- DL manuals
- Cabletron Systems
- Switch
- CyberSWITCH CSX400
- User Manual
Cabletron Systems CyberSWITCH CSX400 User Manual
Summary of CyberSWITCH CSX400
Page 1
Cybermonitor user’s guide 9032331-05.
Page 3: Notice
Cybermonitor user’s guide i notice cabletron systems reserves the right to make changes in specifications and other information contained in this document without prior notice. The reader should in all cases consult cabletron systems to determine whether any such changes have been made. The hardware...
Page 4
Notice ii cybermonitor user’s guide fcc notice this device complies with part 15 of the fcc rules. Operation is subject to the following two conditions: (1) this device may not cause harmful interference, and (2) this device must accept any interference received, including interference that may caus...
Page 5
Notice cybermonitor user’s guide iii cabletron systems, inc. Program license agreement important: this license applies for use of product in the united states of america and by united states of america government end users. Before opening or utilizing the enclosed product, carefully read this licens...
Page 6
Notice iv cybermonitor user’s guide component of a plant, export to country groups d:1 or e:2 the direct product of the plant or a major component thereof, if such foreign produced direct product is subject to national security controls as identified on the u.S. Commerce control list or is subject t...
Page 7
Notice cybermonitor user’s guide v cabletron systems sales and service, inc. Program license agreement important: this license applies for use of product in the united states of america and by united states of america government end users. Before opening or utilizing the enclosed product, carefully ...
Page 8
Notice vi cybermonitor user’s guide component of a plant, export to country groups d:1 or e:2 the direct product of the plant or a major component thereof, if such foreign produced direct product is subject to national security controls as identified on the u.S. Commerce control list or is subject t...
Page 9
Notice cybermonitor user’s guide vii cabletron systems limited program license agreement important: this license applies for use of product in the united states of america and by united states of america government end users. Before opening or utilizing the enclosed product, carefully read this lice...
Page 10
Notice viii cybermonitor user’s guide component of a plant, export to country groups d:1 or e:2 the direct product of the plant or a major component thereof, if such foreign produced direct product is subject to national security controls as identified on the u.S. Commerce control list or is subject...
Page 11
Notice cybermonitor user’s guide ix declaration of conformity application of council directive(s): 89/336/eec 73/23/eec manufacturer’s name: cabletron systems, inc. Manufacturer’s address: 35 industrial way po box 5005 rochester, nh 03867 european representative name: mr. J. Solari european represen...
Page 12
Notice x cybermonitor user’s guide.
Page 13: Contents
Cybermonitor user’s guide xi contents chapter 1 introduction related documentation ...................................................................................1-1 how to use this guide ....................................................................................1-1 document conventions...
Page 14
Contents xii cybermonitor user’s guide statistical data tables .....................................................................................3-8 statistic table menu items ........................................................................3-8 statistical table scroll bar....................
Page 15
Contents cybermonitor user’s guide xiii inverse multiplex table data...................................................................3-30 frame relay statistics table ..................................................................3-31 frame relay statistical data ..................................
Page 16
Contents xiv cybermonitor user’s guide.
Page 17: Introduction
Cybermonitor user’s guide 1-1 1 introduction welcome to the cabletron systems cybermonitor user’s guide . This guide provides information on how to use this utility, plus software specifications and troubleshooting tips. This guide also provides background information about ethernet port interfaces,...
Page 18: Document Conventions
Chapter 1: introduction 1-2 cybermonitor user’s guide document conventions the following conventions are used throughout this guide: technical support for additional support related to this device or document, contact cabletron systems using one of the following methods: before you call cabletron sy...
Page 19
Introduction cybermonitor user’s guide 1-3 before calling cabletron systems, have the following information ready: • your cabletron systems service contract number • a description of the problem • a description of any action(s) already taken to resolve the problem. • the serial and revision numbers ...
Page 20
Chapter 1: introduction 1-4 cybermonitor user’s guide.
Page 21: Cybermonitor Overview
Cybermonitor user’s guide 2-1 2 cybermonitor overview this chapter provides an overview of the functionality of the cabletron systems cybermonitor. About the cybermonitor the cabletron systems cybermonitor is a wide area network monitoring system. The cybermonitor polls status conditions, and monito...
