ABB Relion 670 series Manual
Summary of Relion 670 series
Page 1
Relion® 670 series — 670 series version 2.2 cyber security deployment guideline.
Page 3
Document id: 1mrk 511 399-uen issued: october 2017 revision: b product version: 2.2.1 © copyright 2017 abb. All rights reserved.
Page 4
Copyright this document and parts thereof must not be reproduced or copied without written permission from abb, and the contents thereof must not be imparted to a third party, nor used for any unauthorized purpose. The software and hardware described in this document is furnished under a license and...
Page 5
Disclaimer the products are designed to be connected to and to communicate information and data via a network interface. It is the user’s sole responsibility to provide and continuously ensure a secure connection between the product and the user’s network or any other network (as the case may be). T...
Page 6
Conformity this product complies with the directive of the council of the european communities on the approximation of the laws of the member states relating to electromagnetic compatibility (emc directive 2004/108/ec) and concerning electrical equipment for use within specified voltage limits (low-...
Page 7
Table of contents section 1 introduction.......................................................................5 this manual........................................................................................ 5 intended audience.......................................................................
Page 8
Section 5 central account management........................................41 introduction.......................................................................................41 certificate management................................................................... 42 creating ied certificates....
Page 9
Applicable standards........................................................................ 95 ieee1686 compliance...................................................................... 96 section 9 glossary....................................................................... 101 table of contents...
Page 10
4.
Page 11
Section 1 introduction 1.1 this manual guid-ab423a30-13c2-46af-b7fe-a73bb425eb5f v18 the cyber security deployment guideline describes the process for handling cyber security when communicating with the ied. Certification, authorization with role based access control, and product engineering for cyb...
Page 12
1.3 product documentation 1.3.1 product documentation set guid-3aa69ea6-f1d8-47c6-a8e6-562f29c67172 v15 iec07000220-4-en.Vsd p la nn in g & p ur ch as e e ng in ee rin g in st al lin g c om m is si on in g o pe ra tio n m ai nt en an ce d ec om m is si on in g d ei ns ta lli ng & d is po sa l applic...
Page 13
Describes the process of testing an ied in a substation which is not in service. The chapters are organized in the chronological order in which the ied should be commissioned. The relevant procedures may be followed also during the service and maintenance activities. The operation manual contains in...
Page 14
Documents related to rec670 document numbers application manual 1mrk 511 401-uen commissioning manual 1mrk 511 403-uen product guide 1mrk 511 404-ben technical manual 1mrk 511 402-uen type test certificate 1mrk 511 404-ten documents related to red670 document numbers application manual 1mrk 505 376-...
Page 15
Documents related to res670 document numbers application manual 1mrk 511 407-uen commissioning manual 1mrk 511 409-uen product guide 1mrk 511 410-ben technical manual 1mrk 511 408-uen type test certificate 1mrk 511 410-ten documents related to rer670 document numbers application manual 1mrk 506 375-...
Page 16
The warning icon indicates the presence of a hazard which could result in personal injury. The caution hot surface icon indicates important information or warning about the temperature of product surfaces. The caution icon indicates important information or warning related to the concept discussed i...
Page 17
• the character ^ in front of an input/output signal name indicates that the signal name may be customized using the pcm600 software. • the character * after an input signal name indicates that the signal must be connected to another function block in the application configuration to achieve a valid...
Page 18
12.
Page 19
Section 2 security in substation automation 2.1 general security in substation automation guid-d156d1ea-15ef-4700-b6e2-8a316a7c3288 v2 the electric power grid has evolved significantly over the past decade thanks to many technological advancements and breakthroughs. As a result, the emerging “smart ...
Page 20
It easier for our customers to address nerc cip requirements and maintain compliance standards. Remote control center (security zone 3) maintenance center (security zone 4) iec 61850-8-1 station bus microscada pro sys600c firewall / router / vpn firewall / router / vpn encrypted communication encryp...
Page 21
Section 3 secure system setup 3.1 physical interfaces guid-da029f79-3173-4d17-a7b9-aa213fac8f68 v1 to reduce exposure for cyber-attacks and thus comply with cyber security requirements, it must be possible to prevent services in the ied from operating on other physical interfaces than the ones speci...
Page 22
Port protocol default state front 301 302 303 304 3061 3062 service comment 2102 tcp open on on on on on off off pcm access (ied configuration protocol) ied configuration protocol 20 000 tcp closed off off off off off off off dnp3.0 dnp3.0 dnp communication only 20 000 udp closed off off off off off...
