a, it is tagged with the default vlan tag of the po...
Page 164
164 c hapter 19: q in q c onfiguration.
Page 165: Elective
20 s elective q in q c onfiguration selective qinq overview selective qinq implementation on a switch 7750 ethernet switch, selective qinq can be implemented in the following ways. 1 enabling qinq on ports in this type of implementations, qinq is enabled on ports and a received packet is tagged with...
Page 166
166 c hapter 20: s elective q in q c onfiguration configuring selective qinq c caution: ■ you need to execute the vlan-vpn enable command on the inbound ports before performing the operations listed in table 100. ■ qinq is not applicable to ports with the voice vlan feature enabled. C caution: ■ typ...
Page 167
Selective qinq configuration example 167 selective qinq configuration example network requirements ■ switch a is a switch 7750. ■ enable qinq on gigabitethernet2/0/1 port. Set the pvid of the port to 8. ■ insert the tag of vlan 10 to packets of vlan 8 through vlan 15 as the outer vlan tag. Insert th...
Page 168
168 c hapter 20: s elective q in q c onfiguration # configure the port to permit the packets of all the vlans. [switcha-gigabitethernet2/0/1] port hybrid vlan 1 to 4094 untagged # set the pvid of the port to 8. [switcha-gigabitethernet2/0/1] port hybrid pvid vlan 8 # enable qinq. [switcha-gigabiteth...
Page 169: Hared
21 s hared vlan c onfiguration shared vlan overview shared vlan is special vlan which is created based on i/o modules of the device. It is designed to avoid packet broadcast in the applications of selective qinq. Generation of shared vlan like a qinq-enabled port, a port with the selective qinq enab...
Page 170
170 c hapter 21: s hared vlan c onfiguration working principle of shared vlan after shared vlan is configured, all the mac address entries learned by ports will be maintained on the mac address forwarding table of the shared vlan, which can be used to forward all the vlan packets in the device. With...
Page 171
Shared vlan configuration example 171 shared vlan configuration example network requirements ■ the selective qinq feature is enabled on the hybrid port ethernet2/0/6 which is connected to the customer network. The outer tag of vlan 4 is inserted to packets of vlan 3 in the customer network, and thes...
Page 172
172 c hapter 21: s hared vlan c onfiguration.
Page 173: Ort
22 p ort b asic c onfiguration ethernet port configuration configuring the basic settings of an ethernet port use the following two tables when setting the duplex mode and rate of an ethernet port. Table 105 configure the basic settings of an ethernet port operation command description enter system ...
Page 174
174 c hapter 22: p ort b asic c onfiguration configuring port auto-negotiation speed you can configure an auto-negotiation speed for a port by using the speed auto command. Take a 10/100/1000 mbps port as an example. ■ if you expect that 10 mbps is the only available auto-negotiation speed of the po...
Page 175
Ethernet port configuration 175 n ■ only ports on the front panel of the device support the auto-negotiation speed configuration feature. And ports on the extended interface module do not support this feature currently. ■ after you configure auto-negotiation speed(s) for a port, if you execute the u...
Page 176
176 c hapter 22: p ort b asic c onfiguration enabling flow control on a port flow control is enabled on both the local and peer switches. If congestion occurs on the local switch: ■ the local switch sends a message to notify the peer switch of stopping sending packets to itself temporarily. ■ the pe...
Page 177
Ethernet port configuration 177 copying the configuration of a port to other ports to make some other ports have the same configuration as that of a specific port, you can copy the configuration of the specific port to the ports. Specifically, the following types of port configuration can be copied ...
Page 178
178 c hapter 22: p ort b asic c onfiguration configuring loopback detection for a port loopback detection is used to monitor if loopback occurs on a switch port. After you enable loopback detection on ethernet ports, the switch can monitor if external loopback occurs on each port periodically. If lo...
Page 179
Ethernet port configuration 179 last 100 seconds input: 0 packets/sec 0 bytes/sec last 100 seconds output: 0 packets/sec 0 bytes/sec setting speedup for a port perform the following configuration to speed up the hardware in a port or out of a port. C caution: ■ the hardspeedup enable/disable command...
Page 180
180 c hapter 22: p ort b asic c onfiguration displaying basic port configuration after the above configurations, you can execute the display commands in any view to display information about ethernet ports, so as to verify your configurations. You can execute the reset counters interface command in ...
Page 181
Troubleshooting ethernet port configuration 181 network diagram figure 50 network diagram for ethernet port configuration configuration procedure n ■ only the configuration for switch a is listed below. The configuration for switch b is similar to that of switch a. ■ this example supposes that vlan ...
Page 182
182 c hapter 22: p ort b asic c onfiguration.
Page 183: Ink
23 l ink a ggregation c onfiguration overview introduction to link aggregation link aggregation aggregates multiple physical ethernet ports into one logical link, also called an aggregation group. It allows you to increase bandwidth by distributing incoming/outgoing traffic on the member ports in th...
Page 184
184 c hapter 23: l ink a ggregation c onfiguration operational key when aggregating ports, link aggregation control automatically assigns each port an operational key based on its rate, duplex mode, and other basic configurations. ■ in a manual or static lacp aggregation group, the selected ports sh...
Page 185
Overview 185 port, you cannot remove the port unless you remove the whole aggregation group. Lacp is enabled on the member ports of static aggregation groups, and disabling lacp on such a port will not take effect. When you remove a static aggregation group, the system will remain the member ports o...
Page 186
186 c hapter 23: l ink a ggregation c onfiguration besides multiple-port aggregation groups, the system is also able to create single-port aggregation groups, each of which contains only one port. Lacp is enabled on the member ports of dynamic aggregation groups. Port status of dynamic aggregation g...
Page 187
Overview 187 n if devices at one side of the link aggregation group use type-a modules and devices at the other side of the group use modules other than type a, when the number of ports exceeds eight and the number of selected ports reaches to eight in the link aggregation group, packets may be lost...
Page 188
188 c hapter 23: l ink a ggregation c onfiguration aggregation group categories depending on whether or not load sharing is implemented, aggregation groups can be load-sharing or non-load-sharing aggregation groups. In general, the system only provides limited load-sharing aggregation resources, so ...
Page 189
Link aggregation configuration 189 ■ an aggregation group containing special ports (such as 10ge port) which require hardware aggregation resources has higher priority than any aggregation group containing no special port. ■ a manual or static aggregation group has higher priority than a dynamic agg...
Page 190
190 c hapter 23: l ink a ggregation c onfiguration note that: 1 when creating an aggregation group: ■ if the aggregation group you are creating already exists but contains no port, its type will change to the type you set. ■ if the aggregation group you are creating already exists and contains ports...
Page 191
Link aggregation configuration 191 n for a static lacp aggregation group or a manual aggregation group, you are recommended not to cross cables between the two devices at the two ends of the aggregation group. For example, suppose port 1 of the local device is connected to port 2 of the peer device....
Page 192
192 c hapter 23: l ink a ggregation c onfiguration ■ when a dynamic aggregation group or a static aggregation group is changed into a manual aggregation group, the system will disable lacp on all the member ports automatically. When a dynamic aggregation group is changed into a static aggregation gr...
Page 193
Link aggregation configuration example 193 link aggregation configuration example network requirements ■ switch a connects to switch b with three ports ethernet 2/0/1 to ethernet 2/0/3. It is required that incoming/outgoing load between the two switch can be shared among the three ports. ■ adopt thr...
Page 194
194 c hapter 23: l ink a ggregation c onfiguration # create static aggregation group 1. [sw7750] link-aggregation group 1 mode static # add ethernet 2/0/1 through ethernet 2/0/3 to aggregation group 1. [sw7750] interface ethernet2/0/1 [sw7750-ethernet2/0/1] port link-aggregation group 1 [sw7750-ethe...
Page 195: Ort
24 p ort i solation c onfiguration port isolation overview introduction to port isolation through the port isolation feature, you can add the ports to be controlled into an isolation group to isolate layer 2 and layer 3 data between ports in the isolation group. Thus, it can improve network security...
Page 196
196 c hapter 24: p ort i solation c onfiguration n ■ an ethernet port belongs to only one port isolation group. If you add an ethernet port to different isolation groups, the port belongs to only the latest isolation group to which the port is added. ■ currently, modules of type a (3c16860, 3c16861,...
Page 197
Port isolation configuration example 197 [sw7750-port-isolate-group1] port ethernet2/0/2 to ethernet2/0/4 # display information about the ports in the isolation group. [sw7750-port-isolate-group1] display isolate port isolate group id: 1 isolated port(s) in group 1: ethernet2/0/2 ethernet2/0/3 ether...
Page 198
198 c hapter 24: p ort i solation c onfiguration.
Page 199: Ort
25 p ort s ecurity c onfiguration n currently, a type modules (3c16860, 3c16860, 3c16861, 3c16861, ls81fs24a, ls81fs24, 3c16858, 3c16858, 3c16859, and 3c16859) do not support the port security feature. Port security overview introduction port security is a security mechanism for network access contr...
Page 200
200 c hapter 25: p ort s ecurity c onfiguration table 129 description of port security modes security mode description feature autolearn in this mode, the port automatically learns mac addresses and changes them to security mac addresses. This security mode will automatically change to the secure mo...
Page 201
Port security overview 201 n ■ when a port works in the mac-else-userlogin-secure mode or the mac-else-userlogin-secure-ext mode, for the same packet, intrusion protection can be triggered only after both mac authentication and 802.1x authentication fail. ■ when a port works in the userlogin-secure-...
Page 202
202 c hapter 25: p ort s ecurity c onfiguration port security configuration enabling port security c caution: enabling port security resets the following configurations on the ports to the defaults (shown in parentheses below) ■ 802.1x (disabled), port access control method (macbased), and port acce...
Page 203
Port security configuration 203 this configuration is different from that of the maximum number of mac addresses that can be leaned by a port in mac address management. Setting the port security mode n ■ before setting the port security mode to autolearn, you need to set the maximum number of mac ad...
Page 204
204 c hapter 25: p ort s ecurity c onfiguration ■ voice vlan configuring port security features configuring the ntk feature configuring intrusion protection n the port-security timer disableport command is used in conjunction with the port-security intrusion-mode disableport-temporarily command to s...
Page 205
Port security configuration 205 configuring security mac addresses security mac addresses are special mac addresses that never age out. One security mac address can be added to only one port in the same vlan so that you can bind a mac address to one port in the same vlan. Security mac addresses can ...
Page 206
206 c hapter 25: p ort s ecurity c onfiguration displaying port security configuration after the above configuration, you can use the display command in any view to display port security information and verify your configuration. Port security configuration example port security configuration exampl...
Page 207
Port security configuration example 207 # set the maximum number of mac addresses allowed on the port to 80. [sw7750-gigabitethernet2/0/1] port-security max-mac-count 80 # set the port security mode to autolearn. [sw7750-gigabitethernet2/0/1] port-security port-mode autolearn [sw7750-gigabitethernet...
Page 208
208 c hapter 25: p ort s ecurity c onfiguration.
Page 209: Ort
26 p ort b inding c onfiguration n currently, a type modules (3c16860, 3c16860, 3c16861, 3c16861, ls81fs24a, ls81fs24, 3c16858, 3c16858, 3c16859, and 3c16859) do not support the port binding feature. Port binding overview introduction port binding enables the network administrator to bind the mac ad...
Page 210
210 c hapter 26: p ort b inding c onfiguration port binding configuration example network requirements it is required to bind the mac and ip addresses of host a to ethernet 2/0/1 on switch a, so that ethernet 2/0/1 can only forward packets coming from or going to host a. Network diagram figure 54 ne...
Page 211: Dldp C
27 dldp c onfiguration overview introduction you may have encountered unidirectional links in networking. When a unidirectional link occurs, the local device can receive packets from the peer device through the link layer, but the peer device cannot receive packets from the local device. Unidirectio...
Page 212
212 c hapter 27: dldp c onfiguration figure 56 fiber broken or not connected dldp provides the following features: ■ as a link layer protocol, it works together with the physical layer protocols to monitor the link status of a device. ■ the auto-negotiation mechanism at the physical layer detects ph...
Page 213
Dldp fundamentals 213 table 142 dldp packet types dldp packet type function advertisement notifies the neighbor devices of the existence of the local device. An advertisement packet carries only the local port information, and it does not require response from the peer end. Rsy-advertisement packets...
Page 214
214 c hapter 27: dldp c onfiguration 1 if the dldp-enabled link is up, dldp sends dldp packets to the peer device, and analyzes/processes the dldp packets received from the peer device. Dldp packets sent in different dldp states are of different types. 2 a dldp packet received is processed as follow...
Page 215
Dldp fundamentals 215 dldp status a link can be in one of these dldp states: initial, inactive, active, advertisement, probe, disable, and delaydown. Dldp timers table 145 processing procedure when no echo packet is received from the neighbor no echo packet received from the neighbor processing proc...
Page 216
216 c hapter 27: dldp c onfiguration echo waiting timer it is enabled when dldp enters the probe state. The echo waiting timer length is 10 seconds. If no echo packet is received from the neighbor when the echo waiting timer expires, the state of the local end is set to unidirectional link (one-way ...
Page 217
Dldp fundamentals 217 dldp operating mode dldp can operate in two modes: normal and enhanced. Dldp neighbor state a dldp neighbor can be in one of these two states: two way and unknown. You can check the state of a dldp neighbor by using the display dldp command. Delaydown timer when a device in the...
Page 218
218 c hapter 27: dldp c onfiguration link auto-recovery mechanism if the shutdown mode of a port is set to auto shutdown, the port is set to the dldp down state when dldp detects the link connecting to the port is a unidirectional link. A port in dldp down state does not forward service packets or r...
Page 220
220 c hapter 27: dldp c onfiguration n ■ when you use the dldp enable/dldp disable command in system view to enable/disable dldp globally on all optical ports of the switch, this command is only valid for existing optical ports on the device, however, it is not valid for those added subsequently. ■ ...
Page 221
Dldp configuration 221 c caution: ■ this command only applies to the ports in dldp down status. ■ if a port is dldp down, it can return to the up state automatically. You do not need to reset dldp on the port. Precautions during dldp configuration ■ dldp does not work on a port where you configure d...
Page 222
222 c hapter 27: dldp c onfiguration for xgbus products, pay attention to the following points: ■ when interface modules are hot swapped, if the plugged interface module is of the same type as the pulled interface module, dldp restores automatically. ■ when active/standby switchover is performed on ...
Page 223
Dldp network example 223 # set the interval of sending dldp packets to 15 seconds [sw7750a] dldp interval 15 # configure dldp to work in enhanced mode [sw7750a] dldp work-mode enhance # set the dldp handling mode to auto after unidirectional links are detected [sw7750a] dldp unidirectional-shutdown ...
Page 224
224 c hapter 27: dldp c onfiguration.
Page 225: Mac A
28 mac a ddress t able m anagement n this chapter describes the management of static and dynamic mac address entries. For information on the management of multicast mac address entries, refer to “multicast overview” on page 413. Overview introduction to mac address learning an ethernet switch mainta...
Page 226
226 c hapter 28: mac a ddress t able m anagement figure 58 packets forwarded by using a mac address table. After learning the source address of the packet, the switch searches the mac address table for the destination mac address of the received packet: ■ if it finds a match, it directly forwards th...
Page 227
Configuring mac address table management 227 ■ static mac address entry: also known as permanent mac address entry. This type of mac address entries are added/removed manually and can not age out by themselves. Using static mac address entries can reduce broadcast packets remarkably and are suitable...
Page 228
228 c hapter 28: mac a ddress t able m anagement c caution: for a mac address entry to be added, the port specified by the interface keyword must belong to the vlan specified by the vlan keyword in the command. Otherwise, the entry will not be added. Setting the aging time for mac address entries se...
Page 229
Configuring mac address table management 229 disabling mac address learning to gain better control over network security, you can use the following commands to disable the current port from learning mac addresses. N ■ do not use the mac-address mac-learning disable command together with related 802....
Page 230
230 c hapter 28: mac a ddress t able m anagement higig ports are special ports on modules for connecting the modules to the backplane. Higig ports can also learn and synchronize mac addresses. With such characteristics, higig ports may bring about the following issue: with mac address learning disab...
Page 231
Configuration example 231 configuration example network requirements ■ log in to the switch through the console port and enable address table configuration. ■ set the aging time of dynamic mac address entries to 500 seconds. ■ add a static mac address entry 000f-e235-dc71 for ethernet2/0/2 port (ass...
Page 232
232 c hapter 28: mac a ddress t able m anagement.
Page 233: Entralized
29 c entralized mac a ddress a uthentication c onfiguration n currently, 3c16860, 3c16861, ls81fs24a, 3c16859, and 3c16858 i/o modules of 3com switch 7750 ethernet switches do not support the centralized mac address authentication. Centralized mac address authentication overview centralized mac addr...
Page 234
234 c hapter 29: c entralized mac a ddress a uthentication c onfiguration centralized mac address authentication configuration the following are centralized mac address authentication configuration tasks: ■ “enabling centralized mac address authentication globally” on page 234 ■ “enabling centralize...
Page 235
Centralized mac address authentication configuration 235 centralized mac address authentication for a port can be configured but does not take effect before global centralized mac address authentication is enabled. After global centralized mac address authentication is enabled, ports enabled with th...
Page 236
236 c hapter 29: c entralized mac a ddress a uthentication c onfiguration configuring the timers used in centralized mac address authentication the following timers are used in centralized mac address authentication: ■ offline detect timer, which sets the time interval for a switch to test whether a...
Page 237
Displaying and debugging centralized mac address authentication 237 n ■ if the mac address regular re-authentication function is enabled, when the reauth-period times out, the device initiates a re-authentication. ■ when you configure to re-authenticate a user with the specified mac address, each ma...
Page 238
238 c hapter 29: c entralized mac a ddress a uthentication c onfiguration ■ in mac address mode, mac address of user authenticated by radius server need to be configured as both user name and password on the radius server. Network requirement as shown in the following figure, a user workstation (sup...
Page 239
Centralized mac address authentication configuration example 239 [sw7750] mac-authentication timer offline-detect 180 [sw7750] mac-authentication timer quiet 30 for domain-related configuration, refer to the “802.1x configuration example” on page 404..
Page 240
240 c hapter 29: c entralized mac a ddress a uthentication c onfiguration.
Page 241: Mstp C
30 mstp c onfiguration mstp overview spanning tree protocol (stp) cannot enable ethernet ports to transit their states rapidly. It costs two times of the forward delay for a port to transit to the forwarding state even if the port is on a point-to-point link or the port is an edge port. This slows d...
Page 242
242 c hapter 30: mstp c onfiguration figure 60 basic mstp terminologies mst region an mst region (multiple spanning tree region) comprises multiple physically-interconnected mstp-enabled switches and the corresponding network segments connected to these switches. These switches have the same region ...
Page 243
Mstp overview 243 ist an internal spanning tree (ist) is a spanning tree in an mst region. Ists together with the common spanning tree (cst) form the common and internal spanning tree (cist) of the entire switched network. An ist is a special msti; it belongs to an mst region and is a branch of cist...
Page 244
244 c hapter 30: mstp c onfiguration form a loop. Port 3 and port 4 on switch d connect downstream to other mst regions. This figure shows the roles these ports play. N ■ a port can play different roles in different mstis. ■ the role a region edge port plays is consistent with the role it plays in t...
Page 245
Mstp overview 245 implementation of mstp mstp divides a network into multiple mst regions at layer 2. The cst is generated between these mst regions, and multiple spanning trees (or, mstis) can be generated in each mst region. As well as rstp, mstp uses configuration bpdus to generate spanning trees...
Page 246
246 c hapter 30: mstp c onfiguration for each switch in a network, the port through which the configuration bpdu with the highest priority is received is chosen as the root port of the switch. ■ determining the designated port first, the switch generates a designated port configuration bpdu for each...
Page 247
Root bridge configuration 247 n in a network that contains switches with both gvrp and mstp employed, gvrp packets are forwarded along the cist. If you want to broadcast packets of a specific vlan through gvrp, be sure to map the vlan to the cist when configuring the mstp vlan mapping table (the cis...
Page 248
248 c hapter 30: mstp c onfiguration configuring mst region-related parameters (especially the vlan mapping table) results in spanning trees being regenerated. To reduce network topology jitter caused by the configuration, mstp does not regenerate spanning trees immediately after the configuration; ...
Page 249
Root bridge configuration 249 root bridge/secondary root bridge configuration mstp can automatically choose a switch as a root bridge. You can also manually specify the current switch as a root bridge by using the corresponding commands. Root bridge configuration secondary root bridge configuration ...
Page 250
250 c hapter 30: mstp c onfiguration spanning tree instance on two or more switches using the stp root secondary command. ■ you can also configure the current switch as the root bridge by setting the priority of the switch to 0. Note that once a switch is configured as the root bridge or a secondary...
Page 251
Root bridge configuration 251 rstp-enabled switches, you can configure the current mstp-enabled switch to operate in this mode by using the stp mode rstp command. ■ mstp mode: in this mode, the protocol packets sent out of the ports of the switch are mstp packets, or stp packets if the ports have st...
Page 252
252 c hapter 30: mstp c onfiguration configuration example # configure the maximum hops of the mst region to be 30 (assuming that the current switch operates as the region root). System-view [sw7750] stp max-hops 30 network diameter configuration in a switched network, any two switches can communica...
Page 253
Root bridge configuration 253 ■ the hello time parameter is for link testing. A switch regularly sends hello packets to other switches in the interval specified by the hello time parameter to test the links. ■ the max age parameter is used to judge whether or not a configuration bpdu is obsolete. Ob...
Page 254
254 c hapter 30: mstp c onfiguration as for the configuration of these three time-related parameters (that is, the hello time, forward delay, and max age parameters), the following formulas must be met to prevent network jitter. 2 x (forward delay - 1 second) >= max age max age >= 2 x (hello time + ...
Page 255
Root bridge configuration 255 parameter. It depends on the physical state of the port and network structure. You can configure this parameter according to the network. Configuration procedure (in system view) configuration procedure (in ethernet port view) as the maximum transmitting speed parameter...
Page 256
256 c hapter 30: mstp c onfiguration configuration procedure (in system view) configuration procedure (in ethernet port view) on a switch with bpdu protection not enabled, an edge port becomes a non-edge port again once it receives a bpdu from another port. N you are recommended to configure the eth...
Page 257
Root bridge configuration 257 configuration procedure (in system view) configuration procedure (in ethernet port view) n among aggregated ports, you can only configure the links of master ports as point-to-point links. If an auto-negotiating port operates in full duplex mode after negotiation, you c...
Page 258
258 c hapter 30: mstp c onfiguration configuration example # configure the link connected to port ethernet1/0/1 as a point-to-point link. 1 configure in system view. System-view [sw7750] stp interface ethernet1/0/1 point-to-point force-true 2 configure in ethernet port view. System-view [sw7750] int...
Page 259
Leaf node configuration 259 configuration example # enable mstp on the switch and disable mstp on ethernet1/0/1 port. 1 configure in system view. System-view [sw7750] stp enable [sw7750] stp interface ethernet1/0/1 disable 2 configure in ethernet port view. System-view [sw7750] stp enable [sw7750] i...
Page 260
260 c hapter 30: mstp c onfiguration mst region configuration refer to “mst region configuration” on page 247. Mstp operation mode configuration refer to “mstp operation mode configuration” on page 250. Timeout time factor configuration refer to “timeout time factor configuration” on page 254. Maxim...
Page 261
Leaf node configuration 261 normally, the path cost of a port operating in full-duplex mode is slightly less than that of the port operating in half-duplex mode. When calculating the path cost of an aggregated link, the 802.1d-1998 standard does not take the number of the ports on the aggregated lin...
Page 262
262 c hapter 30: mstp c onfiguration changing the path cost of a port may change the role of the port and put it in state transition. Executing the stp cost command with the instance-id argument being 0 sets the path cost on the cist for the port. Configuration example (a) # configure the path cost ...
Page 263
The mcheck configuration 263 configuring port priority in ethernet port view changing port priority of a port may change the role of the port and put the port into state transition. A smaller port priority value indicates a higher possibility for the port to become the root port. If all the ports of...
Page 264
264 c hapter 30: mstp c onfiguration mstp-enabled switch, the port cannot automatically transit to the mstp operation mode. It remains in the stp-compatible mode. In this case, you can force the port to transit to the mstp mode by performing the mcheck operation on the port. Prerequisites mstp runs ...
Page 265
Protection function configuration 265 normally, no configuration bpdu will reach edge ports. But malicious users can attack a network by sending configuration bpdus deliberately to edge ports to cause network jitter. You can prevent this type of attacks by utilizing the bpdu protection function. Wit...
Page 266
266 c hapter 30: mstp c onfiguration mac address tables frequently and negative effects to stp calculation and network stability. You can use the stp tc-protection threshold command to set a threshold for the times of removing mac address tables in a period. If the number of received tc-bpdus is les...
