- DL manuals
- Cabletron Systems
- Switch
- CyberSWITCH CSX150
- User Manual
Cabletron Systems CyberSWITCH CSX150 User Manual
Summary of CyberSWITCH CSX150
Page 1
S mall o ffice r emote a ccess s witch u ser ’ s g uide release 7.2 cabletron systems (603) 332-9400 phone (603) 337-3075 fax support@ctron.Com.
Page 2
User’s guide 2 cyberswitch notice you may post this document on a network server for public use as long as no modifications are made to the document. Cabletron systems reserves the right to make changes in specifications and other information contained in this document without prior notice. The read...
Page 3
Small office remote access switch 3 trademarks cabletron systems, cyberswitch, mmac-plus, smartswitch, spectrum, and securefast virtual remote access manager are trademarks of cabletron systems, inc. All other product names mentioned in this manual are trademarks or registered trademarks of their re...
Page 4
User’s guide 4 cyberswitch warning : changes or modifications made to this device which are not expressly approved by the party responsible for compliance could void the user’s authority to operate the equipment. Doc notice this digital apparatus does not exceed the class a limits for radio noise em...
Page 5
Small office remote access switch 5 contents using this guide 22 documentation set 23 guide conventions 24 s ystem o verview 25 the cyberswitch 26 the cyberswitch network 26 unique system features 27 interoperability overview 29 interoperability protocols 29 interoperability devices 30 security over...
Page 6
User’s guide 6 cyberswitch ordering bri isdn lines using provisioning settings 44 provisioning settings for at&t 5ess switches 45 at&t 5ess ni-1 service 45 at&t 5ess custom point-to-point service 46 provision settings for northern telecom dms-100 switches 46 northern telecom dms100 ni-1 service 47 n...
Page 7
Small office remote access switch 7 configuring resources and lines 69 overview 69 resources 69 configuring resources 69 resource configuration elements 71 resource background information 71 lines 72 configuring lines 72 configuring changes for a commport resource 73 line configuration elements 74 l...
Page 8
User’s guide 8 cyberswitch routing information protocol (rip) option 111 enabling/disabling ip rip 111 ip rip configuration elements 112 ip rip background information 112 s ecurity 113 security overview 114 overview 114 security level 114 system options and information 115 device level databases 115...
Page 9
Small office remote access switch 9 telnet server tcp port number background information 134 emergency telnet server port number background information 135 configuring device level databases 136 overview 136 on-node device database 136 configuring an on-node device database 136 on-node device entrie...
Page 10
User’s guide 10 cyberswitch ace authentication server 166 configuring an ace authentication server 166 ace authentication server configuration elements 167 ace authentication server background information 168 configuring network login information 169 overview 169 network login general configuration ...
Page 11
Small office remote access switch 11 configuring advanced bridging 199 overview 199 bridge dial out 199 configuring the device list for bridge dial out 200 mac hardware filtering 201 enabling/disabling mac hardware filtering 201 mac hardware filtering background information 201 spanning tree protoco...
Page 12
User’s guide 12 cyberswitch ip filters 223 initiating the ip filter configuration 223 configuring packet types 224 configuring the common ip portion 225 configuring tcp 226 configuring udp 226 configuring icmp 227 configuring forwarding filters 228 configuring connection filters 229 using cfgedit 22...
Page 13
Small office remote access switch 13 ipx network interfaces 255 configuring ipx network interfaces 255 ipx network interface configuration elements 257 general ipx network interface configuration elements 257 rip ipx network interface configuration elements 257 sap ipx network interface configuratio...
Page 14
User’s guide 14 cyberswitch configuring snmp 280 configuring snmp 280 snmp configuration elements 282 snmp background information 283 configuring appletalk routing 287 appletalk routing option 287 enabling appletalk routing 287 appletalk routing option configuration element 288 appletalk routing bac...
Page 15
Small office remote access switch 15 bandwidth reservation 305 configuring bandwidth reservation 305 bandwidth reservation configuration elements 307 bandwidth reservation background information 308 semipermanent connections 308 configuring semipermanent connections 308 semipermanent connections con...
Page 16
User’s guide 16 cyberswitch t roubleshooting 334 system verification 335 verifying hardware resources are operational 335 verifying wan lines are available for use 336 verifying lan connection is operational 336 verifying bridge is initialized 337 verifying ip router is initialized 337 verifying a d...
Page 17
Small office remote access switch 17 verifying dhcp: proxy client 362 verifying dhcp proxy client initialization 362 verifying the proxy client is enabled 363 verifying the proxy client is operational 363 udp ports 363 ip address pool 364 verifying a semipermanent connection 364 verifying proxy arp ...
Page 18
User’s guide 18 cyberswitch call detail recording 393 compression 393 dhcp: relay agent 395 relay agent initialization 395 enabling the relay agent 395 relay agent operation 396 dhcp: proxy client 396 proxy client initialization 396 enabling the proxy client 396 proxy client operation 397 proxy arp ...
Page 19
Small office remote access switch 19 snmp 482 installation and configuration 483 usage instructions 483 telnet 484 installation and configuration 485 usage instructions 485 tftp 487 installation and configuration 487 usage instructions 488 remote installation with user2 489 system commands 491 overv...
Page 20
User’s guide 20 cyberswitch system statistics 537 overview 537 connectivity statistics 537 call restriction statistics 538 call statistics 538 throughput monitoring statistics 538 appletalk statistics 539 appletalk protocol statistics 539 appletalk data delivery protocol (ddp) statistics 539 appleta...
Page 21
Small office remote access switch 21 wan statistics 568 x.25 statistics 569 x.25 access related statistics 569 x.25 virtual circuit (vc) related statistics 571 routine maintenance 572 overview 572 installing/upgrading system software 572 executing configuration changes 572 configuration files 572 ma...
Page 22
U sing this g uide the user’s guide is divided into the following parts: s ystem o verview we begin with an overview of bridging, routing, and specific cyberswitch features. Next, we provide an overview for both the system software and hardware. S ystem i nstallation in this section of the user’s gu...
Page 23
Small office remote access switch 23 u sing this g uide documentation set a ppendices the user’s guide provides the following appendices: n etwork w orksheets these worksheets are provided to help you gather pertinent information for configuring your system. We recommend that you print copies of the...
Page 24
User’s guide 24 cyberswitch systems central database access for security authentication purposes. Instructions for obtaining this electronic document can be found in configuring off-node server information . If you have internet access, you may obtain this guide by following the steps outlined below...
Page 25
S ystem o verview we include the following chapters in the system overview segment of the user’s guide. • the cyberswitch provides the “big picture” view of a cyberswitch network. We include an overview of unique system features, interoperability, security, interfaces, system components, remote devi...
Page 26
T he c yber switch because of the strong personal computer presence in the business environment, a move to graphical user interfaces, and the need to make the best use of available resources, there is a growing demand for high speed lan access for remote devices. Pc users need to be part of a work- ...
Page 27
Small office remote access switch 27 t he c yber switch unique system features u nique s ystem f eatures the cyberswitch combines unique features that improve cost-effectiveness, reliability, and performance for wide area network connections to remote devices. These features include: • authenticatio...
Page 28
User’s guide 28 cyberswitch automatically adjust the number of network connections. Thus, your network costs will reflect the actual bandwidth being used. • filtering allows you to control the flow of frames through the network. Filtering becomes necessary if you need to restrict remote access or co...
Page 29
Small office remote access switch 29 t he c yber switch interoperability overview • protocol discrimination it is possible for multiple types of remote devices to use the same line. The system can determine the device type and the protocol encapsulation used by remote devices. • rs232 port: dual usa...
Page 30
User’s guide 30 cyberswitch the cyberswitch supports the following ppp protocols: • link control protocol (lcp) • multilink protocol (mlp) • authentication protocols challenge handshake authentication protocol (chap) password authentication protocol (pap) • network control protocols (ncp) internet p...
Page 31
Small office remote access switch 31 t he c yber switch security overview s ecurity o verview the system provides several options for validating remote devices and for managing network security. The security options available are dependent on the remote device type, type of access, and the level of ...
Page 32
User’s guide 32 cyberswitch s ystem c omponents the major components of the cyberswitch are: • system hardware consisting of a platform and an administration port provided by the platform. • four main categories of system software: the boot device gains control at power-up. It runs diagnostics, down...
Page 33
Small office remote access switch 33 t he c yber switch switches supported s witches s upported switch types supported by the cyberswitch’s basic rate and primary rate isdn adapters: switch support may vary from country to country. Use the following as a guideline: type of switch basic rate primary ...
Page 34
H ardware o verview the cyberswitchis an embedded communications platform. It uses a flash file system (instead of a hard disk) and a two-stage boot device to initialize the platform and download system software. System software is preconfigured to allow immediate connection via a local area network...
Page 35
Small office remote access switch 35 h ardware o verview system platforms s ystem p latforms thecyberswitchplatform consists of a single processor (the intel 386 ex host processor), system memory, and interface adapters. The front of theplatform has a series of led indicators. These indicators light...
Page 36
User’s guide 36 cyberswitch c yber switch s eries front & back panels: back panel as illustrated supports: • wide area network (wan) through 1 bri line, two connections • local area network (lan) through the 10base-t ethernet port or through the 10base2 ether- net port • analog devices (up to two) t...
Page 37
Small office remote access switch 37 h ardware o verview system platforms c yber switch b ack p anel the back panel provides connectors for wan and lan access, as well an rs232 port for an administration console. It also contains termination switches, a dc power input connector and a reset button. T...
Page 38
User’s guide 38 cyberswitch for informational purposes, here are the pin list and signal assignments for the 10base-t lan connector: note: the 10base-t connector and the wan connector are both rj45 connectors. However, they do have different electrical interfaces. Take care to keep these separate. P...
Page 39
S oftware o verview o verview the cyberswitch software provides: • system software for the cyberswitch, lan and wan interfaces, and administration functions • system files containing configuration and operational information this chapter provides an overview for each of the above software categories...
Page 40
User’s guide 40 cyberswitch node.Nei this configuration file contains node-specific information like resources, lines, cyberswitch operating mode and security options, along with the throughput monitor configuration information. If enabled, snmp configuration information is also in this file. Lan.Ne...
Page 41
Small office remote access switch 41 s oftware o verview system files the system stores the tables in ascii format files on the system disk. When the system writes system messages to disk, it stores them in the following location: directory: \log file name: rprt_log.Nn where “nn” is an integer that ...
Page 42
S ystem i nstallation we include the following chapters in thissegment of the user’s guide: • ordering isdn service provides guidelines for ordering isdn service in the united states. • hardware installation step-by-step instructions for installing hardware components. • accessing the cyberswitch pr...
Page 43
O rdering isdn s ervice (us o nly ) o verview this chapter was designed to be a guideline for ordering isdn service in the united states. If you are using ni-1 lines, try using ez-isdn codes to order bri service. If your service provider does not support ez-isdn codes, try using the ni-1 isdn orderi...
Page 44
User’s guide 44 cyberswitch f or d ual pots d evices if you have a system with a dual pots connection, use capability package m, plus the aco option. Capability package m includes alternate voice/circuit-switched data on two b channels. Data and voice capabilities include calling line id. The aco op...
Page 45
Small office remote access switch 45 o rdering isdn s ervice (us o nly ) ordering bri isdn lines using provisioning settings p rovisioning s ettings for at&t 5ess s witches the isdn services supported by at&t 5ess switches are as follows (in order of preference of usage): 1. Ni-1 2. At&t custom poin...
Page 46
User’s guide 46 cyberswitch at&t 5ess c ustom p oint - to -p oint s ervice note that some of the elements below are set per directory number. With custom point-to-point service, you will have two directory numbers. P rovision s ettings for n orthern t elecom dms-100 s witches the isdn services suppo...
Page 47
Small office remote access switch 47 o rdering isdn s ervice (us o nly ) ordering bri isdn lines using provisioning settings n orthern t elecom dms100 ni-1 s ervice note that you must set either ekts or aco to yes. You may not set both of them to yes. Northern telecom dms100 ni-1 service provisionin...
Page 48
User’s guide 48 cyberswitch n orthern t elecom dms100 c ustom s ervice note that you must set either ekts or aco to yes. You may not set both of them to yes. Northern telecom dms100 custom service provisioning element setting signaling functional pvc 1 tei assignment dynamic maxkeys 3 is preferable ...
Page 49
H ardware i nstallation p re -i nstallation r equirements before you begin the installation process, be sure to: • choose a suitable setup location make sure the location is dry, ventilated, dust free, static free, and free from corrosive chemicals • verify system power requirements the appropriate ...
Page 50
A ccessing the c yber switch o verview this chapter describes accessing your cyberswitch, which includes: • making proper connections • establishing an administration session • powering on the system • accessing release notes m aking c onnections there are a number of ways to make a connection to th...
Page 51
Small office remote access switch 51 a ccessing the c yber switch making connections using the provided rs232 null modem cable, attach an administration console to the cyberswitch. The administration port is a 9-pin, male rs232 serial adapter as shown below: connect one end of a null modem cable to ...
Page 52
User’s guide 52 cyberswitch c hanging the b aud r ate the baud rate is changeable. The default rate performs well for configuration changes. A faster rate is useful, however, to download new software upgrades to your system. To change the baud rate through cfgedit: 1. Select physical resources from ...
Page 53
Small office remote access switch 53 a ccessing the c yber switch establishing an administration session e stablishing an a dministration s ession if a login prompt is displayed after the power-on initialization, the system software was preinstalled. Complete the login: 1. The login controls which c...
Page 54
User’s guide 54 cyberswitch 2. Turn on the administration console, and execute the communications program so that your terminal emulator accesses the rs232 port connected to the system. 3. During power-on initialization, the first stage boot (fsb) displays a brief inventory of the system. The fsb th...
Page 55
Small office remote access switch 55 a ccessing the c yber switch accessing the release notes the release notes on cd are located in the rel_note.Txt file. This file is a dos text file you can read on a dos machine. Insert the cd into the drive, change to the proper directory, and enter the followin...
Page 56
U pgrading s ystem s oftware o verview this chapter describes how to install system software onto the cyberswitch. Instructions are included for the following actions: • upgrading system software • changing defaults to secure system • returning configuration to factory defaults • accessing release n...
Page 57
Small office remote access switch 57 u pgrading s ystem s oftware upgrading software for system upgrade, you will need to follow one of the above-mentioned upgrade paths (\product name\country\protocol or access package). This path not only depends upon product, but also the isdn standard you will b...
Page 58
User’s guide 58 cyberswitch l ocal u pgrade of the o perational s oftware (osw) to locally upgrade the operational software (osw) of your system, follow these steps: 1. Change the cyberswitch system’s baud rate to be the fastest baud rate supported by your communications package (up to 115.2 kbps). ...
Page 59
Small office remote access switch 59 u pgrading s ystem s oftware upgrading software osw, , found in the flash file system. The osw has not been updated from this file due to insufficient flash file system space. Please delete unnecessary files from the system. It is possible that you will not have ...
Page 60
User’s guide 60 cyberswitch console messages during ssb upgrade: r emote u pgrade of the o perational s oftware (osw) to remotely upgrade the operational software, follow these steps: 1. From the pc/workstation, telnet to the cyberswitch and login as admin. 2. Verify that the system is ready to rece...
Page 61
Small office remote access switch 61 u pgrading s ystem s oftware change defaults to secure system 4. Using telnet, reboot the system by issuing thecommand: restart it should take approximately 3 minutes for the systemto restart and install the upgrade. 5. Login via telnet and type the ver command t...
Page 62
User’s guide 62 cyberswitch 3. Change the admin and guest system passwords. If your system was previously accessed by your distributor, the preconfigured password will be admin (in lower case). Change this password to secure your system. To make this change, enter the following command at the system...
Page 63
B asic c onfiguration we define basic configuration as the configuration needed by most users. Basic configuration will get your system up and running. Note that not all configuration steps in this part are required. For example, if you are only using bridging, you will have no need to complete the ...
Page 64
C onfiguration t ools o verview we provide the following configuration tools to set up and/or alter your configuration: • cfgedit, the configuration utility • manage mode, the dynamic management utility your cyberswitch is shipped with a default set of configuration files that are preinstalled. Thes...
Page 65
Small office remote access switch 65 c onfiguration t ools dynamic management as long as there is no other “change” session active (cfgedit or manage mode), access is granted, and the following menu is displayed: from this screen you will begin the configuration process. Refer to basic configuration...
Page 66
User’s guide 66 cyberswitch once manage mode is entered, the prompt changes from [system name]> to [system name]: manage> . While operating in manage mode, only dynamic management commands are available. All other system commands are ignored until you exit manage mode. The key sequence will terminat...
Page 67
Small office remote access switch 67 c onfiguration t ools default configuration d efault c onfiguration your cyberswitch is shipped with a default set of configuration files that are preinstalled. These configuration files provide basic functions which will allow you to perform initial installation...
Page 68
User’s guide 68 cyberswitch u sing the c onfiguration c hapters the configuration chapters follow a basic format for explaining the configuration process of each system feature. The format is: 1. A brief outline of the configuration procedure using cfgedit (if applicable). Note: in this guide we hav...
Page 69
C onfiguring r esources and l ines o verview resource refers to the computer resources that are part of the cyberswitch. A wan resource is the physical interface for the attachment of lines (i.E., connections) to your system. Lines are communication facilities from the carriers. These lines directly...
Page 70
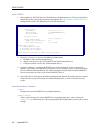
User’s guide 70 cyberswitch united states : for the u.S. Resource configuration, switch type is configurable, but ethernet resource or commport is not. Select resources to display a screen similar to the following: to configure a different switch type, first select (1) to change the basic rate resou...
Page 71
Small office remote access switch 71 c onfiguring r esources and l ines resources u sing m anage m ode c ommands resource displays the current resource configuration. R esource c onfiguration e lements r esource t ype the type of adapter (resource) that plug into the system. Wan adapters are the phy...
Page 72
User’s guide 72 cyberswitch internal asynchronous usage discriminator (aud), which monitors the data stream. The aud determines if this is to be a ppp connection, or a remote console connection. This determination is made within a configurable time frame: • if the aud detects ppp lcp frames, it conn...
Page 73
Small office remote access switch 73 c onfiguring r esources and l ines lines 5. Add the necessary data links. A. Select automatic tei negotiation unless this is a point-to-point ntt line. B. If you need to assign a tei negotiation value, the default value of 0 is normally correct. C. Only if you pl...
Page 74
User’s guide 74 cyberswitch datalink add allows you to add a data link. The following sample screen shows how a data link is added. Datalink change changes an existing data link. Datalink delete deletes an existing data link. Ampconf allows you to change the amp port configuration. L ine c onfigurat...
Page 75
Small office remote access switch 75 c onfiguring r esources and l ines lines c all s creening m ethods if you select a line interface type of point-multipoint, choose one of the following call screening methods: none, subaddress, or telephone number. The paragraphs below define each method. 1. None...
Page 76
User’s guide 76 cyberswitch enter the number of digits to verify (starting at the right-most digit), so that when the system receives a phone call it can determine on which bearer to accept the phone call. The maximum number of digits should be 7, which is the default value in most cases. S ervice p...
Page 77
Small office remote access switch 77 c onfiguring r esources and l ines lines d igits v erified the number of digits to verify (starting at the rightmost digit), so that when the system receives a phone call it can determine on which bearer to accept the phone call. The maximum number of digits shou...
