- DL manuals
- KAPERSKY
- Other
- ANTI-VIRUS 6.0
- User Manual
KAPERSKY ANTI-VIRUS 6.0 User Manual
Summary of ANTI-VIRUS 6.0
Page 1
Kaspersky lab kaspersky ® internet security 6.0 user guide.
Page 2
K a s p e r s k y i n t e r n e t s e c u r i t y 6 . 0 user guide © kaspersky lab http://www.Kaspersky.Com revision date: january 2007.
Page 3
Table of contents chapter 1. Threats to computer security............................................... 11 1.1. Sources of threats .............................................................................................. 11 1.2. How threats spread .................................................
Page 4
4 k aspersky internet security 6.0 3.2.7. Application integrity control.......................................................................... 40 3.2.8. Configuring anti-hacker settings.................................................................. 41 3.2.8.1. Determining a security zone’s sta...
Page 5
Table of contents 5 6.4. Starting virus scan and update tasks under another profile............................... 77 6.5. Configuring virus scan and update schedules ................................................... 78 6.6. Power options...............................................................
Page 6
6 k aspersky internet security 6.0 10.1.3. Office guard.............................................................................................. 126 10.1.4. Registry guard.......................................................................................... 128 10.1.4.1. Selecting registry ...
Page 7
Table of contents 7 13.3.2. Selecting spam filtration technologies...................................................... 172 13.3.3. Defining spam and potential spam factors .............................................. 173 13.3.4. Creating white and black lists manually...............................
Page 8
8 k aspersky internet security 6.0 16.4.3. Configuring connection settings............................................................... 213 16.4.4. Update distribution.................................................................................... 215 16.4.5. Actions after updating the program...
Page 9
Table of contents 9 17.10.1. Creating a rescue disk............................................................................ 252 17.10.1.1. Getting ready to write the disk......................................................... 252 17.10.1.2. Creating an .Iso file ..................................
Page 10
10 k aspersky internet security 6.0 a.1. List of files scanned by extension..................................................................... 282 a.2. Possible file exclusion masks ........................................................................... 284 a.3. Possible exclusion masks by vir...
Page 11
Chapter 1. Threats to computer security as information technology has rapidly developed and penetrated many aspects of human existence, so the number and range of crimes aimed at breaching information security has grown. Cyber criminals have shown great interest in the activities of both state struc...
Page 12
12 k aspersky internet security 6.0 • internal, including the actions of company staff and users of home pcs. Actions taken by this group could be deliberate or accidental. • the technological factor. This threat group is connected with technical problems – use of obsolete or poor-quality software a...
Page 13
Threats to computer security 13 intranet your intranet is your internal network, specially designed for handling information within a company or a home network. An intranet is a unified space for storing, exchanging, and accessing information for all the computers on the network. This means that if ...
Page 14
14 k aspersky internet security 6.0 1.3. Types of threats there are a vast number of threats to computer security today. This section will review the threats that are blocked by kaspersky internet security. Worms this category of malicious programs spreads itself largely by exploiting vulnerabilitie...
Page 15
Threats to computer security 15 traffic that the user cannot control. This can lead to a security breach and to direct financial losses. Spyware this software collects information about a particular user or organization without their knowledge. Spyware often escapes detection entirely. In general, t...
Page 16
16 k aspersky internet security 6.0 other dangerous programs these are programs created to, for instance, set up denial of service (dos) attacks on remote servers, hack into other computers, and programs that are part of the development environment for malicious programs. These programs include hack...
Page 17
Threats to computer security 17 kaspersky internet security uses two methods for detecting and blocking these threat types: • reactive – this method searches for malicious files using a threat signature database that is regularly updated. • proactive – in contrast to reactive protection, this method...
Page 18
18 k aspersky internet security 6.0 • the web browser (e.G., microsoft internet explorer) freezes or behaves unexpectedly (for example, you cannot close the program window). In 90% of cases, these indirect systems are caused by malfunctions in hardware or software. Despite the fact that such symptom...
Page 19
Threats to computer security 19 1.6. Preventing infection not even the most reliable and deliberate measures can provide 100% protection against computer viruses and trojans, but following such a set of rules significantly lowers the likelihood of virus attacks and the level of potential damage. The...
Page 20
20 k aspersky internet security 6.0 once you download the threat signature updates, you will have plenty of time to protect yourself against the new virus. Rule no. 4: do not trust virus hoaxes, such as prank programs and emails about infection threats. Rule no. 5: use the windows update tool and re...
Page 21
Chapter 2. Kaspersky internet security 6.0 kaspersky internet security 6.0 heralds a new generation of data security products. What really sets kaspersky internet security 6.0 apart from other software, even from other kaspersky lab products, is its multi-faceted approach to data security. 2.1. What...
Page 22
22 k aspersky internet security 6.0 • the program protects the computer against rootkits and dialers, blocks banner ads, popup windows, and malicious scripts downloaded from web pages, and detects phishing sites. • file anti-virus technology has been improved to lower the load on the central process...
Page 23
Kaspersky internet security 6.0 23 • the user notification function (see 17.11.1 on pg. 255) has been expanded for certain protection events you can select the method of notification by choosing from emails, sound notifications, log event. • the program now has the ability to scan traffic sent over ...
Page 24
24 k aspersky internet security 6.0 2.2. The elements of kaspersky internet security defense kaspersky internet security protection is designed with the sources of threats in mind. In other words, a separate program component deals with each threat, monitoring it and taking the necessary action to p...
Page 25
Kaspersky internet security 6.0 25 mail anti-virus email is widely used by hackers to spread malicious programs, and is one of the most common methods of spreading worms. This makes it extremely important to monitor all email. The mail anti-virus component scans all incoming and outgoing email on yo...
Page 26
26 k aspersky internet security 6.0 the anti-hacker component protects your computer while you are using the internet and other networks. It monitors inbound and outbound connections, and scans ports and data packets. Anti-spam although not a direct threat to your computer, spam increases the load o...
Page 27
Kaspersky internet security 6.0 27 2.2.3. Program tools kaspersky internet security includes a number of support tools, which are designed to provide real-time software support, expanding the capabilities of the program and assisting you as you go. Updater in order to be prepared for a hacker attack...
Page 28
28 k aspersky internet security 6.0 such a case, you can boot your computer and restore the system to the condition prior to the malicious action. Support all registered kaspersky anti-virus users can take advantage of our technical support service. To learn where exactly you can get technical suppo...
Page 29
Kaspersky internet security 6.0 29 • 128 mb of ram microsoft windows vista, microsoft windows vista x64: • intel pentium 800 mhz 32-bit (x86)/ 64-bit (x64) faster (or compatible) • 512 mb of ram 2.4. Software packages you can purchase the boxed version of kaspersky internet security from our reselle...
Page 30
30 k aspersky internet security 6.0 2.5. Support for registered users kaspersky lab provides its registered users with an array of services to make kaspersky internet security more effective. When the program has been activated, you become a registered user and will have the following services avail...
Page 31
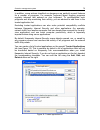
Chapter 3. Installing kaspersky internet security 6.0 you can fully or partially install kaspersky internet security on your computer. If you choose partial installation, you can select the components to install or automatically install just anti-virus components (see step 9 of the installation proc...
Page 32
32 k aspersky internet security 6.0 let’s take a closer look at the steps of the installation procedure. Step 1. Checking for the necessary system conditions to install kaspersky internet security before the program is installed on your computer, the installer checks your computer for the operating ...
Page 33
Installing kaspersky internet security 6.0 33 step 5. Selecting an installation type in this stage, you select how much of the program you want to install on your computer. You have three options: complete. If you select this option, all kaspersky internet security components will be installed. The ...
Page 34
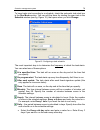
34 k aspersky internet security 6.0 if you want to use the windows firewall, select keep windows firewall enabled. If you select this option, anti-hacker will be installed, but disabled to avoid program conflicts. Step 8. Searching for other anti-virus programs in this stage, the installer searches ...
Page 35
Installing kaspersky internet security 6.0 35 we do not recommend deselecting the enable protection modules before installing when initially installing kaspersky internet security. By enabling the protection modules, you can correctly roll back installation if errors occur while installing the progr...
Page 36
36 k aspersky internet security 6.0 want to import to version 6.0. This might include quarantined or backup files or protection settings. To use this data in version 6.0, check the necessary boxes. 3.2.2. Activating the program you can activate the program by installing a license key that kaspersky ...
Page 37
Installing kaspersky internet security 6.0 37 the first two activation options use a kaspersky lab web server, which requires an internet connection. Before activating, make sure to edit your network settings (see 16.4.3 on pg. 213) in the window that opens when you click lan settings if necessary. ...
Page 38
38 k aspersky internet security 6.0 3.2.2.5. Completing program activation the setup wizard will inform you that the program has been successfully activated. It will also display information on the license key installed: name of the person to whom the software is registered, license number, license ...
Page 39
Installing kaspersky internet security 6.0 39 command line settings, loading into program processes, and window hooks (these settings are disabled by default). 3.2.4. Configuring update settings your computer’s security depends directly on updating the threat signatures and program modules regularly...
