- DL manuals
- 3Com
- Switch
- 3CRWX120695A
- Reference Manual
3Com 3CRWX120695A Reference Manual
Summary of 3CRWX120695A
Page 1
Http://www.3com.Com/ part no. 730-9502-0077, revision b published november 2004 wireless lan mobility system wireless lan switch manager reference manual 3crwx120695a, 3crwx440095a.
Page 2
3com corporation 350 campus drive marlborough, ma usa 01752-3064 copyright © 2004, 3com corporation. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) without writt...
Page 3: Ontents
C ontents a bout t his g uide conventions 15 documentation 16 documentation comments 17 1 i nstalling 3wxm hardware requirements 19 hardware requirements for 3wxm client 19 hardware requirements for 3wxm monitoring service 20 software requirements 20 preparing for installation 21 user privileges 21 ...
Page 4
Alerts panel 51 content panel 53 monitor tab 53 managed devices tab 58 verification tab 59 events tab 60 rogue detection tab 60 information panel 62 configuration wizards 62 reports 66 copying and pasting objects 67 copy and paste 68 copy and paste replace 68 enabling keyboard shortcut mnemonics (wi...
Page 5
4 p lanning the 3c om m obility s ystem building wizard overview 93 accessing the building wizard 93 creating a site 101 to create a site when you create a network plan 102 to create a site in a saved network plan 104 creating or modifying buildings in a site 106 modifying floor defaults 108 importi...
Page 6: Wx S
Generating rf network design information 171 accessing the report page 171 reviewing layout information 172 reviewing the map list 172 generating a work order 173 applying rf auto-tuning settings to the network plan 175 5 c onfiguring wx s ystem and a dministrative p arameters wx switch wizard overv...
Page 7
Configuring wired authentication ports 229 configuring network ports 231 configuring load sharing 235 load sharing 235 link redundancy 235 configuration changes based on port groups 235 to configure load sharing 235 configuring ip services 238 configuring static routes 238 configuring ip aliases 242...
Page 8: Wx S
7 c onfiguring a uthentication , a uthorization , and a ccounting p arameters overview 291 connecting to radius servers and server groups 292 defining radius default values 293 defining radius servers 295 defining radius server groups 298 creating and managing users in the local user database 301 cr...
Page 9
Toolbar options 374 filtering the message list 374 resolving an error or warning 375 disabling a rule from the message list 375 changing verification options 376 disabling and reenabling rules 378 synchronizing local and network changes 383 change management options 384 toolbar options 385 managing ...
Page 10
10 m onitoring the n etwork overview 411 monitoring service requirements 412 accessing monitored data 412 using the explore window 413 toolbar options 414 threshold flags 416 displaying object details 417 displaying 802.11 coverage 417 taking rf measurements 419 using the status summary window 420 u...
Page 11
11 d etecting and c ombatting r ogue d evices overview 469 rogue access points and users 469 ad hoc users 469 rf detection scans 470 countermeasures 470 rogue detection requirements 471 mobility domain 471 snmp traps 471 monitoring service 471 enabling countermeasures 472 using the rogue detection t...
Page 12: 3Wxm W
Generating a rogue details report 495 generating a rogue summary report 496 generating a work order 497 a u sing 3wxm w ith hp o pen v iew preparing to use hp openview and 3wxm 499 starting 3wxm from network node manager 499 b c hanging 3wxm p references overview 501 resetting preferences values 502...
Page 13
Accessing the monitoring service log 558 backing up the database 558 restoring the database 558 e o btaining s upport for your p roduct register your product 561 purchase value-added services 561 troubleshoot online 561 access software downloads 562 telephone technical support and repair 562 contact...
Page 15: Bout
A bout t his g uide this manual shows you how to plan, configure, deploy, and manage a mobility system wireless lan (wlan) using the 3com wireless lan switch manager (3wxm). Read this manual if you are a network administrator or a person responsible for managing a wlan. If release notes are shipped ...
Page 16
16 a bout t his g uide this manual uses the following text and syntax conventions: documentation the 3wxm documentation set includes the following documents. ■ wireless lan switch manager (3wxm) release notes these notes provide information about the system software release, including new features a...
Page 17
Documentation comments 17 ■ wireless lan switch manager reference manual this manual shows you how to plan, configure, deploy, and manage a mobility system wireless lan (wlan) using the 3com wireless lan switch manager (3wxm). ■ wireless lan switch and controller installation and basic configuration...
Page 18
18 a bout t his g uide.
Page 19: Nstalling
1 i nstalling 3wxm this chapter describes how to install 3com wireless lan switch manager (3wxm). Hardware requirements 3wxm can be utilized with a client/server deployment or both client and monitoring services can be run on the same machine. The monitoring service is used for collecting historical...
Page 20
20 c hapter 1: i nstalling 3wxm hardware requirements for 3wxm monitoring service table 4 shows the minimum and recommended requirements to run the 3wxm monitoring service. Table 5 contains general recommended guidelines for hardware requirements and memory allocation based on the number of radios a...
Page 21
Preparing for installation 21 you must use the english version of the operating system you select. Operating system versions in other languages are not supported with 3wxm. The following additional software is required for certain 3wxm features: ■ hp openview network node manager 6.4 or later—must b...
Page 22
22 c hapter 1: i nstalling 3wxm 3com recommends that larger installations (12 or more switches or greater than 500 aps) not use the same machine for site planning with the 3wxm client and for running the optional monitoring service. Each of these features requires system resources. Using all feature...
Page 23
Using the installation wizard 23 2 go to “using the installation wizard” on page 23. Using the installation wizard to use the installation wizard: 1 on the choose installation type page, choose one of the following: ■ to install 3wxm, click the 3wxm icon. ■ to install 3wxm and the plug-in required t...
Page 24
24 c hapter 1: i nstalling 3wxm 3 after reading the 3wxm license agreement, select whether to accept the terms of the agreement. (if you choose not to accept the terms of the license agreement, you cannot proceed with the installation.) 4 click next. The choose install folder page appears..
Page 25
Using the installation wizard 25 5 type the name of the directory in which to install 3wxm, or accept the default. The default installation directory is c:\program files\3com\wireless switch manager. You can also type a directory name in the box, or select a directory by clicking choose and browsing...
Page 26
26 c hapter 1: i nstalling 3wxm 9 to install the 3wxm monitoring service on this machine in addition to 3wxm, leave install 3wxm services selected. Otherwise, click to deselect the option. The monitoring service is not required to configure and manage wx switches. However, data provided by the monit...
Page 27
Using the installation wizard 27 12 check the installation summary information. Click previous to make any changes to previous pages. 13 click install. The installer installs the 3wxm client application (3wxm). The monitoring service also is installed, if you left this option selected. When installa...
Page 28
28 c hapter 1: i nstalling 3wxm 14 click done. See “getting started” on page 71 for more information on getting started with 3wxm. Installing the hp openview plug-in to install the hp openview plug-in: 1 complete step 10 of the procedure in “using the installation wizard” on page 23. 2 in the choose...
Page 29
Installing the hp openview plug-in 29 3 to specify the directory in which hp openview network node manager is installed, click choose. Network node manager must be already be installed on the system. You must specify the correct directory for network node manager for the hp openview plug-in to be in...
Page 30
30 c hapter 1: i nstalling 3wxm 5 if you already have a network plan, type the name of the network plan to be opened by 3wxm when used in conjunction with hp openview network node manager. 6 click next to display the pre-installation summary page. 7 check the installation summary information. Click ...
Page 31
Upgrading 3wxm 31 upgrading 3wxm you can upgrade 3wxm by installing a newer version of 3wxm over a previous version. You do not need to uninstall the previous version before installing a newer version. Before you upgrade, 3com recommends that you make a backup of the xml directory in the 3wxm instal...
Page 32
32 c hapter 1: i nstalling 3wxm by default, the following are removed when you uninstall the client application: ■ network plans ■ access control if the monitoring service was also installed, the monitoring service’s database directory is also uninstalled by default. The database directory contains ...
Page 33
Uninstalling 3wxm 33.
Page 34
34 c hapter 1: i nstalling 3wxm.
Page 35: Orking
2 w orking with the 3wxm u ser i nterface this chapter describes how to use the 3com wireless lan switch manager (3wxm) interface. Overview a network plan is the workspace in 3wxm you use to design a 3com network. In a network plan, you define components of the network (wx switches, map access point...
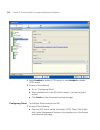
Page 36
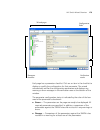
36 c hapter 2: w orking with the 3wxm u ser i nterface figure 1 main 3wxm window the main 3wxm window contains a toolbar with menu categories. Underneath the categories are icons for frequently used menu options. The window also contains panels for navigating to and displaying information. The main ...
Page 37
Toolbar options in main 3wxm window 37 ■ content panel — displays monitored data for objects. The content panel is located to the right of the organizer panel. ■ alerts panel — displays summary statistics for configuration changes or errors and for rogue access points detected in the 3com mobility d...
Page 38
38 c hapter 2: w orking with the 3wxm u ser i nterface table 6 main toolbar options toolbar menu menu option description file (new) create a new network plan. (open) open a network plan. Close close a network plan. (delete network plan) delete a network plan. (save) save a network plan. (save as) sa...
Page 39
Toolbar options in main 3wxm window 39 (paste replace) replace the object that is selected in the organizer panel with the object you copied. (delete) delete the selected object(s). View (monitor) view monitored data for the object selected in the organizer panel. This opens the monitor tab in the c...
Page 40
40 c hapter 2: w orking with the 3wxm u ser i nterface (toolbars) toggle display of toolbar icons. Icons for selected toolbar categories are displayed under the row of toolbar categories. Changes (upload) upload a wx configuration into 3wxm. (move wireless switch) move a wx switch. (policy manager) ...
Page 41
Toolbar options in main 3wxm window 41 (mobility domain configuration) generate a report of the major configuration parameters of all the wx switches in the mobility domain. (wx configuration) generate a report of the configuration parameters of a specific wx switch. (client summary) generate a repo...
Page 42
42 c hapter 2: w orking with the 3wxm u ser i nterface (work order) generate a work order for installing 3com equipment. Tools (preferences) change 3wxm user preferences. (access control) manage 3wxm user accounts. (certificate management) manage certificates. (image repository) open the system imag...
Page 43
Organizer panel 43 organizer panel the organizer panel provides a tree-like view of the 3com equipment and site data managed by 3wxm. The organizer panel contains the following sections: ■ mobility domains — roaming domains of 3com switches and map access points within which network clients can roam...
Page 44
44 c hapter 2: w orking with the 3wxm u ser i nterface ■ third party aps — third-party access points that 3wxm needs to be aware of while planning or monitoring the network. The mobility domains section is expanded by default. To display the objects in a section of the organizer panel, click on the ...
Page 45
Organizer panel 45 ■ sites — the display is restricted to coverage areas. Objects for individual access points are not displayed, although you can expand a coverage area to list the individual 3com radios in the coverage area. However, regardless of whether details is enabled, you can drill down to ...
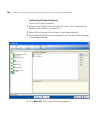
Page 46
46 c hapter 2: w orking with the 3wxm u ser i nterface monitored information for an object, right-click on the object in the organizer panel and select monitor or monitor in new window. Mobility domain objects the mobility domains section of the organizer panel contains configuration objects for 3co...
Page 47
Organizer panel 47 a mobility domain also contains individual wx switches. Wx switches can be added to a mobility domain by 3wxm as part of network planning. You also can add a switch running in the live network by uploading it into 3wxm, or you can create a new switch with the wx switch wizard (see...
Page 48
48 c hapter 2: w orking with the 3wxm u ser i nterface table 7 domain policies objects object description management services settings for the following management services: ■ https — controls web management access to the wx switches. ■ telnet — controls telnet management access to the wx switches. ...
Page 49
Organizer panel 49 table 8 lists the wx switch objects. These objects control configuration parameters for an individual wx switch. Aaa settings for authentication, authorization, and accounting (aaa) parameters: ■ radius servers ■ local user database (configured on the wx switch instead of on the r...
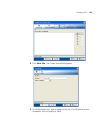
Page 50
50 c hapter 2: w orking with the 3wxm u ser i nterface table 9 lists the rogue detection objects. These objects control configuration parameters for rogue detection. Site objects the sites section of the organizer panel contains objects for the buildings where you want to deploy 3com equipment. A si...
Page 51
Alerts panel 51 third-party aps the third party aps section of the organizer panel contains objects for third-party access points. 3wxm takes these third-party access points into consideration when calculating map access point placement, channel settings, and power settings. In addition, wx switches...
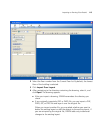
Page 52
52 c hapter 2: w orking with the 3wxm u ser i nterface to navigate to more information and correct the warning or error, click on the arrow to expand the panel, then click on the statistic to open the corresponding tab in the content panel. Table 11 lists the types of alerts displayed in the alerts ...
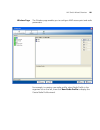
Page 53
Content panel 53 content panel the content panel displays information for objects selected in the organizer panel, or for options selected from the view toolbar option of the main 3wxm window. Information is displayed in the following tabs: ■ monitor ■ managed devices ■ verification ■ events ■ rogue...
Page 54
54 c hapter 2: w orking with the 3wxm u ser i nterface the monitor tab has a toolbar with options to navigate to the windows listed above, to switch the view to the previous or next monitored object, and to reorganize the windows within the tab. Hold the cursor over a toolbar option to display a des...
Page 55
Content panel 55 select the floor or you select a wiring closet, coverage area, map, or radio on the floor. Floor views are available only if you add the floor to the site information in the network plan. Here is an example of the view when a mobility domain is selected. In either view, the operatio...
Page 56
56 c hapter 2: w orking with the 3wxm u ser i nterface properties. To create a new instance of an object (where applicable), right-click on the object’s icon and select insert. Monitor tab — status summary window the status summary window shows the operational status of 3com equipment (wx switches, ...
Page 57
Content panel 57 monitor tab — client monitor window the client monitor window shows detailed information about client activity on the network. Client information is displayed in the following tabs: ■ client activity — displays association and 802.1x information for the clients ■ client sessions — l...
Page 58
58 c hapter 2: w orking with the 3wxm u ser i nterface monitor tab — rf monitor window the rf monitor window shows detailed rf information for each radio. Radio information is displayed in the following tabs: ■ rf neighborhood — lists the other transmitting devices that the radio can hear. ■ ssid-bs...
Page 59
Content panel 59 verification tab the verification tab enables you to troubleshoot configuration issues on wx switches in the network plan or in the live network. Warning or error messages are displayed to indicate issues. You can fix configuration errors and verify the results. If you want to inste...
Page 60
60 c hapter 2: w orking with the 3wxm u ser i nterface events tab the events tab displays log messages for 3wxm, the monitoring service, and for wx switches. To display the events tab, select view > events from the main 3wxm toolbar. Rogue detection tab the rogue detection tab lists information abou...
Page 61
Content panel 61 you can display data about rogues that are currently in operation as well as currently inactive rogues that were detected in the past. You can even display the estimated physical location of a rogue..
Page 62
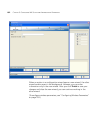
62 c hapter 2: w orking with the 3wxm u ser i nterface information panel the information panel displays details about the object selected in the organizer panel. For example, if a wx switch is selected, details about the switch are displayed. Configuration wizards 3wxm provides configuration wizards...
Page 63
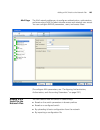
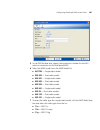
Configuration wizards 63 most wizards contain multiple pages, and buttons at the top of the wizard to allow direct access to the pages. You also can click the next and previous buttons at the bottom of the wizard to navigate among the wizard’s pages. The finish button saves the changes you make in t...
Page 64
64 c hapter 2: w orking with the 3wxm u ser i nterface clicking the new radius server button opens the create radius server wizard. The modify radius server wizard remains open in the background. After you enter information in the create radius server wizard and click.
Page 65
Configuration wizards 65 finish, the modify radius server returns to the foreground. The new server added with the create radius server wizard appears in the server list. Most of the configuration wizards in 3wxm are similar to the modify radius server wizard. Two of the wizards are more complex: ■ ...
Page 66
66 c hapter 2: w orking with the 3wxm u ser i nterface reports the reports option of the main toolbar enables you to generate reports for network clients, rf usage, rogue devices, and 3com equipment. ■ 3com equipment reports: ■ inventory report ■ mobility domain configuration ■ wx configuration ■ ne...
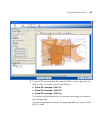
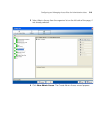
Page 67
Copying and pasting objects 67 here is an example of a wx configuration report. Copying and pasting objects 3wxm allows you to duplicate objects, using the copy, paste, and paste replace options. ■ use the copy and paste options to create a new object. ■ use the copy and paste replace options to rep...
Page 68
68 c hapter 2: w orking with the 3wxm u ser i nterface successfully create the object, you must change its unique attributes (for example, wx name). If the object is a parent of other objects, all the child objects are also created or replaced (depending on the paste action). After an object is copi...