Page 78
User’s guide 78 cyberswitch s ubaddresses c onfiguring a s ubaddress u sing cfgedit 1. To configure a subaddress, select isdn subaddress from the physical resources menu. 2. Enter the subaddress. The subaddress is supplied by your carrier service. S ubaddress c onfiguration e lements s ubaddress the...
Page 79
Small office remote access switch 79 c onfiguring r esources and l ines pots option 2. Select pots from the physical resource menu. 3. Select lines from the pots menu. 4. Press 1 to add a pots line. 5. Select the jack id from the list of available jacks. 6. Optional: enter the primary phone number o...
Page 80
User’s guide 80 cyberswitch pots c onfiguration e lements e ncoding s tandard the encoding standard is the type of standard for tone feeding and ring feed. This should be set properly on the switchtype. Only change the value of the encoding standard if you are having difficulties. J ack i d the id n...
Page 81
C onfiguring b asic b ridging o verview this chapter provides information for configuring basic bridging features. Basic bridging configuration includes: • enabling/disabling bridging a separate chapter, configuring advanced bridging , provides information for configuring advanced bridging features....
Page 82
User’s guide 82 cyberswitch mac l ayer b ridging b ackground i nformation you are given the option of either enabling or disabling the mac layer bridging feature. When bridging is enabled, the system bridges data packets to the proper destination, regardless of the network protocols being used. The ...
Page 83
C onfiguring b asic ip r outing o verview this chapter provides information for configuring basic ip routing features. Basic ip routing configuration includes: • enabling/disabling the internet protocol (ip) when you enable this option, the system operates as an ip router. If you also enable bridgin...
Page 84
User’s guide 84 cyberswitch ip o ption c onfiguration e lements ip o perational s tatus you can enable or disable the internet protocol (ip) option. The default is disabled. Ip b ackground i nformation when ip is enabled, the system acts as a router, routing ip datagrams based on ip address informat...
Page 85
Small office remote access switch 85 c onfiguring b asic ip r outing ip operating mode b. If you select the ip host operating mode, an abbreviated ip configuration is displayed: notes: static arp entries, isolated mode, static route lookup via radius, and ip address pool capabilities are not availab...
Page 86
User’s guide 86 cyberswitch off-node authentication servers are available when ip is enabled regardless of the operating mode. With ip host mode, all traffic is considered bridge traffic, so no ip-specific off-node server lookups are performed. These include: • ip lookup by a next hop ip address or ...
Page 87
Small office remote access switch 87 c onfiguring b asic ip r outing ip network interfaces n. Ip rip v2 authentication key (required only if the ip rip v2 authentication control has been configured with a value other than “no authentication” note: with the secondary ip addressing feature, you may ad...
Page 88
User’s guide 88 cyberswitch if ip rip is enabled, enter the following additional information: h. Ip rip send control i. Ip rip respond control j. Ip rip receive control k. Ip rip v2 authentication control l. Ip rip v2 authentication key (required only if the ip rip v2 authentication control has been...
Page 89
Small office remote access switch 89 c onfiguring b asic ip r outing ip network interfaces s ubnet m ask the subnet mask value (the number of significant bits for the subnet mask) associated with the ip address specified for this interface. The subnet mask is specified by entering the number of cont...
Page 90
User’s guide 90 cyberswitch entered for the interface. For example, if the ip address of the interface is 199.120.211.98, the portion of the menu displaying the available transmit broadcast addresses would appear as: in almost all cases, the default transmit address is used (1). The only time any of...
Page 91
Small office remote access switch 91 c onfiguring b asic ip r outing ip network interfaces ip rip s end c ontrol if ip rip is enabled for a specific interface (lan, wan rlan, and/or numbered wan interfaces), an ip rip send control must be selected. This element controls how ip rip update messages ar...
Page 92
User’s guide 92 cyberswitch the following table provides the possible choices for ip rip respond control. *the default switch. Ip rip r eceive c ontrol if ip rip is enabled for a specific interface, then this element is required. This controls which version of ip rip updates are to be accepted. The ...
Page 93
Small office remote access switch 93 c onfiguring b asic ip r outing ip network interfaces the following table provides the possible choices for ip rip v2 authentication control * this is the default switch. Ip rip v 2 a uthentication k ey if ip rip is enabled for a specific interface, this key is r...
Page 94
User’s guide 94 cyberswitch an ip host device has only one network interface that it uses for data transfer. This network interface is assigned an ip address and belongs to one subnet. A remote ip host typically uses an isdn line for this network interface. All data is sent through this network inte...
Page 95
Small office remote access switch 95 c onfiguring b asic ip r outing ip network interfaces the wan ip network interface is used to define remote ip devices (hosts or routers) that require access to the central network. This network interface represents a different subnet than that connected to a lan...
Page 96
User’s guide 96 cyberswitch in example 1,we show three different types of network interfaces and the ip subnets that are used. It should be noted that even though the cyberswitch only has one physical connection to the wan, it has more than one logical connection. Also, each one of these logical int...
Page 97
Small office remote access switch 97 c onfiguring b asic ip r outing ip network interfaces unnumbered interfaces (such as example 2), then the connecting subnet would not be required. In example 2, the wan unnumbered interface is used to eliminate an unnecessary ip subnet. The rlan interface is uniq...
Page 98
User’s guide 98 cyberswitch configuration. Different interface information must be configured depending on the type of interface used to propagate the ip rip information. Devices used to directly connect two lans use a lan interface for ip rip information propagation. The example network shown below...
Page 99
Small office remote access switch 99 c onfiguring b asic ip r outing ip network interfaces see illustration, example 1. Because site1 is the only cyberswitch that is connected to the logical network, it is reasonable for site1 to advertise the ip rip information on network 3 as subnetwork routes, me...
Page 100
User’s guide 100 cyberswitch for the wan interface to function properly with ip rip, additional wan interface information is configured. The additional information required involves selecting one of the following: disabling host routes propagation (needed for example 1), or enabling host routes prop...
Page 101
Small office remote access switch 101 c onfiguring b asic ip r outing ip network interfaces currently, ip rip is not supported across an unnumbered wan interface. For example, in the following network setup, site1 could not advertise ip rip information across the unnumbered wan ip interface to route...
Page 102
User’s guide 102 cyberswitch in the previous graphic, the wan network interface 1.1.1.1 on site1 is used to connect to a dedicated line and an isdn line. You need to specify to which remote device, either site2 or site3, site1 should exchange rip packets. If it is necessary to run the rip between si...
Page 103
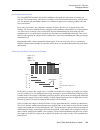
Small office remote access switch 103 c onfiguring b asic ip r outing ip network interfaces ip h ost o perating m ode and the ip n etwork i nterfaces only one network interface can be configured when the ip operating mode is host. The network interface configuration is not much different from the ot...
Page 104
User’s guide 104 cyberswitch with a remote device on a different subnet, the local device will arp for the remote host’s mac address. Since routers do not forward arp requests across subnets, arps sent for hosts which are not on the same physical network segment will go unanswered. The proxy arp fea...
Page 105
Small office remote access switch 105 c onfiguring b asic ip r outing static routes when a local host arps for a remote host, the cyberswitch (with proxy arp enabled) determines if it provides the best route to the destination. If it does, it will reply to the arp request with its own mac address. •...
Page 106
User’s guide 106 cyberswitch u sing m anage m ode c ommands iproute displays the current ip static routing configuration data. The meaning of each displayed field for a route entry is: d estination ip address for the destination network or host. S ubnet -m ask subnet mask value for the destination n...
Page 107
Small office remote access switch 107 c onfiguring b asic ip r outing static routes ip rip p ropagation c ontrol the ip rip propagation control determines how a static route is propagated via ip rip. The following table provides an explanation of how a ip rip propagation control flag is assigned to ...
Page 108
User’s guide 108 cyberswitch reachable directly and therefore no intermediate router will be used. The default metric value is 2. The range of metric values for static routes is from 0 to 15. You may manipulate the metric value to promote a certain default route, or to impede a default route from be...
Page 109
Small office remote access switch 109 c onfiguring b asic ip r outing static routes s tatic r oute b ackground i nformation you only need to configure static routing entries if you need to access a wan network that is not directly connected to the system, or if you need to access a lan network throu...
Page 110
User’s guide 110 cyberswitch d efault r outes c onfiguring d efault r outes the default route is a form of static route that is useful when there are a large number of networks that can be accessed through a gateway. However, care must be taken when specifying a default route. All ip datagrams with ...
Page 111
Small office remote access switch 111 c onfiguring b asic ip r outing routing information protocol (rip) option connection is over a wan. You may want to assign this route a high number of hops to limit toll charges, in case there is a local route that could be used. Ip rip p ropagation c ontrol thi...
Page 112
User’s guide 112 cyberswitch u sing m anage m ode c ommands iprip this command tells you if ip rip is currently enabled or disabled. Iprip off if ip rip is enabled, this command allows you to disable ip rip. Iprip on if ip rip is disabled, this command allows you to enable ip rip. Ip rip c onfigurat...
Page 113
S ecurity the cyberswitch provides a great variety of security options. These options include device level security, user level security, a combination of the two, or if preferred, no security. There are different ways to authenticate, as well as different locations (both local and remote) to store ...
Page 114
S ecurity o verview o verview security is an important issue to consider when you are setting up a network. The cyberswitch provides several security options, and this chapter describes the “big picture” of how these options work and interoperate. This information will better equip you to proceed wi...
Page 115
Small office remote access switch 115 s ecurity o verview system options and information multilevel security provides both user level security and device level security for local (on-node) database, radius, and sfvra. This provides added protection; first, a device will be authenticated, and then a ...
Page 116
User’s guide 116 cyberswitch these environments include an on-node database and a variety of off-node, central authentication databases. The on-node database contains a list of valid devices that can access the network resources connected to the cyberswitch. This list of valid devices is configured ...
Page 117
C onfiguring s ecurity l evel o verview the cyberswitch offers the following levels of network security: no security, device level security, user level security, or device and user level security. The network security level determines the type of security you want activated on your network. As the n...
Page 118
User’s guide 118 cyberswitch plan what level(s) of security you will use, and configure them now. You will later assign and configure authentication databases to the network security level you configure and to administration sessions. The table below identifies the types of authentication databases ...
Page 119
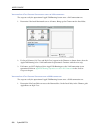
Small office remote access switch 119 c onfiguring s ecurity l evel no security n o s ecurity c onfiguring n o s ecurity u sing cfgedit 1. To begin the configuration of an on-node database or any of the security database options, start at the main menu and progress through the screens as shown below...
Page 120
User’s guide 120 cyberswitch d evice l evel s ecurity c onfiguring d evice l evel s ecurity u sing cfgedit 1. Select device level security from the security level menu. If you need guidance to find this menu, refer to the instructions provided in the no security configuration section. 2. Refer to th...
Page 121
Small office remote access switch 121 c onfiguring s ecurity l evel user level security o verview of d evice a uthentication p rocess when a remote device connects, the cyberswitch negotiates the required authentication. It then collects the information which is used to identify and authenticate the...
Page 122
User’s guide 122 cyberswitch the following sections provide information regarding authentication via securid cards, system requirements for user level security, and the authentication process with user level security. A uthentication u sing a s ecurity t oken c ard the cyberswitch supports interacti...
Page 123
Small office remote access switch 123 c onfiguring s ecurity l evel user level security s ystem r equirements when providing user level security for the cyberswitch, you must establish remote user-to- lan connectivity (like terminal servers). You may not establish lan-to-lan connectivity as routers ...
Page 124
User’s guide 124 cyberswitch a uthentication p rocess with u ser l evel s ecurity making a telnet connection in order to access user level security, you must first establish a telnet connection to the cyberswitch. Depending upon your application, the prompts or procedures may vary; however, the info...
Page 125
Small office remote access switch 125 c onfiguring s ecurity l evel device and user level security tacacs: with pinpad secureid card 1. Enter login id (remote machine). 2. Enter password onto securid card, which generates a dynamic password. 3. Enter dynamic password onto remote machine’s password p...
Page 126
User’s guide 126 cyberswitch d evice and u ser l evel b ackground i nformation multi-level security (device and user level) provides you with increased security options for your network. This feature supports device level security for all remote devices. User-level authentication can be performed on...
Page 127
C onfiguring s ystem o ptions and i nformation o verview system options include security options for remote devices. The security required for the authentication of each device will depend on the information you have entered for that device. System information includes a system name, system password...
Page 128
User’s guide 128 cyberswitch notes: it is not necessary to disable a security option, even if you are not using the option. The security required for the authentication of each device will depend on the information you have entered for that device. If, for some reason, you wish to disable an option,...
Page 129
Small office remote access switch 129 c onfiguring s ystem o ptions and i nformation system options note: if a system is brought on line with a device that has a required calling line id that is a duplicate of another device’s calling line id, and no other type of authentication is used, a warning m...
Page 130
User’s guide 130 cyberswitch the above process applies to the system’s authentication of the remote device. It is also possible that the remote device may wish to authenticate the system itself, a desire that is also negotiated during the lcp initialization of the link. Enabling chap via configurati...
Page 131
Small office remote access switch 131 c onfiguring s ystem o ptions and i nformation system information the following table summarizes the identifying and authenticating information used by each remote device type to connect to the system: s ystem i nformation c onfiguring s ystem i nformation u sin...
Page 132
User’s guide 132 cyberswitch s ystem p assword the system password is a user-defined password that is only required if there are remote devices on the network that require this information for system validation. This is passed in the password field during pap negotiation. This password can be from 1...
Page 133
Small office remote access switch 133 c onfiguring s ystem o ptions and i nformation administrative session 4. You may specify an authentication database location for administrative sessions that is different from the user authentication database location. Note: if you select radius, tacacs, or ace,...
Page 134
User’s guide 134 cyberswitch t imeout v alue allows you to terminate login sessions after the configured “time-out value” length in time. If “0” is entered, the value will be disabled. The time-out will be enabled by entering a number greater than 0. The range is from 0 to 1,440 minutes. N umber of ...
Page 135
Small office remote access switch 135 c onfiguring s ystem o ptions and i nformation administrative session e mergency t elnet s erver p ort n umber b ackground i nformation there are some telnet client programs that do not clear telnet connections when terminating telnet sessions. Since they do not...
Page 136
C onfiguring d evice l evel d atabases o verview devicelevel securityis an authentication process between internetworking devices, in which authentication takes place automatically. Both bridges and routers support this form of security.Devicelevel security is available to the network locally throug...
Page 137
Small office remote access switch 137 c onfiguring d evice l evel d atabases on-node device entries 2. Select option (1) on-node device database from the device level databases menu. The following screen will be displayed. Follow the on-screen instructions to enable the on-node database device: o n ...
Page 138
User’s guide 138 cyberswitch 4. The device table menu will then be displayed similar to the example screen shown below: we suggest that you first enter the information pertaining to the device’s access type(s). Access types include: isdn (which also includes configuration elements for devices connec...
Page 139
Small office remote access switch 139 c onfiguring d evice l evel d atabases on-node device entries 6. For frame relay devices: note: you must first configure the frame relay access. Instructions for configuring the access is found in the frame relay accesses section of the configuring alternate acc...
Page 140
User’s guide 140 cyberswitch if you select pvc, the list of available pvcs are displayed. The lcn of the selected pvc and the x.25 access name are stored in the device table to bind the device to a particular virtual circuit configuration: if you select svc, you must enter the x.121 address of the r...
Page 141
Small office remote access switch 141 c onfiguring d evice l evel d atabases on-node device entries for ppp, the ability to enable/disable outbound authentication (selection 3) is available. However, it is generally not necessary to enable outbound authentications on a point-to-point line. If the de...
Page 142
User’s guide 142 cyberswitch a. Enable or disable ipx routing. B. If you enable ipx routing and want dial-out capabilities to this device, enable the make calls feature. C. If you enable ipx routing, you may enable or disable ipxwan protocol. D. If you enable ipx routing, select ipx routing protocol...
Page 143
Small office remote access switch 143 c onfiguring d evice l evel d atabases on-node device entries for ip remote lan networks, you must explicitly configure the ip (sub)network number. For ipx remote lan networks, you may configure the ipx external network number, or you may leave the value at none...
Page 144
User’s guide 144 cyberswitch device change allows you to change information for a specific device entry. The current device table will be displayed. Enter the device id or device name of the entry you wish to change. Note that the device name is case sensitive. Step through the configuration informa...
Page 145
Small office remote access switch 145 c onfiguring d evice l evel d atabases on-node device entries data to begin to flow at greater rates without waiting for the throughput monitor to detect an overload condition. Calls will be made until an additional call would exceed the configured value. The va...
Page 146
User’s guide 146 cyberswitch p rofile n ame the device profile identifies which line or lines are reserved for a particular profile, which in turn are reserved for a particular device(s). The feature that uses this configuration element, bandwidth reservation , is described in detail, in the configu...
Page 147
Small office remote access switch 147 c onfiguring d evice l evel d atabases on-node device entries information, system secret. As opposed to a password, a chap secret is not sent across the link, and therefore is not susceptible to interception. Instead, a calculation is done on the packets transmi...
Page 148
User’s guide 148 cyberswitch c alling l ine i dentifier (clid) applicable to isdn connections only, and only when the clid option is enabled. You can specify eight clids for each device entry. Each clid for a given device must be unique. This is the telephone number of the calling party that is conn...
Page 149
Small office remote access switch 149 c onfiguring d evice l evel d atabases on-node device entries ipx routing protocol indicates the protocol the remote device will be using to communicate with the csx system: • none • rip/sap • triggered rip/sap wan p eer t ype specifies an active wan peer (recei...
Page 150
User’s guide 150 cyberswitch b ridge i nformation c onfiguration e lements ip (s ub ) n etwork n umber if the cyberswitch uses an ip rlan interface to connect to a remote bridge, you must provide this information. This address associates the bridge with the ip network to which it connects. Enter thi...
Page 151
Small office remote access switch 151 c onfiguring d evice l evel d atabases on-node device entries pots i nformation p ots p riority there are three different selections available for pots priority. They are: • preemption of 2nd b-channel by pots appropriate when both b-channels are active to the d...
Page 152
User’s guide 152 cyberswitch o n - node d evice d atabase s ecurity r equirements the following sections provide the on-node device table configuration requirements for possible security option configurations for each category of remote device. Categories are defined by the operating mode (bridging ...
Page 153
Small office remote access switch 153 c onfiguring d evice l evel d atabases on-node device entries the following table identifies the configuration requirements for possible security options for ip routing with bridge devices. *conditionally required means you must specify at least one of either th...
Page 154
User’s guide 154 cyberswitch the following table identifies the configuration requirements for possible security options for ppp ip devices. *required: an ip address is required if the remote device does not support ip address negotiation. When the remote device does support ip address negotiation, ...
Page 155
Small office remote access switch 155 c onfiguring d evice l evel d atabases on-node device entries ip routing with ppp bridge devices (using bcp) to allow devices to connect to the cyberswitch using ip routing through a ppp bridge device, you must configure a rlan ip network interface. Ip routing m...
Page 156
User’s guide 156 cyberswitch o ff - node d evice d atabase l ocation c onfiguring o ff - node d evice d atabase l ocation u sing cfgedit 1. Select off-node device database location from the device level databases menu. If you need guidance to find this menu, refer to the instructions provided in the...
