D-Link DFL-1600 - Security Appliance User Manual - 2.4. Maintenance
2.4. Maintenance
2.4.1. Reset to Factory Defaults
It is possible to apply the original defaults that existed when the D-Link Firewall was purchased.
These defaults can be applied only to the current configuration or to the entire hardware unit. The
latter option essentially restores the unit to the state it was in when it left the factory.
Example 2.12. Reset to Factory Defaults with the standard user interface
Web Interface
1.
Go to Maintenance > Reset
2.
Select Reset the configuration to Factory Defaults then confirm and wait for the restore to complete, OR
3.
Select Reset the entire unit to Factory Defaults then confirm and wait for the restore to complete.
Reset alternative via the Serial Console
Connect the serial cable and connect with a console using a terminal emulator software product. If
Microsoft Windows is being used, "HyperTerminal" can be used. Reset the firewall. Press a key
when the "Press any key to abort and load boot menu" message appears at the console. When the
boot menu appears, select the desired option then confirm and wait for the process to complete.
Reset alternative for the DFL-210/260/800/860 only
To reset the DFL-210/260/800/860 you must hold down the reset button at the rear panel for 10-15
seconds while powering on the unit. After that, release the reset button and the DFL-210/800 will
continue to load and startup in default mode, i.e. with 192.168.1.1 on the LAN interface.
Reset alternatives for the DFL-1600 and DFL-2500 only
Press any key on the keypad when the "Press keypad to Enter Setup" message appears on the dis-
play. Select "Reset firewall", confirm by selecting "Yes" and wait for the process to complete.
Warning
DO NOT ABORT THE RESET TO FACTORY DEFAULTS PROCESS. If aborted the
firewall can cease to function properly.
2.4.2. Configuration Backup and Restore
The configuration of D-Link Firewalls can be backed up or restored on demand. This could, for in-
stance, be used to recall the "last known good" configuration when experimenting with different
configuration setups.
Example 2.13. Configuration Backup and Restore
Web Interface
To create a backup of the currently running configuration:
2.4. Maintenance
Chapter 2. Operations and Maintenance
28
Summary of DFL-1600 - Security Appliance
Page 1
Network security solution http://www.Dlink.Com security security dfl-210/ 800/1600/ 2500 dfl-260/ 860 ver. 1.05 network security firewall user manual.
Page 2: User Manual
User manual dfl-210/260/800/860/1600/2500 netdefendos version 2.12 d-link corporation no. 289, sinhu 3rd rd, neihu district, taipei city 114, taiwan r.O.C. Http://www.Dlink.Com published 2007-05-29 copyright © 2007.
Page 3
User manual dfl-210/260/800/860/1600/2500 netdefendos version 2.12 published 2007-05-29 copyright © 2007 copyright notice this publication, including all photographs, illustrations and software, is protected under interna- tional copyright laws, with all rights reserved. Neither this manual, nor any...
Page 4: Table Of Contents
Table of contents preface .............................................................................................................. Xii 1. Product overview .............................................................................................. 1 1.1. About d-link netdefendos ...............
Page 5
3.5. The ip rule-set .....................................................................................52 3.5.1. Overview ...................................................................................52 3.5.2. Rule evaluation .....................................................................
Page 6
6.3.7. Idp actions .............................................................................. 131 6.3.8. Smtp log receiver for idp events .............................................. 131 6.4. Anti-virus .......................................................................................... ...
Page 7
9.4. Pptp/l2tp ......................................................................................... 202 9.4.1. Pptp ....................................................................................... 202 9.4.2. L2tp ..............................................................................
Page 8
13.20. Ppp settings .................................................................................... 275 13.21. Idp ................................................................................................ 276 13.22. Hardware monitor settings .................................................
Page 9: List Of Figures
List of figures 1.1. Packet flow schematic part i ............................................................................ 6 1.2. Packet flow schematic part ii ........................................................................... 7 1.3. Packet flow schematic part iii .........................
Page 10: List Of Examples
List of examples 1. Example notation ............................................................................................. Xii 2.1. Enabling ssh remote access ..........................................................................12 2.2. Enabling remote management via https. ................
Page 11
6.5. H.323 with private ip addresses ...................................................................... 114 6.6. Two phones behind different d-link firewalls ................................................. 115 6.7. Using private ip addresses .......................................................
Page 12: Preface
Preface intended audience the target audience for this reference guide is administrators who are responsible for configuring and managing d-link firewalls which are running the netdefendos operating system. This guide assumes that the reader has some basic knowledge of networks and network security....
Page 13: Notes To The Main Text
Notes to the main text special sections of text which the reader should pay special attention to are indicated by icons on the the left hand side of the page followed by a short paragraph in italicized text. Such sections have the following types and purposes: note this indicates some piece of infor...
Page 14
Chapter 1. Product overview this chapter outlines the key features of netdefendos. • about d-link netdefendos, page 1 • netdefendos architecture, page 3 • netdefendos packet flow, page 6 1.1. About d-link netdefendos d-link netdefendos is the firmware, the software engine that drives and controls al...
Page 15
For more information about the idp capabilities of netdefen- dos, please see section 6.3, “intrusion detection and preven- tion”. Anti-virus netdefendos features integrated gateway anti-virus function- ality. Traffic passing through the gateway can be subjected to in-depth scanning for viruses, and ...
Page 16: 1.2.3. Basic Packet Flow
1.2. Netdefendos architecture 1.2.1. State-based architecture the netdefendos architecture is centered around the concept of state-based connections. Tradition- al ip routers or switches commonly inspect all packets and then perform forwarding decisions based on information found in the packet heade...
Page 17
• if the ethernet frame contains a ppp payload, the system checks for a matching pppoe in- terface. If one is found, that interface becomes the source interface for the packet. If no matching interface is found, the packet is dropped and the event is logged. • if none the above is true, the receivin...
Page 18
Connection. 10. The traffic shaping and the threshold limit rule-sets are now searched. If a match is found, the corresponding information is recorded with the state. This will enable proper traffic man- agement on the connection. 11. From the information in the state, netdefendos now knows what to ...
Page 19
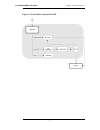
1.3. Netdefendos packet flow the diagrams in this section provide a summary of the flow of packets through the netdefendos state-engine. There are three diagrams, each flowing into the next. Figure 1.1. Packet flow schematic part i the packet flow is continued on the following page. 1.3. Netdefendos...
Page 20
Figure 1.2. Packet flow schematic part ii the packet flow is continued on the following page. 1.3. Netdefendos packet flow chapter 1. Product overview 7.
Page 21
Figure 1.3. Packet flow schematic part iii 1.3. Netdefendos packet flow chapter 1. Product overview 8.
Page 22
1.3. Netdefendos packet flow chapter 1. Product overview 9.
Page 23: 2.1.1. Overview
Chapter 2. Operations and maintenance this chapter describes the operations and maintenance related aspects of netdefendos. • configuring netdefendos, page 10 • events and logging, page 21 • radius accounting, page 24 • maintenance, page 28 2.1. Configuring netdefendos 2.1.1. Overview netdefendos is...
Page 24
By default, netdefendos has a local user database, adminusers, with one user account pre-defined: • username admin with password admin. The admin account has full administrative rights. Important for security reasons, it is highly recommended that you change the default password of the default accou...
Page 25
Ssh (secure shell) the ssh (secure shell) protocol can be used to access the cli over the network from a remote host. Ssh is a protocol primarily used for secure communication over insecure networks, providing strong authentication and data integrity. Netdefendos supports version 1, 1.5 and 2 of the...
Page 26: 2.1.4. Web Interface
2.1.4. Web interface netdefendos provides a highly versatile web user interface for management of the system using a standard web browser. This allows you to perform remote management from virtually anywhere in the world without having to install any third-party clients. 2.1.4.1. Logging on to the w...
Page 27
Note access to the web interface is regulated by the remote management policy. By default, the system will only allow web access from the internal network. 2.1.4.2. Interface layout the main web interface page is divided into three major sections: menu bar the menu bar located at the top of the web ...
Page 28
Cli gw-world:/> add remotemanagement remotemgmthttp https network=all-nets interface=any localuserdatabase=adminusers https=yes web interface 1. Go to system > remote management > add > http/https management 2. Enter a name for the http/https remote management policy, e.G. Https. 3. Check the https ...
Page 29
Example 2.3. Listing configuration objects this example shows how to list all service objects. Cli gw-world:/> show service a list of all services will be displayed, grouped by their respective type. Web interface 1. Go to objects > services 2. A web page listing all services will be presented. A li...
Page 30
Note when accessing object via the cli you can omit the category name and just use the type name. The cli command in the above example, for instance, could be simplified to: gw-world:/> show servicetcpudp telnet editing a configuration object when you need to modify the behavior of netdefendos, you ...
Page 31
Dress book. Cli gw-world:/> add address ip4address myhost address=192.168.10.10 show the new object: gw-world:/> show address ip4address myhost property value --------------------- ------------- name: myhost address: 192.168.10.10 userauthgroups: (none) nodefinedcredentials: no comments: (none) web ...
Page 32
Cli gw-world:/> undelete address ip4address myhost web interface 1. Go to objects > address book 2. Right-click on the row containing the myhost object. 3. In the dropdown menu displayed, select undo delete. Listing modified objects after modifying several configuration objects, you might want to se...
Page 33
Example 2.10. Activating and committing a configuration this example shows how to activate and commit a new configuration. Cli gw-world:/> activate the system will validate and start using the new configuration. When the command prompt is shown again: gw-world:/> commit the new configuration is now ...
Page 34: 2.2. Events And Logging
2.2. Events and logging 2.2.1. Overview the ability to log and analyze system activities is one of the most vital and fundamental features of a netdefendos system. Logging enables you not only to monitor system status and health, but also to audit the usage of your network as well as to assist you w...
Page 35
2.2.3.1. Logging to syslog hosts syslog is a standardized protocol for sending log data to loghosts, although there is no standardized format of these log messages. The format used by netdefendos is well suited for automated pro- cessing, filtering and searching. Although the exact format of each lo...
Page 36
2.2.3. Event message distribution chapter 2. Operations and maintenance 23.
Page 37: 2.3. Radius Accounting
2.3. Radius accounting 2.3.1. Overview within a network environment containing large numbers of users, it is advantageous to have one or a cluster of central servers that maintain user account information and are responsible for authentica- tion and authorization tasks. The central database residing...