Page 69
Enabling keyboard shortcut mnemonics (windows xp only) 69 after you click finish to close the configuration wizard, the new object appears. For example, to copy a radius server from one wx switch to another: 1 expand the view of a mobility domain in the organizer panel to display the wx switches in ...
Page 70
70 c hapter 2: w orking with the 3wxm u ser i nterface 3 click effects. 4 clear the box labeled hide underlined letters for keyboard navigation until i press the alt key. Clearing this option allows programs to show the underlined character for mnemonics in 3wxm. 5 click ok. 6 in the display propert...
Page 71: Etting
3 g etting s tarted this chapter contains information about starting 3com wireless lan switch manager (3wxm), restricting access to 3wxm, creating and managing network plans, and defining a mobility domain. Starting 3wxm the following steps describe how to start 3wxm. 1 to start 3wxm, select start >...
Page 72
72 c hapter 3: g etting s tarted 3 click get activation key. A 3com web page appears. Register your copy of 3wxm and the license in order to obtain an activation key. 4 copy the activation key from the web page and paste it into the activation key box of the activation key page. 5 if you plan to man...
Page 73
Starting 3wxm 73 6 type the upgrade license key in the license key box and click next. The activation key page appears. 7 click get activation key. A 3com web page appears. Register your upgrade license in order to obtain its activation key..
Page 74
74 c hapter 3: g etting s tarted 8 copy the activation key for the upgrade license from the web page and paste it into the activation key box of the activation key page. 9 click finish. 10 after you enter the license information, the 3wxm main window and the options dialog box appear. In the options...
Page 75
Restricting access to 3wxm 75 if you have already saved network plans, you can open one of the last seven saved network plans. Select the network plan you want to open, and click next. Click finish to display the network plan information in the 3wxm window. ■ close the options dialog box, by clickin...
Page 76
76 c hapter 3: g etting s tarted to create an administrator account: 1 select tools > access control. The access control dialog box appears. 2 select allow only specific accounts to use the application. The add account dialog box appears. The name of the user currently logged in appears in the accou...
Page 77
Restricting access to 3wxm 77 creating provision or monitor accounts to create a provision or monitor account: 1 select tools > access control. The access control dialog box appears. 2 to add a provision user account, click add provision account. To add a monitor account, click add monitor account. ...
Page 78
78 c hapter 3: g etting s tarted to disable access control: 1 select tools > access control. The access control dialog box appears. 2 click allow all accounts on this computer to use the application. All 3wxm accounts that were created are deleted. 3 to save changes and close the access control dial...
Page 79
Creating and managing network plans 79 to create a network plan 1 from the main 3wxm window, select file > new. The options wizard appears. 2 in the network plan name box, type a name for the network plan. You can use 1 to 60 alphanumeric characters, with no spaces, tabs, or any of the following: sl...
Page 80
80 c hapter 3: g etting s tarted selections for 802.11a and 802.11b/g radios later in the planning process or allow wx switches to set the channels automatically. 5 do one of the following: ■ if you intend to use the physical planning features, click next to configure site information. Go to “planni...
Page 81
Creating and managing network plans 81 to save a network plan: 1 in the main 3wxm window, select file > save. 2 click finish. You can also save a network plan with a new name, enable the autosave option so that a network plan is saved at specified intervals, and save a version of a network plan..
Page 82
82 c hapter 3: g etting s tarted saving a network plan with a new name you can save a network plan with a new name by using the save as feature. To save a network plan with a new name: 1 in the main 3wxm window, select file > save as. The save as network plan wizard appears. 2 in specify plan name, ...
Page 83
Creating and managing network plans 83 if you need to roll back configuration changes, you can use a saved version to roll back the system software image and configuration files to a known state. Before you can save a version of a network plan, you need to deploy and save the network plan. Versions ...
Page 84
84 c hapter 3: g etting s tarted 3 select auto save changes. 4 in the save interval box, type the interval, from 1 to 1440 minutes (24 hours). The default value is 10 minutes. 5 click close. Network plan changes are automatically saved at the interval you specify. Saving versions of a network plan y...
Page 85
Creating and managing network plans 85 to open a network plan: 1 in the main 3xm window, select file > open. The open network plan wizard appears. 2 select the network plan you want to open. 3 click next. 4 click finish. The network plan information appears in the 3wxm window. Closing a network plan...
Page 86
86 c hapter 3: g etting s tarted deleting a network plan you can delete a network plan at any time. Caution: the delete network plan wizard has a cancel button, but this button does not cancel deletion of a network plan. 3wxm deletes the plan as soon as you click finish. To delete a network plan: 1 ...
Page 87
Creating and managing network plans 87 a new installation of 3wxm does not contain the xml/db directory until a plan is created. Only one user at a time can edit a network plan. When a user with an administrator or provision account tries to open a plan that is already open for edit by another user,...
Page 88
88 c hapter 3: g etting s tarted if you override the lock, 3wxm obtains the lock and notifies the other 3wxm users about the lock change. From this point on, the former lock holder cannot save any current or future changes to the plan. By default, 3wxm sends a message to all users who have the plan ...
Page 89
Defining a mobility domain 89 roaming behavior for a client session to be considered a roaming session (and not a new session), the following criteria must be met: ■ the client associates or reassociates with a map in the mobility domain, and the client already has a session on a different map in th...
Page 90
90 c hapter 3: g etting s tarted roaming creates the following effects: ■ remote authentication dial-in user service (radius) accounting is treated as a continuation of an existing session, rather than a new one. ■ for tracked users, you can view roaming history in the monitor tab. See “using the cl...
Page 91
Defining a mobility domain 91 the traffic typically sent between wx switches within a mobility domain uses ip/udp protocol 17 traffic on port 8817 for both source and destination. Roaming traffic uses ip protocol 4. Creating a mobility domain to create a mobility domain, follow these steps. 1 access...
Page 92
92 c hapter 3: g etting s tarted 4 do one of the following: ■ to close the wizard, click finish. ■ to create a wx switch and add it to the mobility domain, see “adding a wx switch to the network plan” on page 183..
Page 93: Lanning
4 p lanning the 3c om m obility s ystem the 3com wireless lan switch manager (3wxm) planning tools help you plan your mobility system. This chapter discusses the building wizard and describes how to create a site, create or modify buildings, import or draw floor details, specify the rf characteristi...
Page 94
94 c hapter 4: p lanning the 3c om m obility s ystem depending on how you access the wizard, the wizard’s title can be create building, modify building, create floor, or modify floor. The wizard is the same regardless of the title. The building wizard contains the following pages: ■ setup ■ edit con...
Page 95
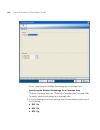
Building wizard overview 95 building wizard — setup page the setup page (shown above) enables you to configure basic building parameters including the building name, number of floors for which you want to plan wireless coverage, and default settings for unit of measurement and ceiling attenuation. T...
Page 96
96 c hapter 4: p lanning the 3c om m obility s ystem building wizard — edit content page the edit content page enables you to modify imported floor drawings or create new ones, and characterize rf obstacles. You can assign attenuation information to objects. The edit options area has icons for free-...
Page 97
Building wizard overview 97 table 14 lists the toolbar icons at the top of the floor display area. Table 14 toolbar options on edit content page option description adjust the paper space (crop the drawing). Define the drawing scale. Change the grid size. Open the information pane. The information pa...
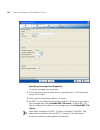
Page 98
98 c hapter 4: p lanning the 3c om m obility s ystem building wizard — plan rf coverage page the plan rf coverage page enables you to identify the wiring closet locations, draw and characterize the wireless coverage areas, insert third-party access points, and compute installation locations for wx s...
Page 99
Building wizard overview 99 page 136, “adding a third-party access point” on page 148, and “placing rf measurement points” on page 168. Table 15 lists the toolbar icons at the top of the floor display area. Table 15 toolbar options on plan rf coverage page option description define the drawing scale...
Page 100
100 c hapter 4: p lanning the 3c om m obility s ystem building wizard — report page the report page enables you to generate work orders for installing 3com equipment. You also can display 3com equipment inventories and other network information. Table 16 lists the toolbar icons at the top of the flo...
Page 101
Creating a site 101 creating a site a site is a folder that contains the buildings in the network plan. A site usually represents a campus of geographically colocated buildings. If your network plan encompasses multiple campuses, create a site for each campus. You can create a site when you create a...
Page 102
102 c hapter 4: p lanning the 3c om m obility s ystem to create a site when you create a network plan to create a site when you create a network plan, use the following procedure. 1 access the create network plan wizard, if not already open. Then type the plan name and select the country code and ch...
Page 103
Creating a site 103 3 click new site. The create site wizard appears. 4 in the site name box, type a name for the site (1 to 80 alphanumeric characters, with no spaces or tabs)..
Page 104
104 c hapter 4: p lanning the 3c om m obility s ystem 5 in the number of buildings box, specify how many buildings are in your site. When you specify the number of buildings a site contains and save the site, 3wxm creates each building using the default settings. You can edit the buildings 3wxm crea...
Page 105
Creating a site 105 4 click new site. The create site wizard appears. 5 in the site name box, type a name for the site (1 to 80 alphanumeric characters, with no spaces or tabs)..
Page 106
106 c hapter 4: p lanning the 3c om m obility s ystem 6 in the number of buildings box, specify how many buildings are in your site. When you specify the number of buildings a site contains and save the site, 3wxm creates each building using the default settings. You can edit the buildings 3wxm crea...
Page 107
Creating or modifying buildings in a site 107 2 click the building you want to modify and click modify, or click new building to add a building to the site. The create building or modify building wizard appears. The create and modify wizards are the same. They differ only in the title. Throughout th...
Page 108
108 c hapter 4: p lanning the 3c om m obility s ystem 6 in the skip floor levels box, specify floor numbers you want to skip. Skipping floors is useful when you want to model only certain floors in a building. To enter a list of floors, use commas to separate the floor numbers (example: 1,3,7). To e...
Page 109
Importing or drawing floor details 109 2 in the unit of measurement list, select feet or metric. If you are importing a drawing of a floor plan, choose the measurement system the drawing uses. 3 in the height of the ceiling box, type the number of feet or meters from the floor to the ceiling (1 to 1...
Page 110
110 c hapter 4: p lanning the 3c om m obility s ystem importing a drawing of a floor you can import a drawing of your floor plan into 3wxm. 3wxm supports the following file types: ■ autocad drawing (dwg), a native binary format used by autocad. You can import the following versions: r13, r14, r2000....
Page 111
Importing or drawing floor details 111 preparing a drawing before importing it 3wxm has a file cleanup feature that can help remove unwanted information from an imported drawing. However, the more cleanup work you do before importing a file, the better the results will be. In addition, cleaning up a...
Page 112
112 c hapter 4: p lanning the 3c om m obility s ystem you will to assign differing rf values to, or if some objects will not become rf obstacles, ungroup the objects and delete the unneeded objects. If all the rf objects in the grouped object will have the dame rf value, you might want to leave the ...
Page 113
Importing or drawing floor details 113 file > drawing utilities > purge. Make sure purge nested items is selected. Click purge until the option is greyed out. Caution: in autocad, you cannot delete a layer if the layer is not empty. However, in turbocad, options > layers allows you to delete a layer...
Page 114
114 c hapter 4: p lanning the 3c om m obility s ystem useful autocad operations and naming-conventions table 17 and table 18 provide autocad operating tips and naming conventions that can be helpful as you prepare your floor plans for 3wxm. Importing the drawing you can import a floor drawing from t...
Page 115
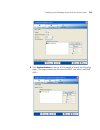
Importing or drawing floor details 115 2 select the floor number from the current floor list. By default, the lowest floor of the building is selected. 3 click import floor layout. 4 after navigating to the directory containing the drawing, select it, and click open. The drawing appears. ■ after you...
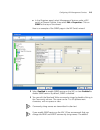
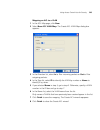
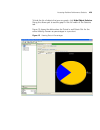
Page 116
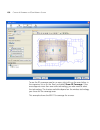
116 c hapter 4: p lanning the 3c om m obility s ystem 5 read the message about verifying the drawing scale, then click ok. (“adjusting the scale of a drawing” on page 120 describes how to adjust the scale.) the drawing is displayed in the view panel. Figure 2 floor plan after importing 6 do one of t...
Page 117
Importing or drawing floor details 117 cropping the paper space you can crop the paper space of a drawing to remove unneeded space and objects around the floor. For example, if the drawing includes parking lot information, you can easily remove the parking lot by cropping. Caution: all objects that ...
Page 118
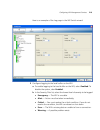
118 c hapter 4: p lanning the 3c om m obility s ystem figure 3 floor plan after cropping adjusting the origin point 3wxm uses a building’s origin point to understand what is above or below a given floor. When calculating rf coverage, 3wxm needs to understand where map access points on adjacent floor...
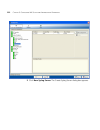
Page 119
Importing or drawing floor details 119 on the floor itself, you can extend the drawing beyond the exterior walls by moving the origin farther up and left. To adjust the origin point 1 access the floor plan in the edit content page. 2 drag and drop (the crosshairs icon) to the new location. The follo...
Page 120
120 c hapter 4: p lanning the 3c om m obility s ystem in this example, the origin point has been moved to an interior shaft. Adjusting the scale of a drawing if you imported a dwg or dxf drawing, you might need to adjust the scale of the drawing because the units used in these drawings might not hav...
Page 121
Importing or drawing floor details 121 3 type the actual distance between the two points. 4 click ok. Until you adjust or verify the scale of a floor, 3wxm reminds you to do so each time you navigate to the edit content page when the floor is displayed. To stop the reminders, perform the procedure a...
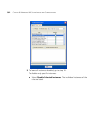
Page 122
122 c hapter 4: p lanning the 3c om m obility s ystem figure 4 floor plan after layers hidden adding or removing a layer to add a new layer to a drawing, do the following in the edit content page: 1 right-click the list of layers next to the view panel. 2 select add layer from the menu that is displ...
Page 123
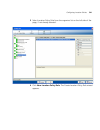
Importing or drawing floor details 123 moving an object from one layer to another to move an object from one drawing layer to another: 1 in the view panel of the edit content page, select the object(s). 2 click on the toolbar. The layer assignment dialog box appears. 3 click the down arrow to displa...
Page 124
124 c hapter 4: p lanning the 3c om m obility s ystem to clean up a drawing 1 on the edit content page, click clean layout. The floor plan clean up wizard appears. 2 in the remove lines and remove objects group boxes, click next to any items you do not want 3wxm to remove from the drawing during cle...
Page 125
Importing or drawing floor details 125 5 to change the maximum size of objects to be removed, type the new horizontal and vertical dimensions in the x-axis and y-axis boxes. 3wxm removes all objects that fit within both the specified axes. 6 in the layer list group box, select the layers you want to...
Page 126
126 c hapter 4: p lanning the 3c om m obility s ystem 9 do one of the following: ■ click finish to accept the changes. ■ click previous to change the cleanup constraints. Go to step 2 on page 124. ■ click cancel to cancel the changes. Drawing floor objects manually you can use the free draw palette ...
Page 127
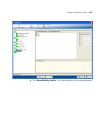
Importing or drawing floor details 127 tools in the insert rf obstacle group box. (see“drawing rf obstacles” on page 132.) to draw an object 1 in the free draw group box of the edit content page, click one of the following icons and draw the object as described: 2 click finish to save the changes an...
Page 128
128 c hapter 4: p lanning the 3c om m obility s ystem 3 to change the floor name, type the new name in the floor name box (1 to 60 alphanumeric characters, with no tabs). Each floor name in a building must be unique. 4 to change the ceiling attenuation or ceiling height values, select or type the ne...
Page 129
Specifying the rf characteristics of a floor 129 ■ use the graphics tools in the insert rf obstacle group box of the edit content page to draw the rf obstacles and assign attenuation values to them. This method is available for any floor plan. (see “drawing rf obstacles” on page 132.) recommendation...
Page 130
130 c hapter 4: p lanning the 3c om m obility s ystem to create rf obstacles for multiple selected objects in a drawing 1 click an object on the floor. 2 press shift while clicking on additional objects. 3 right-click, and select create rf obstacle. The create rf obstacle dialog box appears. 4 go to...
Page 131
Specifying the rf characteristics of a floor 131 figure 5 create rf obstacle dialog box 1 in the description box, type a description for the rf obstacle (1 to 60 characters, with no tabs). 2 in the obstacle type list, select the material of which the rf obstacle is made. Select other if the material...
Page 132
132 c hapter 4: p lanning the 3c om m obility s ystem drawing rf obstacles to draw rf obstacles, you use the insert rf obstacle box of the edit content page. Follow these steps. 1 in the insert rf obstacle group box of the edit content page, click one of the following icons and draw the object as de...
Page 133
Defining wireless coverage areas 133 the create rf obstacle dialog box appears. 2 go to “to use the create rf obstacle dialog box” on page 130. Defining wireless coverage areas you must define which areas of your enterprise require wireless network coverage. In 3wxm, you plan for both coverage and c...