Page 23
Defined in the configuration which type of ethernet communication is used. Only one type is possible at a time. • the tcp/ udp port used for ieee1344/c37.118 protocol can be changed in the ied. • the port used for ftp (default tcp port 21) can be changed in the ied if needed by a 3rd party ftp clien...
Page 24
Iec13000268-2-en.Vsd iec13000268 v2 en-us figure 4: optical ethernet ports, position x311, rear view 3.3 ftp access with tls, ftpaccs guid-9e64ea68-6fa9-4576-b5e9-92e3cc6aa7fd v3 the ftp client defaults to the best possible security mode when trying to negotiate with tls. The automatic negotiation m...
Page 25
No passwords are stored in clear text within the ied. A hashed representation of the passwords with sha 256 is stored in the ied. These are not accessible from outside via any ports. A user with secadm or rbacmnt role is allowed to read out the hashed password on a secured (tls) odbc link. 3.5 denia...
Page 26
The certificate is always trusted during communication between the ied and pcm600. If windows is configured to use uac high the certificate have to be manually trusted in a dialog box. This certificate handling changes with central account management and the possibility to use other certificates but...
Page 27
Section 4 local user account management 4.1 authorization guid-981a881d-9229-45e8-9ee5-d6df2ca457e5 v4 user roles with different user rights are predefined in the ied. It is recommended to use user defined users instead of the predefined built-in users. The ied users can be created, deleted and edit...
Page 28
User roles role explanation user rights secaud security auditor can view audit logs rbacmnt rbac management can change role assignment administrator administrator rights sum of all rights for secadm, secaud and rbacmnt this user role is vendor specific and not defined in iec 62351–8 changes in user ...
Page 29
At delivery, the ied has a default user defined with full access rights. Pcm600 uses this default user to access the ied. This user is automatically removed in ied when users are defined via the ied users tool in pcm600. Default user id: administrator password: administrator for user management, see...
Page 30
Access rights viewer operator engineer installer secadm secaud rbacmnt administrator control – basic - x x - - - - - control – advanced - x x - - - - - iedcmd – basic - x x - - - - - iedcmd – advanced - - x - - - - - filetransfer – limited - x x x x x x x db access normal - x x x x x x x audit log r...
Page 31
First user created must be appointed the role secadm to be able to write users, created in pcm600, to the ied. In order to allow the ied to communicate with pcm600 when users are defined via the ied users tool, the access rights “useradministration” and “filetransfer — limited” must be applied to at...
Page 32
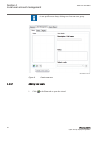
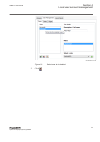
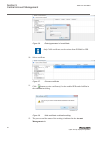
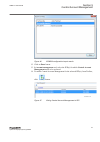
Iec13000027 v2 en-us figure 6: change password policies dialog box in ied users tool in pcm600 4.4 ied user management guid-b3a1a9f3-7f76-413c-a9a1-e090b90a8b3a v3 the ied users tool in pcm600 is used for editing user profiles and role assignments. In the ied users tool, the data can be retrieved fr...
Page 33
The ied user dialog box appears. 4.4.2 general settings guid-0326f993-e3f2-4f72-a94f-d8886eb9f6ad v4 in the general tab, by clicking restore factory settings the default users can be restored in the ied users tool. For the ied series this means reverting back to the factory delivered users. Performi...
Page 34
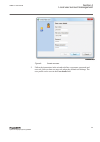
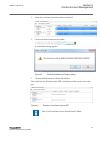
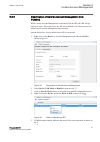
A user profile must always belong to at least one user group. Iec12000199-2-en.Vsd iec12000199 v2 en-us figure 8: create new user 4.4.3.1 adding new users guid-85d09a73-7e14-4bd6-96e5-0959bf4326c0 v3 1. Click in the users tab to open the wizard. Section 4 1mrk 511 399-uen b local user account manage...
Page 35
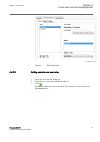
Iec12000200 v2 en-us figure 9: create new user 2. Follow the instructions in the wizard to define a user name, password and user role. Select at least one user role where the defined user belongs. The user profile can be seen in the user details field. 1mrk 511 399-uen b section 4 local user account...