Page 157
C onfiguring u ser l evel d atabases o verview userlevel security is an authentication process between a specific user and a device. The authentication process is interactive; users connect to a terminal server and need to interact with it in order to communicate with other devices beyond the server...
Page 158
User’s guide 158 cyberswitch u ser l evel a uthentication d atabase l ocation c onfiguration e lements d atabase l ocation the database location for user level security. Choices are: radius server, tacacs server, or ace server. D atabase t elnet p ort n umber you must also specify the telnet port nu...
Page 159
C onfiguring o ff - node s erver i nformation o verview you can configure both local device entries and remote authentication databases for device authentication. When a device needs to be authenticated, the cyberswitch will first look the device up locally, and, if there is no device entry, will th...
Page 160
User’s guide 160 cyberswitch vra m anager a uthentication s erver c onfiguring vra m anager a uthentication s erver notes: in order for the cyberswitch to reference vra manager for device authentication, the following configuration steps must first be completed: • ip routing must be enabled. If you ...
Page 161
Small office remote access switch 161 c onfiguring o ff - node s erver i nformation radius authentication server vra m anager a uthentication s erver c onfiguration e lements tcp p ort n umber the tcp port number used by the vra manager. Note that you can assign a device-defined port number, but tha...
Page 162
User’s guide 162 cyberswitch u sing cfgedit 1. Select option (2), radius from the off-node server information menu. If you need guidance to find this menu, refer to the instructions provided in the vra manager authentication server configuration section. The following screen will be displayed: 2. Se...
Page 163
Small office remote access switch 163 c onfiguring o ff - node s erver i nformation radius authentication server radius a uthentication s erver c onfiguration e lements ip a ddress the ip address in dotted decimal notation for the radius server. This information is required for the primary radius se...
Page 164
User’s guide 164 cyberswitch information from the secondary server if one is configured. The connection will be released if neither server responds to the access requests. The section titled on-node device table security requirements describes the device authentication information required for each ...
Page 165
Small office remote access switch 165 c onfiguring o ff - node s erver i nformation tacacs authentication server 3. Optional: configure a secondary tacacs server with selection (2). In the event that the primary server does not respond to system requests, the secondary server will be queried for dev...
Page 166
User’s guide 166 cyberswitch system will send an access request retry if the primary server does not respond. After the configured number of retries, the system will request authentication information from the secondary server if one is configured. The connection will be released if neither server r...
Page 167
Small office remote access switch 167 c onfiguring o ff - node s erver i nformation ace authentication server 4. Select miscellaneous information to finish the configuration. A. Specify the number of access request retries that the system will send to the authentication server. B. Specify the time b...
Page 168
User’s guide 168 cyberswitch n umber of a ccess r equest r etries the number of access request retries that the system will send to the ace server. The initial default value is 3. The acceptable range is from 0 to 32,767. T ime between a ccess r equest r etries the time between access request retrie...
Page 169
C onfiguring n etwork l ogin i nformation o verview the cyberswitch offers a number of configurable options to control the login process for this system and for off-node authentication servers. These options include: • general network login configuration • network login banners • login configuration...
Page 170
User’s guide 170 cyberswitch concerning item (9), authentication timeout, note the following recommendation: if using the security dynamics ace server, modify the timeout value to be greater than the change frequency value of the securid cards. Refer to the security dynamics documentation for more i...
Page 171
Small office remote access switch 171 c onfiguring n etwork l ogin i nformation network login banners n etwork l ogin b anners c onfiguring n etwork l ogin b anners u sing cfgedit 1. Select option (2), network login banners from the network login information menu. If you need guidance to find this m...
Page 172
User’s guide 172 cyberswitch l ogin c onfiguration s pecific to radius s erver c onfiguring radius s erver l ogin i nformation u sing cfgedit 1. Select option (3), login configuration specific to radius server from the network login information menu. If you need guidance to find this menu, refer to ...
Page 173
Small office remote access switch 173 c onfiguring n etwork l ogin i nformation login configuration specific to tacacs server u sing m anage m ode netlogin displays the current network login configuration data. After entering the netlogin command, you will be prompted for the type of login configura...
Page 174
User’s guide 174 cyberswitch 2. Selection (1) from the tacacs specific device login menu allows you to change the password control character: 3. Selection (2) from the tacacs specific device login menu allows you to customize the prompt order for device login. This prompt is particularly important, ...
Page 175
Small office remote access switch 175 c onfiguring n etwork l ogin i nformation login configuration specific to tacacs server netlogin change allows you to change the current network login configuration data. After entering the netlogin change command, you will be prompted for the type of login conf...
Page 176
A dvanced c onfiguration we define advanced configuration as the configuration you may use to fine tune your system, or to configure options that are not necessarily needed by the majority of users. For example, if you would like to configure an alternate access (an alternate to isdn access); this w...
Page 177
C onfiguring a lternate a ccesses o verview an access defines the connection details the cyberswitch uses to reach the network. The default access is isdn access, a switched-network access. Configurable accesses are required for dedicated network connections, for packet-switched network connections ...
Page 178
User’s guide 178 cyberswitch l ine p rotocol designates the type of line protocol that will be used on the dedicated connection. Ppp line protocol is the correct selection for most configurations. Hdlc protocol may work for devices that only support hdlc protocol. D evice n ame (o ptional ) optional...
Page 179
Small office remote access switch 179 c onfiguring a lternate a ccesses x.25 accesses x.25 a ccesses c onfiguring an x.25 a ccess note the following: • x.25 accesses are available only if you have purchased the additional software module for packet switched accesses. • to establish virtual circuits ...
Page 180
User’s guide 180 cyberswitch 7. Enter a list of bearers (a channel map).The range of channels is from 1 to 2. Separate bearer channels by commas, and/or list a range by using a dash (-). Lapb c onfiguration i nformation note: you will not be prompted for this information if you are using x.25 over a...
Page 181
Small office remote access switch 181 c onfiguring a lternate a ccesses x.25 accesses 3. Configure the x.25 reliability, windows, and acknowledgment facilities. A. Select the type of sequence numbers to be used for x.25: regular or extended. Extended sequence numbering allows for packets to be assig...
Page 182
User’s guide 182 cyberswitch p ermanent v irtual c ircuit i nformation note: svcs and pvcs are specified in the x.25 logical channel assignments section of the configuration. However, pvcs require additional configuration, which is done in this section. 1. Follow the onscreen instructions to begin t...
Page 183
Small office remote access switch 183 c onfiguring a lternate a ccesses x.25 accesses b earer c hannels a list of bearers (a channel map) that will be used on the line associated with this x.25 access. The range of channels is from 1 to 2. Separate bearer channels by commas, and/or list a range by u...
Page 184
User’s guide 184 cyberswitch x.25 a ccess c onfiguration e lements the x.25 access configuration elements are divided into seven different categories: • x.25 logical channel assignments • x.25 timer configuration • x.25 reliability, windows, and acknowledgment facilities • x.25 quality-of-service fa...
Page 185
Small office remote access switch 185 c onfiguring a lternate a ccesses x.25 accesses x.25 r eliability , w indows , and a cknowledgment x.25 s equence n umber r ange the type of sequence numbers to be used for x.25; regular or extended. Extended sequence numbering allows for packets to be assigned ...
Page 186
User’s guide 186 cyberswitch n onstandard d efault t ransmit w indow s ize the number of frames that a dte can send without receiving an acknowledgment. Using modulo 128, the dtes can send up to 127 frames without receiving an acknowledgment. Using modulo 8, the dtes can send up to 7 frames without ...
Page 187
Small office remote access switch 187 c onfiguring a lternate a ccesses x.25 accesses x.25 r estriction f acilities these facilities are used to place restrictions upon incoming and outgoing x.25 calls. B arring i ncoming c alls allows to you bar x.25 calls coming in to the system. The default confi...
Page 188
User’s guide 188 cyberswitch n onstandard d efault r eceive w indow s ize the number of frames that a dte can receive without receiving an acknowledgment. Using modulo 128, the dtes can send up to 127 frames without receiving an acknowledgment. Using modulo 8, the dtes can send up to 7 frames withou...
Page 189
Small office remote access switch 189 c onfiguring a lternate a ccesses x.25 accesses a virtual path, although it appears that a real circuit exits, in reality, the network routes the device’s information packets to the designated designation. Any given path may be shared by several devices. When th...
Page 190
User’s guide 190 cyberswitch c urrent x.25 r estrictions • x.25 virtual circuits must be two-way logical channels; one-way incoming and one-way out- going channels are not currently supported. • each system can have only one x.25 access. The x.25 access can use only one line. • a maximum of forty ei...
Page 191
Small office remote access switch 191 c onfiguring a lternate a ccesses frame relay accesses 5. Enter a list of bearers (a channel map). The range of channels is from 1 to 2. Separate bearer channels by commas, and/or list a range by using a dash (-). 6. Enter the maximum frame size supported by the...
Page 192
User’s guide 192 cyberswitch 7. Enter the rate measurement interval in msecs. Note: you must restart the cyberswitch in order to associate the pvc with a device. After all of the above pvc information is entered, an index number will be assigned to the associated dlci. This is the index number that ...
Page 193
Small office remote access switch 193 c onfiguring a lternate a ccesses frame relay accesses lmi indicates whether or not this frame relay access will support the local management interface (lmi). If this frame relay access supports lmi, lmi information can be displayed by entering the fr lmi comman...
Page 194
User’s guide 194 cyberswitch pvc l ine p rotocol the pvc line protocol determines which type of data encapsulation will be used on the pvc. The options are ppp point to point protocol or fr_ietf. Ppp allows ppp authentication for the associated device. Fr_ietf is a multiprotocol encapsulation for fr...
Page 195
Small office remote access switch 195 c onfiguring a lternate a ccesses frame relay accesses f rame r elay a ccess b ackground i nformation frame relay is a frame mode service in which data is switched on a per frame basis, as opposed to a circuit mode service that delivers packets on a call-by-call...
Page 196
User’s guide 196 cyberswitch configured in the device table. It will find the pvc and the line protocol that corresponds to the pvc name and change its pvc name to match the corresponding device name. Notes: vra manager is currently the only off-node device database supported by the cyberswitch for ...
Page 197
Small office remote access switch 197 c onfiguring a lternate a ccesses frame relay accesses -- the rate at which data frames may be sent into the network without incurring congestion. This is generally accepted as the end-to-end available bandwidth at which frame relay service devices may enjoy sus...
Page 198
User’s guide 198 cyberswitch however, under the above stated conditions, the network configuration shown below would not be allowed: switched connections can only be used as a backup to frame relay. As such, a switched connection would be made to a given node connected by a frame relay access only a...
Page 199
C onfiguring a dvanced b ridging o verview when bridging is enabled, optional advanced features are available. Optional bridging features include: • bridge dial out • enabling/disabling mac hardware filtering • spanning tree protocol • mode of operation • mode of hardware filtering • bridging filter...
Page 200
User’s guide 200 cyberswitch c onfiguring the d evice l ist for b ridge d ial o ut note: the configuring device level databases chapter contains the information needed to completely configure an on-node device entry. The following section provides instructions for entering on-node device information...
Page 201
Small office remote access switch 201 c onfiguring a dvanced b ridging mac hardware filtering 9. Enable bridging. 10. Enable make calls for bridge data. You must have already configured the device’s phone number (step 6) before the system allows you to enable this feature. Return to the current devi...
Page 202
User’s guide 202 cyberswitch s panning t ree p rotocol c onfiguring s panning t ree p rotocol u sing cfgedit 1. Select spanning tree from the bridging menu. 2. Enter the bridge age time. S panning t ree p rotocol c onfiguration e lements b ridge a ge t ime if you are using bridge dial out, you may w...
Page 203
Small office remote access switch 203 c onfiguring a dvanced b ridging mode of hardware filtering • if the packet matches no filter, the packet is forwarded. The specific forwarding action depends upon whether or not the destination is known. (see following descriptions.) no filter match - destinati...
Page 204
User’s guide 204 cyberswitch m anual m ode h ardware f iltering when the system software initializes in the manual mode, no bridge learning occurs. Instead, the bridge will skip the learning phase and move directly to the forwarding phase. The system will check to see if the incoming packet’s destin...
Page 205
Small office remote access switch 205 c onfiguring a dvanced b ridging bridge filters 5. Configure protocol filters. A. Select to add a protocol filter. B. Select a protocol definition id. C. Select a distribution list. 6. Configure packet data filters. A. Select to add a packet data filter. B. Ente...
Page 206
User’s guide 206 cyberswitch srcfilt change allows the current source address filter configuration to be changed. Srcfilt delete allows a source address filter to be deleted from the current configuration. Destination mac filter commands destfilt displays the current destination address filter confi...
Page 207
Small office remote access switch 207 c onfiguring a dvanced b ridging bridge filters hardware filter commands hwfilt displays the current hardware filter configuration data hwfilt add allows a hardware filter to be added to the current configuration. Hwfilt change allows the current hardware filter...
Page 208
User’s guide 208 cyberswitch d ata v alue hexadecimal number up to 80 characters in length that specifies the value used to determine if the packet matches the filter. The value field must be a subset of the mask field. That is, the value field logically “anded” with the mask field must be equal to ...
Page 209
Small office remote access switch 209 c onfiguring a dvanced b ridging bridge filters b ridge f ilters b ackground i nformation user-defined bridge filters allow you to filter unwanted traffic out of the network. The following table lists the four different types of bridge filters and the maximum nu...
Page 210
User’s guide 210 cyberswitch two of the more common protocols used today are: • the ip protocol id, which identifies dod internet protocol packets with ethernet type equal to hexadecimal 800, or 802.3 lsap equal to hexadecimal 6060. • the ipx protocol id, which identifies novell (old) netware ipx pa...
Page 211
Small office remote access switch 211 c onfiguring a dvanced b ridging bridge filters 3. Destination mac-address discard this filter allows you to discard mac frames addressed to the specified mac address. When the specified mac address appears in the destination address field of the mac frame, the ...
Page 212
User’s guide 212 cyberswitch the following charts summarize the filter actions available for unrestricted bridging: * device list may be the on-node device database, or it may be located on an off-node authentication server. Filter action distribution list result discard lan a packet matching this f...
Page 213
Small office remote access switch 213 c onfiguring a dvanced b ridging bridge filters restricted mode bridge filters 1. Source unicast-address forward this filter allows you to stipulate access privileges of a given device. When the specified unicast address appears in the source address field of a ...
Page 214
User’s guide 214 cyberswitch 5. Protocol protocol-id forward this filter allows you to restrict packets based on the ethernet protocol id field or the corresponding 802.3 lsap field. You can specify the protocol id that is to be forwarded. The filtering mechanism will determine if the packet is ethe...
Page 215
Small office remote access switch 215 c onfiguring a dvanced b ridging bridge filters the following chart summarizes the forward filter actions available for restricted bridging: it is possible to use a discard filter action to selectively discard packets that have been forwarded through the previou...
Page 216
User’s guide 216 cyberswitch d ial o ut u sing b ridge f ilters each type of bridge filter for each operating mode supports a different set of “forwarding actions.” your particular set up and device configuration will determine which type of filter and forwarding arrangement will be the most useful....
Page 217
Small office remote access switch 217 c onfiguring a dvanced b ridging bridge filters if you choose connect as a forwarding action, the system will connect and forward the packet to the specified device list only. This eliminates the need for the packet to be broadcast to all connections. After spec...
Page 218
User’s guide 218 cyberswitch your filter is now configured for this example. Remember, each type of filter for each operating mode supports a different set of “forwarding actions.” these are described in detail earlier in the bridge filters section. K nown c onnect l ist the known connect list is a ...
Page 219
Small office remote access switch 219 c onfiguring a dvanced b ridging known connect list k nown c onnect l ist c onfiguration e lements d evice n ame the name of a bridge device that has been preconfigured in the on-node device database section of the configuring device level databases chapter. Thi...
Page 220
C onfiguring a dvanced ip r outing o verview by default, ip routing is disabled when you first install your system software. After ip routing is enabled, there are optional advanced features available. Optional advanced ip routing features include: • static arp table entries arp (address resolution ...
Page 221
Small office remote access switch 221 c onfiguring a dvanced ip r outing static route lookup via radius i solated m ode c onfiguration e lements i solated m ode s tatus you may enable or disable the isolated mode option. I solated m ode b ackground i nformation when operating with isolated mode enab...
Page 222
User’s guide 222 cyberswitch server by enabling this feature. The systems will download necessary static routes information from the server when needed. Refer to this guide’s radius configuration information. The radius authentication server user’s guide (an electronic document) also provides inform...
Page 223
Small office remote access switch 223 c onfiguring a dvanced ip r outing ip filters when a ppp connection is established to the system, the system and the remote device exchange their ip addresses during the ipcp (ip control protocol) phase. If the remote device does not know its own ip address, the...
Page 224
User’s guide 224 cyberswitch upon selecting ip filter information, the following sub-menu is displayed: the configuration of each of the listed functions is described in the following discussion. U sing m anage m ode ipfilt this command displays the ip filter configuration screen from which you can ...
Page 225
Small office remote access switch 225 c onfiguring a dvanced ip r outing ip filters the screen identifies the common portion of the packet type, which includes the ip addresses and protocol information. To modify these values, refer to the following section entitled configuring the common ip portion...
Page 226
User’s guide 226 cyberswitch c onfiguring tcp if you have selected tcp as your ip protocol, a screen similar to the following is displayed. Note that the following tcp defaults constitute a wild card match for any tcp packet: 1. Select tcp source port. Note that the ports are specified in terms of a...
Page 227
Small office remote access switch 227 c onfiguring a dvanced ip r outing ip filters 3. If you have chosen the comparison operator of “range”, you will be prompted for upper-range and lower-range values. If you have chosen a comparison operator other than “range”, you will be prompted for a specific ...
Page 228
User’s guide 228 cyberswitch c onfiguring f orwarding f ilters the configuration of forwarding filters is a two-part process. First you must name the filter, and then you must create a list of conditions for the filter. To add a condition, you must name a previously-created packet type, and then nam...
Page 229
Small office remote access switch 229 c onfiguring a dvanced ip r outing ip filters c onfiguring c onnection f ilters the ip connection filter is used at the point when an ip packet attempts to establish an outbound connection in order to continue the forwarding process. Its configuration parallels ...
Page 230
User’s guide 230 cyberswitch c onfiguring e xception f ilter the ip exception filter is intended for temporary, special conditions within an existing forwarding filter. When enabled, it is logically appended to the beginning of each forwarding filter in effect. U sing cfgedit 1. Select exception fil...
Page 231
Small office remote access switch 231 c onfiguring a dvanced ip r outing ip filters m odifying the f inal c ondition for a f ilter to change the final condition for a filter, select change default condition (currently selection (5) on the conditions for filter menu. A pplying f ilters once you have ...
Page 232
User’s guide 232 cyberswitch 6. Select ip information. 7. Select either ip input filter or ip output filter. 8. Provide the filter name. Ip f ilters c onfiguration e lements the following elements are described in terms of the individual comparisons which make up the packet types. When an ip packet ...
Page 233
Small office remote access switch 233 c onfiguring a dvanced ip r outing ip filters eq equal to neq not equal to lt less than gt greater than range inclusive range = examples: eq 23: tcp port for the telnet protocol. Range 0 65535:any tcp port (wild card and default). Tcp c ontrol this element acces...