Page 134
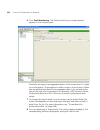
134 c hapter 4: p lanning the 3c om m obility s ystem creating a wiring closet a wiring closet is a room that contains networking devices, such as switches. If you have an existing wiring closet, you can draw it on the floor layout. If you have previously installed wx switches and defined them in 3w...
Page 135
Defining wireless coverage areas 135 3wxm assumes the wx switch that will manage the distributed maps will be located in a wiring closet on another floor in the building. To create a wiring closet 1 on the plan rf coverage page of the building wizard, click the wiring closet icon. 2 on the floor lay...
Page 136
136 c hapter 4: p lanning the 3c om m obility s ystem if there are two or more wx switches in the wiring closet, you can change the order in which 3wxm checks wx switches for free ports. If there are no free ports on the wx switches listed, 3wxm creates and inserts a new wx switch in the wiring clos...
Page 137
Defining wireless coverage areas 137 figure 6 supported shared coverage areas example the coverage areas shown in figure 7 cannot share coverage and are not supported by 3wxm. (however, separate, nonshared coverage areas can overlap.) figure 7 unsupported shared coverage area example keep the follow...
Page 138
138 c hapter 4: p lanning the 3c om m obility s ystem drawing a coverage area 3wxm supports concave polygons, which have an internal angle greater than 180 degrees. When drawing a polygon, make sure that two sides of the polygon do not intersect each other, as shown in figure 8. Also make sure start...
Page 139
Defining wireless coverage areas 139 in the insert area group box in the define coverage page, click one of the following icons and draw the object as described: the coverage area choices wizard appears. Object action (circle) diagonally drag the cursor over the area where you want the circle to app...
Page 140
140 c hapter 4: p lanning the 3c om m obility s ystem go to “specifying the wireless technology for a coverage area”. Specifying the wireless technology for a coverage area (to draw a coverage area, see “drawing a coverage area” on page 138.) to specify wireless technology for a coverage area: 1 in ...
Page 141
Defining wireless coverage areas 141 ■ 802.11a and 802.11b ■ 802.11a and 802.11g select 802.11a and 802.11b if the area requires 802.11a and 802.11b coverage. Select 802.11a and 802.11g if the area requires 802.11a and 802.11g coverage. When you specify a coverage area requiring different technologi...
Page 142
142 c hapter 4: p lanning the 3c om m obility s ystem specifying coverage area properties to specify coverage area properties: 1 in the name box, type a name for the coverage area (1 to 60 characters long, with no tabs). 2 verify that the technology selection is correct. 3 for 802.11g, to prevent th...
Page 143
Defining wireless coverage areas 143 4 to calculate map placement and configuration based solely on coverage and not on capacity, clear use capacity calculation. Go to step 7. Otherwise, go to step 8. By default, 3wxm performs two calculations for map placement. One is based on coverage only. The ot...
Page 144
144 c hapter 4: p lanning the 3c om m obility s ystem go to “specifying association information”. Specifying association information to specify association information: 1 in the mobility domain list, select the mobility domain that contains the maps used for this coverage area. 2 in the radio profil...
Page 145
Defining wireless coverage areas 145 3 in the service profile list group box, click choose available to select a service profile. Service profiles define ssids and their encryption settings, and are associated with radio profiles. You can select more than one service profile. To create a new profile...
Page 146
146 c hapter 4: p lanning the 3c om m obility s ystem 10 to change the ceiling height, specify the new height in the height of the ceiling box. 11 to change the height where maps are mounted, specify the new mounting height in the map placement height box. 12 to change the wx switch model, select th...
Page 147
Defining wireless coverage areas 147 13 to change the default map model, select the model from the default map choice list: ■ ap2750—single-radio model. ■ mp-352—dual-radio model. ■ mp-341—single-radio model. ■ mp-252—dual-radio model. ■ mp-241—single-radio model. ■ mp-52—dual-radio model. ■ mp-122—...
Page 148
148 c hapter 4: p lanning the 3c om m obility s ystem margin listbox. This is the number of dbm below the maximum power setting that you want 3wxm to reserve in case the power needs to be increased later. 17 to plan for redundant map connections to wx switches, select compute redundancy. Only ap mod...
Page 149
Defining wireless coverage areas 149 setting attributes for a third-party access point 1 in miscellaneous group box on the plan rf coverage page, click the third-party access point icon. 2 on the floor background image, click where you want the third-party access point to be placed. The create third...
Page 150
150 c hapter 4: p lanning the 3c om m obility s ystem 8 in the ip address box, type the ip address for the access point. If you specify an ip address, you can use telnet and a web browser with this access point. 9 in the telnet port number box, specify the port number for telnet service. 10 in the h...
Page 151
Computing map placement 151 3 in the mac address box, type the mac address of the radio. 4 to enable the radio, select enabled. The access point’s radio must be enabled in order to be considered in channel allocation. 5 in the transmit power box, specify the transmit power for the radio. 6 in the an...
Page 152
152 c hapter 4: p lanning the 3c om m obility s ystem the rf auto-tuning feature can automatically set the power and channel on each radio. Rf auto-tuning settings are associated with the radio profile that manages the radios. To change rf auto-tuning settings for a radio profile associated with the...
Page 153
Computing map placement 153 you perform the following tasks to compute and place map access points: 1 specify design constraints. (see “to specify design constraints” on page 153.) 2 compute and place map access points. (see “to compute and place map access points” on page 156.) 3 review coverage ar...
Page 154
154 c hapter 4: p lanning the 3c om m obility s ystem 3 to change the height where maps are mounted, specify the new mounting height in the map placement height box. 4 to change the wx switch model, select the model from the use wx type list: ■ wx1200 — provides eight 10/100 ethernet ports, the firs...
Page 155
Computing map placement 155 7 to allow locked map access points to be deleted when compute and place determines that they are no longer required, select allow deletion of locked maps. A locked map is a map that is already associated with the coverage area. For example, if you computed and placed map...
Page 156
156 c hapter 4: p lanning the 3c om m obility s ystem 16 click next. The manage constraints progress page is active. 17 when the completed applying constraints message is displayed in the manage constraints progress page, click finish to save the changes. Go to “to compute and place map access point...
Page 157
Computing map placement 157 you must specify the primary wiring closet for directly attached map access points. Specifying the primary wiring closet for distributed maps is optional. 4 to specify the redundant wiring closet for a coverage area, click in the redundant wiring closet column to display ...
Page 158
158 c hapter 4: p lanning the 3c om m obility s ystem to see the rf coverage area for an area, right-click on the area (either in the organizer list or on the floor) and select show rf coverage. If the area supports more than one radio technology, you also need to select the technology. The choices ...
Page 159
Computing map placement 159 3 to see the rf coverage area for a specific map or radio, right-click the map or radio, and select one of the following: ■ show rf coverage > 802.11a ■ show rf coverage > 802.11b ■ show rf coverage > 802.11g the choices available depend on the wireless technology you cho...
Page 160
160 c hapter 4: p lanning the 3c om m obility s ystem you must now compute the optimal power. See “computing optimal power” on page 162. Locking and unlocking coverage areas after you create a coverage area, it is locked. If you need to move or resize a coverage area, you can unlock it. To unlock a ...
Page 161
Computing map placement 161 3 to relock the coverage area: a select the coverage area. B right-click, and select lock. Locking and unlocking map access points after you compute and place the necessary map access points for a coverage area, you can move them to fine-tune the wireless coverage. If you...
Page 162
162 c hapter 4: p lanning the 3c om m obility s ystem computing optimal power if you do not plan to use the rf auto-tuning feature to automatically set the power levels on the maps after deployment and installation, use the compute optimal power option to calculate the power settings for the maps. T...
Page 163
Computing map placement 163 this option applies only to coverage areas that are configured for coverage, not capacity. (this is configured on the area properties page of the coverage area wizard.) unless you disabled the option to place maps based on capacity, do not select the optimize ap count opt...
Page 164
164 c hapter 4: p lanning the 3c om m obility s ystem if you need to make adjustments, do the following: 1 manually move the map access points, or increase the transmit power levels. 2 manually create more map access points, and place them on the floor. 3 modify the coverage area so that the capacit...
Page 165
Computing map placement 165 2 to change the starting floor for channel assignment, select the floor from the begin on floor list. By default, 3wxm starts at the top floor and works down. 3 to change the ending floor for channel assignment, select the floor from the end on floor list. The ending floo...
Page 166
166 c hapter 4: p lanning the 3c om m obility s ystem 7 review the results. The 802.11a channel assignments are listed on the 802.11a radio(s) tab. The 802.11b/g channel assignments are listed on the 802.11b/g radio(s) tab. 8 click finish to accept the channel assignments. The new channel assignment...
Page 167
Verifying the wireless network 167 verifying the wireless network you can use the following tools to help verify the wireless network: ■ show rf coverage. ■ place rf measurement points. ■ use rf interactive measurement mode. Showing rf coverage looking at the rf coverage allows you to see if the ent...
Page 168
168 c hapter 4: p lanning the 3c om m obility s ystem 3 in the show rf coverage using listbox, select how you want to display the coverage: ■ baseline association rate — coverage is shown based on the map radio baseline association rate. The baseline association rate is the typical data rate the rad...
Page 169
Verifying the wireless network 169 3 in the description box, type a description for the measurement point (1 to 60 characters). 4 in the rssi options box, select display options for the dialog box: ■ to list access points that cannot be detected from this rf measurement point, select show unreachabl...
Page 170
170 c hapter 4: p lanning the 3c om m obility s ystem ■ to generate network design information, see “generating rf network design information” on page 171. ■ click finish to save the changes and close the wizard. Using rf interactive measurement mode rf interactive measurement mode is useful when yo...
Page 171
Generating rf network design information 171 generating rf network design information after 3wxm has calculated the number of map access point required to provide wireless coverage, you can get the following information: ■ floor layout with map access points and other objects defined for the floor ■...
Page 172
172 c hapter 4: p lanning the 3c om m obility s ystem reviewing layout information to see the floor layout, click view layout. Reviewing the map list to review the map list, click view map list. The list of map access points appears in the right panel..
Page 173
Generating rf network design information 173 you can see the following information: ■ list of map access points ■ whether the map access points are enabled ■ channel assignment for each map access point ■ transmit power level for each map access point ■ coverage area in which each map access point i...
Page 174
174 c hapter 4: p lanning the 3c om m obility s ystem information, and projected rssi information that is useful when verifying the installation. After deployment, you can generate a work order with the optional rssi projection tables and map mac addresses, and use it for post-deployment verificatio...
Page 175
Applying rf auto-tuning settings to the network plan 175 a browser must be specified in the tools tab in the preferences dialog box (tools > preferences). 7 select a floor from the select floor list and click view work order. The work order is displayed starting at the floor you specified. You can s...
Page 176
176 c hapter 4: p lanning the 3c om m obility s ystem the network plan’s mobility domains are listed in the scope section. 2 select the scope. If you select a mobility domain as the scope, the change is also applied to the domain policies in the mobility domain. 3 select the rf auto-tuning settings ...
Page 177: Onfiguring
5 c onfiguring wx s ystem and a dministrative p arameters this chapter and the following two chapters describe how to configure wx switch parameters using the wx switch wizard. Depending on how you access the wizard, the wizard’s title can be create wireless switch, or modify followed by the wx swit...
Page 178
178 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters figure 10 wx switch wizard — system and administrative page the wizard has the following pages: ■ system and administrative ■ wireless ■ aaa.
Page 179
Wx switch wizard overview 179 each page has a parameter checklist. Click on an item in the checklist to display or modify the configuration for that parameter. The wizard automatically verifies the configuration parameters and displays any warning or error messages in the verification area at the bo...
Page 180
180 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters ■ blank — error. Comparison of the parameters against the 3wxm rules resulted in an error for at least one of the rules. 3wxm allows you to deploy the switch parameters to a switch if all checkmarks are green. You also can deplo...
Page 181
Wx switch wizard overview 181 wireless page the wireless page enables you to configure map access point and radio parameters. For example, to create a new radio profile, select radio profile in the organizer list on the left, then click new radio profile to display the create radio profile wizard..
Page 182
182 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters when an option in a configuration wizard opens a new wizard, the other wizard remains open in the background. However, you can enter information only in the new wizard. After you click finish to save your changes and close the n...
Page 183
Adding a wx switch to the network plan 183 aaa page the aaa wizard enables you to configure authentication, authorization, and accounting (aaa) for administrative access and network user access. You can configure radius parameters, users, and access filters. (to configure aaa parameters, see “config...
Page 184
184 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters to create a new wx switch based on domain policies to create a new wx switch based on the switch parameters in domain policies, do either of the following: ■ select the mobility domain where you want to create the switch in the ...
Page 185
Accessing the modify switch wizard 185 configuration into 3wxm, edit the switch, then redeploy the switch with the new parameters. 1 use the procedure in “uploading a wx switch configuration into 3wxm” on page 370 to upload the switch. 2 in the organizer panel, select the mobility domain where you p...
Page 186
186 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters configuring basic wx properties to configure basic wx properties, do the following steps. 1 access the wx switch wizard for the switch. (see “accessing the modify switch wizard” on page 185.) 2 select system and administrative a...
Page 187
Configuring basic wx properties 187 6 in the software version list, select the version of mobility system software (mss) you expect to run on the wx switch. 7 to prevent the wx switch from being managed by 3wxm, click next to managed to deselect the option. Management by 3wxm is enabled by default. ...
Page 188
188 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters if the correct software image is already loaded on the wx, go to step 13. Otherwise, select a software image from the list, and click close. This dialog box lists the images that are in the image repository. You must add a syste...
Page 189
Configuring vlans 189 you must assign the system ip address to one of the vlans, to allow communications between wx switches and for unsolicited communications such as snmp traps and radius accounting messages. Any ip address configured on a wx switch can be used for management access unless explici...
Page 190
190 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters the wx switch through which a user is authenticated must be a member of the mobility domain the user is assigned to. However, you are not required to configure the vlan on all wx switches in the mobility domain. When a user roam...
Page 191
Configuring vlans 191 configuring vlan basic properties in addition to defining a vlan name and number, you can also configure the following: ■ tunnel affinity wx switches configured to comprise a mobility domain allow users to roam seamlessly across map access points and across wx switches. Althoug...
Page 192
192 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters if you are creating a new wx switch, the vlans listed in this panel are from the vlans object in the domain policies for the mobility domain the new switch is in. You can modify or delete these vlans. 4 do one of the following: ...
Page 193
Configuring vlans 193 5 in the vlan id box, specify a vlan number (2 to 4095). The vlan number must be unique on a particular wx. 6 in the vlan name box, type the name of the vlan (1 to 16 alphabetic characters long, with no numbers, spaces, or tabs). 7 in the tunnel affinity box, specify the numeri...
Page 194
194 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters 10 in the aging time box, specify the aging timeout period (0 to 1,000,000 seconds) for dynamic entries in the forwarding database. The default is 300 seconds (5 minutes). If you specify 0, aging is disabled. 11 do one of the fo...
Page 195
Configuring vlans 195 to configure vlan membership: 1 in the modify vlan wizard, click vlan member selection. The vlan member selection page appears. Only ports configured as network ports are listed. You cannot add map access ports, distributed maps, or wired authentication ports to a vlan. 2 from ...
Page 196
196 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters moving a port or port group could potentially affect multiple vlans. ■ to add a port or port group to the vlan and retain previous vlan membership, click add. The port or port group now appears in the current members list. 4 to ...
Page 197
Configuring vlans 197 ■ mss uses pvst+ bpdus on vlan ports that are tagged. Pvst+ bpdus include tag information in the 802.1q field of the bpdus. Mss runs a separate instance of pvst+ on each tagged vlan. When you create a vlan, stp is disabled on the new vlan by default, regardless of the stp state...
Page 198
198 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters 2 to enable stp, click enabled. 3 in the bridge priority box, specify this stp bridge’s priority (0 to 65,535). The default is 32,768. The bridge with the lowest priority value becomes the root bridge for the spanning tree. 4 in...
Page 199
Configuring vlans 199 to configure stp port information: 1 in the create vlan wizard, click spanning tree port setup. The spanning tree port setup page appears. 2 select the port whose stp information you want to modify. 3 click modify. The modify port dialog box appears..
Page 200
200 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters 4 to enable spanning tree packet processing (tx/rx) on that port, make sure enabled is selected. This is the default. To disable this feature, clear enabled. If you disable spanning tree packet processing on the port, the follow...
Page 201
Configuring vlans 201 10 do one of the following: ■ to configure internet group management protocol (igmp) information, click next to display the vlan igmp page. (see “configuring igmp”.) ■ to close the wizard and save the changes, click finish. Configuring igmp internet group management protocol (i...
Page 202
202 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters to configure igmp snooping: 1 in the create vlan wizard, click vlan igmp setup. The vlan igmp setup page appears. 2 to enable igmp snooping, select enable. To disable igmp snooping, clear enable. By default, igmp snooping is ena...
Page 203
Configuring vlans 203 6 in the other querier present interval box, specify how long (1 to 65,535 seconds) the wx switch waits for a general query to arrive before making itself the querier. The default interval is 255 seconds. 7 in the query response interval box, specify how long (1 to 65,535 tenth...