Page 40
40 k aspersky internet security 6.0 to automatically scan critical areas of your computer (system memory, startup objects, boot sectors, microsoft windows system folders) for viruses, check the appropriate box. You can configure the schedule by clicking change. The default setting for this automatic...
Page 41
Installing kaspersky internet security 6.0 41 count application checksum files, and create a list of programs that can be trusted from a virus security perspective. For example, this list will automatically include all applications digitally signed by microsoft. In the future, kaspersky internet sec...
Page 42
42 k aspersky internet security 6.0 • blocking rules for applications and packet filtering that allow netbios activity within this subnet even if you have created an open access directory, the information in it will not be available to users from subnets with this status. Additionally, when you sele...
Page 43
Installing kaspersky internet security 6.0 43 to delete a network from the list, click the delete button. 3.2.8.2. Creating a list of network applications the setup wizard analyzes the software installed on your computer and creates a list of applications that use network connections. Anti-hacker cr...
Page 44
44 k aspersky internet security 6.0 to install the application in the background and then restart the computer, enter: msiexec /i allowreboot=1 /qn 3.4. Upgrading from 5.0 to 6.0 if kaspersky anti-virus 5.0 for windows workstations, kaspersky anti-virus personal, or kaspersky anti-virus personal pro...
Page 45
Chapter 4. Program interface kaspersky internet security has a straightforward, user-friendly interface. This chapter will discuss its basic features: • system tray icon (see 4.1 on pg. 45) • context menu (see 4.2 on pg. 46) • main window (see 4.3 on pg. 47) • program settings window (see 4.4 on pg....
Page 46
46 k aspersky internet security 6.0 the kaspersky internet security icon changes in relation to the operation being performed: emails are being scanned. Scripts are being scanned. A file that you or some program is opening, saving, or running is being scanned. Kaspersky internet security threat sign...
Page 47
Program interface 47 scan my computer – launches a complete scan of your computer for dangerous objects. The files on all drives, including removable storage media, will be scanned. Virus scan… – selects objects and starts scanning them for viruses. The default list contains a number of files, such ...
Page 48
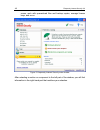
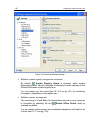
48 k aspersky internet security 6.0 scans, work with quarantined files and backup copies, manage license keys, and so on. Figure 2. Kaspersky internet security main window after selecting a section or component in the left part of the window, you will find information in the right-hand part that mat...
Page 49
Program interface 49 we will now examine the elements in the main window’s navigation panel in greater detail. Main window section purpose this window mostly informs you of the protection status of your computer. The protection section is designed for exactly that. To view general information about ...
Page 50
50 k aspersky internet security 6.0 the comments and tips section accompanies you as you use the application. This section offers tips on raising the security level of your computer. You will also find comments on the application’s current performance and its settings. The links in this section guid...
Page 51
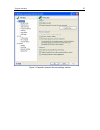
Program interface 51 figure 3. Kaspersky internet security settings window.
Page 52
Chapter 5. Getting started one of kaspersky lab’s main goals in creating kaspersky internet security was to provide optimum configuration for each of the program’s options. This makes it possible for a user with any level of computer literacy to quickly protect their computer straight after installa...
Page 53
Getting started 53 5.1.1. Protection indicators protection status is determined by three indicators, each of which reflect a different aspect of your computer’s protection at any given moment, and indicate any problems in program settings and performance. Figure 4. Indicators reflecting the computer...
Page 54
54 k aspersky internet security 6.0 all threats have been neutralized kaspersky internet security has treated all infected files and programs, and deleted those that could not be treated. Hacker attack has been blocked kaspersky internet security has detected and blocked an attempted network attack....
Page 55
Getting started 55 signatures are obsolete kaspersky internet security has not been updated for some time. You are putting the data at great risk. Update the program as soon as possible. To do so, use the update link.. Signatures are corrupted or partially corrupted the threat signature files are fu...
Page 56
56 k aspersky internet security 6.0 all protection components are disabled protection is fully disabled. To restore the components, select resume protection from the context menu by clicking on the system tray icon. Some protection components have malfunctioned one or more kaspersky internet securit...
Page 57
Getting started 57 • file anti-virus : not running – file protection is not available for some reason. For example, you do not have a license key for the program. • file anti-virus : disabled (error) – the component encountered an error. If this occurs, contact kaspersky lab’s technical support. If ...
Page 58
58 k aspersky internet security 6.0 5.2. How to scan your computer for viruses after installation, the application will without fail inform you with a special notice in the lower left-hand part of the application window that the server has not yet been scanned and will recommend that you scan it for...
Page 59
Getting started 59 when you do this, a scan of the selected areas will begin, and the details will be shown in a special window. When you click the close button, the window with information about installation progress will be hidden. This will not stop the scan. 5.4. How to scan a file, folder or di...
Page 60
60 k aspersky internet security 6.0 5.5. How to train anti-spam one step in getting started is training anti-spam, using your emails to filter out junk. Spam is junk email, although it is difficult to say what constitutes spam for a given user. While there are email categories which can be applied t...
Page 61
Getting started 61 rule in your email client for these emails, such as a rule that deletes them or moves them to a special folder. 5.6. How to update the program kaspersky lab updates the threats signatures and modules for kaspersky internet security using dedicated update servers. Kaspersky lab’s u...
Page 62
62 k aspersky internet security 6.0 to save the report to file: 1. Select the component in the protection section of the main window of the program and left-click anywhere in the statistics box. 2. Click the save as button and in the window that opens specify the file name for the component's perfor...
Page 63
Chapter 6. Protection management system kaspersky internet security lets you multi-task computer security management: • enable, disable, and pause (see 6.1 on pg. 63) the program • define the types of dangerous programs (see 6.2 on pg. 67) against which kaspersky internet security will protect your ...
Page 64
64 k aspersky internet security 6.0 6.1.1. Pausing protection pausing protection means temporarily disabling all the protection components that monitor the files on your computer, incoming and outgoing email, executable scripts, application behavior, and anti-hacker and anti-spam. To pause a kaspers...
Page 65
Protection management system 65 • inactive (gray) names of the disabled components in the protection section of the main window. • inactive (gray) system tray icon. • the third protection indicator (see 5.1.1 on pg. 53) on your computer, which shows that no protection components are enabled. 6.1.2. ...
Page 66
66 k aspersky internet security 6.0 them. It is likely that the problem can be solved in another way, for example, by changing the security level. If, for example, you are working with a database that you are sure does not contain viruses, simply add its files as an exclusion (see 6.3 on pg. 68). To...
Page 67
Protection management system 67 the protection status immediately changes to running. The program’s system tray icon becomes active (color). The third protection indicator (see 5.1.1 on pg. 53) will also inform you that all protection components are enabled. 6.1.5. Shutting down the program if you h...
Page 68
68 k aspersky internet security 6.0 to choose what malicious programs kaspersky internet security will protect you from, select the protection section in the program settings window (see 4.4 on pg. 50). The malware categories box contains threat types: viruses, worms, trojans, and hacker tools. This...
Page 69
Protection management system 69 warning! Excluded objects are not subject to scans when the disk or folder where they are located are scanned. However, if you select that object in particular, the exclusion rule will not apply. In order to create an exclusion list, 1. Open the kaspersky internet sec...
Page 70
70 k aspersky internet security 6.0 you can exclude files of certain formats from the scan, use a file mask, or exclude a certain area, such as a folder or a program, program processes, or objects according to their virus encyclopedia classification.\ the classification is the status that kaspersky ...
Page 71
Protection management system 71 figure 9. Creating an exclusion rule if you check both boxes at once, a rule will be created for that object with a certain virus encyclopedia classification. In such a case, the following rules apply: • if you specify a certain file as the object and a certain status...
Page 72
72 k aspersky internet security 6.0 you can add advanced settings for the following verdicts, among others: o invader (injects into program processes). For this verdict, you can give a name, mask, or complete path to the object being injected into (for example, a .Dll file) as an additional exclusio...
Page 73
Protection management system 73 figure 10. Dangerous object detection notification 2. In the window that opens, be sure that all the exclusion rule settings match your needs. The program will fill in the object name and threat type automatically, based on information from the notification. To create...
Page 74
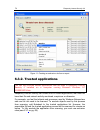
74 k aspersky internet security 6.0 figure 11. Creating an exclusion rule from a report 6.3.2. Trusted applications you can only exclude trusted applications from the scan in kaspersky internet security if installed on a computer running microsoft windows nt 4.0/2000/xp/vista. Kaspersky internet sec...
Page 75
Protection management system 75 in addition, some actions classified as dangerous are perfectly normal features for a number of programs. For example, keyboard layout toggling programs regularly intercept text entered on your keyboard. To accommodate such programs and stop monitoring their activity,...
Page 76
76 k aspersky internet security 6.0 to add a program to the trusted application list: 1. Click the add button on the right-hand part of the window. 2. In the trusted applications window (see fig. 13) that opens, select the application using the browse button. A context menu will open, and by clickin...