Page 36
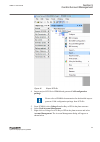
Iec12000201-3-en.Vsd iec12000201 v3 en-us figure 10: select user role 3. Select the user from the user list and type a new name or description in the description/full name field to change the name or description of the user. Section 4 1mrk 511 399-uen b local user account management 30 670 series 2....
Page 37
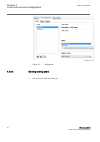
Iec12000202-2-en.Vsd iec12000202 v2 en-us figure 11: enter description 4.4.3.2 adding users to new user roles guid-f335590a-eac7-42e2-ac6b-c0051fd21d05 v2 1. Select the user from the users list. 2. Select the new role from the select a role list. 3. Click . Information about the roles to which the u...
Page 38
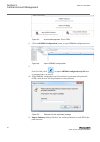
Iec12000203-2-en.Vsd iec12000203 v2 en-us figure 12: adding user 4.4.3.3 deleting existing users guid-472bf39b-ddac-4d88-9b74-e6c49d054524 v2 1. Select the user from the users list. Section 4 1mrk 511 399-uen b local user account management 32 670 series 2.2 iec cyber security deployment guideline.
Page 39
Iec12000204-2-en.Vsd iec12000204 v2 en-us figure 13: select user to be deleted 2. Click . 1mrk 511 399-uen b section 4 local user account management 670 series 2.2 iec 33 cyber security deployment guideline.
Page 40
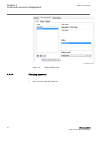
Iec12000205-2-en.Vsd iec12000205 v2 en-us figure 14: delete existing user 4.4.3.4 changing password guid-6180d722-cc49-445b-b520-bad8904a60af v2 1. Select the user from the users list. Section 4 1mrk 511 399-uen b local user account management 34 670 series 2.2 iec cyber security deployment guidelin...
Page 41
Iec12000206-2-en.Vsd iec12000206 v2 en-us figure 15: select user 2. Click . 3. Type the old password once and the new password twice in the required fields. The passwords can be saved in the project database or sent directly to the ied. No passwords are stored in clear text within the ied. A hash re...
Page 42
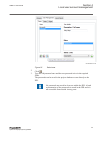
Iec12000207 v2 en-us figure 16: change password 4.4.4 user role management guid-213fbf87-3268-42e6-88b0-8ee260127b08 v2 in the roles tab, the user roles can be modified. The user's memberships to specific roles can be modified with a list of available user roles and users. Section 4 1mrk 511 399-uen...
Page 43
Iec12000208-2-en.Vsd iec12000208 v2 en-us figure 17: editing users 4.4.4.1 adding new users to user roles guid-c53b644a-6c5c-43fc-96d7-e2ca152bd84a v1 1. Select the required role from the roles list. The role profile can be seen under the role details field. 2. Select the new user from the select a ...
Page 44
Iec12000210-2-en.Vsd iec12000210 v2 en-us figure 18: remove role from user 4.4.4.3 reusing user accounts guid-c28c87ec-7027-440c-bb38-2c8ec14eca40 v2 ied user account data can be exported from one ied and imported to another. The data is stored in an encrypted file. Exported passwords are hashed and...
Page 45
Iec12000209-2-en.Vsd iec12000209 v2 en-us figure 19: importing and exporting user account data 4.4.5 writing user management settings to the ied guid-2066776c-72cc-49cc-b8d8-f2c320541a5e v2 • click the write user management settings to ied button on the toolbar. Iec12000211 v2 en-us figure 20: write...
Page 46
4.4.7 saving user management settings guid-ae198606-6e71-4c77-a4e1-02b79e4270b4 v2 • select file/save from the menu. • click the save toolbar button. The save function is enabled only if the data has changed. Section 4 1mrk 511 399-uen b local user account management 40 670 series 2.2 iec cyber secu...
Page 47
Section 5 central account management 5.1 introduction guid-63e85a54-d3a2-46f4-8315-eec364251065 v1 central account management is an authentication infrastructure that offers a secure solution for enforcing access control to ieds and other systems within a substation. This incorporates management of ...
Page 48
5.2 certificate management guid-fff5c8f8-8227-435e-8e5b-70d37d8e86dc v1 security administrator normal user manually transferred certificate files start secure communication replicate users login change own password start secure communication deploy certificate to ied write role to right mapping acti...
