- DL manuals
- 3Com
- Switch
- Switch 4500 PWR 26-Port
- Configuration Manual
3Com Switch 4500 PWR 26-Port Configuration Manual
Summary of Switch 4500 PWR 26-Port
Page 1
3com switch 4500 family configuration guide switch 4500 26-port switch 4500 50-port switch 4500 pwr 26-port switch 4500 pwr 50-port product version: v3.03.02p02 manual version: 6w100-20100418 www.3com.Com 3com corporation 350 campus drive, marlborough, ma, usa 01752 3064.
Page 2
Copyright © 2006-2010, 3com corporation. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) without written permission from 3com corporation. 3com corporation reserv...
Page 3
About this manual organization 3com switch 4500 family configuration guide is organized as follows: chapter contents 1 cli configuration details how to use command line interface. 2 logging in to an ethernet switch details how to logging in to an ethernet switch. 3 user control details how to config...
Page 4
Chapter contents 32 aaa overview introduces the authentication, authorization and accounting functions. 33 aaa configuration details how to configure aaa. 34 ead configuration details how to configure ead. 35 mac address authentication configuration details how to configure mac address authenticatio...
Page 5
Chapter contents 67 remote-ping configuration details how to configure remote-ping. 68 ipv6 configuration details how to configure ipv6. 69 ipv6 application configuration details how to configure ipv6 application. 70 password control configuration details how to configure password control. 71 access...
Page 6
Symbols convention description means reader be extremely careful. Improper operation may cause bodily injury. Means reader be careful. Improper operation may cause data loss or damage to equipment. Means an action or information that needs special attention to ensure successful configuration or good...
Page 7: Table of Contents
Table of contents 1 cli configuration....................................................................................................................................... 1-1 what is cli? .................................................................................................................
Page 8
Logging in through the web-based network management system.................................................... 2-31 introduction.................................................................................................................................... 2-32 establishing an http connection .....
Page 9
Introduction to vlan ....................................................................................................................... 6-1 advantages of vlans ..................................................................................................................... 6-2 vlan fundamen...
Page 10
How an ip phone works ............................................................................................................... 10-1 how switch 4500 series switches identify voice traffic .............................................................. 10-3 setting the voice traffic transmission...
Page 11
Introduction to link aggregation.................................................................................................... 13-1 introduction to lacp ..................................................................................................................... 13-1 consistency consid...
Page 12
Port binding configuration example ..................................................................................................... 16-2 port binding configuration example ............................................................................................. 16-2 17 dldp configuration......
Page 13
Configuring the mstp operation mode ...................................................................................... 20-21 configuring the maximum hop count of an mst region ........................................................... 20-22 configuring the network diameter of the switched netwo...
Page 14
Routing table ................................................................................................................................ 21-1 routing protocol overview ................................................................................................................... 21-3 stati...
Page 15
Configuring an ip-prefix list ............................................................................................................ 24-5 displaying ip route policy .................................................................................................................... 24-5 ip rout...
Page 16
Configuring igmp snooping........................................................................................................ 27-16 configuring multicast vlan ........................................................................................................ 27-18 troubleshooting igmp snoop...
Page 17
Configuring system guard.................................................................................................................... 31-2 configuring system guard against ip attacks.............................................................................. 31-2 configuring system guard ag...
Page 18
Displaying and maintaining hwtacacs protocol configuration............................................... 33-29 aaa configuration examples.............................................................................................................. 33-29 remote radius authentication of telnet/ssh us...
Page 19
Arp attack defense configuration task list................................................................................ 37-4 configuring the maximum number of dynamic arp entries that a vlan interface can learn .. 37-5 configuring arp source mac address consistency check ............................
Page 20
Configuring bims server information for the dhcp client......................................................... 39-21 configuring option 184 parameters for the client with voice service........................................ 39-21 configuring the tftp server and bootfile name for the dhcp client.....
Page 21
Ip filtering configuration example.............................................................................................. 41-12 42 dhcp packet rate limit configuration ............................................................................................... 42-1 introduction to dhcp pac...
Page 22
Traffic classification ...................................................................................................................... 45-3 priority trust mode ........................................................................................................................ 45-4 protoco...
Page 23
Specifying the fabric port of a switch........................................................................................... 47-6 specifying the vlan used to form an xrn fabric...................................................................... 47-7 setting a unit id for a switch ...............
Page 24
Poe profile configuration...................................................................................................................... 50-1 configuring poe profile ................................................................................................................. 50-1 displayi...
Page 25
Configuration procedure.............................................................................................................. 54-12 configuring optional ntp parameters ............................................................................................... 54-13 configuring an interfa...
Page 26
Flash memory operations ............................................................................................................. 56-3 prompt mode configuration .......................................................................................................... 56-4 file system configurati...
Page 27
Log output to a linux log host................................................................................................... 59-17 log output to the console .......................................................................................................... 59-18 configuration example ......
Page 28
Configuration procedure ................................................................................................................ 64-3 65 vlan-vpn configuration ...................................................................................................................... 65-1 vlan-vpn...
Page 29
Ipv6 unicast address configuration............................................................................................ 68-14 69 ipv6 application configuration ............................................................................................................ 69-1 introduction to ipv...
Page 30
Setting lldp operating mode ...................................................................................................... 72-7 setting the lldp re-initialization delay ....................................................................................... 72-7 enabling lldp polling............
Page 31
Configuration prerequisites ........................................................................................................... 74-3 configuration procedure................................................................................................................ 74-3 ssl server policy ...
Page 32: Cli Configuration
1 cli configuration this chapter includes these sections: z what is cli? Z entering the cli z 3com products cli descriptions the cli z tips on using urations z cli config wha it it to your device. At the cli, you can enter commands to configure your switch, and verify the configuration based on the ...
Page 33
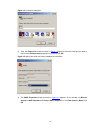
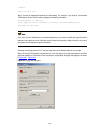
Figure 1-1 use the console cable to connect your pc to your switch identify the interface to avoid connection errors. Beca switch is po cons ug the rj-45 connector of the console cable into your switch. Your switch, first unplug the rj-45 connector and then the db-9 use the serial port of a pc is no...
Page 34
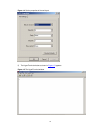
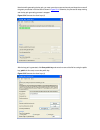
Figure 1-2 connection description 3) then, the connect to window as shown in figure 1-3 appears. Select the serial port you want to use from the connect using drop-down list, and then click ok. Figure 1-3 specify the serial port used to establish the connection 4) the com1 properties window as shown...
Page 35
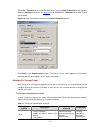
Figure 1-4 set the properties of the serial port 5) the hyperterminal window as shown in figure 1-5 appears. Figure 1-5 the hyperterminal window 1-4.
Page 36
Select file > properties on the hyperterminal window, and the switch properties window appears. Select the settings tab as shown in figure 1-6 , select vt100 then click ok. Figure 1-6 select the emulation terminal on the switch pro from the emulation drop-down list, and perties window minal window. ...
Page 37
Authentication application description configuration method scenarios password z easy to configure z allows any user knowing the password to telnet to your switch z secure, but incapable of assigning different privilege levels to different users environments that do not need granular privilege manag...
Page 38
[sysname-ui-vty0-4] # configure the authentication method for the vty user interfaces as needed. Omitted. For more information, see login configuration. # configure the command level available to the users that log in through vty user interfaces 0 through 4. Command level 3 is used as an example, wh...
Page 39
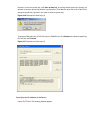
Figure 1-7 read command line parameters type the following command line in the cli of a device and press enter. You set the device system time to 10 o’clock 30 minutes 20 seconds, february 23, 2010. Clock datetime 10:30:20 2/23/2010 you can read any commands more complicated according to table 1-2 ....
Page 40
Available view prompt example enter method quit method operation aux1/0/0 port (the console port) view the 3com switch 4500 does not support configuration on port aux1/0/0 [sysname-aux1/0/ 0] execute the interface aux 1/0/0 command in system view vlan view configure vlan parameters [sysname-vlan1] e...
Page 41
Available view prompt example enter method quit method operation configure the rsa public key for ssh users [sysname-rsa-publ ic-key] execute the rsa peer-public-key command in system view. Public key view configure the rsa or dsa public key for ssh users [sysname-peer-pu blic-key] execute the publi...
Page 42
Available view prompt example enter method quit method operation radius scheme view configure radius scheme parameters [sysname-radius-1 ] execute the radius scheme command in system view. Isp domain view configure isp domain parameters [sysname-isp-aaa 123.Net] execute the domain command in system ...
Page 43
Available view prompt example enter method quit method operation qinq view configure qinq parameters [sysname-etherne t1/0/1-vid-20] execute the vlan-vpn vid command in ethernet port view. The vlan-vpn enable command should be first executed. Execute the quit command to return to ethernet port view....
Page 44
Trapping send trap information to terminal if ? Is at the position of an argument, the cli displays a description about this argument. System-view [sysname] interface vlan-interface ? Vlan interface number [sysname] interface vlan-interface 1 ? [sysname] interface vlan-interface 1 the string indicat...
Page 45
If in the current view, the character string you have typed can already uniquely identify a keyword, you do not need to type the complete keyword. For example, in user view, commands starting with an s include save, startup saved-configuration, and system-view. Z to save the current configuration, t...
Page 46
You may use arrow keys to access history commands in windows 200x and xp terminal or telnet. However, the up and down arrow keys are invalid in windows 9x hyperterminal, because they are defined differently. You can press ctrl+p or ctrl+n instead. Note that: z the commands saved in the history comma...
Page 47
Action function press displays the previous page. Press displays the next page. Cli configurations configuring command aliases you can replace the first keyword of a command supported by the device with your preferred keyword by configuring the command alias function. For example, if you configure s...
Page 48
Synchronous information output synchronous information output refers to the feature that if your input is interrupted by system output, then after the completion of system output the system displays a command line prompt and your input so far, and you can continue your operations from where you were...
Page 49
Level privilege description 1 monitor involves commands for system maintenance and service fault diagnosis. Commands at this level are not allowed to be saved after being configured. After the device is restarted, the commands at this level will be restored to the default settings. Commands at this ...
Page 50
Modifying the command level configuration example the network administrator (a level 3 user) wants to change some tftp commands (such as tftp get) from level 3 to level 0, so that general telnet users (level 0 users) are able to download files through tftp. # change the tftp get command in user view...
Page 51
2 logging in to an ethernet switch log itch in one of the following ways: sole port ging in to an ethernet switch you can log in to an ethernet sw z logging in through the con z logging in through telnet z logging in using a modem logging in through the web-based network management system z z loggin...
Page 52
Z the absolute aux user interfaces are numbered 0 through 7. Vty user interface indexes follow aux user interf z ace indexes. The first absolute vty user 2) type. It is generated by user interface type. The relative user interface indexes are as vty user interfaces are numbered vty0, vty1, and so on...
Page 54
Figure 2-1 diagram for connecting to the console port of a switch 2) if you use a pc to connect to the console port, launch a terminal emulation utility (such as terminal in windows 3.X or hyperterminal in windows 9x/windows 2000/windows xp. The following assumes that you are running windows xp) and...
Page 55
Figure 2-4 set port parameters 3) turn on the switch. You will be prompted to press the enter key if the switch successfully completes post (power-on self test). The prompt appears after you press the enter key. 4) you can then configure the switch or check the information about the switch by execut...
Page 56
Configuration remarks set the maximum number of lines the screen can contain optional by default, the screen can contain up to 24 lines. Set history command buffer size optional by default, the history command buffer can contain up to 10 commands. Set the timeout time of a user interface optional th...
Page 57
Authentication console port login configuration remarks mode optional specify to perform local authentication or remote radius authentication aaa configuration specifies whether to perform local authentication or radius authentication local authentication is performed by default. Refer to the aaa pa...
Page 59
Z the baud rate of the console port is 19,200 bps. Z the screen can contain up to 30 lines. Z the history command buffer can contain up to 20 commands. Z the timeout time of the aux user interface is 6 minutes. 2) network diagram figure 2-5 network diagram for aux user interface configuration (with ...
Page 60
To do… use the command… remarks enter system view — system-view enter aux user interface view user-interface aux 0 — required by default, users logging in to a switch through the console port are not authenticated; while those logging in through modems or telnet are authenticated. Configure to authe...
Page 61
To do… use the command… remarks optional the default timeout time of a user interface is 10 minutes. With the timeout time being 10 minutes, the connection to a user interface is terminated if no operation is performed in the user interface within 10 minutes. Set the timeout time for the user interf...
Page 62
[sysname-ui-aux0] authentication-mode password # set the local password to 123456 (in plain text). [sysname-ui-aux0] set authentication password simple 123456 # specify commands of level 2 are available to users logging in to the aux user interface. [sysname-ui-aux0] user privilege level 2 # set the...
Page 63
To do… use the command… remarks service-type terminal [ level level ] specify the service type for aux users required quit to system view — quit user-interface aux 0 enter aux user interface view — required the specified aaa scheme determines whether to authenticate users locally or remotely. Authen...
Page 64
To do… use the command… remarks optional the default timeout time of a user interface is 10 minutes. With the timeout time being 10 minutes, the connection to a user interface is terminated if no operation is performed in the user interface within 10 minutes. Set the timeout time for the user interf...
Page 65
System-view # create a local user named guest and enter local user view. [sysname] local-user guest # set the authentication password to 123456 (in plain text). [sysname-luser-guest] password simple 123456 # set the service type to terminal, specify commands of level 2 are available to users logging...
Page 66
Table 2-5 requirements for telnetting to a switch item requirement the ip address is configured for the vlan of the switch, and the route between the switch and the telnet terminal is reachable. (refer to the ip address configuration – ip performance configuration and routing protocol parts for more...
Page 67
Telnet configurations for different authentication modes table 2-7 telnet configurations for different authentication modes authentication telnet configuration description mode optional perform common configuration perform common telnet configuration none refer to table 2-6 . Configure the password ...
Page 68
Telnet configuration with authentication mode being none configuration procedure follow these steps to configure telnet with the authentication mode being none: to do… use the command… remarks enter system view — system-view enter one or more vty user interface views user-interface vty first-number ...
Page 69
Note that if you configure not to authenticate the users, the command level available to users logging in to a switch depends on the user privilege level level command configuration example 1) network requirements assume current user logins through the console port, and the current user level is set...
Page 70
To do… use the command… remarks enter system view — system-view enter one or more vty user interface views user-interface vty first-number [ last-number ] — configure to authenticate users logging in to vty user interfaces using the local password authentication-mode password required set authentica...
Page 71
Configuration example 1) network requirements assume current user logins through the console port and the current user level is set to the administrator level (level 3). Perform the following configurations for users logging in to vty 0 using telnet. Z authenticate users using the local password. Z ...
Page 72
Telnet configuration with authentication mode being scheme configuration procedure follow these steps to configure telnet with the authentication mode being scheme: to do… use the command… remarks enter system view — system-view enter the default isp domain view domain domain-name optional by defaul...
Page 73
To do… use the command… remarks optional by default, the screen can contain up to 24 lines. Set the maximum number of lines the screen can contain screen-length screen-length you can use the screen-length 0 command to disable the function to display information in pages. Optional the default history...
Page 74
Scenario authentication mode user type command command level the user privilege level level command is not executed, and the service-type command does not specify the available command level. Level 0 the user privilege level level command is not executed, and the service-type command specifies the a...
Page 75
Z configure to authenticate users logging in to vty 0 in scheme mode. Z only telnet protocol is supported in vty 0. Z the screen can contain up to 30 lines. Z the history command buffer can store up to 20 commands. Z the timeout time of vty 0 is 6 minutes. 2) network diagram figure 2-10 network diag...
Page 76
Figure 2-11 diagram for establishing connection to a console port z launch a terminal emulation utility (such as terminal in windows 3.X or hyperterminal in windows 95/windows 98/windows nt/windows 2000/windows xp) on the pc terminal, with the baud rate set to 19,200 bps, data bits set to 8, parity ...
Page 77
) appears if the password is correct. If all vty user interfaces of the switch are in use, you will fail to establish the connection and receive the message that says “all user interfaces are used, please try later!”. A 3com ethernet switch can accommodate up to five telnet connections at same time....
Page 78
Logging in using a modem go to these sections for information you are interested in: introduction z configuration on the switch side z modem connection establishment z introduction the administrator can log in to the console port of a remote switch using a modem through public switched telephone net...
Page 79
The configuration commands and the output of different modems may differ. Refer to the user manual of the modem when performing the above configuration. Switch configuration after logging in to a switch through its console port by using a modem, you will enter the aux user interface. The correspondi...
Page 80
Figure 2-15 establish the connection by using modems 4) launch a terminal emulation utility on the pc and set the telephone number to call the modem directly connected to the switch, as shown in figure 2-16 through figure 2-18 . Note that you need to set the telephone number to that of the modem dir...
Page 81
Figure 2-17 set the telephone number figure 2-18 call the modem 5) if the password authentication mode is specified, enter the password when prompted. If the password is correct, the prompt appears. You can then configure or manage the switch. You can also enter the character ? At anytime for help. ...
Page 82
Introduction switch 4500 has a web server built in. It enables you to log in to an ethernet switch through a web browser and then manage and maintain the switch intuitively by interacting with the built-in web server. To log in to a switch 4500 through the built-in web-based network management syste...
Page 83
5) when the login authentication interface (as shown in figure 2-20 ) appears, enter the user name and the password configured in step 2 and click to bring up the main page of the web-based network management system. Figure 2-20 the login page of the web-based network management system configuring t...
Page 84
# enter system view. System-view # configure the banner welcome to be displayed when a user logs into the switch through web. [sysname] header login %welcome% assume that a route is available between the user terminal (the pc) and the switch. After the above-mentioned configuration, if you enter the...
Page 85
Logging in through nms go to these sections for information you are interested in: introduction z connection establishment using nms z introduction you can also log in to a switch through a network management station (nms), and then configure and manage the switch through the agent module on the swi...
Page 86
Overview you can configure the source ip address for telnet service packets for a switch 4500 operating as a telnet client. The ip address can only be the ip address of a layer 3 interface on the switch. Figure 2-24 specify source ip address for telnet service packets as shown in figure 2-24 , suppo...
Page 87
Displaying source ip address configuration to do… use the command… remarks display the source ip address configured for the telnet service packets available in any view display telnet source-ip 2-37.
Page 88: User Control
3-1 3 user control go to these sections for information you are interested in: introduction z controlling telnet users z controlling network management users by source ip addresses z controlling web users by source ip address z refer to the acl part for information about acl. Intro defining access c...
Page 89
3-2 prere e source ip addresses, destination ip addresses and source mac addresses to be controlled and the controlling actions (permitting or denying). Controlling telnet users by source ip addresses c by s achieve ch are numbered from 2000 to 2999. F ol t addres controlling telnet users quisites t...
Page 91
3-4 s network diagram figure 3-1 network diagram for controlling telnet users using acl configuration procedure # define a basic acl. System-view [sysname] acl number 2000 [sysname-acl-basic-2000] rule 1 permit source 10.110.100.52 0 [sysname-acl-basic-2000] quit # apply the acl. [sysname] user-inte...
Page 93
3-6 [sysname] acl number 2000 [sysname-acl-basic-2000] rule 1 permit source 10.110.100.52 0 [sysname-acl-basic-2000] quit # apply the acl to only permit snmp users sourced from the ip addresses of 10.110.100.52 to access the switch. [sysname] snmp-agent community read aaa acl 2000 [sysname] snmp-age...
Page 95: Switching User Level
4-1 4 switching user level ove disconnecting the current l is 3, the user can configure system parameters; after ; when the administrators need to leave for a while or ask vel switching requires ion modes are available: the super password authentication mode and hwtacacs authentication mode. Complet...
Page 96
4-2 to do… use the command… remarks enter system view — system-view enter user interface view user-interface ber [ last-number ] — [ type ] first-num super password authentication ode ssword super authentication-m super-pa hwtacacs authentication ation-mode scheme super authentic super password auth...
Page 98
4-4 switching to a specific user level follow these steps to switch to a specific user level: to do… use the command… remarks required super [ level ] switch to a specified user level execute this command in user view. Z if no user level is specified in the super password command or the super comman...
Page 99
4-5 hwtacacs authentication configuration example z the administrator configures the user level switching authentication policies. # configure a hwtacacs authentication scheme named acs, and specify the user name and password used for user level switching on the hwtacacs server defined in the scheme...
Page 100
5 configuration file management wh n configuring configuration file e management, go to these sections for information you are introduction to configuration file interested in: z z configuration task list intro s and stores user configurations performed to a switch. It also enables users ions easily...
Page 101
Z when saving the current configuration, you can specify the file to be a main or backup or normal configuration file. When removing a configuration file from z a switch, you can specify to remove the main or backup p attribute of the file. Tup, you can specify to use the main or backup startup 1) i...
Page 102
Modes in saving the configuration z fast saving mode. This is the mode when you use the save command without the safely keyword. The mode saves the file quicker but is likely to lose the original configuration file if the switch reboots or the power fails during the process. Z safe mode. This is the...
Page 103
Z it is recommended to adopt the fast saving mode in the conditions of stable power and adopt the safe mode in the conditions of unstable power or remote maintenance. Z if you use the save command after a fabric is formed on the switch, the units in the fabric save their own startup configuration fi...
Page 104
You can specify a configuration file to be used for the next startup and configure the main/backup attribute for the configuration file. Assigning main attribute to the startup configuration file z if you save the current configuration to the main configuration file, the system will automatically se...
Page 105: Vlan Overview
6 vlan overview thi chapter covers the s se topics: vlan overview z z port-based vlan introd ll hosts are in the same broadcast domain and conn z ket or an unknown unicast packet of the switch, it will forward the the ld result in the following network problems. Dcast packets tly. Therefore, using r...
Page 106
Figure 6-1 a vlan implementation advantages of vlans compared with traditional ethernet technology, vlan technology delivers the following benefits: z confining broadcast traffic within individual vlans. This saves bandwidth and improves network performance. Z improving lan security. By assigning us...
Page 107
Figure 6-3 format of vlan tag a vlan tag comprises four fields: tag protocol identifier (tpid), priority, canonical format indicator (cfi), and vlan id. Z the 16-bit tpid field with a value of 0x8100 indicates that the frame is vlan tagged. On the 3com series ethernet switches, the default tpid is 0...
Page 108
Currently, switch 4500 adopt the ivl mode only. For more information about the mac address forwarding table, refer to the “mac address forwarding table management” part of the manual. Vlan interface hosts in different vlans cannot communicate with each other directly unless routers or layer 3 switch...
Page 109
The three types of ports can coexist on the same device. Assigning an ethernet port to specified vlans you can assign an ethernet port to a vlan to forward packets for the vlan, thus allowing the vlan on the current switch to communicate with the same vlan on the peer switch. An access port can be a...
Page 110
Table 6-3 packet processing of a hybrid port processing of an incoming packet for an untagged packet for a tagged packet processing of an outgoing packet z if the port has already been added to its default vlan, tag the packet with the default vlan tag and then forward the packet. Z if the port has ...
Page 111: Vlan Configuration
7-1 7 vlan configuration wh n configuring a vlan, go to these e sections for information you are interested in: vlan configuration z ed vlan z configuring a port-bas vlan complete the following t re vlan: vlan configuration configuration task list asks to configu task remarks basic vlan configuratio...
Page 112
7-2 z vlan 1 is the system default vlan, which needs not to be created and cannot be removed, either. Z the vlan you created in the way described above is a static vlan. On the switch, there are dynamic vlans which are registered through gvrp. For details, refer to “gvrp” part of this manual. Z when...
Page 113
7-3 the operation of enabling/disabling a vlan’s vlan interface does not influence the physical status of the ethernet ports belonging to this vlan. Displaying vlan configuration to do... Use the command... Remarks display the vlan interface information display interface vlan-interface [ vlan-id ] d...
Page 114
7-4 z to change the link type of a port from trunk to hybrid or vice versa, you must set the link type to access first. Z you can use the port link-type xrn-fabric command to configure fabric ports. For information about this command, refer to the xrn fabric module in this manual. Assigning an ether...
Page 115
7-5 to do… use the command… remarks assign the specified access port or ports to the current vlan port interface-list required by default, all ports belong to vlan 1. Configuring the default vlan for a port because an access port can belong to its default vlan only, there is no need for you to confi...
Page 116
7-6 n z configure vlan interfaces for the two vlans on switch a for forwarding data from pc 1 to server 2 at layer 3. Network diagram figure 7-1 network diagram for vlan configuratio configuration procedure z configure switch a. # create vlan 100, specify its descriptive string as dept1, and add eth...
Page 117
7-7 # create vlan 200, specify its descriptive string as dept2 and add ethernet 1/0/11 and ethernet 1/0/12 to vlan 200. [switchb] vlan 200 [switchb-vlan200] description dept2 [swotchb-vlan200] port ethernet1/0/11 ethernet 1/0/12 [switchb-vlan200] quit z configure the link between switch a and switch...
Page 118: Ip Addressing Configuration
8 ip addressing configuration when configuring ip addressing, go to these sections for information you are interested in: ip addressing overview configuring ip addresses displaying ip addressing configuration mples ip address configuration exa verview ip ad 00010000000 in binary. To make ip addresse...
Page 119
Tab ip address clas le 8-1 ses and ranges address range de class scription a 0.0.0.0 to 127.255.255.255 st at bootstrap when it does not know its ip address. This address is never a valid destination address. Addresses starting with 127 are reserved for loopback test. Packets destined to these addre...
Page 120
Adds an additional level, subnet id, to the two-level hierarchy with ip addressing, ip routing now involves three steps: delivery to the site, delivery to the subnet, and delivery to the host. Pecial addresses such as the addresses with the net id of all zeros of all ones, are not assignable to host...
Page 121
Ive ip ong w and the others are secondary ip addresses. A newly specified primary ip address overwrites the previous one if there is any. Mary and secondary ip addresses of an interface cannot reside on the same network segment; the ip address of a vlan interface must not be on the same network segm...
Page 122
Network diagram figure 8-3 network diagram for ip address configuration configuration procedure # configure an ip address for vlan-interface 1. System-view [switch] interface vlan-interface 1 [switch-vlan-interface1] ip address 129.2.2.1 255.255.255.0 ip address configuration example ii network requ...