Page 77
Protection management system 77 do not scan network traffic – excludes from scans for viruses and spam any network traffic initiated by the trusted application . You can exclude all the application’s network traffic or encrypted traffic (ssl) from the scan. To do so, click the alllink. It will chang...
Page 78
78 k aspersky internet security 6.0 figure 14. Configuring an update task from another profile 6.5. Configuring virus scan and update schedules you can run virus scan and update tasks manually, or automatically using a schedule. Virus scans preinstalled with the application are started automatically...
Page 79
Protection management system 79 to have tasks start according to a schedule, check the automatic task start box in the run mode section. You can edit the times for starting the scan task in the schedule window (see fig. Figure 15), that opens when you click change. Figure 15. Configuring a task sche...
Page 80
80 k aspersky internet security 6.0 • select every weekday if you want the scan to run daily, monday through friday. • select every weekend for the task to run on saturdays and sundays only. In addition to the frequency, specify what time of day or night the scan task will run in the time field. Wee...
Page 81
Protection management system 81 note that this setting can be configured individually for every virus scan task. If you choose to do this, the configuration for a specific task has a higher priority. Figure 16. Configuring power settings to configure power settings for virus scan tasks: select the p...
Page 82
Chapter 7. File anti-virus the kaspersky internet security component that protect your computer files against infection is called file anti-virus. It loads when you start your operating system, runs in your computer’s ram, and scans all files opened, saved, or executed. The component’s activity is i...
Page 83
File anti-virus 83 • high – the level with the most comprehensive monitoring of files opened, saved, or run. • recommended – kaspersky lab recommends this settings level. It will scan the following object categories: • programs and files by contents • new objects and objects modified since the last ...
Page 84
84 k aspersky internet security 6.0 based on the source data, one can conclude that you have a fairly high risk of being infected by a malicious program. The size and type of the files being handled is quite varied and skipping them in the scan would put your data at risk. You want to scan the files...
Page 85
File anti-virus 85 the file types scanned are defined in the file types section (see fig. Figure 18). Select one of the three options: scan all files. With this option selected, all file system objects that are opened, run, or saved will be scanned without exceptions. Scan programs and documents (by...
Page 86
86 k aspersky internet security 6.0 figure 18. Selecting the file types scanned for viruses tip: do not forget that someone could send a virus to your computer with an extension (e.G. .Txt) that is actually an executable file renamed as a .Txt file. If you select scan programs and documents (by exte...
Page 87
File anti-virus 87 you can select and scan all files, or only new files, for each type of compound file. To do so, left-click the link next to the name of the object to toggle its value. If the productivity section has been set up only to scan new and modified files, you will not be able to select t...
Page 88
88 k aspersky internet security 6.0 figure 19. Creating a protected zone you can use masks when you add objects for scanning. Note that you can only enter masks will absolute paths to objects: • c:\dir\*.* or c:\dir\* or c:\dir\ - all files in folder c:\dir\ • c:\dir\*.Exe - all files with the exten...
Page 89
File anti-virus 89 to configure additional file anti-virus settings: 1. Select file anti-virus in the main window and go to the component settings window by clicking the settings link. 2. Click the customize button and select the additional tab in the window that opens (see fig. Figure 20). Figure 2...
Page 90
90 k aspersky internet security 6.0 • on execution – only scans files when an attempt is made to run them. You might need to pause file anti-virus when performing tasks that require significant operating system resources. To lower the load and ensure that the user regains access to files quickly, we...
Page 91
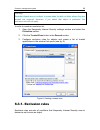
File anti-virus 91 7.2.4. Restoring default file anti-virus settings when configuring file anti-virus, you can always return to the default performance settings. Kaspersky lab considers them to be optimal and has combined them in the recommended security level. To restore the default file anti-virus...
Page 92
92 k aspersky internet security 6.0 figure 23. Possible file anti-virus actions with dangerous objects if the action selected was when it detects a dangerous object prompt for action file anti-virus issues a warning message containing information about what malicious program has infected or potentia...
Page 93
File anti-virus 93 7.3. Postponed disinfection if you select block access as the action for malicious programs, the objects will not be treated and access to them will be blocked. If the actions selected were block access disinfect all untreated objects will also be blocked. In order to regain acces...
Page 94
Chapter 8. Mail anti-virus mail anti-virus is kaspersky internet security’s component to prevent incoming and outgoing email from transferring dangerous objects. It starts running when the operating system boots up, stays active in your system memory, and scans all email on protocols pop3, smtp, ima...
Page 95
Mail anti-virus 95 • if no malicious code is discovered in the email, it is immediately made available again to the user. A special plug-in (see 8.2.2 on pg. 99) is provided for microsoft office outlook that can configure email scans more exactly. If you use the bat!, kaspersky internet security can...
Page 96
96 k aspersky internet security 6.0 you can raise or lower the email security level by selecting the level you want, or editing the settings for the current level. To change the security level: adjust the sliders. By altering the security level, you define the ratio of scan speed to the total number...
Page 97
Mail anti-virus 97 warning! This version of kaspersky internet security does not provide mail anti- virus plug-ins for 64-bit mail clients. • settings that define actions for dangerous email objects (see 8.2.4 on pg. 103) the following sections examine these settings in detail. 8.2.1. Selecting a pr...
Page 98
98 k aspersky internet security 6.0 figure 25. Mail anti-virus settings in addition to selecting an email group, you can specify whether archived attachments should be scanned, and also set the maximum amount of time for scanning a single email object. These settings are configured in the restrictio...
Page 99
Mail anti-virus 99 you can find more information about filtered attachment types in section a.1 on pg. 282. By using the filter, you increase your computer’s security, since malicious programs spread through email most frequently as attachments. By renaming or deleting certain attachment types, you ...
Page 100
100 k aspersky internet security 6.0 figure 26. Configuring mail anti-virus settings in microsoft office outlook select an email scan mode: scan upon receiving – analyzes each email when it enters your inbox. Scan when read – scans each email when you open it to read it. Scan upon sending – scans ea...
Page 101
Mail anti-virus 101 warning! If you use microsoft office outlook to connect to your email service on imap, you are advised not to use scan upon receiving mode. Enabling this mode will lead to emails being copied to the local computer when delivered to the server, and consequently the main advantage ...
Page 102
102 k aspersky internet security 6.0 figure 27. Configuring email scans in the bat! You must decide: • what group of emails will be scanned for viruses (incoming, outgoing) • at what point in time email objects will be scanned for viruses (when opening an email or before saving one to disk) • the ac...
Page 103
Mail anti-virus 103 warning! The bat! Does not mark emails containing dangerous objects with special headers. 8.2.4. Restoring default mail anti-virus settings when configuring mail anti-virus, you can always return to the default performance settings, which kaspersky lab considers to be optimal and...
Page 104
104 k aspersky internet security 6.0 figure 28. Selecting actions for dangerous email objects let’s look at the possible options for processing dangerous email objects in more detail. If the action selected was when a dangerous object is detected prompt for action mail anti-virus will issue a warnin...
Page 105
Mail anti-virus 105 infected will be moved to quarantine. Block access disinfect delete when e-mail anti-virus detects an infected or potentially infected object, it deletes it without informing the user. When disinfecting or deleting an object, kaspersky internet security creates a backup copy (see...
Page 106
Chapter 9. Web anti-virus whenever you use the internet, information stored on your computer is open to the risk of infection by dangerous programs, which can penetrate your computer when you read an article on the internet. Web anti-virus is kaspersky internet security’s component for guarding your...
Page 107
Web anti-virus 107 malicious code. Malicious objects are detected using both the threat signatures included in kaspersky internet security, and the heuristic algorithm. The signatures contain descriptions of all malicious programs known to date, and methods for neutralizing them. The heuristic algor...
Page 108
108 k aspersky internet security 6.0 figure 29. Selecting a web security level by default, the protection level is set to recommended. You can raise or lower the security level by selecting the level you want or editing the settings for the current level. To edit the security level: adjust the slide...
Page 109
Web anti-virus 109 9.2. Configuring web anti-virus web anti-virus scans all objects that are loaded on your computer via the http protocol, and monitors any wsh scripts (javascript or visual basic scripts, etc.) that are run. You can configure web anti-virus settings to increase component operation ...
Page 110
110 k aspersky internet security 6.0 interrupting the connection without reducing security while using the internet. To select the scanning algorithm that web anti-virus will use: 1. Click on the customize button in the web anti-virus configuration window. 2. In the window that opens (see fig. 30), ...
Page 111
Web anti-virus 111 9.2.2. Creating a trusted address list you have the option of creating a list of trusted addresses whose contents you fully trust. Web anti-virus will not analyze data from those addresses for dangerous objects. This option can be used in cases where web anti-virus repeatedly bloc...
Page 112
112 k aspersky internet security 6.0 to restore the default web anti-virus settings: 1. Select web anti-virus in the main window and go to the component settings window by clicking settings. 2. Click the default button in the security level section. 9.2.4. Selecting responses to dangerous objects if...