Page 38
Was authenticated via radius, or local if the user was authenticated via a local user data- base. • delay time - the time delay (in seconds) since the accountingrequest packet was sent and the authentication acknowledgement was received. This can be subtracted from the time of arrival on the server ...
Page 39
Note the (*) symbol in the above list indicates that the sending of the parameter is user configurable. 2.3.3. Interim accounting messages in addition to start and stop messages netdefendos can optionally periodically send interim accounting messages to update the accounting server with the current ...
Page 40
In an ha cluster, accounting information is synched between the active and passive d-link fire- walls. This means that accounting information is automatically updated on both cluster members whenever a connection is closed. Two special accounting events are also used by the active unit to keep the p...
Page 41: 2.4. Maintenance
2.4. Maintenance 2.4.1. Reset to factory defaults it is possible to apply the original defaults that existed when the d-link firewall was purchased. These defaults can be applied only to the current configuration or to the entire hardware unit. The latter option essentially restores the unit to the ...
Page 42
1. Go to tools > backup 2. Download configuration, select a name and begin backup. To restore a configuration backup: 1. Go to tools > backup 2. In restore unit's configuration browse and locate the desired backup. 3. Click upload configuration and then choose to activate that configuration. Note ba...
Page 43
2.4.3. Auto-update mechanism chapter 2. Operations and maintenance 30
Page 44: Chapter 3. Fundamentals
Chapter 3. Fundamentals this chapter describes the fundamental logical objects upon which netdefendos is built. These lo- gical objects include such things as addresses, services and schedules. In addition, this chapter ex- plains how the various supported interfaces work, it outlines how policies a...
Page 45
For example: 192.168.0.0/24 ip range a range of ip addresses is represented on the form a.B.C.D - e.F.G.H. Please note that ranges are not limited to netmask boundaries; they may include any span of ip ad- dresses. For example: 192.168.0.10-192.168.0.15 represents six hosts in consecutive order. Exa...
Page 46: 3.1.3. Ethernet Addresses
1. Go to objects > address book > add > ip address 2. Specify a suitable name for the ip range, for instance wwwservers. 3. Enter 192.168.10.16-192.168.10.21 in the ip address textbox. 4. Click ok. Example 3.4. Deleting an address object to delete an object named wwwsrv1 in the address book, do the ...
Page 47: 3.1.4. Address Groups
3.1.4. Address groups address objects can be grouped in order to simplify configuration. Consider a number of public servers that should be accessible from the internet. The servers have ip addresses that are not in a sequence, and can therefore not be referenced to as a single ip range. Consequentl...
Page 48: 3.2. Services
3.2. Services 3.2.1. Overview a service object is a reference to a specific ip protocol with associated parameters. A service defin- ition is usually based on one of the major transport protocols such as tcp or udp, with the associ- ated port number(s). The http service, for instance, is defined as ...
Page 49
Name: echo destinationports: 7 type: tcpudp (tcp/udp) sourceports: 0-65535 passicmpreturn: no alg: (none) maxsessions: 1000 comments: echo service web interface 1. Go to objects > services 2. Select the specific service object in the grid control. 3. A grid listing all services will be presented. 3....
Page 50: 3.2.3. Icmp Services
Tip the above methods of specifying port numbers are not used just for destination ports. Source port definitions can follow the same conventions, although it is most usual that the source ports are left as their default values, namely 0-65535, which matches all possible source ports. Example 3.8. A...
Page 51
The icmp message types that can be configured in netdefendos are listed as follows: • echo request: sent by ping to a destination in order to check connectivity. • destination unreachable: the source is told that a problem has occurred when delivering a pack- et. There are codes from 0 to 5 for this...
Page 52
Example 3.9. Adding a ip protocol service this example shows how to add an ip protocol service, with the virtual router redundancy protocol. Cli gw-world:/> add service serviceipproto vrrp ipproto=112 web interface 1. Go to objects > services > add > ip protocol service 2. Specify a suitable name fo...
Page 53: 3.3. Interfaces
3.3. Interfaces 3.3.1. Overview an interface is one of the most important logical building blocks in netdefendos. All network traffic that passes through or gets terminated in the system is done so through one or several inter- faces. An interface can be seen as a doorway for network traffic to or f...
Page 54: 3.3.2. Ethernet
L2tp tunnels. For more information about pptp/l2tp, please see section 9.4, “pptp/l2tp”. Even though the various types of interfaces are very different in the way they are implemented and how they work, netdefendos treats all interfaces as logical ip interfaces. This means that all types of interfac...
Page 55
Note the startup process will enumerate all available ethernet interfaces. Each interface will be given a name of the form lann, wann and dmz, where n represents the number of the interface if your d-link firewall has more than one of these interfaces. In most of the examples in this guide lan is us...
Page 56: 3.3.3. Virtual Lan
3. Check the enable dhcp client control. 4. Click ok. 3.3.3. Virtual lan netdefendos is fully compliant with the ieee 802.1q specification for virtual lans. On a pro- tocol level, virtual lans work by adding a virtual lan identifier (vlan id) to the ethernet frame header. The vlan id is a number fro...
Page 57
Dsl line, wireless device or cable modem. All the users on the ethernet share a common connec- tion, while access control can be done on a per-user basis. Internet server providers (isps) often require customers to connect through pppoe to their broad- band service. Using pppoe the provider can: • i...
Page 58: 3.3.5. Interface Groups
If dial-on-demand is enabled, the pppoe connection will only be up when there is traffic on the pppoe interface. It is possible to configure how the firewall should sense activity on the interface, either on outgoing traffic, incoming traffic or both. Also configurable is the time to wait with no ac...
Page 59
Web interface 1. Go to interfaces > interface groups > add > interfacegroup 2. Enter the following information to define the group: • name: the name of the group to be used later • security/transport equivalent: if enabled, the interface group can be used as a destination interface in rules where co...
Page 60: 3.4. Arp
3.4. Arp 3.4.1. Overview address resolution protocol (arp) is a protocol, which maps a network layer protocol address to a data link layer hardware address and it is used to resolve an ip address into its corresponding ether- net address. It works at the osi data link layer (layer 2 - see appendix d...
Page 61
Cifies how long netdefendos is to remember addresses that cannot be reached. This is done to en- sure that netdefendos does not continously request such addresses. The default value for this set- ting is 3 seconds. Displaying the arp cache example 3.14. Displaying the arp cache the contents of the a...
Page 62
Dresses) as well as publishing ip addresses with a specific ethernet address. Static arp entries static arp items may help in situations where a device is reporting incorrect ethernet address in re- sponse to arp requests. Some workstation bridges, such as radio modems, can have such problems. It ma...
Page 63
Xpublish "lies" about the sender ethernet address in the ethernet header; this is set to be the same as the published ethernet address rather than the actual ethernet address of the ethernet interface. If a published ethernet address is the same as the ethernet address of the interface, it will make...
Page 64
Sender ip 0.0.0.0 netdefendos can be configured on what to do with arp queries that have a sender ip of 0.0.0.0. Such sender ips are never valid in responses, but network units that have not yet learned of their ip address sometimes ask arp questions with an "unspecified" sender ip. Normally, these ...
Page 65: 3.5. The Ip Rule-Set
3.5. The ip rule-set 3.5.1. Overview security policies designed by the administrator regulate the way in which network applications are protected against abuse and inappropriate use. Netdefendos provides an array of mechanisms and logical constructs to help with the building of such policies for att...
Page 66: 3.5.3. Ip Rule Components
3.5.3. Ip rule components a rule consists of two logical parts: the connection parameters and the action to take if there is a match with those parameters. Rule parameters are pre-defined and reusable network objects such as addresses and services, which can be used in any rule to specify the criter...
Page 67
3.5.4. Editing ip rule-set entries after adding various rules to the rule-set editing any line can be achieved in the web-ui by right clicking on that line. A context menu will appear with the following options: edit this allows the contents of the rule to be changed. Delete this will remove the rul...
Page 68: 3.6. Schedules
3.6. Schedules in some scenarios, it might be useful to control not only what functionality is enabled, but also when that functionality is being used. For instance, the it policy of an enterprise might stipulate that web traffic from a certain department is only allowed access outside that departme...
Page 69
• action: nat • service: http • schedule: officehours • sourceinterface: lan • sourcenetwork lannet • destinationinterface: any • destinationnetwork: all-nets 4. Click ok. 3.6. Schedules chapter 3. Fundamentals 56.
Page 70: 3.7. X.509 Certificates
3.7. X.509 certificates netdefendos supports digital certificates that comply with the itu-t x.509 standard. This in- volves the use of an x.509 certificate hierarchy with public-key cryptography to accomplish key distribution and entity authentication. 3.7.1. Overview an x.509 certificate is a digi...
Page 71
Left the company from whom the certificate was issued. A crl is regularly published on a server that all certificate users can access, using either the ldap or http protocols. Certificates often contain a crl distribution point (cdp) field, which specifies the location from where the crl can be down...
Page 72
3.8. Setting date and time correctly setting the date and time is important for netdefendos to operate properly. Time sched- uled policies, auto-update of idp signatures, and other product features require that the system clock is accurately set. In addition, log messages are tagged with time-stamps...
Page 73: 3.8.2. Time Servers
Example 3.20. Setting the time zone to modify the netdefendos time zone to be gmt plus 1 hour, follow the steps outlined below: cli gw-world:/> set datetime timezone=gmtplus1 web interface 1. Go to system > date and time 2. Select (gmt+01:00) in the timezone drop-down list. 3. Click ok. 3.8.1.3. Day...
Page 74
3.8.2.1. Time synchronization protocols time synchronization protocols are standardised methods for retrieving time information from ex- ternal time servers. Netdefendos supports the following time synchronization protocols: • sntp - defined by rfc 2030, the simple network time protocol (sntp) is a ...
Page 75
Example 3.23. Manually triggering a time synchronization time synchronization can be triggered from the cli. The output below shows a typical response. Cli gw-world:/> time -sync attempting to synchronize system time... Server time: 2007-02-27 12:21:52 (utc+00:00) local time: 2007-02-27 12:24:30 (ut...
Page 76
3.8.2.4. Synchronization intervals the interval between each synchronization attempt can be adjusted if needed. By default, this value is 86,400 seconds (1 day), meaning that the time synchronization process is executed once in a 24 hour period. 3.8.2.5. D-link time servers using d-link's own time s...
