- DL manuals
- Raritan
- Switch
- Dominion KX III
- Administrator's Manual
Raritan Dominion KX III Administrator's Manual
Summary of Dominion KX III
Page 1
Copyright © 2015 raritan, inc. Dkx3a-v3.1.2-0e-e april 2015 255-62-0002-00 dominion kx iii administrators guide release 3.1.2.
Page 2
This document contains proprietary information that is protected by copyright. All rights reserved. No part of this document may be photocopied, reproduced, or translated into another language without express prior written consent of raritan, inc. © copyright 2015 raritan, inc. All third-party softw...
Page 3
Iii contents chapter 1 introduction 1 overview ........................................................................................................................................ 1 what's new in help ..................................................................................................
Page 4
Contents iv step 7: create and install an ssl certificate .................................................................... 41 rack pdu (power strip) outlet control ....................................................................................... 41 overview ...................................
Page 5
Contents v ssh connection to the kx iii .......................................................................................... 215 logging in ........................................................................................................................ 216 navigation of the cli ..........
Page 6
Contents vi root user permission requirement ................................................................................ 246 virtual media in a mac environment .......................................................................................... 246 active system partition ...................
Page 7
Contents vii scaling ............................................................................................................................. 279 full screen mode............................................................................................................. 280 connect to virtual ...
Page 8
Contents viii proxy server configuration for use with virtual kvm client (vkc) and active kvm client (akc) ......................................................................................................................................... 296 connect to a target from virtual kvm client (vkc) o...
Page 9
Contents ix chapter 9 kx iii local console 319 overview .................................................................................................................................... 319 accessing a target server ....................................................................................
Page 10
Contents x build data and power circuits for the kx iii .............................................................................. 347 submit an add item request for the kx iii ................................................................................ 347 manage the kx iii work order ........
Page 11
Contents xi ipv6 support notes .................................................................................................................... 379 operating system ipv6 support notes ........................................................................... 379 akc download server certificatio...
Page 12
Contents xii appendix f frequently asked questions 395 general faqs ............................................................................................................................ 395 remote access ............................................................................................
Page 13: Introduction
1 in this chapter overview .................................................................................................... 1 what's new in help ................................................................................... 1 package contents ...................................................
Page 14
Chapter 1: introduction 2 restore kx ii backup file to a kx iii to help customers migrating from the previous generation kx ii to kx iii, the kx iii can restore (i.E. Import) a backup file exported from the kx ii to populate many of the kx iii’s settings and options - applying kx ii appliance settin...
Page 15
Chapter 1: introduction 3 dvi support via a standard dvi cable remote access and power management from an iphone ® or ipad ® support for tiering in which a base kx iii device is used to access multiple other tiered devices multiple user capacity (1/2/4/8 remote users; 1 local user) utp (cat5/5e/6)...
Page 16
Chapter 1: introduction 4 support for digital audio over usb port scanning and thumbnail view of up to 32 targets within a configurable scan set web-based access and management intuitive graphical user interface (gui) support for dual port video output 256-bit encryption of complete kvm signal, incl...
Page 17
Chapter 1: introduction 5 diagram key dual power ac 100v/240v dual 10/100/1000 ethernet access local usb ports dvi-d port 32 kvm ports for utp cabling (cat5/5e/6) tier port for tiering devices modem port for external modems.
Page 18
Chapter 1: introduction 6 dominion kx3-864 kx3-864 photos kx3-864 features diagram key dual power ac 100v/240v dual 10/100/1000 ethernet access local usb ports dvi-d port 64 kvm ports for utp cabling (cat5/5e/6) tier port for optional tiering devices.
Page 19
Chapter 1: introduction 7 diagram key modem port for optional external modems supported users and ports per model model ports remote users kx3-864 64 8 kx3-832 32 8 kx3-808 8 8 kx3-464 64 4 kx3-432 32 4 kx3-416 16 4 kx3-232 32 2 kx3-216 16 2 kx3-132 32 1 kx3-116 16 1 kx3-108 8 1 kx iii remote and lo...
Page 20
Chapter 1: introduction 8 kx iii kvm client applications kx iii works with the virtual kvm client (vkc) and the active kvm client (akc). Java ™ 1.7 is required to use the java-based virtual kvm client (vkc). Microsoft .Net ® 3.5 (or later) is required to use kx iii with the microsoft windows ® -base...
Page 21: Getting Started
9 in this chapter install and configure kx iii ........................................................................ 9 allow pop-ups ........................................................................................... 9 security warnings and validation messages ...............................
Page 22
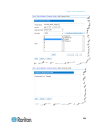
Chapter 2: getting started 10 java validation and access warning when logging in to kx iii, java ™ 1.7 prompts you to validate kx iii, and to allow access to the application. Raritan recommends installing an ssl certificate in each kx iii device in order to reduce java warnings, and enhance security...
Page 23
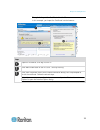
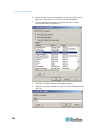
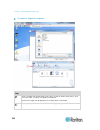
Chapter 2: getting started 11 example 1: import the certificate into the browser in this example, you import the certificate into the browser. Steps open an ie browser, then log in to kx iii. Click more information on the first java ™ security warning. Click view certificate details on the more info...
Page 24
Chapter 2: getting started 12 steps click the content tab. Click certificates. The certificate import wizard opens and walks you through each step. file to import - browse to locate the certificate certificate store - select the location to store the certificate click finish on the last step of ...
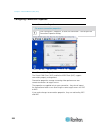
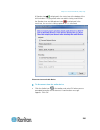
Page 25
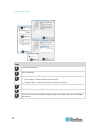
Chapter 2: getting started 13 example 2: add the kx iii to trusted sites and import the certificate in this example, the kx iii's url is added as a trusted site, and the self signed certificate is added as part of the process. Steps open an ie browser, then select tools > internet options to open th...
Page 26
Chapter 2: getting started 14 steps open an ie browser, then log in to kx iii. Click more information on the first java ™ security warning. Click view certificate details on the more information dialog. You are prompted to install the certificate. Follow the wizard steps. For details see, example 1:...
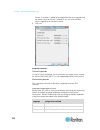
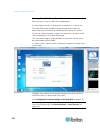
Page 27
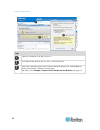
Chapter 2: getting started 15 converting a binary certificate to a base64-encoded der certificate (optional) kx iii requires an ssl certificate in either base64-encoded der format or pem format. If you are using an ssl certificate in binary format, you cannot install it. However, you can convert you...
Page 28
Chapter 2: getting started 16 4 the certificate export wizard opens. Click next to start the wizard. 5 select "base-64 encoded x.509" in the second wizard dialog. 6 click next to save the file as a base-64 encoded x.509. You can now install the certificate on your kx iii..
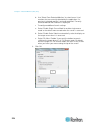
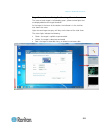
Page 29
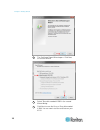
Chapter 2: getting started 17 logging in to the kx iii log in to your kx iii remote console from any workstation with network connectivity. Java ™ 1.7 is required to use the java-based virtual kvm client (vkc). Alternatively, microsoft .Net ® 3.5 (or later) is required to use kx iii with the microso...
Page 30: Kx Iii Administration
18 in this chapter overview .................................................................................................. 18 kx iii installation and configuration ........................................................ 19 rack pdu (power strip) outlet control .....................................
Page 31
Chapter 3: kx iii administration 19 kx iii installation and configuration see the kx iii quick setup guide that came with your device or download it from raritan's support website for a quick reference to the basic, bear minimum setup steps. Additional information and optional steps included here bu...
Page 32
Chapter 3: kx iii administration 20 rear mount the steps correspond to the numbers shown in the rear rackmount diagrams. 1. Secure the cable-support bar to the front end of the side brackets, near the side brackets' “ears,” using two of the included screws. 2. Slide the kx iii between the side brack...
Page 33
Chapter 3: kx iii administration 21 setting value (all lowercase) this user has administrative privileges. Password raritan (all lowercase) the first time you start the kx iii, you are required to change the default password. Ip address 192.168.0.192 important: for backup and business continuity pur...
Page 34
Chapter 3: kx iii administration 22 mouse settings raritan recommends using absolute mouse synchronization to minimize mouse settings on target servers. Additional supported mouse settings (on page 22). In this mode, absolute coordinates are used to keep the client and target cursors in synch, even ...
Page 35
Chapter 3: kx iii administration 23 windows xp, windows 2003, windows 2008 mouse settings configure these mouse settings in windows xp ® , windows 2003 ® and windows 2008 ® : configure the motion settings: set the mouse motion speed setting to exactly the middle speed disable the "enhance pointer pr...
Page 36
Chapter 3: kx iii administration 24 5. Select 'mac os-x (10.4.9) and later' from the available box, then click add to add it to the selected box. 6. Click on 'mac os-x (10.4.9) and later' in the selected box. This automatically adds it to the preferred profile drop-down. 7. Select 'mac os-x (10.4.9)...
Page 37
Chapter 3: kx iii administration 25 a. Ac power 1 use the power cords that came with the kx iii. Attach the female end of the ac power cord to an kx iii power port and plug the male end into an ac power outlet. 2 for dual-power failover protection, plug the female end of the second ac power cord in ...
Page 38
Chapter 3: kx iii administration 26 b. Network port the kx iii provides two ethernet ports for failover purposes - not for load-balancing. By default, only lan1 is active and the automatic failover is disabled. When you enable network failover, lan2 uses the same ip address if the kx iii internal ne...
Page 39
Chapter 3: kx iii administration 27 connect to a dvi monitor the local monitor must support a minimum 1024x768 resolution. To connect to a dvi monitor: 1 connect a usb keyboard and mouse to the respective local user ports on the back of the kx iii device. 2 connect one end of a dvi cable into the dv...
Page 40
Chapter 3: kx iii administration 28 g. Connect the modem (optional) see configuring modem settings (on page 147) step 4: configuring the kx iii for the following steps, you must change the default password and assign the kx iii its ip address at the local console. All other steps can be performed ei...
Page 41
Chapter 3: kx iii administration 29 assign the kx iii a device name choose device settings > network. The basic network settings page opens. 1 specify a meaningful device name for your kx iii device. Up to 32 alphanumeric and valid special characters, no spaces between characters. Next, configure th...
Page 42
Chapter 3: kx iii administration 30 3 set up your ip auto configuration by selecting - none or dhcp a none - for a static ip. Default selection. Recommended option. If none is selected, you must manually specify the network parameters by entering the default gateway. Leaving the selection set to non...
Page 43
Chapter 3: kx iii administration 31 b dhcp - with this option, the ip address is automatically assigned by a dhcp server. Dynamic host configuration protocol is used by networked computers (clients) to obtain unique ip addresses and other parameters from a dhcp server. Enter the preferred dhcp host ...
Page 44
Chapter 3: kx iii administration 32 a none - for a static ip. Default selection. Recommended option. If none is selected, you must manually specify - global/unique ip address - this is the ip address assigned to kx iii prefix length - this is the number of bits used in the ipv6 address gateway ip ad...
Page 45
Chapter 3: kx iii administration 33 configure the dns settings 1 do one of the following to configure dns - "obtain dns server address automatically" "use the following dns server addresses" a select "obtain dns server address automatically" if dhcp is selected. The dns information is then provided ...
Page 46
Chapter 3: kx iii administration 34 b enter the following information if the "use the following dns server addresses" is selected - primary dns server ip address secondary dns server ip address these addresses are the primary and secondary dns addresses used if the primary dns server connection ...
Page 47
Chapter 3: kx iii administration 35 specify power supply autodetection kx iii provides dual power supplies. When both power supplies are used, kx iii automatically detects them and notifies you of their status. Additionally, both the powerln1 and powerln2 auto detect checkboxes are automatically sel...
Page 48
Chapter 3: kx iii administration 36 configure date/time settings (optional) optionally, configure the date and time settings. The date and time settings impact ssl certificate validation if ldaps is enabled. Use the date/time settings page to specify the date and time for kx iii. There are two ways ...
Page 49
Chapter 3: kx iii administration 37 3 choose the method to use to set the date and time: user specified time - use this option to input the date and time manually. For the user specified time option, enter the date and time. For the time, use the hh:mm format (using a 24-hour clock). Synchronize wit...
Page 50
Chapter 3: kx iii administration 38 note on microsoft active directory microsoft ® active directory ® uses the ldap/ldaps protocol natively, and can function as an ldap/ldaps server and authentication source for the kx iii. If it has the ias (internet authorization server) component, a microsoft act...
Page 51
Chapter 3: kx iii administration 39 access a target server from the kx iii to access a target server: 1. On the kx iii port access page, click the port name of the target you want to access. The port action menu is displayed. 2. Choose connect from the port action menu. A kvm window opens with a con...
Page 52
Chapter 3: kx iii administration 40 disconnect from a target server to disconnect a target server: on the port access page, click the port name of the target you want to disconnect from, then click disconnect on port action menu when it appears. Or close the kvm client window. Step 6: configuring th...
Page 53
Chapter 3: kx iii administration 41 4 shut down the device and power on once again. The dcim-susb performs a reset (power cycle). 5 verify that the characters are correct. Step 7: create and install an ssl certificate raritan strongly recommends you install your own ssl certificate in each kx iii de...
Page 54
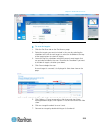
Chapter 3: kx iii administration 42 temperature current amps maximum amps voltage power in watts power in volts ampere outlet display information: name - named assigned to the outlet when it was configured. state - on or off status of the outlet control - turn outlets on or off, or...
Page 55
Chapter 3: kx iii administration 43 provided you have privileges to do so, you can manage power from the virtual kvm client (vkc) and active kvm client (akc) as well. See remote power management via virtual kvm client (vkc) or active kvm client (akc) (on page 293) turning outlets on/off and cycling ...
Page 56
Chapter 3: kx iii administration 44 usb profiles overview to broaden the kx iii's compatibility with different kvm target servers, raritan provides a standard selection of usb configuration profiles for a wide range of operating system and bios-level server implementations. The generic (default) usb...