Page 234
User’s guide 234 cyberswitch f ilter c omposition the ip filtering mechanism is composed of three fundamental building blocks: packet types the criteria for describing an ip datagram’s contents: ip source and destination addresses, protocol (tcp, udp, etc.), protocol-specific fields (tcp port, etc.)...
Page 235
Small office remote access switch 235 c onfiguring a dvanced ip r outing ip filters • through the output network interface: applies the filter only to packets which are transmitted on a specific attached network (i.E. After the routing process has determined the next-hop net- work for the datagram)....
Page 236
User’s guide 236 cyberswitch because the packet types within the conditions specify both source and destination address information, global application may often be sufficient to filter ip traffic across the entire system. However, the input, output and user-based application points are defined in c...
Page 237
Small office remote access switch 237 c onfiguring a dvanced ip r outing ip filters common portion: protocol-specific portion tcp: protocol-specific portion, udp: protocol-specific portion, icmp: l imitations system performance will be affected by the number of packets, conditions and filters config...
Page 238
User’s guide 238 cyberswitch e xample of an ip f ilter c onfiguration this example provides a simple filtering scenario in which a corporate lan utilizes a cyberswitch to provide wan access to both dial-in devices as well as the global internet. A netserver resides on the lan to provide configuratio...
Page 239
Small office remote access switch 239 c onfiguring a dvanced ip r outing ip filters the corporate dial-in access is realized with a wan direct interface, using a pool of ip addresses from the corporate lan for dynamic assignment to the dial-in devices. These devices must first pass authentication pr...
Page 240
User’s guide 240 cyberswitch once the offsite maintenance is completed, the exception filter would be disabled. Configuration control over the exception filter is available both through cfgedit and manage mode (with manage mode being the most practical method due to its dynamic nature). Dhcp r elay ...
Page 241
Small office remote access switch 241 c onfiguring a dvanced ip r outing dhcp relay agent dhcp c onfiguration e lements dhcp/bootp r elay a gent e nable /d isable f lag a global flag that indicates whether the system is relaying the dhcp/bootp bootrequest messages or not. The relay agent is disabled...
Page 242
User’s guide 242 cyberswitch bridge to bridge environment as shown in the picture above, when a remote lan is connected with bridge devices, the dhcp server and clients communicate with each other as if they were on the same lan. This is one example configuration of how dhcp can be used to accomplis...
Page 243
Small office remote access switch 243 c onfiguring a dvanced ip r outing dhcp relay agent e xample dhcp c onfigurations below we have included a common dhcp scenario. It may help you configure your own dhcp feature. Ip router to ip router (with relay agents on both) this configuration is useful when...
Page 244
User’s guide 244 cyberswitch routers shown in the diagram above. Sample configurations for the objects in the above network diagram are as follows: note: the dhcp server must have a route specified to get back to the dhcp-enabled router ruby, or use alex as its default gateway. Configuration for ip ...
Page 245
Small office remote access switch 245 c onfiguring a dvanced ip r outing dhcp relay agent remote bridge to ip router (w/relay agent) this configuration is useful when requests by a dhcp client must be “bridged” to an ip router that is also a dhcp/bootp relay agent. Our equipment is shown in this exa...
Page 246
User’s guide 246 cyberswitch notes: the dhcp server must have a route specified to get back to the dhcp-enabled router alex, or use alex as its default gateway. When you are using a rlan interface, you are limited to one subnetwork. Configuration for ip router "alex" configuration for remote bridge ...
Page 247
Small office remote access switch 247 c onfiguring a dvanced ip r outing dhcp proxy client dhcp p roxy c lient c onfiguring the dhcp p roxy c lient in order to configure the dhcp proxy client, you must first enable the client, and then configure client information for a wan or a wan (direct host) ty...
Page 248
User’s guide 248 cyberswitch dhcp c onfiguration e lements dhcp p roxy c lient e nable /d isable f lag a global flag that indicates whether the dhcp proxy client feature is enabled or not. The proxy client is disabled by default. M aximum n umber of ip a ddresses refers to the maximum number of ip a...
Page 249
Small office remote access switch 249 c onfiguring a dvanced ip r outing dhcp proxy client the dhcp proxy client feature is not applicable for the cyberswitch running in ip host mode. Dhcp servers must support use of the broadcast bit in order to obtain ip addresses for wan (direct host) interfaces....
Page 250
User’s guide 250 cyberswitch configuration for ip router “chloe” system information: system name = chloe system password =pets security level = device level (on-node device database, pap security) bridging disabled ip enabled (router mode) i/f = lan (192.168.1.168); lan port 1 i/f = wan explicit (19...
Page 251
C onfiguring ipx o verview ipx protocol accepts data from remote devices and formats the data for transmission onto the network, and conversely, accepts data from the lan and formats it so it can be understood by remote devices. In short, ipx allows remote devices and their servers to communicate. T...
Page 252
User’s guide 252 cyberswitch c onfiguring ipx i nformation note: ipx is available only if you have purchased the additional software module for our ipx feature. To help you configure your ipx information, we have included an illustration of a sample network. As we explain the steps, we provide sampl...
Page 253
Small office remote access switch 253 c onfiguring ipx ipx routing option ipx r outing o ption e nabling /d isabling ipx note: the cyberswitch does not currently provide ipx data transfer over x.25 links. U sing cfgedit 1. Select options from the main menu. 2. Select ipx routing from the options men...
Page 254
User’s guide 254 cyberswitch ipx o ption b ackground i nformation the internetwork packet exchange (ipx) protocol is a datagram, connectionless protocol in the netware environment analogous to the internet protocol (ip) in the tcp/ip environment. With the help of routing information protocol (rip) a...
Page 255
Small office remote access switch 255 c onfiguring ipx ipx network interfaces ipx n etwork n umber b ackground i nformation novell netware networks use ipx external and internal network numbers. An ipx internal network number is a unique identification number assigned to a network server or router a...
Page 256
User’s guide 256 cyberswitch 9. If ipx rip has been enabled for the system, enter the following: a. Rip send control (do not respond or respond) b. Frequency (in seconds) of sending rip updates c. Rip receive control (do not respond or respond) d. Time (in seconds) to age rip entries e. Rip respond ...
Page 257
Small office remote access switch 257 c onfiguring ipx ipx network interfaces ipx n etwork i nterface c onfiguration e lements g eneral ipx n etwork i nterface c onfiguration e lements i nterface t ype when configuring an ipx network interface, this parameter specifies the type of network segment to...
Page 258
User’s guide 258 cyberswitch s end f requency specifies the frequency at which the system will transmit rip packets, if the send control parameter is set to send for this interface. This parameter is a decimal value specified in seconds from 1 to 300. The default value is 60 seconds. R eceive c ontr...
Page 259
Small office remote access switch 259 c onfiguring ipx ipx network interfaces ipx n etwork i nterface b ackground i nformation traditional routing products ask you to define the network interfaces to which the router is directly connected: lan i nterfaces lan network interfaces are fixed broadcast m...
Page 260
User’s guide 260 cyberswitch ipx r outing p rotocols c onfiguring ipx r outing p rotocols u sing cfgedit 1. Select routing protocols from the ipx menu. The following will be displayed: 2. To change the enable/disable status for any of the ipx protocols, simply enter the id number associated with the...
Page 261
Small office remote access switch 261 c onfiguring ipx ipx routing protocols rip/sap n umber of t able e ntries specifies the maximum number of routing entries which can be stored in the route or service table. You may select a number between 20 and 3072. The default value is 141 ipx r outing p roto...
Page 262
User’s guide 262 cyberswitch static services are configured locally on the system. Sap entries are learned from incoming sap packets. All services are stored, used internally and advertised to other routers. The same factors that affect the maximum number of routes stored also affect the maximum num...
Page 263
Small office remote access switch 263 c onfiguring ipx ipx static routes ipx s tatic r outes note: with the availability of triggered rip/sap ( page 274 ), the configuration of static routes is no longer necessary but still supported. Situations may arise in which a remote router does not support ou...
Page 264
User’s guide 264 cyberswitch u sing m anage m ode c ommands ipxroute displays the current ipx routes (both statically entered and "learned"). Ipxroute [add/change/delete] allows you to add/change/delete an ipx route. Ipx s tatic r outes c onfiguration e lements d estination n etwork the ipx network ...
Page 265
Small office remote access switch 265 c onfiguring ipx ipx netware static services ipx n et w are s tatic s ervices note: with the availability of triggered rip/sap ( page 274 ), the configuration of static services is no longer necessary but still supported. Situations may arise in which a remote r...
Page 266
User’s guide 266 cyberswitch ipx n et w are s tatic s ervices c onfiguration e lements s ervice n ame specifies the netware service name that is the target of this static service definition. This parameter is a 48 character netware service name. S ervice t ype indicates the type of netware service t...
Page 267
Small office remote access switch 267 c onfiguring ipx ipx spoofing ipx n et w are s tatic s ervices b ackground i nformation this ipx feature allows you to configure service servers that are on networks across the wan. The ipx netware static services configuration tells the system which servers are...
Page 268
User’s guide 268 cyberswitch b. Press 2 to select the system serialization packet handling level. The default values for all parameters will be displayed. Enter the id of any parameters you need to change. Follow the onscreen instructions for changing the default values. Return to the ipx spoofing m...
Page 269
Small office remote access switch 269 c onfiguring ipx ipx spoofing w atchdog p rotocol watchdog protocol is used by netware servers to detect “dead” clients. If no traffic has been seen by a server from an attached client for a configurable amount of time, the server sends a watchdog packet to the ...
Page 270
User’s guide 270 cyberswitch some of these packets are overloaded in that they are not just keep-alive packets but are control packets needed for the application to run successfully and hence have to be routed like regular spx data packets. If any netware application does not seem to work across wan...
Page 271
Small office remote access switch 271 c onfiguring ipx ipx isolated mode ipx t ype 20 p acket h andling c onfiguration e lements ipx t ype 20 p acket h andling s tatus you may enable or disable ipx type 20 packet wan forwarding. When it is enabled, you may specify devices that can use this feature. ...
Page 272
User’s guide 272 cyberswitch ipx i solated m ode b ackground i nformation when operating with isolated mode enabled, the cyberswitch does not relay ipx datagrams received from the wan to other ipx routers/hosts located on the wan. Ipx datagrams received from the wan will be discarded if they need to...
Page 273
Small office remote access switch 273 c onfiguring ipx ipx triggered rip/sap c onfiguring t riggered rip/sap g lobal t imers u sing cfgedit 1. Select triggered rip/sap from the ipx routing menu. 2. Select global triggered rip/sap timers. A menu similar to the following will be displayed: 3. Select t...
Page 274
User’s guide 274 cyberswitch o ver - subscription t imer over subscription is the situation in which there are more next-hop routers on the wan that need updates than there are channels available. When a wan circuit goes down, a delay (per the over- subscription timer) is incorporated in marking the...
Page 275
Small office remote access switch 275 c onfiguring ipx ipx-specific information for devices 4. Press 1 to add a device. 5. Enter the device’s name and press . You should provide isdn and authentication information first. 6. Select ipx. A screen similar to the following will be displayed: 7. Enable i...
Page 276
User’s guide 276 cyberswitch b. The screen includes default configuration values. If needed, make changes to the default values. C. Press to return to the ipx device spoofing menu. Press 2 to configure spx watchdog spoofing. The following menu will be displayed: d. The screen includes default config...
Page 277
Small office remote access switch 277 c onfiguring ipx ipx-specific information for devices r emote lan d evices remote lan devices are configured in a slightly different way than wan devices. Since the remote device is a bridge and not an ipx router, the ipx options for remote lan devices are confi...
Page 278
User’s guide 278 cyberswitch ipx c onfiguration e lements for d evices ipx r outing indicates that the remote device is an ipx router and that the system should route ipx datagrams to this device. The system will forward ipx datagrams to this device based on ipx network layer information if this par...
Page 279
Small office remote access switch 279 c onfiguring ipx ipx-specific information for devices b ridging defines the remote device as a bridge and not an ipx router. Since bridges operate at the mac layer, the system must provide mac layer emulation for remote bridge devices, while continuing to route ...
Page 280
C onfiguring snmp o verview a network management station (nms) is a device that contains snmp-specific software, giving it the ability to query snmpagents using various snmp commands. If you have purchased an nms (such as cabletron’s spectrum® management platform), you should enable and configure th...
Page 281
Small office remote access switch 281 c onfiguring snmp configuring snmp the steps to configure snmp are: 1. Enable ip routing if you have not already done so. 2. Select snmp from the options menu. 3. Follow the onscreen instructions to enable snmp. The following snmp menu will then be displayed: 4....
Page 282
User’s guide 282 cyberswitch u sing m anage m ode c ommands currently you cannot configure snmp using the manage mode, but the following command is available: snmp this manage mode command displays the current snmp configuration data. An example output screen is shown below: snmp c onfiguration e le...
Page 283
Small office remote access switch 283 c onfiguring snmp snmp background information ip a ddress the ip address assigned to the management station that should receive trap pdus. C ommunity n ame a list of configured community names will be displayed. Select the community name that should be inserted ...
Page 284
User’s guide 284 cyberswitch the snmp agent will process all snmp protocol data units (pdus) which are received at a lan port or which are received at a wan port. (a pdu contains both data and control (protocol) information that allows the two processes to coordinate their interactions. The snmp fea...
Page 285
Small office remote access switch 285 c onfiguring snmp snmp background information currently, each object in the above mib-2 groups can be retrieved via an snmp getrequest or getnextrequest pdu. However, only the snmpenableauthentraps object in the snmp group can be changed via the snmp setrequest ...
Page 286
User’s guide 286 cyberswitch • authtimeout trap an snmp agent will generate an authtimeout trap pdu anytime an off-node server times out. • cliddisconnect trap an snmp agent will generate an cliddisconnect trap pdu anytime there is a configuration problem with a device’s calling line id. • cdroutofb...
Page 287
C onfiguring a pple t alk r outing o verview the appletalk routing feature allows the cyberswitch to efficiently route appletalk data as opposed to bridging all data relating to the protocol. With the addition of the appletalk remote lan feature, the cyberswitch can be configured to be a router, bri...
Page 288
User’s guide 288 cyberswitch a pple t alk r outing o ption c onfiguration e lement a pple t alk o perational s tatus you can enable or disable the appletalk routing option. When appletalk routing is enabled, the cyberswitch acts as an appletalk router, routing appletalk datagrams based on appletalk ...
Page 289
Small office remote access switch 289 c onfiguring a pple t alk r outing appletalk ports 8. If you are configuring your system in the nondiscovery mode (you entered numbers other than 0 or 0-0 for the network range/number), complete the following: a. Enter either the suggested appletalk address or t...
Page 290
User’s guide 290 cyberswitch a pple t alk n etwork r ange /n umber the appletalk network range (for extended network) or the appletalk network number (for nonextended network) of the lan segment that the port is connected to. Specifying 0.0 (for extended) or 0 (for nonextended) places the port in di...
Page 291
Small office remote access switch 291 c onfiguring a pple t alk r outing appletalk ports t he z one c oncept a zone is a logical group of nodes on an internet, much like the concept of subnetting with the world of ip. Within the framework of phase 2 the logical assignment of zones is limited to 255 ...
Page 292
User’s guide 292 cyberswitch number/range configured for the remote lan port differs from the network number/range that is being broadcasted in rtmp packets by other remote routers, the port becomes unusable. Configuration in order to properly set up an appletalk remote lan, you must: • enable apple...
Page 293
Small office remote access switch 293 c onfiguring a pple t alk r outing appletalk capacities a pple t alk r outing s tatic r outes c onfiguration e lements a pple t alk n etwork t ype the appletalk network type used by the destination network of this static route. Type can be either extended networ...
Page 294
User’s guide 294 cyberswitch a pple t alk c apacities b ackground i nformation this option allows you to control the maximum number of table entries (routing and zone tables) for your network. A pple t alk i solated m ode c onfiguring the a pple t alk i solated m ode u sing cfgedit 1. Select isolate...
Page 295
C onfiguring c all c ontrol o verview the cyberswitch offers a number of configurable options to control how the system will make and accept calls. These options include: • configuring throughput monitor parameters • configuring call interval parameters • configuring monthly call charge parameters •...
Page 296
User’s guide 296 cyberswitch 3. Follow the onscreen instructions to keep the feature enabled. 4. Enter the sample rate in seconds. 5. Enter the overload trigger number. 6. Enter the overload window size. 7. Enter the overload percentage utilization. 8. Enter the underload trigger number. 9. Enter th...
Page 297
Small office remote access switch 297 c onfiguring c all c ontrol throughput monitor u nderload t rigger n umber the number of samples within the window that must be below the next lowest target capacity for the underload condition to occur. U nderload w indow s ize the number of sample periods (up ...
Page 298
User’s guide 298 cyberswitch the throughput monitor feature constantly monitors the use of the connections and looks for the following conditions: • the overload condition, which indicates that demand exceeds the current aggregate capacity of the wan connections. The system can add more bandwidth wh...
Page 299
Small office remote access switch 299 c onfiguring c all c ontrol throughput monitor i dle c ondition m onitoring the cyberswitch monitors for the idle condition when only one connection to another site remains. The system detects when there is no longer a need to maintain connectivity with the othe...
Page 300
User’s guide 300 cyberswitch the average throughput is 40% for the third sample rate period. This is less than the configured utilization, so out of the last 3 samples (a sliding window is in use), 1 out of 3 samples have throughput that is greater than the configured utilization. The overload condi...
Page 301
Small office remote access switch 301 c onfiguring c all c ontrol monthly call charge more than 3 call attempts within 2 seconds. This prevents certain model switches from being overloaded. In areas where these low capacity switches are not installed, calls can be made more frequently. Before the sy...
Page 302
User’s guide 302 cyberswitch c all r estrictions c onfiguring c all r estrictions note: certain restrictions apply to the use of call restrictions and semipermanent connections . Refer to the background information discussion. U sing cfgedit 1. Select call restrictions from the call control options ...
Page 303
Small office remote access switch 303 c onfiguring c all c ontrol call restrictions the following chart provides the numbers you should use to represent the am and pm hours of the hours calls are allowed: the following chart provides example entries for hours calls are allowed: m aximum c alls per d...
Page 304
User’s guide 304 cyberswitch c all m inutes per d ay the limit of number of call minutes per day. The default value is 240 call minutes per day. Call minutes will be calculated periodically while calls are active (not when a call is disconnected). Statistics will be kept to track the total number of...
Page 305
Small office remote access switch 305 c onfiguring c all c ontrol bandwidth reservation notes: it is important to note that the call restriction feature only applies to outbound calls from the system. When a condition occurs that triggers a warning to be written to the log, the message will be writt...
Page 306
User’s guide 306 cyberswitch the port number. This example shows that there is only one bri adapter, and it is installed in slot number one, and has four ports. There is a line for each port number. 4. Press 1 to add a device profile. 5. Enter a user-defined unique name to identify the profile. We w...
Page 307
Small office remote access switch 307 c onfiguring c all c ontrol bandwidth reservation 5. Under isdn information, enter the profile information. This is a profile name you configured in the previous section. Remember from the previous section that each configured profile reserves specific lines. By...