Page 49
Iec15000280 v1 en-us figure 22: export scd file generate the scd file from pcm600 2. In sdm600, import scd via the load structure tool. Refer to setting up the sdm600 structure in the sdm600 user manual. 3. Update "alternative ip addresses" with all configured interfaces on the device. 4. Generate c...
Page 50
Sdm600 allows user to set key length of the certificates that needs to be deployed in ied. While it may be prudent to use a larger key size, it would also mean it requires a considerable longer time for the tls handshake (between ied and tools/ central account management servers) before any secure c...
Page 51
Iec15000346 v1 en-us figure 24: import and write certificates tool view in pcm600 7. Select for those ieds to which certificates needs to be written 8. Click on import certificate button. Iec15000348 v1 en-us figure 25: importing certificate (p12) file 9. If certificate is password protected the use...
Page 52
Iec15000349 v1 en-us figure 26: entering password of a certificate only cam certificates can be written from pcm600 to ied. 10. Select certificate iec15000350 v1 en-us figure 27: choosen certificate 11. Click button to write certificate(s) for the enabled ieds and click yes in the confirmation dialo...
Page 53
Iec15000353 v1 en-us figure 29: result of written certificates when central account management is enabled in ied, and if user deploys an invalid certificate in to an ied (e.G.: sdm600 certificate of another sdm server, than the one that is configured in the ied), then replication will fail at the ti...
Page 54
Iec15000281 v1 en-us figure 30: account management tool in pcm 6. Select the read and delete certificates option. Iec15000334 v1 en-us figure 31: read and delete certificates view in pcm600 7. Select for those ieds from which certificates needs to be read. 8. Click button to read certificates from t...
Page 55
Iec15000339 v1 en-us figure 33: certificates that are read from the ied 10. Double click on a certificate unit to view the details of it or 11. Right click on a certificate unit and select properties iec15000340 v1 en-us iec15000341 v1 en-us figure 34: viewing details of certificate of an ied in pcm...
Page 56
Iec15000324 v1 en-us figure 35: certificates view in the certificates view certificate information is grouped according to usage. Selecting cam and pressing will show information about the certificates used for central account management. Iec15000325 v1 en-us figure 36: certificate information for c...
Page 57
Iec15000326 v1 en-us figure 37: cam certificates by pressing on a menu item without information in the right field more information will be shown. For instance, by pressing in the issued to menu item shown in figure 38 below, more information will be shown as in figure 39 below. Iec15000327 v1 en-us...
Page 58
Iec15000328 v1 en-us figure 39: certificate issued to 5.2.5 invalid certificates guid-66dfac1d-f305-416f-91d9-05d035f1810b v1 the certificate can be invalid for different reasons, e.G. If the certificate has expired. In this case, if the ied is using a self-signed certificate, it will generate a new...
Page 59
1. Select the certificate units that needs to be deleted. Iec15000342 v1 en-us 2. Click on the delete-button in the toolbar. Iec15000343-1-en.Vsdx a confirmation dialog appears iec15000402 v1 en-us figure 40: certificate deletion confirmation dialog 3. Click on the yes button to confirm the deletion...
Page 60
It will not be possible to delete internal and external certificates from pcm600 when ied is in central account management mode, it is not recommended to remove central account management certificates from the ied, because this action could cause connectivity problems between central account managem...
Page 61
Iec15000280 v1 en-us figure 42: export scd file 4. Import project scd file in sdm600 and generate cam configuration package . Please refer to sdm600 documentation for the detailed steps to generate cam configuration package from scd file. 5. From pcm600, select voltage level or bay or ied in the pla...
Page 62
Iec15000281 v1 en-us figure 43: account management tool in pcm 8. Click on sdm600 configuration button, to open sdm600 configuration tool. Iec15000282 v1 en-us figure 44: import sdm600 configuration 9. From tool bar, click to import sdm600 configuration zip file that is generated above at step #4. 1...
Page 63
Iec15000284 v1 en-us figure 46: sdm600 configuration import results 12. Click on done button. 13. In account managemen t tool, select the ied(s) for which central account management needs to be activated. 14. To enable central account management for the selected ied(s), from toolbar, click button. I...
Page 64
Iec15000287 v1 en-us figure 48: central account management write status when central account management is set to active, the ied will do the following: • verify the configuration to secure that sdm600 can be accessed. • replicate the defined user group from sdm600 to the ied. At least one user must...