Page 123
# set the gateway address to 172.16.1.1 on the pcs attached to the subnet 172.16.1.0/24, and to ctivity. Ss ctrl_c to break equence=1 ttl=255 time=25 ms ytes=56 sequence=2 ttl=255 time=27 ms : bytes=56 sequence=3 ttl=255 time=26 ms ce=4 ttl=255 time=26 ms ed information shows the switch can communic...
Page 124
# execute the ping host.Com command to verify that the device can use static domain name resolution ping host.Com (10.1.1.2): 56 data bytes, press ctrl_c to break es=56 sequence=2 ttl=127 time=3 ms me=3 ms --- to get the ip address 10.1.1.2 corresponding to host.Com. [sysname] ping host.Com reply fr...
Page 125: Ation Configuration
9-1 9 ation configuration ip performance optimiz w p performance, ctions for information you are interested in: hen configuring i go to these se ip performance overview g ip performance configurin ng ip displaying and maintaini performance configuration ip pe view introduction to ip performance conf...
Page 126
9-2 ges to time_wait. If non-fin re received, the sy r from receiving th fin packet. Roken after the timer expires. Size of tcp receive/send buffer f cp terminated. If fin packets are received, the tcp connection state chan packets a stem restarts the time e last non- the connection is b ollow these...
Page 127
9-3 in a secure netw can cancel the system-defi tack guard, and ase t s. Ollow these steps to cancel the system-defined acls for icmp attack guard: ork, you ned acls for icmp at thus incre he available acl resource f to do … use the command… remarks enter system view system-view — cancel the system-...
Page 128
9-4 to do… use the command… remarks clear ip traffic statistics reset ip statistics clear tcp traffic statistics reset tcp statistics clear udp traffic statistics reset udp statistics available in user view.
Page 129: Voice Vlan Configuration
10 voice vlan configuration wh n configuring voice vlan, g e o to these sections for information you are interested in: z voice vlan overview z voice vlan configuration displaying and maintaining voice vlan z n example z voice vlan configuratio voic you can have voice traffic transmitted within voic...
Page 130
Refer to dhcp operation for information about the option184 field. Following describes the way an ip phone acquires an figure 10-1 network diagram for ip phones ip address. Hown in as s figure 10-1 , the ip phone needs to work in conjunction with the dhcp server and the ncp bec 2) t in the default v...
Page 131
Dhcp server 1, and sends a new dhcp request message carrying the voice vlan tag to the e vlan. Ceiving the dhcp request, dhcp server 2 residing in the voice vlan assigns a new ip address to the ip phone and sends a tagged response message to the ip phone. After the ip phone sends voice data packets ...
Page 132
Setting the voice traffic transmission priority in order to improve transmission quality of voice traffic, the switch by default re-marks the priority of the traffic in the voice vlan as follows: z set the cos (802.1p) priority to 6. Confi r a po you the proce vlan by learning the source mac address...
Page 133
Table 10-2 matching relationship between port types and voice devices capable of acquiring ip address and voice vlan automatically voice vlan assignment mode voice traffic type port type supported or not access not supported trunk supported make sure the default vlan of the port exists and is not a ...
Page 134
Table 10-3 matching relationship between port types and voice devices acquiring voice vlan through manual configuration voice vlan assignment mode port type supported or not access not supported trunk supported make sure the default vlan of the port exists and is not a voice vlan, and the access por...
Page 135
Voice vlan packet type processing method mode packet carrying the voice vlan tag matches the oui list, the packet is transmitted in the voice vlan. Otherwise, the packet is dropped. Packet carrying any other vlan tag the packet is forwarded or dropped based on whether the receiving port is assigned ...
Page 136
To do… use the command… remarks enable the voice vlan function globally voice vlan vlan-id enable required enter ethernet port view interface interface-type interface-number required enable the voice vlan function on a port voice vlan enable required by default, voice vlan is disabled. Enable the vo...
Page 137
To do… use the command… remarks set the voice vlan aging timer voice vlan aging minutes optional the default aging timer is 1,440 minutes. Enable the voice vlan function globally voice vlan vlan-id enable required enter port view interface interface-type interface-number required enable voice vlan o...
Page 138
Z the voice vlan function can be enabled for only one vlan at one time. Z if the link aggregation control protocol (lacp) is enabled on a port, voice vlan feature cannot be enabled on it. Z voice vlan function can be enabled only for the static vlan. A dynamic vlan cannot be configured as a voice vl...
Page 139
Voice vlan configuration example voice vlan configuration example (automatic voice vlan assignment mode) network requirements create a voice vlan and configure it to operate in automatic voice vlan assignment mode to enable the port to which an ip phone is connected to join or exit the voice vlan au...
Page 140
# configure ethernet 1/0/1 as a hybrid port. [devicea-ethernet1/0/1] port link-type hybrid # configure vlan 6 as the default vlan of ethernet 1/0/1, and configure ethernet 1/0/1 to permit packets with the tag of vlan 6. [devicea-ethernet1/0/1] port hybrid pvid vlan 6 [devicea-ethernet1/0/1] port hyb...
Page 141
[devicea] voice vlan 2 enable # configure ethernet 1/0/1 to operate in manual voice vlan assignment mode. [devicea] interface ethernet 1/0/1 [devicea-ethernet1/0/1] undo voice vlan mode auto # configure ethernet 1/0/1 as a hybrid port. [devicea-ethernet1/0/1] port link-type hybrid # configure the vo...
Page 142: Gvrp Configuration
11 gvrp configuration wh n configuring gvrp, g e o to these sections for information you are interested in: z introduction to gvrp z gvrp configuration displaying and maintaining gvrp z mple z gvrp configuration exa intro garp vlan registration protocol (gvrp) is an implementation of generic attribu...
Page 143
2) garp timers timers determine the intervals of sending different types of garp messages. Garp defines four timers z the timer times out into one join message and sends z sponded for a specific period, a second one is sent. The period is z s z te information on this entity. After that, the entity r...
Page 144
Figure 11-1 format of garp packets the following table describes the fields of a garp packet. Table 11-1 description of garp packet fields field description value protocol id protocol id 1 message each message consists of two parts: attribute type and attribute list. — attribute type defined by the ...
Page 145
Gvrp as an implementation of garp, garp vlan registration protocol (gvrp) maintains dynamic vlan registration information and propagates the information to the other switches through garp. With gvrp enabled on a device, the vlan registration information received by the device from other devices is u...
Page 146
To do ... Use the command ... Remarks enter system view system-view — enable gvrp globally gvrp required by default, gvrp is disabled globally. Enter ethernet port view interface interface-type interface-number — enable gvrp on the port gvrp required by default, gvrp is disabled on the port. Z after...
Page 147
Table 11-2 relations between the timers timer lower threshold upper threshold hold 10 centiseconds this upper threshold is less than or equal to one-half of the timeout time of the join timer. You can change the threshold by changing the timeout time of the join timer. Join this lower threshold is g...
Page 148
Displaying and maintaining gvrp to do … use the command … remarks display garp statistics display garp statistics [ interface interface-list ] display the settings of the garp timers display garp timer [ interface interface-list ] display gvrp statistics display gvrp statistics [interface interface-...
Page 149
[switcha-ethernet1/0/1] port link-type trunk [switcha-ethernet1/0/1] port trunk permit vlan all # enable gvrp on ethernet1/0/1. [switcha-ethernet1/0/1] gvrp [switcha-ethernet1/0/1] quit # configure ethernet1/0/2 to be a trunk port and to permit the packets of all the vlans. [switcha] interface ether...
Page 150
The following dynamic vlans exist: 5, 7, 8, # display the vlan information dynamically registered on switch b. [switchb] display vlan dynamic total 3 dynamic vlan exist(s). The following dynamic vlans exist: 5, 7, 8, # display the vlan information dynamically registered on switch e. [switche] displa...
Page 151
5, 8, # display the vlan information dynamically registered on switch e. [switche] display vlan dynamic no dynamic vlans exist! 11-10
Page 152: Port Basic Configuration
12 port basic configuration wh n performing basic port configuration, e go to these sections for information you are interested in: z ethernet port configuration ethernet port configuration example z figuration z troubleshooting ethernet port con ration com in rate as an electrical port or an optica...
Page 153
To do... Use the command... Remarks enter system view system-view — enter ethernet port view interface-number interface interface-type — enable the ethernet port undo shutdown n command to e port. Optional by default, the port is enabled. Use the shutdow disable th set the description string for the...
Page 156
Reflector ports and fabric ports do not support the flow-control no-pauseframe-sending command. Duplicating the configuration of a port to other ports to make other ports have the same configuration as that of a specific port, you can duplicate the configuration of a port to specific ports. Specific...
Page 157
Z if you have not enabled the loopback port auto-shutdown function on the port, the port will automatically resume the normal forwarding state after the loop is removed. 2) if a loop is found on a trunk or hybrid port, the system sends log and trap messages to the terminal. If you have additionally ...
Page 158
Operation command remarks enable loopback port control on the trunk or hybrid port loopback-detection control enable optional by default, the loopback port control function is enabled on ports if the device boots with the default configuration file (config.Def); if the device boots with null configu...
Page 159
Z external: performs external loop test. In the external loop test, self-loop headers must be used on the port of the switch ( for 100m port, the self-loop headers are made from four cores of the 8-core cables, for 1000m port, the self-loop header are made from eight cores of the 8-core cables, then...
Page 160
To do... Use the command... Remarks enter ethernet port view interface interface-type interface-number — set the interval to perform statistical analysis on port traffic flow-interval interval optional by default, this interval is 300 seconds. Enabling giant-frame statistics function the giant-frame...
Page 161
To do... Use the command... Remarks disable a port from generating up/down log undo enable log updown required by default, up/down log output is enabled. Configuration examples # in the default conditions, where up/down log output is enabled, execute the shutdown command or the undo shutdown command...
Page 162
To do … use the command … remarks set the port state change delay link-delay delay-time required defaults to 0, which indicates that no delay is introduced. The delay configured in this way does not take effect for ports in dldp down state. For information about the dldp down state, refer to dldp. D...
Page 163
Network diagram figure 12-2 network diagram for ethernet port configuration configuration procedure z only the configuration for switch a is listed below. The configuration for switch b is similar to that of switch a. Z this example supposes that vlan 2, vlan 6 through vlan 50 and vlan 100 have been...
Page 164
13 link aggregation configuration wh n configuring link aggregation, g e o to these sections for information you are interested in: z overview z link aggregation classification z aggregation group categories z link aggregation configuration displaying and maintaining link aggregation configuration z...
Page 165
Table 13-1 consistency considerations for ports in an aggregation category considerations stp state of port-level stp (enabled or disabled) attribute of the link (point-to-point or otherwise) connected to the port port path cost stp priority stp packet format loop protection root protection port typ...
Page 166
Lacp is disabled on the member ports of manual aggregation groups, and you cannot enable lacp on ports in a manual aggregation group. Port status in manual aggregation group a port in a manual aggregation group can be in one of the two states: selected or unselected. In a manual aggregation group, o...
Page 167
Z the ports connected to a peer device different from the one the master port is connected to or those connected to the same peer device as the master port but to a peer port that is not in the same aggregation group as the peer port of the master port are unselected ports. Z the system sets the por...
Page 168
For an aggregation group: z when the rate or duplex mode of a port in the aggregation group changes, packet loss may occur on this port; z when the rate of a port decreases, if the port belongs to a manual or static lacp aggregation group, the port will be switched to the unselected state; if the po...
Page 169
Z a load-sharing aggregation group contains at least two selected ports, but a non-load-sharing aggregation group can only have one selected port at most, while others are unselected ports. Z when more than eight load-sharing aggregation groups are configured on a single switch, fabric ports cannot ...
Page 170
For a manual aggregation group, a port can only be manually added/removed to/from the manual aggregation group. Follow these steps to configure a manual aggregation group: to do… use the command… remarks enter system view system-view — create a manual aggregation group link-aggregation group agg-id ...
Page 171
To do… use the command… remarks create a static aggregation group link-aggregation group agg-id mode static required enter ethernet port view interface interface-type interface-number — add the port to the aggregation group port link-aggregation group agg-id required for a static lacp aggregation gr...
Page 172
To do… use the command… remarks configure the port priority lacp port-priority port-priority optional by default, the port priority is 32,768. Changing the system priority may affect the priority relationship between the aggregation peers, and thus affect the selected/unselected status of member por...
Page 173
Link aggregation configuration example ethernet port aggregation configuration example network requirements z switch a connects to switch b with three ports ethernet 1/0/1 to ethernet 1/0/3. It is required that load between the two switches can be shared among the three ports. Z adopt three differen...
Page 174
System-view [sysname] link-aggregation group 1 mode static # add ethernet 1/0/1 through ethernet 1/0/3 to aggregation group 1. [sysname] interface ethernet 1/0/1 [sysname-ethernet1/0/1] port link-aggregation group 1 [sysname-ethernet1/0/1] quit [sysname] interface ethernet 1/0/2 [sysname-ethernet1/0...
Page 175: Port Isolation Configuration
14 port isolation configuration wh n configuring port isolation, g e o to these sections for information you are interested in: z port isolation overview z port isolation configuration displaying and maintaining port isolation configuration z z port isolation configuration example port o an isolatio...
Page 176
Z when a member port of an aggregation group joins/leaves an isolation group, the other ports in the same aggregation group will join/leave the isolation group at the same time. Z for ports that belong to an aggregation group and an isolation group simultaneously, removing a port from the aggregatio...
Page 177
Network diagram figure 14-1 network diagram for port isolation configuration configuration procedure # add ethernet1/0/2, ethernet1/0/3, and ethernet1/0/4 to the isolation group. System-view system view: return to user view with ctrl+z. [sysname] interface ethernet1/0/2 [sysname-ethernet1/0/2] port ...
Page 178: Port Security Configuration
15 port security configuration wh n configuring port security, go to these e sections for information you are interested in: z port security overview z port security configuration task list displaying and maintaining port security configuration z port security configuration examples z the security m...
Page 179
T curity modes able 15-1 description of port se on the port, if you want to… use the security mode… autolearn control mac address learning secure userlogin userloginsecure userloginsecureext perform 802.1x authentication oginwitho userl ui perform mac authentication macaddresswithradius macaddressan...
Page 180
Figure 15-1 packet processing and mode transition in autolearn mode and secure mode yes change the security mode to the port receives a packet secure mode autolearn mode forward the packet yes is the source mac in the mac address table? Yes security mode? Drop the packet no is the source mac in the ...
Page 181
Mac authentication macaddresswithradius: a port in this mode performs mac authentication for users. For description of mac authentication, refer to mac address authentication operation. Security modes with the and keyword z macaddressanduserloginsecure: a port in this mode first performs mac authent...
Page 182
Security modes with the else keyword z macaddresselseuserloginsecure: as the else keyword implies, mac authentication is applied first. A port in this mode performs only mac authentication for non-802.1x frames; it performs mac authentication for 802.1x frames and then, if the authentication fails, ...
Page 183
Figure 15-4 packet processing in a security mode with the or keyword port security features the following port security features are provided: z ntk (need to know) feature: checks the destination mac addresses in outbound frames and allows frames to be sent to only devices passing authentication. Th...
Page 184
Z in userlogin mode, neither ntk nor intrusion protection will be triggered. In any other port security mode, the two features will be triggered upon detection of illegal frames. Z in userloginwithoui mode, intrusion protection will not be triggered even if the oui value does not match. Z when a por...
Page 185
To do... Use the command... Remarks enter system view — system-view required enable port security port-security enable disabled by default enabling port security resets the following configurations on a port to the bracketed defaults. Then values of these configurations cannot be changed manually; t...
Page 186
Setting the port security mode follow these steps to set the port security mode: to do... Use the command... Remarks enter system view — system-view optional in userloginwithoui mode, a port allows only one 802.1x user and one user whose source mac address contains a specified oui to pass authentica...
Page 189
Z if one user of the port has passed or is undergoing authentication, you cannot specify a guest vlan for it. Z when a user using a port with a guest vlan specified fail the authentication, the port is added to the guest vlan and users of the port can access only the resources in the guest vlan. Z m...
Page 190
Z if the amount of secure mac address entries has not yet reach the maximum number, the port will learn new mac addresses and save them as secure mac addresses. Z if the amount of secure mac address entries reaches the maximum number, the port will not be able to learn new mac addresses and the port...
Page 191
To do... Use the command... Remarks interface interface-type interface-number enter ethernet port view — required set the maximum number of secure mac addresses allowed on the port port-security max-mac-count count-value by default, there is no limit on the number of secure mac addresses. Required b...
Page 192
Network diagram figure 15-5 network diagram for port security mode autolearn configuration procedure # enter system view. System-view # enable port security. [switch] port-security enable # enter ethernet1/0/1 port view. [switch] interface ethernet 1/0/1 # set the maximum number of mac addresses all...
Page 193
Network diagram figure 15-6 network diagram for configuring port security mode macaddresswithradius configuration procedure z the following configurations involve some aaa/radius configuration commands. For details about the commands, refer to aaa operation. Z configurations on the user host and the...
Page 194
[switch-isp-aabbcc.Net] scheme radius-scheme radius1 [switch-isp-aabbcc.Net] quit # set aabbcc.Net as the default user domain. [switch] domain default enable aabbcc.Net # configure the switch to use mac addresses as usernames for authentication, specifying that the mac addresses should be lowercase ...
Page 195
Z the following configurations involve some aaa/radius configuration commands. For details about the commands, refer to aaa operation. Z configurations on the user host and the radius server are omitted. Z configure radius parameters # create a radius scheme named radius1. System-view [switch] radiu...
Page 196
[switch-isp-aabbcc.Net] quit # set aabbcc.Net as the default user domain. [switch] domain default enable aabbcc.Net # create a local user. [switch] local-user localuser [switch-luser-localuser] service-type lan-access [switch-luser-localuser] password simple localpass z configure port security # ena...
Page 197
Network diagram figure 15-8 network diagram for configuring port security mode macaddresselseuserloginsecureext configuration procedure z the following configurations involve some aaa/radius configuration commands. For details about the commands, refer to aaa operation. Z configurations on the user ...
Page 198
[switch-radius-radius1] timer realtime-accounting 15 # configure the switch to send a username without the domain name to the radius server. [switch-radius-radius1] user-name-format without-domain [switch-radius-radius1] quit # create a domain named aabbcc.Net and enter its view. [switch] domain aab...
Page 199
Network diagram figure 15-9 network diagram for configuring port security mode macaddresselseuserloginsecureext configuration procedure z the following configurations involve some aaa/radius configuration commands. For details about the commands, refer to aaa operation. Z configurations on the user ...
Page 200
[switch-radius-radius1] timer realtime-accounting 15 # configure the switch to send a username without the domain name to the radius server. [switch-radius-radius1] user-name-format without-domain [switch-radius-radius1] quit # create a domain named aabbcc.Net and enter its view. [switch] domain aab...
Page 201
Figure 15-10 network diagram for guest vlan configuration configuration procedure the following configuration steps include configurations of aaa and radius. For details about these commands, refer to aaa command. The configurations on the 802.1x client and the radius server are omitted. # configure...
Page 202
# enable port security. [switch] port-security enable # specify the switch to trigger mac authentication at an interval of 60 seconds. [switch] port-security timer guest-vlan timer 60 # create vlan 10 and assign the port ethernet 1/0/1 to it. [switch] vlan 10 [switch–vlan10] port ethernet 1/0/1 # se...
Page 203: Port Binding Configuration
16 port binding configuration wh n configuring port binding, go to these sections for infor e mation you are interested in: z port binding overview displaying and maintaining port binding configuration z example z port binding configuration g overview introd eceives a packet, it searches the binding...
Page 204
To do... Use the command... Remarks enter system view system-view — in system view am user-bind mac-addr mac-address ip-addr ip-address[ interface interface-type interface-number ] interface interface-type interface-number create a port-mac-ip binding entry in ethernet port view am user-bind { ip-ad...
Page 205
Network diagram figure 16-1 network diagram for port binding configuration configuration procedure configure switch a as follows: # enter system view. System-view # enter ethernet 1/0/1 port view. [switcha] interface ethernet 1/0/1 # bind the mac address and the ip address of host a to ethernet 1/0/...
Page 206: Dldp Configuration
17 dldp configuration wh n configuring dldp, g e o to these sections for information you are interested in: z overview dldp configuration z configuration example z dldp introd r device through the link layer, but the peer nidirectional link can cause problems such as rk. Z overview uction a special ...
Page 207
Figure 17-2 fiber broken or not connected device a ge1/0/49 ge1/0/50 device b ge1/0/49 ge1/0/50 pc dldp provides the following features: z as a link layer protocol, it works together with the physical layer protocols to monitor the link status of a device. Z the auto-negotiation mechanism at the phy...
Page 208
Dldp packet type function rsy-advertisement packets (referred to as rsy packets hereafter) advertisement packet with the rsy flag set to 1. Rsy advertisement packets are sent to request synchronizing the neighbor information when neighbor information is not locally available or a neighbor informatio...
Page 209
Dldp status a link can be in one of these dldp states: initial, inactive, active, advertisement, probe, disable, and delaydown. Table 17-2 dldp status status description initial initial status before dldp is enabled. Inactive dldp is enabled but the corresponding link is down active this state indic...
Page 210
Timer description entry aging timer when a new neighbor joins, a neighbor entry is created and the corresponding entry aging timer is enabled when an advertisement packet is received from a neighbor, the neighbor entry is updated and the corresponding entry aging timer is updated in the normal mode,...
Page 211
Z in normal dldp mode, only fiber cross-connected unidirectional links (as shown in figure 17-1 ) can be detected. Z in enhanced dldp mode, two types of unidirectional links can be detected. One is fiber cross-connected links (as shown in figure 17-1 ). The other refers to fiber pairs with one fiber...
Page 212
Packet type processing procedure no discards this echo packet no discards this echo packet sets the neighbor flag bit to bidirectional link echo packet checks whether the local device is in the probe state yes checks whether neighbor information in the packet is the same as that on the local device ...
Page 213
The local port and the neighbor is considered to be recovered to bidirectional, the port changes from the disable state to the active state, and neighboring relationship is reestablished between the local port and the neighbor. Only ports in the dldp down state can send and process recover probe pac...
Page 214
Z to ensure unidirectional links can be detected, make sure dldp is enabled on both sides; and the interval for sending advertisement packets, authentication mode, and password are the same on both sides. Z the interval for sending advertisement packets ranges from 1 to 100 seconds and defaults to 5...
Page 216
# enable dldp globally. [switcha] dldp enable # set the interval for sending dldp packets to 15 seconds. [switcha] dldp interval 15 # configure dldp to work in enhanced mode. [switcha] dldp work-mode enhance # set the dldp handling mode for unidirectional links to auto. [switcha] dldp unidirectional...
Page 217: Mac Address Table Management
18 mac address table management wh n configur e ing mac address table management, go to these sections for information you are interested in: z overview z configuring mac address table management displaying mac address table information z uration example z config this chapter describes the managemen...
Page 218
Generally, the majority of mac address entries are created and maintained through mac address ning. The following describes the mac address learning process of a switch: as shown in lear 1) figure 18-1 , user a and user b are both in vlan 1. When user a communicates with user b, the packet from user...
Page 219
Packet from user b is sent to ethernet 1/0/4, the switch records the association between the mac corresponding port to the mac address table of the switch. Ng diagram (3) address of user b and the figure 18-4 mac address learni at this time, the mac address table of the switch includes two forwardin...
Page 220
The entry recorded in th . The switch removes the mac address entry if no more packets with the mac address e entry are received within the aging time. Z s effect on dynamic mac address entries. With the destination mac address triggered update function enabled, when a switch finds a packet with a d...
Page 221
Task remarks configuring a mac address entry required setting the mac address aging timer optional setting the maximum number of mac addresses a port can learn optional enabling destination mac address triggered update optional con concerning a amic or static mac address entries). Adding a mac addre...
Page 222
Z when you add a mac address entry, the current port must belong to the vlan specified by the vlan argument in the command. Otherwise, the entry will not be added. Z if the vlan specified by the vlan argument is a dynamic vlan, after a static mac address is added, it will become a static vlan. Setti...
Page 223
Follow these steps to set the maximum number of mac addresses a port can learn: to do… use the command… remarks enter system view system-view — enter ethernet port view interface interface-type interface-number — set the maximum number of mac addresses the port can learn mac-address max-mac-count co...
Page 224
Configuration example adding a static mac address entry manually network requirements the server connects to the switch through ethernet 1/0/2. To prevent the switch from broadcasting packets destined for the server, it is required to add the mac address of the server to the mac address table of the...
Page 225: Auto Detect Configuration
19 auto detect configuration when configuring the auto detect function, go to these sections for information you are interested in: n z introduction to the auto detect functio auto detect configuration z z auto detect configuration examples intro number of icmp requests and the timeout waiting for a...
Page 226
Task remarks auto detect implementation in vl ackup an interface b optional auto detect basic configuration follo he w these steps to configure t auto detect function: to do… use the command… remarks enter system view system-view — create a detected group and detect-group group-number enter detected...
Page 227
To void such problems, you can configure another route to bac a k up the static route and use the auto te is valid, packets are forwarded ccording to the static route, and the other route is standby. If the static route is invalid, packets are forwarded according to the backup route. In this way, th...
Page 228
P implement vlan interfaces backup. When data can be transmitted through erfaces on the switch to the same destination, configure one of the vlan interface as the ctive interface and the other as the standby interface. The standby interface is enabled automatically detect function is implemented s: ...
Page 229
Z on switch a, configure a static route to switch c. Hen the detected group 8 is reachable. G of the auto detect function, configure a static route to switch a on n iagram z enable the static route w z to ensure normal operatin switch c. Etwork d figure 19-2 network diagram for implementing the auto...
Page 230
Network diagram figure 19-3 network diagram for vlan interface backup configuration procedure configure the ip addresses of all the interfaces as shown in figure 19-3 . The configuration procedure is omitted. # enter system view. System-view # create auto detected group 10. [switcha] detect-group 10...
Page 231: Mstp Configuration
20-1 20 mstp configuration go to these sections for information you are interested in: z overview z mstp configuration task list z configuring root bridge z configuring leaf nodes z performing mcheck operation z configuring guard functions z configuring digest snooping z configuring rapid transition...