Page 57
Chapter 3: kx iii administration 45 available usb profiles the current release of the kx iii comes with the selection of usb profiles described in the following table. New profiles are included with each firmware upgrade provided by raritan. As new profiles are added, they will be documented in the ...
Page 58
Chapter 3: kx iii administration 46 usb profile description bios dellpoweredge keyboard and mouse only dell poweredge bios access (keyboard and mouse only) use this profile to have keyboard functionality for the dell poweredge bios when using d2cim-vusb. When using the new d2cim-dvusb, use 'generic'...
Page 59
Chapter 3: kx iii administration 47 usb profile description usb bus speed limited to full-speed (12 mbit/s) bios hp compaq ® dc7100/dc7600 bios hp compaq dc7100/dc7600 use this profile to boot the hp compaq dc7100/dc7600 series desktops from virtual media. Restrictions: virtual cd-rom and disk d...
Page 60
Chapter 3: kx iii administration 48 usb profile description hp proliant dl360/dl380 g4 (windows 2003 ® server installation) hp proliant dl360/dl380 g4 (windows 2003 server installation) use this profile for the hp proliant dl360/dl380 g4 series server when installing windows 2003 server without the ...
Page 61
Chapter 3: kx iii administration 49 usb profile description phoenix awardbios. Restrictions: virtual cd-rom and disk drives cannot be used simultaneously suse 9.2 suse linux 9.2 use this for suse linux 9.2 distribution. Restrictions: absolute mouse synchronization™ not supported usb bus speed li...
Page 62
Chapter 3: kx iii administration 50 usb profile description media cim this profile resembles the behavior of the original kx3 release with full speed for virtual media cim option checked. Useful for bios that cannot handle high speed usb devices. Restrictions: usb bus speed limited to full-speed (...
Page 63
Chapter 3: kx iii administration 51 selecting profiles for a kvm port the kx iii comes with a set of usb profiles that you can assign to a kvm port based on the characteristics of the kvm target server it connects to. You assign usb profiles to a kvm port in the device settings > port configuration ...
Page 64
Chapter 3: kx iii administration 52 user description another group. Individual group an individual group is essentially a “group” of one. That is, the specific user is in its own group, not affiliated with other real groups. Individual groups can be identified by the “@” in the group name. The indiv...
Page 65
Chapter 3: kx iii administration 53 relationship between users and groups users belong to a group and groups have privileges. Organizing the various users of your kx iii into groups saves time by allowing you to manage permissions for all users in a group at once, instead of managing permissions on ...
Page 66
Chapter 3: kx iii administration 54 6. Click ok. Setting permissions important: selecting the user management checkbox allows the members of the group to change the permissions of all users, including their own. Carefully consider granting these permissions. Permission description device access whil...
Page 67
Chapter 3: kx iii administration 55 permission description when a device is accessed directly while it is under cc-sg management, access and connection activity is logged on the kx iii. User authentication is performed based on kx iii authentication settings. Note: the admin user group has this perm...
Page 68
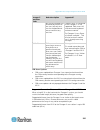
Chapter 3: kx iii administration 56 setting port permissions for each server port, you can specify the access type the group has, as well as the type of port access to the virtual media and the power control. Please note that the default setting for all permissions is deny. Port access option descri...
Page 69
Chapter 3: kx iii administration 57 if you are using a tiered configuration in which a base kx iii device is used to access multiple other tiered devices, the tiered device enforces individual port control levels. See configuring and enabling tiering (on page 137) for more information on tiering. Se...
Page 70
Chapter 3: kx iii administration 58 2. Type the ending ip address in the ending ip field. 3. Choose the action from the available options: accept - ip addresses set to accept are allowed access to the kx iii device. drop - ip addresses set to drop are denied access to the kx iii device. 4. Click...
Page 71
Chapter 3: kx iii administration 59 tip: the rule numbers allow you to have more control over the order in which the rules are created. Modifying an existing user group note: all permissions are enabled for the admin group and cannot be changed. To modify an existing user group: 1. From the group pa...
Page 72
Chapter 3: kx iii administration 60 users users must be granted user names and passwords to gain access to the kx iii. This information is used to authenticate users attempting to access your kx iii. Up to 254 users can be created for each user group. If you are using a tiered configuration in which...
Page 73
Chapter 3: kx iii administration 61 view the kx iii users list the user list page displays a list of all users including their user name, full name, and user group. The list can be sorted on any of the columns by clicking on the column name. From the user list page, you can add, modify, or delete us...
Page 74
Chapter 3: kx iii administration 62 username - username for user logins and target connections access from - ip address of client pc accessing the kx iii status - current active or inactive status of the connection to view users by port: choose user management > user by port. The users by port page ...
Page 75
Chapter 3: kx iii administration 63 modifying an existing user to modify an existing user: 1. Open the user list page by choosing user management > user list. 2. Locate the user from among those listed on the user list page. 3. Click the user name. The user page opens. 4. On the user page, change th...
Page 76
Chapter 3: kx iii administration 64 5. If you choose radius, read the section entitled implementing radius remote authentication for information about completing the fields in the radius section of the authentication settings page. 6. Click ok to save. To return to factory defaults: click reset to d...
Page 77
Chapter 3: kx iii administration 65 microsoft active directory. Active directory is an implementation of ldap/ldaps directory services by microsoft for use in windows environments. 8. Type the name of the active directory domain if you selected microsoft active directory. For example, acme.Com. Co...
Page 78
Chapter 3: kx iii administration 66 11. If you entered a distinguished name for the administrative user, you must enter the password that will be used to authenticate the administrative user's dn against the remote authentication server. Enter the password in the secret phrase field and again in the...
Page 79
Chapter 3: kx iii administration 67 14. The default secure ldap port is 636. Either use the default port or specify another port. This field is only used when the enable secure ldap checkbox is selected. 15. Select the enable ldaps server certificate validation checkbox to use the previously uploade...
Page 80
Chapter 3: kx iii administration 68 the kx iii then tests the ldap configuration from the authentication settings page. This is helpful due to the complexity sometimes encountered when configuring the ldap server and kx iii for remote authentication. Once the test is completed, a message is displaye...
Page 81
Chapter 3: kx iii administration 69 4. From the kx iii, enable and configure your ad server properly. See implementing ldap/ldaps remote authentication (on page 64). Important notes group name is case sensitive. The kx iii provides the following default groups that cannot be changed or deleted: admi...
Page 82
Chapter 3: kx iii administration 70 the timeout is the length of time the kx iii waits for a response from the radius server before sending another authentication request. 9. The default number of retries is 3 retries. This is the number of times the kx iii will send an authentication request to the...
Page 83
Chapter 3: kx iii administration 71 chap - with chap, authentication can be requested by the server at any time. Chap provides more security than pap..
Page 84
Chapter 3: kx iii administration 72 cisco acs 5.X for radius authentication if you are using a cisco acs 5.X server, after you have configured the kx iii for radius authentication, complete the following steps on the cisco acs 5.X server. Note: the following steps include the cisco menus and menu it...
Page 85
Chapter 3: kx iii administration 73 returning user group information via radius when a radius authentication attempt succeeds, the kx iii determines the permissions for a given user based on the permissions of the user's group. Your remote radius server can provide these user group names by returnin...
Page 86
Chapter 3: kx iii administration 74 attribute data log out accounting-request(4) acct-status (40) stop(2) - stops the accounting nas-port-type (61) virtual (5) for network connections. Nas-port (5) always 0. Nas-ip-address (4) the ip address for the kx iii. User-name (1) the user name entered at the...
Page 87
Chapter 3: kx iii administration 75 user authentication process remote authentication follows the process specified in the flowchart below:.
Page 88
Chapter 3: kx iii administration 76 changing a password to change your kx iii password: 1. Choose user management > change password. The change password page opens. 2. Type your current password in the old password field. 3. Type a new password in the new password field. Retype the new password in t...
Page 89
Chapter 3: kx iii administration 77 device management network settings use the basic network settings page to customize the network configuration for your kx iii. Specifically: assign the kx iii a device name (on page 29) configure the ipv4 settings (on page 29) configure the ipv6 settings (on page ...
Page 90
Chapter 3: kx iii administration 78.
Page 91
Chapter 3: kx iii administration 79 to change the network configuration: 1. Choose device settings > network. The network settings page opens. 2. Update the network basic settings. See network basic settings (on page 79). 3. Update the lan interface settings. See lan interface settings (on page 85)....
Page 92
Chapter 3: kx iii administration 80 configure the ipv4 settings in the ipv4 section, enter or select the appropriate ipv4-specific network settings. 1 enter the ip address, if needed. The default ip address is 192.168.0.192. 2 enter the subnet mask. The default subnet mask is 255.255.255.0. 3 set up...
Page 93
Chapter 3: kx iii administration 81 a none - for a static ip. Default selection. Recommended option. If none is selected, you must manually specify the network parameters by entering the default gateway. Leaving the selection set to none - lets you set the network parameters since kx iii is part of ...
Page 94
Chapter 3: kx iii administration 82 configure the ipv6 settings if using ipv6, enter or select the appropriate ipv6-specific network settings in the ipv6 section. 1 select the ipv6 checkbox to activate the fields in the section and enable ipv6 on the device. 2 select an ip auto configuration option ...
Page 95
Chapter 3: kx iii administration 83 a none - for a static ip. Default selection. Recommended option. If none is selected, you must manually specify - global/unique ip address - this is the ip address assigned to kx iii prefix length - this is the number of bits used in the ipv6 address gateway ip ad...
Page 96
Chapter 3: kx iii administration 84 a select "obtain dns server address automatically" if dhcp is selected. The dns information is then provided by the dhcp server that is used. When finished, click ok. Your kx iii device is now network accessible. B enter the following information if the "use the f...
Page 97
Chapter 3: kx iii administration 85 lan interface settings choose device settings > network to open the network settings page. This is where lan network settings are configured. The current parameter settings are identified in the current lan interface parameters section of the page. Update the lan ...
Page 98
Chapter 3: kx iii administration 86 step 1 choose the lan interface speed & duplex from the following options: autodetect (default option) 10 mbps/half - both kx iii device leds blink 10 mbps/full - both kx iii device leds blink 100 mbps/half - yellow kx iii device led blinks 100 mbps/full - yellow ...
Page 99
Chapter 3: kx iii administration 87 step 2 selecting the enable automatic failover checkbox allows the kx iii to automatically recover its network connection. To do this, it uses a second network port if the active network port fails. Note: because a failover port is not activated until after a fail...
Page 100
Chapter 3: kx iii administration 88 step 3 change the bandwidth limit, if needed. The default is no limit. This sets the maximum amount of bandwidth that can be consumed by the kx iii device (for all sessions). Note: lower bandwidth may result in slower performance. Click ok to apply the setting. Re...
Page 101
Chapter 3: kx iii administration 89 configuring ports access the port configuration page to access a port configuration: 1. Choose device settings > port configuration. The port configuration page opens. This page is initially displayed in port number order, but can be sorted on any of the fields by...
Page 102
Chapter 3: kx iii administration 90 port configuration page the port configuration page displays a list of the kx iii ports. When a port's status is down, not available is displayed as its status. A port may be down when the port's cim is removed or powered down. Note: for blade chassis, the blade c...
Page 103
Chapter 3: kx iii administration 91 port name if a kx iii port has no cim connected or is connected to a cim with no name, a default port name of dominion_kx3_port# is assigned to the port. Dominion_kx3 is the device model and port# is the number of the kx iii physical port. When a cim is attached t...
Page 104
Chapter 3: kx iii administration 92 port type port type includes: dcim - dominion cim tierdevice - tiered device not available - no cim connected dvm-dp - display port cim dvm-hdmi - hdmi cim dvm-dvi - dvi cim powerstrip (rack pdu) - power strip connected vm - d2cim - vusb cim dual - vm - d2cim-dvus...
Page 105
Chapter 3: kx iii administration 93 6. Click ok. Configuring kvm switches the kx iii also supports use of hot key sequences to switch between targets. In addition to using hot key sequences with standard servers, kvm switching is supported by blade chassis and in tiered configurations. Important: in...
Page 106
Chapter 3: kx iii administration 94 7. In the kvm switch name field, enter the name you want to use to refer to this port connection. 8. Activate the targets that the kvm switch hot key sequence will be applied to. Indicate that the kvm switch ports have targets attached by selecting ‘active’ for ea...
Page 107
Chapter 3: kx iii administration 95 e. Username field - enter the username parameter that will be used in the url. For example username=admin, where username is the username field. F. Password field - enter the password parameter that will be used in the url. For example password=raritan, where pass...
Page 108
Chapter 3: kx iii administration 96 configure the cim settings (on page 96) configure the cim power associations (on page 96) configure the cim target settings (on page 96) apply selected profiles to other cims (on page 97) apply a native display resolution to other cims (on page 97) configure the c...
Page 109
Chapter 3: kx iii administration 97 3. For digital cims, to set the target's video resolution to match your monitor's native display resolution, select the resolution from the display native resolution drop-down. For a complete list of supported video resolutions from the remote console, see kx iii ...
Page 110
Chapter 3: kx iii administration 98 configuring rack pdu (power strip) targets the kx iii allows you to connect rack pdus (power strips) to kx iii ports. Kx iii rack pdu configuration is done from the kx iii port configuration page. Note: raritan recommends no more than eight (8) rack pdus (power st...
Page 111
Chapter 3: kx iii administration 99 diagram key px rack pdu with serial port d2cim-pwr kx iii d2cim-pwr to rack pdu serial port connection d2cim-pwr to kx iii target server port via cat5 cable naming the rack pdu (port page for power strips) note: px rack pdus (power strips) can be named in the px a...
Page 112
Chapter 3: kx iii administration 100 3. Click ok..
Page 113
Chapter 3: kx iii administration 101 associating outlets with target servers the port page opens when you click on a port on the port configuration page. If an outlet is connected to the same server that the port is connected to, a power association can be made with the target server. A server can h...
Page 114
Chapter 3: kx iii administration 102 4. Click ok. That rack pdu/outlet association is removed and a confirmation message is displayed. To remove a rack pdu association if the rack pdu has been removed from the target: 1. Click device settings > port configuration and then click on the active target....