Page 267
Protection function configuration 267 configuration example # enable the root guard function on ethernet1/0/1 port. 1 configure in system view. System-view [sw7750] stp interface ethernet1/0/1 root-protection 2 configure in ethernet port view. System-view [sw7750] interface ethernet1/0/1 [sw7750-eth...
Page 268
268 c hapter 30: mstp c onfiguration system-view [sw7750] interface ethernet1/0/1 [sw7750-ethernet1/0/1] stp loop-protection tc-bpdu attack prevention configuration configuration prerequisites mstp is enabled on the current switch. Configuration procedure configuration example # enable the tc-bpdu a...
Page 269
Rapid transition configuration 269 the bpdus to be send to the partner’s switch. In this way, the switch 7750s can interwork with the partners’ switches in the same mst region. Digest snooping configuration configure the digest snooping feature on a switch to enable it to interwork with other switch...
Page 270
270 c hapter 30: mstp c onfiguration ■ proposal packets: packets sent by designated ports to request rapid transition ■ agreement packets: packets used to acknowledge rapid transition requests both rstp and mstp switches can perform rapid transition operation on a designated port only when the port ...
Page 271
Rapid transition configuration 271 on the downstream switch receives no agreement packet from the upstream switch and thus sends no agreement packets to the upstream switch. As a result, the designated port of the upstream switch fails to transit rapidly and can only change to the forwarding state a...
Page 272
272 c hapter 30: mstp c onfiguration configuration procedure 1 configure the rapid transition feature in system view. 2 configure in ethernet port view. N ■ the rapid transition feature can be enabled on root ports or alternate ports only. ■ if you configure the rapid transition feature on the desig...
Page 273
Bpdu tunnel configuration 273 figure 65 bpdu tunnel network hierarchy bpdu tunnel configuration configuration prerequisites mstp is enabled on the current switch. Configuration procedure n ■ the bpdu tunnel function can only be enabled on devices with stp enabled. ■ the bpdu tunnel function can only...
Page 274
274 c hapter 30: mstp c onfiguration stp maintenance configuration introduction in a large-scale network with mstp enabled, there may be many mstp instances, and so the status of a port may change frequently. In this case, maintenance personnel may expect that log/trap information is output to the l...
Page 275
Mstp implementation example 275 mstp implementation example network requirements implement mstp in the network shown in figure 66 to enable packets of different vlans to be forwarded along different spanning tree instances. The detailed configurations are as follows: ■ all switches in the network be...
Page 276
276 c hapter 30: mstp c onfiguration # specify switch a as the root bridge of spanning tree instance 1. [sw7750] stp instance 1 root primary 2 configure switch b. # enter mst region view. System-view [sw7750] stp region-configuration # configure the mst region. [sw7750-mst-region] region-name exampl...
Page 277
Bpdu tunnel configuration example 277 [sw7750-mst-region] region-name example [sw7750-mst-region] instance 1 vlan 10 [sw7750-mst-region] instance 3 vlan 30 [sw7750-mst-region] instance 4 vlan 40 [sw7750-mst-region] revision-level 0 # activate the settings of the mst region. [sw7750-mst-region] activ...
Page 278
278 c hapter 30: mstp c onfiguration system-view [sw7750] stp enable # add port ethernet1/0/1 to vlan 10. [sw7750] vlan 10 [sw7750-vlan10] port ethernet 1/0/1 3 configure switch c. # enable mstp. System-view [sw7750] stp enable # enable the bpdu tunnel function. [sw7750] vlan-vpn tunnel # add port e...
Page 279
Bpdu tunnel configuration example 279 # disable stp on port ethernet1/0/2 and then enable the vlan-vpn function on it. [sw7750] interface ethernet 1/0/2 [sw7750-ethernet1/0/2] port access vlan 10 [sw7750-ethernet1/0/2] stp disable [sw7750-ethernet1/0/2] vlan-vpn enable [sw7750-ethernet1/0/2] quit # ...
Page 280
280 c hapter 30: mstp c onfiguration.
Page 281: Ip R
31 ip r outing p rotocol o verview n when running a routing protocol, the ethernet switch also functions as a router. The word “router” and the router icons covered in the following text represent routers in common sense and ethernet switches running a routing protocol. To improve readability, this ...
Page 282
282 c hapter 31: ip r outing p rotocol o verview routes. The one with the highest preference (the smallest numerical value) will be selected as the current optimal route. According to different destinations, routes fall into the following categories: ■ subnet route: the destination is a subnet. ■ ho...
Page 283
Routing management policy 283 the switch 7750 ethernet switches (hereinafter referred to as the switch 7750) support the configuration of static routes as well as a series of dynamic routing protocols such as rip, ospf and bgp. Moreover, the switches in operation can automatically obtain some direct...
Page 284
284 c hapter 31: ip r outing p rotocol o verview except for direct routing, you can manually configure the preferences of various dynamic routing protocols as required. In addition, you can configure different preferences for different static routes. Traffic sharing and route backup traffic sharing ...
Page 285: Tatic
32 s tatic r oute c onfiguration introduction to static route static route static routes are special routes. They are manually configured by the administrator. By configuring static routes, you can build an interconnecting network. The problem for such configuration is when a fault occurs on the net...
Page 286
286 c hapter 32: s tatic r oute c onfiguration the packet; in this case, if there is no default route, the packet will be discarded, and an internet control message protocol (icmp) packet will be returned to inform the source host that the destination host or network is unreachable. Static route con...
Page 287
Static route configuration example 287 static route configuration example network requirements as shown in figure 69, it is required that all the hosts/layer 3 switches in the figure can communicate with each other by configuring static routes. Network diagram figure 69 static route configuration ta...
Page 288
288 c hapter 32: s tatic r oute c onfiguration configuration procedure n before the following configuration, make sure that the ethernet link layer works normally and the ip addresses of the vlan interfaces have been configured correctly. # configure static routes on switch a. System-view [switcha] ...
Page 289: Rip C
33 rip c onfiguration rip overview routing information protocol (rip) is a simple interior gateway protocol (igp) suitable for small-sized networks. Basic concepts rip rip is a distance-vector (d-v) algorithm-based protocol. It exchanges routing information via udp packets. Rip uses hop count (also ...
Page 290
290 c hapter 33: rip c onfiguration ■ garbage-collection timer: an unreachable route will be completely deleted from the routing table if no update packet for the route is received from the neighbor before this timer times out. Rip startup and operation the whole process of rip startup and operation...
Page 291
Basic rip configuration 291 basic rip configuration configuration prerequisites before configuring basic rip functions, perform the following tasks: ■ configuring the link layer protocol configuring rip route control setting the additional routing metrics of an interface optional “setting the additi...
Page 292
292 c hapter 33: rip c onfiguration ■ configuring the network layer addresses of interfaces so that adjacent nodes are reachable to each other at the network layer configuring basic rip functions enabling rip globally and on the interface of a specified network segment n ■ rip can be enabled on an i...
Page 293
Rip route control 293 rip route control in actual implementation, it may be needed to control rip routing information more accurately to accommodate complex network environments. By performing the configuration described in the following sections, you can: ■ control route selection by adjusting addi...
Page 294
294 c hapter 33: rip c onfiguration n the rip metricout command takes effect only on the rip routes learnt by the router and the rip routes generated by the router itself, but not on any route imported to rip from other routing protocols. Configuring rip route summary route summary means that differ...
Page 295
Rip route control 295 configuring rip to filter or advertise the received routes the route filtering function provided by a router enables you to configure inbound/outbound filter policy by specifying an acl or address prefix list to make rip filter incoming/outgoing routes. Besides, you can configu...
Page 296
296 c hapter 33: rip c onfiguration configuring rip to redistribute routes from another protocol n the allow-ibgp keyword is used to redistribute ibgp routes. Because the as-path attribute of redistributed ibgp routes is discarded, routing loops may occur. Therefore, use this keyword with caution. R...
Page 297
Rip network adjustment and optimization 297 configuration tasks configuring rip timers n when configuring the values of rip timers, you should take network performance into consideration and perform consistent configuration on all routers running rip to avoid unnecessary network traffic and network ...
Page 298
298 c hapter 33: rip c onfiguration simple authentication cannot provide complete security, because the authentication keys sent along with packets are not unencrypted. Therefore, simple authentication cannot be applied where high security is required. Configuring a rip neighbor displaying and maint...
Page 299
Rip configuration example 299 rip configuration example network requirements as shown in figure 70, switchc is connected to subnet 117.102.0.0 through an ethernet port. Switcha and switchb are connected to networks 155.10.1.0 and 196.38.165.0 respectively through ethernet ports. Switchc, switcha and...
Page 300
300 c hapter 33: rip c onfiguration # configure rip. System-view [switchc] rip [switchc-rip] network 117.102.0.0 [switchc-rip] network 110.11.2.0 troubleshooting rip configuration symptom: the layer 3 switch cannot receive any rip update packet when the physical connection between the switch and the...
Page 301: Ospf C
34 ospf c onfiguration ospf overview introduction to ospf open shortest path first (ospf) is a link state-based interior gateway protocol developed by ietf. At present, ospf version 2 (rfc 2328) is used, which has the following features: ■ high applicability: ospf supports networks of various sizes ...
Page 302
302 c hapter 34: ospf c onfiguration topology of the whole network. Obviously, all routers get exactly the same map. ■ a router uses the shortest path first (spf) algorithm to calculate the shortest path tree with itself as the root. The tree shows the routes to the nodes in the autonomous system. E...
Page 303
Ospf overview 303 some non-backbone areas on the edge of the as, you can configure these areas as stub areas. A stub area cannot import any external route. For this reason the concept nssa area (not-so-stubby area) is introduced. In an nssa area, type 7 lsas are allowed to be propagated. A type 7 ls...
Page 304
304 c hapter 34: ospf c onfiguration ■ non-broadcast multi-access (nbma): if frame relay, atm, or x.25 is adopted, ospf defaults the network type to nbma. In an nbma network, protocol packets are sent in unicast. ■ point-to-multipoint (p2mp): ospf will not default the network type of any link layer ...
Page 305
Ospf overview 305 in fact, a bdr provides backup for a dr. Dr and bdr are elected at the same time. Adjacencies are also established between the bdr and all the other routers on the segment, and routing information is also exchanged between them. Once the dr becomes invalid, the bdr becomes a dr. Si...
Page 306
306 c hapter 34: ospf c onfiguration ■ the dr on a network segment is not necessarily the router with the highest priority. Likewise, the bdr is not necessarily the router with the second-highest priority. Ospf packets ospf uses five types of packets: hello packet hello packets are most commonly use...
Page 307
Introduction to ospf configuration tasks 307 ■ as-external-lsa: type-5 lsa, also called ase lsa, generated by asbrs to describe the routes to other ass and advertised to the whole as (excluding stub areas). The default as route can also be described by as-external-lsas. Type-7 lsas in rfc 1587 (ospf...
Page 308
308 c hapter 34: ospf c onfiguration ospf network type configuration configuring the network type of an ospf interface optional “configuring the network type of an ospf interface” on page 312 setting an nbma neighbor optional “setting an nbma neighbor” on page 313 setting the dr priority on an ospf ...
Page 309
Basic ospf configuration 309 basic ospf configuration before you can configure other ospf features, you must first enable ospf and specify the interface and area id. Configuration prerequisites before configuring ospf, perform the following tasks: ■ configuring the link layer protocol ■ configuring ...
Page 310
310 c hapter 34: ospf c onfiguration configure router ids manually, make sure each router id is uniquely used by one router in the as. A common practice is to set the router id to the ip address of an interface on the router. ■ enabling ospf the switch 7750 supports multiple ospf processes. To enabl...
Page 311
Ospf area attribute configuration 311 ■ the id of an ospf process is unique. ■ one segment can belong to only one area and you must specify each ospf interface to belong to a particular area. Ospf area attribute configuration area partition in ospf reduces the number of lsas in the network and enhan...
Page 312
312 c hapter 34: ospf c onfiguration n ■ you must use the stub command on all the routers connected to a stub area to configure the area with the stub attribute. ■ you must use the nssa command on all the routers connected to an nssa area to configure the area with the nssa attribute. Ospf network t...
Page 313
Ospf route control 313 n ■ after an interface has been configured with a new network type, the original network type of the interface is removed automatically. ■ note that, neighboring relationship can be established between two interfaces configured as broadcast, nbma, or p2mp only if the interface...
Page 314
314 c hapter 34: ospf c onfiguration configuration prerequisites before configuring ospf route control, perform the following tasks: ■ configuring the network layer addresses of interfaces so that the adjacent nodes are reachable to each other at the network layer ■ completing basic ospf configurati...
Page 315
Ospf route control 315 fact, the filter-policy import command filters the routes calculated by ospf; only the routes passing the filter can be added to the routing table. Configuring the cost for sending packets on an ospf interface setting ospf route priority since multiple dynamic routing protocol...
Page 316
316 c hapter 34: ospf c onfiguration n ■ the import-route command cannot import a default route. To import the default route, you must use the default-route-advertise command. ■ the filtering of advertised routes by ospf means that ospf only converts the external routes meeting the filter criteria i...
Page 317
Ospf network adjustment and optimization 317 configuration prerequisites before adjusting and optimizing an ospf network, perform the following tasks: ■ configuring the network layer addresses of interfaces so that the adjacent nodes are reachable to each other at the network layer ■ configuring bas...
Page 318
318 c hapter 34: ospf c onfiguration configuring the lsa transmission delay n the transmission of ospf packets on a link also takes time. Therefore, a transmission delay should be added to the aging time of lsas before the lsas are transmitted. For a low-speed link, pay close attention on this confi...
Page 319
Ospf network adjustment and optimization 319 ■ after an ospf interface is set to be in silent status, the interface can still advertise its direct route. However, the hello packets from the interface will be blocked, and no neighboring relationship can be established on the interface. This enhances ...
Page 320
320 c hapter 34: ospf c onfiguration enabling ospf logging configuring ospf network management system (nms) displaying ospf configuration after the above configuration, you can use the display command in any view to display and verify the ospf configuration. You can use the reset command in user vie...
Page 321
Ospf configuration example 321 ospf configuration example configuring dr election based on ospf priority network requirements four switch 7750, switcha, switchb, switchc, and switchd, which run ospf, are on the same segment, as shown in figure 73. Perform proper configurations to make switcha and sw...
Page 322
322 c hapter 34: ospf c onfiguration network diagram figure 73 dr election based on ospf priority configuration procedure # configure switcha. System-view [switcha] interface vlan-interface 1 [switcha-vlan-interface1] ip address 196.1.1.1 255.255.255.0 [switcha-vlan-interface1] ospf dr-priority 100 ...
Page 323
Ospf configuration example 323 # configure switchd. System-view [switchd] interface vlan-interface 1 [switchd-vlan-interface1] ip address 196.1.1.4 255.255.255.0 [switchd] router id 4.4.4.4 [switchd] ospf [switchd-ospf-1] area 0 [switchd-ospf-1-area-0.0.0.0] network 196.1.1.0 0.0.0.255 on switcha, r...
Page 324
324 c hapter 34: ospf c onfiguration network diagram figure 74 ospf virtual link configuration configuration procedure # configure switcha. System-view [switcha] interface vlan-interface 1 [switcha-vlan-interface1] ip address 196.1.1.1 255.255.255.0 [switcha-vlan-interface1] quit [switcha] router id...
Page 325
Troubleshooting ospf configuration 325 [switchb-ospf-1-area-0.0.0.1] network 197.1.1.0 0.0.0.255 [switchb-ospf-1-area-0.0.0.1] vlink-peer 3.3.3.3 # configure switchc. System-view [switchc] interface vlan-interface 1 [switchc-vlan-interface1] ip address 152.1.1.1 255.255.255.0 [switchc-vlan-interface...
Page 326
326 c hapter 34: ospf c onfiguration ■ if the network type is broadcast or nbma, ensure that there is at least one interface with a priority greater than zero. ■ if an area is set to a stub area, ensure that the area is set to a stub area for all the routers connected to this area. ■ ensure that the...
Page 327: Is-Is C
35 is-is c onfiguration is-is overview the intermediate system-to-intermediate system (is-is) is a dynamic routing protocol standardized by the international organization for standardization (iso) to operate on connectionless network protocol (clnp). The is-is routing protocol has been adopted in rf...
Page 328
328 c hapter 35: is-is c onfiguration is-is network types is-is supports two network types: ■ broadcast networks, such as ethernet and token-ring ■ point-to-point networks, such as ppp and hdlc for non-broadcast multi-access (nbma) network, such as atm, you need to configure point-to-point or broadc...
Page 329
Is-is overview 329 figure 76 is-is topology i figure 77 shows another is-is network topology. The level-1-2 routers connect the level-1 and level-2 routers, and form the is-is backbone together with the level-2 routers. There is no area defined as the backbone in this topology. The backbone is compo...
Page 330
330 c hapter 35: is-is c onfiguration is-is address structure address structure 1 nsap as shown in figure 78, an nsap address consists of the initial domain part (idp) and the domain specific part (dsp). The idp is equal to the network id field in the ip address, and the dsp is equal to the subnet a...
Page 331
Is-is overview 331 the nsap selector (sel), sometimes present in n-sel, is used as the protocol identifier in ip. Different transmission protocols use different sels. All sels in ip are 00. Because the area is explicitly defined in the address structure, the level-1 router can easily recognize the p...
Page 332
332 c hapter 35: is-is c onfiguration introduction to is-is configuration table 251 is-is configuration tasks configuration task description related section integrated is-is configuration enable is-is. Required “enabling is-is” on page 334 configure a net required “configuring a net” on page 334 ena...
Page 333
Is-is basic configuration 333 is-is basic configuration all configuration tasks, except enabling is-is, are optional. This section covers the following topics: 1 is-is basic configuration ■ enabling is-is ■ configuring a net ■ enabling is-is on the specified interface ■ configuring dis priority ■ co...
Page 334
334 c hapter 35: is-is c onfiguration ■ configuring routing cost type ■ configuring link state routing cost ■ configuring lsp parameters ■ configuring spf parameters 4 networking configuration ■ configuring authentication ■ configuring overload tag ■ configuring adjacency state output ■ configuring ...
Page 335
Is-is basic configuration 335 higher priority a dis has, the more likely it is to be chosen. If two or more routers with the highest priorities exist on the broadcast network, the router that has the greatest mac address will be chosen. For adjacent routers that have the same priority of 0, the rout...
Page 336
336 c hapter 35: is-is c onfiguration n ■ for more information about route redistribution, refer to “ip routing policy configuration” on page 378. ■ the allow-ibgp keyword is used to redistribute ibgp routes. Because the as-path attribute of redistributed ibgp routes is discarded, routing loops may ...
Page 337
Is-is basic configuration 337 configuring route leaking through route leaking, a level-2 router can send the level-1 area routing information and level-2 area routing information that it knows to a level-1 router. Configuring route summarization you can configure the routes having the same ip prefix...
Page 338
338 c hapter 35: is-is c onfiguration configuring a cost style in is-is routing protocol, routing cost of a link can be expressed in one of the following two modes: ■ narrow: in this mode, routing cost ranges from 1 to 63. ■ wide: in this mode, routing cost ranges from 1 to 2 24 -1, namely, 1 to 167...
Page 339
Is-is basic configuration 339 configuring the csnp packets sending interval csnp packets are the packets sent with the synchronous lsdb by the dis on a broadcast network. Csnp packets are broadcast periodically on a broadcast network. You can configure the interval of sending csnp packets. Configuri...
Page 340
340 c hapter 35: is-is c onfiguration configuring the number of hello packets expected from the remote router before it is considered dead in is-is, hello packets are sent and received to maintain router neighbor relationships. If a router does not receive any hello packet from a neighboring router ...
Page 341
Is-is basic configuration 341 predefined. If domain authentication is also required on other routers at the backbone layer (level-2), the authentication works normally only if the authentication mode and password of these routers are the same as those of the neighboring routers. Configuring is-is to...
Page 342
342 c hapter 35: is-is c onfiguration configuring overload tag a failure of a router in an is-is domain will cause errors in the routing of the whole domain. To avoid this, you can configure the overload for the routers. When the overload tag is set, other routers will not ask the router to forward ...
Page 343
Is-is basic configuration 343 assigning an lsp maximum aging time an lsp is given a maximum aging value when it is generated by the router. When the lsp is sent to other routers, its maximum aging value goes down gradually. If the router does not get the update for the lsp before the maximum aging v...
Page 344
344 c hapter 35: is-is c onfiguration configuring spf to release cpu resources automatically in is-is, spf calculation may occupy system resources for a long time and slow down console response. To avoid this, you can configure spf to automatically release cpu resources each time a specified number ...
Page 345
Displaying integrated is-is configuration 345 resetting configuration data of an is-is peer displaying integrated is-is configuration after the above-mentioned configuration, you can use the display command in any view to display the is-is running state. By performing the following operations, you c...
Page 346
346 c hapter 35: is-is c onfiguration network diagram figure 79 network diagram for is-is basic configuration configuration procedure # configure switch a. System-view [switcha] isis [switcha-isis] network-entity 86.0001.0000.0000.0005.00 [switcha] interface vlan-interface 100 [switcha-vlan-interfac...
Page 347
Integrated is-is configuration example 347 [switchc-vlan-interface101] isis enable [switchc] interface vlan-interface 100 [switchc-vlan-interface100] ip address 200.20.0.1 255.255.255.0 [switchc-vlan-interface100] isis enable # configure switch d. [switchd] isis [switchd-isis] network-entity 86.0001...
Page 348
348 c hapter 35: is-is c onfiguration.
Page 349: Bgp C
36 bgp c onfiguration bgp overview introduction to bgp border gateway protocol (bgp) is a dynamic routing protocol designed to be used between autonomous systems (as). An as is a group of routers that adopt the same routing policy and belong to the same technical management department. Four versions...
Page 350
350 c hapter 36: bgp c onfiguration ■ ibgp (internal bgp) ■ ebgp (external bgp) when bgp runs inside an as, it is called interior bgp (ibgp); when bgp runs among different ass, it is called exterior bgp (ebgp). Bgp message type format of a bgp packet header bgp is message-driven. There are five type...
Page 351
Bgp overview 351 ■ version: bgp version. As for bgp-4, the value is 4. ■ my autonomous system: local as number. By comparing this filed of both sides, a router can determine whether the connection between itself and the bgp peer is of ebgp or ibgp. ■ hold time: hold time is to be determined when two...
Page 352
352 c hapter 36: bgp c onfiguration notification when bgp detects error state, it sends the notification message to peers and then tear down the bgp connection. Figure 83 shows the format of an notification message. Figure 83 bgp notification message format the fields of a notification message are d...
Page 353
Bgp overview 353 ■ a bgp speaker advertises the routes obtained from ebgp to all its bgp peers (including both ebgp and ibgp peers); ■ a bgp speaker does not advertise the routes obtained from ibgp to its ibgp peers; ■ a bgp speaker advertises the routes obtained from ibgp to its ebgp peers (in swit...
Page 354
354 c hapter 36: bgp c onfiguration bgp configuration tasks table 288 bgp configuration tasks configuration task description related section basic bgp configuration required “basic bgp configuration” on page 355 configuring the way to advertise/receive routing information importing routes optional “...
Page 355
Basic bgp configuration 355 basic bgp configuration configuration prerequisites before performing basic bgp configuration, you need to ensure: ■ network layer connectivity between adjacent nodes. Before performing basic bgp configuration, make sure the following are available. ■ local as number and ...
Page 356
356 c hapter 36: bgp c onfiguration c caution: ■ a router must be assigned a router id in order to run bgp protocol. A router id is a 32-bit unsigned integer. It uniquely identifies a router in an as. ■ a router id can be configured manually. If no router id is configured, the system will automatica...
Page 357
Configuring the way to advertise/receive routing information 357 importing routes with bgp employed, an as can send its interior routing information to its neighbor ass. However, the interior routing information is not generated by bgp, it is obtained by importing igp routing information to bgp rout...
Page 358
358 c hapter 36: bgp c onfiguration enabling default route advertising n with the peer default-route-advertise command executed, no matter whether the default route is in the local routing table or not, a bgp router sends a default route, whose next hop address is the local address, to the specified...
Page 359
Configuring the way to advertise/receive routing information 359 c caution: ■ only the routes that pass the specified filter are advertised. ■ a peer group member uses the same outbound route filtering policy as that of the peer group it belongs to. That is, a peer group adopts the same outbound rou...
Page 360
360 c hapter 36: bgp c onfiguration configuring bgp-igp route synchronization c caution: bgp-igp route synchronization is not supported on switch 7750 ethernet switches. Configuring bgp route dampening route dampening is used to solve the problem of route instability. Route instability mainly refers...