Page 22: Port Interface Icons
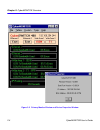
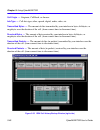
Chapter 2: cybermonitor overview 2-2 cybermonitor user’s guide figure 2-1 primary monitor window port interface icons figure 1 shows the primary monitor window representing a csx400 cyberswitch. The primary monitor window displays two ethernet port icons, and two wide area port icons under the title...
Page 23: Port Interface Stats Panels
Cybermonitor overview cybermonitor user’s guide 2-3 port interface stats panels the ethernet ports are represented by the ethernet 1, and ethernet 2 port panels. The wide area 1, and wide area 2 panels show isdn transmission mode, and drop and insert (di) mode, no protocol set. Inside each panel are...
Page 24
Chapter 2: cybermonitor overview 2-4 cybermonitor user’s guide figure 2-2 primary monitor window and device properties window.
Page 25
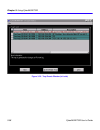
Cybermonitor overview cybermonitor user’s guide 2-5 figure 2-3 statistical data table for wide area 1.
Page 26: Statistical Data Tables
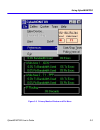
Chapter 2: cybermonitor overview 2-6 cybermonitor user’s guide statistical data tables statistical data tables (see figure 2-3 , on previous page) are expanded data tables for a selected interface, or function within the device you are monitoring. Various status conditions and data throughput are sh...
Page 27
Cybermonitor overview cybermonitor user’s guide 2-7 figure 2-5 chart by protocols drop down menu a statistic chart for wide area network interface port number 1, is shown in figure 2-6 , on the following page. The ip address of the device being monitored is displayed in the upper border of the chart...
Page 28
Chapter 2: cybermonitor overview 2-8 cybermonitor user’s guide figure 2-6 interface statistic chart for wide area 1 there are two menu items at the top of the statistic chart; file, and help. The file menu lets you access either print (which prints the chart), or close, (which closes the window). Th...
Page 29: Alarm Settings
Cybermonitor overview cybermonitor user’s guide 2-9 alarm settings click the custom button in the menu bar of the primary monitor window to access the drop down menu shown in figure 2-7 , below. This menu lets you select either the bandwidth thresholds panel, or the errors threshold panel. (see figu...
Page 30
Chapter 2: cybermonitor overview 2-10 cybermonitor user’s guide figure 2-8 alarm panel for bandwidth parameter.
Page 31
Cybermonitor overview cybermonitor user’s guide 2-11 figure 2-9 alarm panel for errors parameter figure 2-9 , above, shows tx and rx error levels preset to 5% for warning and 10% for critical on the ethernet 1, and ethernet 2 ports, and wide area 1, and wide area 2 ports. Error thresholds have also ...
Page 32: Cybermonitor Help System
Chapter 2: cybermonitor overview 2-12 cybermonitor user’s guide cybermonitor help system the cybermonitor employs an interactive help system with links to related topics. There are four ways to access the help system from within the cybermonitor: • click on the help button on any window to access th...
Page 33: Getting Help
Cybermonitor overview cybermonitor user’s guide 2-13 getting help for additional support related to this device or document, contact cabletron systems using one of the following methods: before calling cabletron systems, have the following information ready: • a description of the failure • a descri...
Page 34
Chapter 2: cybermonitor overview 2-14 cybermonitor user’s guide.
Page 35: Using Cybermonitor
Cybermonitor user’s guide 3-1 3 using cybermonitor prerequisites the following is a list of prerequisites to using the cybermonitor utility: virtual memory enabled (windows 95) you must have virtual memory enabled to run cybermonitor. To check if you have virtual memory enabled for a windows 95 oper...
Page 36: Local User Networks
Chapter 3: using cybermonitor 3-2 cybermonitor user’s guide local user networks if your system is connected to more than one network, you will see the local user networks window shown below in figure 3-1 . Use the scroll button to select the network connection that your cybermonitor-capable device i...
Page 37
Using cybermonitor cybermonitor user’s guide 3-3 figure 3-3 primary monitor window and file menu.
Page 38: Custom Interval
Chapter 3: using cybermonitor 3-4 cybermonitor user’s guide custom interval the custom (polling) interval window shown in figure 3-4 , below displays when you click on polling interval from preferences in the file submenu (see figure 3-3 , on the previous page). The custom interval window is used to...
