- DL manuals
- Raritan
- Switch
- Dominion KX II
- User Manual
Raritan Dominion KX II User Manual
Summary of Dominion KX II
Page 1
Copyright © 2014 raritan, inc. Dkx2-v2.6.0-0r-e march 2014 255-62-4023-00 dominion kx ii user guide release 2.6.0
Page 2
This document contains proprietary information that is protected by copyright. All rights reserved. No part of this document may be photocopied, reproduced, or translated into another language without express prior written consent of raritan, inc. © copyright 2014 raritan, inc. All third-party softw...
Page 3: Contents
Iii contents chapter 1 introduction 1 kx ii overview ............................................................................................................................... 2 package contents .......................................................................................................
Page 4
Contents iv port access page (remote console display) ................................................................... 38 port action menu ............................................................................................................... 41 managing favorites ...........................
Page 5
Contents v virtual media in a mac environment .......................................................................................... 103 active system partition .................................................................................................... 103 drive partitions ................
Page 6
Contents vi lan interface settings ..................................................................................................... 144 device services ......................................................................................................................... 145 enabling ssh .......
Page 7
Contents vii upgrading cims ......................................................................................................................... 245 upgrading firmware .................................................................................................................. 245 upgrade ...
Page 8
Contents viii local console smart card access ............................................................................................ 270 smart card access in kx2 8xx devices ......................................................................... 271 local console usb profile options ...........
Page 9
Contents ix appendix b dual video port groups 317 overview .................................................................................................................................... 317 recommendations for dual port video .......................................................................
Page 10
Contents x virtual media notes .................................................................................................................... 341 cannot connect to drives from linux clients ................................................................. 341 cannot write to/from a file from a...
Page 11
Contents xi appendix f frequently asked questions 355 general faqs ............................................................................................................................ 355 remote access .............................................................................................
Page 12: Chapter 1 Introduction
1 in this chapter kx ii overview ........................................................................................... 2 package contents ..................................................................................... 4 kx ii device photos and features ......................................
Page 13
Chapter 1: introduction 2 kx ii overview raritan's dominion kx ii is an enterprise-class, secure, digital kvm (keyboard, video, mouse) switch that provides bios-level (and up) access and control of servers from anywhere in the world via a web browser. Up to 64 servers can be controlled with a standa...
Page 14
Chapter 1: introduction 3.
Page 15
Chapter 1: introduction 4 diagram key local port access tiering ip-based network access extended local port modem mobile access via iphone ® and ipad ® using cc-sg virtual media digital audio smart card access at the rack cims remote smart card access cat5/6 cable package contents each kx ii ships a...
Page 16
Chapter 1: introduction 5 kx ii device photos and features kx ii kx2-808.
Page 17
Chapter 1: introduction 6 kx2-832 kx2-864 see kx ii dimensions and physical specifications (on page 287) for product specifications. See supported computer interface module (cims) specifications (on page 289) for cim specifications and images..
Page 18
Chapter 1: introduction 7 product features hardware integrated kvm-over-ip remote access 1u or 2u rack-mountable (brackets included) dual power supplies with failover; autoswitching power supply with power failure warning support for tiering in which a base kx ii device is used to access multiple ot...
Page 19
Chapter 1: introduction 8 model remote users ports kx ii-416 4 16 kx ii-232 2 32 kx ii-216 2 16 kx ii-132 1 32 kx ii-116 1 16 kx ii-108 1 8 software virtual media support in windows ® , mac ® and linux ® environments with d2cim-vusb and d2cim-dvusb cims and digital cims support for digital audio ove...
Page 20
Chapter 1: introduction 9 kx ii client applications the following client applications can be used in the kx ii: kx ii 2.2 (and later): virtual kvm client (vkc) active kvm client (akc) multi-platform client (mpc) kx ii (generation 2): virtual kvm client (vkc) multi-platform client (mpc) java ™ 1.7 is...
Page 21
10 in this chapter overview .................................................................................................. 10 rack mounting ......................................................................................... 10 default login information ........................................
Page 22
Chapter 2: installation and configuration 11 5. When connecting cables to the rear panel of the kx ii drape them over the cable-support bar. Rear mount the steps correspond to the numbers shown in the rear rackmount diagrams. 1. Secure the cable-support bar to the front end of the side brackets, nea...
Page 23
Chapter 2: installation and configuration 12 default login information default value user name admin this user has administrative privileges. Password raritan the first time you start the kx ii, you are required to change the default password. Ip address 192.168.0.192. Important: for backup and busi...
Page 24
Chapter 2: installation and configuration 13 step 2: configure the kvm target servers target server video resolutions for optimal bandwidth efficiency and video performance, kvm target servers running graphical user interfaces such as windows ® , linux ® , x-windows, solaris ™ , and kde may require ...
Page 25
Chapter 2: installation and configuration 14 windows xp, windows 2003, windows 2008 mouse settings configure these mouse settings in windows xp ® , windows 2003 ® and windows 2008 ® : configure the motion settings: set the mouse motion speed setting to exactly the middle speed disable the "enhance p...
Page 26
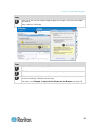
Chapter 2: installation and configuration 15 3. In kx ii, select device settings > port configuration, then click on the target name to open the port page. 4. Expand 'select usb profiles for port' section. 5. Select 'mac os-x (10.4.9) and later' from the available box, then click add to add it to th...
Page 27
Chapter 2: installation and configuration 16 step 3: connect the equipment a. Ac power connect the power supply(s): 1. Attach the included ac power cord to the kx ii, and plug it into an ac power outlet. 2. For dual-power failover protection, attach the second included ac power cord to the kx ii, an...
Page 28
Chapter 2: installation and configuration 17 enable 'automatic failover' on the kx ii network configuration page. D. Local access port (local pc) for access to target servers at the rack, use the kx ii local access port. The local access port also provides a graphical user interface from the kx ii l...
Page 29
Chapter 2: installation and configuration 18 2. Ensure that your target server's video is configured to a supported resolution and refresh rate. For sun servers, ensure your target server's video card is set to output standard vga (h-and-v sync) and not composite sync. 3. Attach the keyboard/mouse c...
Page 30
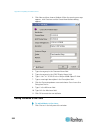
Chapter 2: installation and configuration 19 assign the kx ii an ip address to assign an ip address to the kx ii: 1. Choose device settings > network. The network settings page opens. 2. Specify a meaningful device name for your kx ii device. Up to 32 alphanumeric and valid special characters, no sp...
Page 31
Chapter 2: installation and configuration 20 configure the ipv6 settings 1. If using ipv6, enter or select the appropriate ipv6-specific network settings in the ipv6 section: a. Select the ipv6 checkbox to activate the fields in the section and enable ipv6 on the device. B. Enter a global/unique ip ...
Page 32
Chapter 2: installation and configuration 21 2. If use the following dns server addresses is selected, whether or not dhcp is selected, the addresses entered in this section is used to connect to the dns server. Enter the following information if the following dns server addresses is selected. These...
Page 33
Chapter 2: installation and configuration 22 if either of these checkboxes is selected and only power input is connected, the power led on the front of the device is red. Configure date/time settings (optional) optionally, configure the date and time settings. The date and time settings impact ssl c...
Page 34
Chapter 2: installation and configuration 23 step 5: launching the kx ii remote console log in to your kx ii remote console from any workstation with network connectivity that has microsoft .Net ® and/or java runtime environment ™ installed. To launch the kx ii remote console: 1. Launch a supported ...
Page 35
Chapter 2: installation and configuration 24 3. Choose switch from in the port action menu. The new target server you selected is displayed. Disconnecting a target server to disconnect a target server: on the port access page, click the port name of the target you want to disconnect from, then click...
Page 36
Chapter 2: installation and configuration 25 step 7: configure tiering (optional) the optional tiering feature allows you to use a kx ii as your base device, then connect additional kx ii's to it as tiered devices. You can then access servers and px pdus through the base both locally and remotely. S...
Page 37
Chapter 2: installation and configuration 26 http://ip-address/akc for the microsoft .Net-based active kvm client ip-address is the ip address assigned to your kx ii you can also use https, or the dns name of the kx ii assigned by your administrator (if applicable). You are always redirected to th...
Page 38
Chapter 2: installation and configuration 27 additional security warnings even after an ssl certificate is installed in the kx ii, depending on your browser and security settings, additional security warnings may be displayed when you log in to kx ii. It is necessary to accept these warnings to laun...
Page 39
Chapter 2: installation and configuration 28 example 1: import the certificate into the browser in this example, you import the certificate into the browser. Steps open an ie browser, then log in to kx ii. Click more information on the first java ™ security warning. Click view certificate details on...
Page 40
Chapter 2: installation and configuration 29 steps click the content tab. Click certificates. The certificate import wizard opens and walks you through each step. file to import - browse to locate the certificate certificate store - select the location to store the certificate click finish on th...
Page 41
Chapter 2: installation and configuration 30 example 2: add the kx ii to trusted sites and import the certificate in this example, the kx ii's url is added as a trusted site, and the self signed certificate is added as part of the process. Steps open an ie browser, then select tools > internet optio...
Page 42
Chapter 2: installation and configuration 31 steps click ok on the internet options dialog to apply the changes, then close and reopen the browser. Next, import the certificate. Steps open an ie browser, then log in to kx ii. Click more information on the first java ™ security warning. Click view ce...
Page 43
32 in this chapter kx ii interfaces ........................................................................................ 32 kx ii local console interface: kx ii devices .......................................... 33 kx ii remote console interface .....................................................
Page 44
Chapter 3: working with target servers 33 kx ii local console interface: kx ii devices when you are located at the server rack, the kx ii provides standard kvm management and administration via the kx ii local console. The kx ii local console provides a direct kvm (analog) connection to your connect...
Page 45
Chapter 3: working with target servers 34 kx ii interface both the kx ii remote console and the kx ii local console interfaces provide a web-based interface for device configuration and administration, as well as target server list and selection. The options are organized into various tabs. After a ...
Page 46
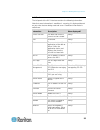
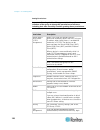
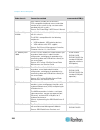
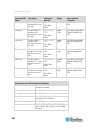
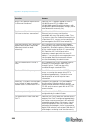
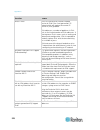
Chapter 3: working with target servers 35 left panel the left panel of the kx ii interface contains the following information. Note that some information is conditional - meaning it is displayed based on your role, features being used and so on. Conditional information is noted here. Information des...
Page 47
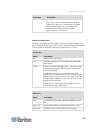
Chapter 3: working with target servers 36 information description when displayed? Powerin2 status of the power 2 outlet connection. Either on or off, or auto-detect off always configured as base or configured as tiered if you are using a tiering configuration, this indicates if the kx ii you are acc...
Page 48
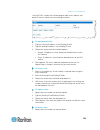
Chapter 3: working with target servers 37 kx ii console navigation the kx ii console interfaces provide many methods for navigation and making your selections. To select an option (use any of the following): click on a tab. A page of available options appears. Hover over a tab and select the appropr...
Page 49
Chapter 3: working with target servers 38 port access page (remote console display) after successfully logging on to the kx ii remote console, the view by port tab on the port access page appears. This page lists all of the kx ii ports, and the target servers, port groups, and blade chassis that are...
Page 50
Chapter 3: working with target servers 39 status - the status of the servers - either up or down. To connect to an available target server or dual monitor target server: 1. Click on the port name. The port action menu opens. 2. Click connect. Once you are connected to a target or dual monitor target...
Page 51
Chapter 3: working with target servers 40 view by group tab the view by group tab displays blade chassis, 'standard' port groups, and dual video port groups. Click the expand arrow icon next to a group to view the ports assigned to the port group. See device management (on page 141) for information ...
Page 52
Chapter 3: working with target servers 41 blade chassis - port access page the blade chassis is displayed in an expandable, hierarchical list on the port access page, with the blade chassis at the root of the hierarchy and the individual blades labeled and displayed below the root. Use the expand ar...
Page 53
Chapter 3: working with target servers 42 on the local port, the kx ii local console interface must be visible in order to perform the switch. Hot key switching is also available from the local port. Note: this option is not available from the kx ii remote console for an available port if all connec...
Page 54
Chapter 3: working with target servers 43 managing favorites a favorites feature is provided so you can organize and quickly access the devices you use frequently. The favorite devices section is located in the lower left side (sidebar) of the port access page and provides the ability to: create and...