Page 77: 3.9. Dns Lookup
3.9. Dns lookup a dns server resolves a textual url address into a numeric ip address. This allows the actual physical ip address to change while the url can stay the same. Urls can be used in various areas of a netdefendos configuration where ip addresses are un- known, or where it makes more sense...
Page 78
3.9. Dns lookup chapter 3. Fundamentals 65.
Page 79: Chapter 4. Routing
Chapter 4. Routing this chapter describes how to configure ip routing in netdefendos. • overview, page 66 • static routing, page 67 • policy-based routing, page 76 • dynamic routing, page 80 • transparent mode, page 88 4.1. Overview ip routing capabilities belong to the most fundamental functionalit...
Page 80: 4.2. Static Routing
4.2. Static routing the most basic form of routing is known as static routing. The term static refers to the fact that entries in the routing table are manually added and are therefore permanent (or static) by nature. Due to this manual approach, static routing is most appropriate to use in smaller ...
Page 81
4.2.1. Static routing in netdefendos this section describes how routing is implemented in netdefendos, and how to configure static routing. Netdefendos supports multiple routing tables. A default table called main is pre-defined and is al- ways present in netdefendos. However, additional and complet...
Page 82
Persistent routes: none the corresponding routing table in netdefendos is similar to this: flags network iface gateway local ip metric ----- ------------------ -------- -------------- --------- ------ 192.168.0.0/24 lan 20 10.0.0.0/8 wan 1 0.0.0.0/0 wan 192.168.0.1 20 the netdefendos way of describi...
Page 83
213.124.165.0/24 wan 0 0.0.0.0/0 wan 213.124.165.1 0 web interface to see the configured routing table: 1. Go to routing > routing tables 2. Select and right-click the main routing table in the grid. 3. Choose edit in the menu. The main window will list the configured routes. To see the active routi...
Page 84: 4.2.2. Route Failover
Web interface to see the core routes from the web interface, select the routes item in the status dropdown menu in the menu bar. Check the show all routes checkbox and click the apply button. The main window will list the active routing table including the core routes. Tip for detailed information a...
Page 85
Interface link status netdefendos will monitor the link status of the interface spe- cified in the route. As long as the interface is up, the route is dia- gnosed as healthy. This method is appropriate for monitoring that the interface is physically attached and that the cabling is working as expect...
Page 86
In the route that has the lowest metric being chosen. If the primary wan router should then fail, this will be detected by netdefendos, and the first route will be disabled. As a consequence, a new route lookup will be performed and the second route will be selected with the first one being marked a...
Page 87
Be controlled by the advanced setting rfo_gratuitousarponfail. Host monitoring overview to provide a more flexible and configurable way to monitor the integrity of routes, netdefendos provides the additonal capability to perform host monitoring as a means to monitor a route. This feature means that ...
Page 88: 4.2.3. Proxy Arp
• sample - the number of polling attempts used as a sample size for calculating the percentage loss and the average latency. • max number of failed attempts - the maximum permissable number of polling attempts that fail. If this number is exceeded then the host is considered unreachable. • max avera...
Page 89: 4.3. Policy-Based Routing
4.3. Policy-based routing 4.3.1. Overview policy-based routing is an extension to the standard approach to routing described previously. It of- fers administrators significant flexibility in implementing routing decision policies by be able to define policy-based routing rules. Normal routing forwar...
Page 90
Based routing rule can be triggered by the type of service (eg. Http) in combination with the source/destination interface and source/destination network. When looking up policy-based rules, it is the first matching rule found that is triggered. 4.3.4. Policy-based routing table selection when a new...
Page 91
Example 4.3. Creating a policy-based routing table in this example we create a policy-based routing table named "testpbrtable". Web interface 1. Go to routing > routing tables > add > routingtable 2. Now enter: • name: testpbrtable • for ordering select one of: • first - the named routing table is c...
Page 92
• this is a "drop-in" design, where there are no explicit routing subnets between the isp gateways and the d- link firewall. In a provider-independent metropolitan area network, clients will likely have a single ip address, belonging to one of the isps. In a single-organization scenario, publicly ac...
Page 93: 4.4. Dynamic Routing
4.4. Dynamic routing 4.4.1. Dynamic routing overview dynamic routing is different to static routing in that the d-link firewall will adapt to changes of network topology or traffic load automatically. Netdefendos first learns of all the directly connec- ted networks and gets further route informatio...
Page 94: 4.4.2. Ospf
Path length the sum of the costs associated with each link. A commonly used value for this metric is called "hop count" which is the number of routing devices a packet must pass through when it travels from source to destination. Item bandwidth the traffic capacity of a path, rated by "mbps". Load t...
Page 95
Advertise externally learned routes throughout the autonomous system. Backbone areas all ospf networks need to have at least the backbone area, that is the area with id 0. This is the area that all other areas should be connected to, and the backbone make sure to distribute routing information betwe...
Page 96
Virtual links are used for: • linking an area that does not have a direct connection to the backbone. • linking the backbone in case of a partitioned backbone. Area without direct connection to the backbone the backbone always need to be the center of all other areas. In some rare case where it is i...
Page 97
Figure 4.3. Virtual links example 2 the virtual link is configured between fw1 and fw2 on area 1, as it is used as the transit area. In the configuration only the router id have to be configured, as in the example above show fw2 need to have a virtual link to fw1 with the router id 192.168.1.1 and v...
Page 98
In a dynamic routing environment, it is important for routers to be able to regulate to what extent they will participate in the routing exchange. It is not feasible to accept or trust all received routing information, and it might be crucial to avoid that parts of the routing database gets publishe...
Page 99
Ble. Specify the destination routing table that the routes should be added to, in this case main. Cli gw-world:/> cc dynamicroutingrule importospfroutes gw-world:/importospfroutes> add dynamicroutingruleaddroute destination=mainroutingtable web interface 1. Go to routing > dynamic routing rules 2. C...
Page 100
2. Click on the recently created exportdefroute. 3. Go to ospf action > add > dynamicroutingruleexportospf. 4. In the export to process control, choose as0. 5. Click ok. 4.4.3. Dynamic routing policy chapter 4. Routing 87.
Page 101: 4.5. Transparent Mode
4.5. Transparent mode 4.5.1. Overview of transparent mode deploying d-link firewalls operating in transparent mode into an existing network topology can significantly strengthen security. It is simple to do and doesn't require reconfiguration of existing nodes. Once deployed, netdefendos can then al...
Page 102
When beginning communication, a host will locate the target host's physical address by broadcast- ing an arp request. This request is intercepted by netdefendos and it sets up an internal arp transaction state entry and broadcasts the arp request to all the other switch-route interfaces ex- cept the...
Page 103
Example 4.8. Setting up transparent mode - scenario 1 web interface configure the interfaces: 1. Go to interfaces > ethernet > edit (wan) 2. Now enter: • ip address: 10.0.0.1 • network: 10.0.0.0/24 • default gateway: 10.0.0.1 • transparent mode: enable 3. Click ok. 4. Go to interfaces > ethernet > e...
Page 104
3. Click ok. Scenario 2 figure 4.5. Transparent mode scenario 2 here the d-link firewall in transparent mode separates server resources from an internal network by connecting them to a separate interface without the need for different address ranges. All hosts connected to lan and dmz (the lan and d...
Page 105
3. Specify a suitable name for the rule, for instance http-lan-to-dmz. 4. Enter following: • action: allow • source interface: lan • destination interface: dmz • source network: all-nets • destination network: 10.1.4.10 5. Under the service tab, choose http in the pre-defined control 6. Click the ok...
Page 106
• transparent mode: disable • add route for interface network: disable 3. Click ok. 4. Go to interfaces > ethernet > edit (dmz) 5. Now enter: • ip address: 10.0.0.2 • network: 10.0.0.0/24 • transparent mode: disable • add route for interface network: disable 6. Click ok. Configure the interface grou...
Page 107
• action: sat • service: http • source interface: wan • destination interface: dmz • source network: all-nets • destination network: wan_ip • translate: select destination ip • new ip address: 10.1.4.10 6. Click ok. 7. Go to rules > ip rules > add > iprule 8. Now enter: • name: http-wan-to-dmz • act...
Page 108
4.5.5. Transparent mode example scenarios chapter 4. Routing 95.
Page 109: Chapter 5. Dhcp Services
Chapter 5. Dhcp services this chapter describes dhcp services in netdefendos. • overview, page 96 • dhcp servers, page 97 • static dhcp assignment, page 99 • dhcp relaying, page 100 5.1. Overview dhcp (dynamic host configuration protocol) is a protocol that allows network administrators to automatic...
Page 110: 5.2. Dhcp Servers
5.2. Dhcp servers netdefendos has the ability to act as one or more logical dhcp servers. Filtering of dhcp client requests is based on interface, so each netdefendos interface can have, at most, one single logical dhcp server associated with it. In other words, netdefendos can provision dhcp client...
Page 111
Example 5.2. Checking the status of a dhcp server web interface 1. Select dhcp server in the status dropdown menu in the menu bar. Tip dhcp leases are remembered by the system between system restarts. 5.2. Dhcp servers chapter 5. Dhcp services 98.
Page 112
5.3. Static dhcp assignment where the administrator requires a fixed relationship between a client and the assigned ip address, netdefendos allows the assignment of a given ip to a specific mac address. Example 5.3. Setting up static dhcp this example shows how to assign the ip address 192.168.1.1 t...
Page 113: 5.4. Dhcp Relaying
5.4. Dhcp relaying with dhcp, clients send requests to locate the dhcp server(s) using broadcast messages. However, broadcasts are normally only propagated across the local network. This means that the dhcp server and client would always need to be in the same physical network area to be able to com...
Page 114
5.4. Dhcp relaying chapter 5. Dhcp services 101.
Page 115: 6.1. Access Rules
Chapter 6. Security mechanisms this chapter describes netdefendos security features. • access rules, page 102 • application layer gateways, page 105 • intrusion detection and prevention, page 125 • anti-virus, page 135 • web content filtering, page 140 • denial-of-service (dos) attacks, page 155 • b...
Page 116
Access rules can provide an anti-spoofing capability by providing an extra filter for source address verification. An access rule can verify that packets arriving at a given interface do not have a source address which is associated with a network of another interface. In other words: • any incoming...