Page 232
20-2 stp identifies the network topology by transmitting bpdus between stp compliant network devices, typically switches and routers. Bpdus contain sufficient information for the network devices to complete the spanning tree calculation. In stp, bpdus come in two types: z configuration bpdus, used t...
Page 233
20-3 figure 20-1 a schematic diagram of designated bridges and designated ports all the ports on the root bridge are designated ports. 4) bridge id a bridge id consists of eight bytes, where the first two bytes represent the bridge priority of the device, and the latter six bytes represent the mac a...
Page 234
20-4 6) port id a port id used on a 3com switch 4500 consists of two bytes, that is, 16 bits, where the first six bits represent the port priority, and the latter ten bits represent the port number. The default priority of all ethernet ports on 3com switches 4500 is 128. You can use commands to conf...
Page 235
20-5 table 20-2 selection of the optimum configuration bpdu step description 1 upon receiving a configuration bpdu on a port, the device performs the following processing: z if the received configuration bpdu has a lower priority than that of the configuration bpdu generated by the port, the device ...
Page 236
20-6 step description 3 the device compares the calculated configuration bpdu with the configuration bpdu on the port whose role is to be determined, and acts as follows based on the comparison result: z if the calculated configuration bpdu is superior, this port will serve as the designated port, a...
Page 237
20-7 device port name bpdu of port bp1 {1, 0, 1, bp1} device b bp2 {1, 0, 1, bp2} cp1 {2, 0, 2, cp1} device c cp2 {2, 0, 2, cp2} z comparison process and result on each device the following table shows the comparison process and result on each device. Table 20-5 comparison process and result on each...
Page 238
20-8 device comparison process bpdu of port after comparison z port cp1 receives the configuration bpdu of device a {0, 0, 0, ap2}. Device c finds that the received configuration bpdu is superior to the configuration bpdu of the local port {2, 0, 2, cp1}, and updates the configuration bpdu of cp1. Z...
Page 239
20-9 figure 20-3 the final calculated spanning tree to facilitate description, the spanning tree calculation process in this example is simplified, while the actual process is more complicated. 3) the bpdu forwarding mechanism in stp z upon network initiation, every switch regards itself as the root...
Page 240
20-10 for this reason, the protocol uses a state transition mechanism. Namely, a newly elected root port and the designated ports must go through a period, which is twice the forward delay time, before they transit to the forwarding state. The period allows the new configuration bpdus to be propagat...
Page 241
20-11 z mstp supports mapping vlans to multiple spanning tree (mst) instances (mstis) by means of a vlan-to-instance mapping table. Mstp introduces instances (which integrates multiple vlans into a set) and can bind multiple vlans to an instance, thus saving communication overhead and improving reso...
Page 242
20-12 3) msti a multiple spanning tree instance (msti) refers to a spanning tree in an mst region. Multiple spanning trees can be established in one mst region. These spanning trees are independent of each other. For example, each region in figure 20-4 contains multiple spanning trees known as mstis...
Page 243
20-13 z a region boundary port is located on the boundary of an mst region and is used to connect one mst region to another mst region, an stp-enabled region or an rstp-enabled region. Z an alternate port is a secondary port of a root port or master port and is used for rapid transition. With the ro...
Page 244
20-14 z forwarding state. Ports in this state can forward user packets and receive/send bpdu packets. Z learning state. Ports in this state can receive/send bpdu packets but do not forward user packets. Z discarding state. Ports in this state can only receive bpdu packets. Port roles and port states...
Page 245
20-15 in addition to the basic mstp functions, 3com switch 4500 also provides the following functions for users to manage their switches. Z root bridge hold z root bridge backup z root guard z bpdu guard z loop guard z tc-bpdu attack guard protocols and standards mstp is documented in: z ieee 802.1d...
Page 246
20-16 task remarks configuring the maximum transmitting rate on the current port optional the default value is recommended. Configuring the current port as an edge port optional setting the link type of a port to p2p optional enabling mstp required to prevent network topology jitter caused by other ...
Page 247
20-17 configuring root bridge configuring an mst region configuration procedure follow these steps to configure an mst region: to do... Use the command... Remarks enter system view system-view — enter mst region view stp region-configuration — configure the name of the mst region region-name name re...
Page 248
20-18 z mstp-enabled switches are in the same region only when they have the same format selector (a 802.1s-defined protocol selector, which is 0 by default and cannot be configured), mst region name, vlan-to-instance mapping table, and revision level. Z the 3com switches 4500 support only the mst r...
Page 249
20-19 specify the current switch as the secondary root bridge of a spanning tree follow these steps to specify the current switch as the secondary root bridge of a spanning tree: to do... Use the command... Remarks enter system view system-view — specify the current switch as the secondary root brid...
Page 250
20-20 configuring the bridge priority of the current switch root bridges are selected according to the bridge priorities of switches. You can make a specific switch be selected as a root bridge by setting a lower bridge priority for the switch. An mstp-enabled switch can have different bridge priori...
Page 253
20-23 configuring the network diameter of the switched network in a switched network, any two switches can communicate with each other through a specific path made up of multiple switches. The network diameter of a network is measured by the number of switches; it equals the number of the switches o...
Page 254
20-24 to do... Use the command... Remarks configure the max age parameter stp timer max-age centiseconds required the max age parameter defaults to 2,000 centiseconds (namely, 20 seconds). All switches in a switched network adopt the three time-related parameters configured on the cist root bridge. ...
Page 255
20-25 configuring the timeout time factor when the network topology is stable, a non-root-bridge switch regularly forwards bpdus received from the root bridge to its neighboring devices at the interval specified by the hello time parameter to check for link failures. Normally, a switch regards its u...
Page 256
20-26 to do... Use the command... Remarks enter system view system-view — enter ethernet port view interface interface-type interface-number — configure the maximum transmitting rate stp transmit-limit packetnum required the maximum transmitting rate of all ethernet ports on a switch defaults to 10....
Page 257
20-27 to do... Use the command... Remarks enter ethernet port view interface interface-type interface-number — configure the port as an edge port stp edged-port enable required by default, all the ethernet ports of a switch are non-edge ports. On a switch with bpdu guard disabled, an edge port becom...
Page 258
20-28 setting the link type of a port to p2p in ethernet port view follow these steps to specify whether the link connected to a port is point-to-point link in ethernet port view: to do... Use the command... Remarks enter system view system-view — enter ethernet port view interface interface-type in...
Page 259
20-29 to do... Use the command... Remarks disable mstp on specified ports stp interface interface-list disable optional by default, mstp is enabled on all ports. To enable a switch to operate more flexibly, you can disable mstp on specific ports. As mstp-disabled ports do not participate in spanning...
Page 260
20-30 configuring the timeout time factor refer to configuring the timeout time factor . Configuring the maximum transmitting rate on the current port refer to configuring the maximum transmitting rate on the current port . Configuring a port as an edge port refer to configuring the current port as ...
Page 261
20-31 rate operation mode (half-/full-duplex) 802.1d-1998 ieee 802.1t latency standard 1,000 mbps full-duplex aggregated link 2 ports aggregated link 3 ports aggregated link 4 ports 4 3 3 3 20,000 10,000 6,666 5,000 20 18 16 14 10 gbps full-duplex aggregated link 2 ports aggregated link 3 ports aggr...
Page 262
20-32 1) perform this configuration in system view system-view [sysname] stp interface ethernet 1/0/1 instance 1 cost 2000 2) perform this configuration in ethernet port view system-view [sysname] interface ethernet 1/0/1 [sysname-ethernet1/0/1] stp instance 1 cost 2000 configuration example (b) # c...
Page 263
20-33 to do... Use the command... Remarks enter ethernet port view interface interface-type interface-number — configure port priority for the port stp [ instance instance-id ] port priority priority required. The default port priority is 128. Changing port priority of a port may change the role of ...
Page 264
20-34 configuration procedure you can perform the mcheck operation in the following two ways. Perform the mcheck operation in system view follow these steps to perform the mcheck operation in system view: to do... Use the command... Remarks enter system view system-view — perform the mcheck operatio...
Page 265
20-35 shuts down the edge ports that receive configuration bpdus and then reports these cases to the administrator. Ports shut down in this way can only be restored by the administrator. You are recommended to enable bpdu guard for devices with edge ports configured. Configuration prerequisites mstp...
Page 266
20-36 forwarding packets (as if it is disconnected from the link). It resumes the normal state if it does not receive any configuration bpdus with higher priorities for a specified period. Z you are recommended to enable root guard on the designated ports of a root bridge. Z loop guard, root guard, ...
Page 267
20-37 configuring loop guard a switch maintains the states of the root port and other blocked ports by receiving and processing bpdus from the upstream switch. These bpdus may get lost because of network congestions or unidirectional link failures. If a switch does not receive bpdus from the upstrea...
Page 268
20-38 period, the switch may be busy in removing the mac address table and arp entries, which may affect spanning tree calculation, occupy large amount of bandwidth and increase switch cpu utilization. With the tc-bpdu attack guard function enabled, a switch performs a removing operation upon receiv...
Page 269
20-39 configuring digest snooping introduction according to ieee 802.1s, two interconnected switches can communicate with each other through mstis in an mst region only when the two switches have the same mst region-related configuration. Interconnected mstp-enabled switches determine whether or not...
Page 270
20-40 to do... Use the command... Remarks return to system view quit — enable the digest snooping feature globally stp config-digest-snooping required the digest snooping feature is disabled globally by default. Display the current configuration display current-configuration available in any view z ...
Page 271
20-41 figure 20-6 and figure 20-7 illustrate the rapid transition mechanisms on designated ports in rstp and mstp. Figure 20-6 the rstp rapid transition mechanism root port blocks other non- edge ports, changes to forwarding state and sends agreement to upstream device downstream switch upstream swi...
Page 272
20-42 designated ports, instead of waiting for agreement packets from the upstream switch. This enables designated ports of the upstream switch to change their states rapidly. Configuring rapid transition configuration prerequisites as shown in figure 20-8 , a 3com switch 4500 is connected to anothe...
Page 273
20-43 z the rapid transition feature can be enabled on only root ports or alternate ports. Z if you configure the rapid transition feature on a designated port, the feature does not take effect on the port. Configuring vlan-vpn tunnel introduction the vlan-vpn tunnel function enables stp packets to ...
Page 274
20-44 to do... Use the command... Remarks enable the vlan-vpn tunnel function globally vlan-vpn tunnel required the vlan-vpn tunnel function is disabled by default. Enter ethernet port view interface interface-type interface-number make sure that you enter the ethernet port view of the port for whic...
Page 275
20-45 system-view [sysname] stp instance 1 portlog # enable log/trap output for the ports of all instances. System-view [sysname] stp portlog all enabling trap messages conforming to 802.1d standard a switch sends trap messages conforming to 802.1d standard to the network management device in the fo...
Page 276
20-46 mstp configuration example network requirements implement mstp in the network shown in figure 20-10 to enable packets of different vlans to be forwarded along different mstis. The detailed configurations are as follows: z all switches in the network belong to the same mst region. Z packets of ...
Page 277
20-47 # specify switch a as the root bridge of msti 1. [sysname] stp instance 1 root primary 2) configure switch b # enter mst region view. System-view [sysname] stp region-configuration # configure the region name, vlan-to-instance mapping table, and revision level for the mst region. [sysname-mst-...
Page 278
20-48 vlan-vpn tunnel configuration example network requirements z switch c and switch d are the access devices for the service provider network. Z the 3com switches 4500 operate as the access devices of the customer networks, that is, switch a and switch b in the network diagram. Z switch c and swi...
Page 279
20-49 [sysname] vlan-vpn tunnel # add gigabitethernet 1/0/1 to vlan 10. [sysname] vlan 10 [sysname-vlan10] port gigabitethernet 1/0/1 [sysname-vlan10] quit # enable the vlan vpn function on gigabitethernet 1/0/1. [sysname] interface gigabitethernet 1/0/1 [sysname-gigabitethernet1/0/1] port access vl...
Page 280: Ip Routing Protocol Overview
21 ip routing protocol overview go to these sections for information you are interested in: z introduction to ip route and routing table z routing protocol overview displaying and maintaining a routing table z the term router in this chapter refers to a router in a generic sense or an ethernet switc...
Page 281
Address and network mask, you can get the address of the network segment where the destination host or router resides. For example, if the destination address is 129.102.8.10 and the mask is 255.255.0.0, the address of the network segment where the destination host or router resides is l z z discove...
Page 282
15.0.0.0 17.0.0.2 1 16.0.0.0 16.0.0.2 2 17.0.0.0 17.0.0.1 1 routing protocol overview static all, stable c routing is suitable for large networks. It is her requirements on the system than static routing, but also occupies a certain amount of network resources. Classification of dynamic routing prot...
Page 283
Rout outes (including static routes) to the same destination. Can ority. The route found by the routing protocol with th eferred. T ng table lists some routing protocols and the default priorities for routes found by them: table 21-1 routing protocols and priorities of their d lt route ing protocols...
Page 284
Routing information sharing as different routing protocols use different algorithms to calculate routes, they may discover different routes. In a large network with multiple routing protocols, it is required for routing protocols to share their routing information. Each routing protocol shares routi...
Page 285: Static Route Configuration
22-1 22 static route configuration wh n configuring a static route, e go to these sections for information you are interested in: z introduction to static route z static route configuration z displaying and maintaining static routes static route configuration example z shooting a static route z trou...
Page 286
22-2 defau avoid too larg whe in the routing table, default route, the packet will be discarded and an icmp destination unreachable or network unreachable packet will be returned to the source. Gured or generated by some dynamic routing protocols, such as static route configuration conf r before con...
Page 288
22-4 0 1.1.2.2 ic 1.1.4.0 255.255.255.0 1.1.2.2 .2.2 0 1.1.3.1 ic 1.1.5.0 255.255.255.0 1.1.3.1 .3.1 n switch b. Dure is omitted. # set the default gateway address of host b to 1.1.4.1. Detailed configuration procedure is omitted. To 1.1.1.1. Detailed configuration procedure is omitted. Troubleshoot...
Page 289: Rip Configuration
23-1 23 rip configuration wh n configuring rip, go to these e sections for information you are interested in: z rip overview z rip configuration task list z rip configuration example shooting rip configuration z trouble the term router in this chapter refers to a router in a generic sense or an ethe...
Page 290
23-2 : cost from the local router to the destination. Time: time elapsed since the routing entry was last updated. The time is reset to 0 every time rip timers gar z z n it is deleted from the routing table. During the garbage-collect timer e route with the routing metric set to 16. If no update is ...
Page 291
23-3 task remarks enabling rip on the interfaces attached to a specified network segment required setting the rip operating status on an interface optional configuring basic rip functions specifying the rip version on an interface optional setting the additional routing metrics of an interface optio...
Page 292
23-4 z related rip commands configured in interface view can take effect only after rip is enabled. Z rip operates on the interfaces attached to a specified network segment. When rip is disabled on an interface, it does not operate on the interface, that is, it neither receives/sends routes on the i...
Page 293
23-5 z set the preference of rip to change the preference order of routing protocols. This order makes sense when more than one route to the same destination is discovered by multiple routing protocols. Z redistribute external routes in an environment with multiple routing protocols. Configuration p...
Page 294
23-6 follow these steps to configure rip route summarization: to do... Use the command... Remarks enter system view system-view — enter rip view rip — enable rip-2 automatic route summarization summary required enabled by default disabling the router from receiving host routes in some special cases,...
Page 295
23-7 z the filter-policy import command filters the rip routes received from neighbors, and the routes being filtered out will neither be added to the routing table nor be advertised to any neighbors. Z the filter-policy export command filters all the routes to be advertised, including the routes re...
Page 296
23-8 rip network adjustment and optimization in some special network environments, some rip features need to be configured and rip network performance needs to be adjusted and optimized. By performing the configuration mentioned in this section, the following can be implemented: z changing the conve...
Page 297
23-9 split horizon cannot be disabled on a point-to-point link. Configuring rip-1 packet zero field check follow these steps to configure rip-1 packet zero field check: to do... Use the command... Remarks enter system view system-view — enter rip view rip — enable the check of the must be zero field...
Page 298
23-10 configuring rip to unicast rip packets follow these steps to configure rip to unicast rip packets: to do... Use the command... Remarks enter system view system-view — enter rip view rip — configure rip to unicast rip packets peer ip-address required when rip runs on the link that does not supp...
Page 299
23-11 switch c vlan-int1 110.11.2.3/24 vlan-int4 117.102.0.1/16 configuration procedure only the configuration related to rip is listed below. Before the following configuration, make sure the ethernet link layer works normally and the ip addresses of vlan interfaces are configured correctly. 1) con...
Page 300
24-1 24 ip route policy configuration wh n configuring an ip route policy, go to the e se sections for information you are interested in: z ip route policy overview z ip route policy configuration task list z displaying ip route policy z ip route policy configuration example shooting ip route policy...
Page 301
24-2 iguration, refer to the part discussing acl. Ip gateway option to specify that only ge in the network er. Once an entry is matched, the ip-prefix list filtering is passed and r given routing information and the attributes of the against the node is successful, and the actions can be the attribu...
Page 302
24-3 z if-match clause: defines matching rules; that is, the filtering conditions that the routing information should satisfy for passing the current route policy. The matching objects are some attributes of the routing information. Z apply clause: specifies actions, which are the configuration comm...
Page 304
24-5 ip-prefix configuration ip-prefix plays a role similar to acl and but is more flexible and easier to understand. When ip-prefix is applied to filtering routing information, its matching object is the destination address information field of routing information. Configuration prerequisites befor...
Page 305
24-6 ip route policy configuration example controlling rip packet cost to implement dynamic route backup network requirements the required speed of convergence in the small network of a company is not high. The network provides two services. Main and backup links are provided for each service for th...
Page 306
24-7 z for the oa server, the main link is between switch a and switch c, while the backup link is between switch b and switch c. Z for the service server, the main link is between switch b and switch c, while the backup link is between switch a and switch c. Z apply a route policy to control the co...
Page 307
24-8 [switchc-route-policy] if-match interface vlan-interface2 [switchc-route-policy] if-match ip-prefix 2 [switchc-route-policy] apply cost 6 [switchc-route-policy] quit # create node 30 with the matching mode being permit in the route policy. Define if-match clauses. Apply the cost 6 to routes mat...
Page 308
24-9 2) display data forwarding paths when the main link of the oa server between switch a and switch c is down. Display ip routing-table routing table: public net destination/mask protocol pre cost nexthop interface 1.0.0.0/8 rip 100 6 6.6.6.5 vlan-interface2 3.0.0.0/8 rip 100 5 6.6.6.5 vlan-interf...
Page 309: Multicast Overview
25 multicast overview in this manual, the term “router” refers to a router in the generic sense or a layer 3 ethernet switch nning an ip multicast protocol. Ru mult , online auctions, video on demand (vod), and tele-education in the network, packets are sent in three modes: unicast, broadcast and mu...
Page 310
Assume that hosts b, d and e need this information. The source server establishes transmission channels for the devices of these users respectively. As the transmitted traffic over the network is in direct proportion to the number of users that receive this information, when a large number of users ...
Page 311
Inform er of users ficient. Require specified information, the s the information only once. With rough multicast routing protocols, shown in figure 25-3 ation transmission in the multicast mode as described in the previous sections, unicast is suitable for networks with sparsely distributed users, w...
Page 312
Z all receivers interested in the same information form a multicast group. Multicast groups are not subject to geographic restrictions. R 3 multicast device. In nage multicast group bers. F a better t, yo programs, a z a router that supports layer 3 multicast is called multicast router or laye addit...
Page 313
A li smission. By cast greatly multicast supports the following applications: ultimedia and flow media, such as web tv, web radio, and real-time video/audio conferencing. N. Tions (stock), and so on. Pplication. Multicast models asm model model, any sender can become a multicast source and send info...
Page 314
Z host registration: what receivers reside on the network? Z technologies of discovering a multicast source: which multicast source should the receivers receive information from? Z is information transported? The ing mechanism, host registration, multicast routing, and z source to a group of receive...
Page 315
Note that: the ip addresses of a perma z nent multicast group keep unchanged, while the members of the anent multicast group. Z ent multicast groups can be used by tem class d ip addresses range from 224.0. Group can be changed. Z there can be any number of, or even zero, members in a perm those ip ...
Page 316
Class description d address range 224.0.0.18 virtual router redundancy protocol (vrrp) 224.0.0.19 to 224.0.0.255 other protocols like h n aving reserved the private network segment 10.0.0.0/8 for unicast, iana has also reserved the etwork segment 239.0.0.0/8 for multicast. These are administratively...
Page 317
Z generally, we refer to ip multicast working at the network layer as layer 3 multicast and the corresponding multicast protocols as layer 3 multicast protocols, which include igmp, pim, and msdp; we refer to ip multicast working at the data link layer as layer 2 multicast and the corresponding mult...
Page 318
Z an inter-domain multicast routing protocol is used for delivery of multicast information between two ass. So far, mature solutions include multicast source discovery protocol (msdp). For the ssm model, multicast routes are not divided into inter-domain routes and intra-domain routes. Since receive...
Page 319
Z in the network, multicast packet transmission is based on the guidance of the multicast forwarding table derived from the unicast routing table or the multicast routing table specially provided for multicast. Z to process the same multicast information from different peers received on different in...
Page 320
Considers the path along which the packet from the rpf neighbor arrived on the rpf interface to be the shortest path that leads back to the source. Assume that unicast routes exist in the network, as shown in figure 25-7 . Multicast packets travel along the spt from the multicast source to the recei...
Page 321
26-1 26 common multicast configuration in this manual, the term “router” refers to a router in the generic sense or a layer 3 ethernet switch nning an ip multicast protocol. Ru com table 26-1 complete the following ta rform common multicast configurations: mon multicast configuration sks to pe task ...
Page 322
26-2 to do... Use the command... Remarks enter ethernet port view interface interface-type interface-number — configure multicast source port suppression multicast-source-deny t source port suppression is disabled by default. Optional multicas conf warding entries dynamically through a layer 2 t for...
Page 323
26-3 z if the multicast mac address entry to be created already exists, the system gives you a prompt. Z if you want to add a port to a multicast mac address entry created through the mac-address multicast command, you need to remove the entry first, create this entry again, and then add the specifi...
Page 324: Igmp Snooping Configuration
27-1 27 igmp snooping configuration wh n configuring igmp snooping e , go to these sections for information you are interested in: z igmp snooping overview z configuring igmp snooping z displaying and maintaining igmp snooping igmp snooping configuration examples z troubleshooting igmp snooping z in...
Page 325
27-2 e figure 27-1 before and after igmp snooping is enabled on layer 2 devic multicast packet transmission without igmp snooping source multicast router host a receiver host b host c receiver multicast packets layer 2 switch multicast packet transmission when igmp snooping runs source multicast rou...
Page 326
27-3 member ports. The switch records all member ports on the local device in the igmp snooping forwarding table. Port aging timers in igmp snooping and related messages and actions table 27-1 port aging timers in igmp snooping and related messages and actions timer description message before expiry...
Page 327
27-4 a switch will not forward an igmp report through a non-router port for the following reason: due to the igmp report suppression mechanism, if member hosts of that multicast group still exist under non-router ports, the hosts will stop sending reports when they receive the message, and this prev...
Page 328
27-5 configuring igmp snooping complete the following tasks to configure igmp snooping: task remarks enabling igmp snooping required configuring the version of igmp snooping optional configuring timers optional configuring fast leave processing optional configuring a multicast group filter optional ...
Page 329
27-6 z although both layer 2 and layer 3 multicast protocols can run on the same switch simultaneously, they cannot run simultaneously on a vlan or its corresponding vlan interface. Z before enabling igmp snooping in a vlan, be sure to enable igmp snooping globally in system view; otherwise the igmp...
Page 330
27-7 follow these steps to configure timers: to do... Use the command... Remarks enter system view system-view — configure the aging timer of the router port igmp-snooping router-aging-time seconds optional by default, the aging time of the router port is 105 seconds. Configure the general query res...
Page 331
27-8 z the fast leave processing function works for a port only if the host attached to the port runs igmpv2 or igmpv3. Z the configuration performed in system view takes effect on all ports of the switch if no vlan is specified; if one or more vlans are specified, the configuration takes effect on ...
Page 332
27-9 z a port can belong to multiple vlans, you can configure only one acl rule per vlan on a port. Z if no acl rule is configured, all the multicast groups will be filtered. Z since most devices broadcast unknown multicast packets by default, this function is often used together with the function o...
Page 333
27-10 configuring igmp snooping querier in an ip multicast network running igmp, one dedicated multicast device is responsible for sending igmp general queries, and this router or layer 3 switch is called the igmp querier. However, a layer 2 multicast switch does not support igmp, and therefore cann...
Page 334
27-11 configuring the source address to be carried in igmp queries follow these steps to configure the source address to be carried in igmp queries: to do... Use the command... Remarks enter system view system-view — enter vlan view vlan vlan-id — configure the source ip address of igmp general quer...
Page 335
27-12 to do... Use the command... Remarks enter system view system-view — enter ethernet port view interface interface-type interface-number — configure the current port as a static member port for a multicast group in a vlan multicast static-group group-address vlan vlan-id required by default, no ...
Page 336
27-13 in vlan view follow these steps to configure a static router port in vlan view: to do... Use the command... Remarks enter system view system-view — enter vlan view vlan vlan-id — configure a specified port as a static router port multicast static-router-port interface-type interface-number req...
Page 337
27-14 z before configuring a simulated host, enable igmp snooping in vlan view first. Z the port to be configured must belong to the specified vlan; otherwise the configuration does not take effect. Z you can use the source-ip source-address command to specify a multicast source address that the por...
Page 338
27-15 to do... Use the command... Remarks create a multicast vlan and enter vlan view vlan vlan-id — return to system view quit — enter vlan interface view interface vlan-interface vlan-id — enable igmp igmp enable required by default, the igmp feature is disabled. Return to system view quit — enter...
Page 340
27-17 n network diagram figure 27-3 network diagram for igmp snooping configuratio configuration procedure 1) configure the ip address of each interface configure an ip address and subnet mask for each interface as per figure 27-3 . The detailed configuration steps are omitted. 2) configure router a...
Page 341
27-18 display igmp-snooping group vlan100 total 1 ip group(s). Total 1 mac group(s). Vlan(id):100. Total 1 ip group(s). Total 1 mac group(s). Static router port(s): dynamic router port(s): ethernet1/0/1 ip group(s):the following ip group(s) match to one mac group. Ip group address: 224.1.1.1 static ...