Page 55
Chapter 3: working with target servers 44 enable favorites click enable in the favorite devices section of the left panel of the kx ii interface. Once enabled, the enable button becomes a disable button..
Page 56
Chapter 3: working with target servers 45 access and display favorites to access a favorite kx ii device: click the device name (listed beneath favorite devices). A new browser opens to that device. To display favorites by name: click display by name. To display favorites by ip address: click displa...
Page 57
Chapter 3: working with target servers 46 to use the default discovery port, select the use default port 5000 checkbox. to use a different discovery port: a. Deselect the use default port 5000 checkbox. B. Type the port number in the discover on port field. C. Click save. 3. Click refresh. The l...
Page 58
Chapter 3: working with target servers 47 scanning ports the kx ii provides the port scanning feature to search for selected targets, and display them in a slide show view, allowing you to monitor up to 32 targets at one time. You can connect to targets or focus on a specific target as needed. Scans...
Page 59
Chapter 3: working with target servers 48 note: mpc uses a different method for initiating a scan than the other raritan clients. See set scan group in the kvm and serial client guide for details. The scan results and scan options differ between the remote console and the local console. See scanning...
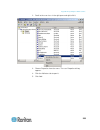
Page 60
Chapter 3: working with target servers 49 using scan port options following are options available to you while scanning targets. With the exception of the expand/collapse icon, all of these options are selected from the options menu in the upper left of the port scan viewer. The options will return ...
Page 61
Chapter 3: working with target servers 50 logging out to quit the kx ii: click logout in the upper right-hand corner of the page. Note: logging out also closes any open virtual kvm client and serial client sessions. Proxy server configuration for use with mpc, vkc and akc when the use of a proxy ser...
Page 62
Chapter 3: working with target servers 51 e. On the general tab, click network settings. The network settings dialog opens. F. Select use proxy server. G. Click advanced. The advanced network settings dialog opens. H. Configure the proxy servers for all protocols. Important: do not select 'use the s...
Page 63
Chapter 3: working with target servers 52 virtual kvm client (vkc) and active kvm client (akc) overview whenever you access a target server from the port access page of kx ii the remote console, a virtual kvm client (vkc) window opens. There is one virtual kvm client for each target server connected...
Page 64
Chapter 3: working with target servers 53 virtual kvm client (vkc) and active kvm client (akc) shared features the virtual kvm client (vkc) and active kvm client (akc) are interfaces used to access remote targets. Vkc and akc share similar features with the exception of the following: minimum system...
Page 65
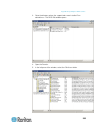
Chapter 3: working with target servers 54 connection properties dynamic video compression algorithms maintain kvm console usability under varying bandwidth constraints. The devices optimize kvm output not only for lan use, but also for wan use. These devices can also control color depth and limit vi...
Page 66
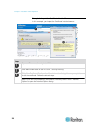
Chapter 3: working with target servers 55 3. Choose the color depth from the drop-down list. The device can dynamically adapt the color depth transmitted to remote users in order to maximize usability in all bandwidths. 15-bit rgb color 8-bit rgb color 4-bit color 4-bit gray 3-bit gray 2...
Page 67
Chapter 3: working with target servers 56 connection information open the connection information dialog for real-time connection information, and copy the information from the dialog as needed. This is useful if, for example, you want to gather real-time information on your current connection. See c...
Page 68
Chapter 3: working with target servers 57 steps click connection > info... To open the connection info dialog. Click copy to clipboard. Paste the information in a file of your choosing. Connection properties dynamic video compression algorithms maintain kvm console usability under varying bandwidth ...
Page 69
Chapter 3: working with target servers 58 33 kb (fast modem) 24 kb (slow modem) note that these settings are an optimization for specific conditions rather than an exact speed. The client and server always attempt to deliver video as quickly as possible on the network regardless of the current n...
Page 70
Chapter 3: working with target servers 59 button button name description same as choosing video > color calibrate. Target screenshot click to take a screenshot of the target server and save it to a file of your choosing. Audio opens a dialog that allows you to select from a list of audio devices con...
Page 71
Chapter 3: working with target servers 60 audio is supported by kx ii 2.4.0 (and later). Audio capture is supported by kx ii 2.5.0 (and later). Audio icons icon name description speaker these icons are located in status bar at the bottom of the client window. Green, blinking waves indicate an audio ...
Page 72
Chapter 3: working with target servers 61 import/export keyboard macros macros exported from active kvm client (akc) cannot be imported into multi-platform client (mpc) or virtual kvm client (vkc). Macros exported from mpc or vkc cannot be imported into akc. To import macros: 1. Choose keyboard > im...
Page 73
Chapter 3: working with target servers 62 the macros are then imported. If a macro is imported that contains a hot key that already exists, the hot key for the imported macro is discarded. To export macros: 1. Choose tools > export macros to open the select keyboard macros to export dialog. 2. Selec...
Page 74
Chapter 3: working with target servers 63 building a keyboard macro to build a macro: 1. Click keyboard > keyboard macros. The keyboard macros dialog appears. 2. Click add. The add keyboard macro dialog appears. 3. Type a name for the macro in the keyboard macro name field. This name appears in the ...
Page 75
Chapter 3: working with target servers 64 9. Select the new macro on the menu to run it or use the keystrokes you assigned to the macro. To use the send text to target function for the macro: 1. Click the keyboard > send text to target. The send text to target dialog appears. 2. Enter the text you w...
Page 76
Chapter 3: working with target servers 65 modifying and removing keyboard macros to modify a macro: 1. Choose keyboard > keyboard macros. The keyboard macros dialog appears. 2. Choose the macro from among those listed. 3. Click modify. The add/edit macro dialog appears. 4. Make your changes. 5. Clic...
Page 77
Chapter 3: working with target servers 66 video properties refreshing the screen the refresh screen command forces a refresh of the video screen. Video settings can be refreshed automatically in several ways: the refresh screen command forces a refresh of the video screen. The auto-sense video setti...
Page 78
Chapter 3: working with target servers 67 adjusting video settings use the video settings command to manually adjust the video settings. To change the video settings: 1. Choose video > video settings to open the video settings dialog. 2. Adjust the following settings as required. As you adjust the s...
Page 79
Chapter 3: working with target servers 68 best possible video mode the device will perform the full auto sense process when switching targets or target resolutions. Selecting this option calibrates the video for the best image quality. quick sense video mode with this option, the device will use...
Page 80
Chapter 3: working with target servers 69 screenshot from target command (target screenshot) you are able to take a screenshot of a target server using the screenshot from target server command. If needed, save this screenshot to a file location of your choosing as a bitmap, jpeg or png file. To tak...
Page 81
Chapter 3: working with target servers 70 mouse options when in dual mouse mode, and provided the option is properly configured, the mouse cursors align. In dual mouse mode, when controlling a target server, the remote console displays two mouse cursors: one belonging to your kx ii client workstatio...
Page 82
Chapter 3: working with target servers 71 mouse pointer synchronization when remotely viewing a target server that uses a mouse, two mouse cursors are displayed: one belonging to your remote client workstation and the other belonging to the target server. When the mouse pointer lies within the virtu...
Page 83
Chapter 3: working with target servers 72 additional notes for intelligent mouse mode be sure that there are no icons or applications in the upper left section of the screen since that is where the synchronization routine takes place. Do not use an animated mouse. Disable active desktop on kvm targe...
Page 84
Chapter 3: working with target servers 73 intelligent mouse mode in intelligent mouse mode, the device can detect the target mouse settings and synchronize the mouse cursors accordingly, allowing mouse acceleration on the target. Intelligent mouse mode is the default for non-vm targets. During synch...
Page 85
Chapter 3: working with target servers 74 please note that mouse configurations will vary on different target operating systems. Consult your os guidelines for further details. Also note that intelligent mouse synchronization does not work with unix targets. Absolute mouse mode in this mode, absolut...
Page 86
Chapter 3: working with target servers 75 single mouse mode single mouse mode uses only the target server mouse cursor and the local mouse pointer no longer appears onscreen. Note: single mouse mode does not work on windows or linux targets when client is running on a virtual machine. To enter singl...
Page 87
Chapter 3: working with target servers 76 united kingdom korean (korea) french (belgium) norwegian (norway) portuguese (portugal) danish (denmark) swedish (sweden) german (switzerland) hungarian (hungary) spanish (spain) italian (italy) slovenian translation: french - us ...
Page 88
Chapter 3: working with target servers 77 5. Click ok. Keyboard limitations turkish keyboards if using a turkish keyboard, you must connect to a target server through the active kvm client (akc). It is not supported by other raritan clients. Slovenian keyboards the limitation. Language configuration...
Page 89
Chapter 3: working with target servers 78 client launch settings kx ii users can configure client launch settings that allow you to define the screen settings for a kvm session. To configure client launch settings: 1. Click tools > options. The options dialog appears. 2. Click on the client launch s...
Page 90
Chapter 3: working with target servers 79 configure scan settings in vkc and akc the kx ii provides the port scanning feature to search for selected targets, and display them in a slide show view, allowing you to monitor up to 32 targets at one time. You can connect to targets or focus on a specific...
Page 91
Chapter 3: working with target servers 80 view status bar by default, the status bar is displayed at the bottom of the target window. To hide the status bar: click view > status bar to deselect it. To restore the status bar: click view > status bar to select it. Scaling scaling your target window al...
Page 92
Chapter 3: working with target servers 81 full screen mode when you enter full screen mode, the target's full screen is displayed and acquires the same resolution as the target server. The hot key used for exiting this mode is specified in the options dialog, see tool options (on page 75). While in ...
Page 93
Chapter 3: working with target servers 82 digital audio the kx ii supports end-to-end, bidirectional, digital audio connections for digital audio playback and capture devices from a remote client to a target server. The audio devices are accessed over a usb connection. Current device firmware is req...
Page 94
Chapter 3: working with target servers 83 saving audio settings audio device settings are applied on a per kx ii device basis. Once the audio devices settings are configured and saved on the kx ii, the same settings are applied to it. For example, you can configure a windows ® audio device to us a s...
Page 95
Chapter 3: working with target servers 84 operating system audio playback and capture supported by: mac ® virtual kvm client (vkc) multi-platform client (mpc) a speaker icon is displayed in the status bar at the bottom of the client window. It is grayed out when no audio is being used. When the spea...
Page 96
Chapter 3: working with target servers 85 connecting to a single target server from multiple remote clients kx ii 2.5.0 (and later) allows up to eight (8) users on different remote clients to connect to the same target server at the same time in order to listen in on audio playback. In order to use ...
Page 97
Chapter 3: working with target servers 86 connecting and disconnecting a digital audio device audio device settings are applied on a per kx ii device basis. Once the audio devices settings are configured and saved on the kx ii, the same settings are applied to it. See saving audio settings (on page ...
Page 98
Chapter 3: working with target servers 87 note: the device names listed in the connect recording device drop-down are truncated to a maximum of 30 characters for java clients. 8. Select the device that you wish to connect from the drop-down list. 9. Select the audio format for the recording device f...
Page 99
Chapter 3: working with target servers 88 to disconnect from the audio device: click the audio icon in the toolbar and select ok when you are prompted to confirm the disconnect. A confirmation message appears. Click ok. Adjusting capture and playback buffer size (audio settings) once an audio devi...
Page 100
Chapter 3: working with target servers 89 smart cards using the kx ii, you are able to mount a smart card reader onto a target server to support smart card authentication and related applications. For a list of supported smart cards, smart card readers, and additional system requirements, see smart ...
Page 101
Chapter 3: working with target servers 90 you are also able to remove or reinsert a smart card. This function can be used to provide notification to a target server os that requires a removal/reinsertion in order to display the appropriate login dialog. Using this function allows the notification to...
Page 102
Chapter 3: working with target servers 91 to update the smart card in the select smart card reader dialog: click refresh list if a new smart card reader has been attached to the client pc. To send smart card remove and reinsert notifications to the target: select the smart card reader that is curren...
Page 103
Chapter 3: working with target servers 92 2. Use the copy to clipboard button to copy the information contained in the dialog to a clipboard file so it can be accessed later when dealing with support (if needed). About the active kvm client active kvm client (akc) is based on microsoft windows .Net ...
Page 104
Chapter 3: working with target servers 93 since .Net is required to run akc, if you do not have .Net installed or you have an unsupported version of .Net installed, you will receive a message instructing you to check the .Net version. Note: raritan recommends windows xp ® operating system users veri...