Page 65
If the central account management activation fails, the activate parameter will be reset and central account management must be activated again and a failure message will be indicated in pcm output window. When central account management is activated, any ongoing sessions with the ied will continue ...
Page 66
Local configuration tab indicates the configuration that currently exists in pcm600. Remote configuration tab indicates the configuration that currently exists in the ied. Iec15000290 v1 en-us figure 51: remote configuration remote configuration tab will have the configuration only if read central a...
Page 67
5.3.3 deactivation of central account management from pcm600 guid-19bdc85e-4175-4b53-909f-0051e5d98492 v1 when central account management is switched off in the ied, the ied will go back to be open. There will not be any ied users defined even if that was the case when central account management was...
Page 68
Iec15000294-1-en.Vsdx iec15000294 v1 en-us figure 55: pcm600 output window indicating deactivation of central account management in the ied 5.3.4 deactivation of central account management on local hmi guid-a3829b79-fb89-4575-9d5c-c28ebcdd24cd v1 in case of wrong configuration of cam and certificate...
Page 69
Iec12000170-4-en.Vsdx iec12000170 v4 en-us figure 58: selection menu 6. Select ok to delete certificates and disable cam please confirm delete certificates, disable cam? (persistent) cancel iec15000364-1-en.Vsd iec15000364 v1 en-us figure 59: confirmation 7. Press to continue the startup sequence (n...
Page 70
Table 7: default users user name user rights superuser full rights, only presented in lhmi. Lhmi is logged on by default until other users are defined guest only read rights, only presented in lhmi. Lhmi is logged on by default when other users are defined (same as viewer) administrator full rights....
Page 71
• a substation can be equipped with two redundant authentication servers operating in a hot standby mode. • if configured by the security administrator, the ied itself maintains a local replica in the database with selected users. This database is periodically updated with data from the server and u...
Page 72
5.5 predefined user roles guid-da25a28a-1e94-4b1d-a0fc-ea151070fa48 v1 there are different roles of users that can access or operate different areas of the ied and tool functions. The meaning of the legends used in the table: • x= full access rights • r= only reading rights • - = no access rights ta...
Page 73
Access rights explanation useradministration useradministration is used to handle user management e.G. Adding new user setting – basic setting – basic is used for basic settings e.G. Control settings and limit supervision setting – advanced setting – advanced is used for the relay engineer to set se...
Page 74
5.6 password policy settings for central account management enabled ied guid-abb0d1df-ff41-4411-95ec-7d4b93ff4e0b v1 the password policy is set in the central account management server (sdm600). Refer to sdm600 user manual. 5.7 pcm600 access to central account management enabled ied guid-d7c470f9-46...
Page 75
5.7.1 changing password guid-c36a2e99-0ba8-42ba-a73e-77cc28dcde65 v1 the user can also change the own password from pcm600 or lhmi. The following process is used: • a change password dialog is presented for the user in pcm600 or lhmi • the ied will forward this to the central account management serv...
Page 76
Iec15000295-1-en.Vsdx iec15000295 v1 en-us figure 60: change own password 4. User can enter details and click on ok button. Password will be changed and the result of the operation will be indicated in the pcm600 output window. 5.7.2 error messages guid-a90a0e1e-0581-4be4-a34a-879bd1782793 v1 when a...
Page 77
Table 12: error indications from failed login description event number user feedback login successful. An additional password expiry time can be sent by the cam server. This information contains the number of seconds for which the password is still valid at the time the authentication was executed.*...
Page 78
Description event number user feedback cam server failed to write password to the provider. Password is not changed. 2220 error in the central account server! Connection to cam server could not be established or connection has been terminated unexpectedly. Verify status and connectivity of the cam s...
Page 79
Iec15000369 v1 en-us figure 61: cam default status 2. When ied is not configured with central account management the default status of the camstatus diagnostics will be: 1mrk 511 399-uen b section 5 central account management 670 series 2.2 iec 73 cyber security deployment guideline.
Page 80
Iec15000354 v1 en-us figure 62: cam diagnostics default staus 3. When the ied is central account management configured with one server, the status of camstatus will be: section 5 1mrk 511 399-uen b central account management 74 670 series 2.2 iec cyber security deployment guideline.
Page 81
Iec15000355 v1 en-us figure 63: ied cam configured status table 14: label rational values remarks uammode user account management mode builtin when ied is configured with pcm users local when ied is configured with default users central when central account management is active camserverxstatus indi...