Page 342
27-19 device device description networking description host a user 1 host a is connected to ethernet 1/0/1 on switch b. Host b user 2 host b is connected to ethernet 1/0/2 on switch b. In this configuration example, you need to configure the ports that connect switch a and switch b to each other as ...
Page 343
27-20 [switcha-ethernet1/0/10] port hybrid vlan 10 tagged [switcha-ethernet1/0/10] quit # configure the interface ip address of vlan 10 as 168.10.2.1, and enable pim-dm and igmp. [switcha] interface vlan-interface 10 [switcha-vlan-interface10] ip address 168.10.2.1 255.255.255.0 [switcha-vlan-interf...
Page 344
27-21 1) igmp snooping is not enabled. Z use the display current-configuration command to check the status of igmp snooping. Z if igmp snooping is disabled, check whether it is disabled globally or in the specific vlan. If it is disabled globally, use the igmp-snooping enable command in both system ...
Page 345: 802.1X Configuration
28 802.1x configuration wh n configuring 802.1x, go to these sec e tions for information you are interested in: z introduction to 802.1x z introduction to 802.1x configuration z basic 802.1x configuration z advanced 802.1x configuration displaying and maintaining 802.1x configuration z z configurati...
Page 346
Figure 28-1 architecture of 802.1x authentication ches client program on the supplicant system. Note that the client program must support the extensible authentication cator system is usually an 802.1x-supported z rver system is an entity that provides authentication service to the ed. Pae a po rela...
Page 347
Z o packets can pass through it. The valid direction of a controlled port figure it to be a unidirectional port, which t cant systems connected to the port can access the network without being authenticated after one supplicant the m ieee 802.1x informatio figure 28-2 the mechanism of an 802.1x auth...
Page 348
Figure 28-3 the format of an eapol packet z the type field can be one of the following: et is an eap-packet, which carries authentication information. Off packet, which sends logging off requests. Y packet, which carries key information. Ncapsulated-asf-alert packet, which is used to g standards for...
Page 349
Z the length field indicates the size of an eap packet, which includes the code, identifier, length, se format differs with the code field. And data fields. Z the data field carries the eap packet, who a success or failure packet does not contain the data field, so the length field of it is 4. Figur...
Page 350
E r this mo (with a valu tran ble authentication protocol (peap), are available in the m, which in turn encrypts the s security ransferred to the right implements bidirectional authentication it message using a tunnel performs new eap ap elay mode de is defined in 802.1x. In this mode, eap packets a...
Page 351
The z est by sending an z z ius server retrieves the user name from the erated key, and sends the key to the switch through an radius z switch, the client program encrypts the password of the supplicant system with the key and sends the encrypted password (contained in an eap-response/md5 challenge ...
Page 352
Figure 28-9 802.1x authentication procedure (in eap terminating mode) the authentication procedure in eap terminating mode is the same as that in the eap relay mode except that the randomly-generated key in the eap terminating mode is generated by the switch, and that it is the switch that sends the...
Page 353
Z re-authentication timer (reauth-period). The switch initiates 802.1x re-authentication at the interval set by the re-authentication timer. Z radius server timer (server-timeout). This timer sets the server-timeout period. After sending an authentication request packet to the radius server, the swi...
Page 354
In response to any of the three cases, a switch can optionally take the following measures: z only disconnects the supplicant system but sends no trap packets. Z sends trap packets without disconnecting the supplicant system. This function needs the cooperation of 802.1x client and a cams server. Z ...
Page 355
Z the switch sends authentication triggering request (eap-request/identity) packets to all the 802.1x-enabled ports. Z after the maximum number retries have been made and there are still ports that have not sent any response back, the switch will then add these ports to the guest vlan. Z users belon...
Page 356
Z the radius server has the switch perform 802.1x re-authentication of users. The radius server sends the switch an access-accept packet with the termination-action attribute field of 1. Upon receiving the packet, the switch re-authenticates the user periodically. Z you enable 802.1x re-authenticati...
Page 357
Basic 802.1x configuration configuration prerequisites z configure isp domain and the aaa scheme to be adopted. You can specify a radius scheme or a local scheme. Z ensure that the service type is configured as lan-access (by using the service-type command) if local authentication scheme is adopted....
Page 358
To do… use the command… remarks enable online user handshaking dot1x handshake enable optional by default, online user handshaking is enabled. Enter ethernet port view interface interface-type interface-number — enable the handshake packet protection function dot1x handshake secure optional by defau...
Page 359
To do… use the command... Remarks set the maximum retry times to send request packets dot1x retry max-retry-value optional by default, the maximum retry times to send a request packet is 2. That is, the authenticator system sends a request packet to a supplicant system for up to two times by default...
Page 361
To do... Use the command... Remarks set the client version checking period timer dot1x timer ver-period ver-period-value optional by default, the timer is set to 30 seconds. As for the dot1x version-user command, if you execute it in system view without specifying the interface-list argument, the co...
Page 362
Z the guest vlan function is available only when the switch operates in the port-based authentication mode. Z only one guest vlan can be configured for each switch. Z the guest vlan function cannot be implemented if you configure the dot1x dhcp-launch command on the switch to enable dhcp-triggered a...
Page 363
During re-authentication, the switch always uses the latest re-authentication interval configured, no matter which of the above-mentioned two ways is used to determine the re-authentication interval. For example, if you configure a re-authentication interval on the switch and the switch receives an ...
Page 364
A real-time accounting packet to the radius servers once in every 15 minutes. A user name is sent to the radius servers with the domain name truncated. Z the user name and password for local 802.1x authentication are “localuser” and “localpass” (in plain text) respectively. The idle disconnecting fu...
Page 365
[sysname-radius-radius1] secondary authentication 10.11.1.2 [sysname-radius-radius1] secondary accounting 10.11.1.1 # set the password for the switch and the authentication radius servers to exchange messages. [sysname-radius-radius1] key authentication name # set the password for the switch and the...
Page 366
29-1 29 quick ead deployment configuration wh n configuring quick ead deployment, e go to these sections for information you are interested in: z introduction to quick ead deployment z configuring quick ead deployment z displaying and maintaining quick ead deployment quick ead deployment configurati...
Page 367
29-2 configuring quick ead deployment configuration prerequisites z enable 802.1x on the switch. Z set the access mode to auto for 802.1x-enabled ports. Configuration procedure configuring a free ip range a free ip range is an ip range that users can access before passing 802.1x authentication. Foll...
Page 368
29-3 large number of users log in but cannot pass authentication, the switch may run out of acl resources, preventing other users from logging in. A timer called acl timer is designed to solve this problem. You can control the usage of acl resources by setting the acl timer. The acl timer starts onc...
Page 369
29-4 t network diagram figure 29-1 network diagram for quick ead deploymen configuration procedure before enabling quick ead deployment, be sure that: z the web server is configured properly. Z the default gateway of the user’s pc is configured as the ip address of the connected vlan interface on th...
Page 370
29-5 troubleshooting symptom: a user cannot be redirected to the specified url server, no matter what url the user enters in the ie address bar. Solution: z if a user enters an ip address in a format other than the dotted decimal notation, the user may not be redirected. This is related with the ope...
Page 371: Habp Configuration
30-1 30 habp configuration wh n configuring habp, go to the e se sections for information you are interested in: z introduction to habp z habp server configuration z habp client configuration z displaying and maintaining habp configuration intro ice packets from and to that port will be blocked, mak...
Page 372
30-2 to do... Use the command... Remarks configure the current switch to be an habp server habp server vlan vlan-id s you want to use the switch as a management switch, you need to configure the switch to be an habp server. Required by default, a switch operate as an habp client after you enable hab...
Page 373: System Guard Configuration
31-1 31 system guard configuration the cpu protection function is added. See cpu protection and configuring cpu protection . E , go to these sections for information you are interested in: wh n configuring system guard z system guard overview configuring system guard z stem guard configuration z dis...
Page 374
31-2 configuring system guard configuring system guard against ip attacks configuration of system guard against ip attacks includes these tasks: z enabling system guard against ip attacks z setting the maximum number of infected hosts that can be concurrently monitored z configuring parameters relat...
Page 375
31-3 to do... Use the command... Remarks set the threshold of tcn/tc packet receiving rate system-guard tcn rate-threshold rate-threshold optional 1 pps by default as the system monitoring cycle is 10 seconds, the system sends trap and log information if more than 10 tcn/tc packets are received with...
Page 376
31-4 displaying and maintaining system guard configuration to do... Use the command... Remarks display the monitoring result and parameter settings of system guard against ip attacks display system-guard ip state display the information about ip packets received by the cpu display system-guard ip-re...
Page 377: Aaa Overview
32 aaa overview intro onym for the three security functions: authentication, authorization and accounting. It ctions to implement network security z ntication: defines what users can access the network, ess the network, /server model: the client runs on the managed resources side while the server st...
Page 378
Acco t counting methods: introd ain name. E different attributes (such as different forms of username and password, different service types/access rights), it is necessary to distinguish the users sp domain attributes (including aaa policy, radius scheme, and so on) for ndently in isp domain view. I...
Page 379
Z clients: this database stores information about radius clients (such as shared key). S used to interpret the attributes and attribute z dictionary: the information stored in this database i values in the radius protocol. Figure 32-1 databases in a radius server in addition, a radius server can act...
Page 380
Radius client an authentication response (access-accept), which contains the user’s authorization information. If the authentication fails, the server returns an access-reject response. The radius client accepts or denies the user depending on the 5) received authentication result. If it -request, w...
Page 381
Code message type message description 4 accounting-request direction: client->server. The client transmits this message to the server to request the server to start or end the accounting (whether to start or to end the accounting is determined by the acct-status-type attribute in the message). This ...
Page 382
Type field value attribute type type field value attribute type 11 filter-id 33 proxy-state 12 framed-mtu 34 login-lat-service 13 framed-compression 35 login-lat-node 14 login-ip-host 36 login-lat-group 15 login-service 37 framed-appletalk-link 16 login-tcp-port 38 framed-appletalk-network 17 (unass...
Page 383
Table 32-3 differences between hwtacacs and radius hwtacacs radius adopts tcp, providing more reliable network transmission. Adopts udp. Encrypts the entire message except the hwtacacs header. Encrypts only the password field in authentication message. Separates authentication from authorization. Fo...
Page 384
Figure 32-6 aaa implementation procedure for a telnet user the basic message exchange procedure is as follows: 1) a user sends a login request to the switch acting as a tacacs client, which then sends an authentication start request to the tacacs server. 2) the tacacs server returns an authenticatio...
Page 385
9) after receiving the response indicating an authorization success, the tacacs client pushes the configuration interface of the switch to the user. 10) the tacacs client sends an accounting start request to the tacacs server. 11) the tacacs server returns an accounting response, indicating that it ...
Page 386: Aaa Configuration
33-1 33 aaa configuration aaa d preventing unauthorized access and repudiation behavior. Complete the following tasks to configure aaa (configuring a combined a domain): configuration task list you need to configure aaa to provide network access services for legal users while protecting network devi...
Page 387
33-2 task remarks creating an isp domain and configuring its attributes required configuring separate aaa schemes required configuring an aaa scheme for an isp domain required with separate aaa schemes, you can specify authentication, authorization and accounting schemes respectively. You need to co...
Page 391
33-6 accounting. In this case, if the combined scheme uses radius or hwtacacs, the system never uses the secondary scheme for authorization and accounting. Z if you configure no separate scheme, the combined scheme is used for authentication, authorization, and accounting. In this case, if the syste...
Page 392
33-7 z for a vlan id with suffix t or t, the authentication port sends the frames of the vlan tagged. Z for the first vlan id with suffix u or u, or with no suffix in the vlan list, the authentication port sends the frames of the vlan untagged and configures the vlan as its default vlan; for the oth...
Page 395
33-10 z the following characters are not allowed in the user-name string: /:*?. And you cannot input more than one “@” in the string. Z after the local-user password-display-mode cipher-force command is executed, any password will be displayed in cipher mode even though you specify to display a user...
Page 396
33-11 task remarks creating a radius scheme required configuring radius authentication/authorization servers required configuring ignorance of assigned radius authorization attributes optional configuring radius accounting servers required configuring shared keys for radius messages optional configu...
Page 397
33-12 the radius service configuration is performed on a radius scheme basis. In an actual network environment, you can either use a single radius server or two radius servers (primary and secondary servers with the same configuration but different ip addresses) in a radius scheme. After creating a ...
Page 398
33-13 to do… use the command… remarks enter system view — system-view required create a radius scheme and enter its view radius scheme radius-scheme-name by default, a radius scheme named "system" has already been created in the system. Required set the ip address and port number of the primary radi...
Page 399
33-14 n figure 33-1 network diagram for the radius authorization attribute ignoring functio follow these steps to configure the radius authorization attribute ignoring function: to do… use the command… remarks enter system view — system-view required create a radius scheme and enter its view radius ...
Page 400
33-15 to do… use the command… remarks required set the ip address and port number of the primary radius accounting server by default, the ip address and udp port number of the primary accounting server are 0.0.0.0 and 1813 for a newly created radius scheme. Primary accounting ip-address [ port-numbe...
Page 401
33-16 received from each other by using the shared keys that have been set on them, and can accept and respond to the messages only when both parties have the same shared key. Follow these steps to configure shared keys for radius messages: to do… use the command… remarks enter system view — system-...
Page 404
33-19 z generally, the access users are named in the userid@isp-name or userid.Isp-name format. Here, isp-name after the “@” or “.” character represents the isp domain name, by which the device determines which isp domain a user belongs to. However, some old radius servers cannot accept the username...
Page 405
33-20 z if you adopt the local radius server function, the udp port number of the authentication/authorization server must be 1645, the udp port number of the accounting server must be 1646, and the ip addresses of the servers must be set to the addresses of this switch. Z the message encryption key...
Page 406
33-21 to do… use the command… remarks optional set the response timeout time of radius servers timer response-timeout seconds by default, the response timeout time of radius servers is three seconds. Optional set the time that the switch waits before it try to re-communicate with primary server and ...
Page 407
33-22 online when the user re-logs into the network before the cams performs online user detection, and the user cannot get authenticated. In this case, the user can access the network again only when the cams administrator manually removes the user's online information. The user re-authentication a...
Page 408
33-23 hwtacacs configuration task list complete the following tasks to configure hwtacacs: task remarks creating a hwtacacs scheme required configuring tacacs authentication servers required configuring tacacs authorization servers required configuring tacacs accounting servers optional configuring ...
Page 409
33-24 to do… use the command… remarks required set the ip address and port number of the primary tacacs authentication server by default, the ip address of the primary authentication server is 0.0.0.0, and the port number is 0. Primary authentication ip-address [ port ] optional set the ip address a...
Page 410
33-25 z you are not allowed to configure the same ip address for both primary and secondary authorization servers. If you do this, the system will prompt that the configuration fails. Z you can remove a server only when it is not used by any active tcp connection for sending authorization messages. ...
Page 411
33-26 the tacacs client and server adopt md5 algorithm to encrypt hwtacacs messages before they are exchanged between the two parties. The two parties verify the validity of the hwtacacs messages received from each other by using the shared keys that have been set on them, and can accept and respond...
Page 412
33-27 generally, the access users are named in the userid@isp-name or userid.Isp-name format. Where, isp-name after the “@” or “.” character represents the isp domain name. If the tacacs server does not accept the usernames that carry isp domain names, it is necessary to remove domain names from use...
Page 413
33-28 displaying and maintaining aaa configuration displaying and maintaining aaa configuration to do… use the command… remarks display configuration information about one specific or all isp domains display domain [ isp-name ] display information about user connections display connection [ access-t...
Page 414
33-29 displaying and maintaining hwtacacs protocol configuration to do… use the command… remarks display the configuration or statistic information about one specific or all hwtacacs schemes display hwtacacs [ hwtacacs-scheme-name [ statistics ] ] available in any view display buffered non-response ...
Page 415
33-30 s network diagram figure 33-2 remote radius authentication of telnet user configuration procedure # enter system view. System-view # adopt aaa authentication for telnet users. [sysname] user-interface vty 0 4 [sysname-ui-vty0-4] authentication-mode scheme [sysname-ui-vty0-4] quit # configure a...
Page 416
33-31 local authentication of ftp/telnet users the configuration procedure for local authentication of ftp users is similar to that for telnet users. The following text only takes telnet users as example to describe the configuration procedure for local authentication. Network requirements in the ne...
Page 417
33-32 this method is similar to the remote authentication method described in remote radius authentication of telnet/ssh users . However, you need to: z change the server ip address, and the udp port number of the authentication server to 127.0.0.1, and 1645 respectively in the configuration step "c...
Page 418
33-33 # configure the domain name of the hwtacacs scheme to hwtac. [sysname] domain hwtacacs [sysname-isp-hwtacacs] scheme hwtacacs-scheme hwtac auto vlan configuration example network requirements as shown in figure 33-5 , use 802.1x authentication on ethernet 1/0/1 and ethernet 1/0/2 to authentica...
Page 419
33-34 [switch-radius-bbb] quit # create authentication domain aaa, and then enter domain view. [switch] domain aaa # configure the vlan assignment mode in domain aaa as vlan list. [switch-isp-aaa] vlan-assignment-mode vlan-list # specify the authentication scheme for the domain. [switch-isp-aaa] rad...
Page 420
33-35 z the switch cannot communicate with the radius server (you can determine by pinging the radius server from the switch) — take measures to make the switch communicate with the radius server normally. Symptom 2: radius packets cannot be sent to the radius server. Possible reasons and solutions:...
Page 421: Ead Configuration
34-1 34 ead configuration intro enhance of switch, aaa sever, security policy server and security client, ead is able to with z e validity of the session control packets it receives according to the source ip addresses eduling priority for user terminals according to access rights of users dynamical...
Page 422
34-2 thentication environment. Figuration of security policy server ip address. For other related configuration, refer to aaa overview z configuring a radius scheme. Z configuring the ip address of the security policy server. Z associating the isp domain with the radius scheme. Ead is commonly used ...
Page 423
34-3 n network diagram figure 34-2 ead configuratio configuration procedure # configure 802.1x on the switch. Refer to “configuring 802.1x” in 802.1x and system guard configuration. # configure a domain. System-view [sysname] domain system [sysname-isp-system] quit # configure a radius scheme. [sysn...
Page 424
35 mac address authentication configuration wh n configuring mac e address authentication, go to these sections for information you are interested: z mac address authentication overview z related concepts z configuring basic mac address authentication functions z mac address authentication enhanced ...
Page 425
Z password configured (which is the mac-authentication authmode usernameasmacaddress in fixed mode, all users’ mac addresses are automatically mapped to the configured local rnames. O be configured as lan-access. Related concept mac d the on in the process of mac address authentication: counting not...
Page 427
Mac address authentication enhanced function configuration mac a tas omplete the following tasks to configure mac address authentication enhanced function: ddress authentication enhanced function configuration k list c task remarks optional configuring a guest vlan configuring the maximum number of ...
Page 428
After a port is added to a guest vlan, the switch will re-authenticate the first access user of this port (namely, the whose unicast m by the switch) p user passes the re-a cation, this port and thus the user ccess the n first user uthenti ac address is learned will exit the guest vlan, eriodically....
Page 429
Z are con not co ure a guest vlan for this port. Z is confi nly one mac address authentication user can access the port. Even if you set the limit on the number of mac address authentication users to figurati z n ove the vlan ove this vlan, you mus he guest vl vlan module in this manual for the desc...
Page 430
Z if both the limit on the number of mac address auth users configured in the port security function are configured limits is adopted as the maximum nu to access this port. Refer to the port security entication users and the limit on the number of configured for a port, the smaller value of the two ...
Page 431
35-8 # set the user name in mac address mode for mac address authentication, requiring hyphened lowercase mac addresses as the usernames and passwords. [sysname] mac-authentication authmode usernameasmacaddress usernameformat with-hyphen lowercase # add a local user. Z specify the user name and pass...
Page 432: Arp Configuration
36 arp configuration wh n configuring arp e , go to these sections for information you are interested in: z introduction to arp z configuring arp z configuring gratuitous arp displaying and debugging arp z amples z arp configuration ex to arp arp ice must know the data link layer address (mac addres...
Page 433
Figure 36-1 arp message format hardware type (16 bits) protocol type (16 bits) length of hardware address length of protocol address operator (16 bits) hardware address of the sender ip address of the sender hardware address of the receiver ip address of the receiver hardware type (16 bits) hardware...
Page 434
Value description 5 chaos 6 ieee802.X 7 arc network arp table in an ethernet, the mac addresses of two hosts must be available for the two hosts to communicate with each other. Each host in an ethernet maintains an arp table, where the latest used ip address-to-mac address mapping entries are stored...
Page 435
Mode, all hosts on this subnet can receive the request, but only the requested host (namely, host b) will process the request. 3) host b compares its own ip address with the destination ip address in the arp request. If they are the same, host b saves the source ip address and source mac address int...
Page 436
To do… use the command… remarks enable the arp entry checking function (that is, disable the switch from learning arp entries with multicast mac addresses) arp check enable optional enabled by default. Z static arp entries are valid as long as the ethernet switch operates normally. But some operatio...
Page 438
37-1 37 arp attack defense configuration arp rk attacks. Currently, arp attacks and viruses are threatening lan security. The device can provide . Introduction to maximum number of dynamic arp entries a vlan interface can learn vlan interface can learn. If the number of arp entries learned by the vl...
Page 439
37-2 k figure 37-1 network diagram for arp man-in-the-middle attac host a ip_a mac_a host b ip_b mac_b host c ip_ c mac_ c switch invalid arp reply invalid arp reply arp attack detection to guard against the man-in-the-middle attacks launched by hackers or attackers, s4500 series ethernet switches s...
Page 440
37-3 z for details about dhcp snooping and ip static binding, refer to dhcp operation. Z for details about 802.1x authentication, refer to 802.1x and system guard operation. Arp restricted forwarding with the arp restricted forwarding function enabled, arp request packets coming from untrusted port ...
Page 441
37-4 k figure 37-2 gateway spoofing attac to prevent gateway spoofing attacks, an s4500 series ethernet switch can work as an access device (usually with the upstream port connected to the gateway and the downstream ports connected to hosts) and filter arp packets based on the gateway’s address. Z t...
Page 442
37-5 task remarks configuring the maximum number of dynamic arp entries that a vlan interface can learn optional the switch serves as a gateway. Configuring arp source mac address consistency check optional the switch serves as a gateway or an access device. Arp packet filtering based on gateway’s a...
Page 443
37-6 to do… use the command… remarks enter ethernet port view interface interface-type interface-number — configure arp packet filtering based on the gateway’s ip address arp filtersource ip-address required not configured by default. Follow these steps to configure arp packet filtering based on gat...
Page 444
37-7 to do… use the command… remarks specify the current port as a trusted port dhcp-snooping trust optional after dhcp snooping is enabled, you need to configure the upstream port connected to the dhcp server as a trusted port. Configure the port as an arp trusted port arp detection trust optional ...
Page 445
37-8 to do… use the command… remarks enable the arp packet rate limit function arp rate-limit enable required by default, the arp packet rate limit function is disabled on a port. Configure the maximum arp packet rate allowed on the port arp rate-limit rate optional by default, the maximum arp packe...
Page 446
37-9 n network diagram figure 37-3 arp attack detection and packet rate limit configuratio configuration procedure # enable dhcp snooping on switch a. System-view [switcha] dhcp-snooping # specify ethernet 1/0/1 as the dhcp snooping trusted port and the arp trusted port. [switcha] interface ethernet...
Page 447
37-10 arp attack defense configuration example ii network requirements as shown in figure 37-4 , host a and host b are connected to gateway through an access switch (switch). The ip and mac addresses of gateway are 192.168.100.1/24 and 000d-88f8-528c. To prevent gateway spoofing attacks from host a ...
Page 448
37-11 arp attack defense configuration example iii network requirements as shown in figure 37-5 , host a and host b are connected to gateway (switch a) through a layer 2 switch (switch b). To prevent arp attacks such as arp flooding: z enable arp packet source mac address consistency check on switch...
Page 449
37-12 e z enable arp attack detection based on bindings of authenticated 802.1x clients on the switch to prevent arp attacks. Network diagram figure 37-6 network diagram for 802.1x based arp attack defens configuration procedures # enter system view. System-view # enable 802.1x authentication global...
Page 450: Dhcp Overview
38 dhcp overview wh n configuring dhcp, go to these e sections for information you are interested in: z introduction to dhcp z dhcp ip address assignment dhcp packet format z z protocol specification intro nd the s to dhcp servers for plement dynamic allocation of network resources. Ne dhcp server a...
Page 451
Z automatic assignment. The dhcp server assigns ip addresses to dhcp clients. The ip addresses will be occupied by the dhcp clients permanently. Dynamic assignment. The dhcp server assign z s ip addresses to dhcp clients for predetermined period of time. In this case, a dhcp client must apply for an...
Page 452
By default, a dhcp client updates its ip address lease automatically by unicasting a dhcp-request packet to the dhcp server when half of the lease time elapses. The dhcp server responds with a ails to update its ip address lease when half of the lease time elapses, it will update asting a dhcp-reque...
Page 453
Z file: path and name of the boot configuration file that the dhcp server specifies for the dhcp client. Packet type, valid lease time, ip address of a dns prot protocol sp rfc2131: dynamic host configuration protocol z rfc2132: dhcp options and bootp vendor extensions z rfc1542: clarifications and ...
Page 454: Dhcp Server Configuration
39-1 39 dhcp server configuration wh n configuring the dhcp server, go to th e ese sections for information you are interested in: cp server z introduction to dh z dhcp server configuration task list z enabling dhcp z configuring the global address pool based dhcp server sed dhcp server z configurin...
Page 455
39-2 t z z p address, you can create an interface-based address pool for the interface by executing the dhcp select interface command in interface view. Ace address pool holds belong to the network segment the interface s tions in turn can be inherited by their client address. So, for the name), 2) ...
Page 456
39-3 z interface will be selected. Est will be selected. Z if no assignable ip address is available in the selected address pool, the dhcp server will not lient because it cannot assign an ip address from the parent address dhcp ss pools or global address pools to dhcp clients or client ids. 3) 4) a...