Page 105
Chapter 3: working with target servers 94 multi-platform client (mpc) raritan multi-platform client (mpc) is a graphical user interface for the raritan product lines, providing remote access to target servers connected to raritan kvm over ip devices. For details on using mpc, see the kvm and serial ...
Page 106
Chapter 3: working with target servers 95 note: depending on your browser and browser security settings, you may see various security and certificate check and warning messages. It is necessary to accept the options in order to open mpc. Note: if you are using firefox 3.0.3, you may experience probl...
Page 107: Chapter 4 Virtual Media
96 all kx ii models support virtual media. Virtual media extends kvm capabilities by enabling target servers to remotely access media from a client pc and network file servers. With this feature, media mounted on client pcs and network file servers are essentially "mounted virtually" by the target s...
Page 108
Chapter 4: virtual media 97 remote pc vm prerequisites certain virtual media options require administrative privileges on the remote pc (for example, drive redirection of complete drives). Note: if you are using microsoft vista or windows 7, disable user account control or select run as administrato...
Page 109
Chapter 4: virtual media 98 supported tasks via virtual media virtual media provides the ability to perform tasks remotely, such as: transferring files running diagnostics installing or patching applications complete installation of the operating system record and playback of digital audio supported...
Page 110
Chapter 4: virtual media 99 supported virtual media operating systems the following client operating systems are supported: windows ® 7 operating system windows 8 operating system windows xp ® operating system opensuse ® 11.4 celadon (x86_64) fedora ® 18 rhel ® 6.4 osx mountain lion ® 10.7 (and late...
Page 111
Chapter 4: virtual media 100 connecting and disconnecting from virtual media access a virtual media drive on a client computer to access a virtual media drive on the client computer: 1. From the virtual kvm client, choose virtual media > connect drive, or click the connect drive... Button . The map ...
Page 112
Chapter 4: virtual media 101 mounting cd-rom/dvd-rom/iso images this option mounts cd-rom, dvd-rom, and iso images. Note: iso9660 format is the standard supported by raritan. However, other cd-rom extensions may also work. To access a cd-rom, dvd-rom, or iso image: 1. From the virtual kvm client, ch...
Page 113
Chapter 4: virtual media 102 note: if you are working with files on a linux ® target, use the linux sync command after the files are copied using virtual media in order to view the copied files. Files may not appear until a sync is performed. Note: if you are using the windows 7 ® operating system ®...
Page 114
Chapter 4: virtual media 103 drive partitions the following drive partition limitations exist across operating systems: windows ® and mac targets are not able to read linux formatted partitions windows and linux cannot read mac formatted partitions only windows fat partitions are supported by linux ...
Page 115
Chapter 4: virtual media 104 virtual media file server setup (file server iso images only) this feature is only required when using virtual media to access file server iso images. Iso9660 format is the standard supported by raritan. However, other cd-rom extensions may also work. Note: smb/cifs supp...
Page 116: Control
105 in this chapter overview ................................................................................................ 105 turning outlets on/off and cycling power ........................................... 106 overview the kx ii allows you to control raritan px and rpc series rack pdu (powe...
Page 117
Chapter 5: rack pdu (power strip) outlet control 106 control - turn outlets on or off, or cycle their power. association - the ports associated with the outlet. Initially, when you open the powerstrip page, the power strips that are currently connected to the kx ii are displayed in the powerstri...
Page 118
Chapter 5: rack pdu (power strip) outlet control 107 2. Click ok on the power off dialog. 3. Click ok on the power off confirmation dialog. The outlet will be turned off and its state will be displayed as 'off'. To cycle the power of an outlet: 1. Click cycle next to the outlet you want to cycle. Th...
Page 119: Chapter 6 Usb Profiles
108 in this chapter overview ................................................................................................ 108 cim compatibility .................................................................................. 109 available usb profiles .............................................
Page 120
Chapter 6: usb profiles 109 cim compatibility in order to make use of usb profiles, you must use a virtual media cim with updated firmware. For a list of virtual media cims, see supported computer interface module (cims) specifications (on page 289). A cim that has not had its firmware upgraded supp...
Page 121
Chapter 6: usb profiles 110 usb profile description usb enumeration will trigger whenever virtual media is connected or disconnected restrictions: usb bus speed limited to full-speed (12 mbit/s) absolute mouse synchronization not supported virtual cd-rom and disk drives cannot be used simult...
Page 122
Chapter 6: usb profiles 111 usb profile description bios generic bios generic use this profile when generic os profile does not work on the bios. Warning: usb enumeration will trigger whenever virtual media is connected or disconnected. Restrictions: usb bus speed limited to full-speed (12 mbit/s)...
Page 123
Chapter 6: usb profiles 112 usb profile description bios lenovo thinkpad t61 & x61 bios lenovo thinkpad t61 and x61 (boot from virtual media) use this profile to boot the t61 and x61 series laptops from virtual media. Restrictions: usb bus speed limited to full-speed (12 mbit/s) generic the generi...
Page 124
Chapter 6: usb profiles 113 usb profile description when using the mac boot menu mac os x ® 10.4.9 (and later) mac os x version 10.4.9 (and later) this profile compensates the scaling of mouse coordinates introduced in recent versions of mac os x. Select this if the remote and local mouse positions ...
Page 125
Chapter 6: usb profiles 114 usb profile description keyboard and mouse (type 2) first mass storage usb bus speed limited to full-speed (12 mbit/s) virtual cd-rom and disk drives cannot be used simultaneously warning: usb enumeration will trigger whenever virtual media is connected or disconn...
Page 126
Chapter 6: usb profiles 115 mouse modes when using the mac boot menu when working with usb profiles in, to use the mouse in the mac boot menu, you must use single mouse mode since absolute mouse mode is not supported in the bios. To configure the mouse to work at the boot menu: 1. Reboot the mac and...
Page 127
116 in this chapter user groups .......................................................................................... 116 users ..................................................................................................... 125 authentication settings ........................................
Page 128
Chapter 7: user management 117 user group list user groups are used with local and remote authentication (via radius or ldap/ldaps). It is a good idea to define user groups before creating individual users since, when you add a user, you must assign that user to an existing user group. The user grou...
Page 129
Chapter 7: user management 118 2. Type a descriptive name for the new user group into the group name field (up to 64 characters). 3. Select the checkboxes next to the permissions you want to assign to all of the users belonging to this group. See setting permissions. 4. Specify the server ports and ...
Page 130
Chapter 7: user management 119 note: several administrative functions are available within and from the kx ii local console. These functions are available only to members of the default admin group..
Page 131
Chapter 7: user management 120 setting permissions important: selecting the user management checkbox allows the members of the group to change the permissions of all users, including their own. Carefully consider granting these permissions. Permission description device access while under cc-sg mana...
Page 132
Chapter 7: user management 121 permission description settings. If you are using a tiered configuration in which a base kx ii device is used to access multiple other tiered devices, user, user group and remote authentication settings must be consistent across all devices. Setting port permissions fo...
Page 133
Chapter 7: user management 122 vm access power control access option description deny deny power control to the target server access full permission to power control on a target server for blade chassis, the port access permission will control access to the urls that have been configured for that bl...
Page 134
Chapter 7: user management 123 use the ip acl section of the group page to add, insert, replace, and delete ip access control rules on a group-level basis. To add (append) rules: 1. Type the starting ip address in the starting ip field. 2. Type the ending ip address in the ending ip field. 3. Choose...
Page 135
Chapter 7: user management 124 2. Click delete. 3. When prompted to confirm the deletion, click ok. Important: acl rules are evaluated in the order in which they are listed. For instance, in the example shown here, if the two acl rules were reversed, dominion would accept no communication at all. Ti...
Page 136
Chapter 7: user management 125 2. Click delete. 3. When prompted to confirm the deletion, click ok. Users users must be granted user names and passwords to gain access to the kx ii. This information is used to authenticate users attempting to access your kx ii. Up to 254 users can be created for eac...
Page 137
Chapter 7: user management 126 6. To activate the new user, leave the active checkbox selected. Click ok. View the kx ii users list the user list page displays a list of all users including their user name, full name, and user group. The list can be sorted on any of the columns by clicking on the co...
Page 138
Chapter 7: user management 127 username - username for user logins and target connections access from - ip address of client pc accessing the kx ii status - current active or inactive status of the connection to view users by port: choose user management > user by port. The users by port page opens....
Page 139
Chapter 7: user management 128 modifying an existing user to modify an existing user: 1. Open the user list page by choosing user management > user list. 2. Locate the user from among those listed on the user list page. 3. Click the user name. The user page opens. 4. On the user page, change the app...
Page 140
Chapter 7: user management 129 4. If you choose ldap/ldaps, read the section entitled implementing ldap remote authentication for information about completing the fields in the ldap section of the authentication settings page. 5. If you choose radius, read the section entitled implementing radius re...
Page 141
Chapter 7: user management 130 microsoft active directory. Active directory is an implementation of ldap/ldaps directory services by microsoft for use in windows environments. 8. Type the name of the active directory domain if you selected microsoft active directory. For example, acme.Com. Consult...
Page 142
Chapter 7: user management 131 11. If you entered a distinguished name for the administrative user, you must enter the password that will be used to authenticate the administrative user's dn against the remote authentication server. Enter the password in the secret phrase field and again in the conf...
Page 143
Chapter 7: user management 132 15. Select the enable ldaps server certificate validation checkbox to use the previously uploaded root ca certificate file to validate the certificate provided by the server. If you do not want to use the previously uploaded root ca certificate file, leave this checkbo...
Page 144
Chapter 7: user management 133 once the test is completed, a message will be displayed that lets you know the test was successful or, if the test failed, a detailed error message will be displayed. It will display successful result or detail error message in failure case. It also can display group i...
Page 145
Chapter 7: user management 134 important notes group name is case sensitive. The kx ii provides the following default groups that cannot be changed or deleted: admin and . Verify that your active directory server does not use the same group names. If the group information returned from the active di...
Page 146
Chapter 7: user management 135 9. The default number of retries is 3 retries. This is the number of times the kx ii will send an authentication request to the radius server. 10. Choose the global authentication type from among the options in the drop-down list: pap - with pap, passwords are sent a...
Page 147
Chapter 7: user management 136 cisco acs 5.X for radius authentication if you are using a cisco acs 5.X server, after you have configured the kx ii for radius authentication, complete the following steps on the cisco acs 5.X server. Note: the following steps include the cisco menus and menu items us...
Page 148
Chapter 7: user management 137 returning user group information via radius when a radius authentication attempt succeeds, the kx ii determines the permissions for a given user based on the permissions of the user's group. Your remote radius server can provide these user group names by returning an a...
Page 149
Chapter 7: user management 138 attribute data acct-status (40) stop(2) - stops the accounting nas-port-type (61) virtual (5) for network connections. Nas-port (5) always 0. Nas-ip-address (4) the ip address for the kx ii. User-name (1) the user name entered at the login screen. Acct-session-id (44) ...
Page 150
Chapter 7: user management 139 user authentication process remote authentication follows the process specified in the flowchart below:.
Page 151
Chapter 7: user management 140 changing a password to change your kx ii password: 1. Choose user management > change password. The change password page opens. 2. Type your current password in the old password field. 3. Type a new password in the new password field. Retype the new password in the con...
Page 152
141 in this chapter network settings ................................................................................... 141 device services ..................................................................................... 145 power supply setup .....................................................
Page 153
Chapter 8: device management 142 assign the kx ii an ip address to assign an ip address to the kx ii: 1. Choose device settings > network. The network settings page opens. 2. Specify a meaningful device name for your kx ii device. Up to 32 alphanumeric and valid special characters, no spaces between...
Page 154
Chapter 8: device management 143 configure the ipv6 settings 1. If using ipv6, enter or select the appropriate ipv6-specific network settings in the ipv6 section: a. Select the ipv6 checkbox to activate the fields in the section and enable ipv6 on the device. B. Enter a global/unique ip address. Thi...
Page 155
Chapter 8: device management 144 2. If use the following dns server addresses is selected, whether or not dhcp is selected, the addresses entered in this section is used to connect to the dns server. Enter the following information if the following dns server addresses is selected. These addresses a...
Page 156
Chapter 8: device management 145 note: because a failover port is not activated until after a failover has actually occurred, raritan recommends that you not monitor the port or monitor it only after a failover occurs. When this option is enabled, the following two fields are used: ping interval (...
