- DL manuals
- Watchguard
- Network Router
- Firebox X10E
- User Manual
Watchguard Firebox X10E User Manual - Table of Contents
User Guide
iii
Table of Contents
Chapter 1
Introduction to Network Security ........................................................................................... 1
About networks and network security .......................................................................................................... 1
About Internet Connections ......................................................................................................................... 1
About protocols................................................................................................................................................. 2
How Information Travels on the Internet................................................................................................. 2
About IP addresses................................................................................................................................................ 3
Private addresses and gateways............................................................................................................. 3
About subnet masks ................................................................................................................................... 4
About slash notation ....................................................................................................................................... 4
About entering IP addresses......................................................................................................................... 4
About DHCP........................................................................................................................................................ 5
About PPPoE....................................................................................................................................................... 5
About Domain Name Service (DNS) ............................................................................................................... 5
About services and policies ............................................................................................................................... 5
About ports .................................................................................................................................................... 6
About Firewalls....................................................................................................................................................... 7
The Firebox X Edge and your Network .......................................................................................................... 8
Chapter 2
Installation ................................................................................................................................ 9
Before you begin.................................................................................................................................................... 9
Verify basic requirements .............................................................................................................................. 9
Network Addressing Requirements .................................................................................................... 11
Find your TCP/IP Properties ................................................................................................................... 11
Finding your TCP/IP properties on Microsoft Windows Vista .................................................... 11
Finding your TCP/IP properties on Microsoft Windows NT ........................................................ 12
Finding your TCP/IP properties on Macintosh OS 9 ...................................................................... 12
Finding your TCP/IP properties on Macintosh OS X 10.5 ............................................................ 12
Finding your TCP/IP properties on other operating systems (Unix, Linux)........................... 12
Find PPPoE settings................................................................................................................................... 12
Disable the HTTP proxy ..................................................................................................................................... 13
Disable the HTTP proxy in Internet Explorer 6.x or 7.x ................................................................. 13
Disable the HTTP proxy in Firefox 2.x ................................................................................................. 14
Disable the HTTP proxy in Safari 2.0.................................................................................................... 14
Summary of Firebox X10E
Page 1
Watchguard firebox x edge e-series user guide firebox x edge e-series version 10 all firebox x edge e-series standard and wireless models.
Page 2
Ii firebox x edge e-series address 505 fifth avenue south suite 500 seattle, wa 98104 support www.Watchguard.Com/support u.S. And canada +877.232.3531 all other countries +1.206.521.3575 sales u.S. And canada +1.800.734.9905 all other countries +1.206.613.0895 about watchguard since 1996, watchguard...
Page 3: Table of Contents
User guide iii table of contents chapter 1 introduction to network security ........................................................................................... 1 about networks and network security .................................................................................................
Page 4
Iv firebox x edge e-series disable pop-up blocking................................................................................................................................... 14 disable the pop-up blocker in internet explorer 6.X or 7.X ...........................................................
Page 5
User guide v about feature keys .............................................................................................................................................. 45 restart the firebox locally..................................................................................................
Page 6
Vi firebox x edge e-series configure wan failover ................................................................................................................................ 97 enable wan failover with the setup wizard ...............................................................................
Page 7
User guide vii about the http proxy..................................................................................................................................... 130 http proxy: proxy limits..........................................................................................................
Page 8
Viii firebox x edge e-series traffic marking ................................................................................................................................................... 167 types of nat..............................................................................................
Page 9
User guide ix configure groups for ldap authentication........................................................................................ 197 add a group for ldap authentication.................................................................................................. 198 set a webblocke...
Page 10
X firebox x edge e-series run the setup wizard................................................................................................................................. 231 define the server location.................................................................................................
Page 11
User guide xi chapter 19 about mobile vpn with pptp .............................................................................................. 265 enable pptp on the edge.................................................................................................................................
Page 12
Xii firebox x edge e-series.
Page 13: Introduction to Network
User guide 1 1 introduction to network security about networks and network security a network is a group of computers and other devices that are connected to each other. It can be two computers that you connect with a serial cable, or many computers around the world connected through the internet. C...
Page 14
Introduction to network security 2 firebox x edge e-series about protocols a protocol is a group of rules that allow computers to connect across a network. Protocols are the grammar of the language that computers use when they speak to each other across a network. The standard protocol when you conn...
Page 15: About Ip Addresses
User guide 3 introduction to network security the tcp and ip protocols are used to send and receive these packets. Tcp disassembles the data and assembles it again. Ip adds information to the packets, such as the sender, the recipient, and any special instructions. About ip addresses to send ordinar...
Page 16
Introduction to network security 4 firebox x edge e-series about subnet masks because of security and performance considerations, networks are often divided into smaller portions called subnets. All devices in a subnet have similar ip addresses. For example, all devices that have ip addresses whose ...
Page 17: About Services and Policies
User guide 5 introduction to network security static and dynamic ip addresses isps (internet service providers) assign an ip address to each device on their network. The ip address can be static or dynamic. A static ip address is an ip address that always stays the same. If you have a web server, ft...
Page 18
Introduction to network security 6 firebox x edge e-series world wide web access uses hypertext transfer protocol (http) email uses simple mail transfer protocol (smtp) or post office protocol (pop3) file transfer uses file transfer protocol (ftp) resolving a domain name to an internet addre...
Page 19: About Firewalls
User guide 7 introduction to network security about firewalls a firewall separates your trusted computers on the internal network from the external network, or the internet, to decrease risk of an external attack. The figure below shows how a firewall divides the trusted computers from the internet..
Page 20
Introduction to network security 8 firebox x edge e-series firewalls use access policies to identify and filter different types of information. They can also control which policies or ports the protected computers can use on the internet (outbound access). Many firewalls have sample security policie...
Page 21: Installation
User guide 9 2 installation before you begin to install the watchguard firebox x edge e-series in your network, you must complete these steps: identify and record the tcp/ip properties for your internet connection. disable the http proxy and pop-up blocker properties of your web browser. conne...
Page 22
Installation 10 firebox x edge e-series check package contents make sure that the package for your firebox x edge e-series includes these items: firebox x edge e-series user guide on cd-rom firebox x edge e-series quick start guide livesecurity service activation card hardware warranty card ...
Page 23
User guide 11 installation identify your network settings to configure your firebox x edge, you must know some information about your network. Use this section to learn how to identify your network settings. For an overview of network basics, see about networks and network security . Network address...
Page 24
Installation 12 firebox x edge e-series finding your tcp/ip properties on microsoft windows 2000, windows 2003, and windows xp 1. Select start > all programs > accessories > command prompt. The command prompt window appears. 2. At the command prompt, type ipconfig /all and press enter. 3. Record the...
Page 25: Disable The Http Proxy
User guide 13 installation register your firebox and activate livesecurity service to enable all of the features on your firebox x edge, you must register on the watchguard livesecurity web site and retrieve your feature key. You have only one user license (seat license) until you apply your feature...
Page 26: Disable Pop-Up Blocking
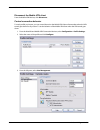
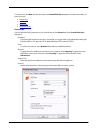
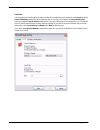
Installation 14 firebox x edge e-series disable the http proxy in firefox 2.X 1. Open the browser software. 2. Select tools > options. The options window appears. 3. Click the advanced icon. 4. Select the network tab. Click settings. 5. Click the connection settings button. The connection settings d...
Page 27: Connect The Firebox X Edge
User guide 15 installation connect the firebox x edge many people configure their firebox x edge e-series on one computer before they put it on the network. Use this procedure to connect a computer to your firebox x edge: 1. Shut down your computer. 2. If you use a dsl or cable modem to connect to t...
Page 28
Installation 16 firebox x edge e-series add computers to the trusted network you can connect as many as three computers to the trusted interface of the firebox x edge e-series if you connect each computer to one of the edge’s ethernet ports 0 through 2. You can use 10/100 baset ethernet hubs or swit...
Page 29
User guide 17 installation about user licenses your firebox x edge firewall is enabled with a set number of user licenses. The total number of available sessions is determined by the edge model you have, and any upgrade licenses you apply. The number of licenses limits the number of sessions. To con...
Page 30
Installation 18 firebox x edge e-series set your computer to connect to the edge before you can use the quick setup wizard, you must configure your computer to connect to the firebox x edge. You can set your network interface card to use a static ip address, or use dhcp to get an ip address automati...
Page 31
User guide 19 installation use a static ip address this procedure configures a computer with the windows xp operating system to use a static ip address. If your computer does not use windows xp, read the operating system help for instructions on how to set your computer to use a static ip address. Y...
Page 32: Run The Quick Setup Wizard
Installation 20 firebox x edge e-series run the quick setup wizard the quick setup wizard starts after you type https://192.168.111.1 into the url or address field of your internet browser. If your browser blocks pop-up windows, you must disable that function to complete the quick setup wizard. You ...
Page 33: Configuration Pages
User guide 21 3 configuration pages overview about edge configuration pages after you connect the watchguard firebox x edge e-series to your network, you must configure the edge. You can create firewall rules to enforce the security requirements of your company. You can also use the edge configurati...
Page 34
Configuration pages overview 22 firebox x edge e-series for example: 1. Start your web browser. 2. Select file > open, type https://192.168.111.1 in the open text box, and click ok. You also can type https://192.168.111.1 directly into the address or location bar and press enter. 3. When a security ...