Page 115
Chapter 3: kx iii administration 103 3. On the port configuration page, click on the name of the blade chassis you want to configure. The port page will open. 4. Select the blade chassis radio button. The page will then display the necessary fields to configure a blade chassis. 5. Select generic fro...
Page 116
Chapter 3: kx iii administration 104 username - not applicable. password - not applicable. port number - the default port number for the blade chassis is 22. Not applicable. 7. Change the blade chassis name, if needed. 8. Check the installed checkbox next to each slot that has a blade installe...
Page 117
Chapter 3: kx iii administration 105 url - enter the url to the interface. Required username - enter the username used to access the interface. Optional password - enter the password used to access the interface. Optional note: leave the username and password fields blank for drac, ilo, and rs...
Page 118
Chapter 3: kx iii administration 106 see tips for adding a web browser interface (on page 120) for tips on adding a web browser interface. 10. In the target settings section, select "640x480 or 720x400 compensation" if you are experiencing display issues when the target is using this resolution. 1...
Page 119
Chapter 3: kx iii administration 107 14. Select 'use international keyboard for scan code set 3' if connecting to the target with a dcim-ps2 and require the use of scan code set 3 with an international keyboard. 15. Click ok to save the configuration. Blade chassis configuration options with the exc...
Page 120
Chapter 3: kx iii administration 108 manual and auto-discovery blade chassis configuration two modes of operation are provided for blade chassis: manual configuration and auto-discovery, depending on the blade chassis capabilities. Configure the mode by selecting device services > port configuration...
Page 121
Chapter 3: kx iii administration 109 hot key sequences to access blade chassis the use of hot key sequences to switch kvm access to a blade chassis is supported. For blade chassis that allow users to select a hot key sequence, those options will be provided on the port configuration page. For exampl...
Page 122
Chapter 3: kx iii administration 110 link to a blade chassis interface - blade chassis managed links you are able to configure the connection to a blade chassis web browser interface if one is available. Configure links when adding a blade by selecting device services > port configuration, and enter...
Page 123
Chapter 3: kx iii administration 111 managing blade chassis blade chassis can be managed from the virtual kvm client (vkc), active kvm client (akc), and cc-sg. Managing blade severs via vkc and akc is the same as managing standard target servers. See virtual kvm client (vkc) help (on page 248), acti...
Page 124
Chapter 3: kx iii administration 112 to configure a dell poweredge m1000e: 1. If you selected dell poweredge ™ m1000e, auto-discovery is available. Configure the blade chassis as applicable. Prior to configuring a blade chassis that can be auto-discovered, it must be configured to enable ssh connect...
Page 125
Chapter 3: kx iii administration 113 click the blade chassis managed links icon to expand the section on the page. The first url link is intended for use to connect to the blade chassis administration module gui. Note: access to the url links entered in this section of the page is governed by the bl...
Page 126
Chapter 3: kx iii administration 114 10. Select the cims native, display resolution from the display native resolution drop-down. This is the preferred resolution and timing mode of the digital cim. Once a resolution is selected, it is applied to the cim. If no selection is made, the default 1024x12...
Page 127
Chapter 3: kx iii administration 115 a. Active - to activate the link once it is configured, select the active checkbox. Leave the checkbox deselected to keep the link inactive. Entering information into the link fields and saving can still be done even if active is not selected. Once active is sele...
Page 128
Chapter 3: kx iii administration 116 3. On the port configuration page, click on the name of the blade chassis you want to configure. The port page will open. 4. Select the blade chassis radio button. The page will then display the necessary fields to configure a blade chassis. 5. Select the ibm ® b...
Page 129
Chapter 3: kx iii administration 117 5. In the blade chassis managed links section of the page, you are able to configure the connection to a blade chassis web browser interface if one is available. Click the blade chassis managed links icon to expand the section on the page. The first url link is i...
Page 130
Chapter 3: kx iii administration 118 6. If applicable, define the usb profile for the blade chassis or select an existing usb profile. Click the usb profiles select usb profiles for port icon or the apply select profiles to other ports icon to expand these sections of the page. See configuring usb p...
Page 131
Chapter 3: kx iii administration 119 a. Active - to activate the link once it is configured, select the active checkbox. Leave the checkbox deselected to keep the link inactive. Entering information into the link fields and saving can still be done even if active is not selected. Once active is sele...
Page 132
Chapter 3: kx iii administration 120 tips for adding a web browser interface you can add a web browser interface to create a connection to a device with an embedded web server. A web browser interface can also be used to connect to any web application, such as the web application associated with an ...
Page 133
Chapter 3: kx iii administration 121 hp and cisco ucs blade chassis configuration (port group management) the kx iii supports the aggregation of ports connected to certain types of blades into a group representing the blade chassis. Specifically, cisco ® ucs, hp ® bladeserver blades and dell ® power...
Page 134
Chapter 3: kx iii administration 122 4. Select the blade server group checkbox. If you want to designate that these ports are attached to blades housed in a blade chassis (for example, hp c3000 or dell poweredge 1855), select the blade server group checkbox. Note: this is especially important to cc-...
Page 135
Chapter 3: kx iii administration 123 supported blade chassis models this table contains the blade chassis models that are supported by the kx iii and the corresponding profiles that should be selected per chassis model when configuring them in the kx iii application. A list of these models can be se...
Page 136
Chapter 3: kx iii administration 124 blade chassis connection method recommended cim(s) generic if a d2cim-vusb or d2cim-dvusb is used when connecting to a blade-chassis configured as generic, you will be able to select the usb profiles from the port configuration page and the client's usb profile m...
Page 137
Chapter 3: kx iii administration 125 blade chassis connection method recommended cim(s) vga monitors with ddc support. Source: dell chassis management controller, firmware version 1.0, user guide hp ® bladesystem c3000 the hp c-class blade suv cable enables you to perform blade chassis administratio...
Page 138
Chapter 3: kx iii administration 126 blade chassis connection method recommended cim(s) the management module only features the leds for displaying status. All ethernet and kvm connections are fed through to the rear to the lan and kvm modules. The kvm module is a hot swap module at the rear of the ...
Page 139
Chapter 3: kx iii administration 127 blade chassis required/recommended action done. do not designate any slots for scan operations in the ikvm gui setup scan menu. Ikvm may not work correctly otherwise. do not designate any slots for broadcast keyboard/mouse operations in the ikvm gui setup bro...
Page 140
Chapter 3: kx iii administration 128 blade chassis required/recommended action ibm ® /dell ® auto- discovery it is recommended that auto-discovery be enabled when applying blade level access permissions. Otherwise, set access permissions on a blade-chassis wide basis. secure shell (ssh) must be ...
Page 141
Chapter 3: kx iii administration 129 blade chassis sample url format password: calvin password field: text_password ibm ® bladecenter ® e or h http://192.168.84.217/private/welcome.Ssi configuring usb profiles (port page) you choose the available usb profiles for a port in the select usb profiles fo...
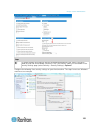
Page 142
Chapter 3: kx iii administration 130 ctrl-click to select several discontinuous profiles. 2. Click add. The selected profiles appear in the selected list. These are the profiles that can be used for the kvm target server connected to the port. To specify a preferred usb profile: 1. After selecting...
Page 143
Chapter 3: kx iii administration 131 configuring kx iii local port settings note: some changes you make to the settings on the local port settings page restart the browser you are working in. If a browser restart occurs when a setting is changed, it is noted in the steps provided here. To configure ...
Page 144
Chapter 3: kx iii administration 132 configure the local port scan mode settings 1. If needed, configure the local port scan mode settings. These settings apply to scan settings feature, which is accessed from the port page. in the "display interval (10-255 sec):" field, specify the number of seco...
Page 145
Chapter 3: kx iii administration 133 us portuguese (portugal) us/international norwegian (norway) united kingdom swedish (sweden) french (france) danish (denmark) german (germany) belgian (belgium) german (switzerland) hungarian simplified chinese spanish traditional ch...
Page 146
Chapter 3: kx iii administration 134 select the local port connect key 1. Select the local port connect key. Use a connect key sequence to connect to a target and switch to another target. You can then use the hot key to disconnect from the target and return to the local port gui. Once the local por...
Page 147
Chapter 3: kx iii administration 135 b. Set the amount of time (in minutes) in which power save mode will be initiated. Select the local user authentication 1. Choose the type of local user authentication. local/ldap/radius. This is the recommended option. none. There is no authentication for lo...
Page 148
Chapter 3: kx iii administration 136 3. Enter the ssh port information. The standard ssh tcp port number is 22 but the port number can be changed to provide a higher level of security operations. 4. Click ok. Http and https port settings you are able to configure http and/or https ports used by the ...
Page 149
Chapter 3: kx iii administration 137 configuring and enabling tiering the tiering feature allows you to access kx iii targets and pdus through one base kx iii device. Devices can be added and removed from a tiering configuration as needed up to a maximum of two tiered levels. When setting up the dev...
Page 150
Chapter 3: kx iii administration 138 unsupported and limited features on tiered targets the following features are not supported on tiered targets: blade chassis on tiered devices audio on tiered devices smart cards on tiered devices virtual media tiered devices mccat as a tiered device port group m...
Page 151
Chapter 3: kx iii administration 139 steps kx iii base device kx iii tiered device cim to connect the target server to kx iii the tiered device. Target server base device tier port to tiered device tier port connection: connect one end of a cat5/5e/6 cable into a target server port on the kx iii b...
Page 152
Chapter 3: kx iii administration 140 6 in the tier secret field, enter the same secret word you entered for the base device on the device settings page. Click ok. Once devices are enabled and configured, they appear on the port access page. When the kx iii is configured to function as a base device ...
Page 153
Chapter 3: kx iii administration 141 power control from tiered devices you can power on and off targets that are a part of the tiered configuration. These targets are accessed from the port access page. If targets and outlets are associated, power control is available from the port access page. Targ...
Page 154
Chapter 3: kx iii administration 142 username and password are optional. If username and password are not provided, a login dialog will be displayed and, after being authenticated, the user will be directly connected to the target. The port may be a port number or port name. If you are using a port ...
Page 155
Chapter 3: kx iii administration 143 username and password are optional. If username and password are not provided, a login dialog will be displayed and, after being authenticated, the user will be directly connected to the target. The port may be a port number or port name. If you are using a port ...
Page 156
Chapter 3: kx iii administration 144 enabling the akc download server certificate validation if you are using the akc client, you can choose to use the enable akc download server certificate validation feature or opt not to use this feature. Note: when operating in ipv4 and ipv6 dual stack mode with...
Page 157
Chapter 3: kx iii administration 145 2. Launch internet explorer ® using the kx iii ip address as the url. A certificate error message will be displayed. 3. Select view certificates. 4. On the general tab, click install certificate. The certificate is then installed in the trusted root certification...
Page 158
Chapter 3: kx iii administration 146 3. Select either or both enable snmp v1/v2c and enable snmp v3. At least one option must be selected. Required 4. Complete the following fields for snmp v1/v2c (if needed): a. Community - the device's community string b. Community type - grant either read-only or...
Page 159
Chapter 3: kx iii administration 147 configure snmp traps on the event management - settings page, which can be quickly accessed by clicking the snmp trap configuration link. See configuring snmp traps (on page 156)for information on creating snmp traps and list of kx iii snmp traps (on page 159) fo...
Page 160
Chapter 3: kx iii administration 148 3. The serial line speed of the modem is set to 115200. 4. Enter the initial modem string in the modem init string field. If the modem string is left blank, the following string is sent to the modem by default: atz ok at ok. This information is used to configure ...
Page 161
Chapter 3: kx iii administration 149 configure settings to access kx iii via modem through direct port access.
Page 162
Chapter 3: kx iii administration 150 in order to access kx iii via a modem through direct port access, you must configure settings in: the kx iii remote console on the client machine in the java control panel and in your browser (microsoft internet explorer ® and firefox ® information is provided he...
Page 163
Chapter 3: kx iii administration 151 steps 3 for better modem performance, raritan recommends deselecting the “apply encryption mode to kvm and virtual media (forced in fips 140- 2 mode)” setting if it is enabled on the security settings page (select security > security settings). Optional configure...
Page 164
Chapter 3: kx iii administration 152 steps 4 access the java control panel from the microsoft windows ® control panel. 5 in the java control panel, open to the general tab. 6 click settings. 7 select "keep temporary files on my computer". 8 click ok. You can now close the java control panel and micr...
Page 165
Chapter 3: kx iii administration 153 steps 8 for microsoft internet explorer ® , click tools > internet options. The steps here follow internet explorer 9. 9 click on the general tab. 10 click settings in the browser history section to open the windows database settings dialog. 11 click the "caches ...
Page 166
Chapter 3: kx iii administration 154 steps 12 for firefox ® , click tools > options. 13 click on privacy. 14 set the history to "firefox will" to "remember history". 15 click ok to apply the settings. Finally, you need to perform the following steps the first time you access each target server via t...
Page 167
Chapter 3: kx iii administration 155 steps 16 in vkc, click connection > properties to open the connection properties dialog. 17 set the vi deo mode to “greyscale 2” so you use the least bandwidth. 18 click ok. 19 it may be necessary to set the “noise filter” to greater than 2 if the modem connectio...
Page 168
Chapter 3: kx iii administration 156 note: if dhcp is selected for the network settings on the network page, the ntp server ip address is automatically retrieved from the dhcp server by default. Manually enter the ntp server ip address by selecting the override dhcp checkbox. 6. Click ok. Event mana...
Page 169
Chapter 3: kx iii administration 157 3. Select either or both snmp v1/v2c traps enabled and snmp trap v3 enabled. At least one option must be selected. Once selected, all related fields are enabled. Required 4. Complete the following fields for snmp v1/v2c (if needed): a. Destination ip/hostname - t...
Page 170
Chapter 3: kx iii administration 158 use the link to snmp agent configuration link to quickly navigate to the devices services page from the event management - settings page. The events that are captured once an snmp trap is configured are selected on the event management - destination page. See con...