Page 361
Configuring bgp route attributes 361 configuring bgp load balance configuring bgp route attributes configuring bgp route attributes bgp possesses many route attributes for you to control bgp routing policies. Table 297 configure bgp route dampening operation command description enter system view sys...
Page 362
362 c hapter 36: bgp c onfiguration c caution: ■ using routing policy, you can configure the preference for the routes that match the filtering conditions. As for the unmatched routes, the default preference is adopted. ■ if other conditions are the same, the route with the lowest med value is prefe...
Page 363
Adjusting and optimizing a bgp network 363 adjusting and optimizing a bgp network adjusting and optimizing bgp network involves the following aspects: 1 bgp clock bgp peers send keepalive messages to each other periodically through the connections between them to make sure the connections operate pr...
Page 364
364 c hapter 36: bgp c onfiguration ■ value of bgp timer ■ interval for sending the update packets ■ md5 authentication password adjusting and optimizing a bgp network c caution: ■ the reasonable maximum interval for sending keepalive message is one third of the holdtime, and the interval cannot be ...
Page 365
Configuring a large-scale bgp network 365 ■ bgp soft reset can refresh the bgp routing table and apply a new routing policy without breaking the ngp connections. Configuring a large-scale bgp network in large-scale network, there are large quantities of peers. Configuring and maintaining the peer be...
Page 366
366 c hapter 36: bgp c onfiguration c caution: ■ it is not required to specify an as number for creating an ibgp peer group. ■ if there already exists a peer in a peer group, you can neither change the as number of the peer group, nor delete a specified as number through the undo command. Configurin...
Page 367
Configuring a large-scale bgp network 367 configuring bgp rr c caution: ■ normally, full connection is not required between an rr and a client. A route is reflected by an rr from a client to another client. If an rr and a client are fully connected, you can disable the reflection between clients to ...
Page 368
368 c hapter 36: bgp c onfiguration ■ if the confederation implementation mechanism of other routers is different from the rfc standardization, you can configure related command to make the confederation compatible with the non-standard routers. Displaying and maintaining bgp displaying bgp after th...
Page 369
Configuration example 369 bgp connection reset when a bgp routing policy or protocol changes, if you need to make the new configuration effective through resetting the bgp connection, perform the following configuration in user view. Clearing bgp information use the reset command in user view to cle...
Page 370
370 c hapter 36: bgp c onfiguration configuration procedure # configure switcha. [switcha] bgp 1001 [switcha-bgp] confederation id 100 [switcha-bgp] confederation peer-as 1002 1003 [switcha-bgp] group confed1002 external [switcha-bgp] peer 172.68.10.2 group confed1002 as-number 1002 [switcha-bgp] gr...
Page 371
Configuration example 371 network diagram figure 85 diagram for configuring a bgp rr configuration procedure 1 configure switcha. [switcha] interface vlan-interface 2 [switcha-vlan-interface2] ip address 192.1.1.1 255.255.255.0 [switcha-vlan-interface2] interface vlan-interface 100 [switcha-vlan-int...
Page 372
372 c hapter 36: bgp c onfiguration [switchb-bgp] group in internal [switchb-bgp] peer 193.1.1.1 group in 3 configure switchc. # configure vlan3. [switchc] interface vlan-interface 3 [switchc-vlan-interface3] ip address 193.1.1.1 255.255.255.0 # configure vlan4. [switchc] interface vlan-interface 4 ...
Page 373
Configuration example 373 network diagram figure 86 diagram for bgp routing configuration procedure 1 configure switch a. [switcha] interface vlan-interface 2 [switcha-vlan-interface2] ip address 192.1.1.1 255.255.255.0 [switcha] interface vlan-interface 3 [switcha-vlan-interface3] ip address 193.1....
Page 374
374 c hapter 36: bgp c onfiguration create an access control list to permit routing information sourced from the network 1.0.0.0. [switcha] acl number 2000 [switcha-acl-basic-2000] rule permit source 1.0.0.0 0.255.255.255 [switcha-acl-basic-2000] rule deny source any define two routing policies, nam...
Page 375
Configuration example 375 [switchc-bgp] group ex external [switchc-bgp] peer 193.1.1.1 group ex as-number 100 [switchc-bgp] group in internal [switchc-bgp] peer 195.1.1.1 group in [switchc-bgp] peer 194.1.1.2 group in 4 configure switch d. [switchd] interface vlan-interface 4 [switchd-vlan-interface...
Page 376
376 c hapter 36: bgp c onfiguration (switch b does not configure the local preference attribute, the default value is 100), switch d still chooses the route 1.0.0.0 coming from switch c first. Bgp error configuration example bgp peer connection establishment error symptom 1: a bgp neighbor relations...
Page 377: Ip R
37 ip r outing p olicy c onfiguration ip routing policy overview when a router distributes or receives routing information, it may need to implement some policies to filter the routing information, so as to receive or distribute only the routing information meeting given conditions. A routing protoc...
Page 378
378 c hapter 37: ip r outing p olicy c onfiguration destination network segment addresses or next-hop addresses of routing information. If an advanced acl is used, the specified range of source addresses will be used for matching. Ip-prefix ip-prefix plays a role similar to acl. But it is more flexi...
Page 379
Ip routing policy configuration 379 n refer to “acl configuration” on page 637. 2 you can have routing policy applied in the following cases: ■ when routes are imported ■ when routes are advertised/received configuring a route-policy a route-policy can comprise multiple nodes. Each node is a unit fo...
Page 380
380 c hapter 37: ip r outing p olicy c onfiguration defining if-match clauses for a route-policy node an if-match clause defines a matching rule, that is, a filtering condition that the routing information should satisfy for passing the current route-policy node. The matching objects are some attrib...
Page 381
Ip routing policy configuration 381 by default, no apply clause is defined. Note that, if the apply cost-type internal clause is defined for a route-policy node, when all the matching conditions of the node are met, igp cost will be used as the bgp med value when the system advertises igp routes to ...
Page 382
382 c hapter 37: ip r outing p olicy c onfiguration n among the items defined in an ip prefix list, at least one item should be in permit mode. The items in deny mode can be used to quickly filter out undesired routing information. But if all the items are in deny mode, no route will pass the filter...
Page 383
Displaying ip routing policy 383 routing costs of the source routing protocol, you should specify a routing cost for the imported routes. N the import-route command (used to import routes) is somewhat different in form in different routing protocol views. Refer to the import-route command descriptio...
Page 384
384 c hapter 37: ip r outing p olicy c onfiguration network diagram figure 87 filter routing information received configuration procedure 1 configure switcha: # configure the ip addresses of the interfaces. System-view [switcha] interface vlan-interface 100 [switcha-vlan-interface100] ip address 10....
Page 385
Troubleshooting ip routing policy 385 # apply route policy when the static routes are imported. [switcha] ospf [switcha-ospf-1] import-route static route-policy ospf 2 configure switchb: # configure the ip address of the interface. System-view [switchb] interface vlan-interface 100 [switchb-vlan-int...
Page 386
386 c hapter 37: ip r outing p olicy c onfiguration the condition. However, if all the items are in the deny mode, no route will pass the ip-prefix filtering. You can define the item “permit 0.0.0.0 0 less-equal 32” after multiple items in the deny mode for all other routes to pass the filtering (if...
Page 387: Oute
38 r oute c apacity c onfiguration route capacity configuration overview introduction in actual networking applications, there are a large number of routes, especially ospf routes and bgp routes, in the routing table. If the routing table occupies too much memory, the switch performance will decline...
Page 388
388 c hapter 38: r oute c apacity c onfiguration n the safety-value must be greater than the limit-value. Enabling/disabling automatic protocol connection recovery c caution: if automatic protocol recovery is disabled, the broken ospf or bgp connection will not recover even when the free memory exce...
Page 389: 802.1
39 802.1 x c onfiguration introduction to 802.1x the 802.1x protocol (802.1x for short) was developed by ieee802 lan/wan committee to address security issues of wireless lans. It was then used in ethernet as a common access control mechanism for lan ports to address mainly authentication and securit...
Page 390
390 c hapter 39: 802.1 x c onfiguration the authentication server system serves to perform aaa (authentication, authorization, and accounting). It also stores user information, such as user name, password, the vlan a user belongs to, priority, and the acls (access control list) applied. Following ar...
Page 391
Introduction to 802.1x 391 the mechanism of an 802.1x authentication system ieee 802.1x authentication system uses extensible authentication protocol (eap) to exchange information between the supplicant system and the authentication server. Figure 89 the mechanism of an 802.1x authentication system ...
Page 392
392 c hapter 39: 802.1 x c onfiguration 02: indicates that the packet is an eapol-logoff packet, which sends logging off requests. 03: indicates that the packet is an eapol-key packet, which carries key information packets. 04: indicates that the packet is an eapol-encapsulated-asf-alert packet, whi...
Page 393
Introduction to 802.1x 393 figure 92 data fields ■ the type field specifies the eap authentication type. A type value of 1 indicates identity and that the packet is used to query the identity of the peer. A type value of 4 represents md5-challenge (similar to ppp chap) and indicates that the packet ...
Page 394
394 c hapter 39: 802.1 x c onfiguration three authentication ways, eap-md5, eap-tls (transport layer security), and peap (protected extensible authentication protocol), are available for the eap relay mode. ■ eap-md5 authenticates the supplicant system. The radius server sends md5 keys (contained in...
Page 395
Introduction to 802.1x 395 ■ upon receiving the authentication request packet, the switch sends an eap-request/identity packet to ask the 802.1x client for the user name. ■ the 802.1x program responds by sending an eap-response/identity packet to the switch with the user name included. The switch th...
Page 396
396 c hapter 39: 802.1 x c onfiguration figure 96 802.1x authentication procedure (in eap terminating mode) the authentication procedure in eap terminating mode is the same as that in the eap relay mode except that the randomly-generated key in the eap terminating mode is generated by the switch, an...
Page 397
Introduction to 802.1x 397 ■ supplicant system timer (supp-timeout): this timer sets the supp-timeout period and is triggered by the switch after the switch sends a request/challenge packet to a supplicant system. The switch sends another request/challenge packet to the supplicant system if the supp...
Page 398
398 c hapter 39: 802.1 x c onfiguration ■ the 802.1x clients are capable of detecting multi-network adapter, proxies, and ie proxies. ■ cams is configured to disable the use of multiple network adapters, proxies, or ie proxies. By default, an 802.1x client program allows use of multiple network adap...
Page 399
802.1x configuration 399 802.1x configuration 802.1x provides a solution for authenticating users. To implement this solution, you need to execute 802.1x-related commands. You also need to configure aaa schemes on switches and to specify the authentication scheme (radius authentication scheme or loc...
Page 400
400 c hapter 39: 802.1 x c onfiguration c caution: ■ 802.1x-related configurations can all be performed in system view. Port access control mode and port access method can also be configured in port view. ■ if you perform a configuration in system view and do not specify the interface-list argument,...
Page 401
802.1x-related parameter configuration 401 802.1x-related parameter configuration n ■ as for the dot1x max-user command, if you execute it in system view without specifying the interface-list argument, the command applies to all ports. You can also use this command in port view. In this case, this c...
Page 402
402 c hapter 39: 802.1 x c onfiguration prerequisites configuration of basic 802.1x configuring proxy checking this function needs the support of 802.1x client program and cams, as listed below. ■ the 802.1x clients must be able to check whether multiple network modules, proxy servers, or ie proxy s...
Page 403
Displaying and debugging 802.1x 403 n as for the dot1x version-user command, if you execute it in system view without specifying the interface-list argument, the command applies to all ports. You can also use this command in port view. In this case, this command applies to the current port only and ...
Page 404
404 c hapter 39: 802.1 x c onfiguration configuration example 802.1x configuration example network requirements ■ authenticate users on all ports to control their accesses to the internet. The switch operates in mac address-based access control mode. The access control mode is mac-address-based. ■ a...
Page 405
Configuration example 405 configure the number of times that a switch resends packets to the radius server to be 5. Configure the switch to send real-time counting packets to the radius server every 15 minutes with the domain names removed from the user name beforehand. ■ the user name and password ...
Page 406
406 c hapter 39: 802.1 x c onfiguration # assign ip addresses to the secondary authentication and accounting radius server. [sw7750-radius-radius1] secondary authentication 10.1.1.2 [sw7750-radius-radius1] secondary accounting 10.1.1.1 # set the password for the switch and the authentication radius ...
Page 407
Configuration example 407 # create a local access user account. [sw7750] local-user localuser [sw7750-luser-localuser] service-type lan-access [sw7750-luser-localuser] password simple localpass.
Page 408
408 c hapter 39: 802.1 x c onfiguration.
Page 409: Habp C
40 habp c onfiguration introduction to habp with 802.1x enabled, a switch authenticates and then authorizes 802.1x-enabled ports. Packets can be forwarded only by authorized ports. If ports connected to the switch are not authenticated and authorized by 802.1x, their received packets will be filtere...
Page 410
410 c hapter 40: habp c onfiguration habp client configuration habp clients reside on switches attached to habp servers. After you enable habp for a switch, the switch operates as an habp client by default. So you only need to enable habp on a switch to make it an habp client. Displaying habp after ...
Page 411
Habp configuration example 411 network diagram figure 99 network diagram for habp configuration configuration procedure 1 configure switch b. # enable habp globally. System-view [sw7750]habp enable # configure the habp server. [sw7750]habp server vlan 2 # enable the 802.1x globally. [sw7750]dot1x 80...
Page 412
412 c hapter 40: habp c onfiguration.
Page 413: Ulticast
41 m ulticast o verview n “router” or a router icon in this document refers to a router in a generic sense or an ethernet switch running a routing protocol. This will not be otherwise described in this manual. Multicast overview with development of networks on the internet, more and more interaction...
Page 414
414 c hapter 41: m ulticast o verview transmitted traffic over the network is proportional to the number of users that receive this information, when a large number of users need this information, the server must send many pieces of information with the same content to the users. Therefore, the limi...
Page 415
Multicast overview 415 multicast solves this problem. When some users on a network require specified information, the multicast information sender (namely, the multicast source) sends the information only once. With tree-type routes established for multicast data packets through a multicast routing ...
Page 416
416 c hapter 41: m ulticast o verview ■ each receiver receiving multicast information is a multicast group member. ■ a router providing multicast routing is a multicast router. The multicast router can be a member of one or multiple multicast groups, and it can also manage members of the multicast g...
Page 417
Multicast architecture 417 ■ multicast routing: how is information transported? Ip multicast is a kind of peer-to-peer service. Based on the protocol layer sequence from bottom to top, the multicast mechanism contains addressing mechanism, host registration, multicast routing, and multicast applicat...
Page 418
418 c hapter 41: m ulticast o verview ■ a multicast group whose addresses are assigned by iana is a permanent multicast group. It is also called reserved multicast group. Note that: ■ the ip addresses of a permanent multicast group keep unchanged, while the members of the group can be changed. ■ the...
Page 419
Multicast architecture 419 n like having reserved the private network segment 10.0.0.0/8 for unicast, iana has also reserved the network segments ranging from 239.0.0.0 to 239.255.255.255 for multicast. These are administratively scoped addresses. With the administratively scoped addresses, you can ...
Page 420
420 c hapter 41: m ulticast o verview figure 104 positions of protocols related to multicast multicast group management protocol internet group management protocol (igmp) is adopted between a host and its directly-connected multicast routers. This protocol defines the mechanism of establishing and m...
Page 421
Forwarding mechanism of multicast packets 421 in order to guarantee the transmission of multicast packets in the network, multicast packets must be forwarded based on unicast routing tables or those specially provided to multicast (such as an mbgp multicast routing table). In addition, to prevent th...
Page 422
422 c hapter 41: m ulticast o verview.
Page 423: Gmrp C
42 gmrp c onfiguration gmrp overview gmrp (garp multicast registration protocol), based on garp, is used for maintaining multicast registration information of the switch. All gmrp-capable switches can receive multicast registration information from other switches, dynamically update local multicast ...
Page 424
424 c hapter 42: gmrp c onfiguration displaying and maintaining gmrp after the above-described configuration, execute the display command in any view to display the running of the gmrp configuration, and to verify the effect of the configuration. Gmrp configuration example enabling gmrp network requ...
Page 425
Gmrp configuration example 425 [sw7750] interface ethernet 2/0/1 [sw7750-ethernet2/0/1] gmrp gmrp is enabled on port ethernet 2/0/1..
Page 426
426 c hapter 42: gmrp c onfiguration.
Page 427: Igmp S
43 igmp s nooping c onfiguration overview igmp snooping fundamentals internet group management protocol snooping (igmp snooping) is a multicast control mechanism running on layer 2 switch. It is used to manage and control multicast groups. When the igmp messages transferred from the hosts to the rou...
Page 428
428 c hapter 43: igmp s nooping c onfiguration igmp snooping implementation igmp snooping terminologies ■ router port: the switch port directly connected to the multicast router. ■ multicast member port: a switch port connected to a multicast group member (a host in a multicast group). ■ mac multica...
Page 429
Overview 429 table 335 igmp snooping messages message sender receiver purpose action of the multicast member switch igmp general query message multicas t router and multicas t switch multicast member switch and host query if the multicast groups contain any member check if the message comes from the...
Page 430
430 c hapter 43: igmp s nooping c onfiguration c caution: an igmp-snooping-enabled switch 7750 ethernet switch judges whether the multicast group exists when it receives an igmp leave packet sent by a host in a multicast group. If this multicast group does not exist, the switch will drop the igmp le...
Page 431
Igmp snooping configuration 431 enabling igmp snooping you can use the command here to enable igmp snooping so that it can establish and maintain mac multicast group forwarding tables at layer 2. C caution: ■ although both layer 2 and layer 3 multicast protocols can run on the same switch simultaneo...
Page 432
432 c hapter 43: igmp s nooping c onfiguration c caution: ■ before configuring the igmp snooping version, you must enable igmp snooping in the vlan. ■ different multicast group addresses should be configured for different multicast sources because igmpv3 snooping cannot distinguish multicast data fr...
Page 433
Igmp snooping configuration 433 if the igmp fast leave feature is enabled, when receiving an igmp leave message, the switch immediately removes the port from the multicast group. When a port has only one user, enabling the igmp fast leave feature on the port can save bandwidth. Enabling the igmp fas...
Page 434
434 c hapter 43: igmp s nooping c onfiguration configuring igmp snooping filtering acls for a port n ■ one port can belong to multiple vlans. Only one acl rule can be configured on each of the vlans to which the port belongs. ■ if the port does not belong to the vlan where the command is configured,...
Page 435
Igmp snooping configuration 435 however, a layer 2 multicast switch does not support igmp, and therefore does have an igmp querier to send general queries by default. By enabling igmp snooping querier on a layer 2 switch in a vlan where multicast traffic needs to be layer-2 switched only and no mult...
Page 436
436 c hapter 43: igmp s nooping c onfiguration configuring igmp snooping simulated joining generally, hosts running igmp respond to the igmp query messages of the igmp querier. If hosts fail to respond for some reason, the multicast router may consider that there is no member of the multicast group ...
Page 437
Displaying and maintaining igmp snooping 437 ■ if you configure igmp snooping simulated joining in ethernet port view, the ethernet port must belong to the specified vlan; otherwise the configuration does not take effect. ■ you can use the source-ip source-address command to specify a multicast sour...
Page 438
438 c hapter 43: igmp s nooping c onfiguration igmp snooping configuration example configure igmp snooping on a switch network requirements connect the router port on the switch to the router, and other non-router ports which belong to vlan 10 to user pcs. Enable igmp snooping on the switch. Network...
Page 439
Igmp snooping configuration example 439 configure multicast vlan network requirements table 351 lists all the devices in the network. Assume that port type configuration, vlan division configuration, and ip address configuration for the interface are completed. Configure vlan 1024 as a multicast vla...
Page 440
440 c hapter 43: igmp s nooping c onfiguration configuration procedure # configure router a. System-view [router-a] multicast routing-enable [router-a] interface gigabitethernet0/0/0 [router-a-gigabitethernet0/0/0] pim sm [router-a-gigabitethernet0/0/0] igmp enable [router-a-gigabitethernet0/0/0] qu...
Page 441: Ommon
44 c ommon m ulticast c onfiguration overview common multicast configuration tasks are the common contents of multicast group management protocol and multicast routing protocol. You must enable the common multicast configuration on the switch before enabling the two protocols. Common multicast confi...
Page 442
442 c hapter 44: c ommon m ulticast c onfiguration enabling multicast routing and configuring limit on the number of multicast route entries c caution: the other multicast configurations do not take effect until multicast routing is enabled. Configuring suppression on the multicast source port confi...
Page 443
Common multicast configuration tasks 443 to the forwarding entry. If the packet is not received on the right ingress of the forwarding entry, the packet is regarded as a wrongif packet. The wrongif packet will be reported to the cpu for processing. In some network, many wrongif packets will be repor...
Page 444
444 c hapter 44: c ommon m ulticast c onfiguration ■ enable igmp snooping globally ■ enable multicast routing globally ■ allocate an ethernet port to the corresponding vlan ■ configure an ip address for the vlan ■ enable the multicast routing protocol on the vlan interface ■ bring the ethernet port ...
Page 445
Displaying common multicast configuration 445 displaying common multicast configuration after the configuration above, you can execute the display command to verify the configuration by checking the displayed information. The multicast forwarding table is mainly used for debugging. Generally, you ca...
Page 446
446 c hapter 44: c ommon m ulticast c onfiguration three kinds of tables affect data transmission. The correlations of them are: ■ each multicast routing protocol has its own multicast routing table. ■ the multicast routing information of all multicast routing protocols is integrated to form the cor...
Page 447: Tatic
45 s tatic m ulticast mac a ddress t able c onfiguration overview in layer 2 multicast, the system can add multicast forwarding entries dynamically through layer 2 multicast protocol. However, you can also statically bind a port to a multicast address entry by configuring a multicast mac address ent...
Page 448
448 c hapter 45: s tatic m ulticast mac a ddress t able c onfiguration table 361 display the multicast mac addresses operation command description display the static multicast mac addresses display mac-address multicast [ count ] you can use the display command in any view..
Page 449: Igmp C
46 igmp c onfiguration overview introduction to igmp internet group management protocol (igmp) is responsible for the management of ip multicast members. It is used to establish and maintain membership between ip hosts and their directly connected neighboring routers. The igmp feature does not trans...
Page 450
450 c hapter 46: igmp c onfiguration in igmp version 1, the multicast routing protocol selects the querier. In igmp version 2, it is defined that the multicast router with the lowest ip address is selected as the querier when there are multiple multicast routers in a network segment. Leave group mec...
Page 451
Overview 451 figure 110 working mechanism of igmpv1 a host joins in the multicast group in the following procedure: ■ the igmp querier (such as dr) periodically multicasts igmp general group query messages to all the hosts in the shared network segment whose address is 224.0.0.1. ■ all hosts in the ...
Page 452
452 c hapter 46: igmp c onfiguration enhancements provided by igmpv2 compared with igmpv1, igmpv2 provides the querier election mechanism and leave group mechanism. ■ querier election mechanism in igmpv1, the dr elected by the layer 3 multicast routing protocol (such as pim) serves as the querier am...
Page 453
Overview 453 3 switch in the leaf network (switch b in the figure). The layer 3 switch will then forward igmp join or igmp leave messages sent by the connected hosts. After the configuration of igmp proxy, the leaf switch is no longer a pim neighbor but a host for the external network. Only when the...
Page 454
454 c hapter 46: igmp c onfiguration igmp configuration tasks configuring igmp version c caution: each igmp version cannot be switched to each other automatically. So all the layer 3 switches on a subnet must be configured to use the same igmp version. Configuring igmp query packets igmp general que...
Page 455
Igmp configuration tasks 455 igmp group-specific query messages the query router (querier for short) maintains the igmp join messages on the interface on the shared network. After the related features are configured, the igmp querier will send igmp group-specific query messages at the user-defined i...
Page 456
456 c hapter 46: igmp c onfiguration c caution: when there are multiple multicast routers in a network segment, the querier is responsible for sending igmp query messages to all the hosts in the network segment. Configuring igmp multicast groups on the interface you can perform the following configu...
Page 457
Igmp configuration tasks 457 interface of the switch may fail when plenty of multicast groups join in the routing interface. You can configure limit on the number of igmp multicast groups on the interface of the switch. Thus, when users are ordering the programs of multicast groups, the network band...
Page 458
458 c hapter 46: igmp c onfiguration c caution: ■ if the number of joined multicast groups on the interface exceeds the user-defined limit, new groups are not allowed to join any more. ■ if the number of existing igmp multicast groups has exceeded the configured limit on the number of joined multica...
Page 459
Igmp configuration tasks 459 ■ if you configure igmp simulated joining in ethernet port view, the port to be configured must belong to the specified vlan; otherwise the configuration does not take effect. Configuring igmp proxy configuring igmp proxy you can configure igmp proxy to reduce the worklo...