Page 35
User guide 23 configuration pages overview navigating the firebox x edge user interface on the left side of the system status page is the navigation bar you use to get to other firebox x edge configuration pages. Each menu item contains secondary menus that you use to configure the properties of tha...
Page 36
Configuration pages overview 24 firebox x edge e-series network page the network page shows the current configuration of the trusted, optional, and external networks. On this page, you can also view wan failover and any static routes you have configured. Adjacent to each section is a button you can ...
Page 37
User guide 25 configuration pages overview firebox users page the firebox users page shows statistics on active sessions and local user accounts. It also has buttons to close current sessions and to add, edit, and delete user accounts. This page also shows the muvpn client configuration files that y...
Page 38
Configuration pages overview 26 firebox x edge e-series administration page the administration page shows whether the firebox x edge uses http or https for its configuration pages, if the edge is configured as a managed firebox client, and which feature upgrades are enabled. It has buttons to change...
Page 39
User guide 27 configuration pages overview firewall page the firewall page shows incoming and outgoing policies and proxies, blocked web sites, and other firewall settings. This page also has buttons to change these settings. For more information, look at the topics below proxy settings in the table...
Page 40
Configuration pages overview 28 firebox x edge e-series logging page the logging page shows the current event log, and the status of the log server and syslog logging. For more information, see the topics under logging in the table of contents..
Page 41
User guide 29 configuration pages overview webblocker page the webblocker page shows the webblocker settings, profiles, allowed sites, and denied sites. For more information, see about webblocker ..
Page 42
Configuration pages overview 30 firebox x edge e-series spamblocker page the spamblocker page shows spamblocker status and settings, including actions for suspected spam and the use of trusted email forwarders. For more information, see about spamblocker ..
Page 43
User guide 31 configuration pages overview gateway av/ips page the gateway av/ips page shows the gateway antivirus and intrusion prevention service status and settings. It tells you which proxies are enabled for the service, and what version of the signature database you are using. The gateway av/ip...
Page 44
Configuration pages overview 32 firebox x edge e-series vpn page the vpn page shows information on managed vpn gateways, manual vpn gateways, echo hosts, and buttons to change the configuration of vpn tunnels. You can add the firebox x edge e-series to a watchguard system manager vpn network with th...
Page 45
User guide 33 configuration pages overview monitoring the firebox x edge when you expand system status on the navigation bar, you see a list of monitoring categories. With these pages, you can monitor all the components of the edge and how they work. The firebox x edge monitor pages are not set to r...
Page 46
Configuration pages overview 34 firebox x edge e-series connections this status page shows all tcp/ip connections that go through the edge. It is divided between proxy filters and packet filters. The packet filter list is sorted by protocol, with tcp protocols at the top of the list, then udp connec...
Page 47
User guide 35 configuration pages overview components list this status page shows the software that is installed on the edge. Each attribute is shown separately: name version build number build time remove link - the remove column does not usually show any components. Any components shown ...
Page 48
Configuration pages overview 36 firebox x edge e-series dynamic dns this status page shows the state of the dynamic dns configuration. Last last time the dns was updated. Next next time the dns will be updated. Hostile sites this status page shows the amount of time an ip address is blocked from acc...
Page 49
User guide 37 configuration pages overview license this status page shows basic information about licenses that are used on the edge. It also shows the original feature key. You can see this information for each license: name - the name of the license use - the number of users maximum use - ma...
Page 50
Configuration pages overview 38 firebox x edge e-series protocols this status page shows the protocol statistics for ip, icmp, tcp, and udp. Routes this status page shows the edge routing table. Interface interface associated with the route. Network network that the route has been created for. Gatew...
Page 51
User guide 39 configuration pages overview traffic control this status page shows how traffic control handles packets. Priority you can set four levels of priority for traffic control: o interactive o high o medium o low rate rate set for each priority. Ceiling maximum bandwidth each priority can us...
Page 52
Configuration pages overview 40 firebox x edge e-series.
Page 53: Configuration and
User guide 41 4 configuration and management basics about basic configuration and management tasks after your firebox x edge e-series is installed on your network and operating with a basic configuration file, you can start to add custom configuration settings to meet the needs of your organization....
Page 54
Configuration and management basics 42 firebox x edge e-series before you begin do not edit your configuration file manually. Always use a watchguard management server or the firebox x edge web interface to make changes to your configuration. user passwords in the backup configuration file are e...
Page 55
User guide 43 configuration and management basics back up your edge configuration after you have configured your firebox x edge e-series, you can save your edge configuration file to your local hard drive for backup purposes. You can use your backup file to restore your edge to a previous configurat...
Page 56
Configuration and management basics 44 firebox x edge e-series about factory default settings the term factory default settings refers to the configuration on the firebox x edge when you first receive it before you make any changes. The default network and configuration properties for the edge are: ...
Page 57: About Feature Keys
User guide 45 configuration and management basics restore the firebox to the factory default settings if you cannot correct a configuration problem and must start over, you can restore the factory default settings. For example, if you do not know the administrator account passphrase or a power inter...
Page 58
Configuration and management basics 46 firebox x edge e-series get a feature key before you activate a new feature, you must have a license key certificate from watchguard that is not already registered on the livesecurity web site. 1. Open a web browser and connect to: https://www.Watchguard.Com/ac...
Page 59: About Restarting The Firebox
User guide 47 configuration and management basics about restarting the firebox you can restart the firebox x edge e-series from a computer on the trusted network. If you enable external access to the edge, you also can restart the edge from a computer on the internet. The firebox x edge restart cycl...
Page 60
Configuration and management basics 48 firebox x edge e-series restart the firebox remotely if you want to be able to connect to the edge to manage it or restart it from a computer external to the edge, you must first configure the edge to allow incoming https traffic to the edge trusted interface i...
Page 61
User guide 49 configuration and management basics about using ntp to set system time to set the system time for edge, you can specify a ntp server to set the time automatically. The network time protocol (ntp) synchronizes computer clock times across a network. The firebox can use ntp to get the cor...
Page 62
Configuration and management basics 50 firebox x edge e-series to set the system time 1. To connect to the system status page, type https:// in the browser address bar, and the ip address of the firebox x edge trusted interface. The default url is: https://192.168.111.1 2. From the navigation bar, s...
Page 63
User guide 51 configuration and management basics 5. If you set the system time automatically, the firebox x edge gets the current time from the selected server in the ntp servers list. If that server is not available, the edge uses the next server. O to add a time server, type the server name in th...
Page 64: About Snmp
Configuration and management basics 52 firebox x edge e-series about snmp simple network management protocol (snmp) is a set of tools for monitoring and managing networks. Snmp uses management information bases (mibs) that give configuration information for the devices the snmp server manages or mon...
Page 65
User guide 53 configuration and management basics about mibs a mib (management information base) is a database of objects that can be monitored by a network management system. The firebox x edge e-series supports six different public, read-only mibs: ip-mib if-mib tcp-mib udp-mib snmpv2-mi...
Page 66
Configuration and management basics 54 firebox x edge e-series about selecting http or https for management http (hypertext transfer protocol) is the language used to move files (text, graphic images, and multimedia files) on the internet. Https (hypertext transfer protocol over secure socket layer)...
Page 67
User guide 55 configuration and management basics change the http server port https typically uses tcp port 443 and http typically uses tcp port 80. By default, you must connect to the firebox x edge e-series configuration pages on those ports. You can change the default port on the administration >...
Page 68
Configuration and management basics 56 firebox x edge e-series enable centralized management with wsm use these instructions to configure remote access from watchguard system manager (wsm) 10. Wsm 10 allows centralized management of firebox x edge e-series devices running v10. 1. To connect to the s...
Page 69
User guide 57 configuration and management basics 8. In the management server address text box, type the ip address of the management server if it has a public ip address. If the management server has a private ip address, type the public ip address of the firebox that protects the management server...
Page 70
Configuration and management basics 58 firebox x edge e-series enable remote management with wfs v7.3 or earlier use these instructions to configure remote access from watchguard firebox system v7.3 or earlier. These versions of watchguard firebox system use vpn manager and the firebox is the dvcp s...
Page 71
User guide 59 configuration and management basics 7. Select the enable managed vpn check box to configure the firebox x edge as a client to the watchguard dvcp server. 8. In the dvcp server address text box, type the ip address of the dvcp server. 9. Type the client name to give to your firebox x ed...
Page 72
Configuration and management basics 60 firebox x edge e-series method 2: install software manually the second method uses the firebox x edge e-series configuration pages. This method can be used with windows or other operating systems. You must first download the software update file, which is a sma...
Page 73: About Upgrade Options
User guide 61 configuration and management basics about upgrade options you use two items to add upgrades to your firebox x edge: a feature key and a license key. It is important to understand the differences between these two keys. Your firebox x edge comes with certain features by default. These f...
Page 74
Configuration and management basics 62 firebox x edge e-series add a feature to your firebox x edge when you purchase an upgrade for your firebox x edge, you receive a license key. This can be a paper certificate or an email message. You can use this procedure to manually apply a new feature key to ...
Page 75
User guide 63 configuration and management basics upgrade your firebox x edge model a model upgrade gives the firebox x edge e-series the same functions as a higher model. A model upgrade increases capacity, user licenses, sessions, and vpn tunnels. For a brochure that shows the features of the diff...
Page 76
Configuration and management basics 64 firebox x edge e-series.
Page 77: Network Settings
User guide 65 5 network settings about network interface setup a primary component of the watchguard firebox setup is the configuration of network interface ip addresses. When you run the quick setup wizard, the external and trusted interfaces are set up so traffic can flow through the firebox. You ...