Page 204
204 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters you can only add network ports as static multicast router ports or multicast receiver ports. Ports you add are immediately added to the list and do not age out. You cannot add map ports or wired authentication ports as static mu...
Page 205
Configuring vlans 205 3 to add a multicast router port, select the multicast router present checkbox for each port you want to add. By default, ports are not selected. To remove a static multicast receiver port, clear the checkbox. 4 to close the wizard and save the changes, click finish. Configurin...
Page 206
206 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters the uplink fast convergence feature is applicable to bridges that are acting as access switches to the network core (distribution layer) but are not in the core themselves. Do not enable the feature on wx switches that are in th...
Page 207
Configuring the system ip address 207 modifying vlans to modify a vlan: 1 in the organizer panel, navigate to the domain policy or wx switch you want to configure. 2 expand the object to see the configuration options. 3 expand vlans. 4 select the vlan you want to modify. 5 select edit > properties. ...
Page 208
208 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters 3 select system ip address from the organizer list on the left side of the page, if not already selected. 4 select the vlan on which the system ip address is configured from the system vlan/ip list box. 5 optionally, enter the i...
Page 209
Configuring wx management services 209 configuring wx management services you can configure the following information and management services for the wx: ■ system information — you can specify system contact information, as well as the cli prompt and the banner message that appears at each session. ...
Page 210
210 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters setting system information to set system information: 1 do one of the following: ■ open the wx switch wizard, then select system information under management services in the organizer list of the system and administrative page. ...
Page 211
Configuring wx management services 211 if you do not specify a prompt, the cli uses the following default prompts: ■ wxmmmm> for restricted access ■ wxmmmm# for enabled access the mmmm portion of the prompt shows the wx switch’s model number. 4 in the message of the day box, type the message that ap...
Page 212
212 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters 2 select enabled to enable https access, or clear enabled to disable https access. 3 do one of the following: ■ go to “configuring telnet”. ■ select another item in the wx switch wizard, if you are using this wizard. ■ click fin...
Page 213
Configuring wx management services 213 ■ in the organizer panel, select management services under a wx switch or domain policies, then select edit > properties. Click on https, telnet, ssh & web auth at the top of the wizard. 2 select enabled to enable telnet access, or clear enabled to disable teln...
Page 214
214 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters disabling or reenabling web aaa to disable or reenable web aaa on the wx: 1 do one of the following: ■ open the wx switch wizard, then select https, telnet, ssh & web auth under management services in the organizer list of the s...
Page 215
Configuring wx management services 215 ■ in the organizer panel, select management services under a wx switch or domain policies, then select edit > properties. Click on snmp at the top of the wizard. Here is an example of the snmp page in the wx switch wizard. 2 select enabled to enable snmp servic...
Page 216
216 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters strings are commonly used and can easily be guessed. You cannot edit the trap community string. 4 you can enable the following snmp traps: ■ authentication — generated when the wx switch’s snmp agent receives a bad community str...
Page 217
Configuring wx management services 217 ■ clientauthorization — generated when a client is sucessfully authorized. ■ clientdeassociation — generated when a client is deassociated from a radio. ■ clientroaming — generated when a client roams. ■ autotuneradiopowerchange — generated when the rf auto-tun...
Page 218
218 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters 7 click finish to save the changes. The snmp setup page in the modify management services wizard appears. 8 to add other snmp trap receivers, repeat step 5 through step 7 for each trap receiver. You can add a maximum of five tra...
Page 219
Configuring wx management services 219 here is an example of the log page in the wx switch wizard. 2 configure logging to the local buffer on the wx: a to enable logging to the local buffer on the wx, select enabled. To disable the option, clear enabled. B in the severity filter list, select the low...
Page 220
220 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters ■ notice — events that can cause system problems have occurred. These are logged for diagnostic purposes. ■ info — informational messages only. No problems exist. ■ debug — output from debugging. The default severity level is er...
Page 221
Configuring wx management services 221 6 do one of the following: ■ go to “setting up a syslog server”. ■ select another item in the wx switch wizard, if you are using this wizard. ■ click finish to close the wizard and save changes. Setting up a syslog server you can specify a syslog server. Syslog...
Page 222
222 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters 2 click new syslog server. The create syslog server dialog box appears..
Page 223
Configuring wx management services 223 3 in ip address, type the ip address of the syslog server. 4 in the severity filter list, select the lowest level of severity of the event or condition to be logged (see the list in step 2 of “setting up system logging” on page 218). The default severity level ...
Page 224
224 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters ■ select another item in the wx switch wizard, if you are using this wizard. ■ click finish to close the wizard and save changes. Configuring tracing you can configure tracing for debugging mss. You use specific keywords to spec...
Page 225
Configuring wx management services 225 7 in the area box, type one of the following keywords to specify the area to trace. Aaacli accounting acl ams ag_agent ap_buffer_mgr ap_crypto ap_ethernet ap_network ap_radio ap_station ap_stats ap_tapa ap_util ap_vlan apm_trap arp authentication authorization ...
Page 226
226 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters for more information about trace commands, see the wireless lan switch and controller configuration guide. 8 optionally, in the level box, specify the amount of information included in the trace output (0 to 10). 0 provides the ...
Page 227
Configuring wx management services 227 (utc) — also known as greenwich mean time (gmt). The time zone information is used by network time protocol (ntp) if you enabled it. You can also specify whether the wx modifies the clock during daylight savings time or similar summertime period. To set up a ti...
Page 228
228 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters 2 in the name box, type the name for the time zone (1 to 16 alphanumeric characters, with no spaces or tabs). 3 in the offset hours box, specify the number of hours (between -23 and 23) to subtract from or add to utc. 4 optional...
Page 229
Configuring wired authentication ports 229 12 do one of the following: ■ go to “configuring wired authentication ports”. ■ select another item in the wx switch wizard, if you are using this wizard. ■ click finish to close the wizard and save changes. Configuring wired authentication ports a wired au...
Page 230
230 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters 2 to specify a port as a wired authentication port, select wired auth. Enabled for the port. To specify all the ports as wired authentication ports, select the wired auth. Enabled checkbox in the upper left corner of the setup a...
Page 231
Configuring network ports 231 ■ force unauthorized — specifies that the controlled port is unconditionally unauthorized. All 802.1x authentication attempts respond with an eap failure message. ■ automatic — specifies that the wx switch processes 802.1x authentication normally using the authenticatio...
Page 232
232 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters 2 select an ethernet port to modify. 3 click modify. The modify port dialog box appears..
Page 233
Configuring network ports 233 the options in the wired authentication setup group box apply only to wired authentication ports. 4 in the name box, type a name for the port (1 to 16 alphanumeric characters, with no spaces or tabs). 5 to enable the port, select enabled. To disable the port, clear enab...
Page 234
234 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters 7 to specify the speed of a 10/100 ethernet port, select one of the following: ■ auto — sets the port to automatically detect the traffic speed and set the speed accordingly. This is the default value. ■ 10 — sets the speed to 1...
Page 235
Configuring load sharing 235 configuring load sharing a port group is a set of physical ports that function together as a single link and provide load sharing and link redundancy. Only network ports can participate in a port group. Load sharing the wx balances port group traffic among the group’s ph...
Page 236
236 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters 2 select new port group. The create port group wizard appears..
Page 237
Configuring load sharing 237 3 in the port group name box, type the name of the port group (1 to 16 alphanumeric characters, with no spaces or tabs). 4 click next. The port group selection page appears..
Page 238
238 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters 5 to add a port to the port group, select the member checkbox for the port. The port group name appears in the port group column for the port. 6 to remove a port from a port group, clear the member checkbox for the port. 7 to ch...
Page 239
Configuring ip services 239 through which to forward traffic.You can add the following types of static routes: ■ explicit route — forwarding path for traffic to a specific destination ■ default route — forwarding path for traffic to a destination without an explicit route if the ip routing table con...
Page 240
240 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters route command output shows that the static route is down. For more information about these commands, see the wireless lan switch and controller command reference. To create a static route 1 do one of the following: ■ open the wx...
Page 241
Configuring ip services 241 3 in the destination ip address box, type the destination ip address and subnet mask in classless interdomain routing (cidr) notation (for example, 10.10.0.0/16). 4 in the gateway box, type the ip address of the gateway that the route uses. 5 in the metric box, specify th...
Page 242
242 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters 2 to set the gateway ip address for a default route, click on an entry in the gateway ip address column. 3 edit the ip address to the address of the gateway the route uses. 4 to change the cost for using the route, double-click ...
Page 243
Configuring ip services 243 2 click new ip alias. The create ip alias dialog box appears..
Page 244
244 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters 3 in the host name box, type the name of the ip alias (1 to 32 characters, with no spaces or tabs). You cannot use the word all as the name of an ip alias. 4 in the host ip address box, type the ip address that the ip alias is m...
Page 245
Configuring ip services 245 you configure dns by performing the following tasks: ■ enable the dns client and configure a default domain name for dns queries. ■ specify the ip addresses of the dns servers. Setting up dns basic properties to set up dns basic properties: 1 do one of the following: ■ op...
Page 246
246 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters 2 to enable dns, select enabled. To disable dns, clear enabled. 3 if you disabled dns in step 2, go to step 5. Otherwise, go to the next step. 4 in the default dns domain box, type the default domain suffix that is appended to a...
Page 247
Configuring ip services 247 adding dns servers to add a dns server: 1 do one of the following: ■ open the wx switch wizard, then select dns under ip services in the organizer list of the system and administrative page. ■ in the organizer panel, select ip services under a wx switch or domain policies...
Page 248
248 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters setting ntp properties to set ntp properties: 1 do one of the following: ■ open the wx switch wizard, then select ntp under ip services in the organizer list of the system and administrative page. ■ in the organizer panel, selec...
Page 249
Configuring ip services 249 4 to set the interval at which an ntp server is polled, specify its value in seconds (16 to 1024) in the update interval box. The default is 64 seconds. 5 do one of the following: ■ go to “configuring arp”. ■ select another item in the wx switch wizard, if you are using t...
Page 250
250 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters configuring arp the address resolution protocol (arp) table maps ip addresses to mac addresses. Arp is enabled by default on the wx and cannot be disabled. An arp entry is added to the table in one of the following ways: ■ autom...
Page 251
Configuring ip services 251 2 in the aging time box, specify the amount of time a dynamic entry can remain unused before the entry is removed from the arp table. The value range for the aging timeout is 0 to 1,000,000 seconds. The default value is 1200 seconds. To disable aging, specify 0 as the agi...
Page 252
252 c hapter 5: c onfiguring wx s ystem and a dministrative p arameters ■ in the mac address box, type the mac address that the ip address is to be mapped to. ■ in the ip address box, type the ip address for the arp entry. ■ click finish. ■ do one of the following: ■ select another item in the wx sw...
Page 253: Onfiguring
6 c onfiguring w ireless p arameters this chapter describes how to configure the following wireless parameters: ssids, service profiles, radio profiles, directly connected and distributed map access points, and active rf scanning. Overview this chapter describes how to configure the following wirele...
Page 254
254 c hapter 6: c onfiguring w ireless p arameters figure 11 wx switch wizard — wireless page (for information about the wx switch wizard, see “wx switch wizard overview” on page 177.) when a wireless client requests access to the network, the client requests access to a specific service set identif...
Page 255
Configuring an ssid 255 ■ for encrypted traffic, the encryption algorithm used: ■ wired equivalent privacy (wep) ■ wi-fi protected access (wpa) temporal key integrity protocol (tkip) ■ wpa counter mode with cipher block chaining message authentication code protocol (ccmp) ■ wpa wep ■ authentication ...
Page 256
256 c hapter 6: c onfiguring w ireless p arameters 4 to create an ssid, click new ssid. The create ssid wizard appears..
Page 257
Configuring a service profile 257 5 type the ssid name. The name can be 1 to 32 alphanumeric characters long, with no spaces or tabs. 6 do one of the following: ■ click next and go to “configuring and managing access rules for network users” on page 323. ■ click finish to save change and close the w...
Page 258
258 c hapter 6: c onfiguring w ireless p arameters 3 select service profile from the organizer list on the left side of the page. 4 click new service profile. The create service profile wizard appears. 5 in the name box, type a name of up to 16 alphanumeric characters, with no spaces, for the servic...
Page 259
Configuring a service profile 259 ■ last resort — automatically authenticates the client and allows access to the ssid requested by the client, without requiring a username and password from the client. ■ web auth — serves the client a web page from the wx switch’s nonvolatile storage for login to t...
Page 260
260 c hapter 6: c onfiguring w ireless p arameters configuring encryption to configure encryption, follow these steps: 1 in the create service profile wizard, click encryption. The encryption page appears. 2 in the security mode list, select wep, wpa, or wep+wpa. The default is wep. Microsoft window...
Page 261
Configuring a service profile 261 if you use dynamic wep, 802.1x must also be configured on the client in addition to wep. To use static wep, you must provide wep keys. You can specify the wep keys, as well as the wep unicast and multicast key indexes to be used. You can also specify whether shared ...
Page 262
262 c hapter 6: c onfiguring w ireless p arameters configuring wpa wpa is a security enhancement to the ieee 802.11 wireless standard. Wpa provides enhanced encryption with new cipher suites and provides per-packet message integrity checks. Wpa is based on draft 3 of the 802.11i standard. You can us...
Page 263
Configuring a service profile 263 ■ wired equivalent privacy (wep) with 104-bit keys — 104-bit wep uses the rc4 encryption algorithm with a 104-bit key. ■ wep with 40-bit keys — 40-bit wep uses the rc4 encryption algorithm with a 40-bit key. You can configure map access points to support one or more...
Page 264
264 c hapter 6: c onfiguring w ireless p arameters ■ in the pre-shared key box, type an alphanumeric passphrase (8 to 63 characters). ■ click generate key. The preshared key appears in the pre-shared key box. 5 go to “to configure wpa encryption choices”. To configure wpa encryption choices 1 to ena...
Page 265
Configuring a radio profile 265 service profile later. (to configure a radio profile, see “configuring a radio profile” on page 265.) to map a service profile to a radio 1 in the create service profile wizard, click radio profile selection. The radio profile selection page appears. 2 select the radi...
Page 266
266 c hapter 6: c onfiguring w ireless p arameters 3com recommends that you create a new radio profile and leave the default radio profile unchanged as a backup. The default radio profile is associated with a wx switch’s maps, unless you created a new radio profile while configuring a floor plan’s c...
Page 267
Configuring a radio profile 267 4 select new radio profile. The create radio profile wizard appears..
Page 268
268 c hapter 6: c onfiguring w ireless p arameters 5 in the name box, type the name of the radio profile (1 to 16 characters, with no spaces or tabs). 6 to prevent the association of 802.11b clients to 802.11g radios using this profile, select exclude 802.11b clients. Selecting this option prevents ...
Page 269
Configuring a radio profile 269 to change 802.11 attributes to change 802.11 attributes, use the following procedure. 1 in the create radio profile wizard, click 802.11 attributes. The 802.11 attributes page appears. 2 in the beacon interval box, specify the interval at which the map advertises its ...
Page 270
270 c hapter 6: c onfiguring w ireless p arameters outbound frame in buffer storage. The default value is 2,000 ms (2 seconds). 7 in the max. Rx msdu lifetime box, specify the maximum amount of time, from 500 ms to 250,000 ms (250 seconds), the map can hold an inbound frame in buffer storage. The de...
Page 271
Configuring a radio profile 271 to configure rf auto-tuning to configure rf auto-tuning, use the following procedure. 1 in the create radio profile wizard, click auto-tune. The auto-tune page appears. 2 to enable automatic configuration and tuning of the transmit power, select yes next to tune trans...
Page 272
272 c hapter 6: c onfiguring w ireless p arameters you can specify from 0 to 65535 seconds. The default is 10 seconds. 5 to enable automatic configuration and tuning of the channel, select yes next to tune channel. This feature is enabled by default. 6 to change the interval at which rf auto-tuning ...
Page 273
Configuring a radio profile 273 to map the radio profile to a service profile to map the radio profile to a service profile, use the following procedure. 1 in the create radio profile wizard, click service profile selection. The service profile selection page appears. 2 select the service profile in...
Page 274
274 c hapter 6: c onfiguring w ireless p arameters to apply a radio profile to radios 1 in the create radio profile wizard, click radio selection. The radio selection page appears. If the available members column is empty, as shown in this example, no map access points have been configured for the w...
Page 275
Configuring directly connected map access points 275 indirectly through other layer 2 or layer 3 wired networking devices. Configure a map port for each directly connected map. Table 20 lists how many maps you can configure on a wx switch, and how many maps a switch can boot. The numbers are for dir...
Page 276
276 c hapter 6: c onfiguring w ireless p arameters 4 in the table, enable a port as a map port by selecting map enabled for the port. If a port is currently configured as a wired authentication port, you are prompted to choose whether to reconfigure the port. You can see that the port has been label...