Page 460
460 c hapter 46: igmp c onfiguration multicast group and drop the other igmp host report messages from the multicast group. Removing the joined igmp groups from the interface you can remove all the joined igmp groups on all ports of the router or all the joined igmp groups on the specified interface...
Page 461: Pim C
47 pim c onfiguration pim overview protocol independent multicast (pim) means that the unicast routing protocols providing routes for the multicast could be static routes, rip, ospf, is-is, or bgp. The multicast routing protocol is independent of unicast routing protocols only if unicast routing pro...
Page 462
462 c hapter 47: pim c onfiguration ■ rpf check ■ assert mechanism neighbor discovery in pim-dm network, the multicast router needs to use hello messages to perform neighbor discovery and maintain the neighbor relation when it is started. All routers keep in touch with each other through sending hel...
Page 463
Pim overview 463 figure 112 diagram for spt establishment in pim-dm the process above is called “flooding and pruning”. Every pruned node also provides timeout mechanism. If pruning behavior times out, the router will initiate another flooding and pruning process. This process is performed periodica...
Page 464
464 c hapter 47: pim c onfiguration assert mechanism in the shared network such as ethernet, the same packets may be sent repeatedly. For example, the lan network segments contains many multicast routers, a, b, c, and d. They each have their own receiving path to the multicast source s. As shown in ...
Page 465
Pim overview 465 in the receiving end, the router connected to the information receiver sends join messages to the rp corresponding to the multicast group. The join message reaches the root (namely, rp) after passing each router. The passed paths become the branches of the rendezvous point tree (rpt...
Page 466
466 c hapter 47: pim c onfiguration figure 114 diagram for dr election each router on the shared network sends hello messages with the dr priority option to each other. The router with the highest dr priority is elected as the dr in the network. If the priority is the same, the router with the highe...
Page 467
Pim overview 467 one or more candidate bsrs must be configured in a pim domain. Through the auto-election, the candidate bsrs elect a bsr which is responsible for collecting and advertising rp information. The auto-election among candidate bsrs is described in the following section: ■ specify a pim-...
Page 468
468 c hapter 47: pim c onfiguration figure 116 diagram for rpt building in pim-sm each router on the path from the leaf router to rp will generate (*, g) entries in the forwarding table. The routers on the path forms a branch of rpt. A (*, g) entry represents the information from any source to the m...
Page 469
Common pim configuration 469 figure 117 diagram for multicast source registration when rp receives the registration information from s, it will decapsulate the registration information and forward the multicast information to the receiver along rpt, and on the other hand, it will send (s, g) join me...
Page 470
470 c hapter 47: pim c onfiguration enabling pim-dm (pim-sm) on the interface configuring the interval of sending hello packets pim-dm must be enabled on each interface. After the configuration, pim-dm will send pim hello packets periodically and process protocol packets that the pim neighbors send....
Page 471
Common pim configuration 471 configuring pim neighbors in order to prevent plenty of pim neighbors from using out the memory of the router, which may result in router failure, you can limit the number of pim neighbors on the router interface. However, the total number of pim neighbors of a router is...
Page 472
472 c hapter 47: pim c onfiguration pim-dm configuration perform the following configuration to configure pim-dm. When the router runs in pim-dm domain, you are recommended to enable pim-dm on all the interfaces of non-boarder routers. Configuring filtering policies for multicast source/group c caut...
Page 473
Pim-sm configuration 473 c caution: ■ only one candidate bsr can be configured on a layer 3 switch. The bsr configuration on another interface will replace the former configuration. ■ you are recommended to configure both the candidate bsr and candidate rp on the layer 3 switch in the backbone. ■ if...
Page 474
474 c hapter 47: pim c onfiguration ■ if both a dynamic rp and a static rp exist simultaneously, and if you have configured the keyword preferred, the static rp has the priority over the dynamic rp. ■ the pim protocol need not be enabled on the interface of static rps. ■ the limit on the range of va...
Page 475
Displaying and debugging pim 475 c caution: ■ if a source group entry (s, g) is denied in acl, or no operation on the entry is defined in the acl, or acls are not defined, rp will send registerstop messages to dr to stop the registration process of the multicast data flow. ■ only the registration pa...
Page 476
476 c hapter 47: pim c onfiguration pim configuration examples pim-dm configuration example network requirements lanswitch 1 is connected to multicast source through vlan-interface 10, to lanswitch 2 through vlan-interface 11 and to lanswitch3 through vlan-interface 12. Through pim-dm, multicast is ...
Page 477
Pim configuration examples 477 configuration procedure 1 configure unicast routing configure the ospf protocol for interoperation among the switches in the pim-dm domain. Ensure the network-layer interoperation among the switches in the pim-dm domain. Detailed configuration steps are omitted here. 2...
Page 478
478 c hapter 47: pim c onfiguration network diagram figure 119 network diagram for pim-sm configuration configuration procedure 1 configure unicast routing configure the ospf protocol for interoperation among the switches in the pim-sm domain. Ensure the network-layer interoperation among the switch...
Page 479
Troubleshooting pim 479 [sw7750-vlan-interface10] pim sm [sw7750-vlan-interface10] quit [sw7750] interface vlan-interface 11 [sw7750-vlan-interface11] pim sm [sw7750-vlan-interface11] quit [sw7750] interface vlan-interface 12 [sw7750-vlan-interface12] pim sm [sw7750-vlan-interface12] quit # configur...
Page 480
480 c hapter 47: pim c onfiguration.
Page 481: Msdp C
48 msdp c onfiguration msdp overview introduction to msdp multicast source discovery protocol (msdp) is an inter-domain multicast solution developed to address the interconnection of protocol independent multicast sparse mode (pim-sm) domains. It is used to discover multicast source information in o...
Page 482
482 c hapter 48: msdp c onfiguration figure 120 where msdp peers are in the network as shown in figure 120, an msdp peer can be created on any pim-sm router. Msdp peers created on pim-sm routers that assume different roles function differently. 1 msdp peers on rps ■ source-side msdp peer: the msdp p...
Page 483
Msdp overview 483 implementing inter-domain multicast delivery by leveraging msdp peers as shown in figure 121, an active source (source) exists in the domain pim-sm 1, and rp 1 has learned the existence of source through multicast source registration. If rps in pim-sm 2 and pim-sm 3 also wish to kn...
Page 484
484 c hapter 48: msdp c onfiguration 5 upon receiving the sa message created by rp 1, rp 2 in pim-sm 2 checks whether there are any receivers for the multicast group in the domain. ■ if so, the rpt for the multicast group g is maintained between rp 2 and the receivers. Rp 2 creates an (s, g) entry, ...
Page 485
Msdp overview 485 as illustrated in figure 122, these msdp peers dispose of sa messages according to the following rpf check rules: 1 when rp 2 receives an sa message from rp 1 because the source-side rp address carried in the sa message is the same as the msdp peer address, which means that the msd...
Page 486
486 c hapter 48: msdp c onfiguration as shown in figure 123, within a pim-sm domain, a multicast source sends multicast data to multicast group g, and receiver is a member of the multicast group. To implement anycast rp, configure the same ip address (known as anycast rp address, typically a private...
Page 487
Configuring msdp basic functions 487 ■ redundancy backup between rps: when an rp fails, the multicast source previously registered with it or the receivers previous joined it will register with or join another nearest rp, thus achieving redundancy backup between rps. C caution: ■ be sure to configur...
Page 488
488 c hapter 48: msdp c onfiguration whose connection is in the up state will be selected as the active static rpf peer. Configuration prerequisites before configuring basic msdp functions, you need to configure: ■ a unicast routing protocol ■ basic functions of pim-sm ■ basic functions of bgp confi...
Page 489
Configuring connection between msdp peers 489 bgp or mbgp between msdp peers, thus simplifying the rpf checking mechanism. The sessions between msdp peers can be terminated and reactivated sessions as required. When a session between msdp peers is terminated, the tcp connection is closed, and there ...
Page 490
490 c hapter 48: msdp c onfiguration n ■ before you configure an msdp mesh group, make sure that the routers are fully connected with one another. ■ the same group name must be configured on all the peers. ■ if you add the same msdp peer to multiple mesh groups, only the latest configuration takes e...
Page 491
Configuring sa message transmission 491 among msdp peers. For forwarded sa messages, you can also configure a time-to-live (ttl) threshold to control the range where sa messages carrying encapsulated data are transmitted. To reduce the delay in obtaining the multicast source information, you can cac...
Page 492
492 c hapter 48: msdp c onfiguration configuring a rule for filtering the multicast sources of sa messages an rp filters each registered source to control the information of active sources advertised in the sa message. An msdp peer can be configured to advertise only the (s, g) entries in the multic...
Page 493
Displaying and debugging msdp configuration 493 configuring sa message cache with the sa message caching mechanism enabled on the router, the group that a new member subsequently joins can obtain all active sources directly from the sa cache and join the corresponding spt source tree, instead of wai...
Page 494
494 c hapter 48: msdp c onfiguration tracing the transmission path of an sa message over the network you can use the msdp-tracert command in any view to trace the path along which the multicast data travels from the multicast source to the destination receiver over the network, so as to locate error...
Page 495
Msdp configuration example 495 network diagram figure 124 network diagram for msdp configuration configuration procedure 1 configure interface ip addresses and unicast routing protocol on the switches. In each pim-sm domain, configure the interface ip addresses on the switches and interconnect the s...
Page 496
496 c hapter 48: msdp c onfiguration system-view [switchc] multicast routing-enable [switchc] interface vlan-interface 100 [switchc-vlan-interface100] pim sm [switchc-vlan-interface100] quit [switchc] interface vlan-interface 200 [switchc-vlan-interface200] pim sm [switchc-vlan-interface200] quit [s...
Page 497
Msdp configuration example 497 # configure ibgp on switch f, and import ospf routes. [switchf] router id 3.3.3.3 [switchf] bgp 200 [switchf-bgp] group as200 [switchf-bgp] peer as200 as-number 200 [switchf-bgp] peer 192.168.3.1 group as200 [switchf-bgp] import-route ospf [switchf-bgp] quit # carry ou...
Page 498
498 c hapter 48: msdp c onfiguration [switchf] msdp [switchf-msdp] peer 192.168.3.2 connect-interface vlan-interface101 [switchf-msdp] quit # configure msdp peers on switch d. [switchd] msdp [switchd-msdp] peer 192.168.1.1 connect-interface vlan-interface110 [switchd-msdp] peer 192.168.3.1 connect-i...
Page 499
Msdp configuration example 499 configuration example of anycast rp application network requirements each pim-sm network is a single-bsr administrative domain, with multiple multicast sources (s) and receivers. With anycast rp configured in each pim-sm domain, when a new member joins the multicast gr...
Page 500
500 c hapter 48: msdp c onfiguration # enable multicast on switchc and enable pim-sm on all interfaces. The configuration procedures on other switches are similar to that on switchc. The details are omitted here. System-view [switchc] multicast routing-enable [switchc] interface vlan-interface 100 [...
Page 501
Msdp configuration example 501 # configure an msdp peer on loopback0 on switchc. [switchc] msdp [switchc-msdp] originating-rp loopback0 [switchc-msdp] peer 2.2.2.2 connect-interface loopback0 [switchc-msdp] quit # configure an msdp peer on loopback0 on switchd. [switchd] msdp [switchd-msdp] originat...
Page 502
502 c hapter 48: msdp c onfiguration network diagram figure 126 network diagram for static rpf peer configuration configuration procedure 1 configure the interface ip addresses and unicast routing protocols for each switch configure interface ip addresses for each switch, and configure ospf for inte...
Page 503
Msdp configuration example 503 [switchc] interface vlan-interface 110 [switchc-vlan-interface110] pim sm [switchc-vlan-interface110] quit [switchc] interface vlan-interface 101 [switchc-vlan-interface101] pim sm [switchc-vlan-interface101] quit [switchc] interface loopback 0 [switchc-loopback0] pim ...
Page 504
504 c hapter 48: msdp c onfiguration that no information is output after you carry out the display bgp peer command means that the bgp peering relationships are not established between the switches. When the multicast source s1 in pim-sm1 sends multicast information, receivers in pim-sm2 and pim-sm3...
Page 505
Troubleshooting msdp configuration 505 keyword is optional. If you do not use this keyword, all (s, g) entries will be filtered out by default, that is, none of the (s, g) entries in the local multicast domain will be advertised. Before the import-source command is executed, the system will send all...
Page 506
506 c hapter 48: msdp c onfiguration.
Page 507: Aaa & Radius & Hwtacacs
49 aaa & radius & hwtacacs c onfiguration overview introduction to aaa aaa is shortened from the three security functions: authentication, authorization and accounting. It provides a uniform framework for you to configure the three security functions to implement the network security management. The...
Page 508
508 c hapter 49: aaa & radius & hwtacacs c onfiguration accounting aaa supports the following accounting methods: ■ none accounting: no accounting is performed for users. ■ remote accounting: user accounting is performed on the remote radius server or tacacs server. Generally, aaa adopts the client/...
Page 509
Overview 509 ■ users: this database stores information about users (such as user name, password, adopted protocol and ip address). ■ clients: this database stores the information about radius clients (such as shared keys). ■ dictionary: this database stores the information used to interpret the attr...
Page 510
510 c hapter 49: aaa & radius & hwtacacs c onfiguration the basic message exchange procedure of radius is as follows: 1 the user enters the user name and password. 2 the radius client receives the user name and password, and then sends an authentication request (access-request) to the radius server....
Page 511
Overview 511 figure 129 radius packet structure 1 the code field decides the type of the radius packet, as shown in table 395. 2 the identifier field (one byte) identifies the request and response packets. It is subject to the attribute field and varies with the received valid responses, but keeps u...
Page 512
512 c hapter 49: aaa & radius & hwtacacs c onfiguration 4 the authenticator field (16 bytes) is used to verify the packet returned from the radius server; it is also used in the password hiding algorithm. There are two kinds of authenticators: request and response. 5 the attribute field contains spe...
Page 513
Overview 513 customized sub-attributes (containing type, length and value) to obtain extended radius implementation. Figure 130 part of the radius packet containing extended attribute introduction to hwtacacs what is hwtacacs hw terminal access controller access control system (hwtacacs) is an enhan...
Page 514
514 c hapter 49: aaa & radius & hwtacacs c onfiguration figure 131 network diagram for a typical hwtacacs application basic message exchange procedure in hwtacacs for example, use hwtacacs to implement authentication, authorization, and accounting for a telnet user. Figure 132 illustrates the basic ...
Page 515
Overview 515 the basic message exchange procedure is as follows: 1 a user requests access to the switch; the tacacs client sends an authentication start request packet to tacacs server upon receipt of the request. 2 the tacacs server sends back an authentication response requesting for the username;...
Page 516
516 c hapter 49: aaa & radius & hwtacacs c onfiguration configuration tasks table 398 configuration tasks operation description related section aaa configuration create an isp domain required “creating an isp domain” on page 518 configure the attributes of the isp domain optional “configuring the at...
Page 517
Configuration tasks 517 radius configuration create a radius scheme required “creating a radius scheme” on page 525 configure radius authentication/auth orization servers required “configuring radius authentication/authorizati on servers” on page 525 configure radius accounting servers required “con...
Page 518
518 c hapter 49: aaa & radius & hwtacacs c onfiguration aaa configuration the goal of aaa configuration is to protect network devices against unauthorized access and at the same time provide network access services to authorized users. If you need to use isp domains to implement aaa management on ac...
Page 519
Aaa configuration 519 configuring the attributes of an isp domain c caution: ■ on a switch 7750, each access user belongs to an isp domain. You can configure up to 16 isp domains on the switch. When a user logs in, if no isp domain name is carried in the user name, the switch assumes that the user b...
Page 520
520 c hapter 49: aaa & radius & hwtacacs c onfiguration n 3com’s cams server is a service management system used to manage networks and secure networks and user information. Cooperating with other network devices (such as switches) in a network, the cams server implements the aaa (authentication, au...
Page 521
Aaa configuration 521 configuring separate aaa schemes you can use the authentication, authorization, and accounting commands to specify a scheme for each of the three aaa functions (authentication, authorization and accounting) respectively. The following gives the implementations of this separate ...
Page 522
522 c hapter 49: aaa & radius & hwtacacs c onfiguration authentication and authorization configuration for a domain: if the scheme radius-scheme or scheme local command is executed, the authorization none command is executed, while the authentication command is not executed, the authorization inform...
Page 523
Aaa configuration 523 c caution: ■ in string mode, if the vlan id assigned by the radius server is a character string containing only digits (for example, 1024), the switch first regards it as an integer vlan id: the switch transforms the string to an integer value and judges if the value is in the ...
Page 524
524 c hapter 49: aaa & radius & hwtacacs c onfiguration c caution: ■ the character string of user-name cannot contain “/”, “:”, “*”, “?”, “ “>”. Moreover, “@” can be used no more than once. ■ after the local-user password-display-mode cipher-force command is executed, all passwords will be displayed...
Page 525
Radius configuration 525 radius configuration the radius protocol configuration is performed on a radius scheme basis. In an actual network environment, you can either use a single radius server or two radius servers (primary and secondary servers with the same configuration but different ip address...
Page 526
526 c hapter 49: aaa & radius & hwtacacs c onfiguration c caution: ■ the authentication response sent from the radius server to the radius client carries the authorization information. Therefore, no separate authorization server can be specified. ■ in an actual network environment, you can either sp...
Page 527
Radius configuration 527 c caution: ■ in an actual network environment, you can either specify two radius servers as the primary and secondary accounting servers respectively, or specify only one server as both the primary and secondary accounting servers. In addition, because radius adopts differen...
Page 528
528 c hapter 49: aaa & radius & hwtacacs c onfiguration configuring the maximum number of transmission attempts of radius requests the communication in radius is unreliable because this protocol adopts udp packets to carry data. Therefore, it is necessary for the switch to retransmit a radius reques...
Page 529
Radius configuration 529 configuring the attributes for data to be sent to radius servers c caution: ■ generally, the access users are named in the userid@isp-name format. Where, isp-name behind the @ character represents the isp domain name, by which the device determines which isp domain it should...
Page 530
530 c hapter 49: aaa & radius & hwtacacs c onfiguration reason, the user-name-format command is designed for you to specify whether or not isp domain names are carried in the user names sent to the radius server. ■ for a radius scheme, if you have specified that no isp domain names are carried in th...
Page 531
Radius configuration 531 instead of communicating with the secondary server, and at the same time restores the primary server to the active state while keeping the state of the secondary server unchanged. To charge the users in real time, you should set the interval of real-time accounting. After th...
Page 532
532 c hapter 49: aaa & radius & hwtacacs c onfiguration the information contained in this packet (nas-id, nas-ip address and session id), and ends the accounting of the users based on the last accounting update packet. 4 once the switch receives the response from the cams, it stops sending other acc...
Page 533
Hwtacacs configuration 533 c caution: ■ the primary and secondary authentication servers cannot use the same ip address. Otherwise, the system will prompt unsuccessful configuration. ■ you can remove a server only when it is not used by any active tcp connection for sending authentication packets. C...
Page 534
534 c hapter 49: aaa & radius & hwtacacs c onfiguration c caution: ■ the primary and secondary accounting servers cannot use the same ip address. Otherwise, the system will prompt unsuccessful configuration. ■ you can remove a server only when it is not used by any active tcp connection for sending ...
Page 535
Hwtacacs configuration 535 configuring the attributes for data to be sent to tacacs servers c caution: generally, the access users are named in the userid@isp-name format. Where, isp-name behind the @ character represents the isp domain name. If the tacacs server does not accept the user name carryi...
Page 536
536 c hapter 49: aaa & radius & hwtacacs c onfiguration information of online users to the tacacs accounting server at intervals of this value. Even if the server does not respond, the device does not cut down the online user. ■ the interval must be a multiple of 3. ■ the setting of real-time accoun...
Page 537
Aaa & radius & hwtacacs configuration example 537 aaa & radius & hwtacacs configuration example remote radius authentication of telnet/ssh users n the configuration procedure for the remote authentication of ssh users through radius server is similar to that of telnet users. The following descriptio...
Page 538
538 c hapter 49: aaa & radius & hwtacacs c onfiguration ■ a radius server with ip address 10.1.1.1 is connected to the switch. This server will be used as the authentication server. ■ on the switch, set the shared key that is used to exchange packets with the authentication radius server to “expert”...
Page 539
Aaa & radius & hwtacacs configuration example 539 [sw7750-radius-cams] key authentication expert [sw7750-radius-cams] server-type extended [sw7750-radius-cams] user-name-format with-domain [sw7750-radius-cams] quit # associate the isp domain with the radius scheme. [sw7750] domain cams [sw7750-isp-c...
Page 540
540 c hapter 49: aaa & radius & hwtacacs c onfiguration [sw7750] domain system [sw7750-isp-system] scheme local a telnet user logging into the switch with the name telnet@system belongs to the system domain and will be authenticated according to the configuration of the system domain. Method 2: usin...
Page 541
Troubleshooting aaa & radius & hwtacacs configuration 541 [sw7750-hwtacacs-hwtac] primary authentication 10.1.1.1 49 [sw7750-hwtacacs-hwtac] primary authorization 10.1.1.1 49 [sw7750-hwtacacs-hwtac] key accounting expert [sw7750-hwtacacs-hwtac] key authentication expert [sw7750-hwtacacs-hwtac] key a...
Page 542
542 c hapter 49: aaa & radius & hwtacacs c onfiguration symptom 3: the user passes the authentication and gets authorized, but the accounting information cannot be transmitted to the radius server. Possible reasons and solutions: ■ the accounting port number is not properly set - be sure to set a co...
Page 543: Ead C
50 ead c onfiguration introduction to ead endpoint admission defense (ead) is an attack defense solution that monitors endpoint admission. This enhances the active defense ability of endpoints, and prevents viruses and worms from spreading on the network. With the cooperation among security client, ...
Page 544
544 c hapter 50: ead c onfiguration software and install system patches. Figure 137 shows the typical network application of ead. Figure 137 typical network application of ead the security client (software installed on pc) checks the security status of a client that just passes the authentication, a...
Page 545
Ead configuration example 545 ead configuration example network requirements in figure 138: ■ a user is connected to ethernet2/0/1 of the switch ■ the user adopts 802.1x client supporting ead extended function ■ by configuring the switch, user remote authentication is implemented through radius serv...
Page 546
546 c hapter 50: ead c onfiguration network diagram figure 138 ead configuration example configuration procedure # configure 802.1x on the switch. Refer to the “802.1x configuration” on page 399 for detailed description. # configure domain. System-view [sw7750] domain system [sw7750-isp-system] quit...
Page 547: Raffic
51 t raffic a ccounting c onfiguration n the traffic accounting module mentioned in this chapter refers to ls81vsnp i/o module (line processing unit). Introduction to traffic accounting some accounting servers, such as cams, can perform accounting for successfully authenticated 802.1x users based on...
Page 548
548 c hapter 51: t raffic a ccounting c onfiguration figure 139 implementation process of traffic accounting the following details the traffic accounting procedure: 1 after a user passes the 802.1x authentication, the user goes online successfully. 2 the authenticator device acquires the online ip a...
Page 549
Displaying traffic accounting 549 n ■ the interface module that connects external networks (internet) should be configured as traffic collection modules. ■ currently, only single rate is supported, and multi-rate is not supported. Displaying traffic accounting after the above configuration, you can ...
Page 550
550 c hapter 51: t raffic a ccounting c onfiguration traffic accounting configuration example network requirements ■ a user running 802.1x authentication client accesses the internet through a switch. The user can access external networks after passing the authentication. The accounting mode is traf...
Page 551
Traffic accounting configuration example 551 [sw7750-isp-aaa] traffic-group somegroup rate 1 [sw7750-isp-aaa] quit # configure the traffic accounting module, specify the traffic collection module, and enable the traffic accounting function. [sw7750] traffic-accounting accounting-slot 2 [sw7750-accou...
Page 552
552 c hapter 51: t raffic a ccounting c onfiguration.
Page 553: Vrrp C
52 vrrp c onfiguration vrrp overview virtual router redundancy protocol (vrrp) is a fault-tolerant protocol. As shown in figure 141, in general, ■ a default route (for example, the next hop address of the default route is 10.100.10.1, as shown in the following figure) is configured for every host on...
Page 554
554 c hapter 52: vrrp c onfiguration figure 142 virtual router the switches in a backup group have the following features: ■ this virtual router has its own ip address: 10.100.10.1 (which can be the interface address of a switch within the backup group). ■ the switches within the backup group have t...
Page 555
Vrrp overview 555 ■ the virtual router ip address and the ip addresses used by the member switches in a backup group must belong to the same network segment. If not, the backup group will be in the initial state (the state before you configure the vrrp on the switches of the group). In this case, vr...