Page 78: Setup Wizard
Network settings 66 firebox x edge e-series change the firebox ip addresses with the network setup wizard the easiest method to change the network ip addresses of the firebox x edge e-series is with the network setup wizard. 1. To connect to the system status page, type https:// in the browser addre...
Page 79
User guide 67 network settings configure external interfaces you must configure your external network manually if you do not use the network setup wizard. When you configure the external network, set the method your internet service provider (isp) uses to give you an ip address for your firebox. If ...
Page 80
Network settings 68 firebox x edge e-series if your isp uses static ip addresses if your isp uses static ip addresses, you must enter the address information into your firebox x edge before it can send traffic through the external interface. To set your firebox x edge to use a static ip address for ...
Page 81
User guide 69 network settings if your isp uses pppoe if your isp uses pppoe, you must enter the pppoe information into your firebox x edge before it can send traffic through the external interface. For more information in pppoe, see advanced pppoe settings . To set your firebox to use pppoe on the ...
Page 82
Network settings 70 firebox x edge e-series advanced pppoe settings the quick setup wizard allows you to set up basic pppoe settings. If necessary, you can also configure more advanced settings. Click submit when you have completed the configuration of the advanced pppoe settings. Service name use t...
Page 83
User guide 71 network settings configure your external interface as a wireless interface you can configure your primary external interface (wan1) for your edge as a wireless interface. 1. To connect to the system status page, type https:// in the browser address bar, followed by the ip address of th...
Page 84
Network settings 72 firebox x edge e-series about advanced external network settings on the external network configuration page, select the advanced tab to change the settings for link speed or change the mac address for the edge’s external interface. Select automatic from the link speed drop-down l...
Page 85
User guide 73 network settings change the mac address of the external interface some isps use a mac address to identify the computers on their network. Each mac address gets one static ip address. If your isp uses this method to identify your computer, then you must change the mac address of the fir...
Page 86
Network settings 74 firebox x edge e-series about configuring the trusted network you must configure your trusted network manually if you do not use the network setup wizard. You can use static ip addresses or dhcp for the computers on your trusted network. The firebox x edge e- series has a built-i...
Page 87
User guide 75 network settings change the ip address of the trusted network to change the ip address of the trusted network: 1. To connect to the system status page, type https:// in the browser address bar, followed by the ip address of the firebox x edge trusted interface. The default url is: http...
Page 88
Network settings 76 firebox x edge e-series enable dhcp server on the trusted network the dhcp server option allows the firebox x edge e-series to give ip addresses to the computers on the trusted network. When the edge receives a dhcp request from a computer on the trusted network, it gives the com...
Page 89
User guide 77 network settings set trusted network dhcp address reservations 1. You can manually give the same ip address to a specified computer on your trusted network each time that computer makes a request for a dhcp ip address. The firebox x edge identifies the computer by its mac address. 2. U...
Page 90
Network settings 78 firebox x edge e-series about dhcp relay agents one way to get ip addresses for the computers on the trusted or optional networks is to use a dhcp server on a different network. The firebox can send a dhcp request from a dhcp client to a dhcp server at a different location throug...
Page 91
User guide 79 network settings use static ip addresses for trusted computers you can use static ip addresses for some or all of the computers on your trusted network. If you disable the firebox x edge dhcp server and you do not have a dhcp server on your network, you must manually configure the ip a...
Page 92
Network settings 80 firebox x edge e-series restrict access to the trusted interface by mac address 1. To connect to the system status page, type https:// in the browser address bar, and the ip address of the firebox x edge trusted interface. The default url is: https://192.168.111.1 2. From the nav...
Page 93
User guide 81 network settings 4. Click scan to have the edge find all known hardware addresses on the network. If you want the edge to try to resolve host names for all windows computers it finds during the scan process, make sure the try to resolve windows host names during scan check box is selec...
Page 94
Network settings 82 firebox x edge e-series 6. To manually add a hardware address and its host name to your configuration, click add. The add allowed address control dialog box appears. 7. Select the log attempted access from mac addresses not in the list check box if you want the edge to generate a...
Page 95
User guide 83 network settings enable the optional network 1. To connect to the system status page, type https:// in the browser address bar, followed by the ip address of the firebox x edge trusted interface. The default url is: https://192.168.111.1 2. From the navigation bar, select network > opt...
Page 96
Network settings 84 firebox x edge e-series enable dhcp server on the optional network the dhcp server option sets the firebox x edge to give ip addresses to the computers on the optional network. When the edge receives a dhcp request from a computer on the optional network, it gives the computer an...
Page 97
User guide 85 network settings set optional network dhcp address reservations you can manually assign an ip address to a specified computer on your optional network. The firebox x edge identifies the computer by its mac address. 1. Use your browser to connect to the system status page. From the navi...
Page 98
Network settings 86 firebox x edge e-series about dhcp relay agents one way to get ip addresses for the computers on the trusted or optional networks is to use a dhcp server on a different network. The firebox can send a dhcp request from a dhcp client to a dhcp server at a different location throug...
Page 99
User guide 87 network settings allow wireless connections to the optional interface the firebox x edge e-series wireless can be configured as a wireless access point with three different security zones. You can enable wireless devices to connect to the edge wireless as part of the trusted network or...
Page 100: About Static Routes
Network settings 88 firebox x edge e-series about static routes a route is the sequence of devices through which network traffic must go to get from its source to its destination. A router is the device in a route that finds the subsequent network point through which to send the network traffic to i...
Page 101
User guide 89 network settings 4. From the type drop-down list, select host or network. Select network if you have a full network behind a router on your local network. Select host if only one host is behind the router or you want traffic to go to only one host. 5. Type the destination ip address an...
Page 102
Network settings 90 firebox x edge e-series about the dynamic dns service you can register the external ip address of the firebox with the dynamic domain name server (dns) service dyndns.Org. A dynamic dns service makes sure that the ip address attached to your domain name changes when your isp give...
Page 103
User guide 91 network settings 5. In the system drop-down list, select the system to use for this update. For an explanation of each option, see http://www.Dyndns.Com/services/ . O the option dyndns sends updates for a dynamic dns host name. Use the dyndns option when you have no control over your i...
Page 104
Network settings 92 firebox x edge e-series configure the firebox to use bids telstra customers in australia must use client software to connect to the bigpond network. The firebox x edge e-series uses bids to make this connection. If you do not connect to the bigpond network, it is not necessary to...
Page 105
User guide 93 network settings about using multiple external interfaces with the firebox, you can have redundant support for the external interface. Companies use this option if they must have a constant internet connection. If you have an edge pro license for your firebox x edge and have a second i...
Page 106
Network settings 94 firebox x edge e-series about multi-wan and dns when you configure more than one external interface on your edge, it is a good idea to enter two dns server addresses when you configure dhcp settings for the trusted and optional networks. Some isps allow queries to their dns serve...
Page 107
User guide 95 network settings configure advanced wan2 settings you can configure additional settings for your second wan interface (wan2) on the advanced tab below wan 2. 1. From the link speed drop-down list, select automatic if you want the edge to select the best network speed. You can also sele...
Page 108
Network settings 96 firebox x edge e-series configure the edge to use round-robin load balancing 1. From the navigation bar, select network > external. If you have an edge pro license, you see the options to configure your edge with a multi-wan configuration. 2. Select the use multi-wan check box. 3...
Page 109
User guide 97 network settings configure wan failover if you have an edge pro license, you can configure your firebox x edge with a wan failover configuration and use a second external interface connected to a broadband internet connection. To configure the wan failover network: 1. Connect one end o...
Page 110
Network settings 98 firebox x edge e-series 2. Select the enable failover using the ethernet (wan2) interface check box. 3. Type the ip addresses of the hosts to ping for the wan1 (external) and wan2 (failover) interfaces. The firebox x edge will send pings to the ip addresses you type here. If ping...
Page 111
User guide 99 network settings configure your modem for wan failover use the settings available in the modem (serial port) configuration area of the network > external page to set up your external modem for failover. The edge has been tested with these modems: hayes 56k v.90 serial fax modem zoo...
Page 112
Network settings 100 firebox x edge e-series dns settings if your dial-up isp does not give dns server ip addresses, or if you must use a different dns server, you can manually enter the ip addresses for a dns server to use after failover occurs. 1. Select the manually configure dns server ip addres...
Page 113
User guide 101 network settings about virtual local area networks (vlans) an 802.1q vlan (virtual local area network) is a collection of computers on a lan or lans that are grouped together independent of their physical location. When you create a vlan, you create a new software-based network interf...
Page 114
Network settings 102 firebox x edge e-series add a vlan tag to the trusted or optional interface to mark sent to the trusted or optional interface on your edge as part of a vlan: 1. To connect to the system status page, type https:// in the browser address bar, followed by the ip address of the fire...
Page 115: Wireless Setup
User guide 103 6 wireless setup about wireless setup the firebox x edge e-series wireless can be configured as a wireless access point with three different security zones. You can enable wireless devices to connect to the edge wireless as part of the trusted network or part of the optional network. ...
Page 116
Wireless setup 104 firebox x edge e-series about wireless configuration settings when you enable wireless access to the trusted, optional, or wireless guest network, some configuration settings are common to all three security zones. Change the ssid the ssid (service set identifier) is the unique na...
Page 117
User guide 105 wireless setup log authentication events an authentication event occurs when a wireless computer tries to connect to an edge wireless interface. To have the edge record these events in the log file, select the log authentication events check box. Change the fragmentation threshold the...
