- DL manuals
- H3C
- Wireless Access Point
- WA Series
- Configuration Manual
H3C WA Series Configuration Manual - Obtaining Documentation
Category
Documents
Purposes
Provides answers to some of the most frequently asked
questions on how to troubleshoot your AP.
Operations and
maintenance
Provide information about the product release, including the
version history, hardware and software compatibility matrix,
version upgrade information, technical support information,
and software upgrading.
Obtaining Documentation
You can access the most up-to-date H3C product documentation on the World Wide Web at
Click the links on the top navigation bar to obtain different categories of product documentation:
[Technical Support & Documents > Technical Documents]
– Provides hardware installation, software
upgrading, getting started, and software feature configuration and maintenance documentation.
– Provides information about products and technologies, as well as solutions.
[Technical Support & Documents > Software Download]
– Provides the documentation released with
the software version.
Documentation Feedback
You can e-mail your comments about product documentation to info@h3c.com.
We appreciate your comments.
Summary of WA Series
Page 1
H3c wa series wlan access points layer 2 – lan switching configuration guide hangzhou h3c technologies co., ltd. Http://www.H3c.Com document version: 6w100-20100910
Page 2
Copyright © 2010, hangzhou h3c technologies co., ltd. And its licensors all rights reserved no part of this manual may be reproduced or transmitted in any form or by any means without prior written consent of hangzhou h3c technologies co., ltd. Trademarks h3c, , aolynk, , h 3 care, , top g, , irf, n...
Page 3: Preface
Preface the h3c wa documentation set includes 10 configuration guides, which describe the software features for the h3c wa series wlan access points and guide you through the software configuration procedures. These configuration guides also provide configuration examples to help you apply the softw...
Page 4
Convention description # a line that starts with a pound (#) sign is comments. Gui conventions convention description boldface window names, button names, field names, and menu items are in boldface. For example, the new user window appears; click ok. > multi-level menus are separated by angle brack...
Page 5: Obtaining Documentation
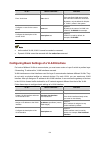
Category documents purposes user faq provides answers to some of the most frequently asked questions on how to troubleshoot your ap. Operations and maintenance release notes provide information about the product release, including the version history, hardware and software compatibility matrix, vers...
Page 6: Table of Contents
I table of contents 1 applicable models and software versions ·····························································································1-1 2 feature matrix ····························································································································...
Page 7
Ii introduction to mstp·······················································································································7-9 protocols and standards ···············································································································7-14 configuration ...
Page 8
1-1 z the models listed in this document are not applicable to all regions. Please consult your local sales office for the models applicable to your region. Z read this chapter before using an h3c wa series wlan access point. 1 applicable models and software versions h3c wa series wlan access points...
Page 9: Feature Matrix
2-1 2 feature matrix z support of the h3c wa series wlan access points for features, commands and parameters may vary by device model. See this document for more information. Z for information about feature support, see table 2-1 . For information about command and parameter support, see table 3-1 ....
Page 10: Command/parameter Matrix
3-1 3 command/parameter matrix table 3-1 command/parameter matrix document module command/parameter wa2200 series wa2600 series display ip https not supported supported ip https acl not supported supported ip https certificate access-control-policy not supported supported fundamentals command refere...
Page 12
4-1 z the models listed in this document are not applicable to all regions. Please consult your local sales office for the models applicable to your region. Z support of the h3c wa series wlan access points (aps) for features may vary by ap model. For more information, see feature matrix. Z the inte...
Page 16
4-5 actions port type no protective action configured a protective action configured hybrid or trunk port z generate traps. Z if loopback detection control is enabled, set the interface in controlled mode. The interface discards all incoming packets, but still forwards outgoing packets. Z delete all...
Page 17
4-6 to do… use the command… remarks display the information about the loopback function display loopback-detection available in any view.
Page 18: Loopback Interface
5-1 5 loopback and null interface configuration this chapter includes these sections: z loopback interface z null interface z displaying and maintaining loopback and null interfaces loopback interface introduction to loopback interface a loopback interface is a software-only virtual interface. The p...
Page 19: Null Interface
5-2 to do… use the command… remarks set a description for the loopback interface description text optional by default, the description of an interface is the interface name followed by the “interface” string. Shut down the loopback interface shutdown optional a loopback interface is up on being crea...
Page 20
5-3 displaying and maintaining loopback and null interfaces to do… use the command… remarks display information about loopback interfaces display interface loopback [ interface-number ] available in any view display information about the null interface display interface null [ 0 ] available in any v...
Page 21: Overview
6-1 z the models listed in this document are not applicable to all regions. Please consult your local sales office for the models applicable to your region. Z support of the h3c wa series wlan access points (aps) for features may vary by ap model. For more information, see feature matrix. Z the inte...