Page 277
Configuring directly connected map access points 277 ■ mp-341 — single-radio model. ■ mp-262 — dual-radio model. ■ mp-252 — dual-radio model. ■ mp-241 — single-radio model. ■ mp-52 — dual-radio model. ■ mp-122 — dual-radio model. ■ mp-101 — single-radio model. 7 to select the radio type for a single...
Page 278
278 c hapter 6: c onfiguring w ireless p arameters to modify map attributes to modify map attributes, use the following procedure. 1 on the map page of the wireless page of the wx switch wizard, select a map port, then click modify map. The modify map wizard appears. 2 select the map model from the ...
Page 279
Configuring directly connected map access points 279 3 to select the radio type for a single-radio model, click the map radio type box and select the radio type from the list: ■ 11a — 802.11a ■ 11b — 802.11b only ■ 11g — 802.11b/g 4 in the name box, type a name (1 to 16 alphanumeric characters, with...
Page 280
280 c hapter 6: c onfiguring w ireless p arameters select no to disable automatic firmware upgrading. Automatic firmware upgrading is enabled by default. 9 do one of the following: ■ to modify radio settings for the map, see “to modify radio settings”. ■ to modify connection settings for the map, se...
Page 281
Configuring directly connected map access points 281 ■ ant1060 ■ ant1120 ■ ant1180 to indicate the direction of the antenna’s coverage, change the value in the directionality of antenna box. The default value of 0 degrees directs the antenna’s coverage to the right on the floor plan. For example, to...
Page 282
282 c hapter 6: c onfiguring w ireless p arameters the default power level is default, which means rf auto-tuning can assign up to the maximum power level allowed for the radio. You can specify from 1 to 20. B to change the minimum rate at which a radio is allowed to transmit traffic to clients, sel...
Page 283
Configuring directly connected map access points 283 to modify a map connection you can change connection parameters for a map, including the wx port (for directly connected maps). For map models that have two ethernet ports, you also can add or change the second wx connection for redundancy. 1 on t...
Page 284
284 c hapter 6: c onfiguring w ireless p arameters 3 modify connection parameters: a to change the wx switch for the connection, select the wx switch from the wx listbox. B to change the map port number or distributed map connection number, select the new value from the port or dap number listbox. C...
Page 285
Configuring distributed map access points 285 table 20 lists how many maps you can configure on a wx switch, and how many maps a switch can boot. The numbers are for directly connected and distributed maps combined. For a map that is directly connected to the wx, configure a map port instead. (for i...
Page 286
286 c hapter 6: c onfiguring w ireless p arameters 4 click new distributed map. The create distributed map wizard appears..
Page 287
Configuring distributed map access points 287 5 in the dap number box, specify the connection number for the wx switch’s connection to this distributed map. 6 select the map model from the map model list: ■ ap2750 — single-radio model. ■ mp-352 — dual-radio model. ■ mp-341 — single-radio model. ■ mp...
Page 288
288 c hapter 6: c onfiguring w ireless p arameters 8 in the name box, type a name (1 to 16 alphanumeric characters, with no spaces or tabs). 9 in the serial number box, type the serial number of the map. 10 if you are configuring dual-homing support, in the bias list, select high or low. Bias is the...
Page 289
Disabling or reenabling active rf scanning 289 disabling or reenabling active rf scanning by default, map radios actively scan for rogue devices by sending probe any requests (probe requests with a null ssid name), to solicit probe responses from other access points. Radios also passively scan by li...
Page 290
290 c hapter 6: c onfiguring w ireless p arameters.
Page 291: Onfiguring
7 c onfiguring a uthentication , a uthorization , and a ccounting p arameters this chapter describes how to configure the following authentication, authorization, and accounting (aaa) parameters for wx switches: ■ radius servers, for backend aaa processing of wx administrator access and network clie...
Page 292
292 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters figure 12 wx switch wizard — aaa page (for information about the wx switch wizard, see “wx switch wizard overview” on page 177.) connecting to radius servers and server groups remote authentication dial-in us...
Page 293
Connecting to radius servers and server groups 293 radius server groups can authenticate administrators and network users. You can specify up to four radius server groups for aaa services in a 3com mobility system. Although you can use the local database on the wx switch to authenticate users, 3com ...
Page 294
294 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters 4 in the timeout box, specify how long wx switch must wait (1 to 65,535 seconds) for a radius server to respond before retransmitting. The default is 5 seconds. 5 in the retry count box, specify the number of...
Page 295
Connecting to radius servers and server groups 295 7 in the key box, type the password (also known as a shared secret key) used to authenticate to the radius server. You must provide the same password that is defined on the radius server. The password can be 1 to 32 characters long, with no spaces o...
Page 296
296 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters 4 click new radius server. The create radius server wizard appears..
Page 297
Connecting to radius servers and server groups 297 5 in the name box, type the name of an existing radius server (1 to 32 alphanumeric characters, with no spaces or tabs). Do not use the same name for a radius server and a radius server group. 6 in the ip address box, type the ip address for the rad...
Page 298
298 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters you must provide the same password that is defined on the radius server. 13 in the authorization password box, type the password used for outbound authentication and authorization to a radius server (1 to 32 ...
Page 299
Connecting to radius servers and server groups 299 4 click new radius server group. The create radius server group wizard appears..
Page 300
300 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters 5 in the name box, type the name of the radius server group (1 to 32 alphanumeric characters, with no spaces or tabs). Do not use the same name for a radius server and a server group. 6 to enable load balanci...
Page 301
Creating and managing users in the local user database 301 10 do one of the following: ■ to change the order of radius servers in the radius server group, see “changing the order in a radius server group”. ■ to close the create radius server group dialog box and save the changes, click finish. Chang...
Page 302
302 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters ■ mac address users — these users are authenticated by a mac address. For example, devices such as pdas or cellular phones that do not support 802.1x authentication are identified when the wx switch discovers...
Page 303
Creating and managing users in the local user database 303 4 click new and select new user. The create user wizard appears..
Page 304
304 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters 5 in the name box, type the name of the user (1 to 60 alphanumeric characters, with no spaces or tabs). 6 in the vlan name box, type the name of the vlan that the user belongs to (1 to 16 alphanumeric charact...
Page 305
Creating and managing users in the local user database 305 10 do one of the following: ■ to configure user attributes, see “configuring user authorization attributes” on page 310. ■ to configure a user group, see “creating named user groups”. ■ to close the create user wizard and save the changes, c...
Page 306
306 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters 4 click new and select new user group. The create user group wizard appears..
Page 307
Creating and managing users in the local user database 307 5 in the user group name box, type a name for the user group (1 to 60 alphanumeric characters, with no spaces or tabs). 6 in the vlan name box, type the vlan that the user group belongs to (1 to 16 alphanumeric characters, with no spaces or ...
Page 308
308 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters to configure mac address user authentication properties 1 access the wx switch wizard for the wx switch. (see “accessing the modify switch wizard” on page 185.) 2 select aaa at the top of the wizard, if not a...
Page 309
Creating and managing users in the local user database 309 8 do one of the following: ■ to configure user attributes, see “configuring user authorization attributes” on page 310. ■ to configure a mac address user group, see “creating mac address user groups”. ■ to close the create mac address user w...
Page 310
310 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters 5 in the user group name box, type a name for the mac address user group (1 to 60 alphanumeric characters, with no spaces or tabs). 6 in the vlan name box, type the vlan that the user group belongs to (1 to 1...
Page 311
Creating and managing users in the local user database 311 to configure user authorization attributes 1 click user attributes at the top of the wizard you are using to create or modify attributes a user or user group. The wizard should be one of the following: ■ create user wizard ■ create user grou...
Page 312
312 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters table 22 lists the user attributes and their value ranges. You can specify these attributes in lowercase when using the cli. Table 22 authentication attributes for local users attribute description valid valu...
Page 313
Creating and managing users in the local user database 313 filter-id inbound or outbound acl to apply to the user. If configured in the wx switch’s local database, this attribute can be an access control list (acl) to filter outbound or inbound traffic. Use the following format: inboundacl.In or out...
Page 314
314 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters service-type type of access the user is requesting. Access type, which can be one of the following numbers: 2—framed; for network user access 6—administrative; for administrative access, with authorization to...
Page 315
Creating and managing users in the local user database 315 time-of-day (network access mode only) day(s) and time(s) during which the user is permitted to log into the network. After authorization, the user’s session can last until either the time-of-day range or the session-timeout duration (if set...
Page 316
316 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters configuring and managing access rules for administrative users the 3com mobility system supports two types of access rules for administrative users, based on how the administrator accesses the wx switch: ■ ad...
Page 317
Configuring and managing access rules for administrative users 317 when configuring authentication for console users, make sure that there is a username and password defined in the local wx user database that you can use to log in through the console. Also make sure that you configure authentication...
Page 318
318 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters mac address globs a mac address glob is a similar method for applying some aaa commands to either a single 6-byte mac address or a set of mac addresses. In a mac address glob, you can use the asterisk (*) as ...
Page 319
Configuring and managing access rules for administrative users 319 3 select admin access from the organizer list on the left side of the page, if not already selected. 4 click new admin access. The create admin access wizard appears..
Page 320
320 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters 5 in the user glob box, type a full or partial username to be matched during authentication. A user glob can have 1 to 80 alphanumeric characters, with no spaces or tabs. You can use asterisks as wildcards. T...
Page 321
Configuring and managing access rules for administrative users 321 to set the authentication method for administrator access 1 at the top of the create admin access wizard, select authentication. The authentication page appears. 2 to enable this authentication rule, select enabled. 3 to select the a...
Page 322
322 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters to add a server group, click create and go to “to define a radius server group” on page 298. After you create the server group, click choose available and then select the server group from the list. 4 do one ...
Page 323
Configuring and managing access rules for network users 323 ■ radius server group — a server group that you have configured previously. ■ local — the wx switch’s local database. You can add one or both methods to the list. ■ if you specify a radius server group as the first method and the administra...
Page 324
324 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters you can configure authentication rules for each type of user, on an individual ssid or wired authentication port basis. Mss authenticates users based on user information on radius servers or in the wx switch’...
Page 325
Configuring and managing access rules for network users 325 authentication types mss provides the following types of authentication: ■ ieee 802.1x — if the network user’s network interface card (nic) supports 802.1x, mss checks for an 802.1x authentication rule that matches the username (and ssid, i...
Page 326
326 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters authentication algorithm mss can try more than one of the authentication types described in “authentication types” to authenticate a user. Mss tries 802.1x first. If the user’s nic supports 802.1x but fails a...
Page 327
Configuring and managing access rules for network users 327 figure 13 authentication flowchart for network users last-resort? Web? None? Client associates with map radio or requests access from wired authentication port use fallthru authentication yes no yes yes yes yes no yes yes no no no no client...
Page 328
328 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters ssid name “any” in authentication rules for wireless access, you can specify the name any for the ssid. This value is a wildcard that matches on any ssid string requested by the user. For 802.1x and web aaa r...
Page 329
Configuring and managing access rules for network users 329 user credential requirements the user credentials that mss checks for on radius servers or in the local database differ depending on the type of authentication rule that matches on the ssid or wired access requested by the user. ■ for a use...
Page 330
330 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters during which the user can access the network, you can apply inbound and outbound access control lists (acls) to the user’s traffic, and so on. To assign attributes on the radius server, use the standard radiu...
Page 331
Configuring and managing access rules for network users 331 mode of the mss cli, or administrative access to the nonenabled mode of the cli. ■ session-timeout — maximum number of seconds allowed for the user’s session. Regardless of whether you configure the user and attributes on radius servers or ...
Page 332
332 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters ■ web network access — if the client name matches the userglob, the wx switch serves a web page to the client so the client can log in. If the username and password entered by the client match a username and ...
Page 333
Configuring and managing access rules for network users 333 3 type the userglob or mac address glob that is allowed to access the ssid. ■ for a user glob — type a full or partial username to be matched during authentication (1 to 80 alphanumeric characters, with no spaces or tabs). The format of a u...
Page 334
334 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters asterisk (*) in mac addresses. The following lists examples of using wildcards in mac addresses: * (all mac addresses) 00:* 00:01:* 00:01:02* 00:01:02:03:* 00:01:02:03:04:* 00:01:02:03:04:0* last-resort acces...
Page 335
Configuring and managing access rules for network users 335 4 click authentication at the top of the wizard to display the following page. (the page contents are the same for mac, last-resort, and web aaa.).
Page 336
336 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters 5 to enable this authentication rule for the ssid, select enabled. By default, a rule you configure in 3wxm is disabled, which means 3wxm does not add the rule to a wx switch’s configuration. 6 for 802.1x aut...
Page 337
Configuring and managing access rules for network users 337 if you select peap, the eap sub-protocol is ms-chapv2. For other protocols, the eap sub-protocol is none. 8 to select the authentication method, click choose available, then select the method from the list: ■ radius server group — a server ...
Page 338
338 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters configuring accounting to configure accounting settings, follow these steps. 1 click accounting at the top of the wizard to display the following page. (the page contents are the same for 802.1x, mac, last-re...
Page 339
Configuring location policies 339 you can add one or both methods to the list. ■ if you specify a radius server group as the first method and a user is denied access by the radius server, no accounting is attempted with the other methods specified in the list. ■ if you specify local as the first met...
Page 340
340 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters during the authorization process, a vlan is assigned as well as optional user attributes, such as session timeout and any applicable security acls. If you need to override the configured user attributes local...
Page 341
Configuring location policies 341 3 select location policy rule from the organizer list on the left side of the page, if not already selected. 4 click new location policy rule. The create location policy rule wizard appears..
Page 342
342 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters 5 in the user glob name list, select one of the following: ■ none — do not use a user glob to determine whether to apply the location policy. ■ equal — apply the location policy to all usernames matching a sp...
Page 343
Configuring location policies 343 ■ equal — apply the location policy to all users with a specified vlan. In the vlan box, type the name of the vlan. ■ not equal — apply the location policy to all users whose assigned vlan does not match a specified vlan. In the vlans box, type the name of the vlan....
Page 344
344 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters about acl name restrictions, see “setting up acl basic properties” on page 348.) 12 in the out acl name box, type the name of the output acl that applies if the location policy rules are matched. The name can...
Page 345
Configuring mobility profiles 345 4 click new mobility profile. The create mobility profile wizard appears..
Page 346
346 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters 5 in the profile name box, type the name of the mobility profile. The name can be up to 16 alphanumeric characters, and it cannot contain tabs. 6 in the ports list, specify ports to include in the mobility pr...
Page 347
Using access control lists for security 347 10 click close. The create mobility profiles dialog box is active. 11 click finish to save the changes and close the wizard. Using access control lists for security an access control list (acl) filters packets to restrict or permit network usage by certain...
Page 348
348 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters setting up acl basic properties to set up acl basic properties: 1 access the wx switch wizard for the wx switch. (see “accessing the modify switch wizard” on page 185.) 2 select aaa at the top of the wizard, ...
Page 349
Using access control lists for security 349 5 in the acl name box, type the name for the acl (1 to 32 alphanumeric characters, with no spaces or tabs). The name can include hyphens (-), underscores (_), or periods (.). Acl names are case-sensitive and must begin with a letter. Do not include any of ...
Page 350
350 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters ■ icmp — filters packets by source and destination ip addresses, tos, precedence, icmp type, or icmp code. For more information, see “creating an icmp ace” on page 355. ■ udp — filters packets by source and d...
Page 351
Using access control lists for security 351 use 6 or 7 only for spectralink voip phones. For other voip phones, use 4 or 5. By default, the cos level is -1, which indicates that class of service is not specified. 5 to enable counting of packets filtered by an acl, select enable hit count. 6 in the s...
Page 352
352 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters ■ 1 (minimum monetary cost) — packets with minimum monetary cost tos defined are filtered. ■ 2 (maximum reliability) — packets with maximum reliability tos defined are filtered. ■ 4 (maximum throughput) — pac...
Page 353
Using access control lists for security 353 ■ to create a tcp ace, click new tcp ace. The create tcp ace dialog box appears. ■ to create a udp ace, click new udp ace. The create udp ace dialog box appears..
Page 354
354 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters 3 in the action list, select permit to allow access if the conditions in the ace are matched, or deny to refuse access if the conditions are matched. 4 if you select permit, in the cos box, specify a class-of...
Page 355
Using access control lists for security 355 for a complete list of port numbers, see www.Iana.Org/assignments/port-numbers . 11 if you specified a port range as the operator, you must specify the end value for the range. In the range end box, specify an ending port number for the range. 12 to define...
Page 356
356 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters 3 to enable counting of packets filtered by an acl, select enable hit count. 4 define the ip attributes (source and destination ip addresses, the tos, and the precedence). The steps are the same as the steps ...
Page 357
Using access control lists for security 357 creating a layer 4 protocol ace to create a layer 4 protocol ace: 1 in the acl setup page of the create acl wizard, click new. A list of aces appears. 2 select new l4 protocol ace. The create l4 protocol ace dialog box appears. 3 in the action list, select...
Page 358
358 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters 6 define the ip attributes (source and destination ip addresses, the tos, and the precedence). The steps are the same as the steps when configuring an ip ace. See step 6 on page 351 through step 9 on page 352...