Page 39: Primary Monitor Window
Using cybermonitor cybermonitor user’s guide 3-5 enter the start and stop times for your monitoring session. Note the am, and pm buttons. The maximum interval that can be set for a monitoring session is twenty-four hours, minus one minute. This interval is for a monitoring session that is automatica...
Page 40
Chapter 3: using cybermonitor 3-6 cybermonitor user’s guide figure 3-6 monitor window for hsim-w6 device inside each panel are the statistics for bandwidth utilization for transmit (tx) and receive (rx), and error statistics for these ports. The panels will always represent the type of network modul...
Page 41: Function Menus
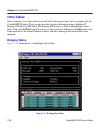
Using cybermonitor cybermonitor user’s guide 3-7 function menus there are four function menu items at the top of the primary monitor window. A brief description of the function of each menu item follows: file menu • file menu item lets you access the four menus shown in figure 3-6 , and described be...
Page 42: Statistical Data Tables
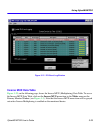
Chapter 3: using cybermonitor 3-8 cybermonitor user’s guide statistical data tables double clicking on any panel in the primary monitor window will produce a statistical data table for that module, or function. Figure 3-7 shows the statistical data table for wide area network module 1- logical inter...
Page 43: Secondary Ip Addresses
Using cybermonitor cybermonitor user’s guide 3-9 secondary ip addresses beneath the primary ip address row in the ethernet statistical data table is the secondary ip address row. If an interface has more than one ip address associated with it, the first secondary ip address will appear in this row o...
Page 44: Statistical Data Charts
Chapter 3: using cybermonitor 3-10 cybermonitor user’s guide statistical data charts clicking charts at the top of the statistical data table will produce a chart (see figure 3-8 below) of the data in one of the charting modes mentioned previously (in this case bandwidth vs. Time). Figure 3-8 statis...
Page 45: Autosizing
Using cybermonitor cybermonitor user’s guide 3-11 autosizing the statistical data chart uses “autosizing”. If a sudden peak exceeds the current scale, the chart will adjust the scale factor to include the peak. All events are always visible on this chart - nothing will ever be off-scale.The scale at...
Page 46
Chapter 3: using cybermonitor 3-12 cybermonitor user’s guide interpreting statistical data tables the following figures and corresponding data will explain the entries within the statistical data tables, and tables of functions such as ipx routing, and inverse multiplexing. Figure 3-9 , ethernet net...
Page 47: Ethernet Statistical Data
Using cybermonitor cybermonitor user’s guide 3-13 ethernet statistical data the following is a row-by-row breakdown of the ethernet network interface statistics: protocol - protocol of the interface being monitored. Admin status - up, down, or testing - the “desired” state of the interface. Operatio...
Page 48: Ethernet Packet Statistics
Chapter 3: using cybermonitor 3-14 cybermonitor user’s guide ethernet packet statistics the packet statistics for an ethernet network interface port are shown below. These statistics appear below the horizontal scroll bar in the ethernet statistical data table. Total packets in - the total packets i...
Page 49
Using cybermonitor cybermonitor user’s guide 3-15 wide area statistical data table figure 3-10 , shown below, and wide area statistical data , explain the interpretation of the statistical data displayed in the wide area statistical data table. Figure 3-10 wide area statistical data table.
Page 50: Wide Area Statistical Data
Chapter 3: using cybermonitor 3-16 cybermonitor user’s guide wide area statistical data the wide area data tables contain all the pertinent information about the wide area network interface port that you are monitoring. The following is a breakdown of these statistics: alias - this is an alias name ...
Page 51: Wide Area Packet Statistics
Using cybermonitor cybermonitor user’s guide 3-17 proxy arp - when proxy arp is enabled, and an arp request is received, ip routing services sends a proxy arp response, with the physical address of the receiving router port in place of the requested host's physical address. Horizontal scroll bar - t...
Page 52: Other Tables
Chapter 3: using cybermonitor 3-18 cybermonitor user’s guide other tables there is another class of data tables discussed in the following sections, that are displayed by the cybermonitor utility. These are the data tables for the following functions; bridging, ip routing, ip event log, rip table, i...
Page 53: Bridging Statistical Data
Using cybermonitor cybermonitor user’s guide 3-19 bridging statistical data the bridging data table shows the state of the bridging interface. The text in the outer border indicates the status of spanning tree (stp). The time frame shows the state of the following spanning tree parameters: hello tim...