Page 457
39-4 z when you merge two or more xrn systems into one xrn system, a new master unit is elected, and the new xrn system adopts new configurations accordingly. This may result in the existing system configurations (including the address pools configured for the dhcp servers) being lost. As the new xr...
Page 458
39-5 to improve security and avoid malicious attacks to unused sockets, s4500 ethernet switches provide the following functions: z udp port 67 and udp port 68 ports used by dhcp are enabled only when dhcp is enabled. Z udp port 67 and udp port 68 ports are disabled when dhcp is disabled. The corresp...
Page 459
39-6 to do… use the command… remarks enter system view system-view — interface interface-type interface-number dhcp select global configure the current interface quit configure the specified interface(s) or all the interfaces to operate in global address pool mode configure multiple interfaces simul...
Page 460
39-7 currently, only one ip address in a global dhcp address pool can be statically bound to a mac address or a client id. Follow these steps to configure the static ip address allocation mode: to do… use the command… remarks enter system view system-view — enter dhcp address pool view dhcp server i...
Page 461
39-8 to improve security and avoid malicious attack to the unused sockets, s4500 ethernet switches provide the following functions: z udp 67 and udp 68 ports used by dhcp are enabled only when dhcp is enabled. Z udp 67 and udp 68 ports are disabled when dhcp is disabled. The corresponding implementa...
Page 462
39-9 z in the same dhcp global address pool, the network command can be executed repeatedly. In this case, the new configuration overwrites the previous one. Z the dhcp server forbidden-ip command can be executed repeatedly. That is, you can configure multiple ip addresses that are not dynamically a...
Page 463
39-10 configuring wins servers for the dhcp client for microsoft windows-based dhcp clients that communicate through netbios protocol, the host name-to-ip address translation is carried out by windows internet naming service (wins) servers. So you need to perform wins-related configuration for most ...
Page 464
39-11 configuring gateways for the dhcp client gateways are necessary for dhcp clients to access servers/hosts outside the current network segment. After you configure gateway addresses on a dhcp server, the dhcp server provides the gateway addresses to dhcp clients as well while assigning ip addres...
Page 465
39-12 meanings of the sub-options for option 184 table 39-1 meanings of the sub-options for option 184 sub-option feature function note ncp-ip (sub-option 1) the ncp-ip sub-option carries the ip address of the network call processor (ncp). The ip address of the ncp server carried by sub-option 1 of ...
Page 466
39-13 mechanism of using option 184 on dhcp server the dhcp server encapsulates the information for option 184 to carry in the response packets sent to the dhcp clients. Supposing that the dhcp clients are on the same segment as the dhcp server, the mechanism of option 184 on the dhcp server is as f...
Page 467
39-14 configuring the tftp server and bootfile name for the dhcp client this task is to specify the ip address and name of a tftp server and the bootfile name in the dhcp global address pool. The dhcp clients use these parameters to contact the tftp server, requesting the configuration file used for...
Page 469
39-16 task remarks enabling the interface address pool mode on interface(s) required configuring the static ip address allocation mode configuring an address allocation mode for an interface address pool configuring the dynamic ip address allocation mode one of the two options is required. And these...
Page 470
39-17 to improve security and avoid malicious attack to the unused sockets, s4500 ethernet switches provide the following functions: z udp port 67 and udp port 68 ports used by dhcp are enabled only when dhcp is enabled. Z udp port 67 and udp port 68 ports are disabled when dhcp is disabled. The cor...
Page 471
39-18 z the ip addresses statically bound in interface address pools and the interface ip addresses must be in the same network segment. Z there is no limit to the number of ip addresses statically bound in an interface address pool, but the ip addresses statically bound in interface address pools a...
Page 472
39-19 z the dhcp server forbidden-ip command can be executed repeatedly. That is, you can configure multiple ip addresses that are not dynamically assigned to dhcp clients. Z use the dhcp server forbidden-ip command to configure the ip addresses that are not assigned dynamically in global address po...
Page 473
39-20 to do… use the command… remarks enter system view system-view — interface interface-type interface-number dhcp server dns-list ip-address& configure the current interface quit configure dns server addresses for dhcp clients configure multiple interfaces in system view dhcp server dns-list ip-a...
Page 475
39-22 follow these steps to configure option 184 parameters for the client with voice service: to do… use the command… remarks enter system view system-view — enter interface view interface interface-type interface-number — specify the primary network calling processor dhcp server voice-config ncp-i...
Page 476
39-23 follow these steps to configure the tftp server and bootfile name for the dhcp client: to do… use the command… remarks enter system view system-view — enter interface view interface interface-type interface-number — specify the tftp server dhcp server tftp-server ip-address ip-address specify ...
Page 477
39-24 be cautious when configuring self-defined dhcp options because such configuration may affect the dhcp operation process. Configuring dhcp server security functions dhcp security configuration is needed to ensure the security of dhcp service. Prerequisites before configuring dhcp security, you ...
Page 478
39-25 server will assign the ip address to the requesting client (the dhcp client probes the ip address by sending gratuitous arp packets). Follow these steps to configure ip address detecting: to do… use the command… remarks enter system view system-view — specify the number of ping packets dhcp se...
Page 479
39-26 dhcp accounting configuration prerequisites before configuring dhcp accounting, make sure that: z the dhcp server is configured and operates properly. Address pools and lease time are configured. Z dhcp clients are configured and dhcp service is enabled. Z the network operates properly. Config...
Page 481
39-28 z in the address pool 10.1.1.0/25, the address lease duration is ten days and twelve hours, domain name suffix aabbcc.Com, dns server address 10.1.1.2, gateway 10.1.1.126, and wins server 10.1.1.4. Z in the address pool 10.1.1.128/25, the address lease duration is five days, domain name suffix...
Page 482
39-29 # configure the ip addresses that are not dynamically assigned. (that is, the ip addresses of the dns server, wins server, and gateways.) [switcha] dhcp server forbidden-ip 10.1.1.2 [switcha] dhcp server forbidden-ip 10.1.1.4 [switcha] dhcp server forbidden-ip 10.1.1.126 [switcha] dhcp server ...
Page 483
39-30 n network diagram figure 39-2 network diagram for option 184 support configuratio configuration procedure 1) configure the dhcp client. Configure the 3com vcx device to operate as a dhcp client and to request for all sub-options of option 184. (configuration process omitted) 2) configure the d...
Page 484
39-31 n z ethernet 1/0/1 belongs to vlan 2; ethernet 1/0/2 belongs to vlan 3. Z the ip address of vlan-interface 1 is 10.1.1.1/24, and that of vlan-interface 2 is 10.1.2.1/24. Z the ip address of the radius server is 10.1.2.2/24. Z dhcp accounting is enabled on the dhcp server. Z the ip addresses of...
Page 485
39-32 [sysname-radius-123] primary accounting 10.1.2.2 [sysname] domain 123 [sysname-isp-123] scheme radius-scheme 123 [sysname-isp-123] quit # create an address pool on the dhcp server. [sysname] dhcp server ip-pool test [sysname-dhcp-pool-test] network 10.1.1.0 mask 255.255.255.0 # enable dhcp acc...
Page 486
40-1 40 dhcp relay agent configuration wh n configuring the dhcp relay agent, go to these se e ctions for information you are interested in: z introduction to dhcp relay agent z configuring the dhcp relay agent z displaying and maintaining dhcp relay agent configuration dhcp relay agent configuratio...
Page 487
40-2 figure 40-1 typical dhcp relay agent application address assignment through the dhcp relay agent, the dhcp client and in the process of dynamic ip dhcp server interoperate with each other in a similar way as they do without the dhcp relay agent. The following sections only describe the forwardi...
Page 488
40-3 figure 40-2 padding contents for sub-option 1 of option 82 figure 40-3 padding contents for sub-option 2 of option 82 anism of option 82 supported on dhcp relay agent ced mech the pro ure for a dhcp client to obtain an ip address from a dhcp server through a dhcp relay gent is similar to that f...
Page 489
40-4 the client to uniquely identify an address allocation process) in the message, and then forward the message to the dhcp server. Fter receiving the message, the dhcp server returns a dhcp-ack message to the client: ack message is unicast, the dhcp relay agent directly forwards the message to the...
Page 490
40-5 follow these nable dhcp: steps to e to do… use the command… remarks enter system view system-view — enable dhcp dhcp enable y default. Required enabled b correlating a dhcp server group with a relay agent interface ce reliability, you can set multiple dhcp servers on the same network. These dhc...
Page 491
40-6 z you can configure up to eight dhcp server ip addresses in a dhcp server group. You can map multiple vlan interfaces to one dhcp server group. But one vlan interface can be z if you execute the dhcp-se d repeatedly, the ne tion overwrites . Z you need to configure the group number specified in...
Page 492
40-7 z ck en dent of the dhcp relay ddress check takes effect when this command is executed, regardless a o e p) are used. Z d ble command configure the static binding of the ip addre server. Otherwise, the dhcp client will fail to obtain an ip address. The address-che able command is indepen of oth...
Page 493
40-8 e ip address, the age with the siaddr field (ip addresses of the hcp relay agent will record the value of the siaddr field and the receiving interface. The administrator can use this information to check out an nauthorized serv f enable unau server detection: nabling unauthorized dhcp server de...
Page 494
40-9 z by default, with the option 82 support function e the dhcp relay t containing option 82. Gies are configured before, then enabling the 82 support on the dhcp red z 82, you need to perfor nfiguration o dhcp server and the dhcp relay agent. Nabled on the dhcp relay agent, agent will adopt the r...
Page 495
40-10 dhcp relay agent configuration example ork requirements vlan-i side. The ip 10.1.1.2/24 th a forward addresses in subnet 10.10.1.0/24 t network diagram netw nterface 1 on the dhcp relay agent (switch a) connects to the network where dhcp clients re address of vlan-interface 1 is 10.10.1.1/24 a...
Page 496
40-11 analysis configuration. When a dhcp relay agent debugging and checking the information about debugging and interface state (you can display the information by executing the corresponding s t p relay agent. E network segment with the dhcp clients is configured on the dhcp server. Figured betwee...
Page 497: Dhcp Snooping Configuration
41-1 41 dhcp snooping configuration when configuring dhcp snooping, go to these sections for information you are interested in: z dhcp snooping overview z configuring dhcp snooping z displaying and maintaining dhcp snooping configuration z dhcp snooping configuration examples p snooping overview dhc...
Page 498
41-2 ing application figure 41-1 typical network diagram for dhcp snoop dhcp client dhcp client switch a (dhcp snooping) internet eth1/0/2 eth1/0/1 switch b (dhcp relay) dhcp client dhcp client dhcp server z dhcp-request packet introduction to dhcp-snooping option 82 introduction to option 82 for de...
Page 499
41-3 figure 41-3 extended format of the remote id sub-option rnet switches support option 82 in the standard format. Refer to figure 41-4 in practice, some network devices do not support the type and length identifiers of the circuit id and remote id sub-options. To interwork with these devices, s45...
Page 500
41-4 when receiving a dhcp client’s request without option 82, the dhcp snooping device will add the option field with the configured sub-option and then forward the packet. For details, see table 41-2 . Table 41-2 ways of handling a dhcp packet without option 82 sub-option configuration the dhcp-sn...
Page 501
41-5 be recorded in the dhcp-snooping table. Consequently, this client cannot pass the ip dhcp-snooping table, thus it cannot access external networks. To s bind , and the port connecting to the client, so that pack ip-to- if m clien to e auth ith the authenticated 802.1x client-based ip filtering f...
Page 502
41-6 z if an s4 net switch is ena ing, the clients c o it cannot z ify the ports c valid dhcp serve trusted to ensure that dhcp add p ted to the dhcp client z ooping on an s45 ch that belongs to an ic, do not configure the e dhcp r to belo o different units of the fabric; otherwise, the switch canno...
Page 503
41-7 configuring a handling policy for dhcp packets with option 82 f gure a h acket ith option 82: ollow these steps to confi andling policy for dhcp p s w to do… use the command… remarks enter system view system-view — configure a global handl policy for requests that co ing ntain option 82 replace...
Page 504
41-8 to do… use the command… remarks enter ethernet port view interface interface-type — interface-number co u circuit id nfigure the circuit id dhcp-snooping optional by default, the s b-option in option 82 information [ vlan vlan-id] circuit-id string string sub-option contains the vlan id and por...
Page 505
41-9 z if you configure a remote id sub-option in both system view and on a port, the remote id l remote z h the vlan vlan-id argument specified, and the other one z the primary and member ports z sub-option configured on the port applies when the port receives a packet, and the globa id applies to ...
Page 506
41-10 z for details about 802.1x authentication, refer to 802.1x and system guard operation. Ended to configure ip filtering on the ports of an aggregation group. Ings. If an acl fails to be assigned to a binding, the , the ip addresses of 802.1x clients cannot be obtained. To ensure ip ts can be up...
Page 507
41-11 dhc configuration example p snooping configuration examples dhcp-snooping option 82 support network requirements as shown in figure 41-6 , ethernet 1/0/5 of the switch is connected to the dhcp server, and ethernet 1/0/1, ethernet 1/0/2, and ethernet 1/0/3 are respectively connected to client a...
Page 508
41-12 nooping information vlan 1 circuit-id string abcd ip fil n [switch-ethernet1/0/3] dhcp-s tering configuration example etwork requirements as shown in figure 41-7 , ethernet 1/0/1 of the s4500 switch is connected to the dhcp server and ost a. The ip address and mac address of host a are 1.1.1.1...
Page 509
41-13 [switch-ethernet1/0/2] quit [switch-ethernet1/0/3] quit [switch-ethernet1/0/2] ip source static binding ip-address 1.1.1.1 mac-address [switch] interface ethernet 1/0/3 [switch-ethernet1/0/3] ip check source ip-address mac-address [switch] interface ethernet 1/0/4 [switch-ethernet1/0/4] ip che...
Page 510
42-1 42 dhcp packet rate limit configuration whe uring the dhcp packet rate limit function, go to t sections for information you are terested in: tion to dhcp packet rate limit n config hese in z introduc ring dhcp packet rate limit z configu z rate limit configuration example intro u to prevent arp...
Page 511
42-2 to do… use the command… remarks enter port view interface interface-type — interface-number enable the dhcp packet rate limit function dhcp rate-limit enable required by default, dhcp packet rate limit is disabled. Configure the maximum dhcp packet rate allowed on the port dhcp rate-limit rate ...
Page 512
42-3 networking diagram n figure 42-1 network diagram for dhcp packet rate limit configuratio c e switch. # specify ethernet 1/0/1 as the trusted port. [switch-ethernet1/0/1] dhcp-snooping trust [sysname-ethernet1/0/11] dhcp rate-limit enable s. Sysname-ethernet1/0/11] dhcp rate-limit 100 onfigurati...
Page 513
43-1 43 dhcp/bootp client configuration w oot these sections for i z introduction to dhcp client hen configuring the dhcp/b p client, go to nformation you are interested in: introduction to bootp client z uring a dhcp/bootp client z config dhcp/bootp client configuration z displaying intro u afte ev...
Page 514
43-2 configuring a dhcp/bootp client nfigure a dhcp/bootp client: follow these steps to co to do… use the command… remarks enter system view system-view — enter vlan interface view interface vlan-interface — vlan-id configure the vlan interface to obtain ip address through ip address { bootp-alloc d...
Page 515
43-3 dhcp client configuration example network requirements using dhcp, vlan-interface 1 of switch b is connected to the lan to obtain an ip address from the dhcp server. Network diagram see xu figure 39-1 ux . Configuration procedure the following describes only the configuration on switch b servin...
Page 516: Acl Configuration
44 acl configuration wh n configuring acl, go to these e sections for information you are interested in: z acl overview z acl configuration task list z displaying and maintaining acl configuration examples for upper-layer software referencing acls z s to hardware z examples for applying acl acl ng a...
Page 517
Z auto: where rules in an acl are matched in the order determined by the system, namely the for d h 1) range of source ip address: the smaller the source ip address range (that is, the more the riority. Depth 1) d by ip is prior to others. The wildcard mask), the higher the match priority. (that is,...
Page 518
Wh n applying an acl in this way, y e ou can specify the order in which the rules in the acl are matched. , unless you delete all the rules in the acl and efine the match order. E referenced by upper-layer software: ced by routing policies z used to control telnet, snmp and web login users the match...
Page 519
Conf r ime ranges can be used to filter packets. You can specify a time range for each rule in an acl. A time acl takes effect only in specified time ranges. Only after a time range is configured and the system time is within the time range, can an acl rule take effect. Iodic time range, which recur...
Page 520
C iday. E range spans from 15:00 1/28/2006 to 15:00 1/28/2008. System-view /28/2008 fro configuring basic acl addresses. A basic acl can be numbered from 2000 to 2999. Configuration prerequisites z s ed to cre responding time range fer to config onfiguration example # define a periodic time range th...
Page 521
Z with the config match order specified for the basic acl, you can modify any existent rule. The unmodified part of the rule remains. With the auto match order specified for the basic acl, you rule; otherwise the system will tell you that the rule cannot be modified. The rule-id argument when creati...
Page 523
Configuring la l l ckets accord er 2 information, su as the source and destination m a bered from 4000 to 4999. Configuration prerequisites z to configure a time range-based layer 2 acl rule, you need to create the co g time about time range configuration, refe ng time range yer 2 ac ayer 2 acls fil...
Page 524
[sysname-acl-ethernetframe-4000] display acl 4000 rule 0 d xcellent-effort source 000d-88f5-97ed ffff-ffff-ffff dest 0011-4301-991e f config a a user-defined acl filters packets by comparing specific bytes in packet headers with specified string. A user-defined acl can be n configuration prerequisit...
Page 525
Z if you do not specify the rule-id argument when creating an acl rule, the rule will be numbered le is numbered 0; otherwise, the number of the rule will s one. If the current greatest rule number is 65534, however, the you that the rule cannot be created and you need to specify a number for the ru...
Page 526
Whe le, you need to specify the ip-protocol combination as tcp or udp, that is, 0x06 or 0x11. To specify the 6-code keyword for a rule, you need to specify the ip-protocol rule-string 0x3a. Z the total length of the fields in a rul more than 32 byt , the rule example, if you define the src-ip and de...
Page 527
Z you can mo time ra dify any existent rule of an ipv6 acl. If you modify only the action to be taken or the he unmodified part of the rule remains the same. If you modify the contents of a user-defined string, the new string overwrites the original one. N acl rule, the rule will be numbered automat...
Page 530
Example for controlling web login users by source ip n s with the source ip address of 10.110.100.46 to log in to the switch n etwork requirement apply an acl to permit web users through http. Etwork diagram figure 44-2 network diagram for controlling web login users by source ip internet switch pc ...
Page 531
Configuration procedure # define a periodic time range that is active from 8:00 to 18:00 everyday. 2000 a switch. The ip address of the wage thernet 1/0/1 of the switch. Apply an he wage server during the working ours (8:00 to 18:00). System-view [sysname] time-range test 8:00 to 18:00 daily # defin...
Page 532
Lay ration example n 1/0/1. Pc 1’s mac address is 0011-0011-0011. Ss of 0011-0011-0011 and the destination . Er 2 acl configu etwork requirements pc 1 and pc 2 connect to the switch through ethernet apply an acl to filter packets with the source mac addre mac address of 0011-0011-0012 from 8:00 to 1...
Page 533
Network diagram figure 44-6 network diagram for user-defined acl c ctive from 8:00 to 18:00 everyday. Acket whose source ip address is 192.168.0.1 from 8:00 to 18:00 everyday (provided that vlan-vpn is not enabled on any port). In the acl rule, 0806 is the arp mask of the rule, 16 is the protocol ty...
Page 534
System-view [sysname] time-range test 8:00 to 18:00 daily d configure a rule for the acl, denying packets from 3001::1/64 to 3002::1/64. Port ethernet 1/0/1. Ct to the switch through ethernet 1/0/1, ethernet of the database server is 192.168.1.2. Apply an abase server from 8:00 to 18:00 in working d...
Page 535: Qos Configuration
45 qos configuration wh n configuring qos, go to these sections e for information you are interested in: z overview z qos supported by switch 4500 series z qos configuration displaying and maintaining qos z configuration examples z qos introd pt concerning service demand and supply. It reflects the ...
Page 536
All these new applications have one thing in common, that is, they have special requirements for bandwidth, delay, and jitter. For instance, bandwidth, delay, and jitter are critical for videoconference their destinations, better network services are demanded, such as allocating dedicated bandwidth,...
Page 537
Qos th series suppo tures listed in table 45-1 supported by switch 4500 series e switch 4500 rt the qos fea : table 45-1 qos fea 00 series tures supported by switch 45 qos feature description refer to … traffic classification traffic based 4500 ollowing acls z efer to the acl operation and acl comma...
Page 538
Protocol or the port number of an application. Normally, traffic classification is done by checking the information carried in packet header. Packet payload is rarely adopted for traffic classification. The identifying rule is unlimited in range. It can be a quintuplet consisting of source address, ...
Page 539
Z assured forwarding (af) class: this class is further divided into four subclasses (af1/2/3/4) and a z ass: this class comes from the ip tos field and includes eight subclasses; without any assurance in the cs class. The af s the limit. Current ip network traffic belongs to t table 45-3 description...
Page 540
2) 802.1p priority 802.1p priority lies in layer 2 packet headers and is applicable to occasions where the layer 3 packet header does not need analysis but qos must be assured at layer 2. Figure 45-3 an ethernet frame with an 802.1q tag header length/type data 6 bytes 6 bytes 4 bytes 2 bytes 46 to 1...
Page 541
P o 802.1q tag 2) acket ure the port to trust port priority. By default, port priority is trusted and the priority of a port in this mode, the switch replaces the 802.1p priority of the received packet with the port priority, rt priority of the receiving port in the 802.1p-to-local pr ng table, and ...
Page 542
Priority marking local precedence. Traf rs. For example, traffic can be limited to get o avoid network congestion caused by excessive to limit the traffic and the resource occupied by emented according to the evaluation result on the cification when traffic policing is performed. Th a certain capaci...
Page 543
Enough to forward the packets, the traffic is conforming to the specification; otherwise, the traffic is nonconforming or excess. Parameters concerning token bucket include: een used and the traffic is excess. T i the affic into the network and limit it to a e range, or to "discipline" the extra tra...
Page 544
The switch 4500 series support three queue scheduling algorithms: strict priority (sp) queuing, weighted fair queuing (wfq), and weighted round robin (wrr) queuing. 1) sp queuing figure 45-6 diagram for sp queuing sp queue-scheduling algorithm is specially designed for critical service applications....
Page 545
Figure 45-7 diagram for wfq queuing before wfq is introduced, you must understand fair queuing (fq) first. Fq is designed for the purpose of sharing network resources fairly and optimizing the delays and delay jitters of all the flows. It takes the interests of all parties into account, such as: ule...
Page 546
Figure 45-8 diagram for wrr queuing ch port. Wrr configures a weight value for ueue, for example: w7, w6, w5, w4, w3, w2, w1, and w0 respectively for queue 7 through queue 0. A weight value indicates the proportion of resources available for a queue. On a 100-mbps port, mbps × 1/(5+5+3+3+1+1+1+1)) b...
Page 547
I er limit a ch queue, and the packets in a queue a z aller than imit, no packet is dropped; z th exceeds the upper limit wly received packets are dropped; z en the lower limit the newly received packets er the queue, the ceived packets may be a maximum drop probability i are generated to dete packe...
Page 548
Configuration procedure follow these steps to configure to trust port priority: to do… use the command… remarks enter system view system-view — enter ethernet port view f interfa inter ace interface-type ce-number — configure to trust port priority iority priority priority-level optional by default,...
Page 549
C between 802.1p priority and local precedence: onfiguration procedure follow these steps to configure the mapping remarks to do… use the command… enter system view system-view — configure the mapping between 802.1p priority and cos0-map-loca cos2-map-loca lo al precedence l-prec cos3-map-local-prec...
Page 550
C z [sysname] protocol-priority protocol-type icmp ip-precedence 3 ol-priority ip-precedence: flash(3) marking packet priority r rking onfiguration example z set the ip precedence of icmp packets to 3. Display the configuration. Configuration procedure: system-view [sysname] display protoc protocol:...
Page 552
Configure traffic traffic-limit inbound acl-rule [ union-effect ] target-rate policing [ bur [ exc st-bucket burst-bucket-size ] eed action ] required specify a committed information rate (cir) for the target-rate argument, and specify a committed bust size (cbs) for the burst-bucket-size argument. ...
Page 555
Z y using the queue-scheduler command in system hm configured in port view must be ured in system view. Otherwise, the system prompts configuration errors. Z dth value) specified in system view for a queue of wrr queuing or wfq t of a port, you can modify the weight (or bandwidth value) for this por...
Page 556
To do… use the command… remarks enter system view system-view — enter ethernet port view interface interface interface-type -number — configure wred wred queue-index qstart probabilit require by default, wred is not configured. D y co c d for queu net ackets in queu number of packets in queue 2 exce...
Page 557
F ring-group the monitor-port command, refer to the part talking about mirroring. Or information about the mirro monitor-port command and co network requirements: z ethernet 1/0/1 is connected to the 10.1 z rk se ror net 1/0/4. C system-view [ [sysname-acl-basic-2000] rule permit source 10.1.1.0 0.0...
Page 558
Qos through an ethernet switch. Pc 1, with the ip and is connected to ethernet 1/0/1 of the switch. To ethernet 1/0/2 of the switch. G requirements: set the maximum rate of outbound packets sourced from the marketing department to 64 kbps. Drop the packets exceeding the rate limit. Of outbound ip pa...
Page 559
Configuration example of priority marking and queue scheduling network requirements as shown in figure 45-10 , an enterprise network connects all the switch. Clients pc 1 through pc 3 are connected to pc 6 are connected to ethernet 1/0/3 of the switch. Server 1 (the d server), and server 3 (the file...
Page 560
[sysname-ethernet1/0/2] traffic-priority inbound ip-group 3000 rule 1 local-precedence 3 [sysname-ethernet1/0/2] traffic-priority inbound ip-group 3000 rule 2 local-precedence 2 ] quit vlan ma netw the e hosts on the two customer networks to r terminal devices in vlan 100 and vlan 200 through 1/0/12...