Page 308
User’s guide 308 cyberswitch b andwidth r eservation b ackground i nformation this feature allows a portion of the possible connections to always be available to specific devices for both inbound and outbound calls. To increase flexibility, this feature may be configured to either allow or prevent b...
Page 309
Small office remote access switch 309 c onfiguring c all c ontrol semipermanent connections 6. Determine if the cyberswitch should always retry a call. If yes, then configuration for the device is done, the device is entered into the semipermanent device list, and appears as shown below. If no, cont...
Page 310
User’s guide 310 cyberswitch s emipermanent c onnections c onfiguration e lements d evice n ame specify the device name (from the device list) that you wish to make a semipermanent connection. Once specified, the semipermanent feature will (at least) keep the initial data rate active to the specifie...
Page 311
Small office remote access switch 311 c onfiguring c all c ontrol semipermanent connections call restrictions you may wish to disable call restrictions when using semipermanent connections. Call restrictions are mainly intended for use in areas where “per minute” isdn tariffs are in place. Typically...
Page 312
User’s guide 312 cyberswitch vra m anager as a c all c ontrol m anager this feature allows you to use the virtual remote access (vra) manager for call control management only. This feature allows you to continue to use other authentication servers (e.G., radius, ace) yet still gain the benefits of v...
Page 313
Small office remote access switch 313 c onfiguring c all c ontrol vra manager as a call control manager a uthentication t imeout t imer this timer represents the amount of time the cyberswitch will wait for the authentication agent to handle a login attempt before timing out. If vra is enabled as ca...
Page 314
User’s guide 314 cyberswitch • user level security if you use user level security for authentication: configure devices on the vra manager as well. This will provide access to the following vra call control management features: call restrictions, maximum bandwidth, and grouping (in addition to the c...
Page 315
C onfiguring o ther a dvanced o ptions o verview this chapter provides information for configuring advanced system options that are not covered in the previous chapters. These options include: • configuring ppp • configuring default line protocol • configuring log options • configuring system compre...
Page 316
User’s guide 316 cyberswitch ppp c onfiguration e lements m ax t erminate the number of terminate-request packets sent without receiving a terminate-ack before assuming that the peer is unable to respond. M ax c onfigure the number of configure-request packets sent without receiving a valid configur...
Page 317
Small office remote access switch 317 c onfiguring o ther a dvanced o ptions ppp configuration l ink f ailure d etection s tatus you can enable or disable the link failure detection feature. If enabled, there will be a periodic transmission of echo-request frames, a maintenance type frame provided b...
Page 318
User’s guide 318 cyberswitch however, the ppp link exists on an end-to-end basis with the remote peer, a domain which exceeds that controlled by the signalling-type entities just cited. Thus, not every end-to-end failure will be detected. Some examples of such failures include: • an isdn peer’s d-ch...
Page 319
Small office remote access switch 319 c onfiguring o ther a dvanced o ptions default line protocol d efault l ine p rotocol the default values for this feature are adequate for most situations. Instructions are included for the rare instance that you need to alter the configuration. Note: this featu...
Page 320
User’s guide 320 cyberswitch l og o ptions log options allow you to direct log reports to a specific location. Reports an be directed to a local log file, or to a unix-style syslogs server. Currently, only call detail recording (cdr) reports can be directed to a specific location. C onfiguring l og ...
Page 321
Small office remote access switch 321 c onfiguring o ther a dvanced o ptions log options one version of unix to the next, the system allows you to set the entire priority value as an integer. This integer will be prepended to all messages sent to this syslog server. Note: you do not have to configur...
Page 322
User’s guide 322 cyberswitch files and devices depending upon its configuration. Refer to your unix system documentation for more information on syslogd. Each log message sent to a syslogd server has a priority tag associated with it. The priority tag is encoded as a combination: facility.Level. The...
Page 323
Small office remote access switch 323 c onfiguring o ther a dvanced o ptions log options .2, and so on up to .10. The file extension cycles through the values 1 through 10 with each write command, similar to the current report log file and status log file, so that the ten most recent versions of the...
Page 324
User’s guide 324 cyberswitch event report contents a cdr event triggers a report which can consist of one or more records. Each record corresponds to a line in the log file. This alleviates any constraints of having to fit a report in an 80 character string. Reports are sent to some sort of log devi...
Page 325
Small office remote access switch 325 c onfiguring o ther a dvanced o ptions log options d ata r ate this field indicates the data rate for a b channel. The possible values are 56 kb, 64 kb and 384 kb. D uration this field reflects the time that a connection is active; it is presented in hours, minu...
Page 326
User’s guide 326 cyberswitch disconnect event report contents on a disconnect event, records 1 through 4 are used. The event type is disconnect. The timestamp reflects the time that the decision to disconnect was made. The phone number displayed is the phone number in the connect report. The duratio...
Page 327
Small office remote access switch 327 c onfiguring o ther a dvanced o ptions compression options c ompression o ptions compression allows the cyberswitch to compress outgoing data and decompress incoming data. This allows user devices on the wan to initiate a connection to the system over the switch...
Page 328
User’s guide 328 cyberswitch compression enable/disable state based on this value when no value is delivered by the off-node database. You may later change a specific device’s enable/disable state. The per-device compression enable/disable state is only supported for connections using the ppp protoc...
Page 329
Small office remote access switch 329 c onfiguring o ther a dvanced o ptions compression options algorithm. The peer and remote compression algorithms must be synchronized, this is accomplished by negotiating compression at channel connect time. Once this has been accomplished compressed data can be...
Page 330
User’s guide 330 cyberswitch to operate, albeit without compression. An error message will be logged indicating an internal decompression failure. Compression is negotiated independently on inbound and outbound channels. It is possible to provide compression in one direction while not in the opposit...
Page 331
Small office remote access switch 331 c onfiguring o ther a dvanced o ptions tftp tftp c onfiguration e lements o perational s tatus of tftp f eature you can enable or disable the tftp feature. O perational s tatus of tftp c lient you can enable or disable the tftp client feature. The tftp client fu...
Page 332
User’s guide 332 cyberswitch when a device remotely access the tftp server, it doesn’t matter what level the device is logged in as. What matters is the device level that is configured for the server on the system that is being logged into. It is this file access level (or device login level) that c...
Page 333
Small office remote access switch 333 c onfiguring o ther a dvanced o ptions file attributes • “rw” is for read and write access • “n” is for no access rights for the corresponding file type the file types that fall under the headings shown above are as follows: file category file types included in ...
Page 334
T roubleshooting we include the following chapters in the troubleshooting segment of the user’s guide: • system verification after your cyberswitch has been configured, and before proceeding with normal system operations, you may want to verify that the system is functional. System verification prov...
Page 335
S ystem v erification o verview after your cyberswitch has been configured, and before proceeding with normal system operation, it is necessary to verify that the system is functional. This chapter provides instructions for verifying the system hardware and system configuration. You only need to per...
Page 336
User’s guide 336 cyberswitch v erifying wan l ines are a vailable for u se to verify the availability of wan lines, the wan resource must already be operational. Also, the wan lines must already be configured and connected to the cyberswitch. To verify the availability of wan lines: 1. Check the lin...
Page 337
Small office remote access switch 337 s ystem v erification verifying bridge is initialized if the system displays this message, then the test packet was transmitted correctly. If this message is not displayed, then the lan connection failed. Refer to lan attachment in the problem diagnosis chapter....
Page 338
User’s guide 338 cyberswitch v erifying a d edicated c onnection to verify a dedicated connection to the cyberswitch, the wan lines that are connected to the system must be available for use, and the routing option must be properly initialized. To verify that you have a dedicated connection: 1. View...
Page 339
Small office remote access switch 339 s ystem v erification verifying an x.25 connection v erifying an x.25 c onnection to verify an x.25 to the cyberswitch, the wan lines that are connected to the system must be available for use, and the routing option must be properly initialized. Follow the step...
Page 340
User’s guide 340 cyberswitch below is an example of a configuration used to verify multi-level security over an ip wan unnumbered interface. It uses ip addresses specific to the example. Substitute the ip address of your network when you perform the multi-level security verification steps. It also u...
Page 341
Small office remote access switch 341 s ystem v erification verifying ip host mode is operational v erifying ip h ost m ode is o perational the follow sections provide methods of verifying that the ip host mode has properly initialized and that the feature is operational. V erifying ip h ost is i ni...
Page 342
User’s guide 342 cyberswitch 2. If a message similar to the following is displayed, the ip host mode feature over the specified lan port is operational. Repeat this step for each lan port on your ethernet resource. 100.0.0.2 is alive 3. If this message is not displayed, then the ip host mode feature...
Page 343
Small office remote access switch 343 s ystem v erification verifying ip routing over interfaces to verify ip routing over a lan connection: 1. Determine if the cyberswitch can access the local ip host. On the administration console type: ip ping 100.0.0.2 issuing this command will result in a respo...
Page 344
User’s guide 344 cyberswitch the steps to verify the operation of ip routing over a wan interface are: 1. Determine if a remote ip host can access the wan interface of the cyberswitch over the wan connection. On the remote ip host, type: ping 192.100.1.1 if the remote ip host successfully pings to t...
Page 345
Small office remote access switch 345 s ystem v erification verifying ip routing over interfaces v erifying ip r outing o ver a wan (d irect h ost ) i nterface to verify that ip routing is properly operational over a wan (direct host) interface, a remote ip host must be operational and available to ...
Page 346
User’s guide 346 cyberswitch v erifying ip r outing o ver a wan r emote lan i nterface to verify that ip routing is properly operational over a wan remote lan interface, a remote ip host must be operational and connected to the remote lan. The remote bridge device must be operational and available t...
Page 347
Small office remote access switch 347 s ystem v erification verifying ip routing over interfaces if the remote ip host successfully pings to the local ip host, then ip routing over the wan remote lan interface is operational. Repeat the above steps for each wan remote lan interface through which you...
Page 348
User’s guide 348 cyberswitch v erifying ip f ilters to verify that ip filters are functioning, perform the following test: 1. Configure and apply at least one ip filter that contains at least one condition whose action is to discard the matching packet. 2. Perform a trace on discarded packets. On th...
Page 349
Small office remote access switch 349 s ystem v erification verifying ip rip v erifying ip rip o utput p rocessing on a lan i nterface to verify that ip rip output processing (routes advertisement) is properly operational on a lan interface, the ip rip processing must be successfully initialized. Al...
Page 350
User’s guide 350 cyberswitch v erifying ip rip i nput p rocessing on a lan i nterface to verify that ip rip input processing (routes learning) is properly operational on a lan interface, ip rip processing must be successfully initialized. Also, a local ip router must be connected to the local lan po...
Page 351
Small office remote access switch 351 s ystem v erification verifying ip rip command is used by a specific router to display the ip routing table. Substitute the equivalent command for your ip router. The steps to verify the operation of ip rip output processing on a wan interface are: 1. Make sure ...
Page 352
User’s guide 352 cyberswitch v erifying ipx r outer is i nitialized to verify that the ipx routing option has initialized properly. 1. Determine if ipx routing has been initialized on the cyberswitch by viewing the system messages. To display the messages enter the following console command: dr 2. L...
Page 353
Small office remote access switch 353 s ystem v erification verifying ipx routing is operational v erifying ipx r outing over a lan c onnection to verify the operation of ipx routing over a lan connection: 1. Determine if site1 can access the local netware server “local.” on site1’s administration c...
Page 354
User’s guide 354 cyberswitch v erifying ipx r outing over a wan c onnection to verify the operation of ipx routing over a wan connection: 1. Determine if netware client a can see the remote netware server “remote.” to do this, activate netware client a’s desktop network neighborhood feature. Then ch...
Page 355
Small office remote access switch 355 s ystem v erification verifying the appletalk routing feature 2. Look for the following message among the system messages: appletalk routing initialized successfully 3. For the appletalk port that has been configured, the following port initialization message sh...
Page 356
User’s guide 356 cyberswitch v erifying a pple t alk r outing o perational over the lan connection the steps to verify the operation of appletalk routing feature over a lan connection are: 1. Determine if the local macintosh can see all zones. Bring up the chooser on the local mac: 2. If a list of a...
Page 357
Small office remote access switch 357 s ystem v erification verifying snmp is operational 2. If remote mac appears in select a file server: box, then appletalk routing over the wan connection is operational. 3. If remote mac is not displayed, then appletalk routing feature over the wan connection is...
Page 358
User’s guide 358 cyberswitch v erifying the d ial o ut f eature to perform the dial out verification for a remote device, you need to know the configured device name associated with the device’s device table entry. Note that the device name is case sensitive. If you already know the device name, ski...
Page 359
Small office remote access switch 359 s ystem v erification verifying compression is operational v erifying c ompression is o perational 1. Make sure compression is enabled on a system-wide basis. 2. Cause a call to be established with a device for which per-device compression is enabled. 3. To veri...
Page 360
User’s guide 360 cyberswitch 1. Set up two systems in a back-to-back, dedicated, bri scenario where at least one of the systems is a pc-platform. Configure a dedicated access between the 2 systems. 2. The usage of a pc-platform exploits the fact that the layer 1 of a pc-based bri board stays active ...
Page 361
Small office remote access switch 361 s ystem v erification verifying dhcp relay agent v erifying the r elay a gent is e nabled if the relay agent has been enabled via configuration, it will attempt to open a udp port for use. A message describing the outcome of this operation will appear in the rep...
Page 362
User’s guide 362 cyberswitch shortly after a dhcp client is powered on, it will attempt to get its ip address from a dhcp server. If it is successful, its ip-related features (e.G., ping, telnet, etc.) will become operational. If the client could not obtain its ip address, it will retry periodically...
Page 363
Small office remote access switch 363 s ystem v erification verifying dhcp: proxy client if you do not see this message in the report log, the dhcp proxy client has successfully performed its initialization processing. If this message is contained in the report log, refer to dhcp proxy client initia...
Page 364
User’s guide 364 cyberswitch ip a ddress p ool as ip addresses are obtained from dhcp servers, they are placed into the system’s ip address pool. To verify the presence of these dhcp-obtained ip addresses, perform the following: 1. Examine the address pool. Type: ip addrpool 2. Look for addresses wi...
Page 365
Small office remote access switch 365 s ystem v erification verifying proxy arp is operational 2. Try to have an ip host device on one ethernet segment communicate with an ip host device on the other ethernet segment. For example, ping from host a to host b. 3. If the communication between two ip de...
Page 366
P roblem d iagnosis o verview this chapter, when used in conjunction with the system verification chapter, helps diagnose and correct problems encountered in the verification process. During some of the diagnosis procedures, we ask you to enter an administration console command. To enter these comma...
Page 367
Small office remote access switch 367 p roblem d iagnosis bridge initialization b ridge i nitialization problem: the system does not display the following bridge initialization messages: lan port is now in the listening state lan port is now in the learning state lan port is now in the forwarding st...
Page 368
User’s guide 368 cyberswitch problem: the system does not display the wan line availability messages. Instead, the system displays the following message after the status console command is issued: out svc 1 (slot #, port #) this means that layer 1 cannot be established, most likely due to wan cablin...
Page 369
Small office remote access switch 369 p roblem d iagnosis dedicated connections problem: a wan line is unavailable, and the following two messages are displayed together (to display messages, issue the dr console command): wan card in slot signals it is operational abnormal response rcvd: state=-1 m...
Page 370
User’s guide 370 cyberswitch x.25 c onnections problem: an x.25 access is configured, but the x.25 stats command response is: no x.25 access configured action: verify that the proper line and port have been selected. 1. Enter the er command to erase the report log. 2. Enter the trace lapb on command...
Page 371
Small office remote access switch 371 p roblem d iagnosis remote device connectivity r emote d evice c onnectivity problem: a remote device is not able to connect to the cyberswitch. Set-up: the system software should be up and running. (at the administration console: if you are in the connection mo...
Page 372
User’s guide 372 cyberswitch ip security rejection - digit string wrong length ip security rejection - invalid security id review the system configuration for the device list. You can also refer to the system messages chapter for the message meanings and the appropriate actions to be taken. The firs...
Page 373
Small office remote access switch 373 p roblem d iagnosis ip host mode ip h ost m ode the following sections provide diagnostic procedures for the ip host mode. Ip h ost i nitialization problem: the system does not display the correct ip host initialization messages. Or, instead, it displays the fol...
Page 374
User’s guide 374 cyberswitch 7. Verify that the hardware address (mac address) for the ip host in the cyberswitch’s arp cache is correct. If it is not correct, verify the configuration in the ip host. Ip h ost m ode o peration over the wan connection problem: the remote ip host connected to a wan rl...
Page 375
Small office remote access switch 375 p roblem d iagnosis ip routing over interface connections encapsulations. Correct the ip host or system configuration (through cfgedit) for encapsulation type. 5. Try to ping the host from another device on the lan. If this is also unsuccessful, this may indicat...
Page 376
User’s guide 376 cyberswitch host, the remote ip host may need a proper route entry for the local network where the cyberswitch is located. Make corrections to the remote ip host configuration. Problem: the remote ip host connected to a wan interface on the cyberswitch does not receive a ping respon...
Page 377
Small office remote access switch 377 p roblem d iagnosis ip routing over interface connections action: 1. Verify that the remote ip host can access the lan interface of the cyberswitch. If it can, continue with the next step. If the remote host is unable to access the lan interface, refer to the pr...
Page 378
User’s guide 378 cyberswitch 3. Verify that the remote bridge device is initiating a call to the cyberswitch. Since the cyberswitch lan interface has an ip address assigned with a different network number than the one for the remote ip host, the remote ip host may need a proper route entry for the l...
Page 379
Small office remote access switch 379 p roblem d iagnosis ip rip a. For packet types, it is important to verify that the contents of the packet in question are indeed correctly specified (ip addresses, protocol, tcp ports, etc.). B. For configured filters, keep in mind that component conditions are ...
Page 380
User’s guide 380 cyberswitch ip rip o utput p rocessing on a lan i nterface problem: the local ip host does not display the correct route entry, for example, the ip host does not seem to be learning route information from the cyberswitch via rip. Action: 1. Using the ipnetif manage mode command, ver...
Page 381
Small office remote access switch 381 p roblem d iagnosis ip rip 3. Also look for the ifstatrcvbadpackets and ifstatrcvbadroutes counters . If these counters are not 0, there may be something wrong with the router. If these counters are 0, there is an unexpected condition present within the cyberswi...
Page 382
User’s guide 382 cyberswitch 2. Enter the ip rip stats administration console command. Look for the ifstatrcvresponses counter for the interface. This statistics is the number of rip update messages received on the interface. If the total number of these counters is 0, check the router to verify tha...
Page 383
Small office remote access switch 383 p roblem d iagnosis ipx routing indicate if it is static (l- locally configured) or dynamically learned via rip (r). If it is learned via rip, then basic communication between the cyberswitch and the local netware server is operational, and it is uncertain why t...
Page 384
User’s guide 384 cyberswitch 6. Verify device configuration on remote bridge. Bridge devices should be configured to make calls over the interface defined to go to the router. Problem: the router does not forward typical data (rip, sap, type 20 packets) to the remote bridge. Action: 1. Make sure a c...
Page 385
Small office remote access switch 385 p roblem d iagnosis ipx routing and service tables ipx r outing and s ervice t ables problem: the routing table on the cyberswitch is full. Action: the number of entries in the routing table is a configurable entity. This parameter may be between the values of 2...