Page 54: Bridging Per Interface Data
Chapter 3: using cybermonitor 3-20 cybermonitor user’s guide bridging per interface table figure 3-12 , below, shows the bridging per interface table. To access the bridging per interface table, click on the bridging panel on the primary monitor window (see figure 3-3 ). Figure 3-12 bridging per int...
Page 55: Ip Per Interface
Using cybermonitor cybermonitor user’s guide 3-21 ip per interface figure 3-13 , below shows the ip per interface table. To access the ip per interface table, click on the ip routing panel on the monitor window for hsim-w6 (see figure 3-6 ). Figure 3-13 ip per interface table ip per interface data t...
Page 56: Ip Routing Tables
Chapter 3: using cybermonitor 3-22 cybermonitor user’s guide ip routing tables figure 3-14 , below, shows the ip routing statistics table. To access the ip routing statistics table, click on the table menu item on the ip per interface table menu bar (see figure 3-13 ). Figure 3-14 ip routing statist...
Page 57: Ip Routing Statistics
Using cybermonitor cybermonitor user’s guide 3-23 ip routing statistics the ip routing statistics table ( figure 3-14 , previous page) shows the following statistics: destination - ip address of the route destination. Interface - logical interface number of the route. Alias - an alias name that you ...
Page 58
Chapter 3: using cybermonitor 3-24 cybermonitor user’s guide when ip events are sorted by event type, similar events will be grouped together. When ip events are sorted by severity, there are three levels: low, medium, and high, with high having the highest priority. Sorting by interface numbers wil...
Page 59: Rip Table
Using cybermonitor cybermonitor user’s guide 3-25 rip table the rip (routing information protocol) table, shown in figure 3-17 , below, displays the ip address, and send and receive rip protocols in use for the interface being monitored. To access the rip table, click on the tables menu on the prima...
Page 60: Ipx Routing Table
Chapter 3: using cybermonitor 3-26 cybermonitor user’s guide ipx routing table the ipx rip/sap routing table is a rip table (routing information protocol) and a sap table (service advertising protocol) combined in one window. Figure 3-18 , below, shows the ipx rip/sap routing table. To access the ip...
Page 61: Ipx Per Interface Table
Using cybermonitor cybermonitor user’s guide 3-27 the find server button will access the rip table information for a server that you select in the sap table. Show all, in the ipx service types drop down list will display all of the servers in the sap table with options allowing you to display only f...
Page 62: Ipx Event Log
Chapter 3: using cybermonitor 3-28 cybermonitor user’s guide ipx event log the ipx event log window ( figure 3-21 on the following page) is a record of ipx routing events, or device status changes. The events are listed in tabular form, and can be sorted by interface number, event type, or severity....
Page 63: Inverse Mux Data Table
Using cybermonitor cybermonitor user’s guide 3-29 figure 3-21 ipx event log window inverse mux data table figure 3-22 , on the following page, shows the inverse mux (multiplexing) data table. To access the inverse mux data table, click on the inverse mux menu item in the tables menu on the primary m...
Page 64
Chapter 3: using cybermonitor 3-30 cybermonitor user’s guide figure 3-22 inverse mux data table inverse multiplex table data the inverse multiplex table shows the interfaces selected to perform the inverse multiplex function. Inverse multiplexing combines two channels to share the bandwidth utilizat...
Page 65: Frame Relay Statistical Data
Using cybermonitor cybermonitor user’s guide 3-31 frame relay statistics table figure 3-23 , below, shows the frame relay statistics table. The frame relay statistics table shows frame relay statistics sorted by dlcis (data link connection identifiers). Dlcis are the indentifying numbers for switche...
Page 66: Traps
Chapter 3: using cybermonitor 3-32 cybermonitor user’s guide committed burst - the maximum amount of data on the network during a time interval, without the network discarding any data. Excess burst - the maximum amount of data allowed to exceed the committed burst (there is no guarantee that this d...
Page 67
Using cybermonitor cybermonitor user’s guide 3-33 figure 3-25 trap destination configuration window figure 3-26 add trap and modify trap windows.
Page 68
Chapter 3: using cybermonitor 3-34 cybermonitor user’s guide the modify button (see figure 3-25 ) lets you modify the ip address or state (enabled, or disabled) of the item highlighted in the trap destination configuration window. The modify button displays the modify trap destination window shown i...