Page 22
6-2 the following is how an ap learns a mac address when it receives a frame from a port, port a for example: 1) check the source mac address (mac-source for example) of the frame. Assume that frames with the source mac address mac-source can be forwarded through port a. 2) look up the mac address t...
Page 23
6-3 z unicast mode: if an entry is available for the destination mac address, the ap forwards the frame directly from the hardware. Z broadcast mode: if the ap receives a frame with the destination address being all fs, or no entry is available for the destination mac address, the ap broadcasts the ...
Page 25
6-5 configuring the aging timer for dynamic mac address entries the mac address table on your ap is available with an aging mechanism for dynamic entries. In this way, dynamic mac address entries that are not updated within their aging time will be deleted to make room for new entries, and the mac a...
Page 27: Mstp Configuration
7-1 z the models listed in this document are not applicable to all regions. Please consult your local sales office for the models applicable to your region. Z support of the h3c wa series wlan access points (aps) for features may vary by ap model. For more information, see feature matrix. Z the inte...
Page 28
7-2 would occur in a loop network and prevents decreased performance of network devices caused by duplicate packets received. In the narrow sense, stp refers to ieee 802.1d stp; in the broad sense, stp refers to the ieee 802.1d stp and various enhanced spanning tree protocols derived from that proto...
Page 29
7-3 figure 7-1 a schematic diagram of designated bridges and designated ports all the ports on the root bridge are designated ports. 4) path cost path cost is a reference value used for link selection in stp. By calculating path costs, stp selects relatively robust links and blocks redundant links, ...
Page 30
7-4 for simplicity, the descriptions and examples below involve only four fields of configuration bpdus: z root bridge id (represented by bridge priority) z root path cost (related to the rate of the link connecting the port) z designated bridge id (represented by bridge priority) z designated port ...
Page 31
7-5 4) selection of the root port and designated ports on a non-root bridge the process of selecting the root port and designated ports is as follows: table 7-3 selection of the root port and designated ports step description 1 a non-root bridge regards the port on which it received the optimum conf...
Page 32
7-6 z initial state of each bridge the following table shows the initial state of each bridge. Table 7-4 initial state of each bridge bridge port name bpdu of port ap1 {0, 0, 0, ap1} device a ap2 {0, 0, 0, ap2} bp1 {1, 0, 1, bp1} device b bp2 {1, 0, 1, bp2} cp1 {2, 0, 2, cp1} device c cp2 {2, 0, 2, ...
Page 33
7-7 bridge comparison process bpdu of port after comparison z port cp1 receives the configuration bpdu of device a {0, 0, 0, ap2}. Device c finds that the received configuration bpdu is superior to the configuration bpdu of the local port {2, 0, 2, cp1}, and updates the configuration bpdu of cp1. Z ...
Page 34
7-8 figure 7-3 the final calculated spanning tree ap1 ap2 device a with priority 0 device b with priority 1 device c with priority 2 bp1 bp2 cp2 5 4 the spanning tree calculation process in this example is only a simplified process. The bpdu forwarding mechanism in stp z upon network initiation, eve...
Page 35
7-9 for this reason, as a mechanism for state transition in stp, the newly elected root ports or designated ports require twice the forward delay time before transiting to the forwarding state to ensure that the new configuration bpdu has propagated throughout the network. Z hello time is the time i...
Page 36
7-10 z mstp supports mapping vlans to mst instances (mstis) by means of a vlan-to-msti mapping table. Mstp can reduce communication overheads and resource usage by mapping multiple vlans to one msti. Z mstp divides a switched network into multiple regions, each containing multiple spanning trees tha...
Page 37
7-11 z they are physically linked with one another. For example, all the bridges in region a0 in figure 7-4 have the same mst region configuration: z the same region name, z the same vlan-to-msti mapping configuration (vlan 1 is mapped to msti 1, vlan 2 to msti 2, and the rest to the common and inte...
Page 38
7-12 9) boundary port a boundary port is a port that connects an mst region to another mst region, or to a single spanning-tree region running stp, or to a single spanning-tree region running rstp. In figure 7-4 , for example, if a bridge in region a0 is interconnected with the first port of a bridg...
Page 39
7-13 figure 7-5 helps understand these concepts. In this figure: z bridges a, b, c, and d constitute an mst region. Z port 1 and port 2 of bridge a connect to the common root bridge. Z port 5 and port 6 of bridge c form a loop. Z port 3 and port 4 of bridge d connect downstream to other mst regions....
Page 40: Configuration Task List
7-14 within an mst region, mstp generates different mstis for different vlans based on the vlan-to-instance mappings. Mstp performs a separate calculation process, which is similar to spanning tree calculation in stp, for each spanning tree. For details, refer to how stp works . In mstp, a vlan pack...