Page 113
Web anti-virus 113 web anti-virus always blocks dangerous scripts, and issues popup messages that inform the user of the action taken. You cannot change the response to a dangerous script, other than by disabling the script scanning module..
Page 114
Chapter 10. Proactive defense warning! This version of the application does not have the proactive defense component: there are no proactive defense components in this version of the application (application integrity control and office guard) for computers running microsoft windows xp professional ...
Page 115
Proactive defense 115 the preventative technologies provided by kaspersky internet security proactive defense do not require as much time as the reactive technique, and neutralize new threats before they harm your computer. How is this done? In contrast with reactive technologies, which analyze code...
Page 116
116 k aspersky internet security 6.0 proactive defense tracks and blocks all dangerous operations by using the set of rules together with a list of excluded applications. Proactive defense also tracks all macros executed in microsoft office applications. In operation, proactive defense uses a set of...
Page 117
Proactive defense 117 taken. You must accept the decision, block, or allow this activity on your own. You can create a rule for the activity and cancel the actions taken in the system. 10.1. Proactive defense settings the categories of settings (see fig. 32) for the proactive defense component are a...
Page 118
118 k aspersky internet security 6.0 figure 32. Proactive defense settings • whether system registry changes are monitored by default, enable registry guard is checked, which means kaspersky internet security analyzes all attempts to make changes to the microsoft windows system registry keys. You ca...
Page 119
Proactive defense 119 this proactive defense component is not available under microsoft windows xp professional x64 edition, microsoft windows vista or microsoft windows vista x64. You can configure exclusions (see 6.3.1 on pg. 69) for proactive defense modules and create a trusted application list ...
Page 120
120 k aspersky internet security 6.0 • appearance of masked processes. A rootkit is a set of programs used to mask malicious programs and their processes in the system. Kaspersky internet security analyzes the operating system for masked processes. • invaders. This activity is used in attempts to re...
Page 121
Proactive defense 121 the types of activity that proactive defense monitors are listed in the settings: application activity analyzer window (see fig. 33). Figure 33. Configuring application activity control to edit a dangerous activity monitoring rule, select it from the list and assign the rule se...
Page 122
122 k aspersky internet security 6.0 if you are running one of the operating systems listed above, only one type of system event is controlled, dangerous activity (behavior analysis). If you want kaspersky internet security to monitor modifications of system user accounts in addition to dangerous ac...
Page 123
Proactive defense 123 security comes with a list of critical applications, each of which has its own monitoring rule to control application activity. You can extend this list of critical applications, and delete or edit the rules for the applications on the list provided. Besides the list of critica...
Page 124
124 k aspersky internet security 6.0 specify whether to log component activity in the component report. The default settings allow most critical operations are allowed to start, be edited, or be started as child processes. To add an application to the critical application list and create a rule for ...
Page 125
Proactive defense 125 you can use any of these actions as a response: allow, prompt for action, or block. Left-click on the action link until it reaches the value that you need. • choose if you want to generate a report about the activity, by clicking log / do not log. To turn off the monitoring of ...
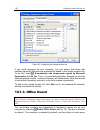
Page 126
126 k aspersky internet security 6.0 figure 36. Configuring the trusted module list if you install programs on your computer, you can ensure that those with modules signed by microsoft are automatically added to the trusted modules list. To do this, check automatically add components signed by micro...
Page 127
Proactive defense 127 run is traced for dangerous behavior, and if suspicious activity is detected, proactive defense allows or blocks the macro. Example: the macro pdfmaker is a plug-in for the adobe acrobat toolbar in microsoft office word that can create a .Pdf file out of any document. Proactive...
Page 128
128 k aspersky internet security 6.0 figure 37. Configuring office guard settings for kaspersky internet security not to block the macro: uncheck the box next to that action. The program will no longer consider that behavior dangerous and proactive defense will not process it. By default, whenever t...
Page 129
Proactive defense 129 proactive defense can detect unknown threats that attempt to edit registry keys on your computer, through the registry guard module. You can enable it by checking the box enable registry guard in the proactive defense settings window. The special proactive defense module traces...
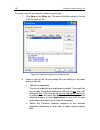
Page 130
130 k aspersky internet security 6.0 figure 38. Controlled registry key groups you can create your own groups of monitored system registry files. To do so, click add in the file group window. Take these steps in the window that opens: 1. Enter the name of the new file group for monitoring system reg...
Page 131
Proactive defense 131 3. Specify the file or group of files, to which you want the rule to apply in the value field. 4. Check including subkeys for the rule to apply to all files attached to the listed registry file. Figure 39. Adding controlled registry keys you only need to use masks with an aster...
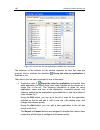
Page 132
132 k aspersky internet security 6.0 to create a rule for your selected system registry files: 1. Click new on the rules tab. The new rule will be added at the top of the list (see fig. 40). Figure 40. Creating an registry key monitoring rule 2. Select a rule on the list and assign the rule settings...
Page 133
Proactive defense 133 you can use any of these actions as a response: allow, prompt for action, and block. Left-click on the link with the action until it reaches the value that you need. • choose if you want to generate a report on the operation carried out, by clicking on the log / do not log link...
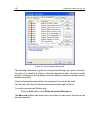
Page 134
Chapter 11. Anti-spy the component of kaspersky internet security which protects you against all types of malware is called anti-spy. Recently, malware has increasingly included programs that aim to: • steal your confidential information, including passwords, credit card numbers, important documents...
Page 135
Anti-spy 135 • the popup blocker component blocks access to internet resources with advertising, such as popup windows the information in these windows is generally not of benefit to you. These windows open automatically when you open a certain website, or go to a different window using a hyperlink....
Page 136
136 k aspersky internet security 6.0 dialers generally establish connections with specific websites, such as sites with pornographic material. Then you are forced to pay for expensive traffic that you never wanted or used. If you want to exclude a number from the blocked list, you must place it on t...
Page 137
Anti-spy 137 4. Specify if addresses in the internet explorer trusted zone or addresses on your local area network will be excluded from the scan. The program considers them trusted by default and does not block pop-up windows from these addresses. Tip: when entering a trusted address mask, you can ...
Page 138
138 k aspersky internet security 6.0 you can also unblock windows through internet explorer if you have windows xp service pack 2. To do so, use the context menu that you can open over the program icon that flashes in the bottom corner of the browser when popup windows are blocked. 11.1.2. Banner ad...
Page 139
Anti-spy 139 figure 42. Blocked banner list the list of standard blocked masks cannot be edited. If you do not want to block a banner covered by a standard mask, uncheck the box next to the mask. To analyze banner ads that do not match the masks from the standard list, check use heuristic analysis m...
Page 140
140 k aspersky internet security 6.0 add the allowed banner mask with the add button. You can either specify the whole, or a partial, url for the banner or mask. In the latter case, when a banner attempts to load, the program will scan its address for the mask. When creating a mask, you can use the ...
Page 141
Anti-spy 141 whenever a secret connection is attempted, the program notifies you by issuing a special message on the screen, which prompts the user to either allow or block the phone call. If you did not initialize the connection, it is very probable that it was configured by a malicious program. If...
Page 142
Chapter 12. Anti-hacker today computers have become quite vulnerable when connected to the internet. They are subjected both to virus infections and to other types of attacks that take advantage of vulnerabilities in operating systems and software. The kaspersky internet security anti-hacker compone...
Page 143
Anti-hacker 143 amount of time, and the user receives a message stating that his computer was subjected to an attempted network attack. The intrusion detection system uses a special network attack database in analysis, which kaspersky lab adds to regularly, and is updated together with the threat si...
Page 144
144 k aspersky internet security 6.0 12.1. Selecting an anti-hacker security level when you use the network, kaspersky internet security protects your computer at one of the following levels (see fig. 44): block all – blocks any network activity on your computer. If you select this security level, y...
Page 145
Anti-hacker 145 the future anti-hacker will apply the new rule for that connection without warning you on screen. Low security – blocks only banned network activity, using block rules that either were installed by with the program or that you created. However, if there is a allow rule for an applica...
Page 146
146 k aspersky internet security 6.0 figure 45. List of rules for the applications installed on a computer the behavior of the buttons in this window depends on how the rules are grouped, that is, whether the checkbox group the rules by application is checked or not. The rules on this tab can be gro...
Page 147
Anti-hacker 147 • general list of rules if group the rules by application is unchecked, then each line in the general list displays complete information for a rule: the application name and the command for starting it, whether to allow or block network activity, the data transfer protocol, the direc...
Page 148
148 k aspersky internet security 6.0 1. Check group the rules by application on the rules for applications tab, if not checked already, and click the add button. 2. In the window that opens, select the executable file of the application for which you want to create a rule. A window with rules for th...
Page 149
Anti-hacker 149 4. Edit the rules created for the application, if necessary. You can modify actions, network connection direction, remote address, ports (local and remote), and the time range for the rule. 5. If you want the rule to apply to a program opened with certain command line settings, check...