Page 171
Chapter 3: kx iii administration 159 use the reset to factory defaults feature to remove the snmp configuration and set the kx iii to its original factory default. To reset to factory defaults: click reset to defaults. Warning: when using snmp traps over udp, it is possible for the kx iii and the ro...
Page 172
Chapter 3: kx iii administration 160 trap name description networkfailure an ethernet interface of the product can no longer communicate over the network. Networkparameterchanged a change has been made to the network parameters. Passwordsettingschanged strong password settings have changed. Portconn...
Page 173
Chapter 3: kx iii administration 161 trap name description userforcedlogout a user was forcibly logged out by admin userlogin a user has successfully logged into the kx iii and has been authenticated. Userlogout a user has successfully logged out of the kx iii properly. Usermodified a user account h...
Page 174
Chapter 3: kx iii administration 162 note: if you have read-write privileges to the mib file, use a mib editor to make changes to the file. Syslog configuration to configure the syslog (enable syslog forwarding): 1. Select enable syslog forwarding to log the device's messages to a remote syslog serv...
Page 175
Chapter 3: kx iii administration 163 configuring event management - destinations system events, if enabled, generate snmp notification events (traps), or can be logged to the syslog or audit log. Use the event management - destinations page to select the system events to track and where to send this...
Page 176
Chapter 3: kx iii administration 164 power supply setup the kx iii provides dual power supplies, and can automatically detect and provide notification regarding the status of these power supplies. Use the power supply setup page to specify whether you are using one or both of the power supplies. Pro...
Page 177
Chapter 3: kx iii administration 165 note: if either of these checkboxes is selected and power input is not actually connected, the power led at the front of the unit turns red. To turn off the automatic detection: deselect the checkbox for the appropriate power supply. To reset to factory default...
Page 178
Chapter 3: kx iii administration 166 connect and disconnect scripts the kx iii provides the ability to execute key macro scripts when connecting to or disconnecting from a target. You can create and edit your own scripts on the connection script page to perform additional actions when connecting to ...
Page 179
Chapter 3: kx iii administration 167 3. In the apply selected scripts to ports section, select the target(s) you want to apply the script to using select all or clicking on the checkbox to the left of each target to apply the script to only select targets. 4. Click apply scripts. Once the script is ...
Page 180
Chapter 3: kx iii administration 168 for example, select f1-f16 to display the function key set in the add box. Select a function key and add it to the script box. Next, select letters from the key set drop-down and add a letter key to the script. 8. Optionally, add text that will display when the s...
Page 181
Chapter 3: kx iii administration 169.
Page 182
Chapter 3: kx iii administration 170 modifying scripts to modify existing scripts: 1. Click device settings > connection scripts. The connection scripts page opens. 2. In the available connection scripts section, select the script you want to modify and click modify. The page is then in edit mode. 3...
Page 183
Chapter 3: kx iii administration 171 5. Click import. The configuration scripts page opens and the imported scripts are displayed. To export a disconnect script: 1. Click device settings > configuration scripts. The configuration scripts page opens. 2. In the available connection scripts section, se...
Page 184
Chapter 3: kx iii administration 172 creating port groups the kx iii supports the aggregation of multiple ports into a single port group. Port groups consist solely of ports configured as standard kvm ports. A port may only be a member of a single group. Ports that are available to be included in a ...
Page 185
Chapter 3: kx iii administration 173 creating a dual video port group the dual video port groups feature allows you to group two video ports into one group. Use this feature when you need to connect to a server with two video cards/ports, and you want to access both ports from the same remote client...
Page 186
Chapter 3: kx iii administration 174 note: if a port is already a part of blade server port group, another dual video port group, or 'standard' port group, the port is not an option since ports can only belong to a single port group at a time. 3. Select the dual video port group radio button. 4. Fro...
Page 187
Chapter 3: kx iii administration 175 2. From the language drop-down, select the language you want to apply to the gui. 3. Click apply. Click reset defaults to change back to english. Note: once you apply a new language, the online help is also localized to match your language selection. Security man...
Page 188
Chapter 3: kx iii administration 176 to reset back to defaults: click reset to defaults. Login limitations using login limitations, you can specify restrictions for single login, password aging, and the logging out idle users. Limitation description enable single login limitation when selected, only...
Page 189
Chapter 3: kx iii administration 177 limitation description enter the number of days after which a password change is required. The default is 60 days. Log out idle users, after (1-365 minutes) select the "log off idle users" checkbox to automatically disconnect users after the amount of time you sp...
Page 190
Chapter 3: kx iii administration 178 strong passwords strong passwords provide more secure local authentication for the system. Using strong passwords, you can specify the format of valid kx iii local passwords such as minimum and maximum length, required characters, and password history retention. ...
Page 191
Chapter 3: kx iii administration 179 user blocking the user blocking options specify the criteria by which users are blocked from accessing the system after the specified number of unsuccessful login attempts. The three options are mutually exclusive: option description disabled the default option. ...
Page 192
Chapter 3: kx iii administration 180 option description timer lockout users are denied access to the system for the specified amount of time after exceeding the specified number of unsuccessful login attempts. When selected, the following fields are enabled: attempts - the number of unsuccessful l...
Page 193
Chapter 3: kx iii administration 181 encryption & share using the encryption & share settings you can specify the type of encryption used, pc and vm share modes, and the type of reset performed when the kx iii reset button is pressed. Warning: if you select an encryption mode that is not supported b...
Page 194
Chapter 3: kx iii administration 182 encryption mode description aes-128 the advanced encryption standard (aes) is a national institute of standards and technology specification for the encryption of electronic data. 128 is the key length. When aes-128 is specified, be certain that your browser supp...
Page 195
Chapter 3: kx iii administration 183 5. If needed, select vm share mode. This option is enabled only when pc-share mode is enabled. When selected, this option permits the sharing of virtual media among multiple users, that is, several users can access the same virtual media session. The default is d...
Page 196
Chapter 3: kx iii administration 184 enabling fips 140-2 for government and other high security environments, enabling fips 140-2 mode may be required. The kx iii uses an embedded fips 140-2-validated cryptographic module running on a linux ® platform per fips 140-2 implementation guidance section g...
Page 197
Chapter 3: kx iii administration 185 fips 140-2 support requirements the kx iii supports the use of fips 140-2 approved encryption algorithms. This allows an ssl server and client to successfully negotiate the cipher suite used for the encrypted session when a client is configured for fips 140-2 onl...
Page 198
Chapter 3: kx iii administration 186 creating an ip access control list, 127.0.0.1 should not be within the range of ip addresses that are blocked or you will not have access to the kx iii local port. To use ip access control: 1. Select security > ip access control to open the ip access control page...
Page 199
Chapter 3: kx iii administration 187 3. Choose the policy from the drop-down list. 4. Click replace. Your new rule replaces the original rule with the same rule #. To delete a rule: 1. Specify the rule # you want to delete. 2. Click delete. 3. You are prompted to confirm the deletion. Click ok. Ssl ...
Page 200
Chapter 3: kx iii administration 188 when a self-signed certificate is created, the kx iii date and time are used to calculate the validity period. If the kx iii date and time are not accurate, the certificate's valid from - to date range may be incorrect, causing certificate validation to fail. See...
Page 201
Chapter 3: kx iii administration 189 to generate self-signed certificate, do the following: a. Select the create a self-signed certificate checkbox if you need to generate a self-signed certificate. When you select this option, the kx iii generates the certificate based on your entries, and acts a...
Page 202
Chapter 3: kx iii administration 190 note: the csr and the private key file are a matched set and should be treated accordingly. If the signed certificate is not matched with the private key used to generate the original csr, the certificate will not be useful. This applies to uploading and download...
Page 203
Chapter 3: kx iii administration 191 5. Edit the information in the restricted services banner message text box. Up to 6000 characters can be entered or uploaded from a text file. To do this, do one of the following: a. Edit the text by manually typing in the text box. Click ok. B. Upload the inform...
Page 204
Chapter 3: kx iii administration 192 maintenance audit log a log is created of the kx iii system events. The audit log can contain up to approximately 2k worth of data before it starts overwriting the oldest entries. To avoid losing audit log data, export the data to a syslog server or snmp manager....
Page 205
Chapter 3: kx iii administration 193 device information the device information page provides detailed information about your kx iii device and the cims in use. This information is helpful should you need to contact raritan technical support. To view information about your kx iii and cims: choose mai...
Page 206
Chapter 3: kx iii administration 194 d2cim-dvusb-dvi d2cim-dvusb-hdmi d2cim-dvusb note: only the numeric portion of the serial numbers are displayed for the dcim-usb, dcim-ps2 and dcim-usb g2 cims. For example, xxx1234567 is displayed. The serial number prefix gn is displayed for cims that hav...
Page 207
Chapter 3: kx iii administration 195 create a backup file note: backups are always complete system backups. Restores can be complete or partial depending on your selection. If you are using internet explorer ® 7 or later, to back up your kx iii: 1. Choose maintenance > backup/restore. The backup/res...
Page 208
Chapter 3: kx iii administration 196 restore your kx iii using a restore file warning: exercise caution when restoring your kx iii to an earlier version. Usernames and password in place at the time of the backup will be restored. If you do not remember the old administrative usernames and passwords,...
Page 209
Chapter 3: kx iii administration 197 user and group restore - this option includes only user and group information. This option does not restore the certificate and the private key files. Use this option to quickly set up users on a different kx iii. device settings restore - this option include...
Page 210
Chapter 3: kx iii administration 198 kx ii-to-kx iii unsupported backup/restore file settings and functions when you use a kx ii backup/restore file to apply settings to a kx iii, the following settings are not applied to the kx iii. Kx ii local extended port settings (kx iii does not support this f...
Page 211
Chapter 3: kx iii administration 199 note: if an error or warning is displayed during the upload process (for example. Overwriting an existing custom profile), you may continue with the upload by clicking upload or cancel it by clicking on cancel. To delete a custom profile to your kx iii: 1. Check ...
Page 212
Chapter 3: kx iii administration 200 4. Click ok to continue the upgrade. Progress bars are displayed during the upgrade. Upgrading takes approximately 2 minutes or less per cim. Upgrading the kx iii firmware use the firmware upgrade page to upgrade the firmware for your kx iii and all attached cims...
Page 213
Chapter 3: kx iii administration 201 note: at this point, connected users are logged out, and new login attempts are blocked. 6. Click upgrade. Please wait for the upgrade to complete. Status information and progress bars are displayed during the upgrade. Upon completion of the upgrade, the unit reb...
Page 214
Chapter 3: kx iii administration 202 to reboot your kx iii: 1. Choose maintenance > reboot. The reboot page opens. 2. Click reboot. You are prompted to confirm the action. Click yes to proceed with the reboot..
Page 215
Chapter 3: kx iii administration 203 stopping cc-sg management while the kx iii is under cc-sg management, if you try to access the device directly, you are notified that it the device is under cc-sg management. If you are managing the kx iii through cc-sg and connectivity between cc-sg and the kx i...
Page 216
Chapter 3: kx iii administration 204 3. Click yes to remove the device cc-sg management. Once cc-sg management has ended, a confirmation will be displayed. Diagnostics network interface page the kx iii provides information about the status of your network interface. To view information about your ne...
Page 217
Chapter 3: kx iii administration 205 statistics - produces a page similar to the one displayed here. interfaces - produces a page similar to the one displayed here..
Page 218
Chapter 3: kx iii administration 206 route - produces a page similar to the one displayed here. 3. Click refresh. The relevant information is displayed in the result field. Ping host page ping is a network tool used to test whether a particular host or ip address is reachable across an ip network....
Page 219
Chapter 3: kx iii administration 207 2. Type either the hostname or ip address into the ip address/host name field. Note: the host name cannot exceed 232 characters in length. 3. Click ping. The results of the ping are displayed in the result field. Trace route to host page trace route is a network ...
Page 220
Chapter 3: kx iii administration 208 device diagnostics note: this page is for use by raritan field engineers or when you are directed by raritan technical support. Device diagnostics downloads the diagnostics information from the kx iii to the client machine. Two operations can be performed on this...
Page 221
Chapter 3: kx iii administration 209 a. Click save to file. The file download dialog opens. B. Click save. The save as dialog box opens. C. Navigate to the desired directory and click save. D. Email this file as directed by raritan technical support. Kx iii local console - kx iii administration func...
Page 222
Chapter 3: kx iii administration 210 security and authentication in order to use the kx iii local console, you must first authenticate with a valid username and password. The kx iii provides a fully-integrated authentication and security scheme, whether your access is via the network or the local po...
Page 223
Chapter 3: kx iii administration 211 select the local console keyboard type 1. Choose the appropriate keyboard type from among the options in the drop-down list. The browser will be restarted when this change is made. us portuguese (portugal) us/international norwegian (norway) united king...
Page 224
Chapter 3: kx iii administration 212 hot key: take this action: double click scroll lock press scroll lock key twice quickly double click num lock press num lock key twice quickly double click caps lock press caps lock key twice quickly double click left alt key press the left alt key twice quickly ...
Page 225
Chapter 3: kx iii administration 213 the connect key works for both standard servers and blade chassis. Configure the power save feature (optional) 1. If you would like to use the power save feature: a. Select the power save mode checkbox. B. Set the amount of time (in minutes) in which power save m...
Page 226
Chapter 3: kx iii administration 214 this option is recommended for secure environments only. Command line interface (cli) overview the command line interface(cli) can be used to configure the kx iii network interface and perform diagnostic functions provided you have the appropriate permissions to ...
Page 227
Chapter 3: kx iii administration 215 accessing the kx iii using cli access the kx iii by using one of the following methods: ssh (secure shell) via ip connection a number of ssh clients are available and can be obtained from the following locations: putty - http://www.Chiark.Greenend.Org.Uk/~sgtatha...
Page 228
Chapter 3: kx iii administration 216 logging in to log in, enter the user name admin as shown: 1. Log in as admin 2. The password prompt appears. Enter the default password: raritan the welcome message displays. You are now logged on as an administrator. After reviewing the following navigation of t...