Page 41: Configuring Mstp
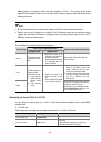
7-15 task remarks configuring the link type of ports optional configuring the mode a port uses to recognize/send mstp packets optional enabling mstp required configuring an mst region required configuring the mstp work mode of the ap optional configuring the timeout factor optional configuring the m...
Page 42
7-16 to do... Use the command... Remarks instance instance-id vlan vlan-list configure the vlan-to-instance mapping table vlan-mapping modulo modulo optional use either command. All vlans in an mst region are mapped to msti 0 (that is, the cist) by default. Configure the mstp revision level of the m...
Page 43
7-17 z when the root bridge of an instance fails or is shut down, the secondary root bridge (if you have specified one) can take over the role of the primary root bridge. However, if you specify a new primary root bridge for the instance then, the secondary root bridge will not become the root bridg...
Page 45
7-19 follow these steps to configure the maximum number of hops of an mst region: to do... Use the command... Remarks enter system view system-view — configure the maximum hops of the mst region stp max-hops hops required 20 by default configuring the network diameter of a switched network any two t...
Page 46
7-20 z mstp can detect link failures and automatically restore blocked redundant links to the forwarding state. A bridge on the cist determines whether a configuration bpdu received by a port has expired according to the max age parameter. If yes, it starts a new spanning tree calculation process. T...
Page 47
7-21 the settings of hello time, forward delay and max age must meet the following formulae; otherwise, network instability will frequently occur. Z 2 × (forward delay – 1 second) ú max age z max age ú 2 × (hello time + 1 second) it is recommended that you specify the network diameter with the stp b...
Page 48
7-22 the higher the maximum port rate is, the more bpdus will be sent within each hello time, and the more system resources will be used. By setting an appropriate maximum port rate, you can limit the rate at which the port sends bpdus and prevent mstp from using excessive network resources when the...
Page 49
7-23 specifying a standard that the ap uses when calculating the default path cost you can specify a standard for the ap to use in automatic calculation for the default path cost. The ap supports the following standards: z dot1d-1998 : the ap calculates the default path cost for ports based on ieee ...
Page 50
7-24 z if you change the standard that the ap uses in calculating the default path cost, the port path cost value set through the stp cost command will become invalid. Z after the path cost of a port is changed, mstp will re-calculate the role of the port and initiate a state transition. If you use ...
Page 51
7-25 z when the priority of a port is changed, mstp will re-calculate the role of the port and initiate a state transition. Z generally, a lower priority value indicates a higher priority. If you configure the same priority value for all the ports on a bridge, the priority of a port depends on the i...
Page 52
7-26 by default, the packet format recognition mode of a port is auto, namely the port automatically distinguishes the two mstp packet formats, and determines the format of packets it will send based on the recognized format. You can configure the mstp packet format on a port. After the configuratio...
Page 53
7-27 to do... Use the command... Remarks enable mstp for the ports stp enable optional by default, mstp is enabled for all ports after it is enabled for the ap globally. To control mstp flexibly, you can use the undo stp enable command to disable mstp for certain ports so that they will not take par...
Page 54
7-28 an mcheck operation takes effect on a bridge only when mstp operates in rstp or mstp mode. Configuring digest snooping as defined in ieee 802.1s, connected bridges are in the same region only when the mst region-related configurations (domain name, revision level, vlan-to-instance mappings) on ...
Page 55
7-29 z with digest snooping enabled, comparison of configuration digest is no longer performed for in-the-same-region check, so the vlan-to-instance mappings must be the same on associated ports. Z with global digest snooping enabled, modification of vlan-to-instance mappings and removing of the cur...
Page 56
7-30 [ap b-ethernet1/0/1] stp config-digest-snooping [ap b-ethernet1/0/1] quit [ap b] stp config-digest-snooping configuring no agreement check in rstp and mstp, two types of messages are used for rapid state transition on designated ports: z proposal: sent by designated ports to request rapid trans...
Page 57
7-31 if the upstream bridge is a third-party device, the rapid state transition implementation may be limited. For example, when the upstream bridge uses a rapid transition mechanism similar to that of rstp, and the downstream bridge adopts mstp and does not work in rstp mode, the root port on the d...
Page 58
7-32 configuring protection functions an mstp bridge supports the following protection functions: z bpdu guard z root guard z loop guard z tc-bpdu guard among loop guard, root guard and edge port settings, only one function can take effect on the same port at the same time. Configuration prerequisit...
Page 59
7-33 enabling root guard the root bridge and secondary root bridge of a spanning tree should be located in the same mst region. Especially for the cist, the root bridge and secondary root bridge are generally put in a high-bandwidth core region during network design. However, due to possible configu...
Page 60
7-34 follow these steps to enable loop guard: to do... Use the command... Remarks enter system view system-view — enter ethernet interface view or wlan mesh interface view interface interface-type interface-number enter interface view or port group view enter port group view port-group manual port-g...