Page 69
Using cybermonitor cybermonitor user’s guide 3-35 figure 3-28 add agent window.
Page 70
Chapter 3: using cybermonitor 3-36 cybermonitor user’s guide figure 3-29 trap events window (left side).
Page 71
Using cybermonitor cybermonitor user’s guide 3-37 figure 3-30 trap events window (right side) the trap events window shown in figure 3-29 on the previous page, and figure 3-30 above, displays when you click ok on the trap agent window. Traps received are displayed in chronological sequence (most rec...
Page 72: Isdn Call History/backup
Chapter 3: using cybermonitor 3-38 cybermonitor user’s guide isdn call history/backup the isdn call history/backup window ( figure 3-32 on the following page) is a record of isdn calls and corresponding device status. To access the isdn call history/backup window, click the isdn/backup menu item, in...
Page 73
Using cybermonitor cybermonitor user’s guide 3-39 connect time hh.Mm.Ss — the time that the connection was established, stated as; hour, minute, and second. Disconnect time hh.Mm.Ss — the time that the connection was taken down, or disconnected stated as; hour, minute, and second. Figure 3-32 isdn c...
Page 74
Chapter 3: using cybermonitor 3-40 cybermonitor user’s guide call origin — originate, call back, or answer. Info type — call data type; other, speech, digital, audio, video, etc. Transmitted bytes — the amount of data transmitted by your interface in bytes, kilobytes, or megabytes over the duration ...
Page 75: Isdn/backup Panel
Using cybermonitor cybermonitor user’s guide 3-41 isdn/backup panel the isdn/backup panel (see figure 3-33 on the previous page) is a list of isdn interface numbers, and aliases and whether they are used as backup isdn interfaces. Isdn can be used as a backup medium for any wan wpim interface. Isdn ...
Page 76
Chapter 3: using cybermonitor 3-42 cybermonitor user’s guide.
Page 77: Troubleshooting
Cybermonitor user’s guide 4-1 4 troubleshooting snmp errors the following messages are representative of a large class of snmp errors. • “unsupported windows version” • “unexpected error =. . . . . . ” • “snmp error . . . . . . . ” snmp errors are critical, and may cause program termination or at le...
Page 78
Chapter 4: troubleshooting 4-2 cybermonitor user’s guide if tcp/ip routing, • check that tcp/ip routing is set on and is enabled at the remote end. • check that the ip address of the lan beyond the remote router is correct, as well as the associated subnet mask. • if the remote router wan ip address...
Page 79: Glossary
Cybermonitor user’s guide a-1 a glossary 10base-t — ieee 802.3 standard for the use of ethernet lan technology over unshielded twisted pair wiring, running at 10 mbps. Ais — ds-1 line status error condition - the alarm indication signal failure is declared when an ais defect is detected at the input...
Page 80
Appendix a: glossary a-2 cybermonitor user’s guide chap — challenge handshake authentication protocol. A security protocol supported under point-to-point protocol (ppp) used to prevent unauthorized access to devices and remote networks. Uses encryption of password, device names and random number gen...
Page 81
Glossary cybermonitor user’s guide a-3 firewall — a combination of techniques used to protect one network from unknown networks and users on the outside. Firewalls can filter or block traffic and act as a management and network security point where all traffic can be scrutinized. Dte — data terminal...
Page 82
Appendix a: glossary a-4 cybermonitor user’s guide leased line — a telecommunications line between two service points leased from a communications carrier for private use, usually incurring a monthly service rate. Leds (light emitting diodes) — type of indicator lights on the panel of a device. Less...
Page 83
Glossary cybermonitor user’s guide a-5 multi-vendor interoperability. The osi reference model defines seven layers, each providing specific network functions. Packet — a group of data that includes a header and usually user data for transmission through a network. Pcvs — path coding violations - a d...
Page 84
Appendix a: glossary a-6 cybermonitor user’s guide serialization frames — frames sent out by servers under ipx to check whether illegal copies of netware are in use on the network. Service advertising protocol — protocol used in ipx for broadcasting information about services available on the networ...
Page 85
Glossary cybermonitor user’s guide a-7 telnet — internet standard protocol for remote terminal emulation that allows a user to remotely log in to another device and appear as if directly connected. Tftp — trivial file transfer protocol. A simplified version of the file transfer protocol (ftp) allowi...
Page 86
Appendix a: glossary a-8 cybermonitor user’s guide.