Page 556
556 c hapter 52: vrrp c onfiguration you can configure a switch 7750 to operate in preemptive mode. You can also set the delay period. A backup switch waits for a period of time (the delay period) before becoming a master switch. Setting a delay period aims at: in an unstable network, backup switche...
Page 557
Vrrp configuration 557 if it does not receive a vrrp packet from the master for the period specified by the master-down-interval argument. Configuring the vlan interfaces/ethernet ports to be tracked for a backup group the vlan interface/ethernet port tracking function expands the backup group funct...
Page 558
558 c hapter 52: vrrp c onfiguration configuring backup group-related parameters table 435 lists the operations to configure a switch in a backup group. Configure that the virtual ip address can be pinged vrrp ping-enable optional by default, the virtual ip address cannot be pinged. Map the virtual ...
Page 559
Displaying and maintaining vrrp 559 displaying and maintaining vrrp after the above configuration, you can execute the display command in any view to view vrrp configuration and verify the configuration effect. And in user view, you can execute the reset command to clear the vrrp statistics and exec...
Page 560
560 c hapter 52: vrrp c onfiguration network diagram figure 143 network diagram for single-vrrp backup group configuration configuration procedure ■ configure switch a. # configure vlan 2. System-view [lsw-a] vlan 2 [lsw-a-vlan2] port ethernet 1/0/6 [lsw-a-vlan2] quit [lsw-a] interface vlan-interfac...
Page 561
Vrrp configuration example 561 # configure the preemptive mode for the backup group. [lsw-a-vlan-interface2] vrrp vrid 1 preempt-mode ■ configure switch b. # configure vlan 2. System-view [lsw-b] vlan 2 [lsw-b-vlan2] port ethernet 1/0/5 [lsw-b-vlan2] quit [lsw-b] interface vlan-interface 2 [lsw-b-vl...
Page 562
562 c hapter 52: vrrp c onfiguration network diagram figure 144 network diagram for interface tracking configuration configuration procedure ■ configure switch a. # configure vlan 2. System-view [lsw-a] vlan 2 [lsw-a-vlan2] port ethernet 1/0/6 [lsw-a-vlan2] quit [lsw-a] interface vlan-interface 2 [l...
Page 563
Vrrp configuration example 563 # set the authentication type for the backup group to md5, and the password to abc123. [lsw-a-vlan-interface2] vrrp vrid 1 authentication-mode md5 abc123 # configure that the master switch to send vrrp packets once in every 5 seconds. [lsw-a-vlan-interface2] vrrp vrid ...
Page 564
564 c hapter 52: vrrp c onfiguration 2 and a backup switch in backup group 1. Some hosts in the network take virtual router 1 as the gateway, while others take virtual router 2 as the gateway. In this way, both load balancing and mutual backup are implemented. Network diagram figure 145 network diag...
Page 565
Troubleshooting vrrp 565 # configure vlan 2. System-view [lsw-b] vlan 2 [lsw-b-vlan2] port ethernet 1/0/6 [lsw-b-vlan2] quit [lsw-b] interface vlan-interface 2 [lsw-b-vlan-interface2] ip address 202.38.160.2 255.255.255.0 # create backup group 1. [lsw-b-vlan-interface2] vrrp vrid 1 virtual-ip 202.38...
Page 566
566 c hapter 52: vrrp c onfiguration symptom 3: vrrp state of a switch changes repeatedly such problems occur when the backup group timer duration is too short. They can be solved through prolonging the duration or configuring the preemption delay period..
Page 567: Ha C
53 ha c onfiguration ha overview the switch 7758 supports high availability (ha) feature. This feature is to achieve a high availability of the system and to recover the system as soon as possible in the event of failures so as to shorten the mean time between failures (mtbf) of the system. The func...
Page 568
568 c hapter 53: ha c onfiguration ha configuration ha configuration overview n ■ when the switch 7758 starts, if you log in to the slave module, it will take about 3 minutes before you can see the system prompt. During the 3 minutes, the slave module does not response to any operation. This is syst...
Page 569
Displaying ha 569 enabling automatic synchronization the switch 7758 supports automatic synchronization. The master module stores its configuration file and backups the configuration file to the slave module simultaneously when the master’s configuration file is modified, so as to ensure the consist...
Page 570
570 c hapter 53: ha c onfiguration.
Page 571: Arp C
54 arp c onfiguration introduction to arp address resolution protocol (arp) is used to map network layer protocol addresses (ip addresses) to corresponding data link layer hardware addresses (mac addresses). Necessity of arp network devices can directly identify layer 2 mac addresses instead of laye...
Page 572
572 c hapter 54: arp c onfiguration arp table in an ethernet network, two hosts must know each other’s mac address for them to communicate with each other. For this reason, each host on the network maintains an arp table, which contains some lately used ip address-to-mac address mapping entries. Not...
Page 573
Introduction to arp 573 arp implementation the arp table of a host is empty when the host just starts up. When a dynamic arp entry has not been used for a specific time period, it is removed from the arp table. The purpose of this is to save memory space and update the entries in the arp table. The ...
Page 574
574 c hapter 54: arp c onfiguration with gratuitous arp learning enabled on a device, each time the device receives a gratuitous arp packet, the device updates the arp entry matching the packet in the cache (if exists) by using the hardware address of the sender carried in the gratuitous arp packet....
Page 575
Configuring arp 575 introduction to arp packet rate limit if an attacker sends a large number of arp packets to a port of a switch, the cpu will get overloaded, causing other functions to fail, and even the whole device to break down. To guard against such attacks, switch 7750 ethernet switches supp...
Page 576
576 c hapter 54: arp c onfiguration configuration tasks adding a static arp entry manually c caution: ■ static arp entries are valid as long as the ethernet switch operates normally, unless they are removed as the results of some operations, like changing/removing a vlan interface, removing a vlan, ...
Page 577
Configuring arp 577 configuring the aging time for dynamic arp entries configuring arp entry checking enabling arp forwarding in the protocol-based vlan the system allows for classifying vlans based on protocols, and such vlans are called protocol-based vlans. For details, refer to “protocol-based v...
Page 578
578 c hapter 54: arp c onfiguration configuring gratuitous arp configuring gratuitous arp learning configuring the gratuitous arp update interval n with vrrp enabled on a vlan interface of a switch ■ if the switch is the master switch, it sends gratuitous arp messages with the ip address of the vrrp...
Page 579
Displaying and maintaining arp configuration 579 configuring arp source suppression by setting the maximum numbers of arp packets of different types that can be sent to the cpu in a unit of time, you can protect the cpu from being attacked by illegal arp packets. Displaying and maintaining arp confi...
Page 580
580 c hapter 54: arp c onfiguration arp configuration example basic arp configuration example network requirements ■ disable the arp entry checking function. ■ enable the switch to send gratuitous arp packets periodically. ■ set the aging time for dynamic arp entries to 10 minutes. ■ add a static ar...
Page 581
Arp configuration example 581 arp packet rate limit configuration example network requirements as shown in figure 147, ethernet 2/0/1 of switch a connects to dhcp server; ethernet 2/0/2 connects to client a, ethernet 2/0/3 connects to client b. Ethernet 2/0/1, ethernet 2/0/2 and ethernet 2/0/3 belon...
Page 582
582 c hapter 54: arp c onfiguration [switcha] arp protective-down recover interval 200
Page 583: Roxy
55 p roxy arp c onfiguration proxy arp overview proxy arp allows hosts that have ip addresses of the same network segment but reside on different physical networks to communicate with each other through arp. Figure 148 work mechanism of proxy arp as shown in figure 148: from the perspective of the s...
Page 584
584 c hapter 55: p roxy arp c onfiguration vlan-interface 3 of the switch, and then the switch routes the packets to host d, so as to realize the layer 3 connectivity between host a and host d. Proxy arp is needed in the following cases (hosts have ip addresses of the same network segment). ■ for ho...
Page 585
Proxy arp configuration example 585 ■ configure the ip address of vlan-interface 3 as 192.168.0.27/24, and that of vlan-interface 4 as 192.168.1.27/24. ■ enable proxy arp on vlan-interface 3 and vlan-interface 4 to allow host a and host d to communicate with each other through arp. Network diagram f...
Page 586
586 c hapter 55: p roxy arp c onfiguration ■ create sub-vlans (vlan 2 and vlan 3). ■ ethernet 2/0/2 belongs to vlan 2 and ethernet 2/0/3 belongs to vlan 3. ■ enable proxy arp on vlan-interface 10 to allow host a (in vlan 2) and host b (in vlan 3) to communicate with each other through arp. Network d...
Page 587
Proxy arp configuration example 587 ■ enable proxy arp on switch a to allow host a (in vlan 2) and host b (in vlan 3) to communicate with each other through arp. Network diagram figure 151 network diagram for proxy arp configuration in isolate-user-vlan configuration procedure 1 configure switch b #...
Page 588
588 c hapter 55: p roxy arp c onfiguration [switcha-vlan-interface5] arp proxy enable [switcha-vlan-interface5] arp proxy source-vlan enable [switcha-vlan-interface5] quit.
Page 589: Dhcp O
56 dhcp o verview introduction to dhcp with networks getting larger in size and more complicated in structure, lack of available ip addresses becomes the common situation the network administrators have to face, and network configuration becomes a tough task for the network administrators. With the ...
Page 590
590 c hapter 56: dhcp o verview ■ dynamic assignment. The dhcp server assigns ip addresses to dhcp clients for predetermined period of time. In this case, a dhcp client must apply for an ip address at the expiration of the period. This policy applies to most clients. Obtaining ip addresses dynamical...
Page 591
Dhcp packet format 591 of the bootp packets. The following table describes the packet format (the number in the brackets indicates the field length, in bytes): figure 153 format of dhcp packets the field meanings are illustrated as follows: ■ op: operation types of dhcp packets: 1 for request packet...
Page 592
592 c hapter 56: dhcp o verview dhcp packet processing modes after the dhcp server is enabled on a device, the device processes the dhcp packet received from a dhcp client in one of the following three modes depending on your configuration: ■ global address pool: in response to the dhcp packets rece...
Page 593: Dhcp S
57 dhcp s erver c onfiguration introduction to dhcp server usage of dhcp server generally, dhcp servers are used in the following networks to assign ip addresses: ■ large-sized networks, where manual configuration method bears heavy load and is difficult to manage the whole network in a centralized ...
Page 594
594 c hapter 57: dhcp s erver c onfiguration segment or some subnets (such as domain name), you just need to configure them on the network segment or the corresponding subnets. The following is the details of configuration inheritance. 1 a newly created child address pool inherits the configurations...
Page 595
Global address pool-based dhcp server configuration 595 enabling dhcp you need to enable dhcp before performing other dhcp-related configurations, which takes effect only after dhcp is enabled. Configuring global address pool mode on interface(s) you can configure the global address pool mode on the...
Page 596
596 c hapter 57: dhcp s erver c onfiguration configuring how to assign ip addresses in a global address pool you can specify to bind an ip address in a global address pool statically to a dhcp client or assign ip addresses in the pool dynamically to dhcp clients as needed. In the global address pool...
Page 597
Global address pool-based dhcp server configuration 597 to avoid ip address conflicts, the ip addresses to be dynamically assigned to dhcp clients are those that are not occupied by specific network devices (such as gateways and ftp servers). The lease time can differ with address pools. But that of...
Page 598
598 c hapter 57: dhcp s erver c onfiguration configuring netbios services for the dhcp server for microsoft windows-based dhcp clients that communicate through netbios protocol, the host name-to-ip address translation is carried out by windows internet naming service (wins) servers. So you need to p...
Page 599
Global address pool-based dhcp server configuration 599 customizing dhcp service with the evolution of dhcp, new options are constantly coming into being. You can add the new options as the properties of dhcp servers by performing the following configuration. Configuring gateway addresses for dhcp c...
Page 600
600 c hapter 57: dhcp s erver c onfiguration interface address pool-based dhcp server configuration c caution: in the interface address pool mode, after the addresses in the interface address pool have been assigned, the dhcp server picks ip addresses from the global interface address pool containin...
Page 601
Interface address pool-based dhcp server configuration 601 enabling dhcp you need to enable dhcp before performing dhcp configurations. Dhcp-related configurations are valid only when dhcp is enabled. Configuring to assign the ip addresses of interface address pools to dhcp clients if the dhcp serve...
Page 602
602 c hapter 57: dhcp s erver c onfiguration n ■ there is no limit to the number of ip addresses statically bound in an interface address pool, but the ip addresses statically bound in interface address pools and the interface ip addresses must be in the same segment. ■ an ip address can be statical...
Page 603
Interface address pool-based dhcp server configuration 603 n ■ the dhcp server forbidden-ip command can be executed repeatedly. That is, you can repeatedly configure ip addresses that are not dynamically assigned to dhcp clients. ■ use the dhcp server forbidden-ip command to configure the ip address...
Page 604
604 c hapter 57: dhcp s erver c onfiguration configuring netbios services for dhcp clients for microsoft windows-based dhcp clients that communicate through netbios protocol, the host name-to-ip address translation is carried out by wins servers. So you need to perform wins-related configuration for...
Page 605
Interface address pool-based dhcp server configuration 605 customizing dhcp service with the evolution of dhcp, new options are constantly coming into being. You can add the new options as the properties of dhcp servers by performing the following configuration. Configure the wins server address for...
Page 606
606 c hapter 57: dhcp s erver c onfiguration dhcp security configuration dhcp security configuration is needed to ensure the security of dhcp service. Prerequisites before configuring dhcp security, you should first complete the dhcp server configuration (either global address pool-based or interfac...
Page 607
Displaying and maintaining a dhcp server 607 displaying and maintaining a dhcp server after the above configuration, execute the display command in any view to display and verify the dhcp server configuration. Execute the reset command in user view to clear dhcp server configuration information. N e...
Page 608
608 c hapter 57: dhcp s erver c onfiguration the dhcp settings of the 10.1.1.0/25 network segment are as follows: ■ lease time: 10 days plus 12 hours ■ domain name: aabbcc.Com ■ dns server: 10.1.1.2 ■ wins server: none ■ gateway: 10.1.1.126 the dhcp settings of the 10.1.1.128/25 network segment are ...
Page 609
Troubleshooting a dhcp server 609 configuration procedure 1 configure a vlan and add a port in this vlan, and then configure the ip address of the vlan interface (omitted). 2 configure dhcp service. # enable dhcp. System-view [sw7750] dhcp enable # configure the ip addresses that are not dynamically...
Page 610
610 c hapter 57: dhcp s erver c onfiguration solution ■ disconnect the dhcp client from the network and then check whether there is a host using the conflicting ip address by performing ping operation on another host on the network, with the conflicting ip address as the destination and an enough ti...
Page 611: Dhcp R
58 dhcp r elay a gent c onfiguration introduction to dhcp relay agent usage of dhcp relay agent since the packets are broadcasted in the process of obtaining ip addresses, dhcp is only applicable to the situation that dhcp clients and dhcp servers are in the same network segment, that is, you need t...
Page 612
612 c hapter 58: dhcp r elay a gent c onfiguration forwarding process of the dhcp relay agent. For the interaction process of the packets, see “obtaining ip addresses dynamically” on page 590. 1 the dhcp client broadcasts the dhcp-discover packet. 2 after receiving the packets, the network device pr...
Page 613
Configuring dhcp relay agent 613 mechanism of option 82 supporting on dhcp relay agent the procedure for a dhcp client to obtain an ip address from a dhcp server through a dhcp relay agent is similar to that for the client to obtain an ip address from a dhcp server directly. The following are the me...
Page 614
614 c hapter 58: dhcp r elay a gent c onfiguration enabling dhcp make sure to enable dhcp before you perform other dhcp relay agent-related configurations, since other dhcp-related configurations cannot take effect with dhcp disabled. Configuring an interface to operate in dhcp relay agent mode when...
Page 615
Configuring dhcp relay agent 615 n ■ you can configure up to eight external dhcp ip addresses in a dhcp server group. ■ you can map multiple vlan interfaces to one dhcp server group. But one vlan interface can be mapped to only one dhcp server group. If you execute the dhcp-server groupno command re...
Page 616
616 c hapter 58: dhcp r elay a gent c onfiguration address of the vlan interface (connecting to the client) into the giaddr field of the message. The dhcp server will assign an ip address in the same network segment as the gateway ip address to the client. Thus, clients connecting to different ports...
Page 617
Configuring dhcp relay agent 617 however, if two equal-cost uplinks to the dhcp server exist, the packets from a client may have different source ip addresses. As a result, some packets may fail to pass the validity check. Switch 7750 ethernet switches supports specifying the source ip address of up...
Page 618
618 c hapter 58: dhcp r elay a gent c onfiguration specifying address checking fields after enabled with the address checking function, switch 7750 ethernet switches default to check the ip address, mac address, vlan id, and port number of a dhcp client respectively. The dhcp client can access exter...
Page 619
Configuring dhcp relay agent 619 this configuration will take effect only after the address checking function of the dhcp relay agent on the vlan interface is enabled. Configuring whether to allow freely-connected clients to pass dhcp security check a freely-connected client refers to the client who...
Page 620
620 c hapter 58: dhcp r elay a gent c onfiguration displaying and maintaining dhcp relay agent after the above configuration, execute the display command in any view to display and verify the dhcp relay agent configuration. Execute the reset command in user view to clear the statistics information o...
Page 621
Troubleshooting dhcp relay agent 621 # enable dhcp. [sw7750] dhcp enable # create dhcp server group 1 and configure an ip address of 202.38.1.2 for it. [sw7750] dhcp-server 1 ip 202.38.1.2 # map vlan-interface 2 to dhcp server group 1. [sw7750] interface vlan-interface 2 [sw7750-vlan-interface2] dhc...
Page 622
622 c hapter 58: dhcp r elay a gent c onfiguration.
Page 623: Dhcp S
59 dhcp s nooping c onfiguration configuring dhcp snooping introduction to dhcp snooping for the sake of security, the ip addresses used by online dhcp clients need to be tracked for the administrator to verify the corresponding relationship between the ip addresses the dhcp clients obtained from dh...
Page 624
624 c hapter 59: dhcp s nooping c onfiguration figure 157 typical network diagram for dhcp snooping application figure 158 illustrates the interaction between a dhcp client and a dhcp server. Figure 158 interaction between a dhcp client and a dhcp server dhcp snooping listens to the following two ty...
Page 625
Configuring dhcp snooping 625 ■ sub-option 1 (circuit id sub-option): padded with the port index (smaller than the physical port number by 1) and vlan id of the port that received the client’s request. ■ sub-option 2 (remote id sub-option): padded with the bridge mac address of the dhcp snooping dev...
Page 626
626 c hapter 59: dhcp s nooping c onfiguration mechanism of dhcp-snooping option 82 with dhcp snooping and dhcp-snooping option 82 support enabled, when the dhcp snooping device receives a dhcp client’s request containing option 82, it will handle the packet according to the handling policy and the ...
Page 627
Configuring dhcp snooping 627 n there are two types of dhcp requests from dhcp clients, namely, dhcp_discover and dhcp_request messages. Since some dhcp servers process option 82 in dhcp_discover messages while others process option 82 in dhcp_discover messages, the dhcp snooping device will add opt...
Page 628
628 c hapter 59: dhcp s nooping c onfiguration dhcp snooping configuration configuring dhcp snooping n ■ dhcp relay agent and dhcp snooping cannot be enabled at the same time. If you have enabled dhcp relay agent on the device, you will fail to enable dhcp snooping. ■ the dhcp-snooping trust command...
Page 629
Dhcp snooping configuration 629 enabling dhcp-snooping option 82 support configuring a handling policy for dhcp packets with option 82 n if a handling policy is configured on a port, this configuration overrides the globally configured handling policy for requests received on this port, while the gl...
Page 630
630 c hapter 59: dhcp s nooping c onfiguration configuring the storage format of option 82 the switch 7750 supports the hex or ascii format for the option 82 field. N the dhcp-snooping information format command applies only to the default content of the option 82 field. If you have configured the c...
Page 631
Dhcp snooping configuration 631 n ■ if you configure a remote id sub-option in both system view and on a port, the remote id sub-option configured on the port applies when the port receives a packet, and the global remote id applies to other interfaces that have no remote id sub-option configured. ■...
Page 632
632 c hapter 59: dhcp s nooping c onfiguration n ■ enable dhcp snooping and specify trusted ports on the switch before configuring ip filtering. ■ you are not recommended to configure ip filtering on the ports of an aggregation group. Displaying and maintaining dhcp snooping after the above configur...
Page 633
Dhcp snooping configuration example 633 network diagram figure 163 dhcp-snooping configuration configuration procedure perform the following configuration on the dhcp-snooping-enabled switch a. # enter system view. System-view # enable the dhcp snooping function. [sw7750] dhcp-snooping # enable dhcp...
Page 634
634 c hapter 59: dhcp s nooping c onfiguration network diagram figure 164 network diagram for dhcp-snooping option 82 support configuration configuration procedure # enable dhcp snooping on the switch. System-view [switch] dhcp-snooping # specify ethernet 2/0/5 as the trusted port. [switch] interfac...
Page 635
Dhcp snooping configuration example 635 ■ enable dhcp snooping on the switch, and specify ethernet 2/0/1 as the dhcp snooping trusted port. ■ enable ip filtering on ethernet 2/0/2, ethernet 2/0/3, and ethernet 2/0/4 to prevent attacks to the server from clients using fake source ip addresses. ■ crea...
Page 636
636 c hapter 59: dhcp s nooping c onfiguration [switch] interface ethernet2/0/2 [switch-ethernet2/0/2] ip source static binding ip-address 1.1.1.1 m ac-address 0001-0001-0001.
Page 637: Acl C
60 acl c onfiguration n type a i/o modules refer to the following: 3c16860, 3c16861, ls81fs24a, 3c16858, 3c16859, 3c16860, 3c16861, ls81fs24, 3c16858, and 3c16859. Acl overview an access control list (acl) is used primarily to identify traffic flows. In order to filter data packets, a series of matc...
Page 638
638 c hapter 60: acl c onfiguration acl referenced by the upper-level modules the switch also uses acls to filter packets processed by software and implements traffic classification. In this case, there are two types of match orders for the rules in an acl: config (user-defined match order) and auto...
Page 639
Choosing acl mode for traffic flows 639 layer 2 acl depth-first order with the depth-first rule adopted, the rules of a layer 2 acl are matched in the order of the mask length of the source mac address and destination mac address. The longer of the mask is, the higher the match priority is. If two m...
Page 641
Defining basic acls 641 note that: ■ if only a periodic time section is defined in a time range, the time range is active only within the defined periodic time section. ■ if only an absolute time section is defined in a time, the time range is active only within the defined absolute time section. ■ ...
Page 642
642 c hapter 60: acl c onfiguration in the case that you specify the rule id when defining a rule: ■ if the rule corresponding to the specified rule id already exists, you will edit the rule, and the modified part in the rule will replace the original content, while other parts remain unchanged. ■ i...
Page 643
Defining advanced acls 643 configuration preparation before configuring an acl rule containing time range arguments, you need to configure define the corresponding time ranges. For the configuration of time ranges, refer to “configuring time ranges” on page 640. The values of source and destination ...
Page 644
644 c hapter 60: acl c onfiguration n sour-wildcard and dest-wildcard represent the wildcard masks of the destination subnet masks, provided in dotted decimal. For example, if you want to specify the subnet mask as 255.255.0.0, you need to input 0.0.255.255. The wildcard mask can be 0, representing ...
Page 645
Defining advanced acls 645 to define the tos value, you can directly input a value ranging from 0 to 15, or input a keyword listed in the following table. If the protocol type is tcp or udp, you can also define the following information: table 514 description of ip precedence value keyword ip preced...
Page 646
646 c hapter 60: acl c onfiguration n only type a i/o modules support the “range” operation on the tcp/udp port. If the protocol type is icmp, you can also define the following information: if the protocol type is icmp, you can also directly input the icmp message name after the icmp-type argument. ...
Page 647
Defining layer 2 acls 647 ■ the content of a newly created rule must not be identical with the content of any existing rule; otherwise the rule creation will fail, and the system will prompt that the rule already exists. If you do not specify a rule id, you will create and define a new rule, and the...
Page 648
648 c hapter 60: acl c onfiguration to define the cos, you can directly input a value ranging from 0 to 7, or input a keyword listed in the following table. Table 520 rule information parameter type function description protocol-type protocol type defines the protocol type over ethernet frames proto...
Page 649
Defining user-defined acls 649 in the case that you specify the rule id when defining a rule: ■ if the rule corresponding to the specified rule id already exists, you will edit the rule, and the modified part in the rule will replace the original content, while other parts remain unchanged. ■ if the...