Page 229
Chapter 3: kx iii administration 217 cli syntax -tips and shortcuts tips commands are listed in alphabetical order. Commands are not case sensitive. Parameter names are single word without underscore. Commands without arguments default to show current settings for the command. Typing a question mark...
Page 230
Chapter 3: kx iii administration 218 initial configuration using cli note: these steps, which use the cli, are optional since the same configuration can be done via kvm. See getting started (on page 9) for more information. Kx iii devices come from the factory with default factory settings. When you...
Page 231
Chapter 3: kx iii administration 219 the kx iii now has the basic configuration and can be accessed remotely via ssh, gui, or locally using the local serial port. The administrator needs to configure the users and groups, services, security, and serial ports to which the serial targets are attached ...
Page 232
Chapter 3: kx iii administration 220 enter admin > config > network. Command description help display overview of commands. History display the current session's command line history. Interface set/get network parameters. Ipv6_interface set/get ipv6 network parameters. Logout logout of the current c...
Page 233
Chapter 3: kx iii administration 221 commands description ipv6 set/get ipv6 network parameters. Interface command theinterface command is used to configure the kx iii network interface. The syntax of the interface command is: interface [ipauto ] [ip ] [mask ] [gw ] [mode ] set/get ethernet parameter...
Page 234
Chapter 3: kx iii administration 222 name command the name command is used to configure the network name. The syntax of the name is: name [devicename ] [hostname ] device name configuration devicename device name hostname preferred host name (dhcp only) name command example the following command set...
Page 235
Chapter 3: kx iii administration 223 recommendations for dual port video set the target server’s primary and secondary displays to the same video resolution in order to maintain mouse synchronization and minimize having to periodically resync. Depending on the desired orientation, the top display (v...
Page 236
Chapter 3: kx iii administration 224 target operating systems supported mouse modes comments linux ® intelligent and standard mouse modes linux ® users may experience display and mouse movement issues using single mouse mode. Raritan recommends linux users do not use single mouse mode. Mac ® operati...
Page 237
Chapter 3: kx iii administration 225 other - enable single mouse cursor setting will not be applied other - enable scale video setting will be applied other - pin menu toolbar setting will be applied dragging and moving items between windows on the primary and secondary target requires a relea...
Page 238
Chapter 3: kx iii administration 226 example dual port video group configuration the following is a general example. Your configuration may vary in the type of cims used, the port you designate as the primary port, the ports you are connecting to and so on. In this example, we are using: a target se...
Page 239
Chapter 3: kx iii administration 227 diagram key connection from the target's primary (first) video port to the kx iii connection from the target's secondary (second) video port to the kx iii ip connection between the kx iii and remote client target server - configure the display settings and launch...
Page 240
Chapter 3: kx iii administration 228 step 2: connect the target server to the kx iii dual port video groups can be created from existing port connections, or new port connections. The steps provided here assume you are creating new connections. If you are creating a dual port video group from existi...
Page 241
Chapter 3: kx iii administration 229 step 3: configure the mouse mode and ports once you have connected the target server to the raritan device through the target server video ports, it detects the connection and displays the ports on the port configuration page. For instructions, see configuring st...
Page 242
Chapter 3: kx iii administration 230 step 5: launch a dual port video group once you have created the dual video port group, it is available on the port access page. You cannot remotely connect to the dual video port group by clicking on a primary port unless two kvm channels are available. If two c...
Page 243
Chapter 3: kx iii administration 231 direct port access and dual port video groups direct port access allows users to bypass having to use the device's login dialog and port access page. This feature also provides the ability to enter a username and password directly to proceed to the target, if the...
Page 244
Chapter 3: kx iii administration 232 from ldap/ldaps when an ldap/ldaps authentication is successful, the kx iii determines the permissions for a given user based on the permissions of the user's group. Your remote ldap server can provide these user group names by returning an attribute named as fol...
Page 245
Chapter 3: kx iii administration 233 setting the registry to permit write operations to the schema to allow a domain controller to write to the schema, you must set a registry entry that permits schema updates. To permit write operations to the schema: 1. Right-click the active directory ® schema ro...
Page 246
Chapter 3: kx iii administration 234 3. Click new and then choose attribute. When the warning message appears, click continue and the create new attribute dialog appears. 4. Type rciusergroup in the common name field. 5. Type rciusergroup in the ldap display name field. 6. Type 1.3.6.1.4.1.13742.50 ...
Page 247
Chapter 3: kx iii administration 235 2. Scroll to the user class in the right pane and right-click it. 3. Choose properties from the menu. The user properties dialog appears. 4. Click the attributes tab to open it. 5. Click add..
Page 248
Chapter 3: kx iii administration 236 6. Choose rciusergroup from the select schema object list. 7. Click ok in the select schema object dialog. 8. Click ok in the user properties dialog. Updating the schema cache to update the schema cache: 1. Right-click active directory ® schema in the left pane o...
Page 249
Chapter 3: kx iii administration 237 3. Go to the directory where the support tools were installed. Run adsiedit.Msc. The adsi edit window opens. 4. Open the domain. 5. In the left pane of the window, select the cn=users folder..
Page 250
Chapter 3: kx iii administration 238 6. Locate the user name whose properties you want to adjust in the right pane. Right-click the user name and select properties. 7. Click the attribute editor tab if it is not already open. Choose rciusergroup from the attributes list. 8. Click edit. The string at...
Page 251: Virtual Media
239 in this chapter overview ................................................................................................ 239 prerequisites for using virtual media .................................................... 240 mounting local drives ........................................................
Page 252
Chapter 4: virtual media 240 prerequisites for using virtual media kx iii virtual media prerequisites for users requiring access to virtual media, the kx iii permissions must be set to allow access to the relevant ports, as well as virtual media access (vm access port permission) for those ports. Po...
Page 253
Chapter 4: virtual media 241 mounting local drives this option mounts an entire drive, which means the entire disk drive is mounted virtually onto the target server. Use this option for hard drives and external drives only. It does not include network drives, cd-rom, or dvd-rom drives. Notes on moun...
Page 254
Chapter 4: virtual media 242 supported virtual media types the following virtual media types are supported for windows ® , mac ® and linux ™ clients: internal and external hard drives internal and usb-mounted cd and dvd drives usb mass storage devices pc hard drives iso images (disk images) iso9660 ...
Page 255
Chapter 4: virtual media 243 number of supported virtual media drives with the virtual media feature, you can mount up to two drives (of different types) that are supported by the usb profile currently applied to the target. These drives are accessible for the duration of the kvm session. For exampl...
Page 256
Chapter 4: virtual media 244 2. Choose the drive from the local drive drop-down list. If you want read and write capabilities, select the read-write checkbox. This option is disabled for nonremovable drives. See the conditions when read/write is not available (on page 242) for more information. When...
Page 257
Chapter 4: virtual media 245 4. For remote iso images on a file server: a. Choose the remote server iso image option. B. Choose hostname and image from the drop-down list. The file servers and image paths available are those that you configured using the file server setup page. Only items you config...
Page 258
Chapter 4: virtual media 246 virtual media in a linux environment active system partitions you cannot mount active system partitions from a linux client. Linux ext3/4 drive partitions need to be unmounted via umount /dev/ prior to a making a virtual media connection. Drive partitions the following d...
Page 259
Chapter 4: virtual media 247 virtual media file server setup (file server iso images only) this feature is only required when using virtual media to access file server iso images. Iso9660 format is the standard supported by raritan. However, other cd-rom extensions may also work. Note: smb/cifs supp...
Page 260
248 in this chapter overview ................................................................................................ 249 recommended minimum virtual kvm client (vkc) requirements ...... 249 virtual kvm client java requirements - kx iii ..................................... 250 proxy server ...
Page 261
Chapter 5: virtual kvm client (vkc) help 249 overview whenever you access a target server from the port access page of kx iii the remote console, a virtual kvm client (vkc) window opens. There is one virtual kvm client for each target server connected. Virtual kvm client windows can be minimized, ma...
Page 262
Chapter 5: virtual kvm client (vkc) help 250 virtual kvm client java requirements - kx iii java ™ 1.7 is required to use the java-based virtual kvm client (vkc). Proxy server configuration for use with virtual kvm client (vkc) and active kvm client (akc) when the use of a proxy server is required, a...
Page 263
Chapter 5: virtual kvm client (vkc) help 251 connect to a target from virtual kvm client (vkc) or active kvm client (akc) once you have logged on to the kx iii remote console, access target servers via the virtual kvm client (vkc) or active kvm client (akc). To connect to an available server: 1. On ...
Page 264
Chapter 5: virtual kvm client (vkc) help 252 configuring connection properties access connection properties to access connection properties: click connection > properties, or click the connection... Icon to open the connection properties dialog. About connection properties the virtual kvm client (vk...
Page 265
Chapter 5: virtual kvm client (vkc) help 253 default connection property settings - optimized for best performance kx iii comes configured to provide optimal performance for the majority of video streaming conditions. Default connection settings are: optimized for: text readability - video modes are...
Page 266
Chapter 5: virtual kvm client (vkc) help 254 optimize for: selections text readability when text readability is selected, all video modes are designed to provide high-quality, readable text. This setting is ideal when working with computer guis, such as when performing server administration and so o...
Page 267
Chapter 5: virtual kvm client (vkc) help 255 in general, moving the slider to the left results in higher quality at the cost of higher bandwidth and, in some cases, lower frame rate. Moving the slider to the right enables stronger compression, reducing the bandwidth per frame, but video quality is r...
Page 268
Chapter 5: virtual kvm client (vkc) help 256 connection information open the connection information dialog for real-time connection information, and copy the information from the dialog as needed. This is useful if, for example, you want to gather real-time information on your current connection. Se...
Page 269
Chapter 5: virtual kvm client (vkc) help 257 steps click connection > info... To open the connection info dialog. Click copy to clipboard. Paste the information in a file of your choosing. Usb profiles set a usb profile for a target server from the virtual kvm client (vkc) by clicking usb profile in...
Page 270
Chapter 5: virtual kvm client (vkc) help 258 keyboard send ctrl+alt+del macro due to its frequent use, a ctrl+alt+delete macro is preprogrammed. Selecting keyboard > send ctrl+alt+del, or clicking on the ctrl+alt+delete button in the toolbar sends this key sequence to the server or to the kvm switch...
Page 271
Chapter 5: virtual kvm client (vkc) help 259 4. Click ok. Keyboard macros keyboard macros ensure that keystroke combinations intended for the target server are sent to and interpreted only by the target server. Otherwise, they might be interpreted by the computer on which the virtual kvm client (vkc...
Page 272
Chapter 5: virtual kvm client (vkc) help 260 a. To remove a step in the sequence, select it and click remove. B. To change the order of steps in the sequence, click the step and then click the up or down arrow buttons to reorder them as needed. 7. Click ok to save the macro. Click clear to clear all...
Page 273
Chapter 5: virtual kvm client (vkc) help 261 click yes to replace the existing macro with the imported version. click yes to all to replace the currently selected and any other duplicate macros that are found. click no to keep the original macro and proceed to the next macro click no to all ...
Page 274
Chapter 5: virtual kvm client (vkc) help 262 4. Select the folder to save the macro file to, enter a name for the file and click save. If the macro already exists, you receive an alert message. 5. Select yes to overwrite the existing macro or no to close the alert without overwriting the macro. Vide...
Page 275
Chapter 5: virtual kvm client (vkc) help 263 calibrating color use the calibrate color command to optimize the color levels (hue, brightness, saturation) of the transmitted video images. The color settings are on a target server-basis. Note: the calibrate color command applies to the current connect...
Page 276
Chapter 5: virtual kvm client (vkc) help 264 if the video image looks extremely blurry or unfocused, the settings for clock and phase can be adjusted until a better image appears on the active target server. Warning: exercise caution when changing the clock and phase settings. Doing so may result in...
Page 277
Chapter 5: virtual kvm client (vkc) help 265 note: some sun background screens, such as screens with very dark borders, may not center precisely on certain sun servers. Use a different background or place a lighter colored icon in the upper left corner of the screen. Screenshot from target command (...
Page 278
Chapter 5: virtual kvm client (vkc) help 266 mouse options you can operate in either single mouse mode or dual mouse mode. When in a dual mouse mode, and provided the option is properly configured, the mouse cursors align. When controlling a target server, the remote console displays two mouse curso...
Page 279
Chapter 5: virtual kvm client (vkc) help 267 dual mouse modes absolute mouse synchronization in this mode, absolute coordinates are used to keep the client and target cursors in synch, even when the target mouse is set to a different acceleration or speed. This mode is supported on servers with usb ...
Page 280
Chapter 5: virtual kvm client (vkc) help 268 intelligent mouse synchronization conditions the intelligent mouse synchronization command, available on the mouse menu, automatically synchronizes mouse cursors during moments of inactivity. For this to work properly, however, the following conditions mu...
Page 281
Chapter 5: virtual kvm client (vkc) help 269 standard mouse mode standard mouse mode uses a standard mouse synchronization algorithm. The algorithm determines relative mouse positions on the client and target server. In order for the client and target mouse cursors to stay in synch, mouse accelerati...
Page 282
Chapter 5: virtual kvm client (vkc) help 270 single mouse mode single mouse mode uses only the target server mouse cursor; the client mouse cursor no longer appears onscreen. Note: single mouse mode does not work on windows or linux targets when the client is running on a virtual machine. To enter s...
Page 283
Chapter 5: virtual kvm client (vkc) help 271 japanese united kingdom korean (korea) french (belgium) norwegian (norway) portuguese (portugal) danish (denmark) swedish (sweden) german (switzerland) hungarian (hungary) spanish (spain) italian (italy) slovenian translation: ...
Page 284
Chapter 5: virtual kvm client (vkc) help 272 further, if a hotkey is added to the application due to an upgrade and the default value for the key is already in use, the next available value is applied to the function instead. 5. Click ok. Keyboard limitations turkish keyboards if using a turkish key...
Page 285
Chapter 5: virtual kvm client (vkc) help 273 language configuration method japanese system settings (control center) uk system settings (control center) korean system settings (control center) belgian keyboard indicator norwegian keyboard indicator danish keyboard indicator swedish keyboard indicato...