Page 118
Wireless setup 106 firebox x edge e-series set the wireless authentication method five authentication methods are available in the firebox x edge e-series wireless. We recommend that you use wpa2 if possible because it is the most secure. The five available methods, from least secure to most secure,...
Page 119
User guide 107 wireless setup about wireless connections to the trusted interface if you enable wireless connections to the trusted interface, we recommend that you enable and use the edge feature that allows you to restrict access to the trusted interface by mac address. This prevents users from co...
Page 120
Wireless setup 108 firebox x edge e-series 8. From the authentication drop-down list, select the type of authentication to enable for wireless connections to the trusted interface. We recommend that you use wpa2 if the wireless devices in your network can support wpa2. 9. From the encryption drop-do...
Page 121
User guide 109 wireless setup allow wireless connections to the optional interface 1. To connect to the system status page, type https:// in the browser address bar, and the ip address of the firebox x edge trusted interface. The default url is: https://192.168.111.1 2. From the navigation bar, sele...
Page 122
Wireless setup 110 firebox x edge e-series 6. In the network name (ssid) text box, type a unique name for your edge wireless optional network or use the default name. 7. To change the fragmentation threshold, type a value in the fragmentation threshold field. The possible values are 256 through 2346...
Page 123
User guide 111 wireless setup enable a wireless guest network manually 1. To connect to the system status page, type https:// in the browser address bar, and the ip address of the firebox x edge trusted interface. The default url is: https://192.168.111.1 2. From the navigation bar, select network >...
Page 124
Wireless setup 112 firebox x edge e-series 5. If you want to configure the edge as a dhcp server when a wireless device tries to make a connection, select the enable dhcp server on wireless guest network check box. To learn more about configuring the settings for the dhcp server, see enable dhcp ser...
Page 125
User guide 113 wireless setup about wireless radio settings the firebox x edge e-series wireless uses radio frequency signals to send and receive traffic from computers with wireless ethernet cards. Several settings are specific to edge channel selection. You can see and change these settings if you...
Page 126
Wireless setup 114 firebox x edge e-series configure the wireless card on your computer these instructions are for the windows xp with service pack 2 operating system. To see the installation instructions for other operating systems, go to your operating system documentation or help files. 1. Select...
Page 127: Firewall Policies
User guide 115 7 firewall policies about policies the firebox uses two categories of policies to filter network traffic: packet filters and proxies. A packet filter examines each packet’s ip and tcp/udp header. If the packet header information is legitimate, then the firebox allows the packet. Other...
Page 128
Firewall policies 116 firebox x edge e-series as an example of how a policy might be used, suppose the network administrator of a company wants to activate a windows terminal services connection to the company’s public web server on the optional interface of the firebox. He or she routinely administ...
Page 129
User guide 117 firewall policies about policy-based routing to send network traffic, a router usually examines the destination address in the packet and looks at the routing table to find the next-hop destination. In some cases, you want to send traffic to a different path than the default route spe...
Page 130
Firewall policies 118 firebox x edge e-series about using common packet filter policies you can control the traffic between the trusted, optional, and external networks using packet filter policies. The firebox x edge supplies a list of frequently used policies, called common policies, that you can ...
Page 131
User guide 119 firewall policies editing common packet filter policies you can edit some default settings of a common packet filter policy. On the incoming tab, you can define a service host, redirect the port, enable logging, or restrict the ip addresses on the external network that can connect to ...
Page 132
Firewall policies 120 firebox x edge e-series set access control options (outgoing) 1. From the edit policies page, select the outgoing tab. 2. From the outgoing filter drop-down list, select the rule you want to apply. This rule affects only outgoing traffic. 3. To specify which computers on your t...
Page 133: About Custom Policies
User guide 121 firewall policies about custom policies you must define a custom policy for traffic if you need to allow for a protocol that is not included by default as a firebox configuration option. A custom policy is also necessary if: you must create an additional packet filter for a policy. ...
Page 134
Firewall policies 122 firebox x edge e-series add a custom packet filter policy manually you can add a custom policy without the wizard. 1. To connect to the system status page, type https:// in the browser address bar, and the ip address of the firebox x edge trusted interface. The default url is: ...
Page 135
User guide 123 firewall policies filter outgoing traffic for a custom policy these steps restrict outgoing traffic through the firebox x edge. For information on how to restrict incoming traffic, see filter incoming traffic for a custom policy . 1. From the outgoing filter drop-down list, select all...
Page 136
Firewall policies 124 firebox x edge e-series about policies for the optional network by default, the firebox x edge e-series allows all traffic that starts in the trusted network and tries to go to the optional network, and denies all traffic that starts in the optional network and tries to go to t...
Page 137
User guide 125 firewall policies disable traffic filters between trusted and optional networks to allow network traffic from the optional network to the trusted network, you must allow all traffic between the trusted and optional networks. Select the disable traffic filters check box to allow all in...
Page 138: About Policy Precedence
Firewall policies 126 firebox x edge e-series about policy precedence precedence is the sequence in which the firebox examines network traffic and applies a policy rule. The firebox automatically sorts policies from the most detailed to the most general. It compares the information in the packet to ...
Page 139: Proxy Settings
User guide 127 8 proxy settings about proxy policies all watchguard policies, whether they are packet filter policies or proxy policies, are important tools for network security. While a packet filter examines each packet’s ip and tcp/udp header, a proxy monitors and scans whole connections. It exam...
Page 140
Proxy settings 128 firebox x edge e-series about adding and configuring proxy policies when you add a proxy policy to your firebox configuration, you specify types of content that the proxy must look for as it filters traffic. If the content matches (or does not match) the criteria you set in the pr...
Page 141
User guide 129 proxy settings to add or edit a custom proxy policy: 1. To connect to the system status page, type https:// in the browser address bar, and the ip address of the firebox x edge trusted interface. The default url is: https://192.168.111.1 2. From the navigation bar, select firewall set...
Page 142: About The Http Proxy
Proxy settings 130 firebox x edge e-series about the http proxy hyper text transfer protocol (http) is a request/response protocol between clients and servers. The http client is usually a web browser. The http server is a remote resource that keeps or creates html files, images, and other content. ...
Page 143
User guide 131 proxy settings http responses: general settings when the remote http server accepts the connection request from the http client, most browser status bars show, "site contacted. Waiting for reply..." then the http server sends the appropriate response to the http client. This is usuall...
Page 144
Proxy settings 132 firebox x edge e-series configure the http proxy policy deny message 1. To connect to the system status page, type https:// in the browser address bar, and the ip address of the firebox x edge trusted interface. The default url is: https://192.168.111.1 2. From the navigation bar,...
Page 145
User guide 133 proxy settings http proxy exceptions you use http proxy exceptions to bypass http proxy rules for certain web sites without bypassing the proxy framework. Traffic that matches http proxy exceptions still goes through the standard proxy handling used by the http proxy. However, when a ...
Page 146
Proxy settings 134 firebox x edge e-series add, delete, or modify content types 1. Select the http content tab. 2. Select the allow only safe content types check box if you want to limit content types allowed through the proxy. A list of common mime types is included by default. 3. To add common con...
Page 147: About The Ftp Proxy
User guide 135 proxy settings about the ftp proxy ftp (file transfer protocol) is used to send files from one computer to a different computer over a tcp/ip network. The ftp client is usually a computer. The ftp server can be a resource that keeps files on the same network or on a different network....
Page 148
Proxy settings 136 firebox x edge e-series ftp proxy: proxy limits on the ftp settings tab, you can set the maximum user name length, password length, file name length, and command-line length allowed through the proxy. These limits help protect your network from buffer overflow attacks. Use the def...
Page 149
User guide 137 proxy settings ftp proxy: upload and download content you can control the type of files that the ftp proxy allows for downloads and uploads. For example, because many hackers use executable files to deploy viruses or worms on a computer, you could select to deny requests for *.Exe fil...
Page 150: About The Pop3 Proxy
Proxy settings 138 firebox x edge e-series about the pop3 proxy pop3 (post office protocol v.3) is a protocol that moves email messages from an email server to an email client on a tcp connection on port 110. Most internet-based email accounts use pop3. With pop3, an email client contacts the email ...
Page 151
User guide 139 proxy settings pop3 proxy: proxy limits on the pop3 settings tab, you can adjust timeout and line length limits. This stops the pop3 proxy from using too many network resources and can prevent some types of attacks. You can also customize the deny message that users see when an email ...
Page 152
Proxy settings 140 firebox x edge e-series %(filename)% puts the name of the attached file. %(virus)% puts the type of virus found. %(action)% puts the action taken by the proxy policy. %(reason)% puts the reason the proxy policy denied the content. %(recovery)% puts whether you can recover the atta...
Page 153
User guide 141 proxy settings pop3 proxy: content types certain kinds of content embedded in email can be a security threat to your network. Other kinds of content can decrease the productivity of your users. On the pop3 content tab, you limit content types, and block specified path patterns and url...
Page 154
Proxy settings 142 firebox x edge e-series pop3 proxy: allow only safe content types the headers for email messages include a content type header to show the mime type of the email and the mime type of any attachments. The content type or mime type tells the computer the types of media the message c...
Page 155: About The Smtp Proxy
User guide 143 proxy settings about the smtp proxy smtp (simple mail transport protocol) is a protocol used to send email messages between email servers and also between email clients and email servers. It usually uses a tcp connection on port 25. You use the smtp proxy to control email messages and...