Page 650
650 c hapter 60: acl c onfiguration when you specify the rule id by using the rule command, note that: ■ you can specify an existing rule id to modify the corresponding rule. Aces that are not modified remain unchanged. ■ you can create a rule by specifying an id that identifies no rule. ■ you will ...
Page 651
Applying acls on ports 651 acl-rule: applied acl, which can be a combination of different types of acl rules. Table 524 and table 526 describe the acl combinations on type a i/o modules and the corresponding parameter description. Table 525 and table 526 describe the acl combinations on i/o modules ...
Page 652
652 c hapter 60: acl c onfiguration configuration example # apply acl 2100 in the inbound direction on ethernet 2/0/1 to filter packets. System-view [sw7750] interface ethernet 2/0/1 [sw7750-ethernet2/0/1] qos [sw7750-qoss-ethernet2/0/1] packet-filter inbound ip-group 2100 displaying acl configurati...
Page 653
Acl configuration example 653 acl configuration example basic acl configuration example network requirements through basic acl configuration, packets from the host with the source ip address of 10.1.1.1 (the host is connected to the switch through ethernet 2/0/1 port) are to be filtered within the t...
Page 654
654 c hapter 60: acl c onfiguration advanced acl configuration example network requirements different departments of an enterprise are interconnected on the intranet through the ports of a switch. The ip address of the wage query server is 192.168.1.2. Devices of the r&d department are connected to ...
Page 655
Acl configuration example 655 filtered within the time range from 8:00 to 18:00 everyday. Apply this acl on ethernet 2/0/1 port. Network diagram figure 168 network diagram for layer 2 acl configuration configuration procedure n only the commands related to the acl configuration are listed below. 1 d...
Page 656
656 c hapter 60: acl c onfiguration network diagram figure 169 network diagram for user-defined acl configuration configuration procedure n only the commands related to the acl configuration are listed below. 1 define the time range. # define the time range ranging from 8:00 to 18:00. System-view [s...
Page 657: S C
61 q o s c onfiguration n ■ type-a i/o modules include 3c16860, 3c16861, ls81fs24a, 3c16858, 3c16859, 3c16860, 3c16861, ls81fs24, 3c16858, and 3c16859. ■ on type-a i/o modules, the prompt for qos view is qoss; on non-type-a i/o modules, the prompt for qos view is qosb. Overview quality of service (q...
Page 658
658 c hapter 61: q o s c onfiguration precedence 1 ip precedence, tos precedence and differentiated services code point (dscp) precedence figure 170 ds fields and tos bytes the tos field in an ip header contains 8 bits: ■ the first three bits indicate ip precedence in the range of 0 to 7. ■ bit 3 to...
Page 659
Overview 659 service level can be segmented. The qos rank of the af class is lower than that of the ef class; ■ class selector (cs) class: this class comes from the ip tos field and includes 8 classes; ■ best effort (be) class: this class is a special class without any assurance in the cs class. The...
Page 660
660 c hapter 61: q o s c onfiguration as shown in the figure above, each host supporting 802.1q protocol adds a 4-bit 802.1q tag header after the source address of the former ethernet frame header when sending packets. The 4-bit 802.1q tag header contains a 2-bit tag protocol identifier (tpid) whose...
Page 661
Overview 661 dropped and the other traffic is permitted. The ethernet switch adopts a complicated traffic classification rule to filter the packets based on much information and to drop these useless, unreliable, and doubtful packets. Therefore, the network security is enhanced. The two critical ste...
Page 662
662 c hapter 61: q o s c onfiguration figure 173 evaluate the traffic with the token bucket 1 evaluate the traffic with the token bucket the evaluation for the traffic specification is based on whether the number of tokens in the bucket can meet the need of packet forwarding. If the number of tokens...
Page 663
Overview 663 two token buckets are used in this evaluation. Their rates of putting tokens into the buckets are cir and pir respectively, and their sizes are cbs and ebs respectively (the two buckets are called c bucket and e bucket respectively for short), representing different permitted burst leve...
Page 664
664 c hapter 61: q o s c onfiguration in the following section, strict priority (sp) queues and weighted round robin (wrr) queues are introduced. 1 sp queue figure 174 diagram for sp queues sp queue-scheduling algorithm is specially designed for critical service applications. An important feature of...
Page 665
Overview 665 figure 175 diagram for wrr 3 wrr queue-scheduling algorithm schedules all the queues in turn and every queue can be assured of a certain service time. Assume there are 8 priority queues on the port. Wrr configures a weight value for each queue, which are w7, w6, w5, w4, w3, w2, w1, and ...
Page 666
666 c hapter 61: q o s c onfiguration ■ when the queue length is bigger than the upper limit, all inbound packets all dropped. ■ when the queue length is in the range of the upper limit and the lower limit, the inbound packets are dropped at random. In this case, a number is assigned to each inbound...
Page 667
Configuring priority to be used when a packet enters an output queue 667 configuration example ■ set the port priority of ethernet 2/0/1 to 7. Configuration procedure: system-view [sw7750] interface ethernet 2/0/1 [sw7750-ethernet2/0/1] priority 7 configuring priority to be used when a packet enters...
Page 668
668 c hapter 61: q o s c onfiguration configuring priority to be used when a packet enters an output queue you can select the corresponding priority as the basis for a packet to enter an output queue on a port as required. Configuration prerequisites the priority to be used when a packet enter a que...
Page 669
Configuring priority remark 669 configuration example # configure to use the dscp precedence when a packet enters an output queue system-view [sw7750] priority-trust dscp configuring the mapping relationship between 802.1p priority values and queues you can modify the mapping relationship between 80...
Page 670
670 c hapter 61: q o s c onfiguration ■ through the traffic-priority command. Refer to the following description in this section. Configuration prerequisites ■ acl rules used for traffic identifying are defined. Refer to “choosing acl mode for traffic flows” on page 639 for defining acl rules. ■ the...
Page 671
Configuring rate limit on ports 671 configuration example ■ ethernet 2/0/1 of the switch is accessed into the 10.1.1.1/24 network segment ■ remark the dscp precedence of the traffic from the 10.1.1.1/24 network segment to 56 configuration procedure: system-view [sw7750] acl number 2000 [sw7750-acl-b...
Page 672
672 c hapter 61: q o s c onfiguration n only non-type-a i/o modules support port-based rate limit. Configuration example ■ set rate limit on gigabitethernet 2/0/1 of the switch ■ limit the rate to 10 mbps. Configuration procedure: system-view [sw7750] interface gigabitethernet 2/0/1 [sw7750-gigabite...
Page 673
Configuring redirect 673 ■ when a switch is connected to a radius server, if the switch does not support the inbound tp or outbound tp configured on the radius server, the tp configuration will be ignored on the switch. Configuration example ■ gigabitethernet 2/0/1 of the switch is accessed to the 1...
Page 674
674 c hapter 61: q o s c onfiguration n ■ only non-type-a i/o modules support the traffic redirect configuration. ■ the redirect configuration is effective only for the acl rules whose actions are permit. ■ packets redirected to cpu will not be forwarded normally. Configuration example ■ ethernet 2/...
Page 675
Configuring congestion avoidance 675 n only non-type-a i/o modules support the configuration for queue scheduling mode. Configuration example ■ the switch adopts the wrr queue scheduling algorithm, and the weight values of outbound queues are 10, 5, 10, 10, 5, 10, 5, and 10 respectively; ■ display t...
Page 676
676 c hapter 61: q o s c onfiguration configuration procedure acl-rule: applied acl rules which can be the combination of various acl rules. The way of combination is described in table 541. N ■ only type-a i/o modules support the configuration above. ■ only the rules with the permit action can be p...
Page 677
Configuring traffic statistics 677 configuration procedure of traffic statistics acl-rule: applied acl rules which can be the combination of various acl rules. Type-a i/o modules’ way of combination is described in table 540, and non-type-a i/o modules’ way of combination is described in table 541. ...
Page 678
678 c hapter 61: q o s c onfiguration [sw7750] interface ethernet 2/0/1 [sw7750-ethernet2/0/1] qos [sw7750-qosb-ethernet2/0/1] traffic-statistic inbound ip-group 2000 configuring assured bandwidth the function of assured bandwidth is to provide the maximum available bandwidth and minimum assured ban...
Page 679
Configuring bidirectional car 679 system-view [sw7750] acl number 2000 [sw7750-acl-basic-2000] rule permit source 10.1.1.1 0.0.0.255 [sw7750-acl-basic-2000] quit [sw7750] interface ethernet 2/0/1 [sw7750-ethernet2/0/1] qos [sw7750-qoss-ethernet2/0/1] traffic-bandwidth outbound ip-group 2000 64 128 5...
Page 680
680 c hapter 61: q o s c onfiguration selective qinq function can tag a packet with external vlan tags according to the acl rule that the packets matches on the inbound port. The traffic-based selective qinq function is configured on the hybrid port of the edge device connecting the user device to t...
Page 681
Qos configuration example 681 ■ type-a, 3c16863, and 3c16862 i/o modules do not support the traffic-based selective qinq function. Configuration example ■ gigabitethernet 2/0/1 of the switch is accessed to the 10.1.1.1/24 network segment ■ tag all the packets from the 10.1.1.1/24 network segment wit...
Page 682
682 c hapter 61: q o s c onfiguration configuration procedure n only the commands related with qos/acl configurations are listed in the following configurations. 1 define the outbound traffic of the salary query server # enter acl 3000 view. System-view [sw7750] acl number 3000 # define acl 3000 rul...
Page 683
Qos configuration example 683 system-view [sw7750] time-range test 8:00 to 18:00 daily 2 define the traffic rules of pc packets # enter number-identification-based basic acl view identified. [sw7750] acl number 2000 [sw7750-acl-basic-2000] rule 0 permit source 1.0.0.1 0 time-range test [sw7750-acl-b...
Page 684
684 c hapter 61: q o s c onfiguration.
Page 685: Irroring
62 m irroring c onfiguration overview mirroring refers to the process of copying packets that meet the specified rules to a destination port. Generally, a destination port is connected to a data detect device, which you can use to analyze the mirrored packets for monitoring and troubleshooting the n...
Page 686
686 c hapter 62: m irroring c onfiguration figure 179 remote port mirroring application there are three types of switches with remote port mirroring enabled. ■ source switch: the switch to which the monitored port belongs. The source switch copies the mirrored traffic flows to the remote-probe vlan,...
Page 687
Overview 687 to implement remote port mirroring, you need to define a special vlan, called remote-probe vlan, on all the three types of switches. In this vlan, no normal data but only mirrored packets are transmitted. All mirrored packets will be transferred to the specified port of the destination ...
Page 688
688 c hapter 62: m irroring c onfiguration mirroring supported by the switch 7750 mirroring configuration for mirroring features, see “overview” on page 685. Configuring local port mirroring configuration prerequisites ■ the source port is specified and whether the packets to be mirrored are inbound...
Page 689
Mirroring configuration 689 configuring local port mirroring in system view configuration example ■ the source port is gigabitethernet 2/0/1. Mirror all packets received and sent via this port. ■ the destination port is gigabitethernet 2/0/4. 1 configuration procedure 1: system-view [sw7750] mirrori...
Page 690
690 c hapter 62: m irroring c onfiguration [sw7750-gigabitethernet2/0/4] quit [sw7750] interface gigabitethernet 2/0/1 [sw7750-gigabitethernet2/0/1] mirroring-group 1 mirroring-port both 2 configuration procedure 2: system-view [sw7750] mirroring-group 1 local [sw7750] mirroring-group 1 monitor-port...
Page 691
Mirroring configuration 691 n ■ for a centralized i/o module, if multiple source ports are specified in remote port mirroring configuration, all the source ports must be on the same i/o module. ■ you can configure only one reflector port of a remote source mirroring group or one destination port of ...
Page 692
692 c hapter 62: m irroring c onfiguration configuring remote port mirroring on the intermediate switch n when a switch functions as the intermediate device or destination device for remote mirroring, you are recommended to configure traffic redirect on the incoming port in order to guarantee data m...
Page 693
Mirroring configuration 693 n ■ when a switch functions as the intermediate device or destination device for remote mirroring, you are recommended to configure traffic redirect on the incoming port in order to guarantee data mirroring is achieved normally. By configuring traffic redirect, you can re...
Page 694
694 c hapter 62: m irroring c onfiguration module. As for the distributed system, you can configure only one reflector port of a remote source mirroring group or one destination port of a local mirroring group for the whole system. Only one mirroring destination i/o module can be configured for the ...
Page 695
Mirroring configuration 695 system-view [sw7750] vlan 10 [sw7750-vlan10] remote-probe vlan enable [sw7750-vlan10] quit [sw7750] interface gigabitethernet 2/0/1 [sw7750-gigabitethernet2/0/1] port link-type trunk [sw7750-gigabitethernet2/0/1] port trunk permit vlan 10 [sw7750-gigabitethernet2/0/1] qui...
Page 696
696 c hapter 62: m irroring c onfiguration [sw7750] mirroring-group 1 remote-destination [sw7750] mirroring-group 1 monitor-port gigabitethernet 2/0/2 [sw7750] mirroring-group 1 remote-probe vlan 10 [sw7750] display mirroring-group remote-destination mirroring-group 1: type: remote-destination statu...
Page 697
Mirroring configuration 697 n ■ only non-type-a i/o modules support the traffic mirroring configuration. ■ to define a destination port for mirroring, you can also enter the port view of the specified port directly to execute the mirroring-group group-id monitor-port command. Refer to corresponding ...
Page 698
698 c hapter 62: m irroring c onfiguration configuring the source switch table 561 configure the source switch operation command description enter system view system-view - create a vlan and enter the vlan view vlan vlan-id the vlan-id is the id of the remote-probe vlan to be defined. Define the cur...
Page 699
Mirroring configuration 699 acl-rule: applied acl rules, for the acl combinations of service modules other than a type, refer to table 560. N ■ only non-type-a i/o modules support the traffic mirroring configuration. ■ you can configure only one reflector port of a remote source mirroring group or o...
Page 700
700 c hapter 62: m irroring c onfiguration use the remote traffic mirroring function to mirror the packets from the 10.1.1.1/24 network segment to gigabitethernet 2/0/2, the port of switch a, so that the data detect device can monitor the traffic: ■ define vlan10 as remote-probe vlan. ■ define switc...
Page 701
Mirroring configuration 701 [sw7750-vlan10] quit [sw7750] interface gigabitethernet 2/0/1 [sw7750-gigabitethernet2/0/1] port link-type trunk [sw7750-gigabitethernet2/0/1] port trunk permit vlan 10 [sw7750-gigabitethernet2/0/1] quit [sw7750] interface gigabitethernet 2/0/2 [sw7750-gigabitethernet2/0/...
Page 702
702 c hapter 62: m irroring c onfiguration configuration example ■ the mirroring source i/o module resides in slot 3 and all the packets sent or received on the i/o module are mirrored. ■ the mirroring destination i/o module resides in slot 4. Configuration procedure: system-view [sw7750] mirroring-...
Page 703: Luster
63 c luster cluster overview introduction to switch clustering v2 a cluster is implemented through switch clustering v2. By employing the group management protocol (switch clustering v2), a network administrator can manage multiple switches using the public ip address of a switch known as a manageme...
Page 704
704 c hapter 63: c luster a specific member device on the management device instead of logging into it in advance. ■ functions of topology discovery and display provided, which assist network monitoring and debugging ■ software upgrading and parameter configuring can be performed simultaneously on m...
Page 705
Cluster overview 705 information is different from the existing one. Otherwise, only the holdtime of the corresponding entry is updated. Introduction to ntdp ntdp is a protocol for network topology information collection. Ntdp provides the information about the devices that can be added to clusters ...
Page 706
706 c hapter 63: c luster n you need to enable the cluster function and configure cluster parameters on a management device. However, you only need to enable the cluster function on the member devices and candidate devices. Introduction to function of cluster cluster provides the function of batch m...
Page 707
Cluster overview 707 the switch roles are switched according to the following rules: figure 183 role switching roles ■ each cluster has one (and only one) management device. A management device collects ndp/ntdp information to discover and determine candidate devices, which can be then added into th...
Page 708
708 c hapter 63: c luster ■ a member device becomes a candidate device after being removed from the cluster. Management device configuration management device configuration tasks enabling ndp globally and for specific ports configuring ndp-related parameters table 564 management device configuration...
Page 709
Management device configuration 709 enabling ntdp globally and for specific ports configuring ntdp-related parameters enabling the cluster function configuring cluster parameters c caution: when configuring a cluster, you must ensure that the routing table is not full. Otherwise, the private ip rout...
Page 710
710 c hapter 63: c luster as a result cluster handshake messages cannot be properly sent or received and devices will repeatedly join or leave the cluster. ■ if the routing table of the administrative device is full upon establishment of a cluster, all candidate devices will repeatedly join or leave...
Page 711
Member device configuration 711 building a cluster automatically configuring interaction for the cluster c caution: for switch 7750 ethernet switches, the ip address of the cluster public ftp/tftp server must be in the same network segment as that of the layer-3 interface of management vlan (vlan1)....
Page 712
712 c hapter 63: c luster enabling ndp globally and for specific ports enabling ntdp globally and for specific ports configure member devices to access ftp/tftp server of the cluster perform the following configuration in user view of the member device. Configure member devices to access ftp/tftp se...
Page 713
Intra-cluster configuration 713 intra-cluster configuration n after a cluster is established, snmp trap is enabled when switch 7750s join the cluster as candidate devices or leave the cluster as member devices. You can use the undo snmp trap enable command to disable snmp trap. Displaying and mainta...
Page 714
714 c hapter 63: c luster cluster configuration example cluster configuration example network requirements three switches form a cluster, in which: ■ the management device is a switch 7750. ■ the rest are member devices. The switch 7750 manages the rest two member devices as the management device. T...
Page 715
Cluster configuration example 715 configuration procedure 1 configure the member devices (taking one member as an example) # enable ndp globally and for ethernet1/1. System-view [sw7750] ndp enable [sw7750] interface ethernet 1/1 [sw7750-ethernet1/1] ndp enable [sw7750-ethernet1/1] quit # enable ntd...
Page 716
716 c hapter 63: c luster # configure the hop count to collect topology to be 2. [sw7750] ntdp hop 2 # configure the delay time for topology-collection request packets to be forwarded on member devices to be 150 ms. [sw7750] ntdp timer hop-delay 150 # configure the delay time for topology-collection...
Page 717
Cluster configuration example 717 add the devices connected to the management device into the cluster and perform the following configuration on the member device. # connect the member device to the public remote ftp server of the cluster. Ftp cluster # download the file named aaa.Txt from the publi...
Page 718
718 c hapter 63: c luster.
Page 719: E C
64 p o e c onfiguration poe overview introduction to poe power over ethernet (poe) uses 10baset, 100base-tx, and 1000base-t twisted pairs to supply power to the remote powered devices (pd) in the network and implement power supply and data transmission simultaneously. Advantages of poe ■ reliability...
Page 720
720 c hapter 64: p o e c onfiguration ■ the switch 7750 supply power through the ethernet electrical ports on the service modules. Each service module can supply power to up to 48 remote devices at the maximum distance of 100 m (328 feet). ■ each ethernet port can supply at most a power of 15.4 w to...
Page 721
Poe configuration 721 n in auto mode, when the switch is reaching its full load in supplying power, the switch decides whether to supply power to remote pds on a port based on the port priority. Note that the switch can compare only the priority of ports on the same module. Poe configuration poe con...
Page 722
722 c hapter 64: p o e c onfiguration n ■ you can successfully enable poe on a module only when the remaining power of the switch is not less than the full power of this module. ■ the required power of pds may exceed the power configured for them due to their unstable status, thus causing the pds co...
Page 723
Displaying poe configuration 723 n ■ the switch 7750 do not support the spare mode. ■ when a module is almost fully loaded and a new pd is added, the switch will respond to the pd according to the poe management mode. For details, see “setting poe management mode” on page 720. ■ in auto mode, when t...
Page 724
724 c hapter 64: p o e c onfiguration poe configuration example networking requirements ■ two poe-enabled modules are installed in slot 3 and 5 on a switch 7757. ■ online upgrade the pse processing software of the poe module in slot 5 of the switch 7757. ■ ethernet3/0/1 to ethernet3/0/48 are connect...
Page 725
Poe configuration example 725 networking diagram figure 185 network diagram for poe configuration procedure # enter system view. System-view # online upgrade the pse processing software of the poe module in slot 5 of the switch 7757. [sw7750] poe upgrade refresh 0400_001.S19 # enable the poe feature...
Page 726
726 c hapter 64: p o e c onfiguration [sw7750]interface ethernet 3/0/23 [sw7750-ethernet3/0/23] undo poe enable [sw7750-ethernet3/0/23] quit [sw7750]interface ethernet 3/0/24 [sw7750-ethernet3/0/24] undo poe enable [sw7750-ethernet3/0/24] quit # set the priority of ethernet3/0/48 to critical, so tha...
Page 727: E Psu S
65 p o e psu s upervision c onfiguration introduction to poe psu supervision the poe-enabled switch 7750 can monitor the external poe power supply units (psus) through fabrics. N the pse performance will be affected by fast switching of poe psus. The interval of switching poe psus must be no less th...
Page 728
728 c hapter 65: p o e psu s upervision c onfiguration configuration procedure # enter the system view. System-view # set the overvoltage alarm threshold of ac input for poe psus to 264.0 v. [sw7750] poe-power input-thresh upper 264.0 # set the undervoltage alarm threshold of ac input for poe psus t...
Page 729
Displaying poe supervision information 729 # display the dc output state of the poe psus. [sw7750] display poe-power dc-output state # display the dc output voltage/current values of the poe psus. [sw7750] display poe-power dc-output value displaying poe supervision information after the above confi...
Page 730
730 c hapter 65: p o e psu s upervision c onfiguration network diagram figure 186 network diagram for poe supervision configuration configuration procedure # enter the system view. System-view # enable poe on the module in slot 3. [sw7750] poe enable slot 3 # set the overvoltage alarm threshold of a...
Page 731: E P
66 p o e p rofile c onfiguration introduction to poe profile on a large-sized network or a network with mobile users, to help network administrators to monitor the poe features of the switch, switch 7750 ethernet switches provide the poe profile features. Features of poe profile: ■ various poe profi...
Page 732
732 c hapter 66: p o e p rofile c onfiguration n the following rules should be obeyed ■ a poe profile is a group of poe configurations. Multiple poe features can be set in a poe profile. When the apply poe-profile command applies a poe profile to a port, some poe features can be applied successfully...
Page 733
Poe profile configuration example 733 ■ the poe priority for ethernet2/0/1 through ethernet2/0/5 is critical, whereas the poe priority for ethernet2/0/6 through ethernet2/0/10 is high. ■ the maximum power for ethernet2/0/1 through ethernet2/0/5 ports is 3,000 mw, whereas the maximum power for ethern...
Page 734
734 c hapter 66: p o e p rofile c onfiguration poe max-power 3000 poe priority critical # create profile2, and enter poe-profile view. [sw7750] poe-profile profile2 # in profile2, add the poe policy configuration applicable to ethernet2/0/6 through ethernet2/0/10 ports for users of group a. [sw7750-...
Page 735: Udp-H
67 udp-h elper c onfiguration introduction to udp-helper udp-helper is designed to relay specified udp broadcast packets. It enables a device to operate as a udp packet relay. That is, it can convert udp broadcast packets into unicast packets and forward them to a specified server. Normally, all the...
Page 736
736 c hapter 67: udp-h elper c onfiguration c caution: ■ you need to enable the udp-helper function before specifying a udp-helper destination port. ■ the dns, netbios-ds, netbios-ns, tacacs, tftp, and time keywords refers to the six default udp ports. You can configure a default port to be a udp-he...
Page 737
Udp-helper configuration example 737 udp-helper configuration example network requirements the ip address of vlan 1 interface is 10.110.1.1/16. The vlan interface is connected to the network segment 10.110.0.0/16. Configure to forward the broadcast udp packets whose destination udp port number is 55...
Page 738
738 c hapter 67: udp-h elper c onfiguration.
Page 739: Snmp C
68 snmp c onfiguration snmp overview by far, the simple network management protocol (snmp) has gained the most extensive application in the computer networks. Snmp has been put into use and widely accepted as an industry standard in practice. It is used for ensuring the transmission of the managemen...
Page 740
740 c hapter 68: snmp c onfiguration ■ define mib view that a community can access. ■ set read-only or read-write right to access mib objects for the community. The read-only community can only query device information, while the read-write community can configure the device. ■ set the basic acl spe...
Page 741
Configuring snmp basic functions 741 configuring snmp basic functions the configuration of snmp v3 configuration is different from that of snmp v1 and snmp v2c, therefore snmp basic function configurations for different versions are introduced respectively. For specific configurations, refer to tabl...