Page 286
Chapter 5: virtual kvm client (vkc) help 274 b. Use 'select from detected monitors' to select from a list of monitors that are currently detected by the application. If a previously selected monitor is no longer detected, 'currently selected monitor not detected' is displayed. to configure additio...
Page 287
Chapter 5: virtual kvm client (vkc) help 275 configuring port scan settings in vkc and akc configuring port scan options in vkc and akc applies to scanning from the kx iii remote console. To configure port scan options for the local console, see configure local console scan settings (on page 326) us...
Page 288
Chapter 5: virtual kvm client (vkc) help 276 6. Click ok. Collecting a diagnostic snapshot of the target administrators are able to collect a "snapshot" of a target from either the virtual kvm client (vkc) or active kvm client (akc). The "snapshot" function generate log files and image files from th...
Page 289
Chapter 5: virtual kvm client (vkc) help 277 log.Txt file: these are the client logs. Note that the logs are included even if you have not enabled information to be captured in them. Vkc uses internal memory to capture the information in this case. Collect a diagnostic snapshot from the virtual kvm ...
Page 290
Chapter 5: virtual kvm client (vkc) help 278 to capture a diagnostic snapshot: steps 1 access a target via virtual kvm client (vkc) or active kvm client (akc), and then click tools > collect a diagnostic snapshot. Several messages are displayed as the information is collected. 2 you are prompted to ...
Page 291
Chapter 5: virtual kvm client (vkc) help 279 3 the zip file containing the diagnostic files that were collecting opens. View options view toolbar you can use the virtual kvm client with or without the toolbar display. To toggle the display of the toolbar (on and off): choose view > view toolbar. Vie...
Page 292
Chapter 5: virtual kvm client (vkc) help 280 full screen mode when you enter full screen mode, the target's full screen is displayed and acquires the same resolution as the target server. The hot key used for exiting this mode is specified in the options dialog, see tool options (on page 270). While...
Page 293
Chapter 5: virtual kvm client (vkc) help 281 smart cards using the kx iii, you are able to mount a smart card reader onto a target server to support smart card authentication and related applications. For a list of supported smart cards, smart card readers, and additional system requirements, see sm...
Page 294
Chapter 5: virtual kvm client (vkc) help 282 smart card reader detected after a kvm session is established with a target server, a smart card menu and button are available in vkc and akc. Once the smart card button is selected or smart card is selected from the menu, the smart card readers that are ...
Page 295
Chapter 5: virtual kvm client (vkc) help 283 update a smart card reader to update the smart card in the select smart card reader dialog: click refresh list if a new smart card reader has been attached to the client pc. Send smart card remove and reinsert notifications to send smart card remove and r...
Page 296
Chapter 5: virtual kvm client (vkc) help 284 digital audio the kx iii supports end-to-end, bidirectional, digital audio connections for digital audio playback and capture devices from a remote client to a target server. The audio devices are accessed over a usb connection. Current device firmware is...
Page 297
Chapter 5: virtual kvm client (vkc) help 285 digital audio vkc and akc icons audio icons icon name description speaker these icons are located in status bar at the bottom of the client window. Green, blinking waves indicate an audio playback session is currently streaming. A black speaker icon is di...
Page 298
Chapter 5: virtual kvm client (vkc) help 286 recommendations for audio connections when pc share mode is enabled if you are using the audio feature while running pc share mode, audio playback and capture are interrupted if an additional audio device is connected to the target. For example, user a co...
Page 299
Chapter 5: virtual kvm client (vkc) help 287 in practice, the bandwidth used when an audio device connects to a target is higher due to the keyboard and video data consumed when opening and using an audio application on the target. A general recommendation is to have at least a 1.5mb connection befo...
Page 300
Chapter 5: virtual kvm client (vkc) help 288 saving audio settings audio device settings are applied on a per kx iii device basis. Once the audio devices settings are configured and saved on the kx iii, the same settings are applied to it. For example, you can configure a windows ® audio device to u...
Page 301
Chapter 5: virtual kvm client (vkc) help 289 operating system audio playback support review the table shown here to see which raritan client works with audio playback/capture for each operating system: operating system audio playback and capture supported by: windows ® active kvm client (akc) virtua...
Page 302
Chapter 5: virtual kvm client (vkc) help 290 6. Select the audio format for the playback device from the format: drop-down. Note: select the format that you wish to use based on the available network bandwidth. Formats with lower sampling rates consume less bandwidth and may tolerate more network co...
Page 303
Chapter 5: virtual kvm client (vkc) help 291 a speaker icon is displayed in the status bar at the bottom of the client window. It is grayed out when no audio is being used. When the speaker icon and microphone icon are displayed in the status bar, the session is being captured as it is streamed. Dis...
Page 304
Chapter 5: virtual kvm client (vkc) help 292 adjusting capture and playback buffer size (audio settings) once an audio device is connected, the capture and playback buffer size can be adjusted as needed. This feature is useful for controlling the quality of the audio, which may be impacted by bandwi...
Page 305
Chapter 5: virtual kvm client (vkc) help 293 remote power management via virtual kvm client (vkc) or active kvm client (akc) target power is managed by controlling the outlet it is connected to. Specifically, you can power on, power off, and power cycle a target via the outlet it is connected to. To...
Page 306
294 in this chapter overview ................................................................................................ 294 recommended minimum active kvm client (akc) requirements ...... 294 akc supported microsoft .Net framework.......................................... 295 akc supported ope...
Page 307
Chapter 6: active kvm client (akc) help 295 'modern' quad core cpu for two or more simultaneous connections 4gb of ram akc supported microsoft .Net framework the active kvm client (akc) requires windows .Net ® version 3.5, 4.0 or 4.5. Akc works with both 3.5 and 4.0 installed. Akc supported operat...
Page 308
Chapter 6: active kvm client (akc) help 296 include kx iii ip address in 'trusted sites zone' windows vista ® , windows ® 7 and windows 2008 server users should ensure that the ip address of the device being accessed is included in their browser's trusted sites zone. Disable 'protected mode' windows...
Page 309
Chapter 6: active kvm client (akc) help 297 2. Next, configure the proxy settings for the java ™ applets: a. Select control panel > java. B. On the general tab, click network settings. The network settings dialog opens. C. Select "use proxy server". D. Click advanced. The advanced network settings d...
Page 310: Mobile Kvm Client (Mkc) Help
298 in this chapter remotely access targets using a mobile device ................................ 298 connect to a target using the mobile kvm client ................................ 299 touch mouse functions ........................................................................ 299 using the mkc...
Page 311
Chapter 7: mobile kvm client (mkc) help 299 connect to a target using the mobile kvm client mobile access using the mobile access client requires the use of commandcenter secure gateway (cc-sg). Enable pop-ups in your mobile device browser before accessing mobile kvm client (mkc) or cc-sg mobile acc...
Page 312
Chapter 7: mobile kvm client (mkc) help 300 using the mkc toolbar the mkc toolbar may not be completely visible at one time, depending on the resolution of your mobile device. To view the whole toolbar: touch and swipe to move the toolbar icons to the left and right, bringing different icons into vi...
Page 313
Chapter 7: mobile kvm client (mkc) help 301 touch and swipe the toolbar to the left, to view the f5 through f12 icons. Swipe the toolbar back to the right to return to the default view. On a mobile phone device, such as an iphone, you will see fewer icons. Use the same touch-and-swipe motion left an...
Page 314
Chapter 7: mobile kvm client (mkc) help 302 display mobile device keyboard toggle on and off the mkc keyboard to display or hide it. The keyboard is configured on the mobile device. For example, on ipad choose settings > general > keyboard > international keyboards to see the available keyboards or ...
Page 315
Chapter 7: mobile kvm client (mkc) help 303 set keyboard type the default keyboard in mkc is us/international english. Select the language keyboard to match the language keyboard setting of the target you are accessing. This is required to provide the correct keyboard mapping in the target. You must...
Page 316
Chapter 7: mobile kvm client (mkc) help 304 manage mobile client keyboard macros each user must import their user-defined keyboard macros to make them available for use while connected to targets using the mobile kvm client (mkc). Export the file from virtual kvm client (vkc), then import it using t...
Page 317
Chapter 7: mobile kvm client (mkc) help 305 2. Touch mouse mode, then touch absolute, intelligent, or standard. Absolute mouse mode in this mode, absolute coordinates are used to keep the client and target cursors in synch, even when the target mouse is set to a different acceleration or speed. This...
Page 318
Chapter 7: mobile kvm client (mkc) help 306 sync mouse in intelligent or standard mouse mode in intelligent or standard mouse mode, the sync mouse command forces realignment of the target server mouse pointer with the mkc mouse pointer. To sync mouse: 1. In the mkc toolbar, touch menu, then touch mo...
Page 319
Chapter 7: mobile kvm client (mkc) help 307 view mkc help descriptions of the touchscreen techniques can be accessed in mkc. To view mkc help: touch the help icon (?) icon in the toolbar. The help opens. See touch mouse functions (on page 299) to view this information..
Page 320: Kx Iii Remote Console
308 in this chapter overview ................................................................................................ 308 scanning ports - remote console ........................................................ 309 changing a password ............................................................
Page 321
Chapter 8: kx iii remote console 309 scanning ports - remote console use the port scanning feature to search for selected targets and display them in individual thumbnails as part of a slide show. This feature allows you to monitor up to 32 targets at one time since you can view each target server i...
Page 322
Chapter 8: kx iii remote console 310 scanning ports slide show - remote console when you start a scan, the port scan window opens. As each target is found, it is displayed as a thumbnail in a slide show. The slide show scrolls through the target thumbnails based on the default interval of 10 seconds...
Page 323
Chapter 8: kx iii remote console 311 target status indicators during port scanning - remote console the status of each target is indicated by green, yellow and red lights that are displayed below the target thumbnail. As the target is the focus of the rotation, the indicator is in the task bar also ...
Page 324
Chapter 8: kx iii remote console 312 using scan port options following are options available to you while scanning targets. With the exception of the expand/collapse icon, all of these options are selected from the options menu in the upper left of the port scan viewer. The options will return to th...
Page 325
Chapter 8: kx iii remote console 313 scan for targets to scan for targets: 1. Click the set scan tab on the port access page. 2. Select the targets you want to include in the scan by selecting the checkbox to the left of each target, or select the checkbox at the top of the target column to select a...
Page 326
Chapter 8: kx iii remote console 314 changing a password to change your kx iii password: 1. Choose user management > change password. The change password page opens. 2. Type your current password in the old password field. 3. Type a new password in the new password field. Retype the new password in ...
Page 327
Chapter 8: kx iii remote console 315 managing favorites a favorites feature is provided so you can organize and quickly access the devices you use frequently. The favorite devices section is located in the lower left side (sidebar) of the port access page and provides the ability to: create and mana...
Page 328
Chapter 8: kx iii remote console 316 enable favorites click enable in the favorite devices section of the left panel of the kx iii interface. Once enabled, the enable button becomes a disable button..
Page 329
Chapter 8: kx iii remote console 317 access and display favorites to access a favorite kx iii device: click the device name (listed beneath favorite devices). A new browser opens to that device. To display favorites by name: click display by name. To display favorites by ip address: click display by...
Page 330
Chapter 8: kx iii remote console 318 to use the default discovery port, select the use default port 5000 checkbox. to use a different discovery port: a. Deselect the use default port 5000 checkbox. B. Type the port number in the discover on port field. C. Click save. 3. Click refresh. The list o...
Page 331: Kx Iii Local Console
319 in this chapter overview ................................................................................................ 319 accessing a target server .................................................................... 319 local console video resolutions ..........................................
Page 332
Chapter 9: kx iii local console 320 local console video resolutions once a monitor is connected to the kx iii local console, kx iii detects the native resolution of the monitor. This is typically the highest resolution supported by the monitor. As long as the monitor's native resolution is supported...
Page 333
Chapter 9: kx iii local console 321 return to the kx iii local console from a target server - default hot key to return to the kx iii local console from the target server: press the scroll lock hot key twice rapidly the video display switches from the target server interface to the kx iii local cons...
Page 334
Chapter 9: kx iii local console 322 standard servers connect key action key sequence example double click scroll lock special sun key combinations the following key combinations for sun ™ microsystems server’s special keys operate on the local port. These special are available from the keyboard menu...
Page 335
Chapter 9: kx iii local console 323 scanning ports - local console use the port scanning feature to search for selected targets and display them in individual thumbnails as part of a slide show. This feature allows you to monitor up to 32 targets at one time since you can view each target server ind...
Page 336
Chapter 9: kx iii local console 324 scanning port slide show - local console when you start a scan, the port scan window opens. As each target is found, it is displayed as a thumbnail in a slide show. The slide show scrolls through the target thumbnails based on the default interval of 10 seconds or...
Page 337
Chapter 9: kx iii local console 325.
Page 338
Chapter 9: kx iii local console 326 target status indicators during port scanning - local console in thumbnail view on the local console, the status of each target is indicated below the thumbnail on the page until it is the focus of the slide show view. The scanning status of each target is display...
Page 339
Chapter 9: kx iii local console 327 display interval - changes the scan display interval. interval between ports - change interval between switching different port during scan. Scan for targets - local console to scan for targets: 1. Click the set scan tab on the port access page. 2. Select the ...
Page 340
Chapter 9: kx iii local console 328 2. From the local console, click tools. 3. Select the smart card reader from the card readers detected list. Select none from the list if you do not want a smart card reader mounted. 4. Click ok. Once the smart card reader is added, a message will appear on the pa...
Page 341
Chapter 9: kx iii local console 329 local console usb profile options from the usb profile options section of the tools page, you can choose from the available usb profiles. The ports that can be assigned profiles are displayed in the port name field and the profiles that are available for a port ap...
Page 342
Chapter 9: kx iii local console 330 kx iii local console factory reset note: it is recommended that you save the audit log prior to performing a factory reset. The audit log is deleted when a factory reset is performed and the reset event is not logged in the audit log. For more information about sa...