Page 561
Configuration procedure d vlan 200 and service vlans vlan 500 and vlan 600 on d configure its default vlan as vlan 100. Et 1/0/12 in the same way. 0/11 runk pvid vlan 200 itch a as a trunk port, and assign it to vlan 100, vlan 200, vlan t1/0/10] port link-type trunk rt trunk permit vlan 100 200 500 ...
Page 562
# configure vlan mapping on ethernet 1/0/11 to replace vlan tag 100 with vlan tag 500. [switcha] interface ethernet 1/0/11 rk-vlanid inbound link-group 4000 remark-vlan 500 # configure vlan mapping on ethernet 1/0/10 to replace vlan tag 500 with vlan tag 100 and replace vlan tag 600 with vlan tag 20...
Page 563: Mirroring Configuration
46 mirroring configuration wh n configuring mirroring, g e o to these sections for information you are interested in: z mirroring overview z mirroring configuration displaying and maintaining port mirroring z n examples z mirroring configuratio mirr plicated is called the source mirroring port or mo...
Page 564
Remote port mirroring remote port mirroring does not require the source and destination ports to be on the same device. The source and destination ports can be located on multiple devices across the network. This allows an administrator to monitor traffic on remote devices conveniently. To implement...
Page 565
Intermediate switch trunk port sends mirrored packets to the destination switch. Two trunk ports are necessary for the intermediate switch to connect the devices at the source switch side and the destination switch side. Trunk port receives remote mirrored packets. Destination switch destination por...
Page 566
Mirroring configuration complete the following tasks to configure mirroring: task remarks configuring local port mirroring optional configuring remote port mirroring optional on a switch 4500, only one destination port for local port mirroring and only one reflector port can be configured, and the t...
Page 567
To do… use the command… remarks interface interface-type interface-number port for the port mirroring group in port view mirroring-group group-id monitor-port views have the same effect. When configuring local port mirroring, note that: z you need to configure the source and destination ports for th...
Page 568
To do… use the command… remarks enter system view system-view — create a vlan and enter the vlan view vlan vlan-id vlan-id is the id of the remote-probe vlan. Configure the current vlan as the remote-probe vlan remote-probe vlan enable required return to system view quit — enable port mirroring – st...
Page 569
Z do not configure a port connecting the intermediate switch or destination switch as the mirroring source port. Otherwise, traffic disorder may occur in the network. Z with port mirroring – stp collaboration enabled, if you configure a port in discarding state as a mirroring port, the port mirrorin...
Page 570
Z the destination port and the remote-probe vlan are determined. Z layer 2 connectivity is ensured between the source and destination switches over the remote-probe vlan. 2) configuration procedure follow these steps to configure remote port mirroring on the destination switch: to do… use the comman...
Page 572
[sysname] mirroring-group 1 mirroring-port ethernet 1/0/1 ethernet 1/0/2 both [sysname] mirroring-group 1 monitor-port ethernet 1/0/3 # display configuration information about local mirroring group 1. [sysname] display mirroring-group 1 mirroring-group 1: type: local status: active mirroring port: e...
Page 573
Network diagram figure 46-4 network diagram for remote port mirroring configuration procedure 1) configure the source switch (switch a) # create remote source mirroring group 1. System-view [sysname] mirroring-group 1 remote-source # configure vlan 10 as the remote-probe vlan. [sysname] vlan 10 [sys...
Page 574
# configure vlan 10 as the remote-probe vlan. System-view [sysname] vlan 10 [sysname-vlan10] remote-probe vlan enable [sysname-vlan10] quit # configure ethernet 1/0/1 as the trunk port, allowing packets of vlan 10 to pass. [sysname] interface ethernet 1/0/1 [sysname-ethernet1/0/1] port link-type tru...
Page 575: Xrn Fabric Configuration
47 xrn fabric configuration wh n configuring xrn fabric, g e o to these sections for information you are interested in: z introduction to xrn z xrn fabric configuration displaying and maintaining xrn fabric z tion example z xrn fabric configura intro f a network. This feature allows you to build an ...
Page 576
Figure 47-1 xrn networking establishment of an xrn fabric topology and connections of an xrn fabric an xrn fabric typically has a daisy chain topology structure. As shown in figure 47-2 , each switch has two ports connected with two other switches in the fabric, but the switches at both ends of the ...
Page 577
Figure 47-3 port connection mode for switch 4500 series daisy chain topology xrn fabric mode green=speed yellow=duplex rps pwr console unit 1000 base - x 1 speed:green=100mbps ,yellow=10mbps 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 duplx:green=full duplx ,yellow=half ...
Page 578
Z the number of the existing devices in the fabric does not reach the maximum number of devices allowed by the fabric (up to eight devices can form a fabric). Z the fabric name of the device and the existing devices in the fabric are the same. Z the software version of the device is the same as that...
Page 579
Status analysis solution auth failure the xrn fabric authentication modes configured for the local device and that of the fabric are not the same, or the password configured does not match. Configure the xrn fabric authentication modes and the passwords for the local device and the fabric as the sam...
Page 580
Task remarks specifying the vlan used to form an xrn fabric optional setting a unit id for a switch optional assigning a unit name to a switch optional assigning an xrn fabric name to a switch optional setting the xrn fabric authentication mode optional specifying the fabric port of a switch you can...
Page 581
Z establishing an xrn system requires a high consistency of the configuration of each device. Hence, before you enable the fabric port, do not perform any configuration for the port, and do not configure some functions that affect the xrn for other ports or globally. Otherwise, you cannot enable the...
Page 582
Setting a unit id for a switch ftm will automatically number the switches to constitute an xrn fabric by default, so that each switch has a unique unit id in the fabric. You can use the command in the following table to set unit ids for switches. Make sure to set different unit ids for different swi...
Page 583
Z if auto-numbering is selected, the system sets the unit priority to 10. You can use the fabric save-unit-id command to save the modified unit id into the unit flash memory and clear the information about the existing one. Priority is the reference for ftm program to perform automatic numbering. Th...
Page 585
Network diagram figure 47-4 network diagram for forming an xrn fabric xrn fabric ge1/0/25 ge1/0/26 ge1/0/25 ge1/0/26 ge1/0/25 ge1/0/26 switch a(unit 1) switch b(unit 2) switch c(unit 3) switch d(unit 4) configuration procedure 1) configure switch a. # configure fabric ports. System-view [sysname] fa...
Page 586
# configure the unit name as unit 3. [sysname] set unit 1 name unit3 # configure the fabric name as hello. [sysname] sysname hello # configure the fabric authentication mode as simple and the password as welcome. [hello] xrn-fabric authentication-mode simple welcome 4) configure switch d. # configur...
Page 587: Cluster Configuration
48 cluster configuration wh n configuring cluster, go to these e sections for information you are interested in: z cluster overview z cluster configuration task list z displaying and maintaining cluster configuration cluster configuration examples z the cluster synchronization function is added. For...
Page 588
Figure 48-1 a cluster implementation hgmp v2 has the following advantages: z it eases the configuration and management of multiple switches: you just need to configure a public ip address for the management device instead of for all the devices in the cluster; and then you can configure and manage a...
Page 589
Table 48-1 description on cluster roles role configuration function management device configured with a external ip address z provides an interface for managing all the switches in a cluster z manages member devices through command redirection, that is, it forwards the commands intended for specific...
Page 590
Z a candidate device becomes a member device after being added to a cluster. Z a member device becomes a candidate device after it is removed from the cluster. Z a management device becomes a candidate device only after the cluster is removed. After you create a cluster on a switch 4500 switch, the ...
Page 591
Packet data. The receiving devices store the information carried in the ndp packet into the ndp table but do not forward the ndp packet. When they receive another ndp packet, if the information carried in the packet is different from the stored one, the corresponding entry in the ndp table is update...
Page 592
Z to implement ntdp, you need to enable ntdp both globally and on specific ports on the management device, and configure ntdp parameters. Z on member/candidate devices, you only need to enable ntdp globally and on specific ports. Z member and candidate devices adopt the ntdp settings of the manageme...
Page 593
Figure 48-3 state machine of the connection between the management device and a member device receives the handshake or management packets fails to receive handshake packets in three consecutive intervals state holdtime exceeds the specified value disconnect state is recovered active connect disconn...
Page 594
Z enabling the management packets (including ndp packets, ntdp packets, and handshake packets) to be transmitted in the management vlan only, through which the management packets are isolated from other packets and network security is improved. Z enabling the management device and the member devices...
Page 595
Downstream switch compares its own mac address with the destination mac address carried in the multicast packet: z if the two mac addresses are the same, the downstream switch sends a response to the switch sending the tracemac command, indicating the success of the tracemac command. Z if the two ma...
Page 596
Task remarks enabling ndp globally and on specific ports required configuring ndp-related parameters optional enabling ntdp globally and on a specific port required configuring ntdp-related parameters optional enabling the cluster function required configuring cluster parameters required configuring...
Page 597
Configuring ndp-related parameters follow these steps to configure ndp-related parameters: to do… use the command… remarks enter system view system-view — configure the holdtime of ndp information ndp timer aging aging-in-seconds optional by default, the holdtime of ndp information is 180 seconds. C...
Page 598
To do… use the command… remarks launch topology information collection manually ntdp explore optional enabling the cluster function follow these steps to enable the cluster function: to do… use the command… remarks enter system view system-view — enable the cluster function globally cluster enable r...
Page 600
Z the cluster switches are properly connected; z the shared servers are properly connected to the management switch. 2) configuration procedure follow these steps to configure the network management interface for a cluster: to do… use the command… remarks enter system view system-view — enter cluste...
Page 601
To reduce the risk of being attacked by malicious users against opened socket and enhance switch security, the switch 4500 series ethernet switches provide the following functions, so that a cluster socket is opened only when it is needed: z opening udp port 40000 (used for cluster) only when the cl...
Page 602
To do… use the command… remarks enter ethernet port view interface interface-type interface-number — enable ntdp on the port ntdp enable required enabling the cluster function follow these steps to enable the cluster function: to do… use the command… remarks enter system view system-view — enable th...
Page 604
Configuring the enhanced cluster features complete the following tasks to configure the enhanced cluster feature: task remarks configuring cluster topology management function required configuring cluster device blacklist required configuring cluster topology management function 1) configuration pre...
Page 605
If the management device of a cluster is a slave device in an xrn fabric, the standard topology information is saved only to the local flash of the master device in the xrn fabric. Configuring cluster device blacklist follow these steps to configure the cluster device blacklist on a management devic...
Page 606
Z ndp and ntdp have been enabled on the management device and member devices, and ndp- and ntdp-related parameters have been configured. Z a cluster is established, and you can manage the member devices through the management device. 2) configuration procedure perform the following operations on the...
Page 607
Z the mib view name is mib_a, which includes all objects of the subtree org z the snmpv3 user is user_a, which belongs to the group group_a. # create a community with the name of read_a, allowing read-only access right using this community name. [test_0.Sysname-cluster] cluster-snmp-agent community ...
Page 608
Snmp-agent community read read_a@cm0 snmp-agent community write write_a@cm0 snmp-agent sys-info version all snmp-agent group v3 group_a snmp-agent mib-view included mib_a org snmp-agent usm-user v3 user_a group_a undo snmp-agent trap enable standard z configuration file content on a member device (o...
Page 609
Z perform the above operations on the management device of the cluster. Z creating a public local user is equal to executing these configurations on both the management device and the member devices (refer to the aaa operation part in this manual), and these configurations will be saved to the confi...
Page 610
Cluster configuration examples basic cluster configuration example network requirements three switches compose a cluster, where: z a switch 4500 series switch serves as the management device. Z the rest are member devices. Serving as the management device, the switch 4500 switch manages the two memb...
Page 611
[sysname] interface ethernet 1/0/1 [sysname-ethernet1/0/1] ntdp enable [sysname-ethernet1/0/1] quit # enable the cluster function. [sysname] cluster enable 2) configure the management device # add port ethernet 1/0/1 to vlan 2. System-view [sysname] vlan 2 [sysname-vlan2] port ethernet 1/0/1 [sysnam...
Page 612
[sysname] ntdp timer hop-delay 150 # set the delay for a member device port to forward topology collection requests to 15 ms. [sysname] ntdp timer port-delay 15 # set the interval between collecting topology information to 3 minutes. [sysname] ntdp timer 3 # enable the cluster function. [sysname] cl...
Page 614
[sysname] management-vlan 3 # add ethernet 1/0/1 to vlan 3. [sysname] vlan 3 [sysname-vlan3] port ethernet 1/0/1 [sysname-vlan3] quit # set the ip address of vlan-interface 3 to 192.168.5.30. [sysname] interface vlan-interface 3 [sysname-vlan-interface3] ip address 192.168.5.30 255.255.255.0 [sysnam...
Page 615
Network diagram figure 48-6 network diagram for the enhanced cluster feature configuration ftp server 192. 168.0.4 2 4 3 192. 168.0.1 0001- 2034-a0e5 management device member device member device member device 1 configuration procedure # enter cluster view. System-view [aaa_0.Sysname] cluster # add ...
Page 616: Poe Configuration
49 poe configuration wh n configuring poe, g e o to these sections for information you are interested in: z poe overview poe configuration z ration example z poe configu introd rnet (poe)-enabled devices use twisted pairs through electrical ports to supply power evices (pd) in the network and implem...
Page 617
Z it can deliver data and current simultaneously through data wires (1,2,3,and 6) of category-3/5 twisted pairs. Z through the fixed 24/48 ethernet electrical ports, it can supply power to up to 24/48 remote z z or the switch, the maximum total power that can be provided is lying full power to all o...
Page 618
Task remarks upgrading the pse processing software online optional upgrading the pse processing software of fabric switches online optional displaying poe configuration optional enab follow these nable the poe fe ling the poe feature on a port steps to e ature on a port: to do… use the command… rema...
Page 619
Z auto : when the switch is close to its full load in supplying power, it will first supply power to the pds that are connected to the ports with critical priority, and then supply power to the pds that are connected to the ports with high priority. For example: port a has the priority of critical. ...
Page 620
Configuring the pd compatibility detection function after the pd compatibility detection function is enabled, the switch can detect the pds that do not conform to the 802.3af standard and supply power to them. After the poe feature is enabled, perform the following configuration to enable the pd com...
Page 621
Z when the internal temperature of the switch decreases from x (x>65°c, or x>149°f) to y (60°c≤y ports. Z when the internal temperature of the switch increases from x (x (60°c ports. Upgrading the pse processing software online the online upgrading of pse processing software can update the processin...
Page 623
Network diagram figure 49-1 network diagram for poe configuration procedure # upgrade the pse processing software online. System-view [switcha] poe update refresh 0290_021.S19 # enable the poe feature on ethernet 1/0/1, and set the poe maximum output power of ethernet 1/0/1 to 12,000 mw. [switcha] i...
Page 624: Poe Profile Configuration
50-1 50 poe profile configuration wh n configuring poe profile, g e o to these sections for information you are interested in: z introduction to poe profile z poe profile configuration z displaying poe profile configuration le z poe profile configuration examp intro le users, to help network adminis...
Page 627
50-4 n pplication etwork diagram figure 50-1 poe profile a network ip phone switch a ap ap ip phone ap ip phone ip phone ap eth1/0/1~eth1/0/5 eth1/0/6~eth1/0/10 c add the poe policy configuration applicable to ethernet 1/0/1 through ethernet 1/0/5 ports ailed configuration information for profile1. ...
Page 628
50-5 [switcha-poe-profile-profile2] poe mode signal [switcha-poe-profile-profile2] poe priority high [switcha-poe-profile-profile2] poe max-power 15400 [switcha-poe-profile-profile2] quit # display detailed configuration information for profile2. [switcha] display poe-profile name profile2 poe-profi...
Page 629: Udp Helper Configuration
51 udp helper configuration when configuring udp helper, go to these sections for information you are interested in: z introductiontoudphelper z configuring udp helper z displaying and maintaining udp helper le z udp helper configuration examp intro est to relay specified destination server. Acco z ...
Page 630
Protocol udp port number tacacs (terminal access controller access control system) 49 tftp (trivial file transfer protocol) 69 time service 37 configuring udp helper follow these configure udp hel steps to per: to do… use the command… remarks enter system view system-view — enable udp helper udp-hel...
Page 631
Displaying and maintaining udp helper to do… use the command… remarks display the udp broadcast relay forwarding information of a specified vlan interface on the switch display udp-helper server [ interface vlan-interface vlan-id ] available in any view clear statistics about packets forwarded by ud...
Page 632: Snmp Configuration
52 snmp configuration wh n configuring snmp, go to these sec e tions for information you are interested in: z snmp overview z configuring basic snmp functions z configuring trap-related functions anagement z enabling logging for network m displaying snmp z ation example z snmp configur snm can ism a...
Page 633
Z set the permission for a community to access an mib object to be read-only or read-write. Communities with read-only permissions can only query the switch information, while those with read-write permission can configure the switch as well. Z set the basic acl specified by the community name. Supp...
Page 638
Z perform the following configuration on switch a: setting the community name and access permission, administrator id, contact and switch location, and enabling the switch to sent traps. Thus, the nms is able to access switch a and receive the traps sent by switch a. Network diagram figure 52-2 netw...
Page 639
[sysname] snmp-agent trap enable standard linkdown [sysname] snmp-agent target-host trap address udp-domain 10.10.10.1 udp-port 5000 params securityname public configuring the nms authentication-related configuration on an nms must be consistent with that of the devices for the nms to manage the dev...
Page 640: Rmon Configuration
53-1 53 rmon configuration wh n configuring rmon, g e o to these sections for information you are interested in: n z introduction to rmo z rmon configuration z displaying rmon mple z rmon configuration exa intro made to mib ii standards. Rmon is mainly used to monitor the data traffic etwork segment...
Page 641
53-2 of the network segments to which the ports of the managed network devices are connected. Thus, the nms can further manage the networks. Commonly e nts. The arm u ng ways in response to an event: z sending traps to the nms the event and sending traps to the nms a anagement enables monitoring on ...
Page 642
53-3 s e time when the statistics group is created. S, broadcast packets, multicast packets, and with the rmon statistics management function, you can monitor the use of a port and make statistics rmo before g rmon configu nmp agents are correc ed. For the i m uration, refer to section configu basic...
Page 643
53-4 z the rmon alarm and rmon prialarm commands take effect on existing nodes only. Z rmon n rmon statistics entry is already created for a given port, you will fail to create another statistics entry with a different index for each port, only one statistics entry can be created. That is, if a for ...
Page 644
53-5 nded alarm table to allow the system to calculate the alarm .1.2.1.16.1.1.1.10.1) formula to get the numbers of all by ethernet 1/0/1 that are in correct data format and g threshold of ge ratio drops under the falling threshold, event 2 is triggered. 2.1.16.1.1.1.9.1+.1.3.6.1.2.1.16.1.1.1.10.1)...
Page 645: Ntp Configuration
54 ntp configuration wh n configuring ntp, go to these e sections for information you are interested in: z introduction to ntp z ntp configuration task list z configuring ntp implementation modes z configuring access control right z configuring ntp authentication parameters z configuring optional nt...
Page 646
Z defining the accuracy of clocks by stratum to synchronize the clocks of all devices in a network quickly z supporting access control (see section configuring access control right ) and md5 encrypted authentication (see section configuring ntp authentication ) sending protocol packets in unicast, m...
Page 647
Figure 54-1 implementation principle of ntp ip network ip network ip network ip network device b device a device b device a device b device a device b device a 10:00:00 am 11:00:01 am 10:00:00 am ntp message 10:00:00 am 11:00:01 am 11:00:02 am ntp message ntp message ntp message received at 10:00:03...
Page 648
Server/client mode figure 54-2 server/client mode symmetric peer mode figure 54-3 symmetric peer mode in the symmetric peer mode, the local s4500 ethernet switch serves as the symmetric-active peer and sends clock synchronization request first, while the remote server serves as the symmetric-passive...
Page 649
Multicast mode figure 54-5 multicast mode table 54-1 describes how the above mentioned ntp modes are implemented on 3com s4500 series ethernet switches. Table 54-1 ntp implementation modes on 3com s4500 series ethernet switches ntp implementation mode configuration on s4500 series switches server/cl...
Page 650
Z when a 3com s4500 ethernet switch works in server mode or symmetric passive mode, you need not to perform related configurations on this switch but do that on the client or the symmetric-active peer. Z the ntp server mode, ntp broadcast mode, or ntp multicast mode takes effect only after the local...
Page 651
Z execution of one of the ntp-service unicast-server, ntp-service unicast-peer, ntp-service broadcast-client, ntp-service broadcast-server, ntp-service multicast-client, and ntp-service multicast-server commands enables the ntp feature and opens udp port 123 at the same time. Z execution of the undo...
Page 654
To do… use the command… remarks enter system view system-view — enter vlan interface view interface vlan-interface vlan-id — configure the switch to work in the ntp multicast client mode ntp-service multicast-client [ ip-address ] required not configured by default. Configuring access control right ...
Page 655
The access-control right mechanism provides only a minimum degree of security protection for the local switch. A more secure method is identity authentication. Configuring ntp authentication in networks with higher security requirements, the ntp authentication function must be enabled to run ntp. Th...
Page 656
Configuration procedure configuring ntp authentication on the client follow these steps to configure ntp authentication on the client: to do… use the command… remarks enter system view system-view — enable the ntp authentication function ntp-service authentication enable required disabled by default...
Page 657
To do… use the command… remarks configure the specified key as a trusted key ntp-service reliable authentication-keyid key-id required by default, no trusted authentication key is configured. Enter vlan interface view interface vlan-interface vlan-id — configure on the ntp broadcast server ntp-servi...
Page 658
If you have specified an interface in the ntp-service unicast-server or ntp-service unicast-peer command, this interface will be used for sending ntp messages. Configuring the number of dynamic sessions allowed on the local switch a single device can have a maximum of 128 associations at the same ti...
Page 659
To do… use the command… remarks display the information about the sessions maintained by ntp display ntp-service sessions [ verbose ] display the brief information about ntp servers along the path from the local device to the reference clock source display ntp-service trace configuration examples co...
Page 660
[deviceb] display ntp-service status clock status: synchronized clock stratum: 3 reference clock id: 1.0.1.11 nominal frequency: 100.0000 hz actual frequency: 100.0000 hz clock precision: 2^18 clock offset: 0.66 ms root delay: 27.47 ms root dispersion: 208.39 ms peer dispersion: 9.63 ms reference ti...
Page 661
Configuration procedure z configure device c. # set device a as the ntp server. System-view [devicec] ntp-service unicast-server 3.0.1.31 z configure device b (after the device c is synchronized to device a). # enter system view. System-view # set device c as the peer of device b. [deviceb] ntp-serv...
Page 662
Configuring ntp broadcast mode network requirements z the local clock of device c is set as the ntp master clock, with a stratum level of 2. Configure device c to work in the ntp broadcast server mode and send ntp broadcast messages through vlan-interface 2. Z device a and device d are two s4500 eth...
Page 663
View the ntp status of device d after the clock synchronization. [deviced] display ntp-service status clock status: synchronized clock stratum: 3 reference clock id: 3.0.1.31 nominal frequency: 100.0000 hz actual frequency: 100.0000 hz clock precision: 2^18 clock offset: 198.7425 ms root delay: 27.4...
Page 664
Network diagram figure 54-9 network diagram for ntp multicast mode configuration configuration procedure z configure device c. # enter system view. System-view # set device c as a multicast server to send multicast messages through vlan-interface 2. [devicec] interface vlan-interface 2 [devicec-vlan...
Page 665
Root dispersion: 208.39 ms peer dispersion: 9.63 ms reference time: 17:03:32.022 utc apr 2 2007 (bf422ae4.05aea86c) the output information indicates that device d is synchronized to device c, with a clock stratum level of 3, one stratum level lower than that device c. # view the information about th...
Page 666
Z to synchronize device b, you need to perform the following configurations on device a. # enable the ntp authentication function. System-view [devicea] ntp-service authentication enable # configure an md5 authentication key, with the key id being 42 and the key being anicekey. [devicea] ntp-service...
Page 667: Ssh Configuration
55 ssh configuration wh n configuring ssh, go to e these sections for information you are interested: z ssh overview z ssh server and client z displaying and maintaining ssh configuration comparison of ssh commands with the same functions z ration examples z ssh configu introd the same time. As an s...
Page 668
The same key is used for both encryption and decryption. Supported symmetric key algorithms include des, 3des, and aes, which can effectively prevent data eavesdropping. Z asymmetric key algorithm asymmetric key algorithm is also called public key algorithm. Both ends have their own key pair, consis...
Page 669
Cu ently, the switch supports only ssh2 version. Rr versi z he first packet to the client, which includes a version identification string in the ile the software version number is used for debugging. On of the server; otherwise, the client uses its own protocol version. Nt sends to the server a pack...
Page 670
Z the client selects an authentication type from the method list to perform authentication again. The above process repeats until the authentication succeeds, or the connection is torn down when the authentication times reach the upper limit. Provides two authentication methods: password authen z ss...
Page 671
Figure 55-2 network diagram for ssh connections configure the devices accordingly this document describes two cases: h acts as the ssh server to cooperate with another switch that acts as an ssh client. Complete the following tasks to configure the ssh server and clients: z the switch acts as the ss...
Page 672
Complete the following tasks to configure the ssh server: task remarks configuring the user interfaces for ssh clients required preparation configuring the ssh management functions optional key configuring key pairs required authentication creating an ssh user and specifying an authentication type r...
Page 674
Z e a login header on ice type is stelnet. For configuration of service types, refer to specifying a service type for an ssh user on the server you can configur ly when the serv . Z d, ction in for details of the header comman refer to the corresponding se login command. Configuring key pairs the ss...
Page 675
To do… use the command… remarks destroy the rsa key pair public-key local destroy rsa optional ing an authentication type this task is to create an ssh user and specify an authentication type. Specifying an authentication type for a new user is a must to get the user login. Creating an ssh user and ...
Page 677
If the ssh use automatically r service-type command is executed with a username that does not exist, the system will create the ssh user. However, the user cannot log in unless you specify an authentication type for it. Configuring the public key of a client on the server this configuration is not n...
Page 678
To do... Use the command... Remarks enter system iew system-view — v import the public key from a public-key peer keyname required public key file import sshkey filename assigning a public key to an ssh user this configuration task is unnecessary if the ssh user’s authenticatio password. N mode is f...