Page 743
Configuring trap 743 configuring trap trap is the information that the managed device initiatively sends to the nms without request. Trap is used to report some urgent and important events (e.G., the managed device is rebooted). Configuration prerequisites complete snmp basic configuration. Configur...
Page 744
744 c hapter 68: snmp c onfiguration n the snmp-agent trap ifmib command is used to privately extend a linkup/linkdown trap packet and add two objects “ifdescr” (interface description) and “iftype” (interface type) to a trap packet. The two objects facilitate your understanding and failure port loca...
Page 745
Snmp configuration example 745 snmp configuration example snmp configuration example network requirements ■ an nms and switch a are connected through the ethernet. The ip address of the nms is 10.10.10.1 and that of the vlan interface on switch a is 10.10.10.2. ■ perform the following configuration ...
Page 746
746 c hapter 68: snmp c onfiguration system-view [sw7750] snmp-agent [sw7750] snmp-agent sys-info version all [sw7750] snmp-agent community write public [sw7750] snmp-agent mib-view include internet 1.3.6.1 [sw7750] snmp-agent group v3 managev3group write-view internet [sw7750] snmp-agent usm-user v...
Page 747: Rmon C
69 rmon c onfiguration introduction to rmon remote monitoring (rmon) is a kind of management information base (mib) defined by internet engineering task force (ietf) and is a most important enhancement made to mib ii standards. Rmon is mainly used to monitor the data traffic across a network segment...
Page 748
748 c hapter 69: rmon c onfiguration commonly used rmon groups event group the event group is used to define the indexes of events and the processing methods of the events. The events defined in an event group are mainly used in alarm group and extended alarm group to trigger alarms. You can specify...
Page 749
Rmon configuration 749 with the history data management function, you can configure network devices, such as collecting history data, collecting the data of a specific port periodically and saving them. Statistics group statistics group contains the statistics of each monitored port on a network dev...
Page 750
750 c hapter 69: rmon c onfiguration n ■ the rmon alarm and rmon prialarm commands take effect on existing nodes only. ■ for each port, only one rmon statistics entry can be created. That is, if an rmon statistics entry is already created for a given port, creation of another entry with a different ...
Page 751
Rmon configuration example 751 configuration procedures # configure rmon. System-view [sw7750] interface ethernet2/0/1 [sw7750-ethernet2/0/1] rmon statistics 1 owner user1-rmon # view rmon configuration. [sw7750-ethernet2/0/1] display rmon statistics ethernet2/0/1 statistics entry 1 owned by user1-r...
Page 752
752 c hapter 69: rmon c onfiguration.
Page 753: Ntp C
70 ntp c onfiguration introduction to ntp network time protocol (ntp) is a time synchronization protocol defined by rfc1305. It is used for time synchronization among a set of distributed time servers and clients. Ntp transmits packets through udp port 123. Ntp is intended for time synchronization o...
Page 754
754 c hapter 70: ntp c onfiguration with the increasing of stratum number. The clocks with the stratum of 16 are in unsynchronized state and cannot serve as reference clocks. Working principle of ntp figure 192 shows the implementation principle of ntp. Ethernet switch a (device a) is connected to e...
Page 755
Introduction to ntp 755 ■ when receiving a response packet, the local time of device a is 10:00:03 am (t4). At this time, device a has enough information to calculate the following two parameters: ■ delay for an ntp message to make a round trip between device a and device b: delay = (t 4 -t 1 )-(t 3...
Page 756
756 c hapter 70: ntp c onfiguration in peer mode, the active peer sends clock synchronization packets first, and its peer works as a passive peer automatically. If both of the peers have reference clocks, the one with smaller stratum is adopted. Broadcast mode figure 195 ntp implementation mode: bro...
Page 757
Ntp implementation mode configuration 757 ntp implementation mode configuration a switch can operate in the following ntp modes: ■ ntp client mode ■ ntp server mode ■ ntp peer mode ■ ntp broadcast server mode ■ ntp broadcast client mode ■ ntp multicast server mode ■ ntp multicast client mode prerequ...
Page 758
758 c hapter 70: ntp c onfiguration ntp client mode when a switch 7750 operates in the ntp client mode, ■ the remote server identified by the remote-ip argument operates as the ntp time server. The switch 7750 operates as the client, whose clock is synchronized to the ntp server. (in this case, the ...
Page 759
Access control permission configuration 759 ntp multicast client mode will respond this packet and start the clock synchronization procedure. In this mode, the switch can accommodate up to 1,024 multicast clients. N ■ the total number of the servers and peers configured for a switch can be up to 128...
Page 760
760 c hapter 70: ntp c onfiguration configuring ntp authentication configuring ntp authentication on the client n ■ ntp authentication requires that the authentication keys configured for the server and the client are the same. Besides, the authentication keys must be trusted keys. Otherwise, the cl...
Page 761
Configuration of optional ntp parameters 761 n the procedures for configuring ntp authentication on the server are the same as that on the client. Besides, the client and the server must be configured with the same authentication key. Configuration of optional ntp parameters the configurations of op...
Page 762
762 c hapter 70: ntp c onfiguration c caution: ■ the source ip address in an ntp packet is the address of the sending interface specified by the ntp-service unicast-server command or the ntp-service unicast-peer command if you provide the address of the sending interface in these two commands. ■ dyn...
Page 763
Configuration example 763 network diagram figure 197 network diagram for the ntp server mode configuration configuration procedures configure s7750-1. # set the local clock as the ntp master clock, with the stratum being 2. System-view system view: return to user view with ctrl+z. [sw7750-1] ntp-ser...
Page 764
764 c hapter 70: ntp c onfiguration the above output information indicates that s7750-2 is synchronized to s7750-1, and the stratum of its clock is 3, one stratum higher than s7750-1. # view the information about the ntp sessions of s7750-2. You can see that s7750-2 establishes a connection with s77...
Page 765
Configuration example 765 system-view [sw77503] # after the local synchronization, set the switch 7750 to be its peer. [sw77503] ntp-service unicast-peer 3.0.1.32 the switch 7750 and 3com3 are configured to be peers with regard to each other. 3com3 operates in the active peer mode, while the switch ...
Page 766
766 c hapter 70: ntp c onfiguration network diagram figure 199 network diagram for the ntp broadcast mode configuration configuration procedures 1 configure 3com3. # enter system view. System-view [sw77503] # enter vlan-interface 2 view. [sw77503] interface vlan-interface 2 [sw77503-vlan-interface2]...
Page 767
Configuration example 767 system-view [s7500-2] # enter vlan-interface 2 view. [sw7750-2] interface vlan-interface 2 [sw7750-2-vlan-interface2] # configure switch 7750-2 to be a broadcast client. [sw7750-2-vlan-interface2] ntp-service broadcast-client the above configuration configures switch 7750-1...
Page 768
768 c hapter 70: ntp c onfiguration network diagram figure 200 network diagram for ntp multicast mode configuration configuration procedures 1 configure 3com3. # enter system view. System-view [sw77503] # enter vlan-interface 2 view. [sw77503] interface vlan-interface 2 # configure 3com3 to be a mul...
Page 769
Configuration example 769 # enter vlan-interface 2 view. [[sw7750-2] interface vlan-interface 2 # configure switch 7750-2 to be a multicast client. [sw7750-2-vlan-interface2] ntp-service multicast-client the above configuration configures switch 7750-1 and switch 7750-2 to listen to multicast packet...
Page 770
770 c hapter 70: ntp c onfiguration network diagram figure 201 network diagram for ntp server mode with authentication configuration configuration procedures 1 configure switch 7750-2. # enter system view. System-view [sw7750-2] # configure switch 7750-1 to be the time server. [sw7750-2] ntp-service...
Page 771
Configuration example 771 [sw7750-2] display ntp-service status service status: enabled clock status: synchronized clock stratum: 3 reference clock id: 1.0.1.11 nominal frequence: 250.0000 hz actual frequence: 249.9992 hz clock precision: 2^19 clock offset: 0.66 ms root delay: 27.47 ms root dispersi...
Page 772
772 c hapter 70: ntp c onfiguration.
Page 773: Ssh T
71 ssh t erminal s ervices ssh terminal services introduction to ssh secure shell (ssh) can provide information security and powerful authentication to prevent such attacks as ip address spoofing, plain-text password interception when users log on to the switch remotely through an insecure network. ...
Page 774
774 c hapter 71: ssh t erminal s ervices ■ password authentication works as follows: the client sends a password authentication request carrying the encrypted username and password to the server. The server decrypts the request to obtain the username and password in plain text, and matches the usern...
Page 775
Ssh terminal services 775 c caution: ■ when ssh protocol is specified, to ensure a successful login, you must configure the aaa authentication using the authentication-mode scheme command. ■ the protocol inbound ssh configuration fails if you configured authentication-mode password or authentication...
Page 776
776 c hapter 71: ssh t erminal s ervices ■ you just need to execute the command once, with no further action required even after the system is rebooted. ■ if you use this command to generate an rsa key provided an old one exits, the system will prompt you whether to replace the previous one or not. ...
Page 777
Ssh terminal services 777 ■ for the password-publickey authentication type: ssh1 client users can access the switch as long as they pass one of the two authentications. Ssh2.0 client users can access the switch only when they pass both the authentications. ■ for the password authentication, username...
Page 778
778 c hapter 71: ssh t erminal s ervices ssh client configuration configuration prerequisites make sure that the ssh server is configured. Refer to “ssh server configuration” on page 774 for configuration details. Configure the device as an ssh client when a device operating as an ssh client connect...
Page 779
Ssh terminal services 779 displaying ssh configuration use the display commands in any view to view the running of ssh and further to check the configuration result. Through the displaying information, you can verify the configuration effect. Ssh server configuration example network requirements as ...
Page 780
780 c hapter 71: ssh t erminal s ervices network diagram figure 202 network diagram for ssh server configuration configuration procedure 1 generate a local rsa key pair. System-view [sw7750] rsa local-key-pair create n if the local rsa key pair has been generated in previous operations, skip this st...
Page 781
Ssh terminal services 781 [sw7750-ui-vty0-4] protocol inbound ssh # configure the login protocol for user client002 as ssh and authentication type as rsa public key. [sw7750] ssh user client002 authentication-type rsa # generate randomly rsa key pairs on the ssh2.0 client and send the corresponding ...
Page 782
782 c hapter 71: ssh t erminal s ervices [sw7750-vlan-interface1] ip address 10.1.1.3 255.255.255.0 [sw7750-vlan-interface1] quit c caution: generating server rsa key pair is a must for ssh login. # generate an rsa key pair. [sw7750] rsa local-key-pair create # set the authentication mode for the us...
Page 783
Ssh terminal services 783 [sw7750] display rsa local-key-pair public ===================================================== time of key pair created: 09:04:41 2000/04/04 key name: 3com_host key type: rsa encryption key ===================================================== key code: 308188 028180 c933...
Page 784
784 c hapter 71: ssh t erminal s ervices n after generating a key pair on a client, you need to configure the public key on the server and have the configuration on the server done before continuing configuration of the client. # disable first-time authentication. [sw7750] undo ssh client first-time...
Page 785
Sftp service 785 provide secured data transfer. As an sftp client, it allows you to securely log onto another device to transfer files. Sftp server configuration the following sections describe sftp server configuration tasks: ■ “configuring service type for an ssh user” on page 785 ■ “enabling the ...
Page 786
786 c hapter 71: ssh t erminal s ervices enabling the sftp client you can enable the sftp client, establish a connection to the remote sftp server and enter stp client view. Disabling the sftp client sftp file-related operations rename a file or directory on the sftp server rename sftp client view o...
Page 787
Sftp service 787 operating with sftp directories sftp directory-related operations include: changing or displaying the current directory, creating or deleting a directory, displaying files or information of a specific directory. Operating with sftp files sftp file-related operations include: changin...
Page 788
788 c hapter 71: ssh t erminal s ervices sftp configuration example network requirements as shown in figure 204. ■ an ssh connection is present between switch a and switch b. ■ switch b serves as an sftp server, with ip address 10.111.27.91/24. ■ switch a serves as an sftp client, with ip address 10...
Page 789
Sftp service 789 the following files will be deleted: /z are you sure to delete it?(y/n):y this operation may take a long time.Please wait... Received status: success file successfully removed sftp-client> dir -rwxrwxrwx 1 noone nogroup 1759 aug 23 06:52 config.Cfg -rwxrwxrwx 1 noone nogroup 225 aug...
Page 790
790 c hapter 71: ssh t erminal s ervices sftp-client> put pu puk this operation may take a long time, please wait... Local file: pu ---> remote file: /puk received status: success uploading file successfully ended sftp-client> dir -rwxrwxrwx 1 noone nogroup 1759 aug 23 06:52 config.Cfg -rwxrwxrwx 1 ...
Page 791: Ile
72 f ile s ystem m anagement n you can provide the directory argument in the following two ways in this chapter. ■ in the form of [drive] [path]. In this case, the argument can be a string containing 1 to 64 characters. ■ by specifying the name of a storage device, such as flash:/ and cf:/. You can ...
Page 792
792 c hapter 72: f ile s ystem m anagement n currently, only the 96gbps switch fabric supports the cf module. The operations listed in table 627 are available in the directories on a cf module. File system configuration tasks directory-related operations the file system provides directory-related op...
Page 793
File system configuration 793 c caution: ■ for deleted files whose names are the same, only the latest deleted file can be restored. ■ the files which are deleted using the delete command with the /unreserved keyword not specified are actually moved to the recycle bin and thus still take storage spa...
Page 794
794 c hapter 72: f ile s ystem m anagement prompt mode configuration you can set the file system prompt mode to be alert or quiet. When in the alert mode, the file system prompts for confirmation when you perform irreversible operations (such as deleting a file completely or overwriting a file). If ...
Page 795
File system configuration 795 0 -rw- 4 mar 09 2006 13:59:19 snmpboots 1 -rw- 16215134 apr 04 2006 16:36:20 s7750.App 2 -rw- 483 apr 20 2006 14:50:54 diaginfo.Txt 3 -rw- 3980 apr 21 2006 15:08:29 config.Cfg 4 drw- - apr 16 2006 11:18:17 hj 5 drw- - apr 10 2005 19:07:59 dd 6 -rw- 11779 apr 05 2006 10:...
Page 796
796 c hapter 72: f ile s ystem m anagement.
Page 797: Bims C
73 bims c onfiguration introduction to bims to manage a network device through snmp or telnet, you need to know its ip address. This is difficult however when the device obtains address through dhcp or when the device resides behind a nat device. Branch intelligent management system (bims) was thus ...
Page 798
798 c hapter 73: bims c onfiguration 6 the device verifies the device software obtained from the bims center and updates it to the local. Then the device sends an acknowledgement to the bims center. 7 upon receipt of the acknowledgement, the bims center logs the event and sends back a response. Bims...
Page 799
Configuring bims access mode 799 configuring bims access mode enabling bims device to access bims center upon power-on after you make the following configuration, the bims device can access the bims center after it is powered on and initialized. N if you disable the above access function on the devi...
Page 800
800 c hapter 73: bims c onfiguration accessing the bims center as driven by the command execute the following command in system view to enable the bims device access the bims center immediately. Bims configuration example configuring the bims device to access the bims center periodically at startup ...
Page 801
Bims configuration example 801 [sw7750] bims sharekey simple 1122334455667788 # configure the ip address of the bims. The default port 80 is used. [sw7750] bims ip address 10.153.21.97 # configure the interval for accessing the bims center. [sw7750] bims interval 2880 configuring the bims device to ...
Page 802
802 c hapter 73: bims c onfiguration.
Page 803: Ftp
74 ftp and tftp c onfiguration ftp configuration introduction to ftp ftp (file transfer protocol) is commonly used in ip-based networks to transmit files. Before world wide web comes into being, files are transferred through command lines, and the most popular application is ftp. At present, althoug...
Page 804
804 c hapter 74: ftp and tftp c onfiguration c caution: the ftp-related functions require that the route between a ftp client and the ftp server is reachable. ■ ftp client a switch can operate as an ftp client, through which you can access files on ftp servers. In this case, you need to establish a ...
Page 805
Ftp configuration 805 configuration procedure n ■ only one user can access a switch 7750 at a given time when the latter operates as an ftp server. ■ ftp services are implemented in this way: an ftp client sends ftp requests to the ftp server. The ftp server receives the requests, perform operations...
Page 806
806 c hapter 74: ftp and tftp c onfiguration configuration example: a switch operating as an ftp server network requirements a switch operates as an ftp server and a remote pc as an ftp client. ■ create a user account on the ftp server with the user name “switch” and password “hello”. The work direc...
Page 807
Ftp configuration 807 # access the ethernet switch through ftp. Input the user name “switch” and password “hello” to log in and enter ftp view. C:\> ftp 1.1.1.1 connected to 1.1.1.1. 220 ftp service ready. User (1.1.1.1:(none)): switch 331 password required for switch. Password: 230 user logged in. ...
Page 809
Ftp configuration 809 configuration example: a switch operating as an ftp client network requirements a switch operates as an ftp client and a remote pc as an ftp server. ■ create a user account on the ftp server with the user name “switch” and password “hello”, and authorize the user “switch” with ...
Page 810
810 c hapter 74: ftp and tftp c onfiguration # connect to the ftp server using the ftp command. You need to provide the ip address of the ftp server, the user name and the password as well. Ftp 2.2.2.2 trying ... Press ctrl+k to abort connected. 220 wftpd 2.0 service (by texas imperial software) rea...
Page 811
Tftp configuration 811 n ■ before performing tftp-related configurations, you need to configure ip addresses for the tfpt client and the tftp server, and make sure the route between the two is reachable. ■ a switch can only operate as a tftp client. Figure 208 network diagram for tftp configuration ...
Page 812
812 c hapter 74: ftp and tftp c onfiguration tftp configuration example network requirements a switch operates as a tftp client and a pc as the tftp server. ■ the tftp work directory is configured on the tftp server. ■ the ip address of a vlan interface on the switch is 1.1.1.1. The port through whi...
Page 813
Tftp configuration 813 boot boot-loader switch.App reboot n for information about the boot boot-loader command and how to specify the startup file for a switch, refer to “specifying the app to be adopted at reboot” on page 863..
Page 814
814 c hapter 74: ftp and tftp c onfiguration.
Page 815: Nformation
75 i nformation c enter information center overview information center is an indispensable part of ethernet switches and exists as an information hub of system software modules. The information center manages most information outputs; it sorts information carefully, and hence can screen information ...
Page 816
816 c hapter 75: i nformation c enter hh:mm:ss” is the local time, where “hh” is in the 24-hour format, ranging from 00 to 23, both “mm” and “ss” range from 00 to 59. Yyyy” is the year. Note that a space separates the time stamp and host name. 3 host name it refers to the system name of the host, wh...
Page 817
Information center overview 817 ha high availability module habp 3com authentication bypass protocol module hwcm 3com configuration management private mib module hwp nqa module ifnet interface management module igsp igmp snooping module ip internet protocol module ipx ipx protocol module isis interm...
Page 818
818 c hapter 75: i nformation c enter note that a slash (/) separates the module name and severity level. 5 severity switch information falls into three categories: log information, debugging information and trap information. The information center classifies the information into eight levels by sev...
Page 819
Information center configuration 819 7 information text information text contains the detail of system information. N the above section describes the log information format sent to a log server by a switch. Some log server software will resolve the received information as well as its format, so that...
Page 820
820 c hapter 75: i nformation c enter n to view the debugging information of specific modules, you need to set the information type as debug in the info-center source command, and enable debugging for corresponding modules through the debugging command. Enabling information output to the console tab...
Page 821
Information center configuration 821 to view debugging/log/trap output information on the console, you should also enable the corresponding debugging/log/trap information terminal display on the switch. For example, to view log information of the switch on the console, you should not only enable log...
Page 822
822 c hapter 75: i nformation c enter n ■ when there are multiple telnet users or dumb terminal users, some configuration parameters (including module filter, language and severity level threshold settings) are shared between them. In this case, change to any such parameter made by one user will als...
Page 823
Information center configuration 823 enabling information output to the log buffer table 652 lists the related configurations on the switch. N to view debugging information of specific modules, you need to set the information type as debug in the info-center source command, and enable debugging on c...
Page 824
824 c hapter 75: i nformation c enter n to view debugging information of specific modules, you need to set the information type as debug in the info-center source command, and enable debugging on corresponding modules with the debugging command as well. Enabling information output to the snmp table ...
Page 825
Displaying and debugging information center configuration 825 n ■ to view debug information of specific modules, you need to set the information type as debug in the info-center source command, and enable debugging on corresponding modules with the debugging command as well. ■ to send information to...
Page 826
826 c hapter 75: i nformation c enter network diagram figure 210 network diagram for log output to a unix log host configuration procedure 1 configure the switch: # enable the information center. System-view [sw7750] info-center enable # disable for all modules the function of outputting information...
Page 827
Information center configuration examples 827 configured in the commands info-center loghost and info-center source. Otherwise, log information may not be output to the log host normally. Step 3: after the log file “information” is created and the file “/etc/syslog.Conf” is modified, run the followi...
Page 828
828 c hapter 75: i nformation c enter step 2: edit the file “/etc/syslog.Conf” as the superuser (root user) to add the following selector/action pair. # 3com configuration messages local7.Info /var/log/3com/information n note the following items when you edit file “/etc/syslog.Conf”. ■ a note must s...
Page 829
Information center configuration examples 829 # disable for all modules the function of outputting information to the console channels. [sw7750] undo info-center source default channel console # enable log information output to the console. Permit arp and ip modules to output information with severi...
Page 830
830 c hapter 75: i nformation c enter.
Page 831: Dns C
76 dns c onfiguration dns overview domain name system (dns) is a distributed database system that provides domain name-to-ip address mappings for tcp/ip applications. With dns, users using ip applications can directly use meaningful easy-to-remember domain names, which will be resolved and mapped to...
Page 832
832 c hapter 76: dns c onfiguration figure 213 dynamic dns resolution figure 213 shows the relationship between the user program, dns client and dns server. The resolver and cache compose the dns client. The user program runs on the same machine as the dns client, while the dns server and the dns cl...
Page 833
Configuring static dns resolution 833 configuring static dns resolution n as one hostname can mapped to only one ip address, when you add multiple hostname-to-address mapping entries with the same hostname, only the last one will be valid. You can add up to 50 entries for static dns resolution. Conf...
Page 834
834 c hapter 76: dns c onfiguration network diagram figure 214 network diagram for dynamic dns resolution configuration procedure n before doing the following configuration, suppose the route between switch and host is reachable, the dns server works normally, and a mapping entry from host to ip add...
Page 835
Troubleshooting dns configuration 835 troubleshooting dns configuration symptom dynamic dns resolution is enabled, but the user cannot get the correct ip address from a domain name. Analysis dns client needs to be used in conjunction with the dns server to get the correct ip address through domain n...
Page 836
836 c hapter 76: dns c onfiguration.
Page 837: Oot
77 b oot rom and h ost s oftware l oading traditionally, the loading of switch software is accomplished through a serial port. This approach is slow, inconvenient, and cannot be used for remote loading. To resolve these problems, the tftp and ftp modules are introduced into the switch. With these mo...
Page 838
838 c hapter 77: b oot rom and h ost s oftware l oading * * ****************************************** copyright(c) 2004-2007 3com corporation creation date : apr 15 2007, 14:48:52 cpu type : mpc8245 cpu clock speed : 300mhz bus clock speed : 33mhz boot_flash type : amd29lv040b flash size : 32mb mem...
Page 839
Local software loading 839 the xmodem transmission procedure is completed by a receiving program and a sending program: the receiving program sends negotiation characters to negotiate a packet checking method. After the negotiation, the sending program starts to transmit data packets. When receiving...
Page 840
840 c hapter 77: b oot rom and h ost s oftware l oading proceed to step 6 directly. In this case, the system will not display the above information. Following are configurations on pc. Take the hyperterminal using windows operating system as example. Step 4: choose [file/properties] in hyperterminal...
Page 841
Local software loading 841 figure 216 console port configuration dialog box step 5: click the button to disconnect the hyperterminal from the switch and then click the button to reconnect the hyperterminal to the switch, as shown in figure 217. Figure 217 connect and disconnect buttons n the new bau...
Page 842
842 c hapter 77: b oot rom and h ost s oftware l oading figure 218 send file dialog box step 8: click . The system displays the page, as shown in figure 219. Figure 219 sending file page step 9: after the download completes, the system displays the following information: loading ...Cccccccccc done! ...
Page 843
Local software loading 843 loading host software follow these steps to load the host software: step 1: select in boot menu and press . The system displays the following information: 1. Set tftp protocol parameter 2. Set ftp protocol parameter 3. Set xmodem protocol parameter 0. Return to boot menu e...
Page 844
844 c hapter 77: b oot rom and h ost s oftware l oading 2. Set ftp protocol parameter 3. Set xmodem protocol parameter 0. Return to boot menu enter your choice(0-3): step 4: enter 1 to in the above menu to download the bootrom software using tftp. Then set the following tftp-related parameters as re...