Page 150
150 k aspersky internet security 6.0 figure 47. List of packet filtering rules the following information is given for every packet filtering rule: name of the rule, the action (i.E. Whether to allow or block the packet transfer), the data transfer protocol, the direction of the packet, and the netwo...
Page 151
Anti-hacker 151 12.4. Fine-tuning rules for applications and packet filtering the new rule window for advanced rule settings is practically identical for applications and data packets (see figure 48). Figure 48. Creating a new application rule step one: • enter a name for the rule. The program uses ...
Page 152
152 k aspersky internet security 6.0 note that when you a create a blocking rule in anti-hacker training mode, information about the rule being applied will automatically be entered in the report. If you do not need to record this information, deselect the log event checkbox in the settings for that...
Page 153
Anti-hacker 153 4. If you selected a remote address as a network connection property, left-click specify the address and enter the ip address for the rule in the window that opens. You can use one type of ip address or several types for one rule. Several addresses of each type can be specified. 5. S...
Page 154
154 k aspersky internet security 6.0 you can create a rule from the network activity detection alert window (see 12.10 on pg. 161). 12.5. Ranking rule priority each rule created for an program or a data packet has a priority ranking. When other conditions are equal (for example, the network connecti...
Page 155
Anti-hacker 155 if anti-hacker training mode is enabled, a window will open every time your computer connects to a new zone, displaying a basic description about it. You must assign a status to the zone, and network activity will be allowed based on that status. The possible values of the status are...
Page 156
156 k aspersky internet security 6.0 we do not recommend using stealth mode if the computer is being used as a server (for example, an email or http server), as the computers that connect to the server will not see it as connected. The list of zones on which your computer is registered is displayed ...
Page 157
Anti-hacker 157 12.7. Firewall mode the firewall mode (see figure 51) controls anti-hacker compatibility with programs that establish multiple network connections, and to network games. Maximum compatibility – the firewall ensures that anti-hacker will work optimally with programs that establish mul...
Page 158
158 k aspersky internet security 6.0 2. Select the additional tab in the window that opens and select the mode you want, maximum compatibility or maximum speed. Changes to the firewall settings will not take effect until after anti-hacker has been restarted. 12.8. Configuring the intrusion detection...
Page 159
Anti-hacker 159 12.9. List of network attacks detected there are currently a multitude of network attacks that utilize operating system vulnerabilities and other software, system or otherwise, installed on your computer. Malefactors are constantly perfecting attack methods, learning how to steal con...
Page 160
160 k aspersky internet security 6.0 a cycle, which intensifies the load on the processor and can end with some operating systems crashing. • icmp flood sends a large number of icmp packets to your computer. The attack leads to the computer being forced to reply to each inbound packet, which serious...
Page 161
Anti-hacker 161 messenger, and system components that can be accessed through the network – dcom, smb, wins, lsass, iis5. Anti-hacker protects your computer from attacks that use the following known software vulnerabilities (this list of vulnerabilities is cited with the microsoft knowledge base num...
Page 162
162 k aspersky internet security 6.0 for example, after opening microsoft office outlook, it downloads your email from a remote exchange server. To display your inbox, the program connects to the email server. Anti-hacker always tracks this kind of network activity. A message will appear on the scre...
Page 163
Anti-hacker 163 to perform the action this time only: uncheck create a rule and click the button with the name of the action, e.G. Allow. To perform the action you select automatically every time this activity is initiated on your computer: 1. Check create a rule. 2. Select the type of activity that...
Page 164
Chapter 13. Anti-spam the kaspersky internet security component which detects spam, processes it according to a set of rules, and saves you time when using email, is called anti- spam. Anti-spam uses the following method to determine whether an email is spam: 1. The sender’s address is scanned for m...
Page 165
Anti-spam 165 installed. This could include scanning for correctness of html tags, font size, or hidden characters. You can enable or disable each of these stages of the analysis. Anti-spam exists as a plug-in for the following email clients: • microsoft office outlook (see 13.3.9 on pg. 181) • micr...
Page 166
166 k aspersky internet security 6.0 13.1. Selecting an anti-spam sensitivity level kaspersky internet security protects you from spam at one of the following levels (see fig. 54): block all – strictest level of sensitivity, at which only messages containing phrases from the phrase white list (see 1...
Page 167
Anti-spam 167 allow all – lowest sensitivity level. Only email that contains phrases from the phrase black list, or senders listed on the address black list, are marked as spam. At this level, email is only processed using the black list, and all other features all disabled. By default, anti-spam is...
Page 168
168 k aspersky internet security 6.0 13.2.1. Training wizard the training wizard trains anti-spam by indicating which mailbox folders contain spam and which contain accepted email. To open the training wizard: 1. Select anti-spam in the settings window. 2. Click the training wizard button training s...
Page 169
Anti-spam 169 warning! Anti-spam will only train itself with outgoing emails sent via mapi protocol if you check scan when sending in the microsoft office outlook mail anti-virus plug-in (see 13.3.9 on pg. 181). 13.2.3. Training using your email client to training while using your mailbox, you use s...
Page 170
170 k aspersky internet security 6.0 2. Left-click in the statistics box (see fig. 55). The component’s reports can help you make a conclusion about the accuracy of its configuration, and, if necessary, make certain corrections to anti-spam. To mark a certain email as spam or not spam: 1. Select it ...
Page 171
Anti-spam 171 13.3. Configuring anti-spam fine-tuning anti-spam is essential for the spam security feature. All settings for component operation are located in the kaspersky internet security settings window and allow you to: • determine the particulars of operation of anti-spam (see 13.3.1 on pg. 1...
Page 172
172 k aspersky internet security 6.0 figure 56. Configuring scan settings 13.3.2. Selecting spam filtration technologies emails are scanned for spam using state-of-the-art filtration technologies: • ibayes, based on the bayes theorem, analyzes email text to detect phrases that mark it as spam. The a...
Page 173
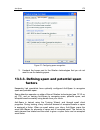
Anti-spam 173 figure 57. Configuring spam recognition 3. Uncheck the boxes next to the filtration technologies that you do not want to use for detecting spam. 13.3.3. Defining spam and potential spam factors kaspersky lab specialists have optimally configured anti-spam to recognize spam and probable...
Page 174
174 k aspersky internet security 6.0 the probable spam factor defines the likelihood that the email will be classified as probable spam. If you are using the recommended level, any email has between a 50% and 59% chance of being considered probable spam. Email that, after being scanned, has a likeli...
Page 175
Anti-spam 175 13.3.4.1. White lists for addresses and phrases the white list contains key phrases from emails that you marked as accepted, and addresses of trusted senders who would not send spam. The white list is filled manually, and the list of senders’ addresses is done automatically while train...
Page 176
176 k aspersky internet security 6.0 you can assign both addresses and address masks in the address list. When entering an address, the use of capitals is ignored. Let’s look at some examples of address masks: • ivanov@test.Ru – emails from this address will always be classified as accepted. • *@tes...
Page 177
Anti-spam 177 to fill the black list: 1. Select anti-spam in the kaspersky internet security settings window. 2. Click the settings button in the right-hand part of the settings window. 3. Open the black list tab (see fig. 59). The tab is divided into two sections: the upper portion contains the add...
Page 178
178 k aspersky internet security 6.0 to disable the use of a certain address or phrase as attributes of spam, it can be deleted using the delete button, or the box alongside the text can be unchecked to disable them. 13.3.5. Additional spam filtration features in addition to the main features that a...
Page 179
Anti-spam 179 to use an additional filtration indicator, check the flag beside it. Each of the factors also requires that you set a spam factor (in percentage points) that defines the likelihood that an email will be classified as spam. The default value for the spam factor is 80%. The email will be...
Page 180
180 k aspersky internet security 6.0 the rest of your email will be downloaded to your computer after you close the mail dispatcher window. Sometimes it can be difficult to decide whether to accept a certain email, judging only by the sender and the email's subject line. In such cases, mail dispatch...
Page 181
Anti-spam 181 13.3.9. Configuring spam processing in microsoft office outlook note that there is no spam plug-in for microsoft office outlook if you are running the application under windows 9x. This option is only supported for the 32-bit build of microsoft office outlook for computers running micr...
Page 182
182 k aspersky internet security 6.0 it opens automatically when the email client is first opened after installing the program and asks if you to configure spam processing. You can assign the following processing rules for both spam and potential spam: move to folder – spam is moved to the specified...
Page 183
Anti-spam 183 2. The rule wizard will guide you through the following windows and steps: step one you can choose to create a rule from scratch or from a template. Select create new rule and select apply this rule after the message arrives. Click the next button. Step two in the rule conditions windo...
Page 184
184 k aspersky internet security 6.0 13.3.10. Configuring spam processing in microsoft outlook express email that is classified by anti-spam as spam or potential spam is by default marked with special markings [!! Spam] or [?? Probable spam] in the subject line. Additional actions for spam and poten...
Page 185
Anti-spam 185 to assign these rules, select the appropriate value from the dropdown list in the spam or probable spam section. 13.3.11. Configuring spam processing in the bat! This option is only supported for the 32-bit build of the bat! For computers running microsoft windows xp professional x64 e...