Page 157
Chapter 8: device management 146 3. Enter the ssh port information. The standard ssh tcp port number is 22 but the port number can be changed to provide a higher level of security operations. 4. Click ok. Http and https port settings you are able to configure http and/or https ports used by the kx i...
Page 158
Chapter 8: device management 147 configuring and enabling tiering the tiering feature allows you to access kx ii targets and pdus through one base kx ii device. This feature is available for standard kx ii devices as well as kx2-808, kx2-832 and kx2-864 devices. Note: base and tiered devices must al...
Page 159
Chapter 8: device management 148 port configuration, including changing the cim name, must be done directly from each device. It cannot be done from the base device for tiered target ports. Tiering also supports the use of kvm switches to switch between servers. See configuring kvm switches (on page...
Page 160
Chapter 8: device management 149 6. In the tier secret field, enter the same secret word you entered for the base device on the device settings page. Click ok. Tiering - target types, supported cims and tiering configurations blade chassis blade chassis that attached directly to the base are accessi...
Page 161
Chapter 8: device management 150 unsupported and limited features on tiered targets the following features are not supported on tiered targets: blade chassis on tiered devices audio on tiered devices smart cards on tiered devices virtual media tiered devices mccat as a tiered device port group manag...
Page 162
Chapter 8: device management 151 cabling example in tiered configurations the following diagram illustrates the cabling configurations between a kx ii tiered device and a kx ii base device..
Page 163
Chapter 8: device management 152 diagram key target server cim from target server to the kx ii tiered device kx ii tiered device d2cim-dvusb cim from the kx ii tiered device to the kx ii base device kx ii base device enabling direct port access via url direct port access allows users to bypass havin...
Page 164
Chapter 8: device management 153 direct port access url syntax for the virtual kvm client (vkc) if you are using the virtual kvm client (vkc) and direct port access, use one of the following syntaxes for standard ports: https://ipaddress/dpa.Asp?Username=username&password=passwo rd&port=port number ...
Page 165
Chapter 8: device management 154 direct port access url syntax for the active kvm client (akc) if you are using the active kvm client (akc) and direct port access, use: https://ipaddress/dpa.Asp?Username=username&password=passwo rd&port=port number&client=akc or https://ipaddress/dpa.Asp?Username=us...
Page 166
Chapter 8: device management 155 enable direct port access to enable direct port access: 1. Choose device settings > device services. The device service settings page opens. 2. Select enable direct port access via url if you would like users to have direct access to a target via the dominion device ...
Page 167
Chapter 8: device management 156 enabling the akc download server certificate validation if you are using the akc client, you can choose to use the enable akc download server certificate validation feature or opt not to use this feature. Note: when operating in ipv4 and ipv6 dual stack mode with 'en...
Page 168
Chapter 8: device management 157 2. Launch internet explorer ® using the kx ii ip address as the url. A certificate error message will be displayed. 3. Select view certificates. 4. On the general tab, click install certificate. The certificate is then installed in the trusted root certification auth...
Page 169
Chapter 8: device management 158 3. Select either or both enable snmp v1/v2c and enable snmp v3. At least one option must be selected. Required 4. Complete the following fields for snmp v1/v2c (if needed): a. Community - the device's community string b. Community type - grant either read-only or rea...
Page 170
Chapter 8: device management 159 configure snmp traps on the event management - settings page, which can be quickly accessed by clicking the snmp trap configuration link. See configuring snmp traps (on page 162)for information on creating snmp traps and list of kx ii snmp traps (on page 165) for a l...
Page 171
Chapter 8: device management 160 this information is used to configure modem settings. Because different modems have different ways of settings these values, this document does not specify how to set these values, rather the user should refer to the modem to create the appropriate modem-specific str...
Page 172
Chapter 8: device management 161 see certified modems (on page 307) for information on certified modems that work with the kx ii. For information on settings that will give you the best performance when connecting to the kx ii via modem, see creating, modifying and deleting profiles in mpc - generat...
Page 173
Chapter 8: device management 162 event management the kx ii event management feature allows you enable and disable the distribution of system events to snmp managers, the syslog and the audit log. These events are categorized, and for each event you can determine whether you want the event sent to o...
Page 174
Chapter 8: device management 163 a. Destination ip/hostname - the ip or hostname of the snmp manager. Up to five (5) snmp managers can be created note: ipv6 addresses cannot exceed 80 characters in length for the host name. B. Port number - the port number used by the snmp manager c. Community - the...
Page 175
Chapter 8: device management 164 use the link to snmp agent configuration link to quickly navigate to the devices services page from the event management - settings page. The events that are captured once an snmp trap is configured are selected on the event management - destination page. See configu...
Page 176
Chapter 8: device management 165 use the reset to factory defaults feature to remove the snmp configuration and set the kx ii to its original factory default. To reset to factory defaults: click reset to defaults. Warning: when using snmp traps over udp, it is possible for the kx ii and the router t...
Page 177
Chapter 8: device management 166 trap name description networkfailure an ethernet interface of the product can no longer communicate over the network. Networkparameterchanged a change has been made to the network parameters. Passwordsettingschanged strong password settings have changed. Portconnect ...
Page 178
Chapter 8: device management 167 trap name description userforcedlogout a user was forcibly logged out by admin userlogin a user has successfully logged into the kx ii and has been authenticated. Userlogout a user has successfully logged out of the kx ii properly. Usermodified a user account has bee...
Page 179
Chapter 8: device management 168 note: if you have read-write privileges to the mib file, use a mib editor to make changes to the file. Syslog configuration to configure the syslog (enable syslog forwarding): 1. Select enable syslog forwarding to log the device's messages to a remote syslog server. ...
Page 180
Chapter 8: device management 169 configuring event management - destinations system events, if enabled, generate snmp notification events (traps), or can be logged to the syslog or audit log. Use the event management - destinations page to select the system events to track and where to send this inf...
Page 181
Chapter 8: device management 170 power supply setup the kx ii provides dual power supplies, and can automatically detect and provide notification regarding the status of these power supplies. Use the power supply setup page to specify whether you are using one or both of the power supplies. Proper c...
Page 182
Chapter 8: device management 171 note: if either of these checkboxes is selected and power input is not actually connected, the power led at the front of the unit turns red. To turn off the automatic detection: deselect the checkbox for the appropriate power supply. To reset to factory defaults: c...
Page 183
Chapter 8: device management 172 alternatively, rename ports that are currently not connected to the kx ii via a cim and, as such, have a status of not available. To rename a port with a status of not available, do one of the following: rename the port. When a cim is attached the cim name will be ...
Page 184
Chapter 8: device management 173 configuring standard target servers to name the target servers: 1. Connect all of the target servers if you have not already done so. See step 3: connect the equipment (on page 16) for a description of connecting the equipment. 2. Choose device settings > port config...
Page 185
Chapter 8: device management 174 8. Click ok. Configuring kvm switches the kx ii also supports use of hot key sequences to switch between targets. In addition to using hot key sequences with standard servers, kvm switching is supported by blade chassis and in tiered configurations. Important: in ord...
Page 186
Chapter 8: device management 175 note: only one switch will appear in the drop-down. 5. Select kvm switch hot key sequence. 6. Enter the maximum number of target ports (2-32). 7. In the kvm switch name field, enter the name you want to use to refer to this port connection. 8. Activate the targets th...
Page 187
Chapter 8: device management 176 configuring cim ports the kx ii supports the use of standard and virtual media cims to connect a server to the kx ii. To access a cim to configure: 1. Choose device settings > port configuration. The port configuration page opens. 2. Click the port name of the target...
Page 188
Chapter 8: device management 177 if you are using an hdmi cim, some operating system/video card combinations may offer a limited range of rgb values. Improve the colors by selecting the dvi compatibility mode checkbox. Apply selected profiles to other cims 1. Apply the profile to other cims by selec...
Page 189
Chapter 8: device management 178 connecting a rack pdu raritan px series rack pdus (power strips) are connected to the dominion device using the d2cim-pwr cim. To connect the rack pdu: 1. Connect the male rj-45 of the d2cim-pwr to the female rj-45 connector on the serial port of the rack pdu. 2. Con...
Page 190
Chapter 8: device management 179 naming the rack pdu (port page for power strips) note: px rack pdus (power strips) can be named in the px as well as in the kx ii. Once a raritan remote rack pdu is connected to the kx ii, it will appear on the port configuration page. Click on the power port name on...
Page 191
Chapter 8: device management 180 3. Click ok..
Page 192
Chapter 8: device management 181 associating outlets with target servers the port page opens when you click on a port on the port configuration page. From this page, you can make power associations, change the port name to something more descriptive, and update target server settings if you are usin...
Page 193
Chapter 8: device management 182 removing power associations when disconnecting target servers and/or rack pdus from the device, all power associations should first be deleted. When a target has been associated with a rack pdu and the target is removed from the device, the power association remains....
Page 194
Chapter 8: device management 183 configuring blade chassis in addition to standard servers and rack pdus (power strips), you can control blade chassis that are plugged into the kx ii device port. Up to eight blade chassis can be managed at a given time. The blade chassis must be configured as a blad...
Page 195
Chapter 8: device management 184 two modes of operation are provided for blade chassis: manual configuration and auto-discovery, depending on the blade chassis capabilities. If a blade chassis is configured for auto-discovery, the dominion device tracks and updates the following: when a new blade se...
Page 196
Chapter 8: device management 185 generic blade chassis configuration the generic blade chassis' selection provides only a manual configuration mode of operation. See supported blade chassis models (on page 198), supported cims for blade chassis (on page 199), and required and recommended blade chass...
Page 197
Chapter 8: device management 186 9. In the blade chassis managed links section of the page, you are able to configure the connection to a blade chassis web browser interface if one is available. Click the blade chassis managed links icon to expand the section on the page. The first url link is inten...
Page 198
Chapter 8: device management 187 13. Select the cims native, display resolution from the display native resolution drop-down. This is the preferred resolution and timing mode of the digital cim. Once a resolution is selected, it is applied to the cim. If no selection is made, the default 1024x1280@6...
Page 199
Chapter 8: device management 188 c. Administrative module primary ip address/host name - enter the primary ip address for the blade chassis. Required for auto-discovery mode d. Port number - the default port number for the blade chassis is 22. Change the port number if applicable. Required for auto-...
Page 200
Chapter 8: device management 189 b. Url - enter the url to the interface. See blade chassis sample url formats (on page 203) for sample configurations for the dell m1000e. C. Username - enter the username used to access the interface. D. Password - enter the password used to access the interface. No...
Page 201
Chapter 8: device management 190 d. Port number - the default port number for the blade chassis is 22. Not applicable. E. Username - not applicable. F. Password - not applicable. 2. Change the blade chassis name if needed. 3. Indicate the blades that are installed in the blade chassis by checking th...
Page 202
Chapter 8: device management 191 5. Usb profiles do not apply to dell chassis. 6. Click ok to save the configuration. Ibm blade chassis configuration see supported blade chassis models (on page 198), supported cims for blade chassis (on page 199), and required and recommended blade chassis configura...
Page 203
Chapter 8: device management 192 f. Password - enter the password used to access the blade chassis. Required for auto-discovery mode 2. If you want the kx ii to auto-discover the chassis blades, select the blade auto-discovery checkbox and then click discover blades on chassis now. Once the blades a...
Page 204
Chapter 8: device management 193 e. The username field and password field, which are both optional, contain the labels that are expected to be associated with the username and password entries. It is in these fields you should enter the field names for the username and password fields used on the lo...
Page 205
Chapter 8: device management 194 the first url link is intended for use to connect to the blade chassis administration module gui. Note: access to the url links entered in this section of the page is governed by the blade chassis port permissions. A. Active - to activate the link once it is configur...
Page 206
Chapter 8: device management 195 tips for adding a web browser interface you can add a web browser interface to create a connection to a device with an embedded web server. A web browser interface can also be used to connect to any web application, such as the web application associated with an rsa,...
Page 207
Chapter 8: device management 196 hp and cisco ucs blade chassis configuration (port group management) the kx ii supports the aggregation of ports connected to certain types of blades into a group representing the blade chassis. Specifically, cisco ® ucs, hp ® bladeserver blades and dell ® poweredge ...
Page 208
Chapter 8: device management 197 3. Enter a port group name. The port group name is not case sensitive and can contain up to 32 characters. 4. Select the blade server group checkbox. If you want to designate that these ports are attached to blades housed in a blade chassis (for example, hp c3000 or ...