Page 117
Of this. It is always advisable to check access rules when troubleshooting puzzling problems in case a rule is preventing some other function, such as vpn tunnel astablishment, from working properly. Example 6.1. Setting up an access rule a rule is to be defined that ensures no traffic with a source...
Page 118: 6.2.1. Overview
6.2. Application layer gateways 6.2.1. Overview to complement low-level packet filtering, which only inspects packet headers in protocols such ip, tcp, udp, and icmp, d-link firewalls provide application layer gateways (algs) which provide filtering at the higher application osi level. An alg act as...
Page 119
In active mode, the ftp client sends a command to the ftp server indicating what ip address and port the server should connect to. The ftp server establishes the data channel back to the ftp client using the received address information. In passive mode, the data channel is opened by the ftp client ...
Page 120
To make it possible to connect to this server from the internet using the ftp alg, the ftp alg and rules should be configured as follows: web interface define the alg: 1. Go to objects > alg > add > ftp alg 2. Enter name: ftp-inbound 3. Check allow client to use active mode 4. Uncheck allow server t...
Page 121
• name: sat-ftp-inbound • action: sat • service: ftp-inbound 3. For address filter enter: • source interface: any • destination interface: core • source network: all-nets • destination network: wan_ip (assuming the external interface has been defined as this) 4. For sat check translate the destinati...
Page 122
Example 6.3. Protecting ftp clients in this scenario shown below the d-link firewall is protecting a workstation that will connect to ftp servers on the internet. To make it possible to connect to these servers from the internal network using the ftp alg, the ftp alg and rules should be configured a...
Page 123
Are no rules disallowing or allowing the same kind of ports/traffic before these rules. The service in use is the "ftp- outbound", which should be using the alg definition "ftp-outbound" as described earlier. Allow connections to ftp-servers on the outside: 1. Go to rules > ip rules > add > iprule 2...
Page 124: 6.2.5. H.323
• mime checking - mail attachment file content can be checked against its filetype. A list of all filetypes checked can be found in appendix c, anti-virus mime filetypes. • anti-virus scanning - the netdefendos anti-virus module can scan email attachments searching for malicious code. • verify sende...
Page 125
H.245 media control and trans- port provides control of multimedia sessions established between two h.323 endpoints. Its most important task is to negotiate opening and closing of logical channels. A logical channel is, for instance, an audio channel used for voice communication. Video and t.120 cha...
Page 126
Registration by clients with the gatekeeper and less probability of a problem if the network be- comes unavailable and the client thinks it is still registered. Presented below are some network scenarios where h.323 alg use is applicable. For each scenario a configuration example of both the alg and...
Page 127
3. Click ok. Incoming rule: 1. Go to rules > ip rules > add > iprule 2. Enter the following: • name: h323allowin • action: allow • service: h323 • source interface: any • destination interface: lan • source network: 0.0.0.0/0 (all-nets) • destination network: lannet • comment: allow incoming calls 3...
Page 128
• service: h323 • source interface: any • destination interface: core • source network: 0.0.0.0/0 (all-nets) • destination network: wan_ip (external ip of the firewall) • comment: allow incoming calls to h.323 phone at ip-phone 3. For sat enter translate destination ip address: to new ip address: ip...
Page 129
Web interface outgoing rule: 1. Go to rules > ip rules > add > iprule 2. Now enter: • name: h323allowout • action: allow • service: h323 • source interface: lan • destination interface: any • source network: lannet • destination network: 0.0.0.0/0 (all-nets) • comment: allow outgoing calls 3. Click ...
Page 130
This scenario consists of two h.323 phones, each one connected behind the d-link firewall on a network with private ip addresses. In order to place calls on these phones over the internet, the following rules need to be ad- ded to the rule-set in the firewall, make sure there are no rules disallowin...
Page 131
• comment: allow incoming calls to h.323 phone at ip-phone 3. Click ok. To place a call to the phone behind the d-link firewall, place a call to the external ip address on the firewall. If multiple h.323 phones are placed behind the firewall, one sat rule has to be con- figured for each phone. This ...
Page 132
1. Go to rules > ip rules > add > iprule 2. Now enter: • name: h323in • action: allow • service: h323-gatekeeper • source interface: any • destination interface: core • source network: 0.0.0.0/0 (all-nets) • destination network: wan_ip (external ip of the firewall) • comment: allow incoming communic...
Page 133
Web interface 1. Go to rules > ip rules > add > iprule 2. Now enter: • name: h323out • action: nat • service: h323-gatekeeper • source interface: lan • destination interface: any • source network: lannet • destination network: 0.0.0.0/0 (all-nets) • comment: allow outgoing communication with a gatek...
Page 134
The head office has placed a h.323 gatekeeper in the dmz of the corporate d-link firewall. This firewall should be configured as follows: web interface 1. Go to rules > ip rules > add > iprule 2. Now enter: • name: lantogk • action: allow • service: gatekeeper • source interface: lan • destination i...
Page 135
• source interface: lan • destination interface: dmz • source network: lannet • destination network: ip-gateway • comment: allow h.323 entities on lannet to call phones connected to the h.323 gateway on the dmz. 3. Click ok. 1. Go to rules > ip rules > add > iprule 2. Now enter: • name: gwtolan • ac...
Page 136
• destination network: ip-gatekeeper • comment: allow communication with the gatekeeper on dmz from the remote network 3. Click ok. Example 6.11. Configuring remote offices for h.323 if the branch and remote office h.323 phones and applications are to be configured to use the h.323 gatekeeper at the...
Page 137
Note there is no need to specify a specific rule for outgoing calls. Netdefendos monitors the communication between "external" phones and the gatekeeper to make sure that it is possible for internal phones to call the external phones that are registered with the gatekeeper. 6.2.5. H.323 chapter 6. S...
Page 138: 6.3.1. Overview
6.3. Intrusion detection and prevention 6.3.1. Overview intrusion definition computer servers can sometimes have vulnerabilites which leave them exposed to attacks carried by network traffic. Worms, trojans and backdoor exploits are examples of such attacks which, if suc- cessful, can potentially co...
Page 139: 6.3.3. Idp Rules
D-link offers two types of idp: • maintenance idp is a basic idp system included as standard with the d-link dfl- 210/800/1600/2500 firewalls. This is a simplfied idp that gives basic protection against attacks. It is upgradeable to the professional level advanced idp. • advanced idp is a subscripti...
Page 140
Rule components an idp rule defines what kind of traffic, or service, should be analyzed. An idp rule is similar in makeup to an ip rule. An idp rule specifies a given combination source/destination interfaces/ad- dresses as well as being associated with a service object which defines which protocol...
Page 141
Believes it has the full data stream. The attacker now sends two futher packets, p2 and p3, which will be accepted by the application which can now complete reassembly but resulting in a different data stream to that seen by the idp subsystem. Evasion attacks an evasion attack has a similar end-resu...
Page 142
Recognising unknown threats attackers who build new intrusions often re-use older code. This means their new attacks can appear "in the wild" quickly. To counter this, d-link idp uses an approach where the module scans for these reusable components, with pattern matching looking for building blocks ...
Page 143
The group type is one of the values ids, ips or policy. These types are explained above. 2. Signature group category this second level of naming describes the type of application or protocol. Examples are: • backup • db • dns • ftp • http 3. Signature group sub-category the third level of naming fur...
Page 144: 6.3.7. Idp Actions
6.3.7. Idp actions action options after pattern matching recognises an intrusion in traffic subject to an idp rule, the action associ- ated with that rule is taken. The administrator can associate one of three action options with an idp rule: • ignore - do nothing if an intrusion is detected and all...
Page 145
Gw-world:/examplerule> set idpruleaction 1 logenabled=yes web interface adding an smtp log receiver: 1. Go to system > log and event receivers > add > smtp event receiver 2. Now enter: • name: smtp4idp • smtp server: smtp-server • server port: 25 • specify alternative e-mail addresses (up to 3) • se...
Page 146
Cli create idp rule: gw-world:/> add idprule service=smtp sourceinterface=wan sourcenetwork=wannet destinationinterface=dmz destinationnetwork=ip_mailserver name=idpmailsrvrule create idp action: gw-world:/> cc idprule idpmailsrvrule gw-world:/idpmailsrvrule> add idpruleaction action=protect idpserv...
Page 147
When this idp rule has been created, an action must also be created, specifying what signatures the idp should use when scanning data matching the idp rule, and what netdefendos should do in case an intrusion is dis- covered. Intrusion attempts should cause the connection to be dropped, so action is...
Page 148: 6.4. Anti-Virus
6.4. Anti-virus 6.4.1. Overview the netdefendos anti-virus module protects against malicious code carried in file downloads. Files may be downloaded as part of a web-page in an http transfer, in an ftp download, or per- haps as an attachment to an email delivered through smtp. Malicious code in such...
Page 149: 6.4.3. Activation
There is no fixed limit on how many anti-virus scans can take place simultaneously in a single d- link firewall. However the available free memory can place a limit on the number of concurrent scans that can be initiated. The administrator can increase the default amount of free memory avail- able t...
Page 150: 6.4.6. Anti-Virus Options
6.4.6. Anti-virus options when configuring anti-virus scanning in an alg, the following parameters can be set: 1. General options mode when enabled anti-virus is active verify mime type the mime type identifies a file's type. For instance a file might be identified as being of type .Gif and therefor...
Page 151
To prevent this situation, the adminstrator should specify a compression ratio limit. If the limit of the ration is specified as 10 then this will mean that if the uncompressed file is 10 times larger than the compressed file, the specified action should be taken. The action can be one of: • allow -...
Page 152
3. Click the service tab 4. Select your new service, http_anti_virus, in the pre-defined service dropdown list 5. Click ok anti-virus scanning is now activated for all web traffic from lannet to all-nets. 6.4.6. Anti-virus options chapter 6. Security mechanisms 139.
Page 153: 6.5.1. Overview
6.5. Web content filtering 6.5.1. Overview web traffic is one of the biggest sources for security issues and misuse of the internet. Inappropriate surfing habits can expose a network to many security threats as well as legal and regulatory liabilit- ies. Productivity and internet bandwidth can also ...
Page 154
Example 6.16. Stripping activex and java applets this example shows how to configure a http application layer gateway to strip activex and java applets. The example will use the content_filtering alg object and presumes you have done one of the previous examples. Cli gw-world:/> set alg alg_http con...
Page 155
Blocks all sites ending with example.Com. Note web content filtering url blacklisting is a separate concept from section 6.7, “blacklisting hosts and networks”. Example 6.17. Setting up a white and blacklist this example shows the use of static content filtering where netdefendos can block or permit...