Page 386
User’s guide 386 cyberswitch t riggered rip/sap s tart u p problem: the cyberswitch does not display a triggered rip/sap starting message for a wan peer. Action: verify that the wan peer is properly configured. Issue the device command in manage mode to display the current device list. Or, you may v...
Page 387
Small office remote access switch 387 p roblem d iagnosis appletalk routing a pple t alk r outing i nitialization problem: the cyberswitch does not display the correct appletalk routing initialization messages. Action: 1. Check the system configuration. Make sure that the appletalk feature is enable...
Page 388
User’s guide 388 cyberswitch if ethertalk is selected, and no zones are displayed, then contact your distributor or customer support. 4. If you are using open transport, verify that local mac has chosen a proper appletalk address within the valid network range (this would be 10-11 for the example ne...
Page 389
Small office remote access switch 389 p roblem d iagnosis appletalk routing if the appletalk address for the router is not same as the one displayed when issuing atalk port console command, then the local mac is getting the information from another router. Please refer to the document for the router...
Page 390
User’s guide 390 cyberswitch 4. If the remote resources can not be seen even when the connection is up, then make sure the appletalk address of the remote device is valid. If the remote device is on an unnumbered network, then appletalk an address of 0.0 must be configured for the remote device in t...
Page 391
Small office remote access switch 391 p roblem d iagnosis snmp problem: the cyberswitch does not generate snmp trap pdus. Action: 1. Enter the snmp stats command at the administrative console. If an “snmp is not enabled” message appears, you must first enable the snmp agent (using cfgedit). 2. If th...
Page 392
User’s guide 392 cyberswitch d ial o ut problem: a dial out call was not completed successfully. Action: 1. If you issued the call device console command to initiate the call, check to see that you entered the device name correctly. Device names are case sensitive. 2. If you issued the call peer con...
Page 393
Small office remote access switch 393 p roblem d iagnosis call detail recording if there are no problems with actions 1 and 2, proceed to action 3. 3. Check for the following system messages: in - proceeding in - disconnect - if the system reports these messages, then the network disconnected the ca...
Page 394
User’s guide 394 cyberswitch 3. Verify that the device to which the connection is being established has compression enabled. If the device is another cyberswitch, refer to the previous step for instructions. 4. Use the trace console command to examine the ccp frames exchanged with the device. This i...
Page 395
Small office remote access switch 395 p roblem d iagnosis dhcp: relay agent dhcp: r elay a gent r elay a gent i nitialization problem: the following messages appear in the report log, after system initialization: [dhcp-r] failed to allocated memory for transmit buffer pool [dhcp-r] relay agent initi...
Page 396
User’s guide 396 cyberswitch r elay a gent o peration problem: the dhcp client is not able to obtain its ip address from a dhcp server. Action: 1. Check the dhcp configuration. This can be done by using cfgedit, or by using the dhcp manage mode command. 2. Make sure that the relay agent is enabled o...
Page 397
Small office remote access switch 397 p roblem d iagnosis dhcp: proxy client action: this message indicated that an internal error occurred while the dhcp proxy client was trying to register as a provider of addresses for the ip address pool. Therefore, the proxy client will not operate correctly. C...
Page 398
User’s guide 398 cyberswitch problem: the dhcp proxy client is enabled, and it has opened its udp port, but there aren’t any “dhcp- obtained” addresses in the ip address pool. Action: 1. Check the dhcp-related configuration for wan and wan (direct host) ip network interfaces which should have ip add...
Page 399
Led i ndicators o verview the front panel of the cyberswitch has several led indicators. The power indicator will remain lit while the unit is on. There is a series of three lan indicators: they will light to indicate transmissions, receptions, or good link integrity on the 10base-t port. The bank o...
Page 400
User’s guide 400 cyberswitch * on dms-100 and ni-1 switches, more than one data link is possible. • the ch-1 and ch-2 indicators signify activity along their respective b channel: s ervice i ndicator the service indicator comes on normally during system power-up, and then goes off. If the service in...
Page 401
Small office remote access switch 401 led i ndicators service indicator s ervice i ndicator r emains l it if the service indicator remains lit during the power-on sequence, this means the system software is unable to boot. The systemmay be having some type of operational problem. While the service i...
Page 402
User’s guide 402 cyberswitch these messages indicate a problem with the lan or bri connections, or an incorrectly programmed spid. The service indicator will also blink if semipermanent devices are configured, and a connection to one of these devices is faulty. Use the sp command to check the status...
Page 403
S ystem m essages o verview system messages provide useful system information. They are listed in the system’s report log, a memory resident table. To manipulate the report log, use the following commands at the administrative console: dr or ds display reports or display statistics er or es erase cu...
Page 404
User’s guide 404 cyberswitch b oot m essages the system boot is accomplished in two stages: a first stage boot and a second stage boot (fsb and ssb). If the fsb or ssb detects an error, the system’s service led will light. The first bank of leds will blink in a pattern, as described in the led indic...
Page 405
Small office remote access switch 405 s ystem m essages warning messages s panning t ree m essages the spanning tree protocol is only supported by the ethernet-2 interface card. Spanning tree protocol messages are prefaced with [stp]. During normal operation, when spanning tree protocol is enabled, ...
Page 406
User’s guide 406 cyberswitch 1 port lan adapter, operating in remote mode only this is an initialization message. It identifies the ethernet adapter type (ethernet-1), and operating mode. Remote bridging is supported. 2 port lan adapter, operating in local and remote mode this is an initialization m...
Page 407
Small office remote access switch 407 s ystem m essages system message summary appletalk routing rtmp initialization error, appletalk disabled appletalk is disabled because there is an initialization problem with the routing table maintenance protocol (rtmp). Contact your distributor or customer sup...
Page 408
User’s guide 408 cyberswitch [auth] ace encryption configured for des: not supported. The ace server is configured for des encryption. Only sdi encryption is currently supported by the ace client. [auth] ace error receiving server log message acknowledgment. A client syntax error occurred during an ...
Page 409
Small office remote access switch 409 s ystem m essages system message summary [auth] radius ip host rejected ip host id: the remote authentication server rejected the ip host id. This indicates that one of the following has occurred: 1. The is not in the remote authentication server’s database. 2. ...
Page 410
User’s guide 410 cyberswitch [auth] tacacs login rejected user: the remote authentication server rejected the named user. This indicates that one of the following has occurred: 1. The is not in the remote authentication server’s database. 2. The is entered incorrectly in the remote authentication se...
Page 411
Small office remote access switch 411 s ystem m essages system message summary [auth] warning code: 0010 received unexpected authentication response code from server a message was received from an authentication server that contained an invalid response message identifier. [auth] warning code: 0011 ...
Page 412
User’s guide 412 cyberswitch bridge is operating in restricted mode bridge is operating in unrestricted mode one of the above messages will be displayed to indicate the configured bridge mode of operation. Calculating crc’s..... An x-modem transfer has been completed and the received data is being c...
Page 413
Small office remote access switch 413 s ystem m essages system message summary call restriction statistics reset for new day call restriction device information. Call restriction statistics reset for new month call restriction device information. Call restrictions will allow calls to be made this ho...
Page 414
User’s guide 414 cyberswitch capability description processing error - . System is in minimal configuration mode. A problem has occurred during system installation. The will further identify the problem: • file not found • could not open file • file already exists • header corruption • file write pr...
Page 415
Small office remote access switch 415 s ystem m essages system message summary cause received for dlci a cllm message was received indicating that the pvc associated with the indicated dlci is subject to the event denoted by the indicated cause code. These events are listed below with their correspo...
Page 416
User’s guide 416 cyberswitch channel in use in host_call_request the system software sent a message to the rbs state machine that the state machine was unable to recognize or the information was incorrect. If this message is displayed in the log messages, contact your distributor or customer support...
Page 417
Small office remote access switch 417 s ystem m essages system message summary cntr-tmr:timed out waiting for tmr interrupt! The i386s specified timer did not respond during a post testing its interrupt capabilities. The boot process should continue; however, make note of the error message in the ev...
Page 418
User’s guide 418 cyberswitch dedicated connection down: the dedicated connection is down. Switched backup connections will be used, if available. This message will occur if the other system is down, or if the network interface line is not connected, or if the authentication of the remote device fail...
Page 419
Small office remote access switch 419 s ystem m essages system message summary [dhcp-p] proxy client disabled this message indicates that the dhcp proxy client has been successfully disabled. This message will appear after the dhcp proxy client has been disabled from manage mode. [dhcp-p] proxy clie...
Page 420
User’s guide 420 cyberswitch [dhcp-r] relay agent enabled the dhcp relay agent has been successfully enabled. This could be during system initialization (if configuration values have enabled it), or after the dhcp relay agent has been enabled from manage mode. [dhcp-r] relay agent initialization fai...
Page 421
Small office remote access switch 421 s ystem m essages system message summary dm card in slot is not functional the system was unable to initialize the digital modem in the specified slot correctly. Check all switch and/or jumper settings on the board to ensure they match the values in cfgedit. If ...
Page 422
User’s guide 422 cyberswitch dm upgrade success. Board=, modem= the system has successfully updated the firmware of the specified modem on the digital modem card. Dm: timeslot driver circuit id already in use on create dm: no timeslot driver circuits available for create dm: timeslot driver circuit ...
Page 423
Small office remote access switch 423 s ystem m essages system message summary eds-des board absent eds-feal board absent the encryption board is either physically not in the backplane, or the dip switches on the board are set incorrectly. Check for the board; verify the switch settings . Error clos...
Page 424
User’s guide 424 cyberswitch error mapping wan adapter # ’x’ into host memory map the configured memory location of the indicated wan card conflicts with another wan card or device. Review the configuration for the indicated adapter. Error opening file error opening file , section = error opening fi...
Page 425
Small office remote access switch 425 s ystem m essages system message summary error reading platform type: couldn’t open file c:\system\platform.Nei error reading platform type: error reading c:\system\platform.Nei error reading platform type: there is no “plat name” field error reading platform ty...
Page 426
User’s guide 426 cyberswitch failed to obtain terminal info in smgr_proc_terminal_auth_sess 0 a session control block was not found for this authentication session. Contact your distributor or customer support. Failed to start a terminal auth session. Device + user level security not enabled a termi...
Page 427
Small office remote access switch 427 s ystem m essages system message summary dm rcvd the network will not allow establishment of the data link at this time. An attempt will be made to re-establish the data link after a switchtype dependent delay. Mdl_err_resp rcvd the network has not responded to ...
Page 428
User’s guide 428 cyberswitch l the network sent a layer 2 frame with a control field error. This is typically an unimplemented frame. M the network sent a layer 2 frame with an illegal info field. N the network sent a layer 2 frame with an incorrect length. O the network sent a layer 2 frame that wa...
Page 429
Small office remote access switch 429 s ystem m essages system message summary frame relay pvc connection down: slot=, port= the frame relay pvc connection is down for the indicated slot and port number. Frame relay pvc connection up: slot=, port=, dlci= the frame relay pvc connection is up for the ...
Page 430
User’s guide 430 cyberswitch invalid cllm received on access an invalid cllm message was received on the indicated frame relay access. The message had either missing elements or invalid contents. Invalid lan adapter identifier the system has detected invalid lan adapter hardware. Check for proper la...
Page 431
Small office remote access switch 431 s ystem m essages system message summary [ipap] resmem returned invalid device maximum value (x) a memory allocation failure was encountered by the ip address pool manager during initialization processing. Contact your distributor or customer support. [ip] canno...
Page 432
User’s guide 432 cyberswitch [ip] invalid rlan ip address , rlan ip stream closed the connection from a hdlc bridge or a ppp device came up and the ip (sub-) network number configured for it is invalid; it does not belong to any of the wan (rlan) interfaces. Correct the ip address for the remote dev...
Page 433
Small office remote access switch 433 s ystem m essages system message summary [ip] wan (direct host) interface , invalid associated lan interface interface name> the wan (direct host) type interface could not come up; the associated lan network interface, specified by configuration, was not found. ...
Page 434
User’s guide 434 cyberswitch [ip host] security rejection - invalid security id the system has received an ip host id, , from a remote device that is not configured in the device list. The system has rejected the incoming call. Verify that the ip host id in the device list information is identical t...
Page 435
Small office remote access switch 435 s ystem m essages system message summary [ip rip] unable to open rip/udp port 520 the udp port for rip was unable to be opened. There are 63 possible udp ports, and none are available for use at this time. No rip information can be transmitted or received. Conta...
Page 436
User’s guide 436 cyberswitch [ipx rip] shutdown complete. The ipx rip protocol was successfully shutdown via dynamic management. No ipx rip routing information will be transmitted or received. Any routes learned via ipx rip will soon expire. [ipx rip] space available in routing table a route entry h...
Page 437
Small office remote access switch 437 s ystem m essages system message summary l3_callrefselect call reference wrapped status message indicating that layer 3’s call reference value has wrapped. If this message is posted frequently, report the problem. Lan adapter abort the ethernet adapter or subsys...
Page 438
User’s guide 438 cyberswitch lan adapter out of receive buffers for the wan port the lan adapter is temporarily out of the buffers it uses to receive packets from the wan port. This condition should clear itself. If the condition persists, contact your distributor or customer support. Lan adapter po...
Page 439
Small office remote access switch 439 s ystem m essages system message summary lan port detected shorted lan media the system detected a problem with the physical lan on the indicated port. The lan is not properly terminated or the lan is not fully connected to the system. Check for proper lan insta...
Page 440
User’s guide 440 cyberswitch manage mode updates have been successfully committed the above message indicates that the dynamic management commit command was successfully completed. Manual intervention required: please replace lan card older versions of the ethernet adapter may need to be updated or ...
Page 441
Small office remote access switch 441 s ystem m essages system message summary mismatch of configured and installed dm card in slot the switch and/or jumper settings on the specified digital modem card are not properly set to match how the card is configured in software. Check the hardware and softw...
Page 442
User’s guide 442 cyberswitch network sent cause - spid not supported - the indicated line does not support spids; however, a spid is configured for use on the line. Is the spid configured incorrectly? Do you have the right switch type? Check the configuration. If the message persists, contact your b...
Page 443
Small office remote access switch 443 s ystem m essages system message summary not enough memory for security module not enough system memory available to operate security module. Contact your distributor or customer support. No ua seen in response to sabmes - slot= port= ces= layer 2 cannot be esta...
Page 444
User’s guide 444 cyberswitch out svc # isdn line failure. The line connected to the indicated slot and port is out of service for the reason indicated by # . 1 = no layer 1 sync for 5 seconds this problem normally occurs due to wan cabling problems. Check your cables to make sure they are connected ...
Page 445
Small office remote access switch 445 s ystem m essages system message summary [pap] remote device rejected system information the system received the pap authenticate-nak packet with the error message against the previous pap authenticate-request sent by the system. The is from the remote device, a...
Page 446
User’s guide 446 cyberswitch pvc for dlci > not active a frame was received on the pvc associated with the indicated dlci which was not active. This is a temporary condition, and results from an asynchronous operation between the network and customer-premise equipment regarding the state of the indi...
Page 447
Small office remote access switch 447 s ystem m essages system message summary system to start dialing. Contact the telephone company and ensure that the line is configured for wink-start. Rbs: unexpected event chan = , state = an illegal signaling event occurred in the rbs task on the specified cha...
Page 448
User’s guide 448 cyberswitch resmem_gettotal: enabled size , greater than checksize for internal error that should be reported to customer support. Resmem_malloc failure for subsystem (size=, type=, class=, ra=) resmem_malloc size too large for subsystem (type=, class= ra=) resmem_malloc device not ...
Page 449
Small office remote access switch 449 s ystem m essages system message summary security rejection - no password given by caller a properly formed bridge security negotiation packet was received, and the bridge is registered in the system device table, but a password is required and none was provided...
Page 450
User’s guide 450 cyberswitch semipermanent. Device "x" reconnected by admin. The administrator has issued the call device command after issuing the disc device command. This restarts the semipermanent feature for the indicated device. Severe congestion cllm received for dlci a cllm message was recei...
Page 451
Small office remote access switch 451 s ystem m essages system message summary spid fsm got unidentifiable info msg - slot= port= ces= suffix> an unexpected information message was received from the network on the indicated line. If you are having trouble establishing calls on this line, the problem...
Page 452
User’s guide 452 cyberswitch ssb: post 28 i960lan_82596sx failure the i960 failed its lan coprocessor test. The boot process should continue; however, make note of the error message in the event of a future problem. Ssb: post 29 i960lan_82503 failure the i960 failed its lan transceiver test. The boo...
Page 453
Small office remote access switch 453 s ystem m essages system message summary [stp] a blan topology change has been detected the system has detected a topology change in the spanning tree environment. [stp] a new root bridge has been detected the system has detected a new root bridge for the spanni...
Page 454
User’s guide 454 cyberswitch [tftp] data buffer allocated successfully all parts of the tftp feature (both server and client) were successfully initialized. Note: the following “[tftp] local error...” messages generated during client operations will be displayed on the console only and will not be l...
Page 455
Small office remote access switch 455 s ystem m essages system message summary [tftp] local error # 13: received unexpected opcode the tftp protocol received a packet that was not expected. There may be a problem with the specified file; try replacing it. If this message appears consistently, contac...
Page 456
User’s guide 456 cyberswitch [tftp] remote error # 0: (text from remote host) undefined error. The accompanying text (if any) should describe the error. The file being transferred may be corrupted. [tftp] remote error # 1: (text from remote host) the remote host could not find the file specified on ...
Page 457
Small office remote access switch 457 s ystem m essages system message summary the call is allowed to continue a call has been up longer than the amount of time configured, but it has not been taken down. The compression subsystem is not enabled check cfgedit; verify that compression is enabled. The...
Page 458
User’s guide 458 cyberswitch transmit rate increased to : access , dlci the effective transmit rate has been increased to the indicated rate for the indicated dlci under the indicated access. Transmit rate reduced to cir : access , dlci the effective transmit rate has been limited to the committed i...
Page 459
Small office remote access switch 459 s ystem m essages system message summary unable to identify a remote device a device that was not identified by any active security measures (for example, pap or chap) was rejected. Unable to identify a remote device - a device that was not identified by any act...
Page 460
User’s guide 460 cyberswitch unexpected error during transmission of lmi frame a system error occurred during the actual transmit request for an lmi frame. Contact your distributor or customer support. Unknown calling bridge mac address security is enabled and the remote combinet does not match any ...
Page 461
Small office remote access switch 461 s ystem m essages system message summary wan: rbs not available on this card. A rbs debugging command was attempted on a pri card that is not configured for rbs. Check the card configuration and ensure you have the proper type of card. Watchdog timeout detected ...
Page 462
User’s guide 462 cyberswitch x25 facilities error, reverse charging not accepted the reverse charging facility was selected by the dte. Verify that reverse charging is enabled by both dte’s and the service provider. X25 facilities error, fast select not available the fast select facility was selecte...
Page 463
Small office remote access switch 463 s ystem m essages system message summary x25 facilities warning, nui not available network device identification not available. No action required. X25 permanent virtual circuit down: access=, pvc=, lcn= the indicated x.25 virtual circuit is down. Switched backu...
Page 464
T race m essages o verview trace messages include the following categories of messages: 1. Call trace messages 2. Ip filter trace messages 3. Ppp packet trace messages 4. Wan fr_ietf trace messages 5. X.25 trace messages 6. X.25 (lapb) trace messages before trace messages can be logged to the system...