Page 343
Chapter 9: kx iii local console 331 2. Use a pointed object to press and hold the reset button. 3. While continuing to hold the reset button, power the kx iii device back on. 4. Continue holding the reset button for 10 seconds..
Page 344: Functionality
332 in this chapter overview ................................................................................................ 332 about the cat5 reach dvi .................................................................... 332 connect a kx iii and cat5 reach dvi .......................................
Page 345
Appendix a: connecting a kx iii and cat5 reach dvi - provide extended local port functionality 333 connect a kx iii and cat5 reach dvi note: the images used in the diagrams are not specific to kx iii but the connections are accurate. This section introduces three scenarios involving kvm switches. Co...
Page 346
Appendix a: connecting a kx iii and cat5 reach dvi - provide extended local port functionality 334 5. Turn on the kvm switch. Tip: the local or remote console can be equipped with a kvm drawer instead of a set of keyboard, mouse and monitor. See the illustration below. To increase the distance betwe...
Page 347
Appendix a: connecting a kx iii and cat5 reach dvi - provide extended local port functionality 335 5. Turn on both kvm switches. To increase the distance between any computer and a kvm switch: 1. Set up an optional local console with the transmitter. 2. Set up a remote console by connecting the rece...
Page 348: III
336 in this chapter overview ................................................................................................ 336 supported paragon ii cims and configurations ................................... 337 connecting the paragon ii to the kx iii ................................................
Page 349
Appendix b: accessing a paragon ii from the kx iii 337 when you access the paragon ii system from kx iii or cc-sg (if the kx iii is managed by cc-sg), the paragon ii osui login screen appears for you to log in. In this integration, you can perform any osui functions implemented with current paragon ...
Page 350
Appendix b: accessing a paragon ii from the kx iii 338 paragon cim supports does not support p2cim-ausbdual servers with usb- or sun ™ usb-type keyboard and mouse ports automatic skew compensation (when the cims are connected to paragon ii, not from a kx iii) intelligent mouse mode standard mouse mo...
Page 351
Appendix b: accessing a paragon ii from the kx iii 339 kx iii-to-kx iii paragon cim guidelines the following system configuration guidelines should be followed when you are using paragon cims in a kx iii-to-kx iii configuration: concurrent access both kx iii kvm switches should be configured with th...
Page 352
Appendix b: accessing a paragon ii from the kx iii 340 if a connection to the target is in place from the other kx iii, the availability is checked when a connection is attempted. Access is denied or allowed consistent with the pc-share policy in place for the kx iii. Until that time, the availabili...
Page 353
Appendix b: accessing a paragon ii from the kx iii 341 paragon ii operation mode mode description supported? Port can be selected and controlled by more than one user, but only one user has keyboard and mouse control at any one time. Timeout, which is configured on the paragon ii, is not supported. ...
Page 354
Appendix b: accessing a paragon ii from the kx iii 342 connecting the paragon ii to the kx iii to connect the paragon ii system to a kx iii: 1. Check whether the paragon ii user station that you want to connect to the kx iii is implemented with version 4.6 firmware (or later). If not, upgrade it. Th...
Page 355
343 in this chapter overview ................................................................................................ 343 locate space in a cabinet for the kx iii ............................................... 344 add kx iii devices to dctrack ..................................................
Page 356
Appendix c: managing kx iii in dctrack 344 locate space in a cabinet for the kx iii use dctrack's capacity management functionality to locate space in a cabinet in your data center for the kx iii. Search by: rack units - dctrack looks for a cabinet with enough rack units open to accommodate the kx i...
Page 357
Appendix c: managing kx iii in dctrack 345 make and model - dctrack looks for a cabinet with enough available space in the cabinet based on the kx iii's dimensions, connectors, and so on see capacity management - locating and reserving cabinet space for an item in dctrack help. Add kx iii devices to...
Page 358
Appendix c: managing kx iii in dctrack 346 import kx iii devices into dctrack if you are adding a large number of kx iiis, complete the 02_items_- _all_other_classes_for_3.X.Xls spreadsheet, which is provided by raritan, with the kx iii information, then import the spreadsheet into dctrack ® using t...
Page 359
Appendix c: managing kx iii in dctrack 347 note that entire cabinets, along with the items in the cabinet and their connections and child devices, can also be cloned. So if you added a kx iii to a cabinet and use the same cabinet configuration throughout your data center, you can clone the cabinet. ...
Page 360
Appendix c: managing kx iii in dctrack 348 visualize the kx iii in a cabinet elevation and on the floor map when you add the kx iii to dctrack ® , you place it in a cabinet. Provided the data center location the cabinet belongs to has a floor map associated with it, and the cabinet the kx iii is hou...
Page 361
Appendix c: managing kx iii in dctrack 349 see locate an item on the floor map and items list (web client) in dctrack help. You can also view the kx iii in the cabinet elevation from the floor map. See cabinet elevations - floor map (web client) in dctrack help. Managing the kx iii lifecycle once th...
Page 362
Appendix c: managing kx iii in dctrack 350 decommission a kx iii to storage submit a request to decommission the kx iii to storage if you plan to temporarily move it to an off-site location. See submit a request to decommission an item to storage in dctrack help. Decommission a kx iii to archive sub...
Page 363
351 in this chapter hardware ............................................................................................... 351 software................................................................................................. 373 hardware kx iii dimensions and physical specifications domini...
Page 364
Appendix d: specifications 352 dominion kx iii model description power & heat dissipation dimensions (wxdxh) weight operating temp humidity 1 local port for use at the rack 52 kcal mm f dkx3-232 32 server ports 2 remote users 1 local port for use at the rack dual power 110v/240v, 50-60hz 1.8...
Page 365
Appendix d: specifications 353 dominion kx iii model description power & heat dissipation dimensions (wxdxh) weight operating temp humidity port for use at the rack dkx3-832 32 server ports 8 remote users 1 local port for use at the rack dual power 110v/240v, 50-60hz 1.8a 60w 52 kcal 17.3" x 1...
Page 366
Appendix d: specifications 354 kx iii supported target server video resolutions when using digital cims, you set the target's video resolution to match your monitor's native display resolution. The native display resolution is set when configuring ports for digital cims (see configure the cim target...
Page 367
Appendix d: specifications 355 1152x864@60hz 1152x864@70hz 1152x864@75hz 1152x864@85hz 1152x870@75.1hz 1280x720@60hz 1280x960@60hz 1280x960@85hz 1280x1024@60hz 1280x1024@75hz 1280x1024@85hz 1360x768@60hz 1366x768@60hz 1368x768@60hz 1400x1050@60hz 1440x900@60hz 1600x1200@60hz 1680x1050@60hz 1920x1080...
Page 368
Appendix d: specifications 356 kx iii supported local port dvi resolutions following are the resolutions supported when connecting to a dvi monitor from the kx iii local port. 1920x1080@60hz 1280x720@60hz 1024x768@60hz (default) 1024x768@75hz 1280x1024@60hz 1280x1024@75hz 1600x1200@60hz 800x480@60hz...
Page 369
Appendix d: specifications 357 supported computer interface module (cims) specifications digital cims support display data channels (ddc) and enhanced extended display identification data (e-edid). Note: both plugs must be plugged in for the hdmi and dvi cims. Cim model description dimensions (wxdxh...
Page 370
Appendix d: specifications 358 cim model description dimensions (wxdxh) weight d2cim-dvusb-dp digital cim that provides digital-to-analog conversion and support for: bios virtual media smartcard/cac audio absolute and relative mouse synchronization 1.7" x 3.5" x 0.8" 43 x 90 x 19mm 0.2...
Page 371
Appendix d: specifications 359 cim model description dimensions (wxdxh) weight dcim-ps2 cim for ps2 1.3" x 3.0" x 0.6" 33 x 76 x 15mm 0.20lb 0.09kg dcim-usbg2 cim for usb and sun usb 1.3" x 3.0" x 0.6" 33 x 76 x 15mm 0.20lb 0.09kg supported digital video cims for mac use a digital vi...
Page 372
Appendix d: specifications 360 if the mac’s hdmi or displayport video has a mini connector, a passive adapter cable may be required to connect to the full sized hdmi and displayport plugs on the digital cims. Alternatively, use the mac vga adapter with the d2cim-vusb or d2cim-dvusb. Note that this m...
Page 373
Appendix d: specifications 361 digital cim established modes 720x400@70hz ibm, vga 640x480@60hz ibm, vga 640x480@67hz apple mac ® ii 640x480@72hz vesa 640x480@75hz vesa 800x600@56hz vesa 800x600@60hz vesa 800x600@72hz vesa 800x600@75hz vesa 832x624@75hz apple mac ii 1024x768@60hz vesa 1024x768@70hz ...
Page 374
Appendix d: specifications 362 supported remote connections remote connection details network 10base-t, 100base-t, and 1000base-t (gigabit) ethernet protocols tcp/ip, udp, sntp, http, https, radius, ldap/ldaps network speed settings kx iii network speed setting network switch port setting auto 1000/...
Page 375
Appendix d: specifications 363 legend: does not function as expected supported functions; not recommended not supported by ethernet specification; product will communicate, but collisions will occur per ethernet specification, these should be “no communication,” however, note that the kx iii behavio...
Page 376
Appendix d: specifications 364 target server requirements when using smart card readers, the basic requirements for interoperability at the target server are: the ifd (smart card reader) handler must be a standard usb ccid device driver (comparable to the generic microsoft ® usb ccid driver). A digi...
Page 377
Appendix d: specifications 365 remote client requirements the basic requirements for interoperability at the remote client are: the ifd (smart card reader) handler must be a pc/sc compliant device driver. The icc (smart card) resource manager must be available and be pc/sc compliant. The jre ® java ...
Page 378
Appendix d: specifications 366 type vendor model verified usb scm microsystems scr331 verified on local and remote usb actividentity actividentity usb reader v3.0 verified on local and remote usb gemalto ® gempc usb-sw verified on local and remote usb keyboard/card reader combo dell ® usb smart card...
Page 379
Appendix d: specifications 367 audio playback and capture recommendations and requirements audio level set the target audio level to a mid-range setting. For example, on a windows ® client, set the audio to 50 or lower. This setting must be configured through the playback or capture audio device, no...
Page 380
Appendix d: specifications 368 in practice, the bandwidth used when an audio device connects to a target is higher due to the keyboard and video data consumed when opening and using an audio application on the target. A general recommendation is to have at least a 1.5mb connection before running pla...
Page 381
Appendix d: specifications 369 certified modems usrobotics ® 56k 5686e zoom ® v90 zoom v92 usrobotics sportster ® 56k usrobotics courier ™ 56k kx iii supported keyboard languages the kx iii provides keyboard support for the languages listed in the following table. Note: you can use the keyboard for ...
Page 382
Appendix d: specifications 370 language regions keyboard layout danish denmark danish swedish sweden swedish hungarian hungary hungarian slovenian slovenia slovenian italian italy italian spanish spain and most spanish speaking countries spanish portuguese portugal portuguese mac mini bios keystroke...
Page 383
Appendix d: specifications 371 keystroke description virtual media cim dual virtual media cim mac lion server hdmi cim button optical disc press n during startup start up from a compatible network server (netboot) press t during startup start up in target disk mode press shift during startup start u...
Page 384
Appendix d: specifications 372 port description https, port 443 this port can be configured as needed. See http and https port settings (on page 136). By default, this port is used for multiple purposes, including the web server for the html client, the download of client software (virtual kvm clien...
Page 385
Appendix d: specifications 373 software supported operating systems, browsers and java versions operating systems browsers java windows 7 ® home premium sp1 64-bit internet explorer ® 10, 11 firefox ® 29.0.1, 30 chrome ® 35 safari ® 7.0.3, 7.0.5 java ™ 1.7 up to update 60 windows 7 ultimate sp1 64-b...
Page 386
Appendix d: specifications 374 jre requirements and browser considerations for mac java runtime environment requirements for mac install java runtime environment 7 (jre) ® on pcs and macs ® when using the virtual kvm client (vkc) to access target servers via kx iii. This ensures in order to provide ...
Page 387
Appendix d: specifications 375 mode operating system browser windows server 2003 ® internet explorer 6.0 sp1++, 9.0, 10.0 or 11.0 firefox 1.06 - 3 windows vista ® internet explorer 9.0, 10.0 or 11.0 windows 7 ® internet explorer 9.0, 10.0 or 11.0 firefox 1.06 - 4 or later windows x64 64-bit mode win...
Page 388
Appendix d: specifications 376 events captured in the audit log and syslog following is a list and description of the events that are captured by the kx iii audit log and syslog: access login - a user has logged in to the kx iii access logout - a user has logged out of the kx iii active usb profile ...
Page 389
377 in this chapter overview ................................................................................................ 377 java runtime environment (jre) notes ............................................... 377 ipv6 support notes .................................................................
Page 390
Appendix e: informational notes 378 b. Click the view applets button. The java applet cache viewer opens. C. Deselect the enable caching checkbox if it is already checked. D. Click ok. 4. To clear the java cache: a. From the temporary files settings dialog, click the delete files button. The delete ...
Page 391
Appendix e: informational notes 379 ipv6 support notes operating system ipv6 support notes java java ™ 1.7 supports ipv6 for the following: solaris ™ 10 (and later) linux ® kernel 2.1.2 (and later)/redhat 6.1 (and later) solaris 10 (and later) windows xp ® sp1 and windows 2003 ® , windows vista ® an...
Page 392
Appendix e: informational notes 380 dual stack login performance issues if you are using the kx iii in a dual stack configuration, it is important you configured the domain system (dns) correctly in the kx iii in order to avoid delays when logging in. See tips for adding a web browser interface (on ...
Page 393
Appendix e: informational notes 381 windows 2000 composite usb device behavior for virtual media the windows 2000 ® operating system does not support usb composite devices, like raritan’s d2cim-vusb, in the same manner as non- composite usb devices. As a result, the “safely remove hardware” system t...
Page 394
Appendix e: informational notes 382 target server video picture not centered (mouse out of synch) at certain resolutions when using an hdmi or dvi cim with the kx iii: the video display may not be centered properly - black rectangles can be seen at the edges of the screen the mouse on the target may...