Page 679
With the filename argument specified, you can export you can configure the key at a remote end by importing th s not specified, this command e host public en in the rsa host public key to a file so that e file. If the filename argument i displays th key information on the scre a specified format. Co...
Page 680
Task remarks required for publickey authentication; opening an ssh connection with publickey authenti unnecessary for password authentication cation z is recommended to use putty release 0.53; putty release 0.58 is also supported. Z on, you must select ssh selecting the ssh version. Since the device...
Page 681
Note that while generating the key pair, you must move the mouse continuously and keep the mouse off the green process bar in the blue box of shown in figure 55-4 . Otherwise, the process bar stops moving and the key pair generating process is stopped. Figure 55-4 generate the client keys (2) after ...
Page 682
Likewise, to save the private key, click save private key. A warning window pops up to prompt you any precaution. Click yes and enter the name of the file for ) to save the private key. Whether to save the private key without saving the private key (“private” in this case figure 55-6 generate the cl...
Page 683
Figure 55-8 ssh client configuration interface 1 in the host name (or ip address) text box, enter the ip address of the server. Note that there must be a route available between the ip address of the server and the client. Selecting a protocol for remote connection as shown in figure 55-8 , select s...
Page 684
Figure 55-9 ssh client configuration interface 2 under protocol options, select 2 from preferred ssh protocol version. Some ssh client software, for example, tectia client software, supports the des algorithm only when the ssh1 version is selected. The putty client software supports des algorithm ne...
Page 685
Figure 55-10 ssh client configuration interface 3 click browse… to bring up the file selection window, navigate to the private key file and click open. If the connection is normal, a user will be prompted for a username. Once passing the authentication, the user can log in to the server. Configuring...
Page 686
Configuring whether first-time authentication is supported when the device connects to the ssh server as an ssh client, you can configure whether the device supports first-time authentication. Z with first-time authentication enabled, an ssh client that is not configured with the server host public ...
Page 687
Follow these steps to specify a source ip address/interface for the ssh client: to do... Use the command... Remarks enter system view system-view — specify a source ip address for the ssh client ssh2 source-ip ip-address optional by default, no source ip address is configured. Specify a source inter...
Page 688
To do... Use the command... Remarks display information about all ssh users display ssh user-information [ username ] display the current source ip address or the ip address of the source interface specified for the ssh server. Display ssh-server source-ip display the mappings between host public ke...
Page 689
The results of the display rsa local-key-pair public command or the public key converted with the sshkey tool contains no information such as the authentication type, so they cannot be directly used as parameters in the public-key peer command. For the same reason, neither can the results of the dis...
Page 690
# enable the user interfaces to support ssh. [switch-ui-vty0-4] protocol inbound ssh [switch-ui-vty0-4] quit # create local client client001, and set the authentication password to abc, protocol type to ssh, and command privilege level to 3 for the client. [switch] local-user client001 [switch-luser...
Page 691
Figure 55-13 ssh client configuration interface (2) under protocol options, select 2 from preferred ssh protocol version. 3) as shown in figure 55-13 , click open. If the connection is normal, you will be prompted to enter the user name client001 and password abc. Once authentication succeeds, you w...
Page 692
Network diagram figure 55-14 switch acts as server for password and radius authentication configuration procedure 1) configure the radius server this document takes cams version 2.10 as an example to show the basic radius server configurations required. # add an access device. Log in to the cams man...
Page 693
Figure 55-15 add an access device # add a user account for device management. From the navigation tree, select user management > user for device management, and then in the right pane, click add to enter the add account page and perform the following configurations: z add a user named hello, and spe...
Page 694
Generating the rsa key pair on the server is prerequisite to ssh login. # generate rsa key pairs. [switch] public-key local create rsa # set the authentication mode for the user interfaces to aaa. [switch] user-interface vty 0 4 [switch-ui-vty0-4] authentication-mode scheme # enable the user interfa...
Page 695
Figure 55-17 ssh client configuration interface (1) in the host name (or ip address) text box, enter the ip address of the ssh server. Z from the category on the left pane of the window, select connection > ssh. The window as shown in figure 55-18 appears. Figure 55-18 ssh client configuration inter...
Page 696
Authentication succeeds, you will log in to the server. The level of commands that you can access after login is authorized by the cams server. You can specify the level by setting the exec privilege level argument in the add account window shown in figure 55-16 . When switch acts as server for pass...
Page 697
# enable the user interfaces to support ssh. [switch-ui-vty0-4] protocol inbound ssh [switch-ui-vty0-4] quit # configure the hwtacacs scheme. [switch] hwtacacs scheme hwtac [switch-hwtacacs-hwtac] primary authentication 10.1.1.1 49 [switch-hwtacacs-hwtac] primary authorization 10.1.1.1 49 [switch-hw...
Page 698
2) from the category on the left pane of the window, select connection > ssh. The window as shown in figure 55-21 appears. Figure 55-21 ssh client configuration interface (2) under protocol options, select 2 from preferred ssh protocol version. Then, click open. If the connection is normal, you will...
Page 699
Configuration procedure z configure the ssh server # create a vlan interface on the switch and assign an ip address, which the ssh client will use as the destination for ssh connection. System-view [switch] interface vlan-interface 1 [switch-vlan-interface1] ip address 192.168.0.1 255.255.255.0 [swi...
Page 700
Figure 55-23 generate a client key pair (1) while generating the key pair, you must move the mouse continuously and keep the mouse off the green process bar shown in figure 55-24 . Otherwise, the process bar stops moving and the key pair generating process is stopped..
Page 701
Figure 55-24 generate a client key pair (2) after the key pair is generated, click save public key and enter the name of the file for saving the public key (public in this case). Figure 55-25 generate a client key pair (3) likewise, to save the private key, click save private key. A warning window p...
Page 702
Figure 55-26 generate a client key pair (4) after a public key pair is generated, you need to upload the pubic key file to the server through ftp or tftp, and complete the server end configuration before you continue to configure the client. # establish a connection with the ssh server 2) launch put...
Page 703
Figure 55-28 ssh client configuration interface (2) under protocol options, select 2 from preferred ssh protocol version. 4) select connection/ssh/auth.The following window appears. Figure 55-29 ssh client configuration interface (3) click browse to bring up the file selection window, navigate to th...
Page 704
5) from the window shown in figure 55-29 , click open. If the connection is normal, you will be prompted to enter the username. When switch acts as client for password authentication network requirements as shown in figure 55-30 , establish an ssh connection between switch a (ssh client) and switch ...
Page 705
[switchb-luser-client001] service-type ssh level 3 [switchb-luser-client001] quit # configure the authentication type of user client001 as password. [switchb] ssh user client001 authentication-type password z configure switch a # create a vlan interface on the switch and assign an ip address, which ...
Page 706
[switchb-vlan-interface1] quit generating the rsa key pair on the server is prerequisite to ssh login. # generate rsa key pair. [switchb] public-key local create rsa # set the authentication mode for the user interfaces to aaa. [switchb] user-interface vty 0 4 [switchb-ui-vty0-4] authentication-mode...
Page 707
After the key pair is generated, you need to upload the pubic key file to the server through ftp or tftp and complete the server end configuration before you continue to configure the client. # establish an ssh connection to the server 10.165.87.136. [switcha] ssh2 10.165.87.136 username: client001 ...
Page 708
Generating the rsa key pair on the server is prerequisite to ssh login. # generate rsa key pair. [switchb] public-key local create rsa # set aaa authentication on user interfaces. [switchb] user-interface vty 0 4 [switchb-ui-vty0-4] authentication-mode scheme # configure the user interfaces to suppo...
Page 709
# create a vlan interface on the switch and assign an ip address, which serves as the ssh client’s address in an ssh connection. System-view [switcha] interface vlan-interface 1 [switcha-vlan-interface1] ip address 10.165.87.137 255.255.255.0 [switcha-vlan-interface1] quit # generate a rsa key pair ...
Page 710
56 file system management configuration wh n configuring file system ma e nagement, go to these sections for information you are interested in: z file system configuration file attribute configuration z estoration z configuration file backup and r ion introd the file system function, allowing you to...
Page 711
Directory s: z creating/deleting a directory z displayi nt work directo ified directory f perform direc ations: operations the file system provides directory-related functions, such a ng the curre ry, or contents in a spec ollow these steps to tory-related oper to do… use the command… remarks create...
Page 712
To do… use the command… remarks rename a file rename fileurl-source fileurl-dest optional available in user view copy a file copy fileurl-source fileurl-dest optional available in user view optional available in user view move a file move fileurl-source fileurl-dest display the content of a file mor...
Page 713
The format operation leads to the loss of all files, including the configuration files, on the flash memory and is irretrievable. Prompt mode configuration y pt mode of system to alert or iet. In alert mode, the file system will give a prompt for confirmation if you execute a command which may cause...
Page 714
Directory of unit1>flash:/ 1 (*) -rw- 5822215 jan 01 1970 00:07:03 test.Bin 2 -rwh 4 apr 01 2000 23:55:49 snmpboots 3 -rwh 428 apr 02 2000 00:47:30 hostkey 4 -rwh 572 apr 02 2000 00:47:38 serverkey 5 -rw- 1220 apr 02 2000 00:06:57 song.Cfg 01 1970 00:04:34 testv1r1.Bin 7 -rwh 88 apr 01 2000 23:55:53...
Page 715
Attribute name description feature identifier backup a switch fails to start up using the main startup file. In the flash memory, there be only one app file, one configuration file and one web file with the backup attribute. (b) identifies backup startup files. The backup startup file is used after ...
Page 716
Configuring file attributes y a ute of t d for the next startup of a ain or b ibute of the file. F ile ou can configure and view the m switch, and change the m in attribute or backup attrib ackup attr he file use ollow these steps to configure f attributes: to do… use the command… remarks configure ...
Page 717
Con introd ackup and restoration feature, you can easily back up and restore the configuration files in the whole fabric as well as in a specific unit. Ystem first saves the current configuration of a unit to the startup e restore process, the system the tftp server to the local unit. Its in the fab...
Page 718: Ftp and Sftp Configuration
57 ftp and sftp configuration wh n configuring ftp a e nd sftp, go to these sections for information you are interested in: nd sftp introduction to ftp a z ftp configuration z sftp configuration z introduction to ftp and sftp introd , files are transferred through command lines, and the most popular...
Page 719
Files from an ftp server, and stops rotating when the file downloading is finished, as shown in figure 57-1 . Figure 57-1 clockwise rotating of the seven-se gment digital led introduction to sftp a ansmit files, providing a securer guarantee for data transmission. In addition, used as a client, you ...
Page 721
Follow these steps to configure connection idle time: to do… use the command… remarks enter system view — system-view optional configure the connection idle time for the ftp server ftp timeout minutes 30 minutes by default specifying the source interface and source ip address for an ftp server you c...
Page 722
Disconnecting a specified user on the ftp server, you can disconnect a specified user from the ftp server to secure the network. Follow these steps to disconnect a specified user: to do… use the command… remarks enter system view — system-view on the ftp server, disconnect a specified user from the ...
Page 723
Figure 57-3 process of displaying a shell banner follow these steps to configure the banner display for an ftp server: to do… use the command… remarks enter system view — system-view configure a login banner header login text required use either command or both. By default, no banner is configured. ...
Page 725
To do… use the command… remarks download a remote file from the ftp server get remotefile [ localfile ] upload a local file to the remote ftp server put ] localfile [ remotefile rename rename a file on the remote server - remote source remote-dest log in with the specified user name and password use...
Page 726
Z the specified interface must be an existing one. Otherwise a prompt appears to show that the configuration fails. Z the value of the ip-address argument must be the ip address of the device where the configuration is performed. Otherwise a prompt appears to show that the configuration fails. Z the...
Page 727
[sysname] local-user switch [sysname-luser-switch] password simple hello [sysname-luser-switch] service-type ftp 2) configure the pc (ftp client) run an ftp client application on the pc to connect to the ftp server. Upload the application named switch.Bin to the root directory of the flash memory of...
Page 728
Z if available space on the flash memory of the switch is not enough to hold the file to be uploaded, you need to delete files not in use from the flash memory to make room for the file, and then upload the file again. The files in use cannot be deleted. If you have to delete the files in use to mak...
Page 729
Configuration procedure 1) configure the switch (ftp server) # configure the login banner of the switch as “login banner appears” and the shell banner as “shell banner appears”. For detailed configuration of other network requirements, see section configuration example: a switch operating as an ftp ...
Page 730
Configuration procedure 1) configure the pc (ftp server) perform ftp server–related configurations on the pc, that is, create a user account on the ftp server with username switch and password hello. (for detailed configuration, refer to the configuration instruction relevant to the ftp server softw...
Page 731
Boot boot-loader switch.Bin reboot for information about the boot boot-loader command and how to specify the startup file for a switch, refer to the system maintenance and debugging module of this manual. Sftp configuration complete the following tasks to configure sftp: task remarks enabling an sft...
Page 732
To do… use the command… remarks enter system view — system-view optional configure the connection idle time for the sftp server ftp timeout time-out-value 10 minutes by default. Supported sftp client software a 3com switch 4500 operating as an sftp server can interoperate with sftp client software, ...
Page 734
If you specify to authenticate a client through public key on the server, the client needs to read the local private key when logging in to the sftp server. Since both rsa and dsa are available for public key authentication, you need to use the identity-key key word to specify the algorithms to get ...
Page 735
[sysname] public-key local create dsa # create a vlan interface on the switch and assign to it an ip address, which is used as the destination address for the client to connect to the sftp server. [sysname] interface vlan-interface 1 [sysname-vlan-interface1] ip address 192.168.0.1 255.255.255.0 [sy...
Page 736
Sftp-client> # display the current directory of the server. Delete the file z and verify the result. Sftp-client> dir -rwxrwxrwx 1 noone nogroup 1759 aug 23 06:52 config.Cfg -rwxrwxrwx 1 noone nogroup 225 aug 24 08:01 pubkey2 -rwxrwxrwx 1 noone nogroup 283 aug 24 07:39 pubkey1 drwxrwxrwx 1 noone nog...
Page 737
-rwxrwxrwx 1 noone nogroup 283 aug 24 07:39 pubkey1 drwxrwxrwx 1 noone nogroup 0 sep 01 06:22 new -rwxrwxrwx 1 noone nogroup 225 sep 01 06:55 pub drwxrwxrwx 1 noone nogroup 0 sep 02 06:33 new2 received status: end of file received status: success # download the file pubkey2 from the server and renam...
Page 738: Tftp Configuration
58-1 58 tftp configuration wh n configuring tftp, g e o to these sections for information you are interested in: introduction to tftp z tftp configuration z intro ble in the networks where client-server . It transfers data through udp tft er. Ackets to the tftp server, then sends data to the ownload...
Page 739
58-2 tftp configuration complete the following tasks to configure tftp: task remarks basic configurations on a tftp client — tftp configuration: a switch operating as a tftp client specifying the source interface r an or source ip address fo ftp client optional tftp server configuration correspondin...
Page 741
58-4 s network diagram figure 58-1 network diagram for tftp configuration configuration procedure 1) configure the tftp server (pc) start the tftp server and configure the working directory on the pc. 2) configure the tftp client (switch). # log in to the switch. (you can log in to a switch through ...
Page 742
58-5 for information about the boot boot-loader command and how to specify the startup file for a switch, refer to the system maintenance and debugging module of this manual..
Page 743: Information Center
59 information center wh n configuring information center, g e o to these sections for information you are interested in: z information center overview z information center configuration displaying and maintaining information center z amples z information center configuration ex introd bugging funct...
Page 744
Information filtering by severity works this way: information with the severity value greater than the z if the threshold is set to 1, only information with the severity being emergencies will be output; ten channels and six ou 5 have their default channel names and are associated with six output de...
Page 745
O the system n be classified by source module and some module names and description are shown in table 59-3 utputting system information by source module information ca then filtered. . Table 59-3 source module name list module name description 8021x 802.1x module acl access control list module adbm...
Page 746
Module name description sysmib system mib module tac hwtacacs module telnet telnet module tftpc e tftp client modul vlan virtual local area network module vty virtual type terminal module xm xmodem module default default settings for all the modules the information center is to output the three type...
Page 747
Z if the address of the log host is specified in the information center of the switch, when logs are generated, the switch sends the logs to the log host in the above format. For detailed information, refer to setting to output system information to a log host . There is the syslog proce z ss on the...
Page 748
Locate and solve problems globally. In this case, you can configure the information center to add utc the standard time when the ow the greenwich standard formation center output information, you must: set the time stamp format in the output destination of the information center to date he above con...
Page 749
Source t , such as the source ip address of the log sender. This f is the log host. Co t information center configuration inform com r: his field indicates the source of the information ield is optional and is displayed only when the output destination ntext his field provides the content of the sys...
Page 750
Z if the system information is output before you input any informati g the current command n pro output. Z mode, you are e information t. If the input is interrupted by o om will be echoed after the output, but your a ew on followin line prompt, the system does ot echo any command line mpt after the...
Page 752
Follow these steps to enable the system information display on the console: to do… use the command… remarks enable the debugging/log/trap information terminal display function terminal monitor optional enabled by default. Enable debugging information optional terminal display function terminal debug...
Page 753
Z when there are multiple telnet users or dumb terminal users, they share some configuration case, change to any such pa ade by one use other use z to view de formation of spe to set the info e as debug nforma nd enab ing for corresponding and. Parameters including module filter, language and severi...
Page 757
With this feature applied to a port, when the state of the port changes, the system does not generate port link up/dow information. In this c tor the port s c e rmal cases. N logging ase, you cannot moni state change onveniently. Therefore, it is recommend d to use the default configuration in no di...
Page 758
C the host whose ip address is 202.38.1.10 as the log host. Permit arp and ip modules to ity level higher than informational to the log host. Arp channel loghost log level informational debug state off trap el loghost log level informational debug state off trap systems are similar. Er user (root us...
Page 759
# kill -hup 147 after all the above operations, the switch can make records in the corresponding log file. Through combined configuration of the device name (facility), information severity level threshold the file “syslog.Conf”, you can sort information precisely for filtering. (severity), module n...
Page 760
Note the following items when you edit file “/etc/syslog.Conf”. Z a note must start in a new line, starting with a “#" sign. Z in each pair, a tab should be used as a separator instead of a space. Z no space is permitted at the end of the file name. Z the device name (facility) and received log info...
Page 761
System-view [switch] info-center enable # disable the function of outputting information to the console channels. [switch] undo info-center source default channel console # enable log information output to the console. Permit arp and ip modules to output log information with severity level higher th...
Page 762
60 boot rom and host software loading traditionally, switch software is loaded through a serial port. This approach is slow, time-consuming and cannot be used for remote loading. To resolve these problems, the tftp and ftp modules are troduces how to load the boot rom and host software to a switch l...
Page 763
The loading process of the boot rom software is the same as that of the host software, except that during the former process, you should press “6” or and after entering the boot menu and the system gives different prompts. The following text mainly describes the boot rom loading process. Boot menu s...
Page 764
1. Download application file to flash 2. Select application file to boot 3. Display all files in flash 4. Delete file from flash 5. Modify bootrom password 6. Enter bootrom upgrade menu 7. Skip current configuration file 8. Set bootrom password recovery 9. Set switch startup mode 0. Reboot enter you...
Page 765
0. Return enter your choice (0-5): step 3: choose an appropriate baudrate for downloading. For example, if you press 5, the baudrate 115200 bps is chosen and the system displays the following information: download baudrate is 115200 bit/s please change the terminal's baudrate to 115200 bit/s and sel...
Page 766
Figure 60-2 console port configuration dialog box step 5: click the button to disconnect the hyperterminal from the switch and then click the button to reconnect the hyperterminal to the switch, as shown in figure 60-3 . Figure 60-3 connect and disconnect buttons the new baudrate takes effect after ...
Page 767
Figure 60-4 send file dialog box step 8: click . The system displays the page, as shown in figure 60-5 . Figure 60-5 sending file page step 9: after the sending process completes, the system displays the following information: loading ...Cccccccccc done! Step 10: reset hyperterminal’s baudrate to 96...
Page 768
Loading host software follow these steps to load the host software: step 1: select in boot menu and press . The system displays the following information: 1. Set tftp protocol parameter 2. Set ftp protocol parameter 3. Set xmodem protocol parameter 0. Return to boot menu enter your choice(0-3): step...
Page 769
You can use one pc as both the configuration device and the tftp server. Step 2: run the tftp server program on the tftp server, and specify the path of the program to be downloaded. Tftp server program is not provided with the 3com series ethernet switches. Step 3: run the hyperterminal program on ...
Page 770
0. Return to boot menu enter your choice(0-3): step 2: enter 1 in the above menu to download the host software using tftp. The subsequent steps are the same as those for loading the boot rom, except that the system gives the prompt for host software loading instead of boot rom loading. When loading ...
Page 771
Bootrom update menu: 1. Set tftp protocol parameter 2. Set ftp protocol parameter 3. Set xmodem protocol parameter 0. Return to boot menu enter your choice(0-3): step 4: enter 2 in the above menu to download the boot rom using ftp. Then set the following ftp-related parameters as required: load file...
Page 772
Remote boot rom and software loading if your terminal is not directly connected to the switch, you can telnet to the switch, and use ftp or tftp to load the boot rom and host software remotely. Remote loading using ftp loading procedure using ftp client 1) loading the boot rom as shown in figure 60-...
Page 773
Before restarting the switch, make sure you have saved all other configurations that you want, so as to avoid losing configuration information. 2) loading host software loading the host software is the same as loading the boot rom program, except that the file to be downloaded is the host software f...
Page 774
System view: return to user view with ctrl+z. [sysname] interface vlan-interface 1 [sysname-vlan-interface1] ip address 192.168.0.28 255.255.255.0 step 3: enable ftp service on the switch, and configure the ftp user name to test and password to pass. [sysname-vlan-interface1] quit [sysname] ftp serv...
Page 775
Figure 60-11 enter boot rom directory step 6: enter ftp 192.168.0.28 and enter the user name test, password pass, as shown in figure 60-12 , to log on to the ftp server. Figure 60-12 log on to the ftp server step 7: use the put command to upload the file switch.Btm to the switch, as shown in figure ...
Page 776
Figure 60-13 upload file switch.Btm to the switch step 8: configure switch.Btm to be the boot rom at next startup, and then restart the switch. Boot bootrom switch.Btm this will update bootrom on unit 1. Continue? [y/n] y upgrading bootrom, please wait... Upgrade bootrom succeeded! Reboot after the ...
Page 777
61-1 61 basic system configuration and debugging wh n configuring basic system c e onfiguration and debugging, go to these sections for information you tion are interested in: z basic system configura displaying the system status z z debugging the system bas perform the f ng basic ic system configur...
Page 778
61-2 displaying the sys atus tem st to do… use the command… remarks display the current date and time of the system display clock display the version of the system display version display the information about use switch rs logging onto the display users [ all ] available in any view deb enab res su...
Page 779
61-3 you can use the following commands to s. Follow these steps to enable debugging and terminal display for a sp le: enable the two switche ecific modu to do… use the command… remarks enable system debugging fo specific mod r ule ame es by debugging module-n [ debugging-option ] required disabled ...
Page 780: Network Connectivity Test
62-1 62 network connectivity test wh n config e uring network connectivity test, go to these sections for information you are interested in: ping z z tracert network connectivity test ping you can u command to chec chability of a host. Se the ping k the network connectivity and the rea to do… use th...
Page 781: Device Management
63-1 63 device management wh n configuring device management, g e o to these sections for information you are interested in: z introduction to device management z device management configuration z displaying the device management configuration mple z remote switch app upgrade configuration exa intro...
Page 782
63-2 before rebooting, the system checks whether there is any configuration change. If yes, it prompts whether or not to proceed. This prevents the system from losing the configurations in case of shutting down the system without saving the configurations use the following command to reboot the ethe...
Page 783
63-3 enabling of this function consumes some amounts of cpu resources. Therefore, if your network has a high cpu usage requirement, you can disable this function to release your cpu resources. Specifying the app to be used at reboot app is the host software of the switch. If multiple apps exist in t...
Page 784
63-4 currently, in the s4500 series ethernet switches, the auto power down configuration does not take effect on 1000base-x sfp ports. Upgrading the host software in the fabric you can execute the following command on any device in a fabric to use specified host software to upgrade all devices in a ...
Page 785
63-5 to do… use the command… remarks display main parameters of the pluggable transceiver(s) display transceiver interface [ interface-type interface-number ] available for all pluggable transceivers display part of the electrical label information of the anti-spoofing transceiver(s) customized by h...
Page 786
63-6 to do… use the command… remarks display system diagnostic information or save system diagnostic information to a file with the extension .Diag into the flash memory display diagnostic-information display enabled debugging on a specified switch or all switches in the fabric display debugging{ fa...
Page 787
63-7 refer to the login operation part of this manual for configuration commands and steps about telnet user. 3) execute the telnet command on the pc to log into the switch. The following prompt appears: if the flash memory of the switch is not sufficient, delete the original applications before dow...
Page 788
63-8 unit 1: the current boot app is: switch.Bin the main boot app is: switch.Bin the backup boot app is: # reboot the switch to upgrade the boot rom and host software of the switch. Reboot start to check configuration with next startup configuration file, please wait...... This command will reboot ...
Page 789: Scheduled Task Configuration
64-1 64 scheduled task configuration wha fines a command or a group of commands and when such commands will be with a scheduled task configured, the device checks the configured task list every minute; if the device reached, it automatically executes the command. D task conf z e in the same view. Z ...
Page 790
64-2 modification of the system time will affect the execution of a scheduled task. Config to after a delay time f a scheduled task that will be executed after e uring a scheduled task be executed ollow these steps to configure a delay tim to do… use the command… description enter system view system...
Page 791
64-3 configuration procedure task pc1, and enter scheduled task view. View ethernet1/0/1 isabled on switch at six pm from hone2, phone3, and configure the scheduled task so that the ethernet port witch at eight am from monday to friday. Repeating at 18:00 week-day mon tue wed thu fri command shutdow...
Page 792: Vlan-Vpn Configuration
65 vlan-vpn configuration wh n configuring vlan-vpn, e go to these sections for information you are interested in: z vlan-vpn overview z vlan-vpn configuration displaying and maintaining vlan-vpn configuration z n example z vlan-vpn configuratio introd specify to process ags. In public networks, pac...