Page 156
Proxy settings 144 firebox x edge e-series set access control options on the outgoing or incoming tab, you can set rules that filter ip addresses, network addresses, or host ranges. This is the same functionality you have in packet filter policies. 1. Select the outgoing tab. 2. From the outgoing fi...
Page 157
User guide 145 proxy settings smtp proxy: proxy limits on the smtp settings tab, you can adjust timeout, email size, and line length limits. This stops the smtp proxy from using too many network resources and can prevent some types of attacks. You can also customize the deny message that users see w...
Page 158
Proxy settings 146 firebox x edge e-series smtp proxy: deny message in the deny message field, you can write a custom plain text message that will appear in the recipient email message when the proxy blocks that message. You can use these variables: %(type)% puts the content type of the email messag...
Page 159
User guide 147 proxy settings smtp proxy: email content certain kinds of content embedded in email can be a security threat to your network. Other kinds of content can decrease the productivity of your users. On the smtp content tab, you limit content types, and block specified path patterns and url...
Page 160: About The Https Proxy
Proxy settings 148 firebox x edge e-series add or remove a content type 1. To add additional content types to the default list, type the mime type and click add. 2. To remove a content type, select it from the list and click remove. You cannot remove message/* or multipart/* because the smtp proxy c...
Page 161: About The H.323 Proxy
User guide 149 proxy settings about the h.323 proxy if you use voice-over-ip (voip) in your organization, you can add an h.323 or sip (session initiation protocol) proxy policy to open the ports necessary to enable voip through your firebox. These proxy policies have been created to work in a nat en...
Page 162: About The Sip Proxy
Proxy settings 150 firebox x edge e-series about the sip proxy if you use voice-over-ip (voip) in your organization, you can add a sip (session initiation protocol) or h.323 proxy policy to open the ports necessary to enable voip through your firebox. These proxy policies have been created to work i...
Page 163: About The Outgoing Proxy
User guide 151 proxy settings about the outgoing proxy the outgoing policy applies to all outgoing network traffic, including traffic managed by other common policies such as http or ftp. As a packet filter policy, you can restrict which ip addresses can send traffic from the trusted or optional int...
Page 164
Proxy settings 152 firebox x edge e-series.
Page 165: Default Threat Protection
User guide 153 9 default threat protection about intrusion prevention the firebox x edge e-series includes a set of default threat protection features designed to keep out network traffic from systems you know or think are a security risk. This set of features includes: permanently blocked site the ...
Page 166: About Blocked Sites
Default threat protection 154 firebox x edge e-series about blocked sites the blocked sites feature helps protect your network from systems you know or think are a security risk. After you find the source of suspicious traffic, you can block all connections from that ip address. You can also configu...
Page 167
User guide 155 default threat protection block a site permanently 1. To connect to the system status page, type https:// in the browser address bar, and the ip address of the firebox x edge trusted interface. The default url is https://192.168.111.1 2. From the navigation bar, click firewall > intru...
Page 168
Default threat protection 156 firebox x edge e-series block sites temporarily 1. To connect to the system status page, type https:// in the browser address bar, and the ip address of the firebox x edge trusted interface. The default url is https://192.168.111.1. 2. From the navigation bar, click fir...
Page 169: About Blocked Ports
User guide 157 default threat protection about blocked ports you can block the ports that you know can be used to attack your network. This stops specified external network services. When you block a port, you override all the rules in your firewall configuration. You can block a port because: blo...
Page 170
Default threat protection 158 firebox x edge e-series block a port 1. To connect to the system status page, type https:// in the browser address bar, and the ip address of the firebox x edge trusted interface. The default url is https://192.168.111.1 2. From the navigation bar, click firewall > intr...
Page 171
User guide 159 default threat protection about denial-of-service attacks the firebox x edge e-series includes an integrated denial-of-service (dos) protection feature to protect against some of the most common and frequent dos and distributed dos (ddos) attacks used on the internet. A dos attack is ...
Page 172
Default threat protection 160 firebox x edge e-series on the firewall > intrusion prevention page, select the dos defense tab and set the packet/second threshold for these types of dos flood attacks: ipsec flood attack a dos attack where the attacker overwhelms a computer system with a large number ...
Page 173
User guide 161 default threat protection distributed denial-of-service prevention use the distributed dos prevention feature to set limits for server and client traffic. Use the server quota setting to set a maximum number of simultaneous connections allowed incoming through the firebox from externa...
Page 174: Configure Firewall Options
Default threat protection 162 firebox x edge e-series configure firewall options you can use the firewall options page to configure rules that increase your network security. 1. To connect to the system status page, type https:// in the browser address bar, and the ip address of the firebox x edge t...
Page 175
User guide 163 default threat protection firewall options are pre-configured to meet the needs of many edge customers. Select the check box of any option you want to enable and click submit to save your changes to the edge. Firewall options include: do not respond to ping requests you can configure ...
Page 176
Default threat protection 164 firebox x edge e-series.
Page 177: Traffic Management
User guide 165 10 traffic management about traffic management the firebox x edge e-series supplies many different ways to manage the traffic on your network. You can limit the rate of traffic sent to the external or ipsec interface using qos (quality of service) through traffic control. You can mana...
Page 178: Traffic Categories
Traffic management 166 firebox x edge e-series traffic categories the firebox x edge e-series allows you to limit data sent through policies and traffic control filters. A policy can allow or deny all data of a specified type. Traffic control does not allow or deny data, but creates filters that sep...
Page 179: Traffic Marking
User guide 167 traffic management traffic marking if your firebox x edge is part of a larger network that uses quality of service (qos) and your upstream device, lan equipment, and ips support it, you can apply marking to each category of network traffic you define on your edge. The edge then marks ...
Page 180
Traffic management 168 firebox x edge e-series the following table shows the dscp values you can select, the corresponding ip precedence value (which is the same as the cs value), and the description in phb keywords. * scavenger class is intended for the lowest priority traffic such as media sharing...
Page 181
User guide 169 traffic management about traffic control options the firebox x edge e-series has many different traffic control options, including: traffic control is off the edge sends network traffic in the sequence it was received. Traffic control is on, but prioritization is off this option limit...
Page 182
Traffic management 170 firebox x edge e-series enable traffic control you must have at least one packet filter policy, proxy policy, or vpn tunnel enabled to add traffic filters. You can use any enabled policy or active vpn tunnel as a traffic control filter. Incoming and outgoing policies are ident...
Page 183
User guide 171 traffic management 3. Select the enable traffic control check box. The interactive traffic list is enabled. 4. In the upstream bandwidth limit text box, type the upstream bandwidth limit of your external network connection (wan1). Enter a value from 19 kbps to 100,000 kbps. The defaul...
Page 184
Traffic management 172 firebox x edge e-series about network address translation (nat) network address translation (nat) is a term used to describe any of several forms of ip address and port translation. At its most basic level, nat changes the ip address of a packet from one value to a different v...
Page 185
User guide 173 traffic management secondary ip addresses you can assign eight public ip addresses to the primary external interface (wan1). These addresses are used for 1-to-1 nat. When you configure secondary ip addresses on the external network: the primary ip address must be a static ip address...
Page 186
Traffic management 174 firebox x edge e-series about 1-to-1 nat when you enable 1-to-1 nat, the firebox changes and routes all incoming and outgoing packets sent from one range of addresses to a different range of addresses. A 1-to-1 nat rule always has precedence over dynamic nat. 1-to-1 nat is fre...
Page 187
User guide 175 traffic management enable 1-to-1-nat three steps are necessary to enable 1-to-1 nat: 1. Add an ip address pair. For more information, see add a secondary external ip address . A secondary external ip address is a public ip address on the external interface that also has an ip address ...
Page 188
Traffic management 176 firebox x edge e-series add or edit a policy for 1-to-1 nat 1. To connect to the system status page, type https:// in the browser address bar, and the ip address of the firebox x edge trusted interface. The default url is: https://192.168.111.1 2. From the navigation bar, sele...
Page 189: Logging
User guide 177 11 logging about logging and log files an important feature of a good network security policy is to gather messages from your security systems, to examine those records frequently, and to keep them in an archive. You can use logs to monitor your network security and activity, identify...
Page 190: See The Event Log File
Logging 178 firebox x edge e-series logging and notification in applications and servers the log server can receive log messages from your firebox or a watchguard server. After you have configured your firebox and log server, the firebox sends log messages to the log server. You can enable logging i...
Page 191
User guide 179 logging about logging to a watchguard log server the watchguard log server (previously known as the watchguard system event processor, or wsep) is a component of watchguard system manager. If you have a firebox iii, firebox x core, or firebox x peak, configure a primary log server to ...
Page 192
Logging 180 firebox x edge e-series 4. Select the send logs in native xml format check box to have the edge log messages sent to the watchguard log server in the xml format standard for fireware v8.0 or higher. The wsm/log server installation must be wsm v8.3 or greater. If you select this option, t...
Page 193: About Syslog
User guide 181 logging about syslog syslog is a log interface developed for unix but also used by a number of computer systems. You can configure the firebox to send log information to a syslog server. A firebox can send log messages to a log server and a syslog server at the same time, or send log ...
Page 194
Logging 182 firebox x edge e-series.
Page 195: Certificates
User guide 183 12 certificates about certificates when you use local authentication to connect to your firebox over secure http, the firebox uses a certificate to secure your session. You can also use certificates for vpn authentication. Certificates are files that use a digital signature to match t...