Page 395
Appendix e: informational notes 383 virtual media via vkc and akc in a windows environment windows xp ® operating system administrator and standard user privileges vary from those of the windows vista ® operating system and the windows 7 ® operating system. When enabled in vista or windows 7, user a...
Page 396
Appendix e: informational notes 384 virtual media support on windows 7, windows 2008 and windows xp targets virtual media is not supported on a windows 7, windows 2008 or windows xp target server when connecting via vkc and akc from windows 2008 or windows 2012. Virtual media not refreshed after fil...
Page 397
Appendix e: informational notes 385 2. Restart the target. Virtual media connection failures using high speed for virtual media connections under certain circumstances it may be necessary to select the "use full speed for virtual media cim" when a target has problems with "high speed usb" connection...
Page 398
Appendix e: informational notes 386 usb profile help appears in the usb profile help window. For detailed information about specific usb profiles, see available usb profiles. Raritan provides a standard selection of usb configuration profiles for a wide range of operating system and bios level serve...
Page 399
Appendix e: informational notes 387 changing a usb profile when using a smart card reader there may be certain circumstances under which you will need to change the usb profile for a target server. For example, you may need to change the connection speed to "use full speed for virtual media cim" whe...
Page 400
Appendix e: informational notes 388 black stripe/bar(s) displayed on the local port certain servers and video resolutions may display on the local port with small black bars at the edge of the screen. If this occurs: 1. Try a different resolution, or 2. If using a digital cim, then change the displa...
Page 401
Appendix e: informational notes 389 keyboard notes french keyboard caret symbol (linux clients only) the virtual kvm client (vkc) do not process the key combination of alt gr + 9 as the caret symbol (^) when using french keyboards with linux ® clients. To obtain the caret symbol: from a french keybo...
Page 402
Appendix e: informational notes 390 tilde symbol from the virtual kvm client (vkc), the key combination of alt gr + 2 does not produce the tilde (~) symbol when using a french keyboard. To obtain the tilde symbol: create a macro consisting of the following commands: press right alt press 2 release 2...
Page 403
Appendix e: informational notes 391 note: the keyboard indicator should be used on linux systems using gnome as a desktop environment. When using a hungarian keyboard from a linux client, the latin letter u with double acute and the latin letter o with double acute work only with jre 1.6 (and later)...
Page 404
Appendix e: informational notes 392 mac keyboard keys not supported for remote access when a mac ® is used as the client, the following keys on the mac ® keyboard are not captured by the java ™ runtime environment (jre ™ ): f9 f10 f11 f14 f15 volume up volume down mute eject as a result, the virtual...
Page 405
Appendix e: informational notes 393 audio audio playback and capture issues features that may interrupt an audio connection if you use any of the following features while connected to an audio device, your audio connection may be interrupted. Raritan recommends you do not use these features if you a...
Page 406
Appendix e: informational notes 394 audio in a windows environment on windows ® 64-bit clients, only one playback device is listed on the connect audio panel when accessing the device through the virtual kvm client (vkc). The audio device is the default device, and is listed on the connect audio pan...
Page 407
395 in this chapter general faqs ........................................................................................ 395 remote access ..................................................................................... 397 universal virtual media .................................................
Page 408
Appendix f: frequently asked questions 396 question answer what is dominion kx iii? Dominion kx iii is a third-generation digital kvm (keyboard, video, mouse) switch that enables one, two, four or eight it administrators to access and control 8, 16, 32 or 64 servers over the network with bios-level ...
Page 409
Appendix f: frequently asked questions 397 question answer how does dominion kx iii differ from remote control software? When using dominion kx iii remotely, the interface, at first glance, may seem similar to remote control software such as pcanywhere tm , windows ® terminal services/remote desktop...
Page 410
Appendix f: frequently asked questions 398 question answer how many users can remotely access servers on each dominion kx iii? Dominion kx iii models offer remote connections for up to eight users per user channel to simultaneously access and control a unique target server. For one-channel devices l...
Page 411
Appendix f: frequently asked questions 399 question answer what is the file size of the applet that’s used to access dominion kx iii? How long does it take to retrieve? The virtual kvm client (vkc) applet used to access dominion kx iii is approximately 500kb in size. The following chart describes th...
Page 412
Appendix f: frequently asked questions 400 question answer do you support servers with dual video cards? Yes, dual video cards are supported with an extended desktop configuration available to the remote user. How do i access servers connected to dominion kx iii if the network ever becomes unavailab...
Page 413
Appendix f: frequently asked questions 401 question answer what is required for virtual media? A dominion kx iii virtual media cim is required. There are two vga-based cims: a d2cim- vusb or d2cim-dvusb. The d2cim-vusb has a single usb connector and is for customers who will use virtual media at the...
Page 414
Appendix f: frequently asked questions 402 question answer why would i use a usb profile? Usb profiles are most often required at the bios level where there may not be full support for the usb specification when accessing virtual media drives. However, profiles are sometimes used at the os level, fo...
Page 415
Appendix f: frequently asked questions 403 question answer how is bandwidth used in kvm- over-ip systems? Dominion kx iii offers totally new video processing that provides flexible, high performance video, efficient use of bandwidth and anytime/anywhere access via lan, wan or internet. The dominion ...
Page 416
Appendix f: frequently asked questions 404 question answer what factors affect bandwidth? There are many factors that determine how much bandwidth will be used. The primary factor, noted above, is the amount of change in the target server’s video display. This is dependent on the user’s task and act...
Page 417
Appendix f: frequently asked questions 405 question answer how do i optimize performance and bandwidth? Kx iii provides a variety of settings in our remote clients for the user to optimize bandwidth and performance. The default settings will provide an at-the-rack level of performance in standard la...
Page 418
Appendix f: frequently asked questions 406 question answer what is the maximum remote (over ip) video resolution supported? The dominion kx iii is the first and only kvm- over-ip switch to support full high definition (hd) remote video resolution – 1920x1080 at frame rates up to 30 frames per second...
Page 419
Appendix f: frequently asked questions 407 question answer why does kx iii support ipv6 networking? U.S. Government agencies and the department of defense are now mandated to purchase ipv6- compatible products. In addition, many enterprises and foreign countries, such as china, will be transitioning...
Page 420
Appendix f: frequently asked questions 408 question answer what should i do to prepare a server for connection to dominion kx iii? Set the mouse parameter options to provide users with the best mouse synchronization and turn off screensavers and any power management features that affect screen displ...
Page 421
Appendix f: frequently asked questions 409 question answer do i have to use hotkeys to switch between blades? Some blade servers require you to use hotkeys to switch between blades. With the dominion kx iii, you don’t have to use these hotkeys. Just click on the name of the blade server, and the dom...
Page 422
Appendix f: frequently asked questions 410 question answer is absolute mouse synchronization supported? Servers with internal kvm switches inside the blade chassis typically do not support absolute mouse technology. For hp blade and some dell blade servers, a cim can be connected to each blade, so a...
Page 423
Appendix f: frequently asked questions 411 question answer how far can my servers be from dominion kx iii? In general, servers can be up to 150 feet (45 m) away from dominion kx iii, depending on the type of server. (see target server video resolution supported connection distances and refresh rates...
Page 424
Appendix f: frequently asked questions 412 question answer how do i connect a serially controlled (rs-232) device, such as a cisco router/switch or a headless sun server, to dominion kx iii? If there are only a few serially controlled devices, they may be connected to a dominion kx iii using raritan...
Page 425
Appendix f: frequently asked questions 413 question answer can i use a usb keyboard or mouse at the local port? Yes. The dominion kx iii has usb keyboard and mouse ports on the local port. Dominion kx iii switches do not have ps/2 local ports. Customers with ps/2 keyboards and mice should utilize a ...
Page 426
Appendix f: frequently asked questions 414 question answer what is the extended local port? The dominion kx2-808, kx2-832 and kx2-864 featured an extended local port. The corresponding dominion kx iii models do not have an extended local port. Instead all kx iii models have a tiering port. To extend...
Page 427
Appendix f: frequently asked questions 415 question answer what type of power strips does dominion kx iii support? Raritan’s dominion px ™ and remote power control (rpc) power strips. These come in many outlet, connector and amp variations. Note that you should not connect the pm series of power str...
Page 428
Appendix f: frequently asked questions 416 question answer can i access dominion kx iii over a wireless connection? Yes. Dominion kx iii not only uses standard ethernet, but also very conservative bandwidth with very high quality video. Thus, if a wireless client has network connectivity to a domini...
Page 429
Appendix f: frequently asked questions 417 question answer i’m having problems connecting to the dominion kx iii over my ip network. What could be the problem? The dominion kx iii relies on your lan/wan network. Some possible problems include: ethernet auto-negotiation. On some networks, 10/100 auto...
Page 430
Appendix f: frequently asked questions 418 question answer how do i physically connect multiple dominion kx iii devices together into one solution? To physically connect multiple kx iii devices together for consolidated local access, you can connect the tiering ports of multiple "tiered" (or "cascad...
Page 431
Appendix f: frequently asked questions 419 question answer do i have to physically connect dominion kx iii devices together? Multiple dominion kx iii units do not need to be physically connected together. Instead, each dominion kx iii unit connects to the network, and they automatically work togethe...
Page 432
Appendix f: frequently asked questions 420 question answer what type of video is supported by your cims? Our cims have traditionally supported analog vga video. Three new cims support digital video formats, including dvi, hdmi and displayport. These are the d2cim-dvusb- dvi, d2cim-dvusb-hdmi and d2c...
Page 433
Appendix f: frequently asked questions 421 question answer is the dominion kx iii fips 140-2 certified? The dominion kx iii uses an embedded fips 140-2 validated cryptographic module running on a linux platform per fips 140-2 implementation guidelines. This cryptographic module is used for encryptio...
Page 434
Appendix f: frequently asked questions 422 question answer does dominion kx iii support strong passwords? Yes. The dominion kx iii has administrator- configurable, strong password checking to ensure that user-created passwords meet corporate and/or government standards and are resistant to brute for...
Page 435
Appendix f: frequently asked questions 423 question answer which cims support smart card/cac? The d2cim-dvusb, d2cim-dvusb-dvi, d2cim-dvusb-hdmi and d2cim-dvusb- dp are the required cims. Which smart card readers are supported? The required reader standards are usb ccid and pc/sc. Consult the user d...
Page 436
Appendix f: frequently asked questions 424 question answer can dominion kx iii integrate with syslog? Yes. In addition to domin ion kx iii’s own internal logging capabilities, dominion kx iii can send all logged events to a centralized syslog server. Can dominion kx iii integrate with snmp? Yes. In ...
Page 437
Appendix f: frequently asked questions 425 question answer what cim should i use for a particular server? Consult the cim guide available with the kx iii documentation. Note that dvi, hdmi and displayport video standards are supported with the digital video cims. How long is the hardware warranty fo...
Page 438
Appendix f: frequently asked questions 426 question answer how do i migrate from the dominion kx ii to dominion kx iii? In general, kx ii customers can continue to use their existing switches for many years. As their data centers expand, customers can purchase and use the new kx iii models. Raritan’...
Page 439: Index
427 a a. Ac power • 25 about connecti on properties • 252 about the cat5 reach dvi • 332 absolute mouse mode • 304, 305 absolute mouse synchronization • 267 accent symbol (windows xp operating system clients only) • 389 access a target server from the kx iii • 39 access a virtual media drive on a cl...
Page 440
Index 428 calibrating color • 263 cannot connect to drives from linux clients • 382 cannot write to/from a file from a mac cl ient • 382 caret symbol (linux clients only) • 389 cc- sg notes • 394 certified modems • 147, 369 change the default password • 28 change the keyboard layout code (sun target...
Page 441
Index 429 connect to virtual media • 280 connecting a kx iii and cat5 reach dvi - provide extended local port functionality • 332, 414 connecting a rack pdu • 98 connecting and disconnecting from a digital audio device • 288, 289 connecting and disconnecting from virtual media • 243 connecting the p...
Page 442
Index 430 encryption & share • 181, 185, 330 enter intelligent mouse mode • 267 entering the discovery port • 136 ethernet and ip networking • 415 event management • 156 events captured in the audit log and syslog • 192, 376 example 1 import the certificate into the browser • 11, 14 example 2 add th...
Page 443
Index 431 keyboard limitations • 272 keyboard macros • 259 keyboard notes • 389 kx iii administration • 18 kx iii device photos and features • 2 kx iii dimensions and physical specifications • 351 kx iii installation and confi guration • 19 kx iii kvm client applications • 8 kx iii local console • 2...
Page 444
Index 432 naming the rack pdu (port page for power strips) • 99 navigation of the cli • 216 network basic settings • 79 network interface page • 204 network settings • 77, 372 network speed settings • 86, 362 network statistics page • 204 noise filter • 255 note on microsoft active directory • 38 no...
Page 445
Index 433 returning user group information via radius • 73 root user permission requirement • 246 s saving audio settings • 288, 289 scaling • 279 scan for targets • 313 scan for targets - local console • 327 scanning port slide show - local console • 324 scanning ports - local console • 310, 323 sc...
Page 446
Index 434 sun solaris mouse settings • 24 supported audio device formats • 284 supported blade chassis models • 102, 111, 115, 123 supported cims for blade chassis • 102, 111, 115, 123 supported computer interface module (cims) specifications • 23, 44, 224, 281, 357 supported connection distances be...
Page 447
Index 435 view status bar • 279 view the kx iii users list • 61 view toolbar • 279 view users by port • 61 viewing the kx iii mib • 145, 156, 161 virtual kvm client (vkc) and active kvm client (akc) requirements • 374 virtual kvm client (vkc) help • 8, 111, 248, 294, 399 virtual kvm client (vkc) sma...
Page 448
U.S./canada/latin america monday - friday 8 a.M. - 6 p.M. Et phone: 800-724-8090 or 732-764-8886 for commandcenter noc: press 6, then press 1 for commandcenter secure gateway: press 6, then press 2 fax: 732-764-8887 email for commandcenter noc: tech-ccnoc@raritan.Com email for all other products: te...