Page 465
Small office remote access switch 465 t race m essages call trace messages c all t race m essages a feature of the cyberswitch console is the ability to save and display a record of the high level isdn calls between the system and the local telephone switch. If calls are unable to be completed, this...
Page 466
User’s guide 466 cyberswitch c all t race m essage s ummary access information discarded cause call trace message. This message is used to indicate additional details on the received in the “call progress” information message. Alerting off informational call trace message. The alerting signal inform...
Page 467
Small office remote access switch 467 t race m essages call trace messages in - abnormal rpt call id= slot= port= connid= ces= the system has detected an internal error condition. The are included for your distributor or cabletron customer support. An error message describing the problem should be r...
Page 468
User’s guide 468 cyberswitch in - disconnect call id= slot= port= loc= cause= ces= connid= the system has received a disconnect message from the network. The call id and ces values are for your distributor or cabletron customer support. The remaining parameters are used to report line details. Refer...
Page 469
Small office remote access switch 469 t race m essages call trace messages in - progress call id= slot= port= chans= causeloc= cause= signal= progloc= prog= ces= connid= the system has received a call progress message from the network. This is usually received in response to sending a call request. ...
Page 470
User’s guide 470 cyberswitch out - dl cfg slot= port= ces= the system is initializing the indicated data link. Out - dsl cfg slot= port= the system is initializing the indicated line. Out - init data link the system is sending a message to the network to initialize a data link on an isdn line. The a...
Page 471
Small office remote access switch 471 t race m essages ip filters trace messages ip f ilters t race m essages you can trace packets that are discarded as a result of ip filters. Enable this feature by using the ip filter trace discard command, and disable it with ip filter trace off . Note that when...
Page 472
User’s guide 472 cyberswitch ppp p acket t race m essages ppp packet trace allows you to display the ppp protocol negotiation that takes place when a link is established. This information is useful when diagnosing mismatches in configuration between two systems. Ppp packet trace puts ppp packet info...
Page 473
Small office remote access switch 473 t race m essages ppp packet trace messages • configure request the configure request is used to indicate the options that are supported by this sending device. The request contains an option list and the desired values if they are different from the default valu...
Page 474
User’s guide 474 cyberswitch • echo reply the echo reply is transmitted in response to an echo request. The echo reply packet contains the magic number of the sending device. Until the magic number option has been negotiated the value must be set to zero. • discard request the discard request packet...
Page 475
Small office remote access switch 475 t race m essages x.25 trace messages in - x25 connection confirmation connid= access= remdteaddr= the system has received a connect message from the network. This indicates that a new call is now established. In - x25 connection indication connid= access= remdte...
Page 476
User’s guide 476 cyberswitch out - x25 call accept lcn , bytes the dte is accepting an svc call. Out - x25 call request lcn , bytes the dte is attempting to place an svc call. Out - x25 clear ind lcn , bytes the dce is clearing the x.25 virtual circuit on the indicated lcn. Out - x25 clear request l...
Page 477
Small office remote access switch 477 t race m essages x.25 (lapb) trace messages out - x25 dte rr lcn , bytes the dte is acknowledging 1 or more data packets received from the dce. Out - x25 reset ind lcn , bytes the dce is resetting a virtual circuit. Out - x25 reset request lcn , bytes the dte is...
Page 478
User’s guide 478 cyberswitch in - lapb sabme the dce is resetting the link layer. In - lapb ua the dce is acknowledging a sabm or sabme from the dte. Out - lapb disc the dte link layer is going off-line. Out - lapb dm the dte is going off-line. Out - lapb frmr the dte has received an invalid frame. ...
Page 479
S ystem m aintenance this grouping of information provides information to help you maintain your cyberswitch once it is operating. Note that the included system statistics information may also prove valuable in troubleshooting. We include the following chapters in the system maintenance segment of t...
Page 480
R emote m anagement o verview once your system is initially configured (and thus assigned an ip address), you may use a variety of methods to remotely access and manage your system. This chapter describes many of these methods. For information on first-time access (either local or remote), refer to ...
Page 481
Small office remote access switch 481 r emote m anagement amp out-of-band management • connect a modem to the cyberswitch (using the console connection) • connect the modem to the analog line (use a standard pc modem rs232 cable for this, do not use the supplied cable) 2. At the remote management si...
Page 482
User’s guide 482 cyberswitch snmp snmp: the nms gathers information (including problem reports) from any cyberswitch snmp (simple network management protocol) is a standard way of monitoring communication devices in ip networks. With snmp, you purchase and then set up a network management station (s...
Page 483
Small office remote access switch 483 r emote m anagement snmp i nstallation and c onfiguration snmp has two basic components: the snmp agent, which is executed on the cyberswitch, and the network management station (nms), which you purchase separately for the environment. This section will describe...
Page 484
User’s guide 484 cyberswitch t elnet telnet is the standard way of providing remote login service. With telnet, any user on the lan or wan executing a standard telnet client program can remotely login to the cyberswitch and get an cyberswitch console session. When you have an active console session,...
Page 485
Small office remote access switch 485 r emote m anagement telnet on the same subnetwork as the telnet client on system 1’s lan, a static route is needed to allow system 2 to communicate with devices on network 1. Because the cyberswitch had no telnet client capabilities in previous releases, the onl...
Page 486
User’s guide 486 cyberswitch ip address of the cyberswitch. You will then be presented with the “ enter login id: ” prompt. Now enter commands as if directly connected to the cyberswitch. When finished with the session, enter the exit command at the system prompt to end the session with the cyberswi...
Page 487
Small office remote access switch 487 r emote m anagement tftp tftp tftp (trivial file transfer protocol) is the standard way of providing file transfers between devices. With tftp any wan or lan user executing a standard tftp client program can transfer files to and from the cyberswitch. You can co...
Page 488
User’s guide 488 cyberswitch the default file access for the guest user is “read” access to all files. The default file access for the admin user is “read” access to the report and statistics files, and “read and write” access to all other files. The default for the tftp server is admin file access ...
Page 489
Small office remote access switch 489 r emote m anagement remote installation with user2 r emote i nstallation with user2 the cyberswitch is delivered with a default configuration. This default configuration includes a configured device, user2. Advanced users may use the default configuration to per...
Page 490
User’s guide 490 cyberswitch if you are using an cyberswitch as your local isdn device, you can either configure an outbound phone number for the cyberswitch site or use the call peer command to call the cyberswitch without configuring the phone number for the device explicitly. Modify the switch ty...
Page 491
S ystem c ommands o verview two classes of system administration commands are available on the cyberswitch: guest commands and administrator commands. Guest commands provide current operational information only, and are available to all security levels. Administrator commands allows access to the co...
Page 492
User’s guide 492 cyberswitch logout terminates the administration session by logging-out the current administrator. You can start another session by using one of the two log-in commands outlined above. Pswd changes the password for the current access level (administrator or guest). Your password mus...
Page 493
Small office remote access switch 493 s ystem c ommands accessing dynamic management autobaud this command notifies the boot device to check the baud rate. It prepares the boot device to recognize an imminent change. At this time, you should be prepared to set or change the baud rate in your communi...
Page 494
User’s guide 494 cyberswitch cs displays the list of connected devices along with the data rate for each device. The output for this command contains the connection time for each device along with a detailed breakdown (per connection type) of channel usage and available data rates. If there is at le...
Page 495
Small office remote access switch 495 s ystem c ommands viewing operational information number, and the operational status of each interface (up or down). This information can help to determine system problems by identifying those physical interfaces that are not operating as expected. Refer to the ...
Page 496
User’s guide 496 cyberswitch t rying the system is attempting to call the device. Some connections may be up, but not at the initial data rate. Status displays initialization, current status, and connection information, as well as any errors that have been detected. Led status allows you to view a s...
Page 497
Small office remote access switch 497 s ystem c ommands viewing throughput information connections available is less than that amount (33). This means that any of the following combinations of connections would be allowed: if there was enough memory for all connections, the connection table would re...
Page 498
User’s guide 498 cyberswitch note: if data compression is being used, an extra line will be displayed on the connection monitor screen that will provide the compression and decompression ratios, and the estimated throughput. The estimated throughput is calculated as follows: est. Thruput (in kbits/s...
Page 499
Small office remote access switch 499 s ystem c ommands saving operational information # 4. Example of three samples where actual bandwidth utilization was around 70% and underload was being monitored at around 25% utilization of current bandwidth. In this example, overload is occurring on all three...
Page 500
User’s guide 500 cyberswitch c onfiguration -r elated c ommands the following commands provide configuration file information, and restore backup configuration files: cfg provides information on the status of system configuration changes. With manage mode and/ or cfgedit, you can make changes to the...
Page 501
Small office remote access switch 501 s ystem c ommands setting the date and time s etting the d ate and t ime the following commands are used to set the date and the time on the system: date changes the date on the system as specified. The can be specified as a numeral from 1 to 12, spelled out in ...
Page 502
User’s guide 502 cyberswitch list [/c] [bin] displays an ascii file - pausing after every 24 lines. If the “/c” option is used, pausing is disabled. If the binary option is selected, the files will be displayed in uuencoded format. Del deletes the specified file (assuming you have the appropriate ac...
Page 503
Small office remote access switch 503 s ystem c ommands appletalk routing commands note: if you have configured multiple admin login names on your off-node server, the login- id field will not distinguish between the various names. Use the sess-id field to help identify the different admin users. Se...
Page 504
User’s guide 504 cyberswitch atalk port this command will display appletalk port information. A sample output screen is shown below: the fields in this display are defined as follows: type the port type. Possible types are lan, wan, wan unnumbered. Note that the wan unnumbered port information is no...
Page 505
Small office remote access switch 505 s ystem c ommands appletalk routing commands network range for a lan port, this specifies the appletalk network range of the lan segment to which the port is connected. For a wan port, this specifies the appletalk network range of the logical segment to which th...
Page 506
User’s guide 506 cyberswitch distance the number of appletalk routers that are traversed in order to reach the destination appletalk network. State the state of the route. Possible values are: good - this indicates that this is a valid route. Bad - this indicates that the indicated router has not be...
Page 507
Small office remote access switch 507 s ystem c ommands bridge commands atalk zone this command will display appletalk zone information. A sample output screen is shown below: the fields in this display are defined as follows: zone the appletalk zone name for the network that the appletalk port is c...
Page 508
User’s guide 508 cyberswitch the type field is ethernet type field of the lan frame. This hexadecimal field represents the protocol identifier for an ethernet formatted frame. For an 802.3 formatted frame, it is the length of the data unit. The count field is the number of frames transferred for tha...
Page 509
Small office remote access switch 509 s ystem c ommands call control commands could not be found in the device table indicates that the device name could not be found in the table of configured device names. Is already connected indicates that a connection to a device can not be initiated if there i...
Page 510
User’s guide 510 cyberswitch bearer this field applies only to digital modem calls. The valid values are: • speech (the default if no bearer type is specified) • 3.1khz the call peer command allows you to make a connection with another device. For example, to call a site with the configured phone nu...
Page 511
Small office remote access switch 511 s ystem c ommands call detail recording commands disc device disconnects all calls to the specified device. To obtain the device name, enter the manage mode and issue the device command. Note that the device name is case sensitive. In response to the disc device...
Page 512
User’s guide 512 cyberswitch cdr verify generates a sample message to all servers that have been configured for cdr. A message similar to the following will be displayed: cdr verify 1 of 1 refer to log commands for the commands that will allow you to display or erase cdr log reports. C all r estrict...
Page 513
Small office remote access switch 513 s ystem c ommands frame relay commands ip addrpool displays the current ip address pool. Refer to the ip addrpool command description under ip routing commands . F rame r elay c ommands the following commands are used to display information concerning both the s...
Page 514
User’s guide 514 cyberswitch lmi state the condition of the lmi link. Possible settings for this item are wait full status (s1), wait t391 timeout (s2), and wait liv status (s3) . The possible settings are defined as follows: wait full status the lmi state entered when the local frame relay software...
Page 515
Small office remote access switch 515 s ystem c ommands ip routing commands fr cong displays the congestion control information for the last 32 rate measurement intervals for the currently selected access and dlci. It is provided mainly for debug support of frame relay pvcs in order to monitor pvc u...
Page 516
User’s guide 516 cyberswitch always displayed on one line. If the ip protocol is one of the explicitly recognized values (icmp, udp, tcp) the next line will contain a decode of the key fields of that protocol. Off disables the trace. Ip ping [timeout /dnnnn] sends an icmp echo message to a specified...
Page 517
Small office remote access switch 517 s ystem c ommands ip routing commands ip rip routes displays information pertaining to the routing table(s) that are maintained by the ip rip protocol. The following example screen illustrates the output from this command. Following the table is an explanation o...
Page 518
User’s guide 518 cyberswitch ip rip send used to send the ip rip update messages to a particular interface on demand. The example screen below demonstrates how you use this command. Ip rip stats displays global rip statistics and also statistics for each configured rip interface. Refer to rip statis...
Page 519
Small office remote access switch 519 s ystem c ommands ipx routing commands ip route displays the routing information for the indicated device. The meaning of each displayed field for a route entry is included in the above ip route command explanation. Ip stats displays the current ip related stati...
Page 520
User’s guide 520 cyberswitch optional parameter that indicates the number of seconds to wait for a reply. The valid range for the time out value is 1 to 60 seconds. The default value is 10. Note: the ipx diag and the ipx ping commands both test device connectivity (although both send back different ...
Page 521
Small office remote access switch 521 s ystem c ommands isdn usage commands ipx stats displays the ipx statistics. Refer to ipx general statistics , for a list of available statistics and their definitions. Ipx trigreq [device] generates a triggered rip/sap update request to the specified device. Yo...
Page 522
User’s guide 522 cyberswitch lan c ommands the following commands are used to display current system lan diagnostic information: lan stats displays the current lan packet forwarding statistics, including the number of frames received and transmitted from lan and wan connections. Refer to lan statist...
Page 523
Small office remote access switch 523 s ystem c ommands packet capture commands pkt capture [all/idle/reqd/pend/actv/none] specifies which packets will be captured by the packet capture feature. A definition of each possible parameter follows. All all packets will be captured. None no packets will b...
Page 524
User’s guide 524 cyberswitch the following is an example pkt display screen: it is possible to display packet details for a specific packet. To do so, use the keyboard’s arrow keys to move the cursor to the desired packet number (on the “pkt display” screen); then press to display detailed informati...
Page 525
Small office remote access switch 525 s ystem c ommands packet capture commands banyan vines packet detail screen (bridged packet) ip datagram detail screen (routed datagram) while the “pkt display” is displayed on your monitor, you can display the following help screen by entering “?”: the time men...
Page 526
User’s guide 526 cyberswitch radius c ommands the following console commands may be used to diagnose problems with: • connections to the off-node radius authentication server • cyberswitch configuration • authentication server device database entries radius chap attempts an authentication session us...
Page 527
Small office remote access switch 527 s ystem c ommands radius commands radius ipres attempts an authentication session using the ip resolution. The following is an example display of the screen. Radius macres attempts an authentication session using the mac resolution. The following is an example d...
Page 528
User’s guide 528 cyberswitch snmp c ommands when the snmp agent is enabled on the cyberswitch, the following command is available: snmp stats displays the current snmp related statistics. Refer to snmp statistics , for a list of available statistics and their definitions. Tcp c ommands tcp (transmit...
Page 529
Small office remote access switch 529 s ystem c ommands telnet commands telnet ? Displays the help screen for the telnet command. The help screen provides the syntax for the command described below. Telnet [port number] begins a telnet session for the telnet host at the indicated ip address. The por...
Page 530
User’s guide 530 cyberswitch the possible send parameters are defined as follows: send ayt the send ayt command sends the telnet command function for “are you there?” to the target host. This can be used to determine whether or not the target host is still responding. The target host is not required...
Page 531
Small office remote access switch 531 s ystem c ommands terminal commands • , where is in the range of ascii 'a' to ascii '_' • , where is in the range of ascii 'a' to ascii 'z' (note that lower case letters are converted to upper case before they are used) • , where is in the range of ascii '!' to ...
Page 532
User’s guide 532 cyberswitch tftp c ommands the tftp feature and its commands are only available when ip routing is enabled. The tftp feature and file access are enabled by default when the system software is installed. Using the manage mode, configuration changes may be made that will limit file ac...
Page 533
Small office remote access switch 533 s ystem c ommands trace commands session information for a tftp session that has terminated. The screen below illustrates the use of this command. Tftp stats displays the current tftp related statistics. Refer to tftp statistics , for a list of available statist...
Page 534
User’s guide 534 cyberswitch trace x25 [on/off] enables or disables the x.25 packet tracing option. This feature displays up to 15 octets of the packet. To display the log file, issue the dr console command. This option is initially disabled. Wan fr-ietf trace [on/off] [in/out] [device/fr_accessname...
Page 535
Small office remote access switch 535 s ystem c ommands wan commands sentry ace attempts an authentication session using ace. The system will report whether the authentication attempted was successful or rejected. Wan c ommands the following commands are used to display current system wan diagnostic...
Page 536
User’s guide 536 cyberswitch x25 a the “a” option will set the access name specified by as the default access for subsequent commands entered without an explicit access specifier. This access name will remain the current access, until it is changed through issuing another x25 a command. Note: this c...
Page 537
S ystem s tatistics o verview statistics can either be generated by issuing the ds command to display the set of statistics known as the system statistics, or by issuing a specific command to display statistics in a specific category. In addition to using the ds command to display the system statist...
Page 538
User’s guide 538 cyberswitch c all r estriction s tatistics the system keeps a tally of the following call restriction statistics. These statistics can be compared to the limits you have configured. These statistics can be displayed by issuing the cr stats or the ds command at the administration con...
Page 539
Small office remote access switch 539 s ystem s tatistics appletalk statistics a pple t alk s tatistics you may display appletalk protocol statistics (subdivided into six subgroups) and appletalk port statistics. You can display all six subgroups of the appletalk protocol statistics by issuing the a...
Page 540
User’s guide 540 cyberswitch ddptooshorterrors the total number of input ddp datagrams dropped because the received data length was less than the data length specified in the ddp header or the received data length was less than the length of the expected ddp header. Ddptoolongerrors the total number...
Page 541
Small office remote access switch 541 s ystem s tatistics appletalk statistics atechoinreplies the count of appletalk echo replies received. A pple t alk r outing t able m aintenance p rotocol (rtmp) s tatistics you can display this subgroup of appletalk statistics by issuing the atalk stats rtmp co...
Page 542
User’s guide 542 cyberswitch zip zoneconflcterrors the number of times a conflict has been detected between this entity’s zone information and another system’s zone information. Zipinobsoletes the number of zip takedown or zip bringup packets received by this system. Note that as the zip takedown an...
Page 543
Small office remote access switch 543 s ystem s tatistics appletalk statistics atpretrycntexceeds the number of times the retry count was exceeded, and an error was returned to the client of atp. A pple t alk p ort s tatistics you can display the appletalk port statistics by issuing the atalk port s...
Page 544
User’s guide 544 cyberswitch b ridge s tatistics the system collects bridge statistics for each lan port and for wan connections. These bridge statistics include information on the number of frames received, forwarded, discarded or transmitted. If the system is configured for two lan ports, there is...