Page 196
Certificates 184 firebox x edge e-series use openssl to generate a csr openssl is installed with most gnu/linux distributions. To download the source code or a windows binary file, go to http://www.Openssl.Org/ and follow the installation instructions for your operating system. You can use openssl t...
Page 197
User guide 185 certificates issue the certificate 1. Connect to the server where the certification authority is installed, if necessary. 2. From the start menu, select control panel > administrative tools > certification authority. 3. From the certification authority (local) tree in the left navigat...
Page 198
Certificates 186 firebox x edge e-series remove a certificate 1. From the system status page on the firebox x edge, select administration > certificates. 2. Select the certificate you want to delete, and then click the adjacent remove button. Examine a certificate you can examine a certificate you h...
Page 199: User and Group Management
User guide 187 13 user and group management about user licenses your firebox x edge firewall is enabled with a set number of user licenses (also called nodes). The total number of available sessions is determined by the edge model you have, and any upgrade licenses you apply. The number of licenses ...
Page 200: About User Authentication
User and group management 188 firebox x edge e-series user licensing when authentication is not required a user license is not used when: traffic is passed between the trusted and optional networks. traffic is passed from a computer on the trusted or optional network to a computer on the other e...
Page 201
User guide 189 user and group management set authentication options for all users some authentication options have an effect on all users. To set or change authentication options: 1. To connect to the system status page, type https:// in the browser address bar, and the ip address of the firebox x e...
Page 202: About User Accounts
User and group management 190 firebox x edge e-series about user accounts when you create a local user for the firebox x edge e-series, you select the administrative access level for that user. You select access control for the external network and the branch office vpn tunnel, and time limits on th...
Page 203
User guide 191 user and group management 4. In the account name field, type a name for the account. The user types this name to authenticate. The account name is case-sensitive. 5. In the full name field, type the first and last name of the user. This is for your information only. A user does not us...
Page 204
User and group management 192 firebox x edge e-series authenticate a session without administrative access if you require authentication to the edge for the user to access resources such as the external network, they must connect to the trusted interface ip address of the edge using https, and type ...
Page 205
User guide 193 user and group management use the built-in administrator account the firebox x edge e-series has a built-in administrator account that cannot be deleted. You can change some of the administrator account settings. On the firebox users page, click the icon in the edit column of the admi...
Page 206
User and group management 194 firebox x edge e-series change a user account name or password you can change an account name or account password. If you change the account name, you must give the account password. 1. To connect to the system status page, type https:// in the browser address bar, and ...
Page 207
User guide 195 user and group management about ldap/active directory authentication if you use ldap authentication, you do not have to keep a separate user database on the firebox x edge. You can configure the edge to forward user authentication requests to a generic ldap or active directory server....
Page 208
User and group management 196 firebox x edge e-series configure the ldap/active directory authentication service when you enable ldap authentication, you define one authentication server and its properties. To enable ldap authentication: 1. To connect to the system status page, type https:// in the ...
Page 209
User guide 197 user and group management 8. In the ldap server port text box, type the port number the firebox x edge will use for connections to the ldap server. The default ldap server port number is 389. Usually you do not have to change this number. 9. Use the ldap timeout drop-down list to sele...
Page 210
User and group management 198 firebox x edge e-series add a group for ldap authentication 1. To connect to the system status page, type https:// in the browser address bar, and the ip address of the firebox x edge trusted interface. The default url is: https://192.168.111.1 2. From the navigation ba...
Page 211
User guide 199 user and group management 9. Select the allow access to manual and managed vpn tunnels check box to allow the members of this group to access vpn tunnels using the firebox x edge. 10. Select the allow remote access with mobile vpn with pptp check box to allow the members of this group...
Page 212
User and group management 200 firebox x edge e-series about single sign-on (sso) when users log on to a computer using active directory authentication, they must enter a user id and password. If you use your firebox to restrict outgoing network traffic to specified users or groups, users must log on...
Page 213
User guide 201 user and group management enable single sign-on 1. To connect to the system status page, type https:// in the browser address bar, and the ip address of the firebox x edge trusted interface. The default url is: https://192.168.111.1 2. From the navigation bar, select firebox users > s...
Page 214
User and group management 202 firebox x edge e-series install the sso agent service double-click wg-authentication-gateway.Exe to start the authentication gateway setup wizard. You may need to type a local administrator password to run the installer on some operating systems. Follow the instructions...
Page 215: Enable Radius Authentication
User guide 203 user and group management enable radius authentication when you enable radius authentication, you define one authentication server and its properties. When you set up your radius server, you must make sure that, when it sends a message to the firebox that a user is authenticated, it a...
Page 216
User and group management 204 firebox x edge e-series see active sessions and users on the firebox users page, you see information about the users who are online. 1. To connect to the system status page, type https:// in the browser address bar, with the ip address of the firebox x edge trusted inte...
Page 217
User guide 205 user and group management stop a session the firebox x edge e-series monitors and records the properties of each user session. If the automatic session termination time limit for all sessions is reached, or if the firebox x edge restarts, all sessions are stopped at the same time. The...
Page 218
User and group management 206 firebox x edge e-series editing a user account to edit a user account, click the edit icon. For descriptions of the fields you can configure, see about user accounts . Deleting a user account to remove a user account, click the x adjacent to the account name. A dialog b...
Page 219: Webblocker
User guide 207 14 webblocker about webblocker if you give users unlimited web site access, your company can suffer lost productivity and reduced bandwidth. Uncontrolled internet surfing can also increase security risks and legal liability. The webblocker security subscription gives you control of th...
Page 220
Webblocker 208 firebox x edge e-series to configure webblocker: 1. To connect to the system status page, type https:// in the browser address bar, and the ip address of the firebox x edge trusted interface. The default url is: https://192.168.111.1 2. From the navigation bar, select webblocker > set...
Page 221
User guide 209 webblocker 6. Use the when the webblocker server is unavailable, access to all sites is drop-down list to select if the firebox x edge is to allow or deny all traffic when it cannot connect to the webblocker server. If you allow web traffic when the webblocker server is unavailable, e...
Page 222: About Webblocker Profiles
Webblocker 210 firebox x edge e-series install quarantine server and webblocker server double-click wgedge10qwb.Exe to start the setup wizard. You may need to type a local administrator password to run the installer on some operating systems. Follow the instructions to install the software: watchgua...
Page 223
User guide 211 webblocker 3. Click new. The new profile page appears..
Page 224: About Webblocker Categories
Webblocker 212 firebox x edge e-series 4. In the profile name field, type a familiar name. Use this name to identify the profile during configuration. For example, give the name 90day to a group of employees that have worked at your company for less than 90 days. 5. In blocked categories, select the...
Page 225
User guide 213 webblocker see whether a site is categorized to see whether webblocker denies access to a web site as part of a category block, go to the filter testing and submissions form on the surfcontrol web site. 1. Open a web browser and go to: http://mtas.Surfcontrol.Com/mtas/watchguardtest-a...
Page 226
Webblocker 214 firebox x edge e-series add, remove, or change a category if you receive a message that the url you entered is not in the surfcontrol list, you can submit it on the test results page. 1. Click submit a site. The submit a site page appears. 2. Select whether you want to add a site, del...
Page 227
User guide 215 webblocker about allowing sites to bypass webblocker webblocker might deny a web site that is necessary for your business. You can override webblocker by defining a web site normally denied by webblocker as an exception to allow users to access it. For example, suppose employees in yo...
Page 228
Webblocker 216 firebox x edge e-series add a denied site 1. From the navigation bar, select webblocker > denied sites. The webblocker denied sites page appears. 2. From the drop-down list, select host ip address or domain name/url 3. Type the host ip address or domain name of the denied web site. 4....
Page 229
User guide 217 webblocker allow internal hosts to bypass webblocker you can make a list of internal hosts that bypass webblocker. The internal hosts that you put on this list also bypass any user authentication settings. If a user is on this list, that user does not have to authenticate to get acces...
Page 230
Webblocker 218 firebox x edge e-series.
Page 231: Spamblocker
User guide 219 15 spamblocker about spamblocker unwanted email, also known as spam, fills the average inbox at an astonishing rate. A large volume of spam decreases bandwidth, degrades employee productivity, and wastes network resources. The watchguard spamblocker option uses industry-leading patter...
Page 232
Spamblocker 220 firebox x edge e-series about virus outbreak detection (vod) virus outbreak detection (vod) is a technology that identifies email virus outbreaks worldwide within minutes. Provided by commtouch, an industry leader in email spam and virus protection, vod isincorporated into the spambl...
Page 233
User guide 221 spamblocker spamblocker categories the commtouch recurrent-pattern detection (rpd) solution classifies spam attacks in its anti-spam detection center database according to severity. Spamblocker queries this database and assigns a category to each email message. Spamblocker has three c...
Page 234: Enable Spamblocker
Spamblocker 222 firebox x edge e-series enable spamblocker 1. To connect to the system status page, type https:// in the browser address bar, and the ip address of the firebox x edge trusted interface. The default url is: https://192.168.111.1 2. From the navigation bar, select spamblocker > setting...
Page 235
User guide 223 spamblocker 5. At the bottom of the page, you can set the number of bytes of an email message that spamblocker checks with the limit scanning to first text box. If you type a very large number in this text box, your network throughput may be slow. We recommend that you keep the scan l...