Page 82
Label rational values remarks failed when last replication cycle has failed last update indicates the last update of the status information above. Never when replication was not configured timestamp time when successful replication took place. 4. Errors during activation or redeployment of certifica...
Page 83
Table 16: symptoms probable causes solution diagnostics on local hmi: central account manager server status will be indicated as offline. Security event: 3810 cam server communication failed. Server(s) not reachable check if ldap server is up and running check ied connection authentication will cont...
Page 84
Table 17: symptoms probable causes solution diagnostics: replication failed. Replicalastupdate shows the time when last successful replication. Security event: 3810 cam server communication failed server(s) not reachable server configuration has changed check if ldap server is up and running verify ...
Page 85
Section 6 user activity logging 6.1 activity logging protocol guid-9d7788e2-f94d-40e5-be3e-3c47c39d34fc v1 activity logging can be reported from the ied through two different protocols; either iec 61850 or syslog. Syslog is a standard for computer message logging (rfc 5424). For iec61850, configurat...
Page 86
Name values (range) unit step default description extlogsrv2ip 0 - 18 ip address 1 127.0.0.1 external log server 2 ip-address extlogsrv3type off syslog udp/ip syslog tcp/ip cef tcp/ip - - off external log server 3 type extlogsrv3port 1 - 65535 - 1 514 external log server 3 port number extlogsrv3ip 0...
Page 87
It is possible to map respective protocol to the signals of interest and configure them for monitoring with the communication management tool (cmt) in pcm600. No events are mapped by default. Parameter names: • eventid: event id of the generated security event • seqnumber: sequence number of the gen...
Page 88
6.7 event types guid-f56b592a-fa2e-4812-bed2-337115aaaf60 v2 the following table contains the event types that can be logged, including their 61850 mapping on the logical node gsal table 21: event type codes event number acronyms gsal mapping english 1110 login_ok gsal.Ina login successful 1115 logi...
Page 89
Event number acronyms gsal mapping english 3710 cam_srv_comm_ok gsal.Ina cam server communication successful 3810 cam_srv_comm_fail gsal.Ina cam server communication failed 3820 cam_replication_no_users gsal.Ina replication performed. No users replicated! 3830 cam_replication_no_capacity gsal.Ina re...
Page 90
Event number acronyms gsal mapping english 10042 maint_update_abort_fail gsal.Ina failed to abort firmware update procedure 10050 maint_recovery_enter_ok gsal.Ina recovery menu entered successfully 10052 maint_recovery_enter_fail gsal.Ina failed to enter recovery menu 10060 maint_auth_dis_ok gsal.In...
Page 91
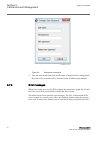
Section 7 local hmi use guid-9d51f5a5-b05a-4bec-9e71-8bd0beb87764 v3 at delivery, login is not required and the user has full access until users and passwords are created with pcm600 and written into the ied. The lhmi is logged on as superuser by default until other users are defined. Commands, chan...
Page 92
Iec12000161-3-en.Vsd iec12000161 v3 en-us figure 66: selecting the user name 4. Select ok on the on-screen keyboard and press to stop editing the user name. 5. Press to select the password field and press to activate it. An on-screen keyboard is shown. Each added character is shown for a short time,...
Page 93
Only characters a - z, a - z and 0 - 9 shall be used in user names. User names are not case sensitive. For passwords see the password policies in pcm600. 7. Select ok on the on-screen keyboard and press to stop editing the password. 8. Select ok in the log on dialog and press to confirm the login, o...
Page 94
7.2 logging off guid-0fddb51b-d1c2-4442-aae5-865bc39ae253 v1 the user is automatically logged off after the display timeout. The ied returns to a state where only reading is enabled. Manual logoff is also possible. 1. Press . 2. To confirm logoff, select yes and press . Iec12000159-3-en.Vsd iec12000...
Page 95
7.4 maintenance menu guid-6e41f1ac-a4ab-40a0-b48d-2f4c91d838af v1 it is possible to disable the maintenance menu. This is done by setting the parameter maintmenuenable to no in the group authman: 1 using the parameter settings in pcm600. If the maintenance menu is disabled, there is no way to bypass...
Page 96
Iec12000168-4-en.Vsdx iec12000168 v4 en-us figure 73: select recovery menu 2. Enter pin code 8282 and press . Iec13000036-4-en.Vsdx iec13000036 v4 en-us figure 74: enter pin code 3. Select turn off authority and press or . Iec12000170-4-en.Vsdx iec12000170 v4 en-us figure 75: turn off authority 4. S...