Page 156
6.5.4. Dynamic content filtering 6.5.4.1. Overview netdefendos supports dynamic content filtering of web traffic, which enables an administrator to permit or block access to web pages based on the content of those web pages. This functionality is automated and it is not necessary to manually specify...
Page 157
Will automatically be downloaded to d-link's central data warehouse and automatically analyzed using a combination of techniques including neural networks and pattern matching. Once categor- ized, the url is distributed to the global databases and netdefendos receives the category for the url. Dynam...
Page 158
3. Click the web content filtering tab. 4. Select enabled in the mode dropdown list. 5. In the blocked categories list, select search sites and click the >> button. 6. Click ok. Then, create a service object using the new http alg: 1. Go to local objects > services > add > tcp/udp service 2. Specify...
Page 159
Gw-world:/> add alg alg_http content_filtering webcontentfilteringmode=audit filteringcategories=search_sites web interface first, create an http application layer gateway (alg) object: 1. Go to objects > alg > add > http alg 2. Specify a suitable name for the alg, for instance content_filtering 3. ...
Page 160
Example 6.20. Reclassifying a blocked site this example shows how a user may propose a reclassification of a web site if he believes it is wrongly classified. This mechanism is enabled on a per-http alg level basis. Cli first, create an http application layer gateway (alg) object: gw-world:/> add al...
Page 161
• www.Fullonxxx.Com category 2: news a web site may be classified under the news category if its content includes information articles on recent events pertaining to topics surrounding a locality (eg. A town, city or nation) or culture, in- cluding weather forecasting information. Typically this wou...
Page 162
Isement of goods or services to be exchanged for money, and may also include the facilities to per- form that transaction online. Included in this category are market promotions, catalogue selling and merchandising services. Examples might be: • www.Megamall.Com • www.Buy-alcohol.Se category 7: ente...
Page 163
Category 11: investment sites a web site may be classified under the investment sites category if its content includes information, services or facilities pertaining to personal investment. Urls in this category include contents such as brokerage services, online portfolio setup, money management fo...
Page 164
Category 16: sports a web site may be classified under the sports category if its content includes information or instruc- tions relating to recreational or professional sports, or reviews on sporting events and sports scores. Examples might be: • www.Sportstoday.Com • www.Soccerball.Com category 17...
Page 165
Category 21: health sites a web site may be classified under the health sites category if its content includes health related in- formation or services, including sexuality and sexual health, as well as support groups, hospital and surgical information and medical journals. Examples might be: • www....
Page 166
That relates to educational services or has been deemed of educational value, or to be an educational resource, by educational organisations. This category is populated by request or submission from various educational organisations. Examples might be: • highschoolessays.Org • www.Learn-at-home.Com ...
Page 167
• kaqsovdij.Gjibhgk.Info • www.Pleaseupdateyourdetails.Com category 32: non-managed unclassified sites and sites that don't fit one of the other categories will be placed in this category. It is unusual to block this category since this could result in most harmless urls being blocked. 6.5.4. Dynami...
Page 168: 6.6.1. Overview
6.6. Denial-of-service (dos) attacks 6.6.1. Overview by embracing the internet, enterprises experience new business opportunities and growth. The en- terprise network and the applications that run over it are business critical. Not only can a company reach a larger number of customers via the intern...
Page 169: Boink And Nestea
To run "ping -l 65510 1.2.3.4" on a windows 95 system where 1.2.3.4 is the ip address of the inten- ded victim. "jolt" is simply a purpose-written program for generating such packets on operating sys- tems whose ping commands refuse to generate oversized packets. The triggering factor is that the la...
Page 170
Vices expected to only serve the local network. • by stripping the urg bit by default from all tcp segments traversing the system (configurable via advanced settings > tcp > tcpurg). Winnuke attacks will usually show up in netdefendos logs as normal drops with the name of the rule in your policy tha...
Page 171: 6.6.9. The Jolt2 Attack
The traffic shaping feature built into netdefendos also help absorb some of the flood before it reaches protected servers. 6.6.8. Tcp syn flood attacks the tcp syn flood attack works by sending large amounts of tcp syn packets to a given port and then not responding to syn acks sent in response. Thi...
Page 172
6.7. Blacklisting hosts and networks netdefendos implements a blacklist of host or network ip addresses which can be utilized to pro- tect against traffic coming from specific internet sources. Certain netdefendos modules, specifically the intrusion detection and prevention (idp) module, as well as ...
Page 173
6.7. Blacklisting hosts and networks chapter 6. Security mechanisms 160
Page 174
Chapter 7. Address translation this chapter describes netdefendos address translation capabilites. • dynamic address translation (nat), page 161 • static address translation (sat), page 164 netdefendos supports two types of address translation: dynamic address translation (nat) and static address tr...
Page 175
1. The sender, e.G. 192.168.1.5, sends a packet from a dynamically assigned port, for instance, port 1038, to a server, e.G. 195.55.66.77 port 80. 192.168.1.5:1038 => 195.55.66.77:80 2. In this example, the use interface address option is used, and we will use 195.11.22.33 as the interface address. ...
Page 176
Dresses, destination addresses and protocol numbers. This means that: • an internal machine can communicate with several external servers using the same ip protocol. • an internal machine can communicate with several external servers using different ip protocols. • several internal machines can comm...
Page 177
7.2. Static address translation (sat) netdefendos can translate entire ranges of ip addresses and/or ports. Such translations are trans- positions, that is, each address or port is mapped to a corresponding address or port in the new range, rather than translating them all to the same address or por...
Page 178
1. Go to rules > ip rules > add > iprule 2. Specify a suitable name for the rule, for instance allow_http_to_dmz. 3. Now enter: • action: allow • service: http • source interface: any • source network: all-nets • destination interface: core • destination network: wan_ip 4. Under the service tab, sel...
Page 179
This increases the number of rules for each interface allowed to communicate with the web server. However, the rule ordering is unimportant, which may help avoid errors. If option 2 was selected, the rule-set must be adjusted thus: # action src iface src net dest iface dest net parameters 1 sat any ...
Page 180
This reply arrives directly to pc1 without passing through the d-link firewall. This causes problems. The reason this will not work is because pc1 expects a reply from 195.55.66.77:80, not 10.0.0.2:80. The unexpected reply is discarded and pc1 continues to wait for a response from 195.55.66.77:80, w...
Page 181
Example 7.4. Translating traffic to multiple protected web servers in this example, we will create a sat policy that will translate and allow connections from the internet to five web servers located in a dmz. The d-link firewall is connected to the internet using the wan interface, and the public i...
Page 182
1. Go to interfaces > arp > add > arp 2. Now enter: • mode: publish • interface: wan • ip address: 195.55.66.77 3. Click ok and repeat for all the five public ip addresses. Create a sat rule for the translation: 1. Go to rules > ip rules > add > iprule 2. Specify a suitable name for the rule, for in...
Page 183: 7.2.4. Port Translation
And 194.1.2.30) to the ip 192.168.0.50. • attempts to communicate with 194.1.2.16, port 80, will result in a connection to 192.168.0.50 • attempts to communicate with 194.1.2.30, port 80, will result in a connection to 192.168.0.50 note when 0.0.0.0/0 is the destination, all-to-one mapping is always...
Page 184
Designed to read and/or alter application data. These are commonly referred to as application layer gateways or application layer filters. Netdefendos supports a number of such application layer gateways and for more information please see section 6.2, “application layer gateways”. 7.2.6. Which sat ...
Page 185
• return traffic from wwwsrv:80 will match rules 2 and 4, and will appear to be sent from wan_ip:80. Correct. • internal traffic to wan_ip:80 will match rules 1 and 3, and will be sent to wwwsrv. Almost cor- rect; the packets will arrive at wwwsrv, but: • return traffic from wwwsrv:80 to internal ma...
Page 186
7.2.7. Sat and fwdfast rules chapter 7. Address translation 173.
Page 187: 8.1. Overview
Chapter 8. User authentication this chapter describes how netdefendos implements user authentication. • overview, page 174 • authentication components, page 176 • authentication process, page 178 8.1. Overview before any user service request is authorized by firewall's security policies, netdefendos...
Page 188: 8.1.3. User Types
• changed on a regular basis good passwords help secure networks, including layer 2 tunnels, which use passwords for encryp- tion. 8.1.3. User types netdefendos has authentication schemes which support diverse user types. These can be: • administrators • normal users accessing a network • pppoe/pptp...
Page 189
8.2. Authentication components netdefendos can either use a locally stored database, or a database on an external server to provide user authentication. 8.2.1. The local user database (userdb) the local user database is a built-in registry inside netdefendos which contains the profiles of authorized...
Page 190
8.2.4. Authentication rules a user authentication rule specifies: • from where (i.E. Receiving interface, source network) users are allowed to authenticate them- selves at the firewall. • which agent will be used by netdefendos to prompt users for authentication. • where is the location of the datab...
Page 191
8.3. Authentication process netdefendos performs user authentication in the following series of steps: • a user creates a new connection to the firewall. • netdefendos sees the new user connection on an interface, and checks the ip rule-set to see if their is an authentication policy set for traffic...
Page 192
• groups: one user can be specified into more than one group. Enter the group names here separated by comma, e.G. "users" for this example. 3. Click ok. 4. Repeat step b. To add all the "lannet" users having the membership of "users" group into the lan- net_auth_users folder. Note there are two defa...
Page 193
8.3. Authentication process chapter 8. User authentication 180
Page 194: 9.1. Vpn Overview
Chapter 9. Virtual private networks this chapter describes vpn usage with netdefendos. • vpn overview, page 181 • ipsec, page 183 • ipsec tunnels, page 196 • pptp/l2tp, page 202 9.1. Vpn overview 9.1.1. The need for vpns most networks today are connected to each other by the internet. Business incre...
Page 195
• protecting mobile and home computers • restricting access through the vpn to needed services only, since mobile computers are vulner- able • creating dmzs for services that need to be shared with other companies through vpns • adapting vpn access policies for different groups of users • creating k...
Page 196: 9.2. Ipsec
9.2. Ipsec 9.2.1. Ipsec basics 9.2.1.1. Introduction to ipsec ipsec, internet protocol security, is a set of protocols defined by the ietf, internet engineering task force, to provide ip security at the network layer. An ipsec based vpn is made up by two parts: • internet key exchange protocol (ike)...