Page 236
Spamblocker 224 firebox x edge e-series set pop3 email actions 1. From the confirmed drop-down list, select allow or add a subject tag. The default action is allow. If you choose add a subject tag, a text box appears with the default tag * **spam*** . You can change this tag to some text you prefer....
Page 237
User guide 225 spamblocker about spamblocker exceptions you can create an exception list to the general spamblocker actions that is based on the sender’s address. For example, if you want to allow a newsletter that spamblocker identifies as bulk email, you can add that sender to the exception list a...
Page 238
Spamblocker 226 firebox x edge e-series about using spamblocker with multiple proxies you can configure more than one smtp or pop3 proxy service to use spamblocker. This lets you create custom rules for different groups in an organization. For example, you can allow all email to your management and ...
Page 239
User guide 227 spamblocker create rules for your email reader to use the tag action in spamblocker, it is best to configure your email reader to sort messages. Most email readers, such as outlook, thunderbird, and mac mail, allow you to set rules that automatically send email messages with tags to a...
Page 240: Accuracy
Spamblocker 228 firebox x edge e-series report false positives and false negatives a false positive email message is a legitimate message that spamblocker incorrectly identifies as spam. A false negative email message is a spam message that spamblocker does not correctly identify as spam. If you fin...
Page 241: Quarantine Server
User guide 229 16 quarantine server about the quarantine server the watchguard quarantine server provides a safe, full-featured quarantine mechanism for any email messages suspected or known to be spam or to contain viruses. This repository receives email messages from the smtp proxy and are filtere...
Page 242
Quarantine server 230 firebox x edge e-series install the quarantine server and webblocker server to use the quarantine feature of spamblocker or gateway antivirus, or if you want to install and maintain your own webblocker server, you must download and install the watchguard quarantine server and w...
Page 243: Start The Quarantine Server
User guide 231 quarantine server start the quarantine server to start the quarantine server, you must: install quarantine server run the setup wizard define the server location install server components you can install quarantine server as part of watchguard system manager, or as part of a special i...
Page 244
Quarantine server 232 firebox x edge e-series configure the quarantine server when you configure the quarantine server, you have these options: set general server parameters change the expiration and user domain settings : when to delete or how long to keep messages, and add and delete user domains....
Page 245
User guide 233 quarantine server 3. To change the default maximum database size of 10000 mb, type a new value in the maximum database size field. The current database size and available space appear to the right of this field. When the quarantine server runs out of drive space, it refuses to accept ...
Page 246
Quarantine server 234 firebox x edge e-series change expiration settings and user domains 1. To open the quarantine server configuration dialog box: right-click and select configure. Type the server management passphrase. This is the server management passphrase you created in the second screen of t...
Page 247
User guide 235 quarantine server add or remove user domains the expiration settings tab of the quarantine server configuration dialog box shows the domain names for which the quarantine server will accept email messages. Only users in the domains that are in the list can have messages sent to the qu...
Page 248
Quarantine server 236 firebox x edge e-series 3. From the quarantine server configuration dialog box, click the user notification settings tab. 4. To enable or disable notification (and the fields on this dialog box), use the send notification to users check box. 5. In the send email from field, typ...
Page 249
User guide 237 quarantine server change logging settings you can enable or disable logging for the server, and define where the server will send log messages. To open the configuration dialog box: 1. Right-click the icon for the server and select configure. 2. Type the management server passphrase w...
Page 250
Quarantine server 238 firebox x edge e-series change quarantine server rules you set up rules to automatically remove certain messages if they come from a specific domain or sender, or if they contain specific text strings in the subject line. 1. To open the quarantine server configuration dialog bo...
Page 251
User guide 239 quarantine server 5. Click the underlined words in the rule to add a specific domain, sender, or text string in the subject line. The edit auto-remove rule dialog box appears. 6. To add a new domain, sender, or string, type it in the top box and click add. 7. To remove a domain, sende...
Page 252: Manage Messages
Quarantine server 240 firebox x edge e-series manage messages you can see all messages on the quarantine server in a dialog box. You can sort messages by user, quarantine status, sender, subject, and date/time received. Open the messages dialog box 1. Right-click and select manage messages. 2. Type ...
Page 253
User guide 241 quarantine server set viewing options you can use the filter by drop-down list to see all messages or only those with a particular quarantine status. To see the body of a message, select the view message body check box. Select any message. A second pane appears at the bottom of the di...
Page 254
Quarantine server 242 firebox x edge e-series open the messages dialog box 1. Right-click the quarantine server icon and select manage messages. 2. Type the server management passphrase. The quarantine server message and user management dialog box appears. You can only have one quarantine server dia...
Page 255: About Managing Users
User guide 243 quarantine server about managing users you add, delete, and configure users from the users tab of the quarantine server message and user management dialog box. This dialog box shows: email addresses of users that can have email messages sent to the quarantine server. whether users...
Page 256
Quarantine server 244 firebox x edge e-series add users users are automatically added when messages are sent to the quarantine server for them. Use this procedure to manually add users: 1. From the quarantine server message and user management dialog box, click the users tab. Select edit > add user....
Page 257
User guide 245 quarantine server get statistics on quarantine server activity quarantine server statistics include those messages that have been deleted, either manually or automatically. 1. Right-click and select view statistics. 2. Type the server management passphrase. The quarantine server stati...
Page 258
Quarantine server 246 firebox x edge e-series.
Page 259: Gateway Antivirus and
User guide 247 17 gateway antivirus and intrusion prevention service about gateway antivirus and intrusion prevention hackers use many methods to attack computers on the internet. The two primary categories of attack are viruses and intrusions. Viruses, including worms and trojans, are malicious com...
Page 260
Gateway antivirus and intrusion prevention service 248 firebox x edge e-series about gateway antivirus settings watchguard gateway antivirus (gateway av) stops viruses before they get to computers on your network. Gateway av operates with the watchguard smtp, pop3, http, and ftp proxies. When you en...
Page 261
User guide 249 gateway antivirus and intrusion prevention service configure gateway av 1. To connect to the system status page, type https:// in the browser address bar, followed by the ip address of the firebox x edge trusted interface. The default url is: https://192.168.111.1 2. From the navigati...
Page 262
Gateway antivirus and intrusion prevention service 250 firebox x edge e-series 11. When you enable gateway av/ips for smtp, you must specify the ip address of your smtp email server in the email server ip address field near the bottom of the page. The edge creates a policy for you to allow incoming ...
Page 263
User guide 251 gateway antivirus and intrusion prevention service 4. When you enable gateway av/ips for smtp, you must specify the ip address of your smtp email server in the email server ip address field near the bottom of the page. The edge creates a policy for you to allow incoming smtp traffic t...
Page 264: Update Gateway Av/ips
Gateway antivirus and intrusion prevention service 252 firebox x edge e-series update gateway av/ips new viruses and intrusion methods appear on the internet frequently. The gateway av/ips service uses a database of signatures to check for viruses and intrusions. Watchguard frequently publishes upda...
Page 265: Networks
User guide 253 18 branch office virtual private networks about branch office virtual private networks (bovpns) a vpn (virtual private network) creates a secure connection between computers or networks in different locations. This connection is known as a tunnel. When a vpn tunnel is created, the two...
Page 266
Branch office virtual private networks 254 firebox x edge e-series what you need to create a vpn before you configure your watchguard firebox x edge vpn network, read these requirements: you must have two firebox x edge devices or one firebox x edge and a second device that uses ipsec standards. E...
Page 267: About Managed Vpns
User guide 255 branch office virtual private networks about managed vpns you can configure a vpn tunnel on the firebox x edge e-series with two procedures: managed vpn and manual vpn. For information on creating a manual vpn tunnel, see create manual vpn tunnels on your edge . The watchguard managem...
Page 268
Branch office virtual private networks 256 firebox x edge e-series sample vpn address information table item description assigned by external ip address the ip address that identifies the ipsec-compatible device on the internet. Isp example: site a: 207.168.55.2 site b: 68.130.44.15 isp local networ...
Page 269
User guide 257 branch office virtual private networks create manual vpn tunnels on your edge 1. To connect to the system status page, type https:// in the browser address bar, and the ip address of the firebox x edge trusted interface. The default url is: https://192.168.111.1 2. From the navigation...
Page 270
Branch office virtual private networks 258 firebox x edge e-series phase 1 settings internet key exchange (ike) is a protocol used with vpn tunnels to manage keys automatically. Ike negotiates and changes keys. Phase 1 authenticates the two sides and creates a key management security association to ...
Page 271
User guide 259 branch office virtual private networks to change phase 1 configuration: 1. Select the negotiation mode from the mode drop-down list. You can use main mode only when the two devices have static ip addresses. If one or both of the devices have external ip addresses that are dynamically ...
Page 272
Branch office virtual private networks 260 firebox x edge e-series if your edge is behind a device that does nat the firebox x edge e-series can use nat traversal. This means that you can make vpn tunnels if your isp does nat (network address translation) or if the external interface of your edge is...
Page 273
User guide 261 branch office virtual private networks phase 2 settings phase 2 negotiates the data management security association for the tunnel. The tunnel uses this phase to create ipsec tunnels and put data packets together. You can use the default phase 2 settings to make configuration easier. ...
Page 274
Branch office virtual private networks 262 firebox x edge e-series 5. Type the number of kilobytes and the number of hours until the phase 2 key expires. To make the key not expire, enter zero (0). For example, 24 hours and zero (0) kilobytes means that the phase 2 key is renegotiated each 24 hours ...