Page 97
Open pcm600 and start the ied users tool. • remove the faulty user • create a new user with the same access rights • write the user management settings to the ied the ied perform a reboot, new settings are activated and the authority system is enabled again. The maintenance menu is only available on...
Page 98
When the ied is reverted to ied defaults through maintenance menu, the certificates will be deleted. 7.4.3 restore points guid-ad24f69b-beee-4370-8e8c-f245b947f1dd v1 restore points can be used to restore the ied to a previous configuration. A total of three restore points can be active, one of thes...
Page 99
Iec17000034-1-en.Vsdx iec17000034 v1 en-us figure 80: list of restore points 4. To create a restore point, navigate to “user restore point” and press . 5. To confirm, select ok and press . Iec17000035-1-en.Vsdx iec17000035 v1 en-us figure 81: confirm selection this will start a save of the current s...
Page 100
Iec17000038-1-en.Vsdx iec17000038 v1 en-us figure 84: list of restore points here the system can be reverted to the system state of the restore point. In this menu, currently active restore point can be deleted or replaced. Iec17000039-1-en.Vsdx iec17000039 v1 en-us figure 85: confirm selection if a...
Page 101
Section 8 standard compliance statement guid-716dc304-b1c7-417e-ba01-df9c5ad6660a v2 8.1 applicable standards guid-ee0d9238-4dcf-4d2d-96fe-d2879c4cc6c3 v2 cyber security issues have been the subject of standardization initiatives by isa, ieee, or iec for some time and abb plays an active role in all...
Page 102
8.2 ieee1686 compliance guid-009dc366-9abb-430b-a71c-aa4e5fd1b631 v2 table 23: ieee1686 compliance clause title status comment 5 ied cyber security features acknowledge 5.1 electronic access control acknowledge 5.1.1 ied access control overview comply access is protected for local access through con...
Page 103
Clause title status comment 5.1.6 f) id/password or rbac management comply feature is accessible through individual user accounts. 5.1.6 g) audit log comply feature is accessible through individual user accounts. 5.1.7 password display comply 5.1.8 access time-out comply a time-out feature exists. T...
Page 104
Clause title status comment 5.3.3 c) attempted use of unauthorized configuration software exception client certificates are not in use 5.3.3 d) invalid configuration or firmware download comply 5.3.3 e) unauthorized configuration or firmware file exception not supported 5.3.3 f) time signal out of t...
Page 105
Clause title status comment 5.5 ied configuration software acknowledge 5.5.1 authentication exception ied can be configured using unauthorized copies of the configuration software. However configuration download is handled by authentication. 5.5.2 digital signature exception feature not supported 5....
Page 106
100
Page 107
Section 9 glossary guid-2282ae1e-7e51-4f9f-8066-70614fb38695 v4 aes advanced encryption standard (aes) is a specification for the encryption of electronic data. The key size used for an aes cipher specifies the number of repetitions of transformation rounds that convert the input, called the plainte...
Page 108
En 50263 electromagnetic compatibility (emc) - product standard for measuring relays and protection equipment. En 60255-26 electromagnetic compatibility (emc) - product standard for measuring relays and protection equipment. En 60255-27 electromagnetic compatibility (emc) - product standard for meas...
Page 109
Ieee 1686 standard for substation intelligent electronic devices (ieds') cyber security capabilities ieee c37.118-2005 ieee standard for synchrophasors for power systems. The standard was published in 2006 and a new version of the standard was published in december 2011 which split the ieee c37.118-...
Page 110
Scada supervision, control and data acquisition, see also microscada sct system configuration tool according to standard iec 61850 sha the secure hash algorithm is a family of cryptographic hash functions. The sha 2 family comprise two similar hash functions, with different block sizes, known as sha...
Page 111
Utc coordinated universal time. A coordinated time scale, maintained by the bureau international des poids et mesures (bipm), which forms the basis of a coordinated dissemination of standard frequencies and time signals. Utc is derived from international atomic time (tai) by the addition of a whole ...
Page 112
106.
Page 113
107.
Page 114
— abb ab grid automation products 721 59 västerås, sweden phone: +46 (0) 21 32 50 00 abb.Com/protection-control © copyright 2017 abb. All rights reserved. Specifications subject to change without notice. 1mrk 511 399-uen.