Page 209
Chapter 8: device management 198 supported blade chassis models this table contains the blade chassis models that are supported by the kx ii and the corresponding profiles that should be selected per chassis model when configuring them in the kx ii application. A list of these models can be selected...
Page 210
Chapter 8: device management 199 supported cims for blade chassis the following cims are supported for blade chassis being managed through the kx ii: dcim-ps2 dcim-usbg2 d2cim-vusb d2cim-dvusb following is a table containing supported cims for each blade chassis model that the kx ii supports. Blade ...
Page 211
Chapter 8: device management 200 blade chassis connection method recommended cim(s) both modules enable you to connect a ps/2-compatible keyboard, mouse and video monitor to the system (using a custom cable provided with the system). Source: dell poweredge 1955 owner's manual dell poweredge m1000e t...
Page 212
Chapter 8: device management 201 blade chassis connection method recommended cim(s) technology ibm bladecenter e the current model bladecenter e chassis (8677-3rx) ships standard with one advanced management module. Source: ibm bladecenter products and technology dcim-usbg2 d2cim-dvusb ibm bladecent...
Page 213
Chapter 8: device management 202 this table contains information on limitations and constraints that apply to configuring blade chassis to work with the kx ii. Raritan recommends that all of the information below is followed. Blade chassis required/recommended action dell ® poweredge ™ m1000e disa...
Page 214
Chapter 8: device management 203 blade chassis required/recommended action do not designate any slots for scan operations in the ikvm gui setup scan menu or the ikvm may not work properly. to avoid having the ikvm gui display upon connecting to the blade chassis, set the screen delay time to 8 s...
Page 215
Chapter 8: device management 204 blade chassis sample url format password: calvin password field: password dell 1855 url: https://192.168.60.33/forms/f_login username: root username field: text_user_name password: calvin password field: text_password ibm ® bladecenter ® e or h http://192.168.84.217/...
Page 216
Chapter 8: device management 205 2. Click the port name for the kvm port you want to edit. The port page opens. To select the usb profiles for a kvm port: 1. In the select usb profiles for port section, select one or more usb profiles from the available list. shift-click and drag to select several...
Page 217
Chapter 8: device management 206 configuring kx ii local port settings from the local port settings page, you can customize many settings for the kx ii local console including keyboard, hot keys, video switching delay, power save mode, local user interface resolution settings, and local user authent...
Page 218
Chapter 8: device management 207 note: if you are using kx2-808, kx2-832 and kx2-864 as tiered devices, you must connect them to the base kx ii via the extended local port. 4. If you are using the tiering feature, select the enable local port device tiering checkbox and enter the tiered secret word ...
Page 219
Chapter 8: device management 208 note: keyboard use for chinese, japanese, and korean is for display only. Local language input is not supported at this time for kx ii local console functions. Note: if using a turkish keyboard, you must connect to a target server through the active kvm client (akc)....
Page 220
Chapter 8: device management 209 1280x1024 13. Choose the refresh rate from the drop-down list. The browser will be restarted when this change is made. 60 hz 75 hz 14. Choose the type of local user authentication. local/ldap/radius. This is the recommended option. For more information about ...
Page 221
Chapter 8: device management 210 kx2-808, kx2-832 and kx2-864 standard and extended local port settings the kx2-808, kx2-832 and kx2-864 provide you with two local port options: the standard local port and the extended local port. Each of these port options is enabled and disabled from the remote co...
Page 222
Chapter 8: device management 211 connect and disconnect scripts the kx ii provides the ability to execute key macro scripts when connecting to or disconnecting from a target. You can create and edit your own scripts on the connection script page to perform additional actions when connecting to or di...
Page 223
Chapter 8: device management 212 3. In the apply selected scripts to ports section, select the target(s) you want to apply the script to using select all or clicking on the checkbox to the left of each target to apply the script to only select targets. 4. Click apply scripts. Once the script is adde...
Page 224
Chapter 8: device management 213 for example, select f1-f16 to display the function key set in the add box. Select a function key and add it to the script box. Next, select letters from the key set drop-down and add a letter key to the script. 8. Optionally, add text that will display when the scrip...
Page 225
Chapter 8: device management 214.
Page 226
Chapter 8: device management 215 modifying scripts to modify existing scripts: 1. Click device settings > connection scripts. The connection scripts page opens. 2. In the available connection scripts section, select the script you want to modify and click modify. The page is then in edit mode. 3. Ma...
Page 227
Chapter 8: device management 216 5. Click import. The configuration scripts page opens and the imported scripts are displayed. To export a disconnect script: 1. Click device settings > configuration scripts. The configuration scripts page opens. 2. In the available connection scripts section, select...
Page 228
Chapter 8: device management 217 creating port groups the kx ii supports the aggregation of multiple ports into a single port group.Port groups consist solely of ports configured as standard kvm ports. A port may only be a member of a single group. Ports that are available to be included in a port g...
Page 229
Chapter 8: device management 218 creating a dual video port group the dual video port groups feature allows you to group two video ports into one group. Use this feature when you need to connect to a server with two video cards/ports, and you want to access both ports from the same remote client at ...
Page 230
Chapter 8: device management 219 note: if a port is already a part of blade server port group, another dual video port group, or 'standard' port group, the port is not an option since ports can only belong to a single port group at a time. 3. Select the dual video port group radio button. 4. From th...
Page 231
Chapter 8: device management 220 3. Click apply. Click reset defaults to change back to english. Note: once you apply a new language, the online help is also localized to match your language selection..
Page 232
221 in this chapter security settings .................................................................................... 221 configuring ip access control .............................................................. 232 ssl certificates ..............................................................
Page 233
Chapter 9: security management 222 to reset back to defaults: click reset to defaults. Login limitations using login limitations, you can specify restrictions for single login, password aging, and the logging out idle users. Limitation description enable single login limitation when selected, only o...
Page 234
Chapter 9: security management 223 limitation description enter the number of days after which a password change is required. The default is 60 days. Log out idle users, after (1-365 minutes) select the "log off idle users" checkbox to automatically disconnect users after the amount of time you spec...
Page 235
Chapter 9: security management 224 strong passwords strong passwords provide more secure local authentication for the system. Using strong passwords, you can specify the format of valid kx ii local passwords such as minimum and maximum length, required characters, and password history retention. Str...
Page 236
Chapter 9: security management 225 user blocking the user blocking options specify the criteria by which users are blocked from accessing the system after the specified number of unsuccessful login attempts. The three options are mutually exclusive: option description disabled the default option. Us...
Page 237
Chapter 9: security management 226 option description timer lockout users are denied access to the system for the specified amount of time after exceeding the specified number of unsuccessful login attempts. When selected, the following fields are enabled: attempts - the number of unsuccessful log...
Page 238
Chapter 9: security management 227 encryption & share using the encryption & share settings you can specify the type of encryption used, pc and vm share modes, and the type of reset performed when the kx ii reset button is pressed. Warning: if you select an encryption mode that is not supported by y...
Page 239
Chapter 9: security management 228 encryption mode description browser supports it, otherwise you will not be able to connect. See checking your browser for aes encryption (on page 229) for more information. Aes-256 the advanced encryption standard (aes) is a national institute of standards and tech...
Page 240
Chapter 9: security management 229 6. If needed, select local device reset mode. This option specifies which actions are taken when the hardware reset button (at the back of the device) is depressed. For more information, see resetting the kx ii using the reset button (on page 285). Choose one of th...
Page 241
Chapter 9: security management 230 enabling fips 140-2 for government and other high security environments, enabling fips 140-2 mode may be required. The kx ii uses an embedded fips 140-2-validated cryptographic module running on a linux ® platform per fips 140-2 implementation guidance section g.5 ...
Page 242
Chapter 9: security management 231 fips 140-2 support requirements the kx ii supports the use of fips 140-2 approved encryption algorithms. This allows an ssl server and client to successfully negotiate the cipher suite used for the encrypted session when a client is configured for fips 140-2 only m...
Page 243
Chapter 9: security management 232 configuring ip access control using ip access control, you control access to your kx ii. Note that ip access control restricts traffic of any kind from accessing the kx ii, so ntp servers, radius hosts, dns hosts and so on must be granted access to the kx ii. By se...
Page 244
Chapter 9: security management 233 3. Choose the policy from the drop-down list. 4. Click insert. If the rule # you just typed equals an existing rule #, the new rule is placed ahead of the exiting rule and all rules are moved down in the list. Tip: the rule numbers allow you to have more control ov...
Page 245
Chapter 9: security management 234 ssl certificates the kx ii uses the secure socket layer (ssl) protocol for any encrypted network traffic between itself and a connected client. When establishing a connection, the kx ii has to identify itself to a client using a cryptographic certificate. It is pos...
Page 246
Chapter 9: security management 235 f. Country (iso code) - the country where the organization is located. This is the two-letter iso code, e.G. De for germany, or us for the u.S. G. Challenge password - some certification authorities require a challenge password to authorize later changes on the cer...
Page 247
Chapter 9: security management 236 b. A message containing all of the information you entered appears. C. The csr and the file containing the private key used when generating it can be downloaded by clicking download csr. D. Send the saved csr to a ca for certification. You will get the new certific...
Page 248
Chapter 9: security management 237 security banner kx ii provides you with the ability to add a security banner to the kx ii login process. This feature requires users to either accept or decline a security agreement before they can access the kx ii. The information provided in a security banner wil...
Page 249
Chapter 9: security management 238 note: you cannot upload a text file from the local port..
Page 250: Chapter 10 Maintenance
239 in this chapter audit log................................................................................................ 239 device information ................................................................................. 240 backup and restore .................................................
Page 251
Chapter 10: maintenance 240 to page through the audit log: use the [older] and [newer] links. Device information the device information page provides detailed information about your kx ii device and the cims in use. This information is helpful should you need to contact raritan technical support. To...
Page 252
Chapter 10: maintenance 241 dcim-susb d2cim-vusb d2cim-dvusb d2cim-dvusb-dvi d2cim-dvusb-hdmi d2cim-dvusb note: only the numeric portion of the serial numbers are displayed for the dcim-usb, dcim-ps2 and dcim-usb g2 cims. For example, xxx1234567 is displayed. The serial number prefix gn ...
Page 253
Chapter 10: maintenance 242 backup and restore from the backup/restore page, you can backup and restore the settings and configuration for your kx ii. In addition to using backup and restore for business continuity purposes, you can use this feature as a time-saving mechanism. For instance, you can ...
Page 254
Chapter 10: maintenance 243 in ie 7 (and later), ie is used as the default application to open files, so you are prompted to open the file versus save the file. To avoid this, you must change the default application that is used to open files to wordpad ® . 2. To do this: a. Save the backup file. Th...
Page 255
Chapter 10: maintenance 244 usb profile management from the usb profile management page, you can upload custom profiles provided by raritan tech support. These profiles are designed to address the needs of your target server’s configuration, in the event that the set of standard profiles does not al...
Page 256
Chapter 10: maintenance 245 as noted, you may delete a custom profile from the system while it is still designated as an active profile. Doing so will terminate any virtual media sessions that were in place. Handling conflicts in profile names a naming conflict between custom and standard usb profil...
Page 257
Chapter 10: maintenance 246 to upgrade your kx ii unit: 1. Locate the appropriate raritan firmware distribution file (*.Rfp) on the raritan website http://www.Raritan.Com on the firmware upgrades web page. 2. Unzip the file. Please read all instructions included in the firmware zip files carefully b...
Page 258
Chapter 10: maintenance 247 as prompted, close the browser and wait approximately 5 minutes before logging in to the kx ii again. Again. For information about upgrading the device firmware using the multi-platform client, see upgrading device firmware in the kvm and serial access clients guide. Note...
Page 259
Chapter 10: maintenance 248 rebooting the kx ii the reboot page provides a safe and controlled way to reboot your kx ii. This is the recommended method for rebooting. Important: all kvm and serial connections will be closed and all users will be logged off. To reboot your kx ii: 1. Choose maintenanc...
Page 260
Chapter 10: maintenance 249 stopping cc-sg management while the kx ii is under cc-sg management, if you try to access the device directly, you are notified that it the device is under cc-sg management. If you are managing the kx ii through cc-sg and connectivity between cc-sg and the kx ii is lost a...
Page 261
Chapter 10: maintenance 250 3. Click yes to remove the device cc-sg management. Once cc-sg management has ended, a confirmation will be displayed..