Page 359
Using access control lists for security 359 to add aces to an acl and organize them 1 in the acl setup page, select an ace from the list of aces. 2 if you have not already typed the acl name in the acl name box, do so now. 3 to change the position of the ace, click move up or move down until the ace...
Page 360
360 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters mapping user-based acls when you map a user-based acl, you can use any defined acl, even if that acl is also mapped to a port, vlan, or virtual port. You can set a filter-id authorization attribute at the rad...
Page 361
Using access control lists for security 361 mapping acls to ports, vlans, or virtual ports you can map acls to ports (or port groups), vlans, or virtual ports. You cannot map an acl to a map port or a wired authentication port. To map an acl to ports, vlans, or virtual ports: 1 in the create acl wiz...
Page 362
362 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters mapping an acl to a distributed map 1 in the acl map page, click new. 2 select new acl distributed map map. The create acl distributed map map dialog box appears. 3 in the direction list, select in to filter ...
Page 363
Using access control lists for security 363 mapping an acl to a vlan 1 in the acl map page, click new. 2 select new acl vlan map. The create acl vlan map dialog box appears. 3 in the direction list, select in to filter incoming packets or out to filter outgoing packets. 4 in the type list, select id...
Page 364
364 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters mapping an acl to a port 1 in the acl map page, click new. 2 select new acl port map. The create acl port map dialog box appears. 3 in the direction list, select in to filter incoming packets or out to filter...
Page 365
Using access control lists for security 365 mapping an acl to a virtual port to map an acl to a virtual port: 1 in the acl map setup page, click new. 2 select new acl vport map. The create acl vport map dialog box appears. 3 in the direction list, select in to filter incoming packets or out to filte...
Page 366
366 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters configuring 802.1x parameters the ieee 802.1x standard provides an authentication framework that supports a variety of methods for authenticating and authorizing network access for wired or wireless users. Yo...
Page 367
Configuring 802.1x parameters 367 8 to specify the number of seconds the wx switch waits before retransmitting an extensible authentication protocol over lan (eapol) packet, specify the timeout value (1 to 65,535 seconds) in the retransmit timeout box. The default is 5 seconds. 9 to specify the numb...
Page 368
368 c hapter 7: c onfiguring a uthentication , a uthorization , and a ccounting p arameters network. However, mss does not remove a wireless client from the network under these circumstances. 15 to specify the number of seconds before reauthentication is attempted, specify the timeout value, from 60...
Page 369: Anaging
8 m anaging wx s ystem i mages and c onfigurations this chapter describes the management of wx system files. It includes information about uploading a wx switch configuration into 3wxm, verifying configuration information, synchronizing local and network changes, deploying wx switches from a network...
Page 370
370 c hapter 8: m anaging wx s ystem i mages and c onfigurations uploading a wx switch configuration into 3wxm if you have already installed and configured a wx, you can upload its configuration into 3wxm. You must first set the country code using the set system countrycode command in the cli. For m...
Page 371
Uploading a wx switch configuration into 3wxm 371 not defined in 3wxm, uploading the wx configuration creates the mobility domain. If no mobility domain is specified in the configuration, the wx is uploaded into the default mobility domain. When you upload a wx configuration, the version of the mss ...
Page 372
372 c hapter 8: m anaging wx s ystem i mages and c onfigurations 1 in the main 3wxm window, select changes > upload. The upload wireless switch wizard appears. 2 in the ip address box, type the ip address for the wx switch. 3 in the enable password box, type the enable password for the wx switch. Th...
Page 373
Verifying configuration information 373 ■ make sure that the wx certificate is properly installed. ■ if the connection time takes more than 30 seconds, adjust the connect timeout value. (see “changing network synchronization options” on page 502.) verifying configuration information 3wxm uses a set ...
Page 374
374 c hapter 8: m anaging wx s ystem i mages and c onfigurations the verification tab contains a config verification tab and a network verification tab: ■ the config verification tab shows errors and warnings for wx switch configuration information in 3wxm. ■ the network verification tab shows error...
Page 375
Verifying configuration information 375 ■ show errors — error messages are listed only when this option is selected. ■ show warnings — warning messages are listed only when this option is selected. ■ show disabled — disabled rules are listed only when this option is selected. (see “disabling a rule ...
Page 376
376 c hapter 8: m anaging wx s ystem i mages and c onfigurations you can disable rules on a per-instance basis or globally for all instances. ■ if you disable a rule for a specific instance, 3wxm stops alerting you about that particular instance but still uses the rule when evaluating other configur...
Page 377
Verifying configuration information 377 to change verification options 1 on the toolbar of the verification tab click options. The verification options dialog box appears. 2 select the cases in which you want 3wxm to perform verification: ■ verify changes only — 3wxm performs verification only on co...
Page 378
378 c hapter 8: m anaging wx s ystem i mages and c onfigurations ■ allow errors to be uploaded — 3wxm allows you to upload a wx switch’s configuration into 3wxm even if it contains errors. 3 click close to place the changes into effect and close the dialog box. Disabling and reenabling rules if you ...
Page 379
Verifying configuration information 379 to filter the rule list based on class: a click filter by class. The rule list changes to list the rules in the selected class. B select a rule class from the listbox. The list of rules changes to list the rules in the selected class. In this example, the sele...
Page 380
380 c hapter 8: m anaging wx s ystem i mages and c onfigurations 5 in the rule column, click on the rule name. The disable settings are displayed and become editable. ■ if the rule is disabled for all instances, the disable all instances option is selected. ■ if individual instances of the rule are ...
Page 381
Verifying configuration information 381 6 reenable the rule or instances: ■ to reenable a rule all of whose instances are disabled, click on the checkbox in the enabled column. The disable all instances option is deselected. ■ to reenable an individual instance of a rule, click on the checkbox next ...
Page 382
382 c hapter 8: m anaging wx s ystem i mages and c onfigurations 9 to leave all instances disabled, go to step 10. To disable only specific instances: a select disable selected instances. The individual instances of the rule are listed..
Page 383
Synchronizing local and network changes 383 b click next to the instances you want to disable, then go to step 10. 10 click close. Synchronizing local and network changes whenever configuration changes occur to a wx switch, 3wxm alerts you that changes have occurred. If configuration changes occur o...
Page 384
384 c hapter 8: m anaging wx s ystem i mages and c onfigurations you also can display the managed devices tab by selecting view > managed devices from the main 3wxm toolbar. The managed devices tab enables you to review changes and synchronize the wx switches in the network with their counterparts i...
Page 385
Synchronizing local and network changes 385 ■ for network changes: ■ review — display the configuration changes that have occurred in the network for the selected wx switch. ■ accept — update the wx switch in the network plan with the changes from the live wx switch. ■ undo — remove the changes from...
Page 386
386 c hapter 8: m anaging wx s ystem i mages and c onfigurations managing wx switch configuration changes you can review wx switch configuration changes, deploy local changes, and accept or undo changes. To review changes 1 display the managed devices tab by doing one of the following: ■ click on lo...
Page 387
Synchronizing local and network changes 387 4 click close to return to the managed devices tab. 5 do one of the following: ■ to deploy local changes, go to “to deploy local changes”. ■ to accept network changes, go to “to accept network changes”. ■ to undo changes, go to “to undo changes”. To deploy...
Page 388
388 c hapter 8: m anaging wx s ystem i mages and c onfigurations the dialog lists the wx switches that have configuration changes. 3 select the wx switches to which you want to deploy the changes. To select more than one wx, click shift while clicking to select contiguous items, or click ctrl while ...
Page 389
Synchronizing local and network changes 389 2 do one of the following: ■ to undo local changes, click undo in the local changes group box. ■ to undo network changes, click undo in the network changes group box. The status is shown in the network status and local status columns. Synchronizing when th...
Page 390
390 c hapter 8: m anaging wx s ystem i mages and c onfigurations 3 to enable the detection of configuration changes in the network, make sure poll config is selected. To disable automatic detection, clear poll config. By default, this option is enabled. 4 to specify how often network checks occur, s...
Page 391
Deploying wx switches from a network plan to the network 391 this dialog box is also accessible from the managed devices tab, and is displayed when you click deploy on that tab. To deploy network plan changes to the network to deploy network plan changes to the network, use the following procedure. ...
Page 392
392 c hapter 8: m anaging wx s ystem i mages and c onfigurations the dialog lists the wx switches that have configuration changes. To deploy wx switches from a network plan to the network to deploy wx switches from a network plan to the network, use the following procedure. 1 select the wx switches ...
Page 393
Distributing image and configuration files 393 by default, this option is selected. If you deselect this option, 3wxm sends the configuration changes to the wx switch but the changes are not saved in the wx switch’s configuration file and are therefore not restored following a restart of the wx swit...
Page 394
394 c hapter 8: m anaging wx s ystem i mages and c onfigurations 4 select the system image. 5 click add to repository. The image is added to the image repository and appears in the image list. 6 to close the image repository dialog box, click close. To delete a system image 1 in the image repository...
Page 395
Distributing image and configuration files 395 2 in the mobility domain selection list, select the mobility domain of the wx switch or switches you want to distribute images to. 3 select a wx or multiple wx switches. To select more than one wx, click shift while clicking to select contiguous items, ...
Page 396
396 c hapter 8: m anaging wx s ystem i mages and c onfigurations distributing wx configuration files you can distribute a complete wx configuration defined in a network plan as a file and download it to one or more wx switches at one time. Using this feature replaces the current configuration file o...
Page 397
Importing and exporting wx switch configuration files 397 if you import a configuration containing information that an older version of 3wxm or mss does not support, the information is ignored when the configuration is imported. If you import a wx switch configuration, you must enable 3wxm managemen...
Page 398
398 c hapter 8: m anaging wx s ystem i mages and c onfigurations 4 click select files. The select files to import dialog box appears. 5 select one or more configuration files to be imported. To make multiple selections, press shift (for contiguous items) or control (for noncontiguous items) while cl...
Page 399
Importing and exporting wx switch configuration files 399 to export a configuration to export a configuration, use the following procedure. 1 select file > export. The export configurations dialog box appears. 2 in the export from list, select the mobility domain whose configuration you want to expo...
Page 400
400 c hapter 8: m anaging wx s ystem i mages and c onfigurations 5 to have 3wxm create a backup copy of a previous configuration file, select copy files before overwriting. 6 to include the default configuration commands in the exported file, select export defaults. 7 select the format for the expor...
Page 401
Working with domain policies 401 sure that all domain policy changes are applied to existing wx switches before you create a new wx. 3com recommends that you verify the network plan before applying domain policy changes to wx switches. To apply domain policy changes to wx switches: 1 in the main 3wx...
Page 402
402 c hapter 8: m anaging wx s ystem i mages and c onfigurations ■ clear the apply checkbox for any changes you do not want to apply. ■ click the clear all button to clear all checkboxes. 5 to apply the domain policy to another wx in the mobility domain, repeat step 4. 6 click apply changes. 7 click...
Page 403
Rebooting wx switches or map access points 403 6 to apply configuration changes to another domain policy, repeat step 3 through step 5. 7 click close to close the policy manager dialog box. If you later make configuration changes to a domain policy, you can apply the changes to one or more wx switch...
Page 404
404 c hapter 8: m anaging wx s ystem i mages and c onfigurations a list of the managed wx switches in the mobility domain appears. 3 do one of the following: ■ to reboot a wx, select it from the list on the wireless switch tab. ■ to reboot a map, click managed access point, and select the map(s) you...
Page 405: Anaging
9 m anaging c ertificates a digital certificate is a form of electronic identification for computers. This chapter describes processing and managing certificates, and distributing pks #12 files. Overview a digital certificate is a form of electronic identification for computers. The 3com mobility sy...
Page 406
406 c hapter 9: m anaging c ertificates before 3wxm can communicate with the wx switch or monitoring service over a secure https connection, you must specify how to deal with the certificate required for secure communication. The options you select in this dialog box apply to all https connections w...
Page 407
Managing certificates 407 2 do one of the following: ■ click accept to allow the connection to the wx switch. If you did not select either of the options in step 1, when you click accept, a secure connection with these certificate credentials is allowed for this session until you close the network p...
Page 408
408 c hapter 9: m anaging c ertificates distributing pkcs #12 files you can use 3wxm to distribute pkcs #12 files to one or more wx switches. After you select the file to distribute, you must enter the pkcs #12 password that was used to generate the certificate. You must also select whether the file...
Page 409
Distributing pkcs #12 files 409 6 in the certificate type list, select one of the following: ■ eap — to install an 802.1x/eap certificate ■ web — to install a web aaa certificate ■ admin — to install an administrative certificate 7 click start download. Download progress appears in the status column...
Page 410
410 c hapter 9: m anaging c ertificates.
Page 411: Onitoring
10 m onitoring the n etwork this chapter describes how to use the 3wxm monitoring service. It includes information about monitoring service requirements, accessing monitored data, using the explore, status summary, client monitor, rf monitor, and rf trends windows, and accessing realtime performance...
Page 412
412 c hapter 10: m onitoring the n etwork monitoring service requirements to enable the service to monitor network data, you or the monitoring services administrator must specify the wx switches to monitor. The monitoring service collects data from the switches and updates the information in the win...
Page 413
Using the explore window 413 3 do one of the following: ■ select view > monitor or view > monitor in new window from the toolbar in the main 3wxm window. ■ right-click on the object and select monitor or monitor in new window from the pulldown list. The monitor tab appears in the content panel. Each...
Page 414
414 c hapter 10: m onitoring the n etwork in either view, the operational status of 3com equipment is indicated by the following colors: ■ green — up ■ yellow — up (but with minor service degradation) ■ orange — up (but with major service degradation) ■ red — down ■ blue — unknown toolbar options th...
Page 415
Using the explore window 415 table 29 toolbar options in floor view of explore window icon description show the zoom navigator panel. Zoom in. Zoom out. Refresh the information. Fit the view in the explore window. Print the view displayed in the explore window. Show rf coverage using modifies displa...
Page 416
416 c hapter 10: m onitoring the n etwork threshold flags a red flag next to an object in the link view of the explore window indicates that a threshold for the object has been exceeded. The thresholds are defined by the monitoring service. (see “changing monitoring service preferences” on page 535....
Page 417
Using the explore window 417 when a red flag appears in the explore window, the column for the statistic whose threshold was exceeded also turns red in the rf trends window. Displaying object details to drill down for more detailed information for an object in the explore window, double-click on the...
Page 418
418 c hapter 10: m onitoring the n etwork click on one or more of the following icons on the explore window’s toolbar: the jagged appearance of the coverage area is normal and is caused by the rf obstacles around the radio. The rf obstacle information in the floor plan enables 3wxm to more accuratel...
Page 419
Using the explore window 419 for all display options except the baseline association rate, a legend is displayed at the bottom of the window to indicate the values represented by each color. Taking rf measurements in the floor view, you can take an rf measurement at any point on the floor plan. An r...
Page 420
420 c hapter 10: m onitoring the n etwork you can change the rssi options even after measurement data is displayed. The data is immediately updated. To take a new measurement, click on the new measurement point. The measurement data is immediately updated for the new measurement point. Using the sta...
Page 421
Using the client monitor window 421 the window begins accumulating data as soon as the monitoring service begins monitoring client activity traps from wx switches. The window accumulates data from up to 1000 traps, then begins discarding the oldest traps to make way for new traps. If data does not a...
Page 422
422 c hapter 10: m onitoring the n etwork refreshing client data by default, the data displayed in the client monitor window is not refreshed. You can refresh the data on demand, or automatically at regular intervals. If you enable automatic data refresh, the data is refreshed based on the client mo...
Page 423
Using the client monitor window 423 table 33 client activity columns when scope is a mobility domain column description scope scope of the data displayed in the row. The scope for each row in the client activity tab is always a wx switch. The down arrow in front of the wx switch name indicates that ...
Page 424
424 c hapter 10: m onitoring the n etwork data displayed when the scope is a switch, map, or radio when a wx switch, map access point, or individual radio is selected in the organizer panel, the client monitor window’s client activity tab displays a row of information for each client activity trap g...
Page 425
Using the client monitor window 425 the activity details section at the bottom of the window displays details for the selected row of information. The details differ depending on the trap type. The following tables list the data displayed in the activity details section for each trap type. Table 34 ...
Page 426
426 c hapter 10: m onitoring the n etwork table 35 activity details for association failure column description mac address mac address of the client. Association failure cause cause of the association failure: ■ already-exist ■ cipher-mismatch ■ cipher-rejected ■ load-balance ■ other ■ switching-ssi...
Page 427
Using the client monitor window 427 client location mobility domain, wx switch, map access point, and radio that was dealing with the client. Session id id used by 3com equipment to track the session within the mobility domain. Auth server ip system ip address of the wx switch that was attempting to...
Page 428
428 c hapter 10: m onitoring the n etwork authorization failure cause reason the authorization failure trap was generated: ■ acl-mismatch ■ crypto-type-mismatch ■ end_date_mismatch ■ location-policy ■ mobility-profile-mismatch ■ other ■ ssid-mismatch ■ start_date_mismatch ■ timeofday-mismatch ■ user...