Page 186
186 k aspersky internet security 6.0 figure 63. Configuring spam recognition and processing in the bat! Warning! After processing an email, kaspersky internet security assigns a spam or potential spam status to the email based on a factor ( see 13.3.3 on pg. 173 ) with a value that you can adjust. T...
Page 187
Chapter 14. Scanning for viruses on your computer one of the important aspects of protecting your computer is scanning user- defined areas for viruses. Kaspersky internet security can scan individual items – files, folders, disks, plug-and-play devices – or the entire computer. Scanning for viruses ...
Page 188
188 k aspersky internet security 6.0 14.1. Managing virus scan tasks you can run a virus scan task manually or automatically using a schedule (see 6.5 on pg. 78). To start a virus scan task manually: check the box beside the task name in the scan section of the main program window, and click the but...
Page 189
Scanning for viruses on your computer 189 object scan lists are already made for default tasks created when you install the program. When you create your own tasks or select an object for a virus scan task, you can create a list of objects. You can add to or edit an object scan list using the button...
Page 190
190 k aspersky internet security 6.0 14.3. Creating virus scan tasks to scan objects on your computer for viruses, you can use built-in scan tasks included with the program and create your own tasks. New scan tasks are created using existing tasks that a template. To create a new virus scan task: 1....
Page 191
Scanning for viruses on your computer 191 14.4. Configuring virus scan tasks the methods are used to scan objects on your computer are determined by the properties assigned for each task. To configure task settings: select the task name in the scan of the main window. Right-click on the task name to...
Page 192
192 k aspersky internet security 6.0 figure 66. Selecting a virus scan security level by default, the file anti-virus security level is set to recommended. You can raise or lower the scan security level by selecting the level you want or changing the settings for the current level. To edit the secur...
Page 193
Scanning for viruses on your computer 193 note: there are files in which viruses cannot insert themselves, since the contents of such files does not contain anything for the virus to hook onto. An example would be .Txt files. And vice versa, there are file formats that contain or can contain executa...
Page 194
194 k aspersky internet security 6.0 in the productivity section, you can specify that only new files and those that have been modified since the previous scan or new files should be scanned for viruses. This mode noticeably reduces scan time and increases the program’s performance speed. To do so, ...
Page 195
Scanning for viruses on your computer 195 please note, when scanning password-protected email databases: • kaspersky internet security detects malicious code in microsoft office outlook 2000 databases but does not disinfect them; • kaspersky internet security does not support scans for malicious cod...
Page 196
196 k aspersky internet security 6.0 figure 68. Selecting actions for dangerous objects if the action selected was when it detects a malicious or potentially infected object prompt for action when the scan is complete the program does not process the objects until the end of the scan. When the scan ...
Page 197
Scanning for viruses on your computer 197 do not prompt for action disinfect delete if disinfection fails the program attempts to treat the object detected without asking the user for confirmation. If the object cannot be disinfected, it is deleted. Do not prompt for action disinfect delete the prog...
Page 198
198 k aspersky internet security 6.0 enable ichecker technology – uses technology that can increase the scan speed by excluding certain objects from the scan. An object is excluded from the scan using a special algorithm that takes into account the release date of the threat signatures, the date the...
Page 199
Scanning for viruses on your computer 199 show detected dangerous objects on the “detected” report tab – display a list of threats detected during the scan on the detected tab of the report (see 17.3.2 on pg. 229) window. Disabling this function may be appropriate for special scans, for example of t...
Page 200
Chapter 15. Testing kaspersky internet security features after installing and configuring kaspersky internet security, we recommend that you verify that settings and program operation are correct using a test virus and variations of it. 15.1. The eicar test virus and its variations the test virus wa...
Page 201
Testing kaspersky internet security 201 features prefix test virus status corresponding action when the application processes the object corr– corrupted. The application could access the object but could not scan it, since the object is corrupted (for example, the file structure is breached, or it i...
Page 202
202 k aspersky internet security 6.0 the first column of the table contains the prefixes that need to be added to the beginning of the string for a standard test virus. The second column describes the status and reaction of kaspersky internet security to various types of test virus. The third column...
Page 203
Testing kaspersky internet security 203 features when you select different options for dealing with detected objects, you can test file anti-virus's reaction to detecting various object types. You can view details on file anti-virus performance in the report on the component. 15.3. Testing virus sca...
Page 204
204 k aspersky internet security 6.0 this way, by selecting different options for actions, you can test kaspersky internet security reactions to detecting various object types. You can view details on virus scan task performance in the report on the component..
Page 205
Chapter 16. Program updates keeping your anti-virus software up-to-date is an investment in your computer’s security. Because new viruses, trojans, and malicious software emerge daily, it is important to regularly update the application to keep your information constantly protected. This task is man...
Page 206
206 k aspersky internet security 6.0 if you do not have access to kaspersky lab’s update servers (for example, your computer is not connected to the internet), you can call the kaspersky lab main office at +7 (495) 797-87-00 to request contact information for kaspersky lab partners, who can provide ...
Page 207
Program updates 207 to start the updater from the shortcut menu: 1. Right click the application icon in the system tray to open the shortcut menu. 2. Select update. To start the updater from the main program window: 1. Select update in the service section. 2. Click the update now! Button in the righ...
Page 208
208 k aspersky internet security 6.0 for example, you installed kaspersky internet security on a laptop that you use at home and at your office. At home, you update the program from the kaspersky lab update servers, and at the office, from a local folder that stores the updates you need. Use two dif...
Page 209
Program updates 209 • the source from which the updates are downloaded and installed (see 16.4.1 on pg. 209) • the run mode for the updating procedure (see 16.4.2 on pg. 211) • which objects are updated • what actions are to be performed after updating is complete (see 16.4.4 on pg. 215) the followi...
Page 210
210 k aspersky internet security 6.0 figure 72. Selecting an update source to download updates from another ftp or http site: 1. Click add. 2. In the select update source dialog box, select the target ftp or http site or specify the ip address, character name, or url address of this site in the sour...
Page 211
Program updates 211 the updates from the first available source. You can change the order of sources in the list using the move up and move down buttons. To edit the list, use the add, edit and remove buttons. The only source you cannot edit or delete is the one labeled kaspersky lab’s update server...
Page 212
212 k aspersky internet security 6.0 if you want to download and install updates for program modules: check update program modules in the settings dialog box of the update service. If there are currently program module updates on the update source, the program will download the updates it needs and ...
Page 213
Program updates 213 manually. With this option, you start the updater manually. Kaspersky internet security notifies you when it needs to be updated: • a popup message, informing you that updating is required, appears above the application icon in the system tray (if notices are enabled; see 17.11.1...
Page 214
214 k aspersky internet security 6.0 check use passive ftp mode if possible if you download the updates from an ftp server in passive mode (for example, through a firewall). If you are working in active ftp mode, clear this checkbox. In the connection timeout (sec) field, assign the time allotted fo...
Page 215
Program updates 215 this feature is unavailable under windows 9x/nt 4.0. However, the proxy server is by default not used for local addresses. 16.4.4. Update distribution if your home computers are connected through a home network, you do not need to download and installed updates on each of them se...
Page 216
216 k aspersky internet security 6.0 figure 76. Copy updates tool settings you can also specify the method for update distribution: • complete, which copies threat signatures and component updates for all kaspersky lab 6.0 applications. To select complete updates, select the copy updates for all com...
Page 217
Program updates 217 16.4.5. Actions after updating the program every threat signature update contains new records that protect your computer from the latest threats. Kaspersky lab recommends that you scan quarantined objects and startup objects each time after the database is updated. Why these obje...
Page 218
Chapter 17. Advanced options kaspersky internet security has other features that expand its functionality. The program places some objects in special storage areas, in order to ensure maximum protection of data with minimum losses. • backup contains copies of objects that kaspersky internet security...
Page 219
Advanced options 219 monitored ports can regulate which kaspersky internet security modules control data transferred on select ports (see 17.7 on pg. 246). The rescue disk can help restore your computer’s functionality after an infection (see 17.10 on pg. 251). This is particularly helpful when you ...
Page 220
220 k aspersky internet security 6.0 when you place an object in quarantine, it is moved, not copied. The object is deleted from the disk or email and is saved in the quarantine folder. Files in quarantine are saved in a special format and are not dangerous. 17.1.1. Actions with quarantined objects ...
Page 221
Advanced options 221 figure 77. List of quarantined objects • scan and disinfect all potentially infected objects in quarantine using the current threat signatures by clicking, click scan all. After scanning and disinfecting any quarantined object, its status may change to infected, potentially infe...
Page 222
222 k aspersky internet security 6.0 tip: we recommend that you only restore objects with the status false positive, ok, and disinfected, since restoring other objects could lead to infecting your computer. • delete any quarantined object or group of selected objects. Only delete objects that cannot...
Page 223
Advanced options 223 17.2. Backup copies of dangerous objects sometimes when objects are disinfected their integrity is lost. If a disinfected file contains important information which is partially or fully corrupted, you can attempt to restore the original object from a backup copy. A backup copy i...