Page 262: Chapter 11 Diagnostics
251 in this chapter network interface page ......................................................................... 251 network statistics page ......................................................................... 251 ping host page .................................................................
Page 263
Chapter 11: diagnostics 252 statistics - produces a page similar to the one displayed here. interfaces - produces a page similar to the one displayed here..
Page 264
Chapter 11: diagnostics 253 route - produces a page similar to the one displayed here. 3. Click refresh. The relevant information is displayed in the result field. Ping host page ping is a network tool used to test whether a particular host or ip address is reachable across an ip network. Using th...
Page 265
Chapter 11: diagnostics 254 2. Type either the hostname or ip address into the ip address/host name field. Note: the host name cannot exceed 232 characters in length. 3. Click ping. The results of the ping are displayed in the result field. Trace route to host page trace route is a network tool used...
Page 266
Chapter 11: diagnostics 255 device diagnostics note: this page is for use by raritan field engineers or when you are directed by raritan technical support. Device diagnostics downloads the diagnostics information from the kx ii to the client machine. Two operations can be performed on this page: exe...
Page 267
Chapter 11: diagnostics 256 a. Click save to file. The file download dialog opens. B. Click save. The save as dialog box opens. C. Navigate to the desired directory and click save. D. Email this file as directed by raritan technical support..
Page 268
257 in this chapter overview ................................................................................................ 257 accessing the kx ii using cli .............................................................. 258 ssh connection to the kx ii ................................................
Page 269
Chapter 12: command line interface (cli) 258 accessing the kx ii using cli access the kx ii by using one of the following methods: ssh (secure shell) via ip connection a number of ssh clients are available and can be obtained from the following locations: putty - http://www.Chiark.Greenend.Org.Uk/~s...
Page 270
Chapter 12: command line interface (cli) 259 logging in to log in, enter the user name admin as shown: 1. Log in as admin 2. The password prompt appears. Enter the default password: raritan the welcome message displays. You are now logged on as an administrator. After reviewing the following navigat...
Page 271
Chapter 12: command line interface (cli) 260 cli syntax -tips and shortcuts tips commands are listed in alphabetical order. Commands are not case sensitive. Parameter names are single word without underscore. Commands without arguments default to show current settings for the command. Typing a quest...
Page 272
Chapter 12: command line interface (cli) 261 initial configuration using cli note: these steps, which use the cli, are optional since the same configuration can be done via kvm. See getting started (on page 12) for more information. Kx ii devices come from the factory with default factory settings. ...
Page 273
Chapter 12: command line interface (cli) 262 the kx ii now has the basic configuration and can be accessed remotely via ssh, gui, or locally using the local serial port. The administrator needs to configure the users and groups, services, security, and serial ports to which the serial targets are at...
Page 274
Chapter 12: command line interface (cli) 263 enter admin > config > network. Command description help display overview of commands. History display the current session's command line history. Interface set/get network parameters. Ipv6_interface set/get ipv6 network parameters. Logout logout of the c...
Page 275
Chapter 12: command line interface (cli) 264 commands description ipv6 set/get ipv6 network parameters. Interface command theinterface command is used to configure the kx ii network interface. The syntax of the interface command is: interface [ipauto ] [ip ] [mask ] [gw ] [mode ] set/get ethernet pa...
Page 276
Chapter 12: command line interface (cli) 265 name command the name command is used to configure the network name. The syntax of the name is: name [devicename ] [hostname ] device name configuration devicename device name hostname preferred host name (dhcp only) name command example the following com...
Page 277
266 in this chapter overview ................................................................................................ 266 simultaneous users .............................................................................. 266 kx ii local console interface: kx ii devices ..........................
Page 278
Chapter 13: kx ii local console 267 kx ii local console interface: kx ii devices when you are located at the server rack, the kx ii provides standard kvm management and administration via the kx ii local console. The kx ii local console provides a direct kvm (analog) connection to your connected ser...
Page 279
Chapter 13: kx ii local console 268 port access page (local console server display) after you login to the kx ii local console, the port access page opens. This page lists all of the kx ii ports, and the target servers, port groups, and blade chassis that are connected to those ports. The port acces...
Page 280
Chapter 13: kx ii local console 269 scanning ports - local console the kx ii scanning feature is supported by the local console. The targets that are found during the scan are displayed on the scan page one at a time, which is different from the remote console port slide show. Each target is display...
Page 281
Chapter 13: kx ii local console 270 local port scan mode following are options available to you to change scan options on local port. To configure the local console scan port settings: 1. On the local console, select device settings. 2. In the local port settings section, select local port scan mode...
Page 282
Chapter 13: kx ii local console 271 4. Click ok. Once the smart card reader is added, a message will appear on the page indicating you have completed the operation successfully. A status of either selected or not selected will appear in the left panel of the page under card reader. To update the car...
Page 283
Chapter 13: kx ii local console 272 local console usb profile options from the usb profile options section of the tools page, you can choose from the available usb profiles. The ports that can be assigned profiles are displayed in the port name field and the profiles that are available for a port ap...
Page 284
Chapter 13: kx ii local console 273 hot keys and connect keys because the kx ii local console interface is completely replaced by the interface for the target server you are accessing, a hot key is used to disconnect from a target and return to the local port gui. A connect key is used to connect to...
Page 285
Chapter 13: kx ii local console 274 standard servers connect key action key sequence example disconnect from a target and return to the local port gui disconnect from target port 5, slot 11 and return to the local port gui (the page from which you connected to target): double click scroll lock speci...
Page 286
Chapter 13: kx ii local console 275 returning to the kx ii local console interface important: the kx ii local console default hot key is to press the scroll lock key twice rapidly. This key combination can be changed in the local port settings page. See configuring kx ii local port settings from the...
Page 287
Chapter 13: kx ii local console 276 us us/international united kingdom french (france) german (germany) jis (japanese industry standard) simplified chinese traditional chinese dubeolsik hangul (korean) german (switzerland) portuguese (portugal) norwegian (norway) swedish (s...
Page 288
Chapter 13: kx ii local console 277 hot key: take this action: double click left ctrl key press the left ctrl key twice quickly 4. Select the local port connect key. Use a connect key sequence to connect to a target and switch to another target. You can then use the hot key to disconnect from the ta...
Page 289
Chapter 13: kx ii local console 278 note: if you initially choose not to ignore cc manage mode on the local port but later want local port access, you will have to remove the device from under cc-sg management (from within cc-sg). You will then be able to check this checkbox. 11. Click ok..
Page 290
Chapter 13: kx ii local console 279 configuring kx ii local port settings from the local console the standard local port and the extended local port can be configured from the remote console on the port configuration page, or from the local console on the local port settings page. See configuring kx...
Page 291
Chapter 13: kx ii local console 280 ip auto configuration ip address subnet mask gateway ip address primary dns server ip address secondary dns server ip address discovery port bandwidth limit lan interface speed & duplex enable automatic failover ping interval (seconds) time...
Page 292
Chapter 13: kx ii local console 281 connect and disconnect scripts the kx ii provides the ability to execute key macro scripts when connecting to or disconnecting from a target. You can create and edit your own scripts on the connection script page to perform additional actions when connecting to or...
Page 293
Chapter 13: kx ii local console 282 3. In the apply selected scripts to ports section, select the target(s) you want to apply the script to using select all or clicking on the checkbox to the left of each target to apply the script to only select targets. 4. Click apply scripts. Once the script is a...
Page 294
Chapter 13: kx ii local console 283 for example, select f1-f16 to display the function key set in the add box. Select a function key and add it to the script box. Next, select letters from the key set drop-down and add a letter key to the script. 8. Optionally, add text that will display when the sc...
Page 295
Chapter 13: kx ii local console 284.
Page 296
Chapter 13: kx ii local console 285 modifying scripts to modify existing scripts: 1. Click device settings > connection scripts. The connection scripts page opens. 2. In the available connection scripts section, select the script you want to modify and click modify. The page is then in edit mode. 3....
Page 297
Chapter 13: kx ii local console 286 4. Continue holding the reset button for 10 seconds. Once the device has been reset, two short beeps signal its completion..
Page 298
287 in this chapter hardware ............................................................................................... 287 software................................................................................................. 311 hardware kx ii physical specifications dkx2-832 - dual power ...
Page 299
Appendix a: specifications 288 dominion kx ii model description dimensions (wxdxh) weight power and heat dissipation remote users, 1 local port for use at the rack 1.75"; 439 x 290 x 44mm 4.1kg 47/63hz 1a 63w 54 kcal dkx2-232 32 server ports, 2 remote users, 1 local port for use at the rack 17.3" x ...
Page 300
Appendix a: specifications 289 specifications for all dominion kx ii models local port access video hd15(f) vga keyboard/mouse usb(f), 1 usb front, 3 usb rear warranty two years standard with advanced replacement* supported target server video resolution/refresh rate/connection distance the maximum ...
Page 301
Appendix a: specifications 290 cim model description dimensions (wxdxh) weight d2cim-vusb usb cim for virtual media and absolute mouse synchronization 1.3" x 3.0" x 0.6"; 33 x 76 x 15mm 0.20lb; 0.09kg dcim-ps2 cim for ps/2 1.3" x 3.0" x 0.6"; 33 x 76 x 15mm 0.20lb; 0.09kg dcim-sun cim for sun 1.3" x...
Page 302
Appendix a: specifications 291 cim model description dimensions (wxdxh) weight p2cim-ser paragon ii/dominion kx ii cim for serial (ascii) devices 1.3" x 3.0" x 0.6"; 33 x 76 x 15mm 0.20lb; 0.09kg d2cim-dvusb- dvi digital cim that provides digital-to-analog conversion and support for virtual media, s...
Page 303
Appendix a: specifications 292 cim model description dimensions (wxdxh) weight d2cim-dvusb- dp digital cim that provides digital-to-analog conversion and support for virtual media, smartcard/cac, audio, absolute and relative mouse synchronization 1.7" x 3.5" x 0.8"; 43 x 90 x 19mm 0.25lb; 0.11kg d2c...
Page 304
Appendix a: specifications 293 digital cim timing modes following are the default timing modes that are used when the kx ii communicates with a video source via a digital cim. The timing mode that is used is dependent on the native resolution of the video source. 1920x1080@60hz 1600x1200@60hz 1280x1...
Page 305
Appendix a: specifications 294 digital cim established and standard modes the following additional established and standard resolutions and timing modes are supported by the kx ii 2.5.0 (and later). Established modes 720x400@70hz ibm, vga 640x480@60hz ibm, vga 640x480@67hz apple mac ® ii 640x480@72h...
Page 306
Appendix a: specifications 295 digital cim display native resolution you are able to select the native resolution of the cim on the port configuration page from the display native resolution drop-down. This is the preferred resolution and timing mode of the digital cim. Once a resolution is selected...
Page 307
Appendix a: specifications 296 supported paragon ii cims and configurations the kx ii supports the p2cim-aps2dual and p2cim-ausbdual cims, which provide two rj45 connections to different kvm switches. Support of these cims provides a second path to access the target in the event that one of the kvm ...
Page 308
Appendix a: specifications 297 kx ii-to-kx ii paragon cim guidelines the following system configuration guidelines should be followed when you are using paragon cims in a kx ii-to-kx ii configuration: concurrent access both kx ii kvm switches should be configured with the same policy for concurrent ...
Page 309
Appendix a: specifications 298 if a connection to the target is in place from the other kx ii, the availability is checked when a connection is attempted. Access is denied or allowed consistent with the pc-share policy in place for the kx ii. Until that time, the availability is not be updated on th...
Page 310
Appendix a: specifications 299 paragon ii operation mode mode description supported? Port can be selected and controlled by more than one user, but only one user has keyboard and mouse control at any one time. Timeout, which is configured on the paragon ii, is not supported. Both users will have con...
Page 311
Appendix a: specifications 300 supported remote connections remote connection details network 10base-t, 100base-t, and 1000base-t (gigabit) ethernet protocols tcp/ip, udp, sntp, http, https, radius, ldap/ldaps network speed settings kx ii network speed setting network switch port setting auto 1000/f...
Page 312
Appendix a: specifications 301 legend: does not function as expected supported functions; not recommended not supported by ethernet specification; product will communicate, but collisions will occur per ethernet specification, these should be “no communication,” however, note that the kx ii behavior...