Page 429
Using the client monitor window 429 auth protocol type 802.1x protocol used to authenticate the client: ■ eap-tls ■ md5 ■ none ■ pass-through ■ peap rssi strength of the signal received by the radio from the client. Session id id used by 3com equipment to track the session within the mobility domain...
Page 430
430 c hapter 10: m onitoring the n etwork table 39 activity details for disassociation column description user name username of the client. Mac address mac address of the client. Client vlan name vlan to which the client was assigned. Auth protocol type 802.1x protocol used to authenticate the clien...
Page 431
Using the client monitor window 431 dot1x state 802.1x state of the client: ■ administrative-kill ■ bad-rsnie ■ bonded-auth-failure ■ fourway-hs-failure ■ max-sessions-exceeded ■ other ■ quiet-period ■ timeout ■ user-glob-mismatch mac address mac address of the client. Ssid ssid the client was reque...
Page 432
432 c hapter 10: m onitoring the n etwork displaying client session information the client session tab displays session statistics. The data fields in the display depend on the scope: ■ if a mobility domain is selected, a row of data is displayed for each wx switch in the mobility domain. ■ if a wx ...
Page 433
Using the client monitor window 433 data displayed when the scope is a switch, map, or radio when a wx switch, map access point, or individual radio is selected in the organizer panel, the client monitor window’s client sessions tab displays a row of information for each client session. Table 43 lis...
Page 434
434 c hapter 10: m onitoring the n etwork displaying session details to display details for a user session, select the session in the client sessions list. Details for the session appear in the following tabs at the bottom of the window: ■ session properties ■ session statistics ■ location history t...
Page 435
Using the client monitor window 435 displaying session properties on the client sessions tab, select the session properties tab at the bottom of the window. Table 44 lists the information displayed on the tab. Table 44 session properties columns column description username username the client used t...
Page 436
436 c hapter 10: m onitoring the n etwork session state state of the user session: ■ associated — user is authenticated using an 802.11 protocol and associated with a map. ■ authorizing — user is authenticated and is starting the aaa authorization process. ■ authorized — user is authorized. ■ active...
Page 437
Using the client monitor window 437 displaying session statistics on the client sessions tab, select the session statistics tab at the bottom of the window. On the session statistics tab, you can select statistics for the map the client is associated with, or total statistics for the client’s entire...
Page 438
438 c hapter 10: m onitoring the n etwork unicast packets out number of unicast packets transmitted by the radio to the client during this session. Transmit timeouts number of times a packet transmitted by the radio to a client remained unacknowledged long enough for the transmission attempt to time...
Page 439
Using the client monitor window 439 displaying session location history on the client sessions tab, select the location history tab at the bottom of the window. Each row represents a session with a 3com radio. When a client roams from one radio to another, the session on the radio the client is leav...
Page 440
440 c hapter 10: m onitoring the n etwork managing the client watch list you can add clients to a watch list. The watch list allows you to monitor client roaming history and network performance. 3wxm monitors the clients on the watch list by mac address. Adding a client to the watch list you can add...
Page 441
Using the client monitor window 441 using the find client dialog box to find a user you can use 3wxm to find users (network clients) on the network. You can search for individual users based on specific criteria, or you can find all users in a mobility domain. 1 in the client monitor window, click o...
Page 442
442 c hapter 10: m onitoring the n etwork 3 use any or all of the following search criteria: ■ in the username box, specify the username of the user you want to find. ■ in the ip address box, specify the ip address of the user. ■ in the mac address box, specify the mac address of the user. ■ in the ...
Page 443
Using the client monitor window 443 7 to add a user to the watch list in the user management tab, select the add watch checkbox in the user row. Repeat for all users that you want to add to the watch list. 8 click finish. Displaying the client watch list to display the watch list, select the client ...
Page 444
444 c hapter 10: m onitoring the n etwork details are displayed on the following tabs: ■ session — displays the session properties, session statistics, and location history tabs. These are the same tabs displayed at the bottom of the client sessions tab. (for descriptions of the data they display, s...
Page 445
Using the client monitor window 445 delta (rate of change) values are calculated with the following equation: value at end of polling interval - value at beginning of polling interval time difference (in seconds) to change how you view data values, select absolute to see absolute values or deltas to...
Page 446
446 c hapter 10: m onitoring the n etwork using the rf monitor window the rf monitor window shows detailed rf information for each radio. Radio information is displayed in the following tabs: ■ rf neighborhood — lists the other transmitting devices that the radio can hear. ■ ssid-bssid mapping — lis...
Page 447
Using the rf monitor window 447 3wxm service setup window. (see “changing monitoring settings” on page 552.) table 47 lists the information displayed in the top section of the rf monitor window. Displaying rf neighborhood information in the rf monitor window, select the rf neighborhood tab at the bo...
Page 448
448 c hapter 10: m onitoring the n etwork displaying the ssid-to-bssid mapping to display the ssids configured on a radio and their bssids, in the rf monitor window, select the ssid-bssid mapping tab at the bottom of the window. Table 48 rf monitor rf neighborhood columns column description neighbor...
Page 449
Using the rf monitor window 449 displaying the activity log the activity log displays rf auto-tuning and countermeasures activity for the radio. To display the activity log, in the rf monitor window, select the activity tab at the bottom of the window. Table 49 lists the information displayed on the...
Page 450
450 c hapter 10: m onitoring the n etwork displaying rf environment statistics to display rf environment statistics, in the rf monitor window, select the rf environment tab at the bottom of the window. Table 50 lists the information displayed on the tab. Using the rf trends window the rf trends wind...
Page 451
Using the rf trends window 451 if the snr, associated clients, or receiver threshold column is red, this indicates that the threshold configured for this parameter has been exceeded. (see “changing monitoring settings” on page 552.) when looking at graphed data, you can see the data in absolute or d...
Page 452
452 c hapter 10: m onitoring the n etwork refreshing rf trend data by default, the data displayed in the rf trends window is not refreshed. You can refresh the data on demand, or automatically at regular intervals. If you enable automatic data refresh, the data is refreshed based on the rf trending ...
Page 453
Accessing realtime performance statistics 453 2 select the scope to monitor from the list on the left side of the dialog box. 3 select the specific object(s) to monitor from the list on the right side of the dialog box. ■ to select multiple contiguous objects, click shift while selecting. ■ to selec...
Page 454
454 c hapter 10: m onitoring the n etwork 6 click start monitoring. The statistics tab for your scope selection appears in the content panel. Generally, the scope is an aggregate object, which means that it is made up of sub-objects. (the exception is when a scope is a set of ports.) when you see pe...
Page 455
Accessing realtime performance statistics 455 if you make changes in the network plan that affect the object membership list (for example, you add a wx to a mobility domain and deploy it), the current monitoring session does not update this change. Stop the session, and restart performance monitorin...
Page 456
456 c hapter 10: m onitoring the n etwork viewing current data to see the current performance data, click the current tab. To sort data you can sort data in ascending or descending order to see the highest or lowest values at a glance. To sort data, click the title of the column whose data you want ...
Page 457
Accessing realtime performance statistics 457 viewing historical data to see historical performance data in a graph, click the history tab. Graphing starts when you click the tab and is based on the polling interval you selected. To see details for historical data you can see historical data for the...
Page 458
458 c hapter 10: m onitoring the n etwork figure 14 viewing historical data (delta values) in a line graph viewing data in percentages to see a set of objects in a particular category of data as percentages in a pie chart, click the percent tab. Data for the pie chart is captured when you click the ...
Page 459
Accessing realtime performance statistics 459 to hide the list of objects that you can graph, click hide object selector. Doing this allows you to see the graph in the full width of the statistics tab. Figure 15 shows the delta values for octets in and octets out for the entire mobility domain as pe...
Page 460
460 c hapter 10: m onitoring the n etwork exporting performance data you can export performance data (absolute values only) to a file in comma-delimited text (.Csv) format. To export data to a file 1 in the statistics tab, click export absolute. The export data dialog box appears. 2 to specify a dir...
Page 461
Accessing the event log 461 accessing the event log 3wxm maintains a log of system events. The log contains messages generated by the following: ■ 3wxm client — messages generated by the instance of the 3wxm client you are using ■ 3wxm monitoring service — messages generated by the monitoring servic...
Page 462
462 c hapter 10: m onitoring the n etwork toolbar options table 52 lists the options on the event tab’s toolbar. Refreshing the data by default, the event data is refreshed whenever the 3wxm client generates a new message for itself, or receives a new message from the monitoring service. To disable ...
Page 463
Accessing the event log 463 you now see the log entries in event tab that match the criteria of the filter that you chose. To monitor event messages for a wx switch in the network plan, the switch must be in the list of monitored switches configured on the monitoring service. In addition, the log mo...
Page 464
464 c hapter 10: m onitoring the n etwork 3 in the ip address box, type an ip address or a partial ip address. For example, if you type 10.20, you see all events that pertain to ip addresses containing the string 10.20. Set the search criteria by selecting contains the string, contains all of the st...
Page 465
Accessing the event log 465 filtering events by severity you can limit the events you see in event tab based on event severity. 1 click on the severity tab. 2 select or clear the severity levels to display (the following descriptions are wx-based): ■ emergency — the wx is unusable. ■ alert — action ...
Page 466
466 c hapter 10: m onitoring the n etwork 3 click save. The filter is saved and appears in the stored filters list. Deleting filters you can delete any filter that you created, but you cannot delete predefined filters. To delete a filter: 1 in the stored filters group box, select the filter to be de...
Page 467
Accessing the event log 467 4 to copy files before overwriting them, select copy files before overwriting. By default, this option is selected. The existing file is copied to a file with a .Bak extension. 5 click export. You can see the status of the export process in the results box. 6 click close....
Page 468
468 c hapter 10: m onitoring the n etwork.
Page 469: Etecting
11 d etecting and c ombatting r ogue d evices this chapter discusses how to manage rogue devices that try to use your wireless network. Information includes an overview of detection features, enabling countermeasures, using the rogue detection tab, displaying a rogue’s geographical location, ignorin...
Page 470
470 c hapter 11: d etecting and c ombatting r ogue d evices to a wireless laptop. Users can configure a wireless network interface card (nic) in “ad hoc” mode and easily set up a simple peer-to-peer network. Although this wlan might be isolated from the corporate wlan, the users are stealing the air...
Page 471
Rogue detection requirements 471 automatically selects individual radios to send the countermeasure packets. You can issue countermeasures against specific devices. In this case, mss attacks only those devices. Rogue detection requirements rogue detection in 3wxm has the following requirements. Mobi...
Page 472
472 c hapter 11: d etecting and c ombatting r ogue d evices ■ the collect radio activity traps option is enabled on the monitoring settings tab. This option enables the monitoring service to collect countermeasures data from the countermeasurestart and countermeasurestop traps sent by the mobility d...
Page 473
Using the rogue detection tab 473 device, add the device to known addresses list. (see “ignoring friendly third-party devices”.) using the rogue detection tab to display rogue information, select view > rogue detection from the toolbar in the main 3wxm window. The rogue detection tab appears in the ...
Page 474
474 c hapter 11: d etecting and c ombatting r ogue d evices the rogue details section contains the following tabs: ■ activity log — lists activity (appearance or disappearance) of the rogue selected in the rogue list the entries in the activity log tab come from either of the following sources: ■ tr...
Page 475
Using the rogue detection tab 475 toolbar options the rogue detection tab has a toolbar. Table 53 lists the options on the toolbar. Filtering the rogue list by default, the rogue list contains all rogues detected during the most-recent polling interval, in all mobility domains in the network plan. Y...
Page 476
476 c hapter 11: d etecting and c ombatting r ogue d evices 2 select the period by which you want to filter the list from the filter by listbox: ■ current — lists the rogues detected during the most-recent polling interval. Go to step 4. ■ current hour — lists the rogues detected during the most-rec...
Page 477
Using the rogue detection tab 477 current, current hour, current day, and history tabs the current, current hour, current day, and history tabs show rogues detected in the past. ■ current — lists the rogues observed during the most-recent polling intervals. ■ current hour — lists the rogues observed...
Page 478
478 c hapter 11: d etecting and c ombatting r ogue d evices location tab the location tab displays the likely physical location of the rogue. (see “displaying a rogue’s geographical location”.) displaying a rogue’s geographical location if building and floor information for the site is modeled in th...
Page 479
Ignoring friendly third-party devices 479 ignoring friendly third-party devices by default, when countermeasures are enabled, mss considers any third-party transmitter to be a rogue device and can send countermeasures to prevent clients from using that device. To prevent mss from sending countermeas...
Page 480
480 c hapter 11: d etecting and c ombatting r ogue d evices to remove an address from the known address list to remove an address from the known address list, use the following procedure. 1 in the organizer panel, click on the plus sign next to a mobility domain name to display the objects in the do...
Page 481
Converting a rogue into a third party ap 481 3 enter the information for the ap and place the icon for the ap in its floor location, if applicable. (see “adding a third-party access point” on page 148.) to display the list in the organizer panel, click on third party aps. The third-party aps are lis...
Page 482
482 c hapter 11: d etecting and c ombatting r ogue d evices.
Page 483: Enerating
12 g enerating r eports this chapter describes the reports you can generate with 3wxm: ■ inventory ■ mobility domain configuration ■ wx configuration ■ client summary ■ client details ■ client errors ■ watch list client ■ network usage ■ rf summary ■ radio details ■ rogue summary ■ work order.
Page 484
484 c hapter 12: g enerating r eports overview the reports option of the main toolbar enables you to generate reports for network clients, rf usage, rogue devices, and 3com equipment. ■ 3com equipment reports: ■ inventory report ■ mobility domain configuration ■ wx configuration ■ network client rep...
Page 485
Generating a mobility domain configuration report 485 4 to prevent 3wxm from replacing an existing report of the same type with this new report, click next to overwrite existing files to deselect this option. 5 click generate. 6 when the report is generated, click the report link to view it. Table 5...
Page 486
486 c hapter 12: g enerating r eports generating a wx configuration report the wx configuration report lists configuration details for a wx switch. 1 select reports > wx configuration from the toolbar in the main 3wxm window. The wx configuration report dialog box appears. 2 select the wx switch for...
Page 487
Generating a client summary report 487 generating a client summary report the client summary report lists current client sessions. The data for this report comes from the monitoring service. The enable client session collection option, located in the client monitor group box of the monitoring settin...
Page 488
488 c hapter 12: g enerating r eports 2 select the scope type of the report from the report scope type listbox: ■ mobility domain ■ wireless switch ■ site ■ building ■ floor ■ coverage area 3 select the instance for which you want the report. For example, if the scope is building, select the buildin...
Page 489
Generating a client details report 489 generating a client details report the client details report lists details about current client sessions. The data for this report comes from the monitoring service. The enable client session collection option, located in the client monitor group box of the mon...
Page 490
490 c hapter 12: g enerating r eports ■ current ap statistics ■ lifetime ap statistics (see “using the client monitor window” on page 420 for information about the data columns in each section of the report.) generating a client errors report the client errors report lists error statistics for curre...
Page 491
Generating a watch list client report 491 6 to prevent 3wxm from replacing an existing report of the same type with this new report, click next to overwrite existing files to deselect this option. 7 click generate. 8 when the report is generated, click the report link to view it. The client errors r...
Page 492
492 c hapter 12: g enerating r eports 6 press enter to complete the filter. 7 repeat step 3 through step 6 for each user you want to display details for. 8 to change the output directory for the report, click on the button next to output directory, navigate to the new directory, and click select. 9 ...
Page 493
Generating an rf summary report 493 ■ floor ■ coverage area 3 select the instance for which you want the report. For example, if the scope is building, select the building. 4 select the time period for the report: ■ 1 hour ■ 24 hours ■ 7 days ■ 30 days 5 to change the output directory for the report...
Page 494
494 c hapter 12: g enerating r eports ■ building ■ floor ■ coverage area 3 select the instance for which you want the report. For example, if the scope is building, select the building. 4 select the time period for the report: ■ 1 hour ■ 24 hours ■ 7 days ■ 30 days 5 to change the output directory f...
Page 495
Generating a rogue details report 495 3 to change the output directory for the report, click on the button next to output directory, navigate to the new directory, and click select. 4 to prevent 3wxm from replacing an existing report of the same type with this new report, click next to overwrite exi...
Page 496
496 c hapter 12: g enerating r eports generating a rogue summary report the rogue summary report lists information about rogues. The data for this report comes from the monitoring service. The enable rogue detection option, located in the rogue detection group box of the monitoring settings tab, mus...
Page 497
Generating a work order 497 generating a work order a work order provides all of the necessary information for the physical installation of the 3com mobility system. A work order shows where the map access points should be installed, wx initial setup configuration information, and projected rssi inf...
Page 498
498 c hapter 12: g enerating r eports.
Page 499: Sing
A u sing 3wxm w ith hp o pen v iew if you installed the hp openview plug-in during installation of 3com wireless lan switch manager (3wxm), you can use hp openview in conjunction with 3wxm to manage the 3com mobility system. This chapter discusses preparing to use hp openview and 3wxm, and starting ...
Page 500
500 a ppendix a: u sing 3wxm w ith hp o pen v iew.