Page 545
Small office remote access switch 545 s ystem s tatistics compression statistics c ompression s tatistics the system collects the following compression statistics for each active compression connection. These statistics can be displayed by issuing the cmp stats or the cmp stats command at the admini...
Page 546
User’s guide 546 cyberswitch peer sent resets the number of decompression resets sent from peer devices. System sent resets the number of decompression resets sent from the system. Dropped pkts the number of dropped packets that could not be queued. Fcs errors the number of frame checksum errors. Dh...
Page 547
Small office remote access switch 547 s ystem s tatistics dhcp statistics dhcp r elay a gent s tatistics bootrequest msgs rcvd incremented whenever the system identifies a udp datagram as a dhcp/bootp bootrequest message. This datagram has passed the initial consistency checks. Bootrequest msgs rlyd...
Page 548
User’s guide 548 cyberswitch bootreply bad ’giaddr’: number of dhcp/bootp bootreply messages that were discarded by the dhcp relay agent because the ’giaddr’ (gateway ip address) field could not be mapped to one of the system’s ip network interfaces. Bootreply arp_add0 fail number of times that the ...
Page 549
Small office remote access switch 549 s ystem s tatistics frame relay statistics dhcpnaks rcvd incremented whenever the dhcp proxy client has received a dhcpnak message from a dhcp server. Invalid dhcp pkts rcvd incremented whenever the dhcp proxy client encounters a dhcp message that is invalid due...
Page 550
User’s guide 550 cyberswitch # line not ready count the number of times the physical link underlying the frame relay access has become unusable. # frames received the total number of frames received on the frame relay access. This is the sum of the number of frames received on each pvc associated wi...
Page 551
Small office remote access switch 551 s ystem s tatistics frame relay statistics # new & existing pvc the number of times a new pvc was indicated by a lmi status message—but the frame relay software believed the pvc already existed. # pvc not configured the number of times a frame was received conta...
Page 552
User’s guide 552 cyberswitch # bytes received the total number of bytes received on the pvc. # frames sent the total number of frames sent on the pvc. # bytes sent the total number of bytes sent on the pvc. # flow control events the number of times the pvc was congested due to busy transmit hardware...
Page 553
Small office remote access switch 553 s ystem s tatistics ip statistics ip s tatistics you can access ip statistics by using the ip stats console command. These statistics are parts of the ip group and the icmp group mib variables that are defined in rfc-1213:mib-ii. Ip g roup s tatistics ipforwardi...
Page 554
User’s guide 554 cyberswitch ipoutrequests the total number of ip datagrams which local ip device-protocols (including icmp) supplied to ip in requests for transmission. Ipoutdiscards the number of output ip datagrams for which no problem was encountered that would prevent their transmission to thei...
Page 555
Small office remote access switch 555 s ystem s tatistics ip statistics icmpindestunreachs the number of icmp destination unreachable messages received. Icmpintimeexcds the number of icmp time exceeded messages received. Icmpinparmprobs the number of icmp parameter problem messages received. Icmpins...
Page 556
User’s guide 556 cyberswitch icmpoutsrcquenchs the number of icmp source quench messages sent. Icmpoutredirects the number of icmp redirect messages sent. For a host, this will always be zero, since hosts do not send redirects. Icmpoutechos the number of icmp echo (request) messages sent. Icmpoutech...
Page 557
Small office remote access switch 557 s ystem s tatistics ipx statistics ipxbasicsysinhdrerrors the number of ipx packets discarded due to errors in their headers, including any ipx packet with a size less than the minimum of 30 bytes. Ipxbasicsysinunknownsockets the number of ipx packets discarded ...
Page 558
User’s guide 558 cyberswitch ipxadvsysintoomanyhops the number of ipx packets discarded due to exceeding the maximum hop count. Ipxadvsysinfiltered the number of incoming ipx packets discarded due to filtering. Ipxadvsysincompressdiscards the number of incoming ipx packets discarded due to decompres...
Page 559
Small office remote access switch 559 s ystem s tatistics ipx statistics ipx t riggered rip s tatistics you can access ipx triggered rip statistics by using the ipx trigrip stats command. Trigripupdaterequestssent number of triggered rip update requests sent. Trigripupdaterequestsrcvd number of trig...
Page 560
User’s guide 560 cyberswitch ipx sap s tatistics you can access ipx sap statistics by using the ipx sap stats console command. Sapinstance with the cyberswitch, the value of this statistic is always 1. With other products, this statistic is useful. Currently, it is not useful for the cyberswitch. Sa...
Page 561
Small office remote access switch 561 s ystem s tatistics rip statistics maximum services maximum number of services this router is configured to handle. Available services number of services currently available on this router. High water mark peak number of services this router has used. Rip s tati...
Page 562
User’s guide 562 cyberswitch ifstatsentresponses the number of rip messages with ‘response’ command code sent on this interface. Ifstatsentupdates the number of triggered rip updates actually sent on this interface. This explicitly does not include full updates sent containing new information. Snmp ...
Page 563
Small office remote access switch 563 s ystem s tatistics snmp statistics snmpinreadonlys the total number of valid snmp pdus that were delivered to the snmp agent and for which the value of the error-status field is “readonly”. It should be noted that it is a protocol error to generate an snmp pdu ...
Page 564
User’s guide 564 cyberswitch snmpoutgetrequests the total number of snmp get-request pdus that have been generated by the snmp agent. Snmpoutgetnexts the total number of snmp get-next pdus that have been generated by the snmp agent. Snmpoutsetrequests the total number of snmp set-request pdus that h...
Page 565
Small office remote access switch 565 s ystem s tatistics tftp statistics tcpattemptfails the number of times tcp connections have made a direct transition to the closed state from either the syn-sent state or the syn-rcvd state, plus the number of times tcp connections have made a direct transition...
Page 566
User’s guide 566 cyberswitch failed file gets displays the count of failed gets. (remote host failed to download a file from the local system.) total bytes put displays the total number of bytes successfully put. (number of bytes uploaded to the local system by remote hosts.) total bytes get display...
Page 567
Small office remote access switch 567 s ystem s tatistics udp statistics data packets sent displays the total number of data packets sent. Data packets received displays the total number of data packets received. Error packets sent displays the total number of error packets sent. Error packets recei...
Page 568
User’s guide 568 cyberswitch wan fr_ietf s tatistics you can access fr_ietf statistics by issuing the wan fr-ietf stats [device/ fr_accessname_dlci] [prot] console command. Protocol the line protocol of the packets transmitted or received. Frames sent the number of frames sent for the indicated prot...
Page 569
Small office remote access switch 569 s ystem s tatistics x.25 statistics connection request failure a counter that is incremented each time a connection is requested and no response has been received after a connection request failure period of time. Rcv fail a counter that is incremented each time...
Page 570
User’s guide 570 cyberswitch # normal disconnect the number of svc connections that terminated normally. # abnrml disconnect the number of vc connections that terminated due to lapb problems. # packets sent count the number of x.25 data packets sent. # packets received the number of x.25 data packet...
Page 571
Small office remote access switch 571 s ystem s tatistics x.25 statistics # bytes received the total number of data bytes received. X.25 v irtual c ircuit (vc) r elated s tatistics you can access these statistics by issuing the x25 vc stats console command. The statistics displayed will be associate...
Page 572
R outine m aintenance o verview the information in this chapter provides instructions for performing routing maintenance on the cyberswitch. The information falls into the following categories: • installing/upgrading system software • executing configuration changes • performing a configuration back...
Page 573
Small office remote access switch 573 r outine m aintenance configuration backup and restore changes are not dynamic. The changes are saved in a temporary copy of configuration data, and will not affect the current run-time operation of the system in any way. To terminate the session, return to the ...
Page 574
A ppendices the user’s guide includes the following appendices: • system worksheets we have designed a set of worksheets you can fill out before you begin your cyberswitch configuration. Once filled out, they will contain information you will need for the configuration process. • cfgedit map a cfged...
Page 575
S ystem w orksheets the worksheets included in this appendix will be helpful in configuring and managing your system. They capture important network information. To see examples of completed worksheets, refer to the example networks guide. Worksheets included in this appendix are: 1. Network topolog...
Page 576
User’s guide 576 cyberswitch n etwork t opology.
Page 577
Small office remote access switch 577 s ystem w orksheets system details system name: _____________________ pap password:_______________ chap secret:___________________ r esources l ines bri lines type slot switch type synchronization type name slot port line type call screen tei spid directory numb...
Page 578
User’s guide 578 cyberswitch a ccesses dedicated accesses over isdn: over serial connection : x.25 accesses over isdn : over serial connection : frame relay accesses over isdn : over serial connection : line name data rate bearer channels line protocol device tied to this access ❒ 56 kbps ❒ 64 kbps ...
Page 579
Small office remote access switch 579 s ystem w orksheets device information device name: _____________________________ calling (isdn, fr, etc.) information x.25 information authentication information : frame relay information * hdlc bridge only protocol for this particular device? Bridge ip ipx app...
Page 580
User’s guide 580 cyberswitch b ridging ip r outing network interface information bridging ❒ enabled ❒ disabled mode of operation ❒ restricted ❒ unrestricted bridge filters bridge dial out/ known connect list ip routing ❒ enabled ❒ disabled mode of operation ❒ router ❒ ip host lan name ip address mas...
Page 581
Small office remote access switch 581 s ystem w orksheets bridging and routing information ip r outing , continued static routes ipx r outing routing information network interface information static routes netware static services destination network address mask next hop ❒ default? ❒ default? ❒ defa...
Page 582
User’s guide 582 cyberswitch a pple t alk r outing appletalk routing/port information appletalk port static routes appletalk routing ❒ enabled ❒ disabled lan name port number network type ❒ extended ❒ nonextended netwk range/ number appletalk address zone name(s) wan name network type ❒ extended ❒ n...
Page 583
Cfgedit m ap o verview the following pages provide an outline of the cyberswitch cfgedit configuration utility. As you configure your system, you may find it helpful to use this outline as a map to help you navigate through cfgedit. M ain m enu note: all options listed may not be available on your p...
Page 584
User’s guide 584 cyberswitch p hysical r esources m enu r esources • basic rate switch type • t1/e1/pri switch type synchronization • des, feal d ata l ines • name/slot/port/framing/line coding/signalling/line build out • datalinks ppp: tei negotiation pmp: call screen method name subaddress telepho...
Page 585
Small office remote access switch 585 cfgedit m ap options menu o ptions m enu b ridging • enable/disable • spanning tree • mode of operation unrestricted, restricted • bridge filters protocol definition filters (source, destination, protocol, packet data) • known connect list ip r outing • enable/d...
Page 586
User’s guide 586 cyberswitch • routing protocols ipx rip, ipx sap number table entries • ipx static routes rip info number of ticks, hops next hop destination ipx number • netware static services sap info number of hops to service service ipx socket number service ipx node number service ipx network...
Page 587
Small office remote access switch 587 cfgedit m ap options menu c all c ontrol • throughput monitor • call interval • monthly call charges • call restrictions • device profile • bandwidth reservation • semipermanent connection • vra manager for call control enable/disable tcp port number d efault l ...
Page 588
User’s guide 588 cyberswitch s ecurity m enu s ecurity l evel • no security • device level security • user level security • device and user level security s ystem o ptions and i nformation • system options pap password chap challenge bridge mac address ip host id calling line id • system information...
Page 589
Small office remote access switch 589 cfgedit m ap security menu authentication pap password chap secret outbound authentication user level authentication ip host id bridge ethernet calling line id ip information ip address ip enable/disable make calls for ip data ipx enable/disable calls for ipx da...
Page 590
User’s guide 590 cyberswitch o ff - node s erver i nformation • vra manager tcp port • radius primary server secondary server miscellaneous info number of retries time between retries • tacacs primary server secondary server miscellaneous info number of retries time between retries packet format • a...
Page 591
G etting a ssistance r eporting p roblems for a fast response, please take the time to fill out the system problem report to inform us of any difficulties you have with our products. A copy of this report can be found at the end of this chapter. This report provides us with important information to ...
Page 592
Date: ______________ number of pages including this page: ______ to: customer service from: ______________________________________ cabletron systems company:_______________________________________ (603) 332-9400 phone address: ______________________________________ (603) 337-3075 fax _______________...
Page 593
A dministrative c onsole c ommands t able the following table lists all system administration commands. Guest commands are identified in the command column. Command use ? (guest) displays help screen autobaud notifies boot device to check baud rate atalk arp displays the aarp cache atalk ping . {tim...
Page 594
User’s guide 594 cyberswitch cdr stats clear (guest) clears current call detail recording statistics cdr verify (guest) verifies call detail recording servers are configured cfg provides information on changes to configuration files cfgedit starts the cfgedit configuration utility cls (guest) clears...
Page 595
Small office remote access switch 595 a dministrative c onsole c ommands t able ds (guest) displays system statistics er erases current system messages in memory es erases current system statistics in memory exit (guest) terminates a session flash reclaim searches the flashfile system for files mark...
Page 596
User’s guide 596 cyberswitch ip rip send forces an ip rip update message to be sent ip rip stats displays ip rip statistics ip route displays the current routing table ip route displays the routing information for the indicated device ip stats displays or resets current ip related statistics ipconfi...
Page 597
Small office remote access switch 597 a dministrative c onsole c ommands t able list [file name] displays the indicated file useful for displaying release notes (“list rel_notes.Txt”) log cdr display (guest) local log file only - displays the call detail recording log report log cdr erase (guest) lo...
Page 598
User’s guide 598 cyberswitch sentry radius attempts an authentication session using radius sentry status displays current status of user level authentication servers sentry log logs rejection messages from the authentication server session displays the current active administration sessions session ...
Page 599
Small office remote access switch 599 a dministrative c onsole c ommands t able trace lapb[on/off] enables or disables the packet tracing option for lapb data link information trace ppp [on/off] enables or disables the tracing of ppp packets trace x25 [on/off] enables or disables the packet tracing ...
Page 600
User’s guide 600 cyberswitch.
Page 601
M anage m ode c ommands t able the following table displays the available dynamic management commands: command use ace displays ace off-node server configuration ace change allows changes to the ace off-node server configuration ace reinit reinitializes the cyberswitch ace client admlogin [change] d...
Page 602
User’s guide 602 cyberswitch exit exits from manage mode and returns to the normal system command mode fileattr displays the current user file access rights (guest or admin) fileattr change allows the current file access rights configuration data to be changed help displays a list of the valid manag...
Page 603
Small office remote access switch 603 m anage m ode c ommands t able ipxsap displays the current ipx sap status (enabled or disabled) ipxsap [off/on] disables/enables ipx sap ipxsvc displays current ipx service data ipxsvc [add/change/delete] adds/changes/deletes an ipx service ipxspoof allows you t...
Page 604
User’s guide 604 cyberswitch snmp displays the current snmp configuration data seclevel displays current security level semiperm allows you to add or delete device entries for semipermanent connections srcfilt [add/change/delete] adds/changes/deletes the a source address filter tacacs displays tacac...
Page 605
C ause c odes t able the following table provides q.931 cause codes and their corresponding meanings. Cause codes may appear in call trace messages. Dec value hex value q.931 cause 0 0 valid cause code not yet received 1 1 unallocated (unassigned number) indicates that, although the isdn number was ...
Page 606
User’s guide 606 cyberswitch 19 13 no answer from device (device alerted) indicates that the destination has responded to the connection request but has failed to complete the connection within the prescribed time. Problem at remote end. 21 15 call rejected indicates that the destination was capable...
Page 607
Small office remote access switch 607 c ause c odes t able 34 22 no circuit/channel available indicates that the connection could not be established because there was no appropriate channel available to handle the call. 35 23 destination unattainable 37 25 degraded service 38 26 network (wan) out of...
Page 608
User’s guide 608 cyberswitch 52 34 outgoing calls barred 53 35 outgoing calls barred within cug 54 36 incoming calls barred 55 37 incoming calls barred within cug 56 38 call waiting not subscribed 57 39 bearer capability not authorized indicates that the device has requested a bearer capability that...
Page 609
Small office remote access switch 609 c ause c odes t able 81 51 invalid call reference value indicates that the remote equipment has received a call with a call reference that is not currently in use by the device-network interface. 82 52 identified channel does not exist indicates that the receivi...
Page 610
User’s guide 610 cyberswitch 97 61 message type non-existent or not implemented indicates that the receiving equipment received a message that was not recognized either because the message type was invalid, or because the message type was valid but not supported. This is either a problem with the re...
Page 611
Small office remote access switch 611 c ause c odes t able unknown indicates that an event occurrent but that the network does not provide causes for the actions that it takes, therefore the precise nature of the event cannot be ascertained. This may, or may not, indicate the occurrence of an error....
Page 612
User’s guide 612 cyberswitch i ndex a access request retries 165, 168 accesses alternate accesses 177 x.25 179 accessing the cyberswitch 50 ace 167 ace authentication server alternate method of configuring 167 configuring 166 active wan peer 278 adapters configuring adapters 69 overview 71 admin 53,...
Page 613
Small office remote access switch 613 cfgedit 64, 572 map 583 cfgedit 64 chap secret 146 clid 148 cls 66, 493 cmp commands 512 commands administration services 491 appletalk 503 bridging 507 call control 508 call detail recording 511 call restriction 512 compression 512 dynamic management 601 frame ...
Page 614
User’s guide 614 cyberswitch dhcp commands 512 diagnosis 395 example configurations 243 in a bridge to bridge environment 242 in a router to bridge environment 242 proxy client 247 proxy client verification 362 relay agent 240 relay agent verification 360 statistics 546 verifying 360 dhcp 240, 247 d...
Page 615
Small office remote access switch 615 ip addrpool 513 ip commands 515 ip filters 223, 233 applying filters 231 configuration elements 232 connection filters 229 example 238 exception filter 230 forwarding filters 228 global 231 icmp configuration 227 network interfaces 231 packet type configuration ...
Page 616
User’s guide 616 cyberswitch isolated mode 220 k known connect list 218 l lan adapter problem diagnosis 366, 372 verification messages 337 lan commands 522 lan connection operation verification 336 lan ip interface 86 lan led indicators 399 lan statistics 552 lan test 336 lapb 183 led indicators 399...
Page 617
Small office remote access switch 617 o off-node server information 159 on-node device table configuration elements 144 operational files 40 outbound authentication 147 overload condition 298 over-subscription timer (triggered rip/sap) 274 p packet data filter commands 206 packet types 224, 234, 236...
Page 618
User’s guide 618 cyberswitch remote management 480 amp out-of-band 480 snmp 482 telnet 484 tftp 487 reporting problems 591 resource 71 resources 69, 71 see also adapters restart 500 restore 500 restoring configuration 573 restricted bridge mode 203, 213 retransmission timer (triggered rip/sap) 273 r...
Page 619
Small office remote access switch 619 statistics appletalk routing 539 bridging 544 call detail recording 544 call restriction 538 call statistics 538 compression 545 connectivity 537 dhcp 546 ip 553 ipx 556 ipx route 559 lan 552 snmp 562 tcp 564 tftp 565 throughput monitoring 538 triggered rip/sap ...
Page 620
User’s guide 620 cyberswitch unrestricted bridge mode 202 update 493 upgrading software 572 user level authentication 147 user level databases 157 user level security 114, 121 configuration 121, 158 configuration specific to ipx 274, 277 device and user level security 125 login banner files 41 utili...