Page 313
Appendix a: specifications 302 target server requirements when using smart card readers, the basic requirements for interoperability at the target server are: the ifd (smart card reader) handler must be a standard usb ccid device driver (comparable to the generic microsoft ® usb ccid driver). A digi...
Page 314
Appendix a: specifications 303 remote client requirements the basic requirements for interoperability at the remote client are: the ifd (smart card reader) handler must be a pc/sc compliant device driver. The icc (smart card) resource manager must be available and be pc/sc compliant. The jre ® java ...
Page 315
Appendix a: specifications 304 type vendor model verified usb scm microsystems scr331 verified on local and remote usb actividentity ® actividentity usb reader v2.0 verified on local and remote usb actividentity actividentity usb reader v3.0 verified on local and remote usb gemalto ® gempc usb-sw ve...
Page 316
Appendix a: specifications 305 supported audio device formats the kx ii supports one playback and capture device and one record device on a target at a time. The following audio device formats are supported: stereo, 16 bit, 44.1k mono, 16 bit, 44.1k stereo, 16 bit, 22.05k mono, 16 bit, 22.05k stereo...
Page 317
Appendix a: specifications 306 bandwidth requirements the table below details the audio playback and capture bandwidth requirements to transport audio under each of the selected formats. Audio format network bandwidth requirement 44.1 khz, 16bit stereo 176 kb/s 44.1 khz, 16bit mono 88.2 kb/s 2.05 kh...
Page 318
Appendix a: specifications 307 audio in a mac environment following are known issues in a mac ® environment. On mac clients, only one playback device is listed on the connect audio panel when accessing the device through the virtual kvm client (vkc) and multi-platform client (mpc). The device listed...
Page 319
Appendix a: specifications 308 kx2 8xx extended local port recommended maximum distances extended device 1024x768, 60 hz 1280x1024, 60 hz paragon ii umt using eust 1000 900 paragon eust 500 400 urkvm 650 250 paragon ust 500 200 mac mini bios keystroke commands the following bios commands have been t...
Page 320
Appendix a: specifications 309 keystroke description virtual media cim dual virtual media cim mac lion server hdmi cim press n during startup start up from a compatible network server (netboot) press t during startup start up in target disk mode press shift during startup start up in safe boot mode ...
Page 321
Appendix a: specifications 310 port description by default, this port is used for multiple purposes, including the web server for the html client, the download of client software (multi-platform client (mpc) and virtual kvm client (vkc)) onto the client's host, and the transfer of kvm and virtual me...
Page 322
Appendix a: specifications 311 software supported operating systems (clients) the following operating systems are supported on the virtual kvm client (vkc) and multi-platform client (mpc). Windows 7 ® windows xp ® windows 2008 ® windows vista ® windows 2000 ® sp4 server windows 2003 ® server windows...
Page 323
Appendix a: specifications 312 linux ® the jre ™ plug-in is available for the windows ® 32-bit and 64-bit operating systems. Mpc and vkc can be launched only from a 32-bit browser, or 64-bit browser. Following are the java ™ 32-bit and 64-bit windows operating system requirements. Mode operating sys...
Page 324
Appendix a: specifications 313 mac os x mountain lion 10.8.5 * using safari 6.1.1 running jre 1.7.0_51 *note: upon upgrading from os x 10.8.2 to os x 10.8.3, safari ® may block java ™ . Jre requirements and browser considerations for mac java runtime environment requirements for mac install java r...
Page 325
Appendix a: specifications 314 resolutions 640x480 @72hz 1152x864 @85hz 640x480 @75hz 1152x870 @75.1hz 640x480 @85hz 1152x900 @66hz 720x400 @70hz 1152x900 @76hz 720x400 @84hz 1280x720@60hz 720x400 @85hz 1280x960 @60hz 800x600 @56hz 1280x960 @85hz 800x600 @60hz 1280x1024 @60hz 800x600 @70hz 1280x1024...
Page 326
Appendix a: specifications 315 video image appears dark when using a mac if you are using a mac ® with an hdmi video port and the video seems too dark, enable dvi compatibility mode on the cim to help resolve the issue. See configuring cim ports (on page 176) kx ii supported keyboard languages the k...
Page 327
Appendix a: specifications 316 language regions keyboard layout danish denmark danish swedish sweden swedish hungarian hungary hungarian slovenian slovenia slovenian italian italy italian spanish spain and most spanish speaking countries spanish portuguese portugal portuguese events captured in the ...
Page 328
317 in this chapter overview ................................................................................................ 317 recommendations for dual port video ................................................. 318 dual video port group supported mouse modes ................................. 31...
Page 329
Appendix b: dual video port groups 318 recommendations for dual port video set the target server’s primary and secondary displays to the same video resolution in order to maintain mouse synchronization and minimize having to periodically resync. Depending on the desired orientation, the top display ...
Page 330
Appendix b: dual video port groups 319 target operating systems supported mouse modes comments mouse mode is recommended. Linux ® intelligent and standard mouse modes linux ® users may experience display and mouse movement issues using single mouse mode. Raritan recommends linux users do not use sin...
Page 331
Appendix b: dual video port groups 320 monitor settings will not be applied. Instead the port group management configured 'display orientation' will be applied. other - enable single mouse cursor setting will not be applied other - enable scale video setting will be applied other - pin menu ...
Page 332
Appendix b: dual video port groups 321 example dual port video group configuration the following is a general example. Your configuration may vary in the type of cims used, the port you designate as the primary port, the ports you are connecting to and so on. In this example, we are using: a target ...
Page 333
Appendix b: dual video port groups 322 diagram key connection from the target's primary (first) video port to the kx ii connection from the target's secondary (second) video port to the kx ii ip connection between the kx ii and remote client target server - configure the display settings and launch ...
Page 334
Appendix b: dual video port groups 323 note: if the target primary and secondary displays are set to different resolutions the mouse will not stay in sync and will need to be periodically re-synced from the top-left target window. Step 2: connect the target server to the kx iii dual port video group...
Page 335
Appendix b: dual video port groups 324 step 3: configure the mouse mode and ports once you have connected the target server to the raritan device through the target server video ports, it detects the connection and displays the ports on the port configuration page. For instructions, see configuring ...
Page 336
Appendix b: dual video port groups 325 step 5: launch a dual port video group once you have created the dual video port group, it is available on the port access page. Two kvm channels are required to remotely connect to the dual video port group by clicking primary port. If two channels are not ava...
Page 337
Appendix b: dual video port groups 326 direct port access and dual port video groups direct port access allows users to bypass having to use the device's login dialog and port access page. This feature also provides the ability to enter a username and password directly to proceed to the target, if t...
Page 338
327 in this chapter overview ................................................................................................ 327 connecting the paragon ii to the kx ii .................................................. 328 overview connect the paragon ii system to a kx ii device that is managed by ...
Page 339
Appendix c: accessing a px2 from the kx ii 328 when you access the paragon ii system from kx ii or cc-sg (if the kx ii is managed by cc-sg), the paragon ii osui login screen appears for you to log in. In this integration, you can perform any osui functions implemented with current paragon ii firmwar...
Page 340
Appendix c: accessing a px2 from the kx ii 329.
Page 341
330 note: the procedures in this chapter should be attempted only by experienced users. In this chapter returning user group information ........................................................ 330 setting the registry to permit write operations to the schema ........... 331 creating a new attribute...
Page 342
Appendix d: updating the ldap schema 331 setting the registry to permit write operations to the schema to allow a domain controller to write to the schema, you must set a registry entry that permits schema updates. To permit write operations to the schema: 1. Right-click the active directory ® schem...
Page 343
Appendix d: updating the ldap schema 332 3. Click new and then choose attribute. When the warning message appears, click continue and the create new attribute dialog appears. 4. Type rciusergroup in the common name field. 5. Type rciusergroup in the ldap display name field. 6. Type 1.3.6.1.4.1.13742...
Page 344
Appendix d: updating the ldap schema 333 2. Scroll to the user class in the right pane and right-click it. 3. Choose properties from the menu. The user properties dialog appears. 4. Click the attributes tab to open it. 5. Click add..
Page 345
Appendix d: updating the ldap schema 334 6. Choose rciusergroup from the select schema object list. 7. Click ok in the select schema object dialog. 8. Click ok in the user properties dialog. Updating the schema cache to update the schema cache: 1. Right-click active directory ® schema in the left pa...
Page 346
Appendix d: updating the ldap schema 335 3. Go to the directory where the support tools were installed. Run adsiedit.Msc. The adsi edit window opens. 4. Open the domain. 5. In the left pane of the window, select the cn=users folder..
Page 347
Appendix d: updating the ldap schema 336 6. Locate the user name whose properties you want to adjust in the right pane. Right-click the user name and select properties. 7. Click the attribute editor tab if it is not already open. Choose rciusergroup from the attributes list. 8. Click edit. The strin...
Page 348
337 in this chapter overview ................................................................................................ 337 java runtime environment (jre) notes ............................................... 337 ipv6 support notes .................................................................
Page 349
Appendix e: informational notes 338 java not loading properly on mac if you are using a mac ® and see the following message when connecting to a device from the kx ii port access table, java ™ is not loaded properly: "error while getting the list of open targets, please try again in a few seconds". ...
Page 350
Appendix e: informational notes 339 ipv6 support notes operating system ipv6 support notes java java ™ 1.7 supports ipv6 for the following: solaris ™ 10 (and later) linux ® kernel 2.1.2 (and later)/redhat 6.1 (and later) solaris 10 (and later) windows xp ® sp1 and windows 2003 ® , windows vista ® an...
Page 351
Appendix e: informational notes 340 dual stack login performance issues if you are using the kx ii in a dual stack configuration, it is important you configured the domain system (dns) correctly in the kx ii in order to avoid delays when logging in. See tips for adding a web browser interface (on pa...
Page 352
Appendix e: informational notes 341 windows 2000 composite usb device behavior for virtual media the windows 2000 ® operating system does not support usb composite devices, like raritan’s d2cim-vusb, in the same manner as non-composite usb devices. As a result, the “safely remove hardware” system tr...
Page 353
Appendix e: informational notes 342 cannot write to/from a file from a mac client if you are connecting to the kx ii from a mac ® 10.8.5 client running safari ® 6.1 with java ™ 1.7 and cannot write to/from a file on a target server or access virtual media, do the following to correct this: 1. In saf...
Page 354
Appendix e: informational notes 343 virtual media via vkc and akc in a windows environment windows xp ® operating system administrator and standard user privileges vary from those of the windows vista ® operating system and the windows 7 ® operating system. When enabled in vista or windows 7, user a...
Page 355
Appendix e: informational notes 344 virtual media linux drive listed twice for kx ii 2.4.0 (and later) and lx 2.4.5 (and later), users who are logged in to linux ™ clients as root users, the drives are listed twice in the local drive drop-down. For example, you will see eg /dev/sdc and eg /dev/sdc1 ...
Page 356
Appendix e: informational notes 345 usb port and profile notes vm-cims and dl360 usb ports hp ® dl360 servers have one usb port on the back of the device and another on the front of the device. With the dl360, both ports cannot be used at the same time. Therefore, a dual vm-cim cannot be used on dl3...
Page 357
Appendix e: informational notes 346 usb profile help appears in the usb profile help window. For detailed information about specific usb profiles, see available usb profiles (on page 109). Raritan provides a standard selection of usb configuration profiles for a wide range of operating system and bi...
Page 358
Appendix e: informational notes 347 changing a usb profile when using a smart card reader there may be certain circumstances under which you will need to change the usb profile for a target server. For example, you may need to change the connection speed to "use full speed for virtual media cim" whe...
Page 359
Appendix e: informational notes 348 note: these procedures do not apply to the circumflex accent (above vowels). In all cases, the ^ key (to the right of the p key) works on french keyboards to create the circumflex accent when used in combination with another character. Accent symbol (windows xp ® ...
Page 360
Appendix e: informational notes 349 keyboard language preference (fedora linux clients) because the sun ™ jre ™ on linux ® has problems generating the correct keyevents for foreign-language keyboards configured using system preferences, raritan recommends that you configure foreign keyboards using t...
Page 361
Appendix e: informational notes 350 4. Click close. To set the keyboard language using the keyboard indicator: 1. Right-click the task bar and choose add to panel. 2. In the add to panel dialog, right-click the keyboard indicator and from the menu choose open keyboard preferences. 3. In the keyboard...
Page 362
Appendix e: informational notes 351 3. Restart the x server. With this change, the internal video mode timing from the x server is used and corresponds exactly with the vesa video mode timing, resulting in the proper video display on the kx ii. List of supported target video resolutions not displayi...