Page 224
224 k aspersky internet security 6.0 figure 79. Backup copies of deleted or disinfected objects you can restore selected copies using the restore button. The object is restored from backup with the same name that it had prior to disinfection. If there is an object in the original location with that ...
Page 225
Advanced options 225 17.2.2. Configuring backup settings you can define the maximum time that backup copes remain in the backup area. The default backup storage time is 30 days, at the end of which backup copies are deleted. You can change the storage time or remove this restriction altogether. To d...
Page 226
226 k aspersky internet security 6.0 figure 80. Reports on component operation to review all the events reported for a component or task: select the name of the component or task on the reports tab and click the details button. A window will then open that contains detailed information on the perfor...
Page 227
Advanced options 227 • the macros and registry tabs are only in the proactive defense report and contain information about all macros which attempted to run on your computer, and on all attempts to modify the operating system registry. • the phishing sites, popup windows, banner ads, and dial attemp...
Page 228
228 k aspersky internet security 6.0 discard all – clears the report on detected objects. When you use this function, all detected dangerous objects remain on your computer. View on www.Viruslist.Ru – goes to a description of the object in the virus encyclopedia on the kaspersky lab website. Search ...
Page 229
Advanced options 229 17.3.2. The detected tab to view detected objects: in the main application window, click on data files in the service area on the left-hand panel. Click anywhere in the reports section to open the protection window, which will open at the reports tab. Select a scan task in the l...
Page 230
230 k aspersky internet security 6.0 17.3.3. The events tab this tab (see fig. 83) provides you with a complete list of all the important events in component operation, virus scans, and threat signature updates that were not overridden by an activity control rule (see 10.1.1 on pg. 119). These event...
Page 231
Advanced options 231 for virus scan tasks, the event log contains the name of the object scanned and the status assigned to it by the scan/processing. You can also train anti-spam while viewing the report using the special context menu. To do so, select the name of the email and open the context men...
Page 232
232 k aspersky internet security 6.0 dangerous objects, or what settings are being used for program updates. Use the change settings link to configure the component. You can configure advanced settings for virus scans: • establish the priority of scan tasks used if the processor is heavily loaded. T...
Page 233
Advanced options 233 17.3.6. The macros tab all the macros that attempted to run during the current kaspersky internet security session are listed on the macros tab (see fig. ). Here you will find the full name of each macro, the time it was executed, and its status after macro processing. Figure 86...
Page 234
234 k aspersky internet security 6.0 figure 87. . Read and modify system registry events the tab lists the full name of the key, its value, the data type, and information about the operation that has taken place: what action was attempted, at what time, and whether it was allowed. 17.3.8. The phishi...
Page 235
Advanced options 235 17.3.9. The popups tab this report tab (see fig. 89) lists the addresses of all the popup windows that anti-spy has blocked. These windows generally open from websites. The address and date and time when popup blocker blocked the window are recorded for each popup. Figure 89. Li...
Page 236
236 k aspersky internet security 6.0 figure 90. Blocked banner ad list you can allow blocked banners to be displayed. To do so, select the object you want from the list and click actions → allow. 17.3.11. The hidden dials tab this tab (see fig. 91) displays all secret dialer attempts to connect to p...
Page 237
Advanced options 237 17.3.12. The network attacks tab this tab (see fig. 92) displays a brief overview of network attacks on your computer. This information is recorded if the intrusion detection system is enabled, which monitors all attempts to attack your computer. Figure 92. List of blocked netwo...
Page 238
238 k aspersky internet security 6.0 figure 93. Blocked host list 17.3.14. The application activity tab if kaspersky internet security is using the firewall, all applications with actions that match rules for applications and were logged during the current session of the program are listed on the ap...
Page 239
Advanced options 239 17.3.15. The packet filtering tab the packet filtering tab contains information about sending and receiving packets that match filtration rules and were logged during the current session of the application (see fig. 95). Figure 96. Monitored data packets activity is only recorde...
Page 240
240 k aspersky internet security 6.0 figure 97. List of established connections 17.3.17. The open ports tab all ports currently open on your computer for network connections are listed on the open ports tab (see fig. 98). It lists the port number, data transfer protocol, name of the application that...
Page 241
Advanced options 241 this information may be useful during virus outbreaks and network attacks if you know exactly which port is vulnerable. You can find out whether that port is open on your computer and take the necessary steps to protect your computer (for example, enabling intrusion detector, cl...
Page 242
242 k aspersky internet security 6.0 figure 100. Information on the program, the license, and the system it is installed on all the information is broken into three sections: • the program version, the date of the last update, and the number of threats known to date are displayed in the product info...
Page 243
Advanced options 243 without a license key, unless a trial version of the application has been activated, kaspersky internet security will run in one update mode. The program will not download any new updates. If a trial version of the program has been activated, after the trial period expires, kasp...
Page 244
244 k aspersky internet security 6.0 figure 101. License information kaspersky lab regularly has special pricing offers on license extensions for our products. Check for specials on the kaspersky lab website in the products ! Sales and special offers area. Information about the license key used is a...
Page 245
Advanced options 245 figure 102. Technical support information depending on the problem, we provide several technical support services: user forum. This resource is a dedicated section of the kaspersky lab website with questions, comments, and suggestions by program users. You can look through the b...
Page 246
246 k aspersky internet security 6.0 computer. You can describe the system configuration on your own or use the automatic information collector on your computer. To go to the comment form, use the submit a bug report or a suggestion link. Technical support. If you need help with using kaspersky inte...
Page 247
Advanced options 247 figure 103. List of monitored ports this window provides a list of ports monitored by kaspersky internet security. To scan data streams enter on all open network ports, select the option monitor all ports. To edit the list of monitored ports manually, select monitor only selecte...
Page 248
248 k aspersky internet security 6.0 however, when kaspersky internet security intercepts the connection query initiated by iexplorer.Exe on port 80, it transfers it to avp.Exe, which in turn attempts to establish a connection with the web page independently. If there is no allow rule for avp.Exe, t...
Page 249
Advanced options 249 figure 104. Notification on ssl connection detection to scan encrypted connections, kaspersky internet security replaces the security certificate requested with a certificate it signs itself. In some cases, programs that are establishing connections will not accept this certific...
Page 250
250 k aspersky internet security 6.0 17.9. Configuring the kaspersky internet security interface kaspersky internet security gives you the option of changing the appearance of the program by creating and using skins. You can also configure the use of active interface elements such as the system tray...
Page 251
Advanced options 251 depending on the program operation performed, the system tray icon changes. For example, if a script is being scanned, a small depiction of a script appears in the background of the icon, and if an email is being scanned, an envelope. By default, icon animation is enabled. If yo...
Page 252
252 k aspersky internet security 6.0 • microsoft windows xp service pack 2 system files • a set of operating system diagnostic utilities • kaspersky internet security program files • files containing threat signatures to create a rescue disk: 1. Open the program’s main window and select rescue disk ...
Page 253
Advanced options 253 • folder where rescue disk files will be saved before burning the cd if you are not creating an emergency disk for the first time, this folder will already contain a set of files made the last time. To use files saved previously, check the corresponding box. Note that a previous...
Page 254
254 k aspersky internet security 6.0 17.10.2. Using the rescue disk note that kaspersky internet security only works in system rescue mode if the main window is opened. When you close the main window, the program will close. Bart pe, the default program, does not support .Chm files or internet brows...
Page 255
Advanced options 255 session with a rescue disk. Otherwise, these objects will be lost when you restart your computer. 17.11. Using advanced options kaspersky internet security provides you with the following advanced features: • notifications of certain events that occur in the program • kaspersky ...
Page 256
256 k aspersky internet security 6.0 to use this feature, you must: 1. Check enable notifications in the interaction with user box (see fig. 106). Figure 106. Enabling notifications 2. Click on the settings button to open the notification settings window. 3. On the events tab, define the event types...
Page 257
Advanced options 257 you can configure the following notification methods for the events listed above in the notification settings window that opens (see fig. 107): • popup messages above the program icon in the system tray that contain an informative message on the event that occurred. To use this ...
Page 258
258 k aspersky internet security 6.0 17.11.1.2. Configuring email notification after you have selected the events (see 17.11.1.1 on pg. 256) about which you wish to receive email notifications, you must set up notification delivery. To do so: 1. Open the program setup window with the settings link i...
Page 259
Advanced options 259 figure 108. Configuring email notification settings 17.11.1.3. Configuring event log settings to configure event log settings: 1. Open the application settings window with the settings link in the main window. 2. Select service in the settings tree. 3. Click advanced in the inte...
Page 260
260 k aspersky internet security 6.0 logs can be viewed in the microsoft windows event viewer, which you can open by going to start/settings/control panel/administration/view events. 17.11.2. Self-defense and access restriction kaspersky internet security ensures your computer’s security against mal...
Page 261
Advanced options 261 figure 109. Configuring program defense to password-protect the program, check enable password protection. Click on the settings button to open the password protection window, and enter the password and area that the access restriction will cover(see fig. 110). You can block any...