Page 61: Mstp Configuration Example
7-35 to do... Use the command... Remarks view the historical information of port role calculation for the specified msti or all mstis display stp [ instance instance-id ] history available in any view view the statistics of tc/tcn bpdus sent and received by all ports in the specified msti or all mst...
Page 62
7-36 [ap a-mst-region] region-name example [ap a-mst-region] instance 1 vlan 10 [ap a-mst-region] instance 2 vlan 20 [apa-mst-region] revision-level 0 # activate mst region configuration. [ap a-mst-region] active region-configuration [ap a-mst-region] quit # enable mstp globally. [ap a] stp enable #...
Page 63
7-37 [ap c] stp region-configuration # configure the region name, vlan-to-instance mappings and revision level of the mst region. [ap c-mst-region] instance 1 vlan 10 [ap c-mst-region] instance 2 vlan 20 [ap c-mst-region] revision-level 0 # activate mst region configuration manually. [ap c-mst-regio...
Page 64: Vlan Configuration
8-1 z the models listed in this document are not applicable to all regions. Please consult your local sales office for the models applicable to your region. Z support of the h3c wa series wlan access points (aps) for features may vary by ap model. For more information, see feature matrix. Z the inte...
Page 65
8-2 figure 8-1 a vlan diagram vlan 2 vlan 5 switch b switch a router a vlan is logically divided on an organizational basis rather than on a physical basis. For example, all workstations and servers used by a particular workgroup can be connected to the same lan, regardless of their physical locatio...
Page 66
8-3 figure 8-3 the position and format of vlan tag a vlan tag comprises four fields: tag protocol identifier (tpid), priority, canonical format indicator (cfi), and vlan id. Z the 16-bit tpid field with a default value of 0x8100 indicates that the frame is vlan-tagged. Z the 3-bit priority field ind...
Page 67
8-4 to do… use the command… remarks enter vlan view vlan vlan-id required if the specified vlan does not exist, this command creates the vlan first. By default, only the default vlan (that is, vlan 1) exists in the system. Configure a name for the current vlan name text optional by default, the name...
Page 68
8-5 to do… use the command… remarks bring up the vlan interface undo shutdown optional by default, a vlan interface is in the up state. In this case, the vlan interface is up so long as one port in the vlan is up and goes down if all ports in the vlan go down. An administratively shut down vlan inte...
Page 69
8-6 vlan command, the default vlan of the port changes to vlan 1. The removal of the vlan specified as the default vlan of a trunk or hybrid port, however, does not affect the default vlan setting on the port. Z it is recommended that you set the same default vlan id for the local and remote ports. ...
Page 70
8-7 to do… use the command… remarks assign one or multiple access ports to the current vlan port interface-list required by default, all ports belong to vlan 1. 2) in ethernet interface view or wlan-bss interface view follow these steps to assign an access port in interface view to a vlan: to do… us...
Page 71: Mac-Based Vlan Configuration
8-8 z to change the link type of a port from trunk to hybrid or vice versa, you must set the link type to access first. Z after configuring the default vlan for a trunk port, you must use the port trunk permit vlan command to configure the trunk port to allow packets from the default vlan to pass th...
Page 72
8-9 mac-based vlan implementation with mac-based vlan configured, the ap processes received packets as follows: z when receiving an untagged frame, the ap looks up the list of mac-to-vlan mappings based on the source mac address of the frame for a match. Two matching modes are available: exact match...
Page 73: Vlan Configuration Example
8-10 to do... Use the command... Remarks associate mac addresses with a vlan mac-vlan mac-address mac-address [ mask mac-mask ] vlan vlan-id [ priority priority ] required enter interface view interface interface-type interface-number required. Configure the link type of the port as hybrid port link...
Page 74
8-11 figure 8-4 network diagram for port-based vlan configuration configuration procedure 1) configure ap # create vlan 2, vlan 6 through vlan 50, and vlan 100. System-view [ap] vlan 2 [ap-vlan2] quit [ap] vlan 100 [ap-vlan100] vlan 6 to 50 please wait... Done. # enter ethernet 1/0/1 interface view....
Page 75
8-12 port link-type: trunk vlan passing : 2, 6-50, 100 vlan permitted: 2, 6-50, 100 trunk port encapsulation: ieee 802.1q port priority: 0 last 300 seconds input: 0 packets/sec 0 bytes/sec last 300 seconds output: 0 packets/sec 0 bytes/sec input (total): 0 packets, 0 bytes 0 broadcasts, 0 multicasts...
Page 76: Index
9-1 9 index c configuration task list 7-14 configuring a layer 2 ethernet interface 4-3 configuring a mac address table 6-3 configuring basic settings of a vlan interface 8-4 configuring basic vlan settings 8-3 configuring mstp 7-15 d displaying and maintaining an ethernet interface 4-5 displaying a...