Page 501: Hanging
B c hanging 3wxm p references this chapter discusses how to set 3com wireless lan switch manager (3wxm) client preferences. It describes how to reset preferences values and change options for network synchronization, user interface, persistence, tools, certificate management, rf planning, and 3wxm l...
Page 502
502 a ppendix b: c hanging 3wxm p references figure 16 preferences dialog box resetting preferences values you can reset the preferences values to their default values by doing one of the following: ■ to reset the values for a tab, click the tab to display it, and click reset. (each tab has a reset ...
Page 503
Changing network synchronization options 503 3 to set the amount of time that 3wxm waits for a connection to be established to a wx before trying to connect again, specify the timeout (1 to 30 seconds) in the connect timeout box. The default is 5 seconds. 4 to set the number of times (0 to 5) 3wxm t...
Page 504
504 a ppendix b: c hanging 3wxm p references changing user interface options you can change the following user interface options: ■ confirmation prompt when closing wizard pages ■ window style for exploring the topological view in the main 3wxm window ■ size of icons in 3wxm ■ placement of the wizar...
Page 505
Changing persistence options 505 5 within icon size, select one of the following: ■ 16x16 — change all icons to 16x16 pixels. This is the default setting. ■ 20x20 — change all icons to 20x20 pixels. ■ 24x24 — change all icons to 24x24 pixels. 6 within show wizard index, select one of the following: ...
Page 506
506 a ppendix b: c hanging 3wxm p references 3 to enable automatic saving of changes to a network plan, select auto save changes. To disable this option, clear auto save changes. By default, this option is disabled. 4 in the save interval box, specify how often network plan is to be saved, from 1 to...
Page 507
Changing certificate management options 507 the default telnet executable file is c:\windows\system32\telnet.Exe. You can also click browse to navigate the computer filesystem. 4 to change the web browser executable file or location used by 3wxm, type the path of the executable file in the browser e...
Page 508
508 a ppendix b: c hanging 3wxm p references to clear this option, clear always accept self-signed certificates. By default, this option is disabled. The 3wxm client accepts a certificate only if the certificate is signed by a certificate authority (ca). 4 click close to close the preferences dialog...
Page 509
Changing options for rf planning 509 changing colors you can change the color schemes for showing the following types of rf information: ■ 802.11a channels ■ 802.11b and 802.11g channels ■ rf obstacles ■ radio transmit data rates ■ receive signal strength (rssi) ■ signal-to-noise ratio (snr) ■ clien...
Page 510
510 a ppendix b: c hanging 3wxm p references see one of the following sections: ■ for more information about using the color palette, see “defining a color from the palette” on page 511. ■ for more information about using hsb, see “defining a color by changing hsb properties” on page 512. ■ for more...
Page 511
Changing options for rf planning 511 defining a color from the palette 1 to specify a color using the color palette, click swatches in the choose color dialog box. 1 from the color palette, click the color you want to see. Repeat until you find the color you want. In the preview box, you can see the...
Page 512
512 a ppendix b: c hanging 3wxm p references defining a color by changing hsb properties you can define colors by changing the hue, saturation, and brightness (hsb). ■ hue is the color itself (for example, blue, orange, or purple). Hue is measured in degrees (0 to 360 degrees). ■ saturation is the s...
Page 513
Changing options for rf planning 513 3 to change the saturation value, select the s option and do one of the following: ■ in the s box, specify a value between 0 and 100 percent. ■ use the slider to specify the saturation value. 4 to change the brightness value, select the b option and do one of the...
Page 514
514 a ppendix b: c hanging 3wxm p references 2 use the red, green, and blue sliders to define a color. You can see a preview of the color in the preview box. 3 click ok to accept the color. The rf planning options tab in the preferences dialog box is active. 4 do one of the following: ■ change anoth...
Page 515
Changing 3wxm logging options 515 3 in the log event level list, select one of the following event levels: ■ critical — a critical condition has occurred that requires immediate resolution. ■ warning — an event that might require attention has occurred. ■ info — informational messages only. No actio...
Page 516
516 a ppendix b: c hanging 3wxm p references.
Page 517: 3Wxm V
C 3wxm v erification r ules this appendix lists the verification rules used by 3wxm. Rules are listed alphabetically by rule class. (for information about how to interpret and respond to errors or warnings that occur when a configuration or a device in the network conflicts with a rule, see “verifyi...
Page 518
518 a ppendix c: 3wxm v erification r ules table 60 802.1x network access rules title description classification 802.1x policy server check verifies that the authentication method includes a server group. Error 802.1x policy server group check verifies that no more than four server groups are specif...
Page 519
519 table 62 acl rules title description classification ace requirement check verifies that each acl contains at least one ace. Error conflicting ace check verifies that two aces do not contradict each other. Warning duplicate acl map distributed map check verifies that the configuration does not co...
Page 520
520 a ppendix c: 3wxm v erification r ules table 64 console access rules title description classification access rule disabled check verifies whether the access rule is enabled in 3wxm. The rule does not take effect and is not deployed to wx switches in the network unless the rule is enabled in 3wxm...
Page 521
521 map boundary check verifies that a map’s wiring closet is the same as the wiring closet of the coverage area that uses that map. Error map coverage area check verifies that all coverage areas that share a map have the map in the same wiring closet. Error wx support of distributed map check verif...
Page 522
522 a ppendix c: 3wxm v erification r ules table 70 ip services rules title description classification default route check verifies that a maximum of four static routes are configured per destination. (this includes default routes, which have a destination of 0.0.0.0/0.) error ntp servers check veri...
Page 523
523 table 72 location policy rules title description classification duplicate location policy rule check verifies that each location policy rule is unique. Warning location policy rule check ■ verifies the following: ■ a vlan name, incoming acl name, or outgoing acl name is assigned to a location po...
Page 524
524 a ppendix c: 3wxm v erification r ules aaa user/group attribute mobility-profile check verifies that a mobility-profile attribute specified for a user or user group exists. Warning aaa user/group attribute service-type check verifies that the service-type is an integer from 1 to 11. Error aaa us...
Page 525
525 table 76 mac user group rules title description classification aaa user/group attribute encryption-type check verifies that the encryption-type attribute is in the range of 0 to 64. Error aaa user/group attribute end-date check verifies that the end-date attribute is specified in the following f...
Page 526
526 a ppendix c: 3wxm v erification r ules table 78 map radio rules title description classification beacon ssid check verifies that an mp-101 or mp-122 is not configured in the network plan to advertise (beacon) more than one ssid. Error maximum allowed tx power check verifies that the radio has a ...
Page 527
527 table 80 mobility profile rules title description classification mobility profile ports check verifies that there is at least one physical port in the selected port list of a mobility profile. Error table 81 network plan rules title description classification country code check verifies that all...
Page 528
528 a ppendix c: 3wxm v erification r ules table 84 radius server group rules title description classification radius server group radius server check verifies that at least one radius server is defined in a radius server group. Error radius server group radius servers check verifies that a radius s...
Page 529
529 wpa authentication check verifies that at least one authentication option is selected if wpa is the security mode. Error wpa cipher check verifies that at least one cipher option is selected if wpa is the security mode. Error table 88 stp port rules title description classification stp portfast ...
Page 530
530 a ppendix c: 3wxm v erification r ules table 90 user rules title description classification aaa user password check verifies that a password is configured for the user. Warning aaa user/group attribute encryption-type check verifies that the encryption-type attribute is in the range of 0 to 64. ...
Page 531
531 aaa user/group attribute idle-timeout check verifies that the idle-timeout is a positive integer. Error aaa user/group attribute mobility-profile check verifies that a mobility-profile attribute specified for a user or user group exists. Warning aaa user/group attribute service-type check verifi...
Page 532
532 a ppendix c: 3wxm v erification r ules table 93 web network access rules title description classification access rule disabled check verifies whether the access rule is enabled in 3wxm. The rule does not take effect and is not deployed to wx switches in the network unless the rule is enabled in ...
Page 533
533 system ip assignment check verifies that the system ip address for the wx is assigned, if the wx is managed. Assignment means that the system ip address has been assigned to a vlan and the vlan has a non-zeros ip address. Error table 94 wireless switch rules (continued) title description classif...
Page 534
534 a ppendix c: 3wxm v erification r ules.
Page 535: Hanging
D c hanging m onitoring s ervice p references this chapter discusses how to start and stop the monitoring service, how to enable the 3wxm client to access the monitoring service, changing service settings, selecting wx switches to monitor, changing wx connection settings, changing monitoring setting...
Page 536
536 a ppendix d: c hanging m onitoring s ervice p references figure 17 3wxm services setup dialog box the 3wxm services setup window contains a configuration area and a message area at the bottom. When you click save to implement changes you make on one of the window’s tabs, the monitoring service v...
Page 537
Starting or stopping the monitoring service 537 starting or stopping the monitoring service the monitoring service is started automatically when you complete installation and starts automatically whenever you restart your system. You can start the monitoring service from within 3wxm or from windows ...
Page 538
538 a ppendix d: c hanging m onitoring s ervice p references the monitoring service requires configuration before it can provide data to the 3wxm client. See the other sections in this chapter. 1 select monitor -> service selection from the toolbar in the main 3wxm window. The monitor service select...
Page 539
Enabling 3wxm client to access the monitoring service 539 5 enter a username and password, if required for access to the service. Usernames and passwords for accessing the monitoring service are configured on the service settings tab. (see “changing service settings” on page 542.) 6 click next. The ...
Page 540
540 a ppendix d: c hanging m onitoring s ervice p references b wait one minute for 3wxm to retrieve updates from the server, then check the color of the objects for 3com equipment displayed in the explore window. ■ if the status color is blue, then 3wxm is not receiving status data from the server y...
Page 541
Enabling 3wxm client to access the monitoring service 541 the options you select in this dialog box apply to all https connections with the 3wxm client. For example, the 3wxm client also checks the validity of certificates presented by wx switches, and the settings you select in this dialog affect t...
Page 542
542 a ppendix d: c hanging m onitoring s ervice p references to reject the certificate and refuse the connection, click reject. The 3wxm ends the connection. The certificate check dialog box is redisplayed each time the 3wxm client attempts to establish a connection with the monitoring service. Chan...
Page 543
Changing service settings 543 needs to save backup copy 49, the service deletes backup copy 1 to make room for the new backup. 7 to change the name of the key store file that contains the encryption keys the monitoring service uses for authentication with 3wxm, edit the name in the file box. The def...
Page 544
544 a ppendix d: c hanging m onitoring s ervice p references the monitoring service automatically makes the first user account you add an admin account. ■ add provision account — users with provision role can change the list of wx switches monitored by the service. ■ add monitor account — users with...
Page 545
Selecting wx switches to monitor 545 12 add other users if needed, then click save to save the changes or cancel to cancel the changes. 13 click another tab to configure more settings or click close to close the 3wxm services setup dialog box. Selecting wx switches to monitor you must specify the wx...
Page 546
546 a ppendix d: c hanging m onitoring s ervice p references the monitoring service does not monitor any wx switches by default. Also, if you change network plans later and want to monitor the wx switches in the new plan, you must add the wx switches to the list of monitored wx switches. The monitor...
Page 547
Selecting wx switches to monitor 547 3 to add all the wx switches from a mobility domain in the network plan, click add from plan. The network plan wx dialog box is displayed..
Page 548
548 a ppendix d: c hanging m onitoring s ervice p references a select the mobility domain from the mobility domain box. The wx switches configured in that mobility domain are listed. B click on the wx switches you want to add. To make multiple selections, press shift (for contiguous items) or contro...
Page 549
Selecting wx switches to monitor 549 for the monitoring service to access the wx switch, the wx switch must have an enable password configured by the wx switch administrator. To configure or change the enable password on the wx switch, use the set enablepass command. E click ok to add the wx switch ...
Page 550
550 a ppendix d: c hanging m onitoring s ervice p references changes to the wx switch. (see “managing wx system images and configurations” on page 369.) 9 repeat step 7 and step 8 to change snmp settings for other wx switches if needed. 10 click save to save the changes or cancel to cancel the chang...
Page 551
Changing wx connection settings 551 3 to change the number of seconds the monitoring service waits for a tcp connection with a wx switch to reach the connect stage, type or select the value in the connect timeout box. You can specify from 1 to 30 seconds. The default is 15 seconds. 4 to change the n...
Page 552
552 a ppendix d: c hanging m onitoring s ervice p references by default, the monitoring service accepts certificates from wx switches regardless of whether they are generated by a certificate authority (ca) or they are self-signed certificates. When you disable this option, the accept self-signed ce...
Page 553
Changing monitoring settings 553 table 95 sources of monitor data 3wxm client display data source default event tab 3wxm client, for 3wxm client messages enabled monitoring service, for monitoring service messages enabled enable log monitoring option, for wx switch messages disabled monitor tab — ex...
Page 554
554 a ppendix d: c hanging m onitoring s ervice p references the options that use snmp trap data require the corresponding snmp traps to be enabled on the monitored wx switches and also require the monitoring service to be a trap receiver for each of the wx switches. (see “selecting wx switches to m...
Page 555
Changing monitoring settings 555 to change monitoring settings to change monitoring settings, use the following procedure. 1 select tools > 3wxm services setup. The 3wxm services setup dialog box appears. (see figure 17 on page 536.) 2 click the monitoring settings tab. 3 to change the number of min...
Page 556
556 a ppendix d: c hanging m onitoring s ervice p references 4 to change settings for monitoring of the log buffers on wx switches: a select enable log monitoring. This option is disabled by default. B to change the number of minutes between queries of the wx switches’ log buffers, change the value ...
Page 557
Changing monitoring settings 557 b to enable the monitoring service to track channel and power changes caused by rf auto-tuning, and also track countermeasures, select collect radio activity traps. This option enables the monitoring service to collect data from the following traps: autotuneradiochan...
Page 558
558 a ppendix d: c hanging m onitoring s ervice p references 9 click another tab to configure more settings or click close to close the 3wxm services setup dialog box. Accessing the monitoring service log you can access the monitoring service log through a web browser. To access the monitoring servi...
Page 559
Restoring the database 559 to restore the database: 1 stop the monitoring service. (see “starting or stopping the monitoring service” on page 537.) 2 access a command-line interface on the machine where the monitoring service is installed. 3 enter the following command: dbtools -restore [filename.Zi...
Page 560
560 a ppendix d: c hanging m onitoring s ervice p references.
Page 561: Btaining
E o btaining s upport for your p roduct register your product warranty and other service benefits start from the date of purchase, so it is important to register your product quickly to ensure you get full use of the warranty and other service benefits available to you. Warranty and other service be...
Page 562
562 a ppendix e: o btaining s upport for your p roduct 3com knowledgebase helps you troubleshoot 3com products. This query-based interactive tool is located at http://knowledgebase.3com.Com and contains thousands of technical solutions written by 3com support engineers. Access software downloads sof...
Page 563
Contact us 563 product is registered and under warranty, you can obtain an rma number online at http://esupport.3com.Com/ . First time users will need to apply for a user name and password. Contact us 3com offers telephone, e-mail and internet access to technical support and repair services. To acce...
Page 564
564 a ppendix e: o btaining s upport for your p roduct latin america telephone technical support and repair antigua argentina aruba bahamas barbados belize bermuda bonaire brazil cayman chile colombia costa rica curacao ecuador dominican republic 1 800 988 2112 0 810 444 3com 1 800 998 2112 1 800 99...
Page 565: Ndex
I ndex numbers 3comstarterexample 74 3wxm restricting access to 75 software requirements 20 toolbar icons 37 802.1q tagging 190 802.1x access rules 323 802.1x authentication configuring 366 standard 366 802.1x network access rules setting up policy properties 334 a aaa (authentication, authorization...
Page 566
566 i ndex console access 316 console access rules accounting 322 authentication 321 creating 318 managing 323 setting up properties 318 conventions notice icons, about this guide 15 text, about this guide 16 copying objects 67 countermeasures enabling 472 ignoring friendly devices 479 coverage area...
Page 567
I ndex 567 i icmp ace, creating 355 igmp (internet group management protocol) configuring 201 definition 201 image repository adding image 393 deleting image 393 using 393 importing configurations 396 installation hp openview plug-in 28 license key 21 preparing for 21 serial number 21 software requi...
Page 568
568 i ndex network plans closing 85 creating 78 deleting 86 managing 80 opening 84 saving 80 saving a version 82 saving automatically 83 sharing 86 network ports configuring 231 network user access rules 323 network users 323 defined 323 ntp (network time protocol) configuring 247 creating servers 2...
Page 569
I ndex 569 snmp (simple network management protocol) configuring 214 parameters 214 traps 216 software requirements for installation 20 spanning tree protocol. See stp (spanning tree protocol) ssh configuring 213 starting monitoring service 537 static acls 361 static multicast ports, configuring 203...
Page 570
570 i ndex vlans (virtual lans) adding ports to 194 configuring basic properties 191 igmp 201 static multicast ports 203 stp 198 stp fast convergence 205 creating 190 definition 188 deleting 207 mapping acls to 363 modifying 207 naming 189 roaming 189 tagging 190 users 189 vlan globs in location pol...