Page 197
Ike negotiation the process of negotiating session parameters consists of a number of phases and modes. These are described in detail in the below sections. The flow of events can summarized as follows: ike phase-1 • negotiate how ike should be protected ike phase-2 • negotiate how ipsec should be p...
Page 198
Ike phase-2 - ipsec security negotiation in phase two, another negotiation is performed, detailing the parameters for the ipsec connection. In phase-2 we will also extract new keying material from the diffie-hellman key exchange in phase-1, to provide session keys to use in protecting the vpn data f...
Page 199
Remote address as the remote gateway. This is particularly useful in cases of roaming access, where the ip addresses of the remote vpn clients are not known beforehand. Setting this to "none" will allow anyone coming from an ip address conforming to the "remote network" address discussed above to op...
Page 200
Des is only included to be interoperable with other older vpn implementations. Use of des should be avoided whenever possible, since it is an old algorithm that is no longer considered secure. Ike authentication this specifies the authentication algorithms used in the ike negotiation phase. The algo...
Page 201
Without encryption. The algorithms supported by d-link firewall vpns are: • aes • blowfish • twofish • cast128 • 3des • des ipsec authentication this specifies the authentication algorithm used on the pro- tected traffic. This is not used when esp is used without authentication, al- though it is not...
Page 202
Cryption/authentication key always, no anti-replay services, and it is not very flexible. There is also no way of assuring that the remote host/firewall really is the one it says it is. This type of connection is also vulnerable for something called "replay attacks", meaning a mali- cious entity whi...
Page 203
There are two protocols associated with ipsec, ah and esp. These are covered in the sections be- low. Ah (authentication header) ah is a protocol used for authenticating a data stream. It uses a cryptographic hash function to pro- duce a mac from the data in the ip packet. This mac is then transmitt...
Page 204
9.2.1.5. Nat traversal both ike and ipsec protocols present a problem in the functioning of nat. Both protocols were not designed to work through nats and because of this, a technique called "nat traversal" has evolved. Nat traversal is an add-on to the ike and ipsec protocols that allows them to fu...
Page 205: 9.2.2. Proposal Lists
• dns - a dns address can be manually entered • e-mail - an email address can be manually entered 9.2.2. Proposal lists to agree on the vpn connection parameters, a negotiation process is performed. As the result of the negotiations, the ike and ipsec security associations (sas) are established. As ...
Page 206: 9.2.3. Pre-Shared Keys
Then, apply the proposal list to the ipsec tunnel: 1. Go to interfaces > ipsec 2. In the grid control, click the target ipsec tunnel 3. Select the recently created esp-l2tptunnel in the ipsec algorithms control. 4. Click ok 9.2.3. Pre-shared keys pre-shared keys are used to authenticate vpn tunnels....
Page 207
Roaming clients. Consider the scenario of travelling employees being given access to the internal corporate networks using vpn clients. The organization administers their own certificate authority, and certificates have been issued to the employees. Different groups of employees are likely to have a...
Page 208
• common name: john doe • organization name:d-link • organizational unit: support • country: sweden • email address: john.Doe@d-link.Com 6. Click ok. Finally, apply the identification list to the ipsec tunnel: 1. Go to interfaces > ipsec 2. In the grid control, click on the ipsec tunnel object of in...
Page 209: 9.3. Ipsec Tunnels
9.3. Ipsec tunnels 9.3.1. Overview of ipsec tunnels an ipsec tunnel defines an endpoint of an encrypted tunnel. Each ipsec tunnel is interpreted as a logical interface by netdefendos, with the same filtering, traffic shaping and configuration capabil- ities as regular interfaces. When another d-link...
Page 210
Computer from different locations is a typical example of a roaming client. Apart from the need for secure vpn access, the other major issue with roaming clients is that the mobile user's ip address is often not known beforehand. To handle the unknown ip address the netdefendos can dynamically add r...
Page 211
5. Under the routing tab: • enable the option: dynamically add route to the remote network when a tunnel is established. 6. Click ok. C. Finally configure the ip rule-set to allow traffic inside the tunnel. 9.3.3.2. Self-signed certificate based client tunnels example 9.5. Setting up a self-signed c...
Page 212
3. For algorithms enter: • ike algorithms: medium or high. • ipsec algorithms: medium or high. 4. For authentication enter: • choose x.509 certificate as authentication method • root certificate(s): select all your client certificates and add them to the selected list • gateway certificate: choose y...
Page 213
1. Go to objects > vpn objects > id list > add > id list 2. Enter a descriptive name, in this example sales. 3. Click ok. 4. Go to objects > vpn objects > id list > sales > add > id 5. Enter the name for the client. 6. Select email as type. 7. In the email address field, enter the email address sele...
Page 214
Cli gw-world:/> add ldapserver host=192.168.101.146 username=myusername password=mypassword port=389 web interface 1. Go to objects > vpn objects > ldap > add > ldap server 2. Now enter: • ip address: 192.168.101.146 • username: myusername • password: mypassword • confirm password: mypassword • port...
Page 215: 9.4. Pptp/l2Tp
9.4. Pptp/l2tp the access by a client using a modem link over dial-up public switched networks, possibly with an unpredictable ip address, to protected networks via a vpn poses particular problems. Both the pptp and l2tp protocols provide two different means of achieving vpn access from remote cli- ...
Page 216: 9.4.2. L2Tp
Cli gw-world:/> add interface l2tpserver mypptpserver serverip=lan_ip interface=any ip=wan_ip ippool=pp2p_pool tunnelprotocol=pptp allowedroutes=all-nets web interface 1. Go to interfaces > l2tp servers > add > l2tpserver 2. Enter a name for the pptp server e.G. Mypptpserver. 3. Now enter: • inner i...
Page 217
2. Enter a suitable name for the l2tp server, for instance myl2tpserver. 3. Now enter: • inner ip address: ip_l2tp • tunnel protocol: l2tp • outer interface filter: l2tp_ipsec • outer server ip: wan_ip 4. Under the ppp parameters tab, select l2tp_pool in the ip pool control. 5. Under the add route t...
Page 218
Ipsecalgorithms=esp-l2tptunnel psk=mypsk encapsulationmode=transport dhcpoveripsec=yes addroutetoremotenet=yes ipseclifetimekilobytes=250000 ipseclifetimeseconds=3600 web interface 1. Go to interfaces > ipsec > add > ipsec tunnel 2. Enter a name for the ipsec tunnel e.G. L2tp_ipsec. 3. Now enter: a....
Page 219
7. In the proxyarp control, select the lan interface. 8. Click ok in order to authenticate the users using the l2tp tunnel, a user authentication rule needs to be configured. 4. Next will be setting up the authentication rules: cli gw-world:/> add userauthrule authsource=local interface=l2tp_tunnel ...
Page 220
5. Go to rules > ip rules > add > iprule 6. Enter a name for the rule e.G. Natl2tp 7. Now enter: • action: nat • service: all_services • source interface: l2tp_tunnel • source network: l2tp_pool • destination interface: any • destination network: all-nets 8. Click ok 9.4.2. L2tp chapter 9. Virtual p...
Page 221
9.4.2. L2tp chapter 9. Virtual private networks 208.
Page 222: 10.1. Traffic Shaping
Chapter 10. Traffic management this chapter describes how netdefendos can manage network traffic. • traffic shaping, page 209 • threshold rules, page 221 • server load balancing, page 223 10.1. Traffic shaping 10.1.1. Introduction a weakness of the tcp/ip protocol is the lack of true quality of serv...
Page 223
• prioritizing traffic according to the administrator's choice; if the traffic in a higher priority in- creases while a communications line is full, traffic in lower priorities should be temporarily lim- ited to make room for the high-priority traffic. • providing bandwidth guarantees. This is typic...
Page 224: 10.1.4. Pipes Basics
10.1.4. Pipes basics 10.1.4.1. Definition of a pipe a pipe is a central concept in the traffic shaping functionality of netdefendos and is the basis for all bandwidth control. Pipes are configured in the pipes section of the firewall configuration. Pipes are fairly simplistic, in that they do not kn...
Page 225
1. Go to traffic management > traffic shaping > pipes > add > pipe 2. Specify a suitable name for the pipe, for instance std-in. 3. Enter 2000 in total textbox. 4. Click ok. However, simply creating the pipe will not accomplish much; traffic actually needs to be passed through the pipe. This is done...
Page 226
However, you cannot just raise the total limit to 4 mbps and hope for the best. Why? Again, pipes are simple things. This single pipe will not know that you mean 2 mbps inbound and 2 mbps out- bound. You could just as well end up with 3 mbps outbound and 1 mbps inbound, since that, too, adds up to 4...
Page 227
Now that we have the pipe defined, what do we do with it? Well, first we will need to set up a rule that covers surfing and place it before the rule that covers "everything else". This way we can get surfing traffic to go through the specific pipes that we want it to, but still let everything else b...
Page 228
Note the respective precedences are not "special" in any way. Their meaning is only defined by the limits and guarantees that you configure. The difference is only in relat- ive importance: traffic in precedence 2 will be passed on before traffic in precedence 0, traffic in precedence 4 before 2 and...
Page 229
10.1.5.2. Applying simple priorities now, how can we use precedences to make some types of traffic more important than others? Let's continue work on our previous example, by giving ssh and telnet traffic a higher priority than everything else passing through our pipes. For this first example, we do...
Page 230
"which traffic is more important?" problem. The solution here is to create two new pipes: one for telnet traffic, and one for ssh traffic, much like the "surf" pipe that we created earlier on. First, remove the 96 kbps limit from the std-in pipe, then create two new pipes: "ssh-in" and "telnet- in"....
Page 231
Measuring and shaping at the entrance of a choke point if you are protecting the "entrance" to a network bottleneck, i.E. Outbound data in your firewall, you can probably set the total limit very close to the bandwidth of your connection. Measuring and shaping at the exit of a choke point if you're ...
Page 232
10.1.6. Grouping users of a pipe 10.1.6.1. Overview if pipes were restricted to the functionality described so far, traffic would be limited without respect to source or destination. This mode of operation is likely sufficient for managing simple traffic lim- its and guarantees. However the ability ...
Page 233
Each inside user gets for inbound ssh traffic. This keeps one single user from using up all available high-priority bandwidth. First, we will have to figure out how to group the users of the ssh-in pipe. What we want to do is ap- ply our limits to each user on the internal network. Considering that ...