Page 845
Local software loading 845 loading process using ftp client ■ loading bootrom software figure 221 local loading using ftp client step 1: as shown in figure 221, connect the switch through an ethernet port to the ftp server, and connect the switch through the console port to the configuration pc. N y...
Page 846
846 c hapter 77: b oot rom and h ost s oftware l oading follow these steps to load the host software: step 1: select in boot menu and press . The system displays the following information: 1. Set tftp protocol parameter 2. Set ftp protocol parameter 3. Set xmodem protocol parameter 0. Return to boot...
Page 847
Remote software loading 847 ftp: 1177900 byte(s) received in 4.594 second(s) 256.39k byte(s)/sec. [ftp] bye n when using different ftp server software on pc, different information will be output to the switch. Step 2: update the bootrom program on fabric of the switch. Boot bootrom s7500.Btm slot 0 ...
Page 848
848 c hapter 77: b oot rom and h ost s oftware l oading step 2: configure the ip address of vlan1 on the switch to 192.168.0.65, and subnet mask to 255.255.255.0. N you can configure the ip address for any vlan on the switch for ftp transmission. However, before configuring the ip address for a vlan...
Page 849
Remote software loading 849 figure 225 switch to bootrom step 6: enter “ftp 192.168.0.65" and enter the user name test, password pass, as shown in figure 226, to log on the ftp server. Figure 226 log on the ftp server step 7: use the put command to upload the file s7500.Btm to the switch, as shown i...
Page 850
850 c hapter 77: b oot rom and h ost s oftware l oading figure 227 upload file s7500.Btm to the switch step 8: configure s7500.Btm to be the bootrom at reboot, and then restart the switch. Boot bootrom s7500.Btm slot 0 this will update bootrom file on board 0 . Continue? [y/n] y board 0 upgrading bo...
Page 851
Remote software loading 851 ■ fabric software and i/o module (line processing unit) software must be identical. Otherwise the switch 7750 cannot work normally. ■ to keep the software of fabric and i/o module identical, you need to restart the i/o module after you upgrade the host software of the fab...
Page 852
852 c hapter 77: b oot rom and h ost s oftware l oading.
Page 853: Asic
78 b asic s ystem c onfiguration & d ebugging basic system configuration basic system configuration tasks entering system view from user view setting the system name of the switch table 659 basic system configuration tasks operation description related section enter system view from user view - “ent...
Page 854
854 c hapter 78: b asic s ystem c onfiguration & d ebugging setting the date and time of the system setting the local time zone this configuration task is to set the name of the local time zone and the difference between the local time zone and the standard utc (universal time coordinated) time. Set...
Page 855
Displaying the system status 855 returning from current view to lower level view returning from current view to user view displaying the system status you can use the following display commands to check the status and configuration information about the system. For information about protocols and po...
Page 856
856 c hapter 78: b asic s ystem c onfiguration & d ebugging figure 228 debugging information output you can use the following commands to operate the two kinds of switches. Perform the following operations in user view. Displaying debugging status table 669 enable debugging and terminal display oper...
Page 857
System debugging 857 displaying operating information about modules in system when your ethernet switch is in trouble, you may need to view a lot of operating information to locate the problem. Each functional module has its own operating information display command(s). You can use the command here ...
Page 858
858 c hapter 78: b asic s ystem c onfiguration & d ebugging.
Page 859: Etwork
79 n etwork c onnectivity t est network connectivity test ping you can use the ping command to check the network connectivity and the reachability of a host. This command can output the following results: ■ response status for each ping packet. If no response packet is received within the timeout ti...
Page 861: Evice
80 d evice m anagement n when different switch fabrics work together with a chassis, note that: if the 96gbps switch fabric switch works with the switch 7708 chassis without the xgbus silkscreen, the four sfp interfaces on the switch fabric do not work. If a 96gbps switch fabric is installed in a sw...
Page 862
862 c hapter 80: d evice m anagement restarting the ethernet switch you can perform the following operation in user view when the switch is in trouble or needs to be restarted. N when rebooting, the system checks whether there is any configuration change. If there is, it prompts you to indicate whet...
Page 863
Device management configuration 863 n there is at most one minute defer for scheduled reboot, that is, the switch will reboot within one minute after reaching the specified reboot date and time. Specifying the app to be adopted at reboot app is the host software of the switch. If multiple apps exist...
Page 864
864 c hapter 80: d evice m anagement c caution: ■ if you do not specify the slot number to upgrade in the boot bootrom command, the system will upgrade all the modules working normally by default. ■ after you specify the boot file of the primary module, if you want to upgrade bootrom, the system wil...
Page 865
Device management configuration 865 identifying and diagnosing pluggable transceivers introduction to pluggable transceivers at present, four types of pluggable transceivers are commonly used, and they can be divided into optical transceivers and electrical transceivers based on transmission media a...
Page 866
866 c hapter 80: d evice m anagement diagnosing pluggable transceivers the system outputs alarm information for you to diagnose and troubleshoot faults of pluggable transceivers. Optical transceivers customized by 3com also support the digital diagnosis function, which enables a transceiver to monit...
Page 867
Configuring layer 3 connectivity detection 867 [sw7750] pause-protection enable slot 7 configuring layer 3 connectivity detection introduction to layer 3 connectivity detection the function that detects layer 3 connectivity is implemented as follows. Local devices send arp request packets continuous...
Page 868
868 c hapter 80: d evice m anagement [sw7750-ethernet4/0/1] uplink monitor ip 1.1.1.1 configuring queue traffic monitoring upon enabling queue traffic monitoring on a switch, the switch monitors the queue traffic and relieves blocks in the output queue of its interfaces. The criterion used to distin...
Page 869
Displaying the device management configuration 869 error packets monitoring configuration example network requirements ■ enable error packets monitoring on ethernet4/0/1 interface and only the packets that are of runt type are concerned. ■ set the interval for detecting error packets to 50 seconds. ...
Page 870
870 c hapter 80: d evice m anagement remote switch update configuration example network requirements telnet to the switch from a pc remotely and download applications from the ftp server to the flash memory of the switch to remotely update the switch software by using the device management commands ...
Page 871
Remote switch update configuration example 871 working directory of the user as switch. The detailed configuration is omitted here. 2 configure the switch as follows: # on the switch, configure a level 3 telnet user with the username and password as user and hello respectively. Authentication by use...
Page 872
872 c hapter 80: d evice m anagement boot boot-loader primary switch.App the specified file will be booted next time on unit 1! Display boot-loader the primary app to boot of board 0 at the next time is: flash:/switch.App the backup app to boot of board 0 at the next time is: flash:/old.App the app ...
Page 873: Emote
81 r emote - ping c onfiguration remote-ping overview introduction to remote-ping remote-ping is a network diagnostic tool. It is used to test the performance of various protocols running in networks. Remote-ping provides more functions than the ping command. ■ the ping command can only use the icmp...
Page 874
874 c hapter 81: r emote - ping c onfiguration test types supported by remote-ping among the test types supported by remote-ping, only the icmp test can be performed when irf fabric is enabled; all other test types cannot be performed when irf fabric is enabled. Remote-ping test parameters you need ...
Page 875
Remote-ping overview 875 source address (source-ip) for remote-ping tests other than dhcp test, you can specify a source ip address for test packets, which will be used by the server as the destination address of response packets. Source port (source-port) for remote-ping tests other than icmp, dhcp...
Page 876
876 c hapter 81: r emote - ping c onfiguration remote-ping configuration the tcp/udp/jitter tests need the cooperation of remote-ping client and remote-ping server, other types of tests need to configure remote-ping client and corresponding different servers. Configuration on a remote-ping server yo...
Page 877
Remote-ping configuration 877 remote-ping server configuration tasks remote-ping server configuration table 693 describes the configuration on remote-ping server, which is the same for remote-ping test types that need to configure remote-ping server. N ■ the remote-ping server function is needed onl...
Page 878
878 c hapter 81: r emote - ping c onfiguration but for non icmp tests, the remote-ping tests you configured cannot be executed until fabric is disabled. 1 configuring an icmp test on remote-ping client 2 configuring a dhcp test on remote-ping client table 694 configure icmp test on remote-ping clien...
Page 879
Remote-ping configuration 879 3 configuring an ftp test on a remote-ping client table 695 configure dhcp test on remote-ping client operation command description enter system view system-view - enable the remote-ping client function remote-ping-agent enable required by default, the remote-ping clien...
Page 880
880 c hapter 81: r emote - ping c onfiguration 4 configuring an http test on a remote-ping client configure the source ip address source-ip ip-address required by default, no source ip address is configured. Configure the source port source-port port-number optional by default, no source port is con...
Page 881
Remote-ping configuration 881 enable the remote-ping client function remote-ping-agent enable required by default, the remote-ping client function is disabled. Create a remote-ping test group and enter its view remote-ping administrator-name operation-tag required by default, no test group is config...
Page 883
Remote-ping configuration 883 6 configuring snmp test on remote-ping client configure the number of probes per test count times optional by default, each test makes one probe. Configure the maximum number of history records that can be saved history-records number figure 236 optional by default, the...
Page 884
884 c hapter 81: r emote - ping c onfiguration 7 configuring tcp test on remote-ping client configure the destination ip address destination-ip ip-address required by default, no destination address is configured. Configure the source ip address source-ip ip-address optional by default, no source ip...
Page 885
Remote-ping configuration 885 configure the destination address destination-ip ip-address required this ip address and the one configured on the remote-ping server for listening services must be the same. By default, no destination address is configured. Configure the destination port destination-po...
Page 886
886 c hapter 81: r emote - ping c onfiguration 8 configuring udp test on remote-ping client display test results display remote-ping results [ admin-name operation-tag ] required the display command can be executed in any view. Table 700 configure tcp test on remote-ping client operation command des...
Page 887
Remote-ping configuration 887 9 configuring dns test on remote-ping client configure the number of probes per test count times optional by default, one probe is made per test. Configure the maximum number of history records that can be saved history-records number figure 239 optional by default, the...
Page 888
888 c hapter 81: r emote - ping c onfiguration configuring remote-ping client to send trap messages trap messages are generated regardless of whether the remote-ping test succeeds or fails. You can specify whether to output trap messages by enabling/disabling trap sending. Configure the maximum numb...
Page 889
Remote-ping configuration example 889 displaying remote-ping configuration after the above-mentioned configuration, you can use the display commands to view the results of the latest test and history information. Remote-ping configuration example icmp test network requirements the switch 7750 serves...
Page 890
890 c hapter 81: r emote - ping c onfiguration [7750-remote-ping-administrator-icmp] test-type icmp # configure the destination ip address as 10.2.2.2. [7750-remote-ping-administrator-icmp] destination-ip 10.2.2.2 # configure to make 10 probes per test. [7750-remote-ping-administrator-icmp] count 10...
Page 891
Remote-ping configuration example 891 configuration procedure ■ configure dhcp server(switch b): configure dhcp server on switch b. For specific configuration of dhcp server, refer to “dhcp server configuration” on page 593. ■ configure remote-ping client (switch a): # enable the remote-ping client....
Page 892
892 c hapter 81: r emote - ping c onfiguration for detailed output description, see the corresponding command manual. N you can perform a remote-ping dhcp test only when no dhcp client is enabled on any interface. Otherwise, the dhcp server sends the response to an interface enabled with the dhcp cl...
Page 893
Remote-ping configuration example 893 [7750-remote-ping-administrator-ftp] filename cmdtree.Txt # configure to make 10 probes per test. [7750-remote-ping-administrator-ftp] count 10 # set the probe timeout time to 30 seconds. [7750-remote-ping-administrator-ftp] timeout 30 # configure the source ip ...
Page 894
894 c hapter 81: r emote - ping c onfiguration network diagram figure 244 network diagram for the http test configuration procedure ■ configure the http server. Use a windows 2003 server as the http server and follow the instructions in your windows 2003 server documentation. ■ configure remote-ping...
Page 895
Remote-ping configuration example 895 dns resolve timeout times: 0 http transmission timeout times: 0 tcp connect time: 73 http operation min time: 27 tcp connect min time: 5 http operation max time: 80 tcp connect max time: 20 tcp connect timeout times: 0 [7750-remote-ping-administrator-http] displ...
Page 896
896 c hapter 81: r emote - ping c onfiguration [7750] remote-ping administrator jitter # configure the test type as jitter [7750-remote-ping-administrator-jitter] test-type jitter # configure the ip address of the remote-ping server as 10.2.2.2. [7750-remote-ping-administrator-jitter] destination-ip...
Page 897
Remote-ping configuration example 897 for detailed output description, see the corresponding command manual. Snmp test network requirements both the remote-ping client and the snmp agent are switch 7750s. Perform remote-ping snmp tests between the two switches to test the time required from switch a...
Page 898
898 c hapter 81: r emote - ping c onfiguration [7750-remote-ping-administrator-snmp] timeout 30 # start the test. [7750-remote-ping-administrator-snmp] test-enable # display test results [7750-remote-ping-administrator-snmp] display remote-ping results administrator s nmp remote-ping entry(admin adm...
Page 899
Remote-ping configuration example 899 system-view [7750] remote-ping-server enable [7750] remote-ping-server tcpconnect 10.2.2.2 8000 ■ configure remote-ping client (switch a): # enable the remote-ping client. System-view [7750] remote-ping-agent enable # create a remote-ping test group, setting the...
Page 900
900 c hapter 81: r emote - ping c onfiguration for detailed output description, see the corresponding command manual. Udp test (udpprivate test) on the specified ports network requirements both the remote-ping client and the remote-ping server are switch 7750s. Perform a remote-ping udpprivate test ...
Page 901
Remote-ping configuration example 901 # display test results. [7750-remote-ping-administrator-udpprivate] display remote-ping results administr ator udpprivate remote-ping entry(admin administrator, tag udpprivate) test result: destination ip address:10.2.2.2 send operation times: 10 receive respons...
Page 902
902 c hapter 81: r emote - ping c onfiguration # create a remote-ping test group, setting the administrator name to administrator and test tag to dns. [7750] remote-ping administrator dns # configure the test type as dns. [7750-remote-ping-administrator-dns] test-type dns # configure the ip address ...
Page 903: Rrpp C
82 rrpp c onfiguration n this board is supported if you have the special order modules listed in “rrpp on 3com switch 7750 family” on page 908. Rrpp overview the rapid ring protection protocol (rrpp) is a link layer protocol designed for ethernet rings. Rrpp can prevent broadcast storm caused by dat...
Page 904
904 c hapter 82: rrpp c onfiguration ethernet ring an ethernet ring is a ring-shaped ethernet topology, on which a rrpp domain is based. An rrpp domain consists of a primary ring and one or more subrings. In configuration, the level of the primary ring is level 0, and that of the subrings is level 1...
Page 905
Rrpp overview 905 the primary port of the master node transmits the loop detection packet, and the secondary port of the master node receives the loop detection packet. When an ethernet ring is in the healthy state, the secondary port of the master node allows only rrpp packets to pass, but logicall...
Page 906
906 c hapter 82: rrpp c onfiguration ■ fail timer: defines the timeout time for the secondary port of the master node to receive health detection packets. The value of fail timer must be greater than or equal to three times the hello timer value. Rrpp message type the following table describes rrpp ...
Page 907
Rrpp overview 907 to avoid temporary data loops, when detecting the port through which it connects to the ring network becomes up again, a transit node blocks the port temporarily (only control vlan packets are permitted to pass), and keeps the port blocked until it receives the complete flush packe...
Page 908
908 c hapter 82: rrpp c onfiguration tangent ring networking figure 252 tangent ring networking there are two or more rings in the network topology and only one common node exists between each pair of rings. In this case, one rrpp domain must be defined for each ring. Intersectant ring networking fi...
Page 909
Master node configuration 909 ■ for 3com switches 7754, 7757, and 7758, bootrom version 527 must be used. ■ the cpld version of the i/o modules is not lower than 005. Ports that support rrpp are: ■ the four gigabit sfp ports on the 96gbps switch fabric. ■ gigabit sfp ports/10 gigabit ports on ls81t1...
Page 910
910 c hapter 82: rrpp c onfiguration c caution: ■ the control vlan of an rrpp domain cannot be a static vlan already created on the switch. If you configure a dynamic vlan as the control vlan of an rrpp domain, the vlan becomes a static vlan automatically. ■ you are not recommended to configure a vl...
Page 911
Transit node configuration 911 system-view [sw7750] rrpp domain 1 [sw7750-rrpp-domain-1] control-vlan 4092 [sw7750-rrpp-domain-1] ring 1 node-mode master primary-port gigabite thernet2/0/1 secondary-port gigabitethernet2/0/2 level 0 [sw7750-rrpp-domain-1] timer hello-timer 2 fail-timer 7 [sw7750-rrp...
Page 912
912 c hapter 82: rrpp c onfiguration c caution: ■ the control vlan of an rrpp domain cannot be a static vlan already created on the switch. If you configure a dynamic vlan as the control vlan of an rrpp domain, the vlan becomes a static vlan automatically. ■ you are not recommended to configure a vl...
Page 913
Edge node configuration 913 edge node configuration tasks the following table describes the edge node configuration tasks. To clear the rrpp statistics information, use the reset rrpp statistics domain domain-id [ ring ring-id ] command. C caution: ■ the control vlan of an rrpp domain cannot be a st...
Page 914
914 c hapter 82: rrpp c onfiguration ■ before creating an rrpp ring, you must create a control vlan. ■ rrpp and loopback test functions are mutually exclusive. You must disenable the loopback test on the primary/secondary port of the master/transit node and the common/edge port of the edge node. ■ w...
Page 915
Assistant edge node configuration 915 to clear the rrpp statistics information, use the reset rrpp statistics domain domain-id [ ring ring-id ] command. C caution: ■ the control vlan of an rrpp domain cannot be a static vlan already created on the switch. If you configure a dynamic vlan as the contr...
Page 916
916 c hapter 82: rrpp c onfiguration ■ before creating an rrpp ring, you must create a control vlan. ■ rrpp and loopback test functions are mutually exclusive. You must disenable the loopback test on the primary/secondary port of the master/transit node and the common/edge port of the edge node. ■ w...
Page 917
Configuration example 917 ■ switch b, switch c and switch d are transit nodes of the primary ring. Their respective gigabitethernet2/0/1 and gigabitethernet2/0/2 serve as the primary and secondary ports ■ the default values are used for the timers on the primary ring network diagram figure 254 netwo...
Page 918
918 c hapter 82: rrpp c onfiguration ethernet2/0/1 secondary-port gigabitethernet2/0/2 level 0 [sw7750-rrpp-domain-1] ring 1 enable [sw7750-rrpp-domain-1] quit [sw7750] rrpp enable ■ configure switch d system-view [sw7750] rrpp domain 1 [sw7750-rrpp-domain-1] control-vlan 4092 [sw7750-rrpp-domain-1]...
Page 919
Configuration example 919 network diagram figure 255 network diagram for intersectant ring topology configuration procedure c caution: make sure that the switch ports connecting the ethernet rings have been configured as trunk ports. All ports allow data vlan packets to pass. And stp has been disena...
Page 920
920 c hapter 82: rrpp c onfiguration igabitethernet 0/1 edge-port gigabitethernet 2/0/3 [sw7750-rrpp-domain-1] ring 1 enable [sw7750-rrpp-domain-1] ring 2 enable [sw7750-rrpp-domain-1] quit [sw7750] rrpp enable ■ configure switch d system-view [sw7750] rrpp domain 1 [sw7750-rrpp-domain-1] control-vl...
Page 921: Elnet
83 t elnet p rotection c onfiguration introduction the telnet protection function is used to protect telnet packets, snmp packets, and icmp packets from the specific source ip addresses in the case of attacks against the network or high cpu utilization. Telnet protection comes in global telnet prote...
Page 922
922 c hapter 83: t elnet p rotection c onfiguration configuring snmp protection configuring icmp protection configuring default-route telnet protection enable global telnet protection or special arp telnet protection attack-protection [ ip-address ] required if you use this command with the ip-addre...
Page 923: Mart
84 s mart l ink c onfiguration smart link overview as shown in figure 256, dual-uplink networking is widely applied currently. Usually, spanning tree protocol (stp) is used to implement link redundancy backup in the network. However, stp is not suitable for users with a high demand for convergence t...
Page 924
924 c hapter 84: s mart l ink c onfiguration slave port the slave port can be either an ethernet port or a manually-configured or static lacp aggregation group. For example, you can configure ethernet2/0/2 of switch a in figure 256 as the slave port through the command line. Flush message when a for...
Page 925
Configuring smart link 925 as shown in figure 257, ethernet2/0/1 on switch a is active and ethernet2/0/2 on switch a is blocked. When the link connected to ethernet2/0/1 fails, ethernet2/0/1 is blocked automatically, and the state of ethernet2/0/2 turns to active state. ■ when link switching occurs ...
Page 926
926 c hapter 84: s mart l ink c onfiguration configuring associated devices an associated device mentioned in this document refers to a device that supports smart link and locally configured to process flush messages received from the specified control vlan so as to work with the corresponding smart...
Page 927
Configuring smart link 927 precautions when configuring smart link, pay attention to the following points: 1 a port or a link aggregation group cannot serve as a member port for two smart link groups. On the other hand, a port or a link aggregation group cannot serve as a member for a smart link gro...
Page 928
928 c hapter 84: s mart l ink c onfiguration displaying and debugging smart link after the above-mentioned configuration, you can use the following display commands in any view to view the smart link group information and the statistics information of flush messages received and processed by current...
Page 929
Smart link configuration example 929 configuration procedure 1 configure a smart link group on switch a and configure member ports for it. Enable the function of sending flush messages in control vlan 1. # enter system view. System-view # enter ethernet port view. Disable stp on ethernet2/0/1 and et...
Page 930
930 c hapter 84: s mart l ink c onfiguration 4 enable the function of processing flush messages received from vlan 1 on switch e. # enter system view. System-view # enable the function of processing flush messages received from vlan 1 on ethernet 2/0/2 and ethernet 2/0/3. [switche] smart-link flush ...
Page 931: Onitor
85 m onitor l ink c onfiguration introduction to monitor link monitor link is a collaboration scheme introduced to complement for smart link. It is used to monitor uplink and to perfect the backup function of smart link. A monitor link consists of an uplink port and one or multiple downlink ports. W...
Page 932
932 c hapter 85: m onitor l ink c onfiguration how monitor link works figure 260 network diagram for a monitor link group implementation as shown in figure 260, the devices switch c and switch d are connected to the uplink device switch e. Switch c is configured with a monitor link group, where ethe...
Page 933
Configuring monitor link 933 and one or multiple downlink ports. The uplink port can be a manually-configured or static lacp link aggregation group, an ethernet port, or a smart link group. The downlink ports can be manually-configured link aggregation groups or static lacp link aggregation groups, ...
Page 934
934 c hapter 85: m onitor l ink c onfiguration c caution: ■ a smart link/monitor link group with members cannot be deleted. A smart link group as a monitor link group member cannot be deleted. ■ the smart link/monitor link function and the remote port mirroring function are incompatible with each ot...
Page 935
Monitor link configuration example 935 network diagram figure 261 network diagram for monitor link configuration configuration procedure 1 enable smart link on switch a and switch b to implement link redundancy backup. Perform the following configuration on switch a. The configuration on switch b is...
Page 936
936 c hapter 85: m onitor l ink c onfiguration # configure ethernet2/0/1 as the master port of the smart link group and ethernet2/0/2 as the slave port. [switcha-smlk-group1] port ethernet 2/0/1 master [switcha-smlk-group1] port ethernet 2/0/2 slave # configure to send flush messages in vlan 1. [swi...
Page 937: Onfiguring
86 c onfiguring h ardware -d ependent s oftware configuring boot rom upgrade with app file by enabling boot rom to upgrade together with the app file, you can ensure that the boot rom versions of the current fabric and service modules can match the version of the current app file, thus avoiding inva...
Page 938
938 c hapter 86: c onfiguring h ardware -d ependent s oftware boot bootrom default # use the specified app file (abcd.App) to upgrade the boot roms of slot 1 i/o module modules in position. Boot bootrom abcd.App # specify the app file abcd.App as the primary startup file for next booting. Boot boot-...
Page 939
Configuring internal channel monitoring 939 configuring internal channel monitoring introduction an internal channel refers to the interface channel between the fabric and the service modules. The fabric sends handshake packets to each service module every second. After receiving the handshake packe...
Page 940
940 c hapter 86: c onfiguring h ardware -d ependent s oftware switch chip auto-reset configuration configuring cpu usage threshold introduction 3com switch 7750 ethernet switches are layer-2/layer-3 ethernet switches with multiple slots and of high reliability. Cpus of fabrics and i/o modules can pr...