Page 793
Z provides simple layer 2 vpn solutions for small-sized mans or intranets. Imple g the received packet with the default vlan tag of the receiving port and add aches a z if the packet already carries a vlan tag, the packet becomes a dual-tagged packet. Ng the default vlan tag of the port. Conf ag. Th...
Page 794
Inner-to-outer tag priority replicating and mapping as shown in figure 65-2 , the user priority field is the 802.1p priority of the tag. The value of this 3-bit field is in the range 0 to 7. By configuring inner-to-outer tag priority replicating or mapping for a vlan-vpn-enabled port, you can replic...
Page 795
To do... Use the command... Remarks enter system view system-view — enter ethernet port view interface interface-type interface-number — set the tpid value on the port vlan-vpn tpid value required do not set the tpid value to any of the protocol type values listed in table 65-1 . For 3com series swi...
Page 796
Displaying and maintaining vlan-vpn configuration to do... Use the command... Remarks display the vlan-vpn configurations of all the ports display port vlan-vpn available in any view vlan-vpn configuration example transmitting user packets through a tunnel in the public network by using vlan-vpn net...
Page 797
# enable the vlan-vpn feature on ethernet 1/0/11 of switch a and tag the packets received on this port with the tag of vlan 1040 as the outer vlan tag. System-view [switcha] vlan 1040 [switcha-vlan1040] port ethernet 1/0/11 [switcha-vlan1040] quit [switcha] interface ethernet 1/0/11 [switcha-etherne...
Page 798
# as the devices in the public network are from other vendors, only the basic principles are introduced here. That is, you need to configure the devices connecting to ethernet 1/0/12 of switch a and ethernet 1/0/22 of switch b to permit the corresponding ports to transmit tagged packets of vlan 1040...
Page 799: Selective Qinq Configuration
66-1 66 selective qinq configuration wh n configuring selective qinq, g e o to these sections for information you are interested in: z selective qinq overview selective qinq configuration z example z selective qinq configuration iew selec n feature. With the selective qinq feature, users. In the pub...
Page 800
66-2 igure to add the tag of vlan 1002 to the packets of the flexibility of network management. On the other hand, network resources are well utilized, are also isolated by their inner vlan tags. This helps to improve network mac addr ts. Thus, users, they may be broadcast if their ac address table ...
Page 801
66-3 r tag and unicast the packet. Dress table of the default vlan and user packets destined for the service provider can be unicast. Selective qinq configuration selective qinq configuration task list complete the following to configure selective qinq: device receives a packet from the service prov...
Page 802
66-4 do not enable both the selective qinq function and the dhcp snooping function on a switch. Otherwise, the dhcp snooping function may operate improperly. Enabling the inter-vlan mac address replicating feature follow these steps to enable the inter-vlan mac address replicating feature: to do... ...
Page 803
66-5 n z the public network permits packets of vlan 1000 and vlan 1200. Apply qos policies for these packets to reserve bandwidth for packets of vlan 1200. That is, packets of vlan 1200 have higher transmission priority over packets of vlan 1000. Z employ the selective qinq feature on switch a and s...
Page 804
66-6 [switcha-ethernet1/0/5] port hybrid vlan 5 1000 1200 tagged [switcha-ethernet1/0/5] quit # configure ethernet 1/0/3 as a hybrid port and configure vlan 5 as its default vlan. Configure ethernet 1/0/3 to remove vlan tags when forwarding packets of vlan 5, vlan 1000, and vlan 1200. [switcha] inte...
Page 805
66-7 [switchb] interface ethernet 1/0/11 [switchb-ethernet1/0/11] port link-type hybrid [switchb-ethernet1/0/11] port hybrid vlan 12 13 1000 1200 tagged # configure ethernet1/0/12 as a hybrid port and configure vlan 12 as its default vlan . Configure ethernet 1/0/12 to remove vlan tags when forwardi...
Page 806: Remote-Ping Configuration
67 remote-ping configuration wh n configuring remote-ping, g e o to these sections for information you are interested in: z remote-ping overview remote-ping configuration z example z remote-ping configuration rem st tistic results of your remote-ping test operation. Remote-ping ote-ping test groups ...
Page 807
If this parameter is set to a number greater than 1, the system sends the second test packet once it receives a response to the first one, or when the test timer times out if it receives no response after d forth until the last test packet is sent out. This parameter is equivalent to ter is similar ...
Page 808
Displ after the a -ping configuration, cute the display co y view to d ote-p can verify the configuration effect. Table 67 ng co aying remote-ping configuration bove remote you can exe mmand in an isplay the information of rem -2 display remote-pi ing test operation status to you nfiguration operati...
Page 809
Square-sum of round trip time: 66 0 on number: 0 ministrator icmp 1 1 0 2004-11-25 16:28:55.0 9 1 1 0 2004-11-25 16:28:55.9 10 1 1 0 2004-11-25 16:28:55.9 refer to the remote-ping command in the command reference guide for detailed description on displayed information. Last complete test time: 2000-...
Page 810: Ipv6 Configuration
68 ipv6 configuration wh n configuring ipv6, go to thes e e sections for information you are interested in: z ipv6 overview ipv6 configuration task list z ration example z ipv6 configu ipv6 engineering task force (ietf) as the successor to internet protocol version 4 (ipv4). The significant tween ip...
Page 811
Hierarchical address structure ipv6 adopts the hierarchical address structure to quicken route search and reduce the system source occupied by the ipv6 routing table by means of route aggregation. Automatic address configuration to simplify the host configuration, ipv6 supports stateful address conf...
Page 812
Z if an ipv6 address contains two or more consecutive groups of zeros, they can be replaced by the double-colon :: option. For example, the above-mentioned address can be represented in the shortest format as 2001:0:130f::9c0:876a:130b. The double-colon :: can be used only once in an ipv6 address. O...
Page 813
Type format prefix (binary) ipv6 prefix id global unicast address other forms — multicast address 11111111 ff00::/8 anycast address anycast addresses are taken from unicast address space and are not syntactically distinguishable from unicast addresses. Unicast address there are several forms of unic...
Page 814
Where, ff02:0:0:0:0:1:ff is permanent and consists of 104 bits, and xx:xxxx is the last 24 bits of an ipv6 address. Interface identifier in ieee eui-64 format interface identifiers in ipv6 unicast addresses are used to identify interfaces on a link and they are required to be unique on that link. In...
Page 815
Icmpv6 message function when the link layer address changes, the local node initiates a neighbor advertisement message to notify neighbor nodes of the change. Router solicitation (rs) message after started, a host sends a router solicitation message to request the router for an address prefix and ot...
Page 816
1) node a multicasts an ns message. The source address of the ns message is the ipv6 address of the interface of node a and the destination address is the solicited-node multicast address of node b. The ns message contains the link-layer address of node a. 2) after receiving the ns message, node b j...
Page 817
Z rfc 1981: path mtu discovery for ip version 6 z rfc 2375: ipv6 multicast address assignments z rfc 2460: internet protocol, version 6 (ipv6) specification. Z rfc 2461: neighbor discovery for ip version 6 (ipv6) z rfc 2462: ipv6 stateless address autoconfiguration z rfc 2463: internet control messa...
Page 819
Z if xrn fabric ports are configured on a 3com switch 4500, no ipv6 address can be configured for the switch. Z ipv6 unicast addresses can be configured for only one vlan interface on a 3com switch 4500. The total number of global unicast addresses and site-local addresses on the vlan interface can ...
Page 820
Configuring the maximum number of neighbors dynamically learned the device can dynamically acquire the link-layer address of a neighbor node through ns and na messages and add it to the neighbor table. Too large a neighbor table may lead to the forwarding performance degradation of the device. There...
Page 821
To do… use the command… remarks specify the ns interval ipv6 nd ns retrans-timer value optional 1,000 milliseconds by default. Configuring the neighbor reachable timeout time on an interface after a neighbor passed the reachability detection, the device considers the neighbor to be reachable in a sp...
Page 822
To do… use the command… remarks set the finwait timer of ipv6 tcp packets tcp ipv6 timer fin-timeout wait-time optional 675 seconds by default. Set the synwait timer of ipv6 tcp packets tcp ipv6 timer syn-timeout wait-time optional 75 seconds by default. Configure the size of ipv6 tcp receiving/send...
Page 824
Network diagram figure 68-5 network diagram for ipv6 address configuration configuration procedure 1) configure switch a. # configure an automatically generated link-local address for the interface vlan-interface 2. System-view [switcha] interface vlan-interface 2 [switcha-vlan-interface2] ipv6 addr...
Page 825
Nd retransmit interval is 1000 milliseconds hosts use stateless autoconfig for addresses # display the brief ipv6 information of the interface on switch b. [switchb-vlan-interface2] display ipv6 interface vlan-interface 2 vlan-interface2 current state : up line protocol current state : up ipv6 is en...
Page 826
Round-trip min/avg/max = 60/66/80 ms [switcha-vlan-interface2] ping ipv6 2001::20f:e2ff:fe00:1 ping 2001::20f:e2ff:fe00:1 : 56 data bytes, press ctrl_c to break reply from 2001::20f:e2ff:fe00:1 bytes=56 sequence=1 hop limit=255 time = 40 ms reply from 2001::20f:e2ff:fe00:1 bytes=56 sequence=2 hop li...
Page 827
69-1 69 ipv6 application configuration wh n configuring ipv6 application e , go to these sections for information you are interested in: z introduction to ipv6 application z configuring ipv6 application ipv6 application configuration example z z troubleshooting ipv6 application intro porting more an...
Page 828
69-2 ipv6 of ipv6 packets from source to destination, nt of failure. Traceroute the traceroute ipv6 command is used to record the route so as to check whether the link is available and determine the poi figure 69-1 traceroute process igure 69 as f -1 shows, the traceroute process is as follows: z he...
Page 830
69-4 displaying and maintaining ipv6 telnet to do… use the command… remarks display the use information of ave logged in display users [ all ] available in any view the users who h ipv6 ipv6 network requirements application configuration example applications in figure 69-3 , swa, swb, and swc are th...
Page 831
69-5 hop limit=64 time = 31 ms bytes=56 sequence=3 hop limit=64 time = 31 ms limit=64 time = 31 ms =5 hop limit=64 time = 31 ms telnet server, and the tftp server. Oget flash:/filegothere received in 1.243 second(s) fully. Telnet server 3001::2. Rver> trou unable to ping a remote destination sy una ...
Page 833
70 password control configuration operations intro rds: et. Z through ftp. Who have logged into the switch and are changing from a lower privilege level to a higher privilege level. Table 70-1 ctions provided by passwo duction to password control configuration the password control feature is designe...
Page 834
Function description application encrypted display: the switch protects the displayed password. The password is always displayed as a string containing only asterisks (*) in the configuration file or on user terminal. Password protection and encryption saving passwords in ciphertext: the switch encr...
Page 835
Password control configuration configuration prerequisites a user pc is connected to the switch to be configured; both devices are operating normally. Configuration tasks the following sections describe the configuration tasks for password control: z configuring password aging z configuring the limi...
Page 836
Operation command description create a local user or enter local user view local-user user-name — configure a password aging time for the local user password-control aging aging-time optional by default, the aging time is 90 days. In this section, you must note the effective range of the same comman...
Page 837
Z you can configure the password aging time when password aging is not yet enabled, but these configured parameters will not take effect. Z after the user changes the password successfully, the switch saves the old password in a readable file in the flash memory. Z the switch does not provide the al...
Page 838
In this section, you must note the effective range of the same commands when executed in different views or to different types of passwords: z global settings in system view apply to all local user passwords and super passwords. Z settings in the local user view apply to the local user password only...
Page 839
Table 70-5 manually remove history password records operation command description remove history password records of one or all users reset password-control history-record [ user-name user-name ] executing this command without the user-name user-name option removes the history password records of al...
Page 840
Z lock-time: in this mode, the system inhibits the user from re-logging in within a certain time period. After the period, the user is allowed to log into the switch again. By default, this time is 120 minutes. Z lock: in this mode, the system inhibits the user from re-logging in forever. The user i...
Page 841
Table 70-9 configure the timeout time for users to be authenticated operation command description enter system view system-view — configure the timeout time for users to be authenticated password-control authentication-timeout authentication-timeout optional by default, it is 60 seconds. Configuring...
Page 842
Operation command description configure the password composition policy for the local user password-control composition type-number policy-type [ type-length type-length ] optional by default, the minimum number of types a password should contain is 1 and the minimum number of characters of each typ...
Page 843
Z for a local user named test, the minimum password length is 6 characters, the minimum number of password composition types is 2, the minimum number of characters in each password composition type is 3, and the password aging time is 20 days. Configuration procedure # enter system view. System-view...
Page 844
71 access management configuration wh n configuring access management, go to these section e s for information you are interested in: z access management overview configuring access management z mples z access management configuration exa acc the access switches provide heir upstream links. In the n...
Page 845
Configuring access management follow these steps to configure access management: to do… use the command… remarks enter system view system-view — enable access management function am enable required by default, the system disables the access management function. Enable access management trap am trap ...
Page 846
Z disable the pcs that are not of organization 1 (pc 2 and pc 3) from accessing the external network through ethernet 1/0/1 of switch a. Network diagram figure 71-2 network diagram for access management configuration configuration procedure perform the following configuration on switch a. # enable a...
Page 847
Z ethernet 1/0/1 and ethernet 1/0/2 belong to vlan 1. The ip address of vlan-interface 1 is 202.10.20.200/24. Z pcs of organization 1 are isolated from those of organization 2 on layer 2. Network diagram figure 71-3 network diagram for combining access management and port isolation configuration pro...
Page 848
[sysname-ethernet1/0/2] am ip-pool 202.10.20.25 26 202.10.20.55 11 # add ethernet 1/0/2 to the port isolation group. [sysname-ethernet1/0/2] port isolate [sysname-ethernet1/0/2] quit 71-5.
Page 849: Lldp Configuration
72-1 72 lldp configuration when configuring lldp, go to these sections for information you are interested in: z overview z lldp configuration task list z performing basic lldp configuration z configuring cdp compatibility z configuring lldp trapping z displaying and maintaining lldp z lldp configura...
Page 850
72-2 figure 72-1 ethernet ii-encapsulated lldp frame format the fields in the frame are described in table 72-1 : table 72-1 description of the fields in an ethernet ii-encapsulated lldp frame field description destination mac address the mac address to which the lldpdu is advertised. It is fixed to...
Page 851
72-3 field description source mac address the mac address of the sending port. If the port does not have a mac address, the mac address of the sending bridge is used. Type the snap type for the upper layer protocol. It is 0xaaaa-0300-0000-88cc for lldp. Data lldpdu. Fcs frame check sequence, a 32-bi...
Page 852
72-4 type description remarks port description port description of the sending port. System name assigned name of the sending device. System description description of the sending device. System capabilities identifies the primary functions of the sending device and the primary functions that have b...
Page 853
72-5 lldp-med tlvs lldp-med tlvs provide multiple advanced applications for voice over ip (voip), such as basic configuration, network policy configuration, and address and directory management. Lldp-med tlvs satisfy the voice device vendors’ requirements for cost effectiveness, ease of deployment, ...
Page 854
72-6 how lldp works transmitting lldp frames an lldp-enabled port operating in txrx mode or tx mode sends lldp frames to its directly connected devices both periodically and when the local configuration changes. To prevent the network from being overwhelmed by lldp frames at times of frequent local ...
Page 855
72-7 performing basic lldp configuration enabling lldp to make lldp take effect on certain ports, you need to enable lldp both globally and on these ports. Follow these steps to enable lldp: to do… use the command… remarks enter system view system-view — enable lldp globally lldp enable required by ...
Page 856
72-8 enabling lldp polling with lldp polling enabled, a device checks for local configuration changes periodically. Upon detecting a configuration change, the device sends lldp frames to inform the neighboring devices of the change. Follow these steps to enable lldp polling: to do… use the command… ...
Page 857
72-9 to do… use the command… remarks enter ethernet interface view interface interface-type interface-number required enable lldp to advertise management address tlvs and configure the advertised management ip address lldp management-address-tlv [ ip-address ] optional by default, the management add...
Page 858
72-10 setting an encapsulation format for lldpdus lldpdus can be encapsulated in ethernet ii or snap frames. Z with ethernet ii encapsulation configured, an lldp port sends lldpdus in ethernet ii frames and processes an incoming lldp frame only when it is ethernet ii encapsulated. Z with snap encaps...
Page 859
72-11 with cdp compatibility enabled, the device can use lldp to receive and recognize cdp packets from cisco ip phones and respond with cdp packets carrying the voice vlan id of the device for the ip phones to configure the voice vlan automatically. In this way, voice traffic is confined in the con...
Page 860
72-12 follow these steps to configure lldp trapping: to do… use the command… remarks enter system view system-view — enter ethernet interface view interface interface-type interface-number required enable lldp trap sending lldp notification remote-change enable required disabled by default quit to s...
Page 861
72-13 figure 72-4 network diagram for basic lldp configuration nms switch a med switch b eth1/0/2 eth1/0/1 eth1/0/1 configuration procedure 1) configure switch a. # enable lldp globally. System-view [switcha] lldp enable # enable lldp on ethernet 1/0/1 and ethernet 1/0/2 (you can skip this step beca...
Page 862
72-14 hold multiplier : 4 reinit delay : 2s transmit delay : 2s trap interval : 5s fast start times : 3 port 1 [ethernet1/0/1]: port status of lldp : enable admin status : rx_only trap flag : no roll time : 0s number of neighbors : 1 number of med neighbors : 1 number of cdp neighbors : 0 number of ...
Page 863
72-15 port status of lldp : enable admin status : rx_only trap flag : no roll time : 0s number of neighbors : 1 number of med neighbors : 1 number of cdp neighbors : 0 number of sent optional tlv : 0 number of received unknown tlv : 5 port 2 [ethernet1/0/2]: port status of lldp : enable admin status...
Page 864
72-16 [switcha-ethernet1/0/1] port link-type trunk [switcha-ethernet1/0/1] voice vlan 2 enable [switcha-ethernet1/0/1] quit [switcha] interface ethernet 1/0/2 [switcha-ethernet1/0/2] port link-type trunk [switcha-ethernet1/0/2] voice vlan 2 enable [switcha-ethernet1/0/2] quit 2) configure cdp-compat...
Page 865: Pki Configuration
73 pki configuration wh n configuring pki, go to thes e e sections for information you are interested in: z introduction to pki z pki configuration task list z displaying and maintaining pki pki configuration examples z z troubleshooting pki intro ers these topics: duction to pki this section cov z ...
Page 866
Cas are trusted by different users in a pki system, the cas will form a ca tree with the root ca at the top level. The root ca has a ca certificate signed by itself while each lower level ca has a ca certificate ed by the ca at the next higher level. Crl umbers of all revoked certificates and provid...
Page 867
Ca a ca is a trusted authority responsible for issuing and managing digital certificates. A ca issues certificates, specifies the validity periods of certificates, and revokes certificates as needed by publishing crls. Ra a registration authority (ra) is an extended part of a ca or an independent au...
Page 868
2) the ra reviews the identity of the entity and then sends the identity information and the public key with a digital signature to the ca. 3) the ca verifies the digital signature, approves the application, and issues a certificate. 4) the ra receives the certificate from the ca, sends it to the ld...
Page 869
The configuration of an entity dn must comply with the ca certificate issue policy. You need to determine, for example, which entity dn parameters are mandatory and which are optional. Otherwise, certificate request may be rejected. Follow these steps to configure an entity dn: to do… use the comman...
Page 870
Configuring a pki domain before requesting a pki certificate, an entity needs to be configured with some enrollment information, which is referred to as a pki domain. A pki domain is intended only for convenience of reference by other applications like ssl, and has only local significance. A pki dom...
Page 873
Z if a pki domain already has a local certificate, creating an rsa key pair will result in inconsistency between the key pair and the certificate. To generate a new rsa key pair, delete the local certificate and then issue the public-key local create command. Z a newly created key pair will overwrit...
Page 874
Z if a pki domain already has a ca certificate, you cannot retrieve another ca certificate for it. This is in order to avoid inconsistency between the certificate and registration information due to related configuration changes. To retrieve a new ca certificate, use the pki delete-certificate comma...
Page 875
To do… use the command… remarks enter pki domain view pki domain domain-name — disable crl checking crl check disable required enabled by default return to system view quit — retrieve the ca certificate refer to retrieving a certificate manually required verify the validity of the certificate pki va...
Page 876
Configuring an access control policy by configuring a certificate attribute-based access control policy, you can further control access to the server, providing additional security for the server. Follow these steps to configure a certificate attribute-based access control policy: to do… use the com...
Page 877
Pki configuration examples z the scep plug-in is required when you use the windows server as the ca. In this case, when configuring the pki domain, you need to use the certificate request from ra command to specify that the entity requests a certificate from an ra. Z the scep plug-in is not required...
Page 878
After configuring the basic attributes, you need to perform configuration on the jurisdiction configuration page of the ca server. This includes selecting the proper extension profiles, enabling the scep autovetting function, and adding the ip address list for scep autovetting. # configure the crl d...
Page 879
. Z apply for certificates # retrieve the ca certificate and save it locally. [switch] pki retrieval-certificate ca domain torsa retrieving ca/ra certificates. Please wait a while...... The trusted ca's finger print is: md5 fingerprint:ede9 0394 a273 b61a f1b3 0072 a0b1 f9ab sha1 fingerprint: 77f9 a...
Page 880
Modulus (1024 bit): 00d67d50 41046f6a 43610335 ca6c4b11 f8f89138 e4e905bd 43953ba2 623a54c0 ea3cb6e0 b04649ce c9cddd38 34015970 981e96d9 ff4f7b73 a5155649 e583ac61 d3a5c849 cbde350d 2a1926b7 0ae5ef5e d1d8b08a dbf16205 7c2a4011 05f11094 73eb0549 a65d9e74 0f2953f2 d4f0042f 19103439 3d4f9359 88fb59f3 8...
Page 881
Configuration procedure 1) configure the ca server z install the certificate server suites from the start menu, select control panel > add or remove programs, and then select add/remove windows components > certificate services and click next to begin the installation. Z install the scep plug-in as ...
Page 882
# specify the entity for certificate request as aaa. [switch-pki-domain-torsa] certificate request entity aaa z generate a local key pair using rsa [switch] public-key local create rsa the range of public key size is (512 ~ 2048). Notes: if the key modulus is greater than 512, it may take a few minu...
Page 883
Subject: cn=switch subject public key info: public key algorithm: rsaencryption rsa public key: (1024 bit) modulus (1024 bit): 00a6637a 8cdea1ac b2e04a59 f7f6a9fe 5aee52ae 14a392e4 e0e5d458 0d341113 0bf91e57 fa8c67ac 6ce8febb 5570178b 10242fdd d3947f5e 2da70bd9 1faf07e5 1d167ce1 fc20394f 476f5c08 c5...
Page 884
Z the network connection is not proper. For example, the network cable may be damaged or loose. Z no trusted ca is specified. Z the url of the registration server for certificate request is not correct or not configured. Z no authority is specified for certificate request. Z the system clock of the ...
Page 885
Z the crl distribution url is not configured. Z the ldap server version is wrong. Solution z make sure that the network connection is physically proper. Z retrieve a ca certificate. Z specify the ip address of the ldap server. Z specify the crl distribution url. Z re-configure the ldap version. 73-2...
Page 886: Ssl Configuration
74 ssl configuration wh n configuring ssl, go to thes e e sections for information you are interested in: z ssl overview z ssl configuration task list displaying and maintaining ssl z ting ssl z troubleshoo ssl ecure connection service for tcp-based application layer protocols, for example, http pro...
Page 887
Ssl protocol stack as shown in figure 74-2 , the ssl protocol consists of two layers of protocols: the ssl record protocol at the lower layer and the ssl handshake protocol, change cipher spec protocol, and alert protocol at the upper layer. Figure 74-2 ssl protocol stack z ssl handshake protocol: a...
Page 888
Configuration prerequisites when configuring an ssl server policy, you need to specify the pki domain to be used for obtaining the server side certificate. Therefore, before configuring an ssl server policy, you must configure a pki domain. Configuration procedure follow these steps to configure an ...
Page 889
Z if you enable client authentication here, you must request a local certificate for the client. Z currently, ssl mainly comes in these versions: ssl 2.0, ssl 3.0, and tls 1.0, where tls 1.0 corresponds to ssl 3.1. When the device acts as an ssl server, it can communicate with clients running ssl 3....
Page 890
[switch-pki-entity-en] quit # create a pki domain and configure it. [switch] pki domain 1 [switch-pki-domain-1] ca identifier ca1 [switch-pki-domain-1] certificate request url http://10.1.2.2/certsrv/mscep/mscep.Dll [switch-pki-domain-1] certificate request from ra [switch-pki-domain-1] certificate ...
Page 891
# configure the system to strip domain name off a user name before transmitting the user name to the radius server. [sysname-radius-radius1] user-name-format without-domain [sysname-radius-radius1] quit # create isp domain aabbcc.Net for web authentication users and enter the domain view. [sysname] ...
Page 893
Z if the ssl server is configured to authenticate the client, but the certificate of the ssl client does not exist or cannot be trusted, request and install a certificate for the client. 2) you can use the display ssl server-policy command to view the cipher suite used by the ssl server policy. If t...
Page 894: Https Configuration
75 https configuration wh n configuring https, go to thes e e sections for information you are interested in: z https overview z https configuration task list z associating the https service with an ssl server policy z enabling the https service z associating the https service with a certificate att...
Page 895
Associating the https service with an ssl server policy you need to associate the https service with a created ssl server policy before enabling the https service. Follow these steps to associate the https service with an ssl server policy: to do… use the command… remarks enter system view system-vi...
Page 896
Associating the https service with a certificate attribute access control policy associating the https service with a configured certificate access control policy helps control the access right of the client, thus providing the device with enhanced security. Follow these steps to associate the https...
Page 897
Https configuration example network requirements z host acts as the https client and device acts as the https server. Z host accesses device through web to control device. Z ca (certificate authority) issues certificate to device. The common name of ca is new-ca. In this configuration example, windo...
Page 898
[device] pki retrieval-certificate ca domain 1 # apply for a local certificate. [device] pki request-certificate domain 1 2) configure an ssl server policy associated with the https service # configure an ssl server policy. [device] ssl server-policy myssl [device-ssl-server-policy-myssl] pki-domain...