Page 234: 10.2. Threshold Rules
10.2. Threshold rules 10.2.1. Overview the objective of a threshold rule is to have a means of detecting abnormal connection activity as well as reacting to it. An example of a cause for such abnormal activity might be an internal host be- coming infected with a virus that is making repeated connect...
Page 235
10.2.5. Multiple triggered actions when a rule is triggered then netdefendos will perform the associated rule actions that match the condition that has occured. If more than one action matches the condition then those matching ac- tions are applied in the order they appear in the user interface. If ...
Page 236: 10.3.1. Overview
10.3. Server load balancing 10.3.1. Overview the server load balancing (slb) feature in netdefendos is a powerful tool that can improve the following aspects of network applications: • performance • scalability • reliability • ease of administration slb allows network service demands to be shared am...
Page 237
Slb also means that network administrators can perform maintenance tasks on servers or applica- tions without disrupting services. Individual servers can be restarted, upgraded, removed, or re- placed, and new servers and applications can be added or moved without affecting the rest of a serv- er fa...
Page 238
Gorithm cycles through the server list and redirects the load to servers in or- der. Regardless of each server's capability and other aspects, for instance, the number of existing connections on a server or its response time, all the available servers take turns in being assigned the next connection...
Page 239: 10.3.6. Slb_Sat Rules
If connection rate is applied instead, r1 and r2 will be sent to the same server because of sticki- ness, but the subsequent requests r3 and r4 will be routed to another server since the number of new connections on each server within the window time span is counted in for the distribution. Figure 1...
Page 240
The key component in setting up slb is the slb_sat rule in the ip rule-set. The steps that should be followed are: 1. Define an object for each server for which slb is to be done. 2. Define a group which included all these objects 3. Define an slb_sat rule in the ip rule-set which refers to this gro...
Page 241
10.3.6. Slb_sat rules chapter 10. Traffic management 228.
Page 242: 11.1. Overview
Chapter 11. High availability this chapter describes the high availability fault-tolerance feature in d-link firewalls. • overview, page 229 • how rapid failover is accomplished, page 231 • high availability issues, page 233 11.1. Overview high availability (ha) is a fault-tolerant capability that i...
Page 243
Broken interfaces will not be detected by the current implementation of d-link high availability, unless they are broken to the point where the firewall cannot continue to run. This means that fail- over will not occur if the active firewall can communicate "being alive" to the inactive firewall thr...
Page 244: 11.2.2. Cluster Heartbeats
11.2. How rapid failover is accomplished this section will detail the outward-visible characteristics of the failover mechanism, and how the two firewalls work together to create a high availability cluster with very low failover times. For each cluster interface, there are three ip addresses: • two...
Page 245
When three heartbeats are missed, i.E. After 0.6 seconds, the peer will be deemed inoperative. So, why not make it even faster? Maybe send a hundred heartbeats per second and declare a firewall inoperative after missing only two of them? This would after all result in a 0.02-second failover time. Th...
Page 246
11.3. High availability issues even though a high availability cluster will behave like a single firewall in most respects, there are some things which should be kept in mind when managing and configuring it. 11.3.1. High availability configuration when configuring high availability clusters, there ...
Page 247
11.3.1. High availability configuration chapter 11. High availability 234.
Page 248: Chapter 12. Zonedefense
Chapter 12. Zonedefense this chapter describes the d-link zonedefense feature. • overview, page 235 • zonedefense switches, page 236 • zonedefense operation, page 237 12.1. Overview zonedefense allows a d-link firewall to control locally attached switches. It can be used as a counter-measure to stop...
Page 249: 12.2. Zonedefense Switches
12.2. Zonedefense switches switch information regarding every switch that is to be controlled by the firewall has to be manually specified in the firewall configuration. The information needed in order to control a switch includes: • the ip address of the management interface of the switch • the swi...
Page 250: 12.3.1. Snmp
12.3. Zonedefense operation 12.3.1. Snmp simple network management protocol (snmp) is an application layer protocol for complex net- work management. Snmp allows the managers and managed devices in a network to communicate with each other. Snmp managers a typical managing device, such as a d-link fi...
Page 251
12.3.3. Manual blocking and exclude lists as a complement to threshold rules, it is also possible to manually define hosts and networks that are to be statically blocked or excluded. Manually blocked hosts and networks can be blocked by default or based on a schedule. It is also possible to specify ...
Page 252: 12.3.4. Limitations
1. Go to zone defense > exclude list 2. For addresses choose the object name of the firewall's interface address 192.168.1.1 from the available list and put it into the selected list. 3. Click ok. Configure an http threshold of 10 connections/second: 1. Go to traffic management > threshold rules > a...
Page 253
12.3.4. Limitations chapter 12. Zonedefense 240
Page 254: 13.1. Ip Level Settings
Chapter 13. Advanced settings this chapter describes the configurable advanced setings for netdefendos. The settings are divided up into the following categories: • ip level settings, page 241 • tcp level settings, page 245 • icmp level settings, page 249 • arp settings, page 250 • stateful inspecti...
Page 255: Lognonip4
Based on illegal checksums. Default: enabled lognonip4 logs occurrences of ip packets that are not version 4. Netdefendos only accepts version 4 ip pack- ets; everything else is discarded. Default: 256 logreceivedttl0 logs occurrences of ip packets received with the "time to live" (ttl) value set to...
Page 256: Layersizeconsistency
Default: 255 layersizeconsistency verifies that the size information contained in each "layer" (ethernet, ip, tcp, udp, icmp) is con- sistent with that of other layers. Default: validatelogbad ipoptionsizes verifies the size of "ip options". These options are small blocks of information that may be ...
Page 257
Strip the don’t fragment flag for packets equal to or smaller than the size specified by this setting. Default: 65535 bytes stripdfonsmall chapter 13. Advanced settings 244.
Page 258: 13.2. Tcp Level Settings
13.2. Tcp level settings tcpoptionsizes verifies the size of tcp options. This function acts in the same way as ipoptionsizes described above. Default: validatelogbad tcpmssmin determines the minimum permissible size of the tcp mss. Packets containing maximum segment sizes below this limit are handl...
Page 259: Tcpzerounusedack
Default: 7000 bytes tcpzerounusedack determines whether netdefendos should set the ack sequence number field in tcp packets to zero if it is not used. Some operating systems reveal sequence number information this way, which can make it easier for intruders wanting to hijack established connections....
Page 260: Tcpopt_Cc
To transport alternate checksums where permitted by altchkreq above. Normally never seen on modern networks. Default: striplog tcpopt_cc determines how netdefendos will handle connection count options. Default: striplogbad tcpopt_other specifies how netdefendos will deal with tcp options not covered...
Page 261: Tcprf
Specifies how netdefendos will deal with tcp packets with either the xmas or ymas flag turned on. These flags are currently mostly used by os fingerprinting. Note: an upcoming standard called explicit congestion notification also makes use of these tcp flags, but as long as there are only a few oper...
Page 262: 13.3. Icmp Level Settings
13.3. Icmp level settings icmpsendperseclimit specifies the maximum number of icmp messages netdefendos may generate per second. This in- cludes ping replies, destination unreachable messages and also tcp rst packets. In other words, this setting limits how many rejects per second may be generated b...
Page 263: 13.4. Arp Settings
13.4. Arp settings arpmatchenetsender determines if netdefendos will require the sender address at ethernet level to comply with the hardware address reported in the arp data. Default: droplog arpquerynosenderip what to do with arp queries that have a sender ip of 0.0.0.0. Such sender ips are never ...
Page 264: Arpexpire
Arpexpire specifies how long a normal dynamic item in the arp table is to be retained before it is removed from the table. Default: 900 seconds (15 minutes) arpexpireunknown specifies how long netdefendos is to remember addresses that cannot be reached. This is done to ensure that netdefendos does n...
Page 265: Logconnectionusage
13.5. Stateful inspection settings logconnectionusage this generates a log message for every packet that passes through a connection that is set up in the netdefendos state engine. Traffic whose destination is the d-link firewall itself eg. Netdefendos management traffic, is not subject to this sett...
Page 266
• nolog – does not log any connections; consequently, it will not matter if logging is enabled for either allow or nat rules in the rules section; they will not be logged. However, fwdfast, drop and reject rules will be logged as stipulated by the settings in the rules section. • log – logs connecti...
Page 267: 13.6. Connection Timeouts
13.6. Connection timeouts the settings in this section specify how long a connection can remain idle, i.E. No data being sent through it, before it is automatically closed. Please note that each connection has two timeout val- ues: one for each direction. A connection is closed if either of the two ...
Page 268: Maxtcplen
13.7. Size limits by protocol this section contains information about the size limits imposed on the protocols directly under ip level, i.E. Tcp, udp, icmp, etc the values specified here concern the ip data contained in packets. In the case of ethernet, a single packet can contain up to 1480 bytes o...
Page 269: Maxipiplen
Specifies the maximum size of an ospf packet. Ospf is a routing protocol mainly used in larger lans. Default: 1480 maxipiplen specifies the maximum size of an ip-in-ip packet. Ip-in-ip is used by checkpoint firewall-1 vpn connections when ipsec is not used. This value should be set at the size of th...
Page 270: Pseudoreass_Maxconcurrent
13.8. Fragmentation settings ip is able to transport up to 65536 bytes of data. However, most media, such as ethernet, cannot carry such huge packets. To compensate, the ip stack fragments the data to be sent into separate packets, each one given their own ip header and information that will help th...
Page 271: Fragreassemblyfail
Default: check8 – compare 8 random locations, a total of 32 bytes fragreassemblyfail reassemblies may fail due to one of the following causes: • some of the fragments did not arrive within the time stipulated by the reasstimeout or reas- stimelimit settings. This may mean that one or more fragments ...
Page 272: Fragmentedicmp
Up. Possible settings are as follows: • nolog - no logging is carried out under normal circumstances. • logsuspect - logs duplicated fragments if the reassembly procedure has been affected by "sus- pect" fragments. • logall - always logs duplicated fragments. Default: logsuspect fragmentedicmp other...
Page 273
Order to prevent further fragments of that packet from arriving. Default: 60 seconds reassillegallinger chapter 13. Advanced settings 260
Page 274: Localreass_Maxconcurrent
13.9. Local fragment reassembly settings localreass_maxconcurrent maximum number of concurrent local reassemblies. Default: 256 localreass_maxsize maximum size of a locally reassembled packet. Default: 10000 localreass_numlarge number of large ( over 2k) local reassembly buffers (of the above size)....