Page 262
262 k aspersky internet security 6.0 17.11.3. Resolving conflicts between kaspersky internet security and other programs in some cases, kaspersky internet security may cause conflicts with other applications installed on a computer. This is because those programs have built- in self-defense mechanis...
Page 263
Advanced options 263 to import settings from a configuration file: 1. Open the kaspersky internet security main window. 2. Select the service section and click settings. 3. Click the load button and select the file from which you want to import kaspersky internet security settings. 17.13. Resetting ...
Page 264
264 k aspersky internet security 6.0 to keep. In addition, settings that you configured with the setup wizard will also be applied..
Page 265
Chapter 18. Working with the program from the command prompt you can use kaspersky internet security from the command prompt. You can execute the following operations: • starting, stopping, pausing and resuming the activity of application components • starting, stopping, pausing and resuming virus s...
Page 266
266 k aspersky internet security 6.0 status displays the current component or task status on screen statistics displays statistics for the component or task on screen help help with command syntax and the list of commands scan scans objects for viruses update begins program update rollback rolls bac...
Page 267
Working with the program from the command prompt 267 program activation code provided when you purchased it. Name of the license key file with the extension .Key. Example: avp.Com activate 00000000-0000-0000-0000-000000000000 avp.Com addkey 00000000.Key 18.2. Managing program components and tasks yo...
Page 268
268 k aspersky internet security 6.0 em mail anti-virus wm web anti-virus bm proactive defense aspy anti-spy ah anti-hacker as anti-spam updater updater scan_objects virus scan task scan_my_computer my computer task scan_critical_areas critical areas task scan_startup startup objects task user-defin...
Page 269
Working with the program from the command prompt 269 avp.Com scan [] [] [ query>] [] [] [ file>] [] to scan objects, you can also start one of the tasks created in kaspersky internet security from the command prompt (see 18.1 on pg. 266). The task will be run with the settings specified in the progr...
Page 270
270 k aspersky internet security 6.0 /@: path to a file containing a list of objects and folders to be included in the scan. The file should be in a text format and each scan object must start a new line. You can enter an absolute or relative path to the file. The path must be placed in quotation ma...
Page 271
Working with the program from the command prompt 271 /fi scan only potentially infected files by contents (default) /fa scan all files - this parameter defines objects that are excluded from the scan. It can include several values from the list provided, separated by spaces. /e:a do not scan archive...
Page 272
272 k aspersky internet security 6.0 start a scan of ram, startup programs, email databases, the directories my documents and program files, and the file test.Exe: avp.Com scan /memory /startup /mail "c:\documents and settings\all users\my documents" "c:\program files" "c:\downloads\test.Exe" pause ...
Page 273
Working with the program from the command prompt 273 /c: path to the configuration file with the settings for program updates. You can enter an absolute or relative path to the file. If this parameter is not defined, the values for the settings in the kaspersky internet security interface are used. ...
Page 274
274 k aspersky internet security 6.0 parameter description: component or task with the settings being exported. One of the following values may be used: rtp – all protection components fm – file anti-virus em – mail anti-virus wm – web anti-virus bm - proactive defense aspy – anti-spy ah – anti-hack...
Page 275
Working with the program from the command prompt 275 note that you cannot execute this command without entering the password. Example: avp.Com import c:\settings.Dat password= 18.8. Starting the program command syntax: avp.Com 18.9. Stopping the program command syntax: exit /password= kaspersky inte...
Page 276
18.11. Return codes from the command line interface this section contains a list of return codes from the command line. The general codes may be returned by any command from the command line. The return codes include general codes as well as codes specific to a specific type of task. General return ...
Page 277
Modifying, repairing, and removing the program 277 chapter 19. Modifying, repairing, and removing the program you can uninstall the application in the following ways: • using the application's installation wizard (see 19.2 on pg. 279) • from the command prompt (see 19.2 on pg. 279) 19.1. Modifying, ...
Page 278
278 k aspersky internet security 6.0 step 1. Installation welcome window if you take all the steps described above necessary to repair or modify the program, the kaspersky internet security installation welcome window will appear. To continue, click the next button. Step 2. Selecting an operation at...
Page 279
Modifying, repairing, and removing the program 279 warning! If a long period of time elapses between uninstalling one version of kaspersky internet security and installing another, you are advised not to use the iswift database from a previous installation. A dangerous program could penetrate the co...
Page 280
Chapter 20. Frequently asked questions this chapter is devoted to the most frequently asked questions from users pertaining to installation, setup and operation of the kaspersky internet security; here we shall try to answer them here in detail. Question: is it possible to use kaspersky internet sec...
Page 281
Chapter 20 281 3. Open kaspersky internet security. 4. Use the settings link in the main window and select the protection section in the program settings window. 5. Uncheck run program system startup and click ok. 6. Reboot the operating system in regular mode. After this contact the technical suppo...
Page 282
Appendix a. Reference information this appendix contains reference materials on the file formats and extension masks used in kaspersky internet security settings. A.1. List of files scanned by extension if you select scan programs and documents (by extension), file anti-virus will scan files with th...
Page 283
Appendix a 283 vbs – visual basic script vbe – bios video extension js, jse – javascript source text htm – hypertext document htt – microsoft windows hypertext header hta – hypertext program for microsoft internet explorer asp – active server pages script chm – compiled html file pht – html with bui...
Page 284
284 k aspersky internet security 6.0 pp* – microsoft office powerpoint documents and files, such as: pps – microsoft office powerpoint slide, ppt – presentation, etc. Md* – microsoft office access documents and files, such as: mda – microsoft office access work group, mdb – database, etc. Remember t...
Page 285
Appendix a 285 tip: *.* and * exclusion masks can only be used if you assign a classification excluded according to the virus encyclopedia. Otherwise the threat specified will not be detected in any objects. Using these masks without selecting a classification essentially disables monitoring. We als...
Page 286
Appendix b. Kaspersky lab founded in 1997, kaspersky lab has become a recognized leader in information security technologies. It produces a wide range of data security software and delivers high-performance, comprehensive solutions to protect computers and networks against all types of malicious pro...
Page 287
Appendix b 287 b.1. Other kaspersky lab products kaspersky anti-virus ® 6.0 kaspersky anti-virus 6.0 is designed to safeguard personal computers against malicious software as an optimal combination of conventional methods of anti- virus protection and new proactive technologies. The program provides...
Page 288
288 k aspersky internet security 6.0 • the product allows the users to subscribe and unsubscribe from news channels. • it retrieves news from each subscribed channel at the specified frequency and notifies the user of fresh news. • it allows news on the subscribed channels to be reviewed. • it allow...
Page 289
Appendix b 289 • anti-virus monitor to intercept viruses in files that are either copied from other handhelds or are transferred using hotsync™ technology. Kaspersky ® security for pda protects your handheld (pda) from unauthorized intrusion by encrypting both access to the device and data stored on...
Page 290
290 k aspersky internet security 6.0 you are free to choose from any of these anti-virus applications, according to the operating systems and applications you use. Kaspersky ® corporate suite this package provides corporate networks of any size and complexity with comprehensive, scalable anti-virus ...
Page 291
Appendix b 291 installed at the entrance to a network, where it monitors incoming email traffic streams for spam, kaspersky ® anti-spam acts as a barrier to unsolicited email. The product is compatible with any email system and can be installed on either an existing email server or a dedicated one. ...
Page 292
292 k aspersky internet security 6.0 kaspersky anti-virus ® for proxy server kaspersky anti-virus ® for proxy server is an antivirus solution for protecting web traffic transferred over http protocol through a proxy server. The application scans internet traffic in real time, protects against malwar...
Page 293
Appendix c. License agreement standard end user license agreement notice to all users: carefully read the following legal agreement (“agreement”), for the license of kaspersky internet security (“software”) produced by kaspersky lab (“kaspersky lab”). If you have purchased this software via the inte...
Page 294
294 k aspersky internet security 6.0 all references to “software” herein shall be deemed to include the software activation code with which you will be provided by kaspersky lab as part of the kaspersky internet security 6.0. 1. License grant. Subject to the payment of the applicable license fees, a...
Page 295
Appendix c 295 1.1.7 kaspersky lab may ask user to install the latest version of the software (the latest version and the latest maintenance pack). 1.1.8 you shall not use this software in automatic, semi-automatic or manual tools designed to create virus signatures, virus detection routines, any ot...
Page 296
296 k aspersky internet security 6.0 (e) technical support via internet and hot phone-line provided by vendor and/or reseller; (f) virus detection and disinfection updates in 24-hours period. (v) support services are provided only if and when you have the latest version of the software (including ma...
Page 297
Appendix c 297 may be reasonably necessary to assist the supplier in resolving the defective item. (v) the warranty in (i) shall not apply if you (a) make or cause to be made any modifications to this software without the consent of kaspersky lab, (b) use the software in a manner for which it was no...
Page 298
298 k aspersky internet security 6.0 (iii) subject to paragraph (i), the liability of kaspersky lab (whether in contract, tort, restitution or otherwise) arising out of or in connection with the supply of the software shall in no circumstances exceed a sum equal to the amount equally paid by you for...