Page 275: Configure Vpn Keep Alive
User guide 263 branch office virtual private networks configure vpn keep alive to keep the vpn tunnel open when there are no connections through it, you can use the ip address of a computer at the other end of the tunnel as an echo host. The firebox x edge e-series sends a ping each minute to the sp...
Page 276: Frequently Asked Questions
Branch office virtual private networks 264 firebox x edge e-series frequently asked questions why do i need a static external address? To make a vpn connection, each device must know the ip address of the other device. If the address for a device is dynamic, the ip address can change. If the ip addr...
Page 277: About Mobile Vpn With Pptp
User guide 265 19 about mobile vpn with pptp you can use point-to-point tunneling protocol (pptp) to make secure vpn tunnels. You can configure the firebox x edge e-series as a pptp vpn endpoint and allow up to 10 users to make simultaneous secure connections to the edge and access the networks prot...
Page 278
About mobile vpn with pptp 266 firebox x edge e-series enable pptp access for firewall users when you enable mobile vpn with pptp on your edge, you must enable pptp access for each remote user who uses pptp to connect to the edge. 1. To connect to the system status page, type https:// and the ip add...
Page 279: Enable Pptp On The Edge
User guide 267 about mobile vpn with pptp enable pptp on the edge 1. To connect to the system status page, type https:// and the ip address of the firebox x edge trusted interface in the browser address bar. The default url is https://192.168.111.1 2. From the navigation bar, select vpn > mobile vpn...
Page 280: Prepare The Client Computers
About mobile vpn with pptp 268 firebox x edge e-series configure dns and wins settings the domain name service (dns) changes host names into ip addresses. The windows internet naming service (wins) changes netbios names to ip addresses. By default, pptp users that connect to the edge use the wins an...
Page 281
User guide 269 about mobile vpn with pptp create and connect a pptp vpn from a windows xp client to prepare a windows xp remote host, you must configure the network connection. From the windows desktop of the client computer: 1. Select start > control panel > network connections. The network connect...
Page 282
About mobile vpn with pptp 270 firebox x edge e-series use pptp and access the internet you can enable remote users to access the internet through a pptp tunnel. When you do this, all firewall policies are applied to the remote user. For example, if you have configured webblocker for outbound traffi...
Page 283: About Mobile Vpn With Ipsec
User guide 271 20 about mobile vpn with ipsec the watchguard mobile vpn with ipsec client is a software application that is installed on a remote computer. The client makes a secure connection from the remote computer to your protected network through an unsecured network. The mobile vpn client uses...
Page 284
About mobile vpn with ipsec 272 firebox x edge e-series enable mobile vpn for a firebox user account 1. To connect to the edge system status page, type https:// in the browser address bar, and the ip address of the firebox x edge trusted interface. The default url is: https://192.168.111.1 2. To add...
Page 285
User guide 273 about mobile vpn with ipsec 10. Select mobile user in the vpn client type drop-down list. This selection is required if you use a windows desktop, laptop, or handheld pc. 11. Select the all traffic uses tunnel (0.0.0.0/0 ip subnet) check box if the remote client sends all its traffic ...
Page 286
About mobile vpn with ipsec 274 firebox x edge e-series about mobile vpn client configuration files with mobile vpn with ipsec, the firebox x edge administrator controls end-user profiles. You use the edge web configuration interface to set the name of the end user and create a client configuration ...
Page 287
User guide 275 about mobile vpn with ipsec wins/dns settings for mobile vpn with ipsec mobile vpn clients use shared windows internet naming service (wins) and domain name system (dns) server addresses. Dns changes host names into ip addresses, while wins changes netbios names to ip addresses. The t...
Page 288
About mobile vpn with ipsec 276 firebox x edge e-series distribute the software and profiles watchguard recommends distributing end-user profiles by encrypted email or by another secure method. Each client computer must have: software installation package the packages are located on the watchguard...
Page 289
User guide 277 about mobile vpn with ipsec about the mobile vpn with ipsec client the watchguard mobile vpn with ipsec client is installed on a user’s computer, whether the user travels or works from home. The user connects with a standard internet connection and activates the mobile vpn client. The...
Page 290
About mobile vpn with ipsec 278 firebox x edge e-series to import a mobile vpn configuration .Wgx file: 1. Select configuration > profile import. The profile import wizard starts. 2. On the select user profile screen, browse to the location of the .Wgx configuration file supplied by your network adm...
Page 291
User guide 279 about mobile vpn with ipsec uninstall the mobile vpn client at some point, it can become necessary to uninstall the mobile vpn client. We recommend that you use the windows add/remove programs tool to uninstall the mobile vpn client. After the mobile vpn client software is installed t...
Page 292
About mobile vpn with ipsec 280 firebox x edge e-series disconnect the mobile vpn client from the mobile vpn monitor, click disconnect. Control connection behavior for each profile you import, you can control the action the mobile vpn client software takes when the vpn tunnel goes down for any reaso...
Page 293
User guide 281 about mobile vpn with ipsec 4. Use the connection mode drop-down list to set a connection behavior for this profile. O manual - when you select manual connection mode, the client does not try to restart the vpn tunnel automatically if the vpn tunnel goes down. To restart the vpn tunne...
Page 294
About mobile vpn with ipsec 282 firebox x edge e-series secure your computer with the mobile vpn firewall the watchguard mobile vpn with ipsec client includes two firewall components: link firewall the link firewall is not enabled by default. When the link firewall is enabled, your computer will dis...
Page 295
User guide 283 about mobile vpn with ipsec about the desktop firewall when you enable a rule in your firewall configurations, you must specify what type of network the rule applies to. In the mobile vpn client, there are three different types of networks: vpn networks networks defined for the client...
Page 296
About mobile vpn with ipsec 284 firebox x edge e-series define friendly networks you can generate a firewall rule set for specific known networks that you define. For example, if you want to use the mobile vpn client on a local network where you want your computer available to other computers, you c...
Page 297
User guide 285 about mobile vpn with ipsec to create a rule, click new. Use the four tabs in the firewall rule entry dialog box to define the traffic you want to control: general tab local tab remote tab applications tab general tab you can define the basic properties of your firewall rules on the g...
Page 298
About mobile vpn with ipsec 286 firebox x edge e-series local tab you can define any local ip addresses and ports that are controlled by your firewall rule on the local tab of the firewall rule entry dialog box. We recommend that, in any rule, you configure the local ip addresses setting to enable t...
Page 299
User guide 287 about mobile vpn with ipsec remote tab you can define any remote ip addresses and ports that are controlled by this rule on the remote tab of the firewall rule entry dialog box. For example, if your firewall is set to deny all traffic and you want to create a rule to allow outgoing po...
Page 300
About mobile vpn with ipsec 288 firebox x edge e-series applications tab you can limit your firewall rule so that it applies only when a specific application is used. 1. On the applications tab of the firewall rule entry dialog box, select the bind rule to application below check box. 2. Click selec...
Page 301: About Mobile Vpn With Ssl
User guide 289 21 about mobile vpn with ssl the watchguard mobile vpn with ssl client is installed on a user’s computer, whether the user travels or works from home. The user can then connect with a standard internet connection and activate the mobile vpn client. The mobile vpn client then creates a...
Page 302: Client Requirements
About mobile vpn with ssl 290 firebox x edge e-series client requirements the watchguard mobile vpn with ssl product supplies a vpn client for all firebox x e-series devices. It does not provide endpoint security. You can install the mobile vpn with ssl client software on computers with the followin...
Page 303
User guide 291 about mobile vpn with ssl enable mobile vpn with ssl for a group when you enable mobile vpn with ssl on your edge, you must make sure to enable access for each remote user or group who uses ssl to connect to the edge. If you use extended authentication, you must configure the group na...
Page 304
About mobile vpn with ssl 292 firebox x edge e-series 7. In the session idle timeout field, set the length of time the computers in this group can stay authenticated when idle (not passing any traffic to the external network, through the branch office vpn, or to the firebox x edge itself). A setting...
Page 305
User guide 293 about mobile vpn with ssl ssl vpn general tab gateway the gateway is the public ip address that mobile vpn clients connect to. You must type an ip address assigned to the external interface of your edge. If you have configured more than one ip address for your external interface, or y...
Page 306
About mobile vpn with ssl 294 firebox x edge e-series ssl vpn advanced tab authentication from the authentication drop-down list, select the authentication algorithm to use. Encryption from the encryption drop-down list, select the encryption algorithm to use. Protocol and port by default, ssl traff...
Page 307: Download The Client Software
User guide 295 about mobile vpn with ssl download the client software to download the mobile vpn client software, connect to the firebox with a web browser. Each user must type: https://ip address of a firebox interface:4100/ or https://host name of the firebox:4100/ the client software is also avai...
Page 308
About mobile vpn with ssl 296 firebox x edge e-series about the mobile vpn with ssl client the watchguard mobile vpn with ssl client is installed on a user’s computer, whether the user travels or works from home. The user can then connect with a standard internet connection and activate the mobile v...
Page 309
User guide 297 about mobile vpn with ssl connect to the firebox with the mobile vpn with ssl client (windows vista and windows xp) after you have installed the mobile vpn with ssl client, you can connect to your firebox. 1. Use one of these three methods to start the client software: o select start ...
Page 310
About mobile vpn with ssl 298 firebox x edge e-series mobile vpn with ssl client controls when the mobile vpn with ssl client is running, the watchguard logo icon appears in the system tray (win) or on the right side of the menu bar (mac). The vpn connection status is displayed in the icon’s magnify...