Page 363
Appendix e: informational notes 352 audio in a linux environment the following are known issues when using the audio feature in a linux ® environment. Linux ® users, use the default audio device for playback. Sound may not come through if a non-default sound card is selected. Suse 11 clients require...
Page 364
Appendix e: informational notes 353 proxy mode and mpc if you are using kx ii in a cc-sg configuration, do not use the cc-sg proxy mode if you are planning to use the multi-platform client (mpc). Moving between ports on a device if you move a between ports on the same raritan device and resume manag...
Page 365
Appendix e: informational notes 354 vkc and mpc smart card connections to fedora servers if you are using a smart card to connect to a linux ® fedora ® server via multi-platform client (mpc) and virtual kvm client (vkc) upgrade the pcsc-lite library to 1.4.102-3 or above. Note: this feature is avail...
Page 366
355 in this chapter general faqs ........................................................................................ 355 remote access ..................................................................................... 356 universal virtual media .................................................
Page 367
Appendix f: frequently asked questions 356 question answer how does dominion kx ii differ from remote control software? When using dominion kx ii remotely, the interface, at first glance, may seem similar to remote control software such as pcanywheretm, windows® terminal services/remote desktop, vnc...
Page 368
Appendix f: frequently asked questions 357 question answer how many users can remotely access servers on each dominion kx ii? Dominion kx ii models offer remote connections for up to eight users per user channel to simultaneously access and control a unique target server. For one-channel devices lik...
Page 369
Appendix f: frequently asked questions 358 question answer do you have a non-windows kvm client? Yes. Both the virtual kvm client (vkc) and the multiplatform client (mpc) allow non-windows users to connect to target servers in the data center. Mpc can be run via web browsers and stand-alone and can ...
Page 370
Appendix f: frequently asked questions 359 question answer what is the file size of the applet that’s used to access dominion kx ii? How long does it take to retrieve? The virtual kvm client (vkc) applet used to access dominion kx ii is approximately 500kb in size. The following chart describes the ...
Page 371
Appendix f: frequently asked questions 360 question answer what is required for virtual media? A dominion kx ii virtual media cim is required: a digital cim, d2cim-vusb or d2cim-dvusb. The d2cim-vusb has a single usb connector and is for customers who will use virtual media at the os level. The d2ci...
Page 372
Appendix f: frequently asked questions 361 question answer why would i use a usb profile? Usb profiles are most often required at the bios level where there may not be full support for the usb specification when accessing virtual media drives. However, profiles are sometimes used at the os level, fo...
Page 373
Appendix f: frequently asked questions 362 question answer how is bandwidth used in kvm-over-ip systems? Dominion kx ii offers next-generation kvm-over-ip technology – the very best video compression available. Raritan has received numerous technical awards, confirming its high video quality transmi...
Page 374
Appendix f: frequently asked questions 363 question answer what factors affect bandwidth? There are many factors that determine how much bandwidth will be used. The primary factor, noted above, is the amount of change in the target server’s video display. This is dependent on the user’s task and act...
Page 375
Appendix f: frequently asked questions 364 question answer how can i reduce bandwidth? Kx ii provides a variety of settings in our remote clients for the user to optimize bandwidth and performance. The default settings will provide an at-the-rack level of performance in standard lan/wan environments...
Page 376
Appendix f: frequently asked questions 365 question answer what should i do on slower bandwidth links? The connection speed and color depth settings can be tweaked to optimize performance for slower bandwidth links. For example, in the multiplatform client or the virtual kvm client, set the connecti...
Page 377
Appendix f: frequently asked questions 366 question answer what about servers with dvi ports? Servers with dvi ports that support dvi-a (analog) and dvi-i (integrated analog and digital) can use raritan’s advi-vga inexpensive, passive adapter to convert the server’s dvi port to a vga plug that can b...
Page 378
Appendix f: frequently asked questions 367 user task default 1mb speed and 15-bit color 1mb speed and 8-bit color open text window 50 – 100 kb/s 25 – 50 kb/s 10 – 15 kb/s continuous typing 1 kb/s .5 – 1 kb/s .2 – .5 kb/s scroll text window 1050 kb/s 5 – 25 kb/s 2 – 10 kb/s close text window 50 – 100...
Page 379
Appendix f: frequently asked questions 368 question answer what is the speed of dominion kx ii’s ethernet interfaces? Dominion kx ii supports gigabit as well as 10/100 ethernet. Kx ii supports two 10/100/1000 speed ethernet interfaces, with configurable speed and duplex settings (either auto detecte...
Page 380
Appendix f: 369 question answer can the dominion kx ii use dhcp? Dhcp addressing can be used; however, raritan recommends fixed addressing since the dominion kx ii is an infrastructure device and can be accessed and administered more effectively with a fixed ip address. I’m having problems connectin...
Page 381
Appendix f: 370 question answer what is ipv6? Ipv6 is the acronym for internet protocol version 6. Ipv6 is the "next generation" ip protocol which will replace the current ip version 4 (ipv4) protocol. Ipv6 addresses a number of problems in ipv4, such as the limited number of ipv4 addresses. It also...
Page 382
Appendix f: 371 question answer what if my network doesn’t support ipv6? The dominion kx ii’s default networking is set at the factory for ipv4 only. When you are ready to use ipv6, then follow the above instructions to enable ipv4/ipv6 dual-stack operation. Where can i get more information on ipv6?...
Page 383
Appendix f: 372 question answer what about mouse synchronization? In the past, kvm-over-ip mouse synchronization was a frustrating experience. The dominion kx ii’s absolute mouse synchronization provides for a tightly synchronized mouse without requiring server mouse setting changes on windows and a...
Page 384
Appendix f: 373 question answer do i have to use hotkeys to switch between blades? Some blade servers require you to use hotkeys to switch between blades. With the dominion kx ii, you don’t have to use these hotkeys. Just click on the name of the blade server, and the dominion kx ii will automatical...
Page 385
Appendix f: 374 question answer is virtual media supported? This depends on the blade server. Hp blades can support virtual media. The ibm bladecenter (except for bladecenter t) supports virtual media if configured appropriately. A virtual media cim – d2cim-vusb or d2cim-dvusb – must be used. Is abs...
Page 386
Appendix f: 375 question answer how do i connect servers to dominion kx ii? Servers that connect to the dominion kx ii require a dominion or paragon cim, which connects directly to the keyboard, video and mouse ports of the server. Then, connect each cim to dominion kx ii using standard utp (unshiel...
Page 387
Appendix f: 376 question answer how do i connect a serially controlled (rs-232) device, such as a cisco router/switch or a headless sun server, to dominion kx ii? If there are only a few serially controlled devices, they may be connected to a dominion kx ii using raritan’s p2cim-ser serial converter...
Page 388
Appendix f: 377 question answer when i am using the local port, do i prevent other users from accessing servers remotely? No. The dominion kx ii local port has a completely independent access path to the servers. This means a user can access servers locally at the rack – without compromising the num...
Page 389
Appendix f: 378 question answer if i use the local port to change the name of a connected server, does this change propagate to remote access clients as well? Does it propagate to the optional commandcenter appliance? Yes. The local port presentation is identical and completely in sync with remote a...
Page 390
Appendix f: 379 question answer must i use the extended local port? No. The extended local port is an optional feature and is disabled by default. Use the "local port settings" page to enable it. You can also disable the standard local port if you are not going to use it for added security. Dual pow...
Page 391
Appendix f: 380 question answer how do i connect the pdu to the dominion kx ii? The d2cim-pwr is used to connect the power strip to the dominion kx ii. The d2cim-pwr must be purchased separately; it does not come with the pdu. Does dominion kx ii support servers with multiple power supplies? Yes. Do...
Page 392
Appendix f: 381 question answer how do i physically connect multiple dominion kx ii devices together into one solution? To physically connect multiple kx ii devices together for consolidated local access, you can connect the local ports of multiple "tiered" (or "cascaded") kx ii switches to a "base"...
Page 393
Appendix f: 382 question answer do i have to physically connect dominion kx ii devices together? Multiple dominion kx ii units do not need to be physically connected together. Instead, each dominion kx ii unit connects to the network, and they automatically work together as a single solution i f dep...
Page 394
Appendix f: 383 computer interface modules (cims) question answer what type of video is supported by your cims? Our cims have traditionally supported analog vga video. Three new cims support digital video formats, including dvi, hdmi and displayport. These are the d2cim-dvusb-dvi, d2cim-dvusb-hdmi a...
Page 395
Appendix f: 384 question answer does dominion kx ii support paragon dual cims? Yes. The dominion kx ii now supports paragon ii dual cims (p2cim-aps2dual and p2cim-ausbdual), which can connect servers in the data center to two different dominion kx ii switches. If one kx ii switch is not available, t...
Page 396
Appendix f: 385 question answer does dominion kx ii allow encryption of video data? Or does it only encrypt keyboard and mouse data? Unlike competing solutions, which only encrypt keyboard and mouse data, dominion kx ii does not compromise security – it allows encryption of keyboard, mouse, video an...
Page 397
Appendix f: 386 smart cards and cac authentication question answer does dominion kx ii support smart card and cac authentication? Yes. Smart cards and dod common access cards (cac) authentication to target servers is supported by release 2.1.10 and greater. What is cac? Mandated by homeland security...
Page 398
Appendix f: 387 question answer can dominion kx ii be remotely managed and configured via web browser? Yes. Dominion kx ii can be completely configured remotely via web browser. Note that this does require that the workstation have an appropriate java runtime environment (jre) version installed. Bes...
Page 399
Appendix f: 388 documentation and support question answer where do i find documentation on the dominion kx ii? The documentation is available at raritan.Com on the kx ii firmware and documentation page: http://www.Raritan.Com/support/dominion-kx-ii. The documentation is listed by firmware release. W...
Page 400
Appendix f: 389 question answer i changed and subsequently forgot dominion kx ii’s administrative password; can you retrieve it for me? Dominion kx ii contains a hardware reset button that can be used to factory reset the device, which will reset the administrative password on the device to the defa...
Page 401: Index
391 a a. Ac power • 16 about the active kvm client • 92 absolute mouse mode • 74 access a virtual media drive on a client compu ter • 100 access and control target servers remotely • 23 access and copy connection information • 56 access and display favorites • 45 accessing a px2 from the kx ii • 326...
Page 402
Index 392 cims required for virtual media • 97 cisco acs 5.X for radius authentication • 136 cli commands • 257, 262 cli prompts • 262 cli syntax - tips and shortcuts • 260 client launch settings • 78 command line interface (cli) • 257 common commands for all command line interface levels • 260 comp...
Page 403
Index 393 disconnecting users from ports • 126, 127 discovering devices on the kx ii subnet • 46 discovering devices on the local subnet • 45 documentation and support • 386 drive partitions • 103 dual port video configuration steps • 316, 321 dual port vide o group usability notes • 318 dual port v...
Page 404
Index 394 java validation and access warning • 27 jre requirements and browser considerations for mac • 312 k keyboard language preference (fedora linux clients) • 347 ke yboard limitations • 77 keyboard macros • 60 keyboard notes • 345 keyboard options • 60 kx ii client applications • 9 kx ii conso...
Page 405
Index 395 o operating system ipv6 sup port notes • 337 overview • 10, 52, 105, 108, 257, 266, 316, 326, 335 p package contents • 4 permissions and dual video port group access • 219, 319 ping host page • 253 port access page (local console server display) • 268 port access page (remote console displ...
Page 406
Index 396 ssh access from a windows pc • 258 ssh connection to the kx ii • 258 ssl ce rtificates • 27, 234 standard mouse mode • 72 step 1 configure the target server display • 321 configuring network firewall settings • 12 step 2 configure the kvm target servers • 13 connect the target server to th...
Page 407
Index 397 v version information - virtual kvm client • 91 video image appears dark when using a mac • 313 video mode and resolution notes • 348 video properties • 66 view by group tab • 40 view by search tab • 40 view options • 79 view status bar • 80 view the kx ii users list • 126 view toolbar • 7...
Page 408
U.S./canada/latin america monday - friday 8 a.M. - 6 p.M. Et phone: 800-724-8090 or 732-764-8886 for commandcenter noc: press 6, then press 1 for commandcenter secure gateway: press 6, then press 2 fax: 732-764-8887 email for commandcenter noc: tech-ccnoc@raritan.Com email for all other products: te...