Page 275: 13.10. Dhcp Settings
13.10. Dhcp settings dhcp_minimumleasetime minimum lease time (seconds) accepted from the dhcp server. Default: 60 dhcp_validatebcast require that the assigned broadcast address is the highest address in the assigned network. Default: enabled dhcp_allowglobalbcast allow dhcp server to assign 255.255...
Page 276: 13.11. Dhcprelay Settings
13.11. Dhcprelay settings dhcprelay_maxtransactions maximum number of transactions at the same time. Default: 32 dhcprelay_transactiontimeout for how long a dhcp transaction can take place. Default: 10 seconds dhcprelay_maxppmperiface how many dhcp-packets a client can send to through netdefendos to...
Page 277: 13.12. Dhcpserver Settings
13.12. Dhcpserver settings dhcpserver_saveleasepolicy what policy should be used to save the lease database to the disk, possible settings are disabled, re- confshut, or reconfshuttimer. Default: reconfshut dhcpserver_autosaveleaseinterval how often should the leases database be saved to disk if dhc...
Page 278: 13.13. Ipsec Settings
13.13. Ipsec settings ikesendinitialcontact determines whether or not ike should send the "initial contact" notification message. This message is sent to each remote gateway when a connection is opened to it and there are no previous ipsec sa using that gateway. Default: enabled ikesendcrls dictates...
Page 279
Ipsecdeletesaonipvalidationfailure controls what happens to the sas if ip validation in config mode fails. If enabled, the sas are dropped on failure. Default: disabled ipsecdeletesaonipvalidationfailure chapter 13. Advanced settings 266.
Page 280: Transp_Camtol3Cdestlearning
13.14. Transparent mode settings transp_camtol3cdestlearning enable this if the firewall should be able to learn the destination for hosts by combining destination address information and information found in the cam table. Default: enabled transp_decrementttl enable this if the ttl should be decrem...
Page 281: Multicastenetsender
Default: droplog multicastenetsender defines what to do when receiving a packet that has the sender hardware (mac) address in ethernet header set to a multicast ethernet address. Options: • accept - accept packet • acceptlog - accept packet and log • rewrite - rewrite to the mac of the forwarding in...
Page 282: 13.15. Logging Settings
13.15. Logging settings logsendperseclimit this setting limits how many log packets netdefendos may send out per second. This value should never be set too low, as this may result in important events not being logged, nor should it be set too high. One situation where setting too high a value may ca...
Page 283: Clusterid
13.16. High availability settings clusterid a (locally) unique cluster id to use in identifying this group of ha d-link firewalls. Default: 0 hasyncbufsize how much sync data, in kb, to buffer while waiting for acknowledgments from the cluster peer. Default: 1024 hasyncmaxpktburst the maximum number...
Page 284: Timesync_Syncinterval
13.17. Time synchronization settings timesync_syncinterval seconds between each resynchronization. Default: 86400 timesync_maxadjust maximum time drift that a server is allowed to adjust. Default: 3600 timesync_servertype type of server for time synchronization, udptime or sntp (simple network time ...
Page 285: Timesync_Dststartdate
Dst offset in minutes. Default: 0 timesync_dststartdate what month and day dst starts, in the format mm-dd. Default: none timesync_dstenddate what month and day dst ends, in the format mm-dd. Default: none timesync_dststartdate chapter 13. Advanced settings 272.
Page 286: Dns_Dnsserverip1
13.18. Dns client settings dns_dnsserverip1 primary dns server. Default: none dns_dnsserverip2 secondary dns server. Default: none dns_dnsserverip3 tertiary dns server. Default: none 13.18. Dns client settings chapter 13. Advanced settings 273.
Page 287: Httpposter_Repdelay
13.19. Http poster settings httpposter_url1, httpposter_url2, httpposter_url3 the urls specified here will be posted in order when netdefendos is loaded. Httpposter_repdelay delays in seconds until all urls are refetcd. Default: 604800 13.19. Http poster settings chapter 13. Advanced settings 274.
Page 288: 13.20. Ppp Settings
13.20. Ppp settings ppp_l2tpbeforerules pass l2tp traffic sent to the d-link firewall directly to the l2tp server without consulting the rule-set. Default: enabled ppp_pptpbeforerules pass pptp traffic sent to the d-link firewall directly to the pptp server without consulting the rule-set. Default: ...
Page 289: 13.21. Idp
13.21. Idp idp_updateinterval the number of seconds between automatic idp signature updates. A value of 0 stops automatic up- dates. Default: 43200 (=12 hours) 13.21. Idp chapter 13. Advanced settings 276.
Page 290: Hwm_Pollinterval
13.22. Hardware monitor settings hwm_pollinterval polling intervall for hardware monitor which is the delay in milliseconds between reading of hard- ware monitor values. Minimum 100, maximum 10000. Default: 500 ms hwmmem_interval memory polling interval which is the delay in minutes between reading ...
Page 291: Reassembly_Maxconnections
13.23. Packet re-assembly settings packet re-assembly collects ip fragments into complete ip datagrams and, for tcp, reorders seg- ments so that they are processed in the correct order and also to keep track of potential segment overlaps and to inform other sub-systems of such overlaps. The associat...
Page 292: Buffloodreboottime
13.24. Miscellaneous settings buffloodreboottime as a final way out, netdefendos automatically reboots if it’s buffers have been flooded for a long time. This setting specifies this amount of time. Default: 3600 highbuffers the number of buffers to allocate in ram above the 1 mb limit. Default: 3% o...
Page 293
Maxpipeusers chapter 13. Advanced settings 280
Page 294: Updates
Appendix a. Subscribing to security updates introduction the netdefendos anti-virus (av) module, the intrusion detection and prevention (idp) module and the dynamic web content filtering module all function using external d-link databases which contain details of the latest viruses, security threats...
Page 295
Gw-world:/> updatecenter -update antivirus querying update status to get the status of idp updates use the command: gw-world:/> updatecenter -status idp to get the status of av updates: gw-world:/> updatecenter -status antivirus querying server status to get the status of the d-link network servers ...
Page 296
Appendix b. Idp signature groups for idp scanning, the following signature groups are available for selection. These groups are avail- able only for the d-link advanced idp service. There is a version of each group under the three types of ids, ips and policy. For further information see section 6.3...
Page 297
Group name intrusion type ftp_formatstring format string attack ftp_general ftp protocol and implementation ftp_login login attacks ftp_overflow ftp buffer overflow game_bomberclone bomberclone game game_general generic game servers/clients game_unreal unreal game server http_apache apache httpd htt...
Page 298
Group name intrusion type pop3_dos denial of service for pop pop3_general post office protocol v3 pop3_login-attacks password guessing and related login attack pop3_overflow pop3 server overflow pop3_request-errors request error portmapper_general portmapper print_general lp printing server: lpr lpd...
Page 299
Group name intrusion type tftp_operation operation attack tftp_overflow tftp buffer overflow attack tftp_reply tftp reply attack tftp_request tftp request attack trojan_general trojan udp_general general udp udp_popup pop-up window for ms windows upnp_general upnp version_cvs cvs version_svn subvers...
Page 300
Appendix c. Anti-virus mime filetypes for anti-virus scanning, the following mime filetypes can be checked to make sure that the content matches the filetype of a file download. Checking is done only if the option is enabled as described in section 6.4.6, “anti-virus options”. Filetype extension app...
Page 301
Filetype extension application exe windows executable fgf free graphics format file flac free lossless audio codec file flc flic animated picture fli flic animation flv macromedia flash video gdbm database file gif graphic interchange format file gzip, gz, tgz gzip compressed archive hap hap archive...
Page 302
Filetype extension application pdf acrobat portable document format pe portable executable file pfb postscript type 1 font pgm portable graymap graphic pkg sysv r4 pkg datastreams pll pakleo archive data pma pmarc archive data png portable (public) network graphic ppm pbm portable pixelmap graphic p...
Page 303
Filetype extension application xcf gimp image file xm fast tracker 2 extended module , audio file xml xml file xmcd xmcd database file for kscd xpm bmc software patrol unix icon file yc yac compressed archive zif zif image zip zip compressed archive file zoo zoo compressed archive file zpk zpack arc...
Page 304
Appendix d. The osi framework the open systems interconnection model defines a framework for intercomputer communications. It categorizes different protocols for a great variety of network applications into seven smaller, more manageable layers. The model describes how data from an application in on...
Page 305
Appendix e. D-link worldwide offices below is a complete list of d-link worldwide sales offices. Please check your own country area's local website for further details regarding support of d-link products as well as contact details for local support. Australia 1 giffnock avenue, north ryde, nsw 2113...
Page 306
Fax: +972-9-9715601. Website: www.Dlink.Co.Il italy via nino bonnet n. 6/b, 20154 – milano, italy. Tel: 39-02-2900-0676, fax: 39-02-2900-1723. Website: www.Dlink.It latinamerica isidora goyeechea 2934, ofcina 702, las condes, santiago – chile. Tel: 56-2-232-3185, fax: 56-2-232-0923. Website: www.Dli...
Page 307: Alphabetical Index
Alphabetical index a access rules, 102 accounting, 24 interim messages, 26 limitations, 27 messages, 24 system shutdowns, 27 address book, 31 ethernet addresses in, 33 ip addresses in, 31 address groups, 34 address translation, 161 allow, ip rule, anti-virus, 135 activating, 136 database, 136 memory...
Page 308
Dynamic routing policy, 84 e ethernet, 41 ip addresses, 42 evasion attack prevention, 127 events, 21 distribution, 21 messages, 21 f fragmentedicmp, setting, 259 fragreassemblyfail, setting, 258 fwdfast, ip rule, h hainitialsilence, setting, 270 hasyncbufsize, setting, 270 hasyncmaxpktburst, setting...
Page 309
Pptp, 202 pseudoreass_maxconcurrent, setting, 257 q qos (see quality of service) quality of service, 209 r radius accounting, 24 authentication, 176 rapid failover, 231 reassdonelinger, setting, 259 reassembly_maxconnections, setting, 278 reassembly_maxprocessingmem, setting, 278 reassillegallinger,...
Page 310
X x.509 certificates, 57 z zonedefense idp, 131 zone defense, 235 switches, 